Malware: Types, Analysis Techniques, and Prevention
Added on 2023-02-01
13 Pages4069 Words89 Views
Table of Contents
Introduction......................................................................................................................................2
What is Malware?............................................................................................................................2
Purpose of Malware.........................................................................................................................2
Malware classification.....................................................................................................................3
Virus:...........................................................................................................................................3
Worm:..........................................................................................................................................4
Trojan Horse:...............................................................................................................................4
RootKit:.......................................................................................................................................4
Exploit Kit:..................................................................................................................................4
Spyware:......................................................................................................................................5
Adware:........................................................................................................................................5
Ransomware:...............................................................................................................................5
Anti-Malware Analysis Technique..................................................................................................6
Static Analysis:............................................................................................................................6
Dynamic Analysis:.......................................................................................................................6
Hybrid Analysis:..........................................................................................................................7
Malware detection techniques.........................................................................................................7
Signature-Based malware detection............................................................................................7
Specification-based Malware detection.......................................................................................8
Heuristic based techniques..........................................................................................................8
Prevention from Malwares..............................................................................................................8
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
Introduction......................................................................................................................................2
What is Malware?............................................................................................................................2
Purpose of Malware.........................................................................................................................2
Malware classification.....................................................................................................................3
Virus:...........................................................................................................................................3
Worm:..........................................................................................................................................4
Trojan Horse:...............................................................................................................................4
RootKit:.......................................................................................................................................4
Exploit Kit:..................................................................................................................................4
Spyware:......................................................................................................................................5
Adware:........................................................................................................................................5
Ransomware:...............................................................................................................................5
Anti-Malware Analysis Technique..................................................................................................6
Static Analysis:............................................................................................................................6
Dynamic Analysis:.......................................................................................................................6
Hybrid Analysis:..........................................................................................................................7
Malware detection techniques.........................................................................................................7
Signature-Based malware detection............................................................................................7
Specification-based Malware detection.......................................................................................8
Heuristic based techniques..........................................................................................................8
Prevention from Malwares..............................................................................................................8
Conclusion.....................................................................................................................................11
References......................................................................................................................................12

Introduction
Privacy is one of the resonating terms in the 21st century. In earlier days when the world was not
so digitized we had no concern about our digital privacy but now with increasing use of digitized
systems we cannot deny the fact that now before indulging in anything new from this digital
domain we have to make sure that our identity is safe and no one is going to misuse that if we are
providing it to someone. Our privacy is linked with our data because when online we are
represented by our data and not physically. This data can be anything, from your security number
to your day-to-day GPS locations. We all are aware of ‘data is the new gold’ phrase but are we
aware of malware? These are the basic tools to make data theft easy and hence are of prime
concern to us. Loky, Petya, WannaCry are some of the famous recent malware know to us.
What is Malware?
If we look closely ‘Malware’ is a blend of two words ‘malicious’ and ‘software’. Malwares are
nothing but some software designed intentionally to damage the computer network. [1]
Malwares can take any form, from an executable code to an advertisement. [2] Malwares are
malicious because their intent is not in favor of the user. Malwares are different from bugs in
which the software lacks something that ultimately proves to be harmful for the user.
If a company has issued a software and the concerned company does not supply full information
about the data they are accessing from user’s end then also the software is considered as malware
because the user has not given his/her prior consent to access the data.
Purpose of Malware
Malwares are generated in order to hack the system. Recently, malwares are used extensively to
get unauthorized access on the websites of a government or corporate organizations to garner
information or to disrupt the systems.[3] Some malwares are used to generate money online by
showing advertisement and using click frauds.
Privacy is one of the resonating terms in the 21st century. In earlier days when the world was not
so digitized we had no concern about our digital privacy but now with increasing use of digitized
systems we cannot deny the fact that now before indulging in anything new from this digital
domain we have to make sure that our identity is safe and no one is going to misuse that if we are
providing it to someone. Our privacy is linked with our data because when online we are
represented by our data and not physically. This data can be anything, from your security number
to your day-to-day GPS locations. We all are aware of ‘data is the new gold’ phrase but are we
aware of malware? These are the basic tools to make data theft easy and hence are of prime
concern to us. Loky, Petya, WannaCry are some of the famous recent malware know to us.
What is Malware?
If we look closely ‘Malware’ is a blend of two words ‘malicious’ and ‘software’. Malwares are
nothing but some software designed intentionally to damage the computer network. [1]
Malwares can take any form, from an executable code to an advertisement. [2] Malwares are
malicious because their intent is not in favor of the user. Malwares are different from bugs in
which the software lacks something that ultimately proves to be harmful for the user.
If a company has issued a software and the concerned company does not supply full information
about the data they are accessing from user’s end then also the software is considered as malware
because the user has not given his/her prior consent to access the data.
Purpose of Malware
Malwares are generated in order to hack the system. Recently, malwares are used extensively to
get unauthorized access on the websites of a government or corporate organizations to garner
information or to disrupt the systems.[3] Some malwares are used to generate money online by
showing advertisement and using click frauds.

Malware classification
Classification of malware can be different based on the criteria on which malwares are classified.
The basic criterion depends on the type of work a malware performs. Traditional malwares
include viruses, worms, Trojan horse, etc. Some advanced malwares in which adware, spyware,
ransomware and bots, etc. are classified. We will discuss in brief some of these malwares which
are found on the web.
Image Source: https://medium.com/s/the-firewall/episode5-antimalware-software-b255b627c879
Virus:
This type of malicious software is the most common among the general public. The target area of
a virus is any legitimate file in which an unintended code is inserted without notifying the user.
This code then transfers with the infected file whenever a transfer takes place.[4] Viruses are
self-replicating in nature. Creeper was the first virus to be detected on ARPANET in 1970. Elk
Cloner was the first computer virus appeared in 1982. A computer virus must contain search
routine so that it can copy itself to a location where the search routine locates.
Classification of malware can be different based on the criteria on which malwares are classified.
The basic criterion depends on the type of work a malware performs. Traditional malwares
include viruses, worms, Trojan horse, etc. Some advanced malwares in which adware, spyware,
ransomware and bots, etc. are classified. We will discuss in brief some of these malwares which
are found on the web.
Image Source: https://medium.com/s/the-firewall/episode5-antimalware-software-b255b627c879
Virus:
This type of malicious software is the most common among the general public. The target area of
a virus is any legitimate file in which an unintended code is inserted without notifying the user.
This code then transfers with the infected file whenever a transfer takes place.[4] Viruses are
self-replicating in nature. Creeper was the first virus to be detected on ARPANET in 1970. Elk
Cloner was the first computer virus appeared in 1982. A computer virus must contain search
routine so that it can copy itself to a location where the search routine locates.
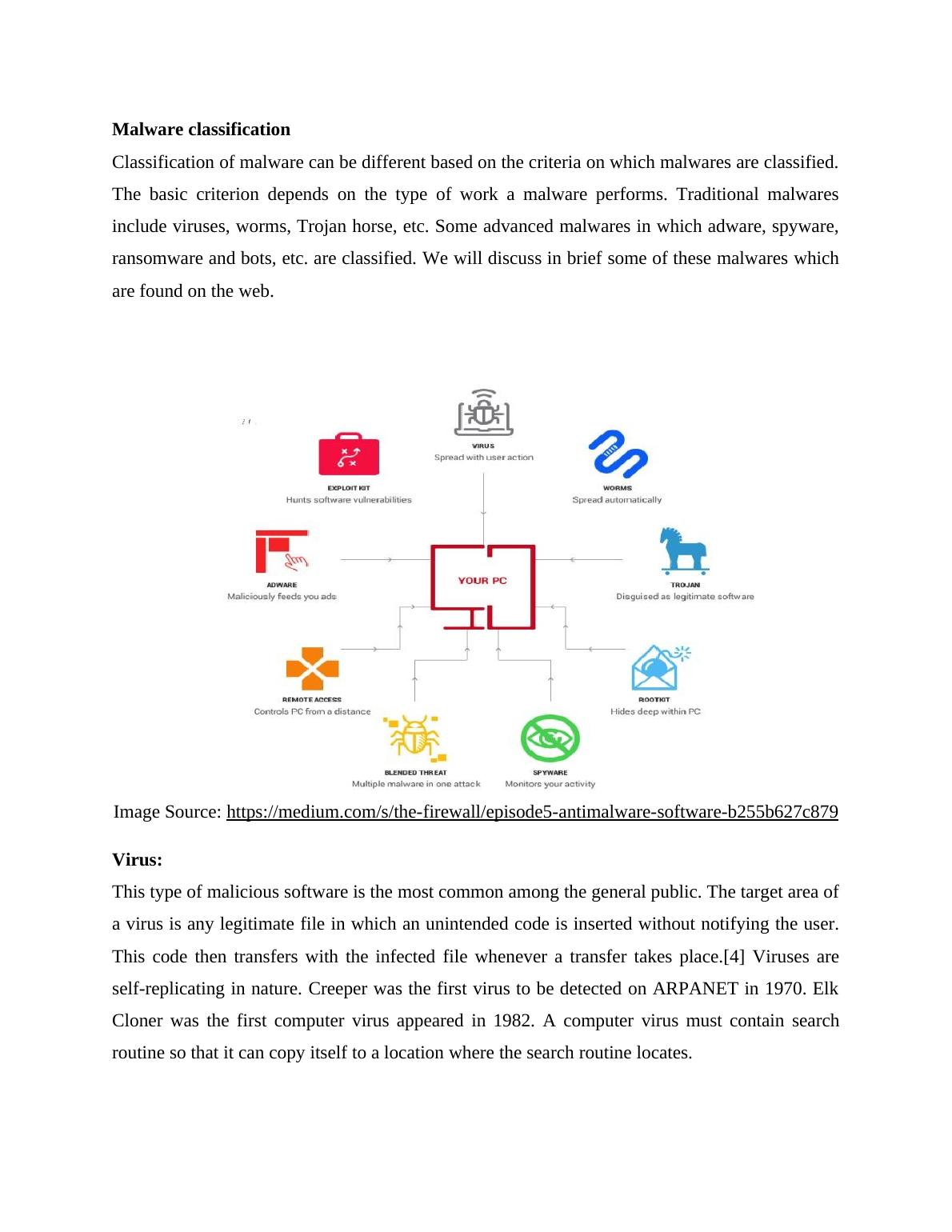
Worm:
Like virus, worms are also self-replicating in nature but they are transferred from one system to
another using a ‘computer network’. [5] Worms wait for a security failure for the targeted
computer to enter into them. Worms affect the bandwidth of the network by occupying the
available space and without affecting the files, unlike viruses which corrupt the entire file.
One well-known worm named Morris worm created by Robert Tappan Morris was released in
1988.
Trojan Horse:
Trojans appear as real/legitimate but are intended to use for illegitimate advantages. [6]
Nowadays most computers are loaded with Trojans. They can take any form like a survey form,
an advertisement. E-mail or any other infected site can become the source of Trojan. Trojans can
cause severe problems as a user might end up filling some confidential information in an
illegitimate form having a legitimate look. Hence to fulfill the requirement of a Trojan software a
user must execute it. Trojans can be backdoor, Exploit, Rootkit etc.
RootKit:
Rootkit, as its name suggests, is a malicious code which is hidden deep inside the root of the
user's computer. The term 'kit' refers to the collection of malicious programs. The rootkit is
installed when the attacker gets administrative access on the user's system. This is the most
severe type of malware as the attacker has administrative or root level access on the computer.
All the files are then in control of the attacker who is now the administrator of the system.
Detection of rootkit is also a very difficult task to perform as the software which is intended to
find the rootkit can be subverted by the rootkit. The ultimate solution if rootkit seems to be the
reinstallation of the operating system. A rootkit is different from bootkit as bootkit attacks on
the boot level and not on the kernel.
Exploit Kit:
Exploit kit also called exploit pack is used to weaken the system so that new malware can be
introduced to perform the malicious activities. A user is made lured to click on a spammed email
or any other means so that the system can be connected to an exploit kit server. Now, the attacker
can download and run the malware program in the victim's system. Exploit kit is the most
popular method of remote access malware.
Like virus, worms are also self-replicating in nature but they are transferred from one system to
another using a ‘computer network’. [5] Worms wait for a security failure for the targeted
computer to enter into them. Worms affect the bandwidth of the network by occupying the
available space and without affecting the files, unlike viruses which corrupt the entire file.
One well-known worm named Morris worm created by Robert Tappan Morris was released in
1988.
Trojan Horse:
Trojans appear as real/legitimate but are intended to use for illegitimate advantages. [6]
Nowadays most computers are loaded with Trojans. They can take any form like a survey form,
an advertisement. E-mail or any other infected site can become the source of Trojan. Trojans can
cause severe problems as a user might end up filling some confidential information in an
illegitimate form having a legitimate look. Hence to fulfill the requirement of a Trojan software a
user must execute it. Trojans can be backdoor, Exploit, Rootkit etc.
RootKit:
Rootkit, as its name suggests, is a malicious code which is hidden deep inside the root of the
user's computer. The term 'kit' refers to the collection of malicious programs. The rootkit is
installed when the attacker gets administrative access on the user's system. This is the most
severe type of malware as the attacker has administrative or root level access on the computer.
All the files are then in control of the attacker who is now the administrator of the system.
Detection of rootkit is also a very difficult task to perform as the software which is intended to
find the rootkit can be subverted by the rootkit. The ultimate solution if rootkit seems to be the
reinstallation of the operating system. A rootkit is different from bootkit as bootkit attacks on
the boot level and not on the kernel.
Exploit Kit:
Exploit kit also called exploit pack is used to weaken the system so that new malware can be
introduced to perform the malicious activities. A user is made lured to click on a spammed email
or any other means so that the system can be connected to an exploit kit server. Now, the attacker
can download and run the malware program in the victim's system. Exploit kit is the most
popular method of remote access malware.

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Types of Malicious Software - PDFlg...
|25
|4952
|204
Malware Analysis Assignment PDFlg...
|29
|6377
|378
Malware Trends: Good News and Bad Newslg...
|8
|1895
|24
Assignment on Risks and Risk Managementlg...
|11
|781
|13
COS30015 IT Security : Malware Analysislg...
|12
|4290
|62
Understanding Malware: Types, Detection, and Analysislg...
|12
|899
|33
