Security and Privacy Issues in Cloud Computing: A Comprehensive Study
22 Pages7085 Words56 Views
Added on 2020-10-01
About This Document
This study addresses the recent existing security and privacy issues in cloud environment. It discusses the background and related work, including a survey of security and privacy issues in cloud computing, database security in cloud, identity and access management in cloud environment, and more. The study also provides experimental analysis and a conclusion. The subject is cloud computing and its related security and privacy concerns. The course code, course name, and college/university are not mentioned.
Security and Privacy Issues in Cloud Computing: A Comprehensive Study
Added on 2020-10-01
ShareRelated Documents
Table of ContentsABSTRACT....................................................................................................................................................2INTRODUCTION...........................................................................................................................................2PROBLEM DOMAIN......................................................................................................................................2BACKGROUND/RELATED WORK..................................................................................................................31.Privacy Protection and Data Security in Cloud Computing: A Survey, Challenges, and Solutions....32.A Study and Survey of Security and Privacy Issues in Cloud Computing..........................................53.Database Security in Cloud..............................................................................................................74.Identity and Access Management in Cloud Environment: Mechanisms and Challenges.................95.Service Delivery Models of Cloud Computing: Security Issues and Open Challenges....................106.Cloud Computing Security and Privacy: An Empirical Study..........................................................117.Security and Privacy of Sensitive Data in Cloud Computing: A Survey of Recent Developments...128.SEPRICC: Security and Privacy in Cloud Computing.......................................................................139.Layers of Cloud – IaaS, PaaS and SaaS: A Survey............................................................................1410.Challenges and Prosperity Research in Cloud Computing..............................................................1411.Cloud Computing Service Models: A Comparative Study...............................................................1512.A Review Paper on Cloud Computing............................................................................................16EXPERIMENTAL ANALYSIS:.........................................................................................................................17CONCLUSION.............................................................................................................................................20SYNOPSIS...................................................................................................................................................20Aim of the Project..................................................................................................................................20Method..................................................................................................................................................20Results...................................................................................................................................................20Discussion..............................................................................................................................................21Conclusion.............................................................................................................................................21REFERENCES..............................................................................................................................................211

ABSTRACT: With the recent advancements, the technology of cloud computing has also gaining risein terms of popularity and success. Cloud computing is a rising technology standard which relocatesrecent technological as well as concept of computing into solutions like utility familiar to water systemsand electricity. Cloud computing is providing huge amount of advantages which includes economicsaving, service flexibility and configurable computer resources. Although with this increasing popularityof cloud computing carries some critical security and privacy issues due to the outsourcing of businessapplications and data to third party. The concerns related to security and privacy are seems to be initialhurdle in the adoption of cloud in vast amount. Cloud introduces some advance concepts like resourcesharing, multi tenancy and outsourcing comes along with new challenges in the security community.Hence the goal of this study is to address the recent existing security and privacy issues in cloudenvironment. Additionally the capability to pursue and adapt the measures of security that was developedfor traditional computing systems, initiating new security policies, models and protocols for addressingdistinct security challenges of cloud. We present a comprehensive study about cloud computing and itsrelated security and privacy concerns. INTRODUCTION: Cloud computer constitutes as an advance firm in the field of informationtechnology and related to the virtualization of the available resources of computer on request. Cloudcomputing liberates times as well as cost for businesses. Along with that the process of computingcontemplates revolutionary advancement in technology related to how companies are constructs,organizes and deployed enterprise applications on the internet. Those clouds computing that arevirtualized specifically provides delivery models of cloud computing i.e. software as a service, platformas a service and infrastructure as a service. However in recent times, the issues regarding security andprivacy in cloud computing considered as a serious component in the any model adaptation of cloudservice delivery. Cloud computing support few technologies in its process hence this model somehowincludes possible security hazards. Hence so far, the security issues in cloud computing have hardlyreceive at service delivery level. Some specific security concerns are network security, integrations, webapplication security, vulnerabilities presents in virtualized environment, physical security and datasecurity. The goal of this research is to provide a comprehensive study of security threats regarding totheir respected cloud service deliver model. We also characterized five most specific security and privacyaspects such as confidentiality, integrity, accountability, availability and privacy preservability. Our mainaim behind this research is to comprehensively present the security threats with respect to their cloudservice deliver models. This study also determines how service delivery models differ from existingenterprise applications, classify these models, and investigate the inherent security challenges. This studyprimarily focuses on the security concerns of each layer of the cloud-service delivery model, as well as onexisting solutions and approaches. In addition, countermeasures to potential security threats are alsopresented for each cloud model.PROBLEM DOMAIN: From previous years, cloud computing is considered as an importantplatform from the perspective of hosting and delivering services through the internet. It gained popularityby providing several computing services like cloud hosting, cloud storage and cloud servers etc. in orderto assist multiple kind businesses as well as in academics [2]. But it suffers from few major security andprivacy challenges. Privacy is cloud an important aspect for the customers. If we consider privacy incloud there are many threats for sensitive data of users over the cloud storage. Although the structure of2

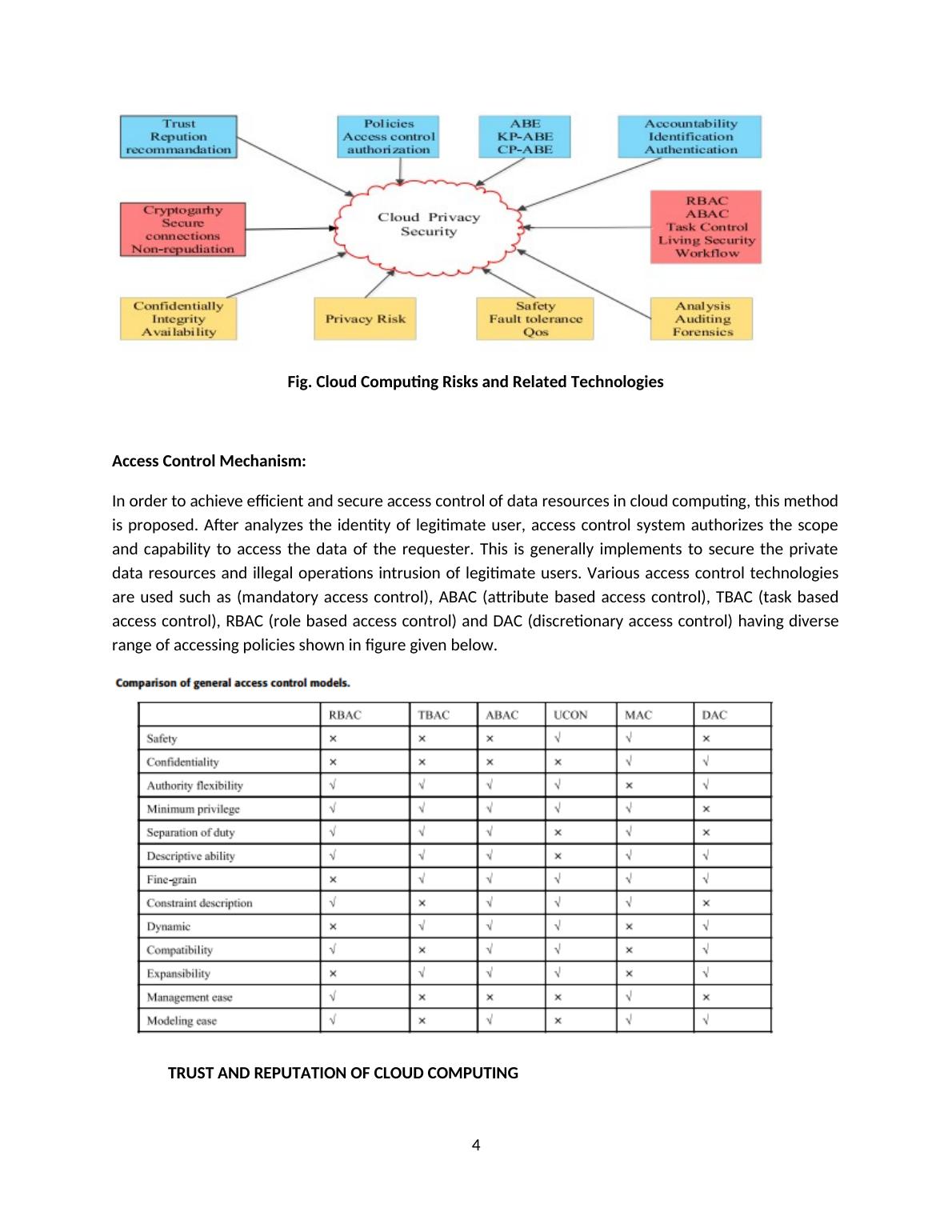
cloud computing is getting advance and progressing fast conceptually as well as in reality. But servicequality, security and privacy, economic, contractual issues still remains crucial challenges. After reviewing several research articles, we conclude that they somehow interlinked over these familiarcategories:Issues of privacy, compliance, trust, legal and audit in cloud.Vulnerabilities and threats present in cloud.Challenges faced by organizations while adopting cloud solutionRecommendations and solutions for cloud security issues and concerns BACKGROUND/RELATED WORK:1.Privacy Protection and Data Security in Cloud Computing: A Survey, Challenges, and SolutionsPrivacy and security related issues are very critical with regards to cloud computing. There are manycurrent research schemes carries out related to access control based cloud computing privacyprotection, trust and reputation and Attribute Based Encryption (ABE). Along with that it also discussesKP-ABE i.e. Key Policy Attribute Based Encryption, CP i.e. Ciphertext Policy Attribute Based Encryption ,revocation, mechanism, fine grain, trace mechanism, access structure, multi authority, proxy re-encryption, reputation, trust, searchable encryption, hierarchical encryption, hierarchical key andextension of tradition access control . Still they are dissipate or had insufficient unified logic. This paperreviewed and identified progressive researches related to these factors and concludes the result on thebasis of its characterization.1.Access control based Mechanism2.Trust and Reputation of cloud computing3.Attribute Based EncryptionCLOUD COMPUTING PRIVACY PROTECTION FRAMEWORKPrivacy data of user is confidential in cloud computing. Although the presence of virtualization, big data,multi-tenancy, data outsourcing storage and some other technologies hence generate the risk of privacydisclosure of user’s data (Sun, 2019). 3

Fig. Cloud Computing Risks and Related TechnologiesAccess Control Mechanism:In order to achieve efficient and secure access control of data resources in cloud computing, this methodis proposed. After analyzes the identity of legitimate user, access control system authorizes the scopeand capability to access the data of the requester. This is generally implements to secure the privatedata resources and illegal operations intrusion of legitimate users. Various access control technologiesare used such as (mandatory access control), ABAC (attribute based access control), TBAC (task basedaccess control), RBAC (role based access control) and DAC (discretionary access control) having diverserange of accessing policies shown in figure given below.TRUST AND REPUTATION OF CLOUD COMPUTING4
Trust and Reputation TR are very crucial to consider for the adaptation of cloud service and arefirmly relatable to privacy protection. Cloud computing system needs trust of user andreputation concerning to information to be entirely disclosed that will introduce undiscoveredprivacy risks of users. Lately different compounds of multiple methods give a nearly optimalsolution for the management of TR in privacy protection of cloud computing services.ABE OF CLOUD COMPUTINGABE related to public key mechanism. The object is decryption of a group instead of a singleuser. Its essential feature is the origination of attribute concept. This group is related to thoseusers that belong to specific fusion of attribute values. ABE introduces advantages in cloudcomputing. ABE is preferable for architecture of cloud computing. Additionally it also providesthe ability to entirely implements data access control in the platform of cloud. Researches hasshown significant progress like attribute revocation, proxy re-encryption, multi-authority,hierarchical encryption, policy flexibility etc. Still there are multiple issues that require furtherresearch [10].Fig. Comparison of several access control model-based encryption2.A Study and Survey of Security and Privacy Issues in Cloud ComputingCloud computing is an emerging model which transforms the information technological ways ofindividuals as well as the organizations. It involves some significant aspects like broad network,rapid elasticity, resource pooling board network access and characterizes services that help theorganization in converting to agile. Characteristics of cloud are related to few open issues suchas scalability, availability, interoperability and security. The security and privacy problemsgenerally come along with cloud deployment, delivery models are main source behind theseissues in current cloud computing world. This paper discusses security and privacy issuesaddressed between the development and delivery. Cloud computing becomes a fragment of business strategies universally now. Cloud adoption isnow become a part of business strategies globally. All sectors of enterprises, research institutes,financial institutes, government agencies and education sectors are adopting cloud computing.Latest advance technologies such as social media, big data analysis and mobility are basic reasonbehind the enforcement of cloud computing in organizations. Few popular cloud providers areSalesforce.com, Amazon’s EC2 (Elastic Compute Cloud), Google’s suite of apps (Google Docs,Google Calendar and Gmail etc), IBM blue cloud, Microsoft’s Azure etc. Along with manyadvantages cloud computing involves issues regarding privacy and security of users. Even aftermany years of cloud existence it still requires adequate trust level in terms of requirements ofsecurity and privacy (Ahmad, 2017)5

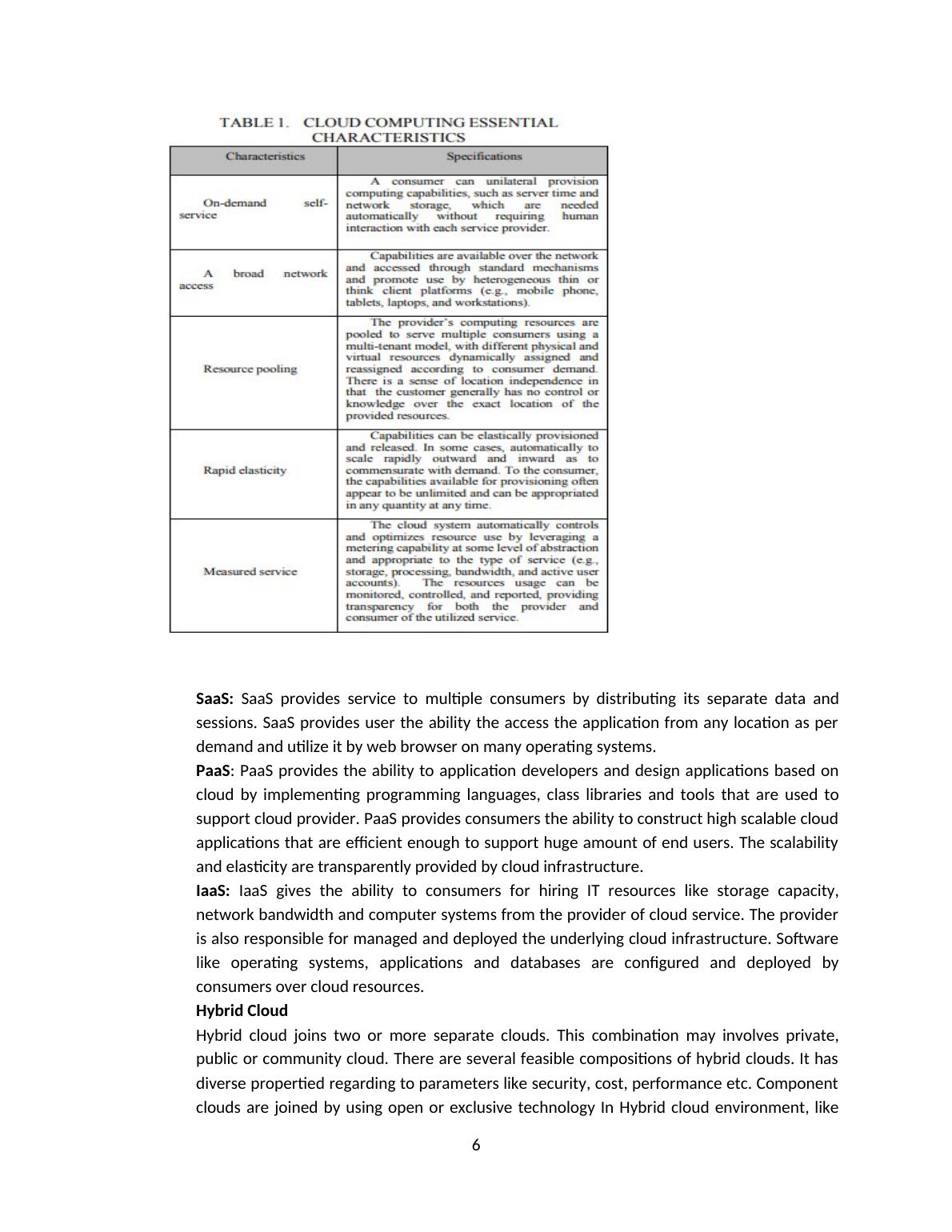
SaaS: SaaS providesservice to multiple consumers by distributing its separate data andsessions. SaaS provides user the ability the access the application from any location as perdemand and utilize it by web browser on many operating systems.PaaS: PaaS provides the ability to application developers and design applications based oncloud by implementing programming languages, class libraries and tools that are used tosupport cloud provider. PaaS provides consumers the ability to construct high scalable cloudapplications that are efficient enough to support huge amount of end users. The scalabilityand elasticity are transparently provided by cloud infrastructure.IaaS: IaaS gives the ability to consumers for hiring IT resources like storage capacity,network bandwidth and computer systems from the provider of cloud service. The provideris also responsible for managed and deployed the underlying cloud infrastructure. Softwarelike operating systems, applications and databases are configured and deployed byconsumers over cloud resources.Hybrid CloudHybrid cloud joins two or more separate clouds. This combination may involves private,public or community cloud. There are several feasible compositions of hybrid clouds. It hasdiverse propertied regarding to parameters like security, cost, performance etc. Componentclouds are joined by using open or exclusive technology In Hybrid cloud environment, like6
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cloud Computing - Research Issues, Challenges, Architecture, Platforms and Applications: A Surveylg...
|5
|4629
|338
Security Threats in Cloud Computing and Preventive Measureslg...
|16
|3755
|361
Optimal Optimization Based On CLOUD COMPUTING ASSIGNMENT -3lg...
|32
|8368
|223
Paper - Data Security Issues In Cloud Computinglg...
|4
|1694
|129
Cloud Computing in Organizationslg...
|14
|3472
|123
Information Security Assignment | Security and Privacylg...
|9
|2067
|44
