impact of network topology, Communication, and bandwidth requirements
VerifiedAdded on 2022/01/22
|89
|14911
|1497
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Table of Contents
Executive summary:-................................................................................................... 3
Objective scope:-........................................................................................................ 3
Introduction............................................................................................................... 4
Discuss the benefits and constraints of different network types and standards..............................4
Explain the impact of network topology, Communication, and bandwidth requirements...............14
Compare common networking principles and how protocols enable the effectiveness of networked
systems................................................................................................................... 19
Discuss the operating principles of networking devices and server types..................................20
Discuss the inter-dependence of workstation hardware with relevant networking software............25
Explore a range of server types and justify the selection of a server, considering a given scenario
regarding cost and performance optimisation....................................................................33
Design a networked system to meet a given specification.....................................................34
Install and configure network services and applications on your choice....................................39
Test and evaluate the design to meet the requirements and analyse user feedback with the aim of
improving efficiency.................................................................................................. 45
Implement a networked system based on a prepared design..................................................49
Document and analyse test results against expected results...................................................73
Design a maintenance schedule to support the networked system...........................................81
Recommend potential enhancements for the networked systems............................................83
Use critical reflection to evaluate own work and justify valid conclusions.................................84
Critically evaluate the topology protocol selected for a given scenario to demonstrate the
efficient utilization of a networking System......................................................................85
Reference:-.............................................................................................................. 85
1 | P a g e
Executive summary:-................................................................................................... 3
Objective scope:-........................................................................................................ 3
Introduction............................................................................................................... 4
Discuss the benefits and constraints of different network types and standards..............................4
Explain the impact of network topology, Communication, and bandwidth requirements...............14
Compare common networking principles and how protocols enable the effectiveness of networked
systems................................................................................................................... 19
Discuss the operating principles of networking devices and server types..................................20
Discuss the inter-dependence of workstation hardware with relevant networking software............25
Explore a range of server types and justify the selection of a server, considering a given scenario
regarding cost and performance optimisation....................................................................33
Design a networked system to meet a given specification.....................................................34
Install and configure network services and applications on your choice....................................39
Test and evaluate the design to meet the requirements and analyse user feedback with the aim of
improving efficiency.................................................................................................. 45
Implement a networked system based on a prepared design..................................................49
Document and analyse test results against expected results...................................................73
Design a maintenance schedule to support the networked system...........................................81
Recommend potential enhancements for the networked systems............................................83
Use critical reflection to evaluate own work and justify valid conclusions.................................84
Critically evaluate the topology protocol selected for a given scenario to demonstrate the
efficient utilization of a networking System......................................................................85
Reference:-.............................................................................................................. 85
1 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2 | P a g e

3 | P a g e
Executive summary:-
Objective scope:-
4 | P a g e
Objective scope:-
4 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction
NIC ASIA Bank was established as Nepal Industrial and Commercial Bank on 21 July 1998.
It was retitled NIC ASIA Bank on 30 June 2013 after it resolved with Bank of Asian Nepal's
first combination of two commercial banks in its Nepal history. After the union, NIC ASIA
was acclaimed as “Bank of the Year 2013-Nepal” by The Banker, Financial Times, UK. NIC
ASIA BANK is one of the largest banks in Nepal and its working more than 300 branches
within Nepal with a good number of services and IT infrastructure. Here for the past few
years, I have been working as a network or IT officer and along with it branch which is
opening in Kathmandu with its Depart name and I need to create design and deploy the
protocols and network types infrastructure along with standards and I also need to configure
several topologies physically and logically. In this part, I am going to configure the server
selection and bandwidth deployment with a selection of a good number of technology and
topology.
Discuss the benefits and constraints of different network types and standards
What is networking? A computer network is a consolidation of computers in sync through
networked devices and media in a structured aspect and these computers communicate to
communicate with each other. About going along with the report it will confession of
networking principles, protocols along with devices, including benefits and constraints of
networked explanation in the network, the impact of network topology, communication and
bandwidth qualification, the capability of networking systems, operating principles of
networking devices and server types and networking software. (What Is Networking? (2021))
Network protocol:-
Network protocols are official standards and policies compromised of rules measures and
formats that describe communication between two or more devices over a network. Network
protocols govern the end-to-end process of appropriate secure and managed data or network
communication. (What Is Networking protocol? (2021))
Network type
There are mainly 3 types of computer networks:
LAN (Local Area Network):
The LAN which is also known as the private network in the building is an area that is several
km in size. They are mainly used to connect with servers and workstations in offices and
factories to share resources and exchange information. I have also used the LANs which are
mainly used for resource sharing expensive hardware like printers and CD/ROM where one
can share by mainly users when they are attached to a network through LAN. (What Is LAN?
(2021))
5 | P a g e
NIC ASIA Bank was established as Nepal Industrial and Commercial Bank on 21 July 1998.
It was retitled NIC ASIA Bank on 30 June 2013 after it resolved with Bank of Asian Nepal's
first combination of two commercial banks in its Nepal history. After the union, NIC ASIA
was acclaimed as “Bank of the Year 2013-Nepal” by The Banker, Financial Times, UK. NIC
ASIA BANK is one of the largest banks in Nepal and its working more than 300 branches
within Nepal with a good number of services and IT infrastructure. Here for the past few
years, I have been working as a network or IT officer and along with it branch which is
opening in Kathmandu with its Depart name and I need to create design and deploy the
protocols and network types infrastructure along with standards and I also need to configure
several topologies physically and logically. In this part, I am going to configure the server
selection and bandwidth deployment with a selection of a good number of technology and
topology.
Discuss the benefits and constraints of different network types and standards
What is networking? A computer network is a consolidation of computers in sync through
networked devices and media in a structured aspect and these computers communicate to
communicate with each other. About going along with the report it will confession of
networking principles, protocols along with devices, including benefits and constraints of
networked explanation in the network, the impact of network topology, communication and
bandwidth qualification, the capability of networking systems, operating principles of
networking devices and server types and networking software. (What Is Networking? (2021))
Network protocol:-
Network protocols are official standards and policies compromised of rules measures and
formats that describe communication between two or more devices over a network. Network
protocols govern the end-to-end process of appropriate secure and managed data or network
communication. (What Is Networking protocol? (2021))
Network type
There are mainly 3 types of computer networks:
LAN (Local Area Network):
The LAN which is also known as the private network in the building is an area that is several
km in size. They are mainly used to connect with servers and workstations in offices and
factories to share resources and exchange information. I have also used the LANs which are
mainly used for resource sharing expensive hardware like printers and CD/ROM where one
can share by mainly users when they are attached to a network through LAN. (What Is LAN?
(2021))
5 | P a g e
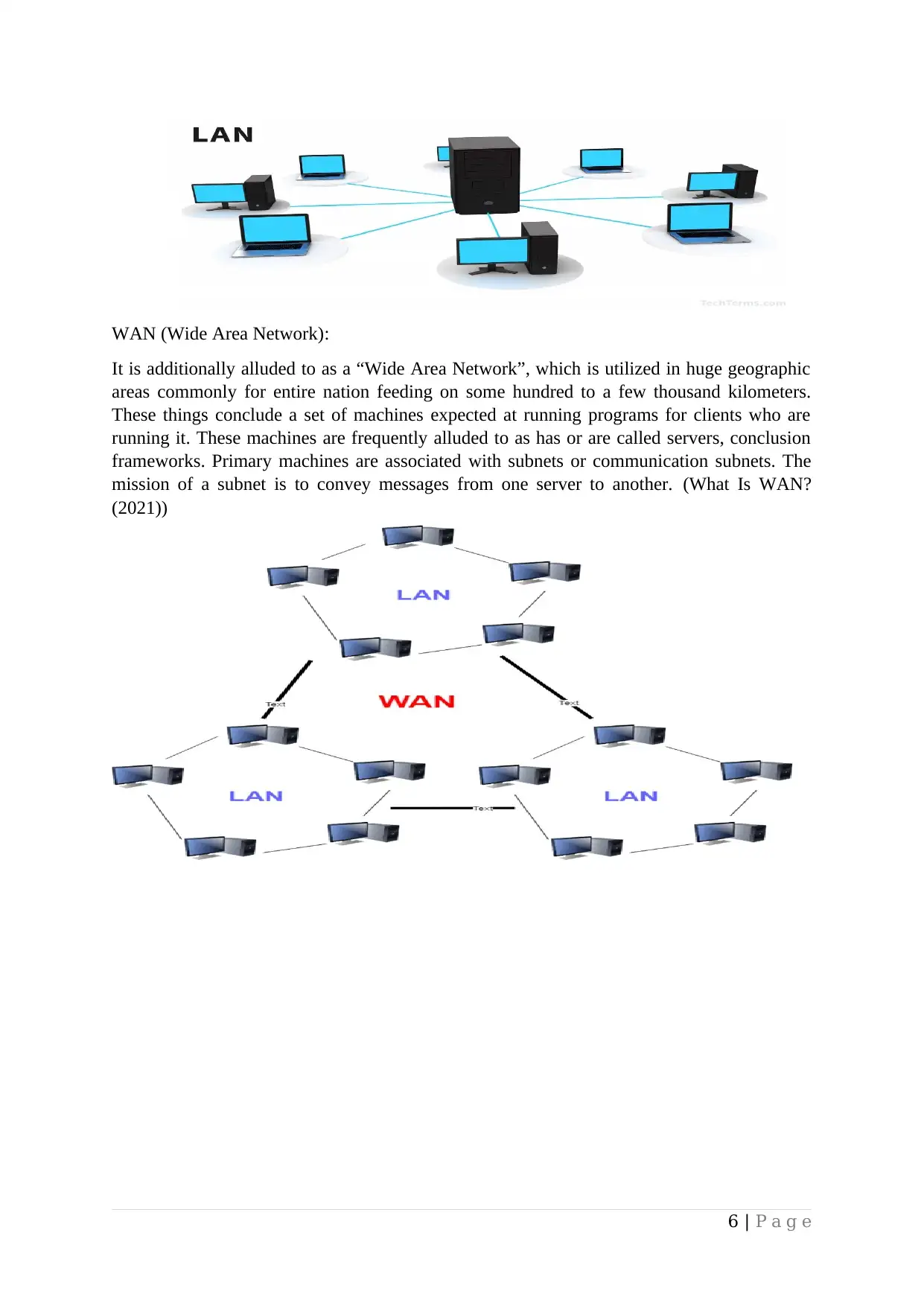
WAN (Wide Area Network):
It is additionally alluded to as a “Wide Area Network”, which is utilized in huge geographic
areas commonly for entire nation feeding on some hundred to a few thousand kilometers.
These things conclude a set of machines expected at running programs for clients who are
running it. These machines are frequently alluded to as has or are called servers, conclusion
frameworks. Primary machines are associated with subnets or communication subnets. The
mission of a subnet is to convey messages from one server to another. (What Is WAN?
(2021))
6 | P a g e
It is additionally alluded to as a “Wide Area Network”, which is utilized in huge geographic
areas commonly for entire nation feeding on some hundred to a few thousand kilometers.
These things conclude a set of machines expected at running programs for clients who are
running it. These machines are frequently alluded to as has or are called servers, conclusion
frameworks. Primary machines are associated with subnets or communication subnets. The
mission of a subnet is to convey messages from one server to another. (What Is WAN?
(2021))
6 | P a g e

MAN (Metropolitan Area Network):-
A metropolitan area network (MAN) is a computer network that connects computers within a
metropolitan area, which could be a single large city, multiple cities, and towns, or any given
large area with multiple buildings. A metropolitan area network (MAN) is larger than a local
area network (LAN) but smaller than a wide area network (WAN) (WAN). MANs do not
have to be in urban areas; the term "metropolitan" implies the size of the network, not the
demographics of the area that it serves. (What Is MAN? (2021))
7 | P a g e
A metropolitan area network (MAN) is a computer network that connects computers within a
metropolitan area, which could be a single large city, multiple cities, and towns, or any given
large area with multiple buildings. A metropolitan area network (MAN) is larger than a local
area network (LAN) but smaller than a wide area network (WAN) (WAN). MANs do not
have to be in urban areas; the term "metropolitan" implies the size of the network, not the
demographics of the area that it serves. (What Is MAN? (2021))
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2 more networks types are widely used which are:-
Peer to peer networks:-
In a peer-to-peer network, computers are connected over the internet and files can be
transferred directly between them without the need for a central server. Each computer in a
peer-to-peer network serves as both a server and a client. To join a peer-to-peer network, all
you need is an internet connection and software like LimeWire, Bear share, or others. You
can search for files on other people's computers once you've linked to a peer-to-peer network.
(What Is Peer-to-peernetworks? (2021))
Advantages of peer to peer network:-
There is no need for an operating system
Doesn’t need an expensive server because individual workstations are used to
access files.
Installation and setup are quite painless because of the building support in the
modern operating system.
Much easier to set up doesn’t need specialist knowledge.
The disadvantage of paper to peer networks:-
Since each computer might be accessed by others it can slow down the
performance of the user.
8 | P a g e
Peer to peer networks:-
In a peer-to-peer network, computers are connected over the internet and files can be
transferred directly between them without the need for a central server. Each computer in a
peer-to-peer network serves as both a server and a client. To join a peer-to-peer network, all
you need is an internet connection and software like LimeWire, Bear share, or others. You
can search for files on other people's computers once you've linked to a peer-to-peer network.
(What Is Peer-to-peernetworks? (2021))
Advantages of peer to peer network:-
There is no need for an operating system
Doesn’t need an expensive server because individual workstations are used to
access files.
Installation and setup are quite painless because of the building support in the
modern operating system.
Much easier to set up doesn’t need specialist knowledge.
The disadvantage of paper to peer networks:-
Since each computer might be accessed by others it can slow down the
performance of the user.
8 | P a g e
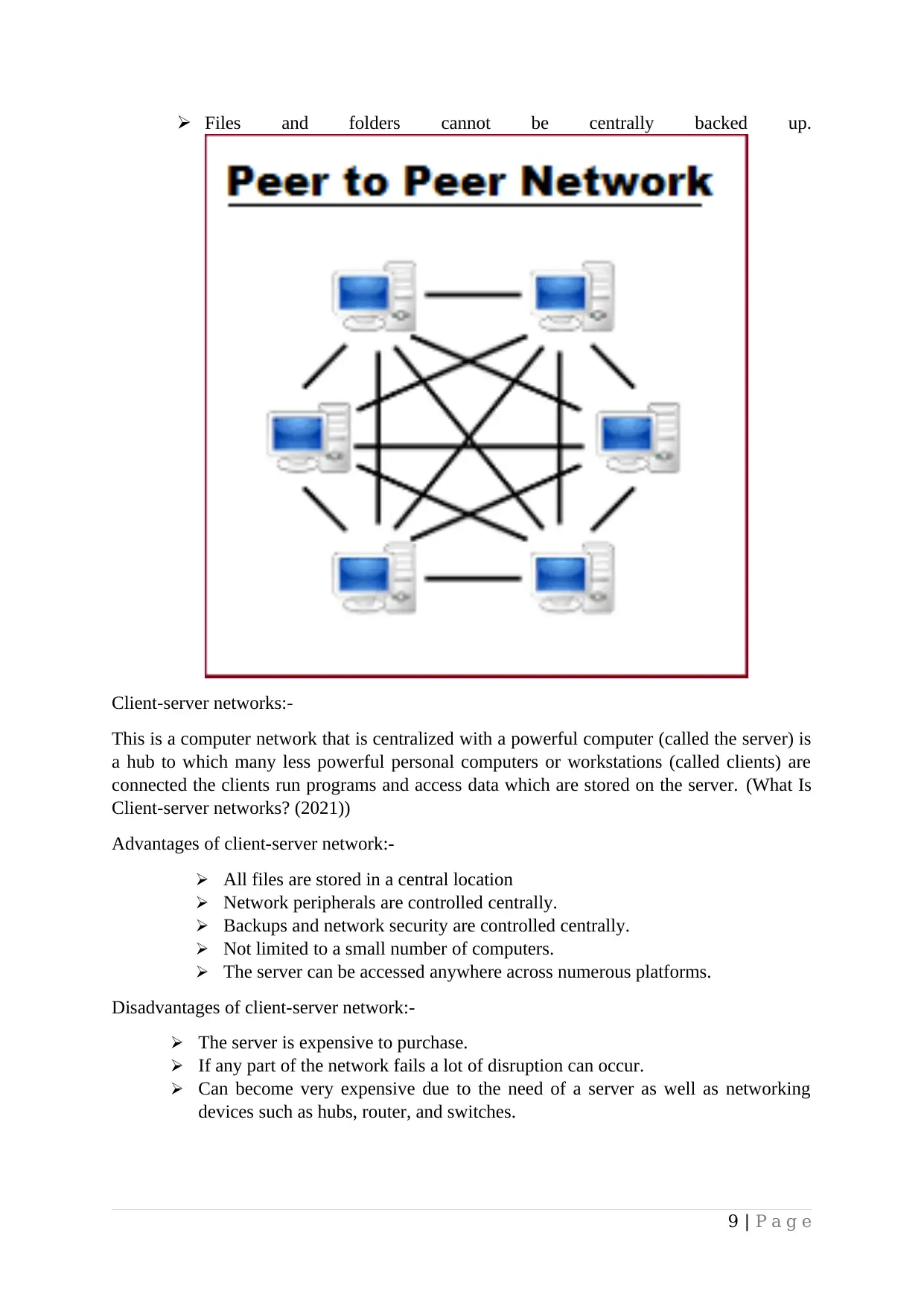
Files and folders cannot be centrally backed up.
Client-server networks:-
This is a computer network that is centralized with a powerful computer (called the server) is
a hub to which many less powerful personal computers or workstations (called clients) are
connected the clients run programs and access data which are stored on the server. (What Is
Client-server networks? (2021))
Advantages of client-server network:-
All files are stored in a central location
Network peripherals are controlled centrally.
Backups and network security are controlled centrally.
Not limited to a small number of computers.
The server can be accessed anywhere across numerous platforms.
Disadvantages of client-server network:-
The server is expensive to purchase.
If any part of the network fails a lot of disruption can occur.
Can become very expensive due to the need of a server as well as networking
devices such as hubs, router, and switches.
9 | P a g e
Client-server networks:-
This is a computer network that is centralized with a powerful computer (called the server) is
a hub to which many less powerful personal computers or workstations (called clients) are
connected the clients run programs and access data which are stored on the server. (What Is
Client-server networks? (2021))
Advantages of client-server network:-
All files are stored in a central location
Network peripherals are controlled centrally.
Backups and network security are controlled centrally.
Not limited to a small number of computers.
The server can be accessed anywhere across numerous platforms.
Disadvantages of client-server network:-
The server is expensive to purchase.
If any part of the network fails a lot of disruption can occur.
Can become very expensive due to the need of a server as well as networking
devices such as hubs, router, and switches.
9 | P a g e

Cloud server:-
This is a server that is build hosted and delivered through a cloud computing platform over
the internet a cloud server can also be called a virtual server. There are two types of cloud
servers logical and physical. Logical is when it is delivered through server virtualization, the
physical is logically distributed into or more logical servers but the physical server is also
accessed through the internet. (What Is Cloud server? (2021))
Cluster server:-
These are computers that are connected and operate close to acting as a single computer. The
performance of a cluster server can match that of an expensive computer or sometimes even
resulting in supercomputer capabilities. Clustering is the connectivity of two or more servers
in orderto work like one. (What Is Cluster server? (2021))
Centralized server:-
This server which acts as the agent for all communications this server stores both
communications and user account information. (What Is Centralized server? (2021))
Virtualized server:-
Server virtualization is a virtualization method that includes dividing a physical server into a
number several virtual servers with the help of virtualization software. In server
virtualization, each virtual server runs multiple operating system instances at the same time.
(What Is Virtualized server? (2021))
Network standards:-
Network standards describe the rules for data communications that are needed for the
interoperability of networking technologies and processes. Standards help in creating and
maintaining an open market and allow different vendors to compete on the basis of the
quality of their products while being compatible with current market products. (What Is
Network standards? (2021))
OSI:-
10 | P a g e
This is a server that is build hosted and delivered through a cloud computing platform over
the internet a cloud server can also be called a virtual server. There are two types of cloud
servers logical and physical. Logical is when it is delivered through server virtualization, the
physical is logically distributed into or more logical servers but the physical server is also
accessed through the internet. (What Is Cloud server? (2021))
Cluster server:-
These are computers that are connected and operate close to acting as a single computer. The
performance of a cluster server can match that of an expensive computer or sometimes even
resulting in supercomputer capabilities. Clustering is the connectivity of two or more servers
in orderto work like one. (What Is Cluster server? (2021))
Centralized server:-
This server which acts as the agent for all communications this server stores both
communications and user account information. (What Is Centralized server? (2021))
Virtualized server:-
Server virtualization is a virtualization method that includes dividing a physical server into a
number several virtual servers with the help of virtualization software. In server
virtualization, each virtual server runs multiple operating system instances at the same time.
(What Is Virtualized server? (2021))
Network standards:-
Network standards describe the rules for data communications that are needed for the
interoperability of networking technologies and processes. Standards help in creating and
maintaining an open market and allow different vendors to compete on the basis of the
quality of their products while being compatible with current market products. (What Is
Network standards? (2021))
OSI:-
10 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
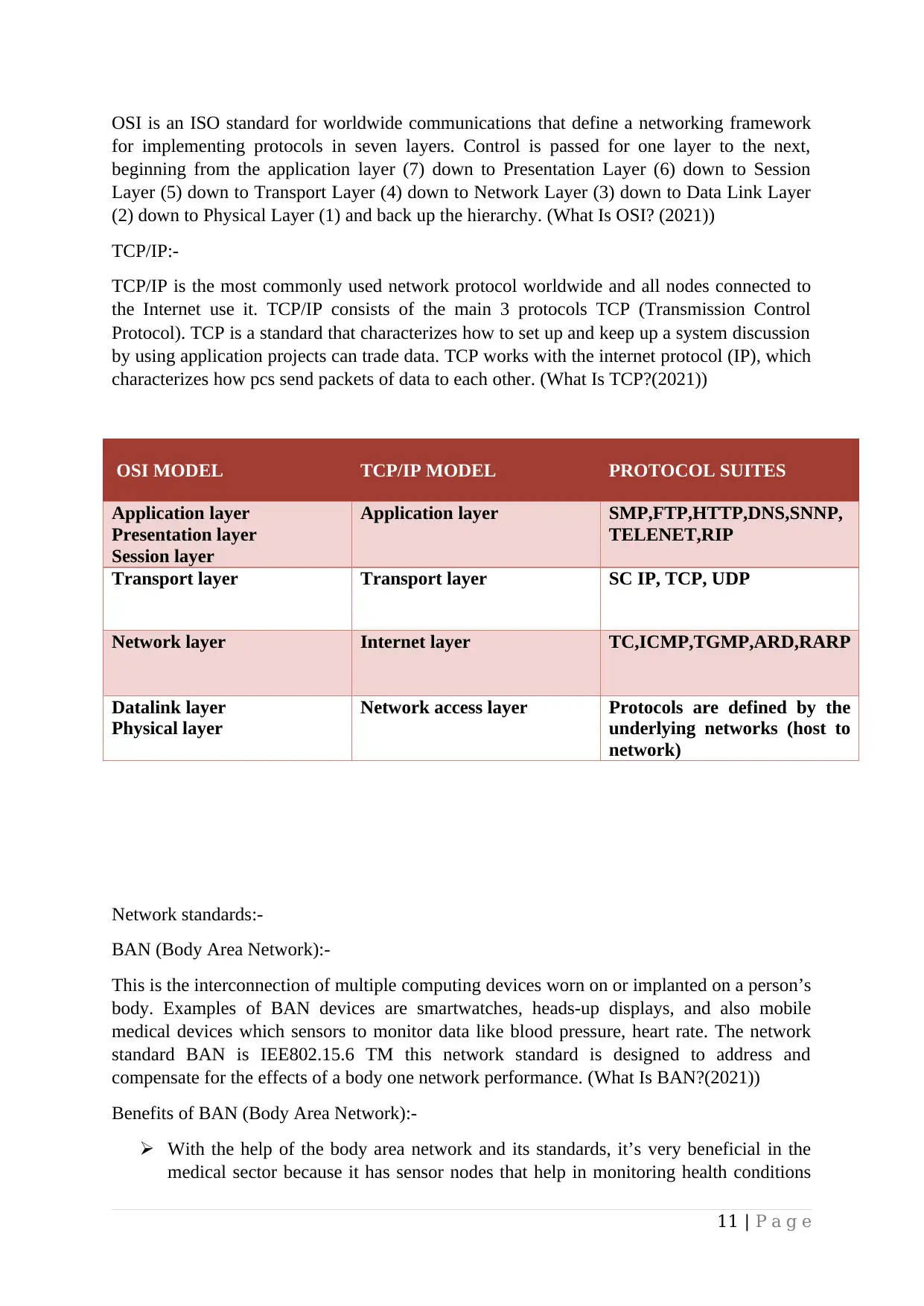
OSI is an ISO standard for worldwide communications that define a networking framework
for implementing protocols in seven layers. Control is passed for one layer to the next,
beginning from the application layer (7) down to Presentation Layer (6) down to Session
Layer (5) down to Transport Layer (4) down to Network Layer (3) down to Data Link Layer
(2) down to Physical Layer (1) and back up the hierarchy. (What Is OSI? (2021))
TCP/IP:-
TCP/IP is the most commonly used network protocol worldwide and all nodes connected to
the Internet use it. TCP/IP consists of the main 3 protocols TCP (Transmission Control
Protocol). TCP is a standard that characterizes how to set up and keep up a system discussion
by using application projects can trade data. TCP works with the internet protocol (IP), which
characterizes how pcs send packets of data to each other. (What Is TCP?(2021))
OSI MODEL TCP/IP MODEL PROTOCOL SUITES
Application layer
Presentation layer
Session layer
Application layer SMP,FTP,HTTP,DNS,SNNP,
TELENET,RIP
Transport layer Transport layer SC IP, TCP, UDP
Network layer Internet layer TC,ICMP,TGMP,ARD,RARP
Datalink layer
Physical layer
Network access layer Protocols are defined by the
underlying networks (host to
network)
Network standards:-
BAN (Body Area Network):-
This is the interconnection of multiple computing devices worn on or implanted on a person’s
body. Examples of BAN devices are smartwatches, heads-up displays, and also mobile
medical devices which sensors to monitor data like blood pressure, heart rate. The network
standard BAN is IEE802.15.6 TM this network standard is designed to address and
compensate for the effects of a body one network performance. (What Is BAN?(2021))
Benefits of BAN (Body Area Network):-
With the help of the body area network and its standards, it’s very beneficial in the
medical sector because it has sensor nodes that help in monitoring health conditions
11 | P a g e
for implementing protocols in seven layers. Control is passed for one layer to the next,
beginning from the application layer (7) down to Presentation Layer (6) down to Session
Layer (5) down to Transport Layer (4) down to Network Layer (3) down to Data Link Layer
(2) down to Physical Layer (1) and back up the hierarchy. (What Is OSI? (2021))
TCP/IP:-
TCP/IP is the most commonly used network protocol worldwide and all nodes connected to
the Internet use it. TCP/IP consists of the main 3 protocols TCP (Transmission Control
Protocol). TCP is a standard that characterizes how to set up and keep up a system discussion
by using application projects can trade data. TCP works with the internet protocol (IP), which
characterizes how pcs send packets of data to each other. (What Is TCP?(2021))
OSI MODEL TCP/IP MODEL PROTOCOL SUITES
Application layer
Presentation layer
Session layer
Application layer SMP,FTP,HTTP,DNS,SNNP,
TELENET,RIP
Transport layer Transport layer SC IP, TCP, UDP
Network layer Internet layer TC,ICMP,TGMP,ARD,RARP
Datalink layer
Physical layer
Network access layer Protocols are defined by the
underlying networks (host to
network)
Network standards:-
BAN (Body Area Network):-
This is the interconnection of multiple computing devices worn on or implanted on a person’s
body. Examples of BAN devices are smartwatches, heads-up displays, and also mobile
medical devices which sensors to monitor data like blood pressure, heart rate. The network
standard BAN is IEE802.15.6 TM this network standard is designed to address and
compensate for the effects of a body one network performance. (What Is BAN?(2021))
Benefits of BAN (Body Area Network):-
With the help of the body area network and its standards, it’s very beneficial in the
medical sector because it has sensor nodes that help in monitoring health conditions
11 | P a g e

each node is able of capturing physiological data it also helps in long-term health
monitoring
Assists in the communication between individuals and machines
Used in the military for security purposes
Disadvantages of BAN:-
Battery life
Wired network restriction between body movement
Lack of integration sensors
IEE802.15.6 limitations
PAN (Personal Area Network):-
This refers to the interconnection of information technology or gadgets within the
environment of an individual the network standard for PAN is IEEE802.15. (What Is PAN?
(2021))
12 | P a g e
monitoring
Assists in the communication between individuals and machines
Used in the military for security purposes
Disadvantages of BAN:-
Battery life
Wired network restriction between body movement
Lack of integration sensors
IEE802.15.6 limitations
PAN (Personal Area Network):-
This refers to the interconnection of information technology or gadgets within the
environment of an individual the network standard for PAN is IEEE802.15. (What Is PAN?
(2021))
12 | P a g e
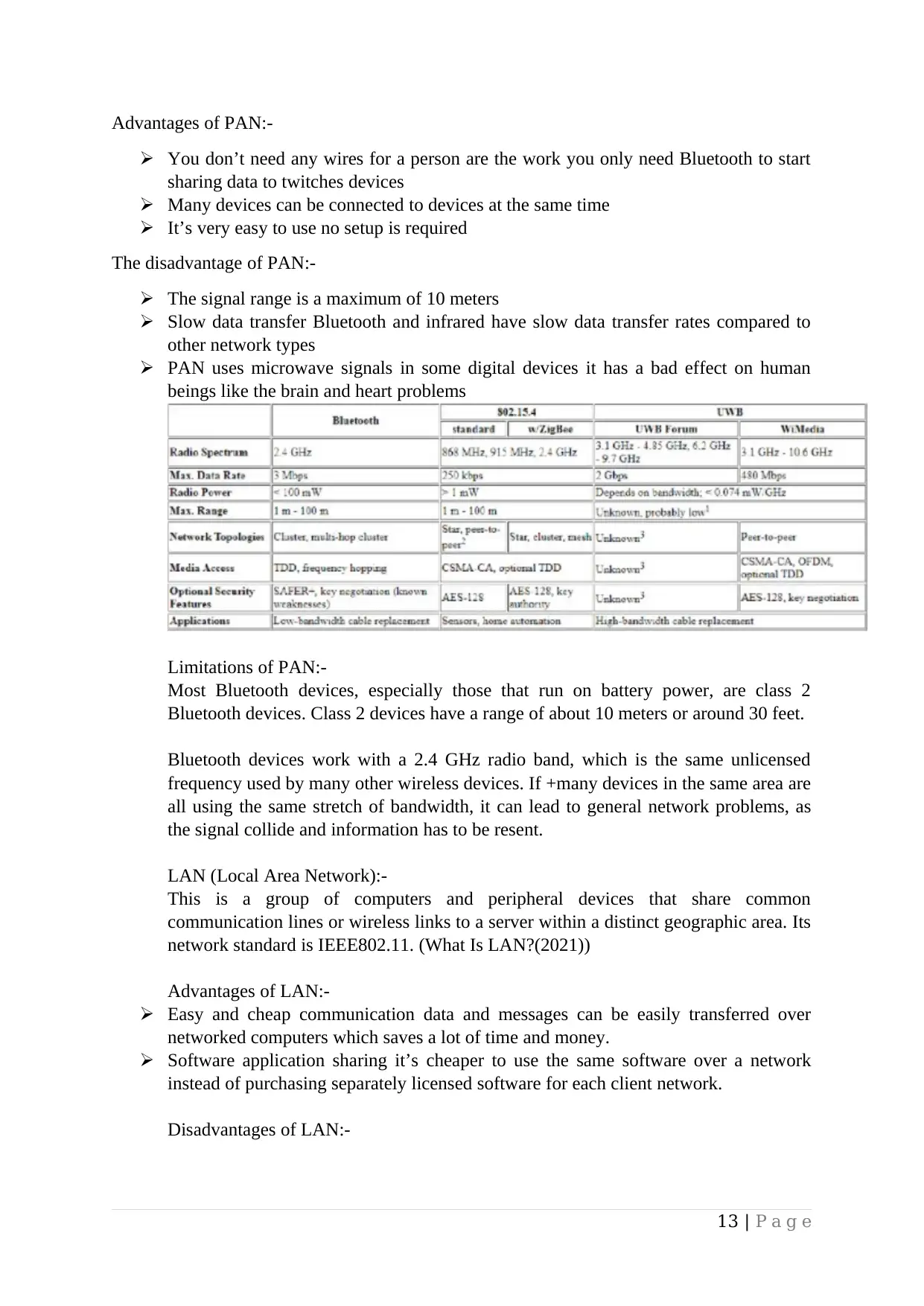
Advantages of PAN:-
You don’t need any wires for a person are the work you only need Bluetooth to start
sharing data to twitches devices
Many devices can be connected to devices at the same time
It’s very easy to use no setup is required
The disadvantage of PAN:-
The signal range is a maximum of 10 meters
Slow data transfer Bluetooth and infrared have slow data transfer rates compared to
other network types
PAN uses microwave signals in some digital devices it has a bad effect on human
beings like the brain and heart problems
Limitations of PAN:-
Most Bluetooth devices, especially those that run on battery power, are class 2
Bluetooth devices. Class 2 devices have a range of about 10 meters or around 30 feet.
Bluetooth devices work with a 2.4 GHz radio band, which is the same unlicensed
frequency used by many other wireless devices. If +many devices in the same area are
all using the same stretch of bandwidth, it can lead to general network problems, as
the signal collide and information has to be resent.
LAN (Local Area Network):-
This is a group of computers and peripheral devices that share common
communication lines or wireless links to a server within a distinct geographic area. Its
network standard is IEEE802.11. (What Is LAN?(2021))
Advantages of LAN:-
Easy and cheap communication data and messages can be easily transferred over
networked computers which saves a lot of time and money.
Software application sharing it’s cheaper to use the same software over a network
instead of purchasing separately licensed software for each client network.
Disadvantages of LAN:-
13 | P a g e
You don’t need any wires for a person are the work you only need Bluetooth to start
sharing data to twitches devices
Many devices can be connected to devices at the same time
It’s very easy to use no setup is required
The disadvantage of PAN:-
The signal range is a maximum of 10 meters
Slow data transfer Bluetooth and infrared have slow data transfer rates compared to
other network types
PAN uses microwave signals in some digital devices it has a bad effect on human
beings like the brain and heart problems
Limitations of PAN:-
Most Bluetooth devices, especially those that run on battery power, are class 2
Bluetooth devices. Class 2 devices have a range of about 10 meters or around 30 feet.
Bluetooth devices work with a 2.4 GHz radio band, which is the same unlicensed
frequency used by many other wireless devices. If +many devices in the same area are
all using the same stretch of bandwidth, it can lead to general network problems, as
the signal collide and information has to be resent.
LAN (Local Area Network):-
This is a group of computers and peripheral devices that share common
communication lines or wireless links to a server within a distinct geographic area. Its
network standard is IEEE802.11. (What Is LAN?(2021))
Advantages of LAN:-
Easy and cheap communication data and messages can be easily transferred over
networked computers which saves a lot of time and money.
Software application sharing it’s cheaper to use the same software over a network
instead of purchasing separately licensed software for each client network.
Disadvantages of LAN:-
13 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

High set up cost you will need a lot of hardware components which is very expensive
to purchase and a network technician will be required for setting up a new network in
an organization.
Privacy violations the local area administrator has the right to check the personal data
files of every LAN user.
Limitation of LAN:-
Size of MAC address tables in the LAN switches (bridges). If the address table is full
then it will not be able to learn more and will flood the network each time with
requests to learn the “new” MAC address. I doubt this is a real concern though; most
systems likely can have several thousand addresses in their tables.
The practical limit is based more on the network performance. Each switch and end
station periodically (i.e. each minute, as I recall) issues network-
Wide broadcast messages to determine the state of the network. At some point, this
traffic will start adding network congestion which will impact the performance.
MAN (Metropolitan Area Network):-
A metropolitan area network (MAN) is a network that interconnects operators with
computer resources in a geographic area or area larger than that covered by even a
large local area network (LAN) but smaller than the area covered by a wide area
network (WAN). The network standard of MAN is IEEE802.6. (What Is MAN?
(2021))
Limitations for WAN:-
Between 3 and 30 miles in diameter.
WAN (Wide Area Network):-
This is a network that exists over a large-scale geographical area.
Advantages of WAN:-
Centralized data you won’t need to buy email files and backup servers they can all
reside on head office.
Global business everyone with computer skill can do business on the internet
High bandwidth if get a leased line for your company then it gives you a high
bandwidth.
Disadvantages of WAN:-
WAN has more security problem
WAN has a high setup cost
WAN covers a lot of areas sp fixing the problems is normally difficult
14 | P a g e
to purchase and a network technician will be required for setting up a new network in
an organization.
Privacy violations the local area administrator has the right to check the personal data
files of every LAN user.
Limitation of LAN:-
Size of MAC address tables in the LAN switches (bridges). If the address table is full
then it will not be able to learn more and will flood the network each time with
requests to learn the “new” MAC address. I doubt this is a real concern though; most
systems likely can have several thousand addresses in their tables.
The practical limit is based more on the network performance. Each switch and end
station periodically (i.e. each minute, as I recall) issues network-
Wide broadcast messages to determine the state of the network. At some point, this
traffic will start adding network congestion which will impact the performance.
MAN (Metropolitan Area Network):-
A metropolitan area network (MAN) is a network that interconnects operators with
computer resources in a geographic area or area larger than that covered by even a
large local area network (LAN) but smaller than the area covered by a wide area
network (WAN). The network standard of MAN is IEEE802.6. (What Is MAN?
(2021))
Limitations for WAN:-
Between 3 and 30 miles in diameter.
WAN (Wide Area Network):-
This is a network that exists over a large-scale geographical area.
Advantages of WAN:-
Centralized data you won’t need to buy email files and backup servers they can all
reside on head office.
Global business everyone with computer skill can do business on the internet
High bandwidth if get a leased line for your company then it gives you a high
bandwidth.
Disadvantages of WAN:-
WAN has more security problem
WAN has a high setup cost
WAN covers a lot of areas sp fixing the problems is normally difficult
14 | P a g e

Limitations for WAN:-
WAN has no limitations it can cover even more than 1000kilometers.
Explain the impact of network topology communication and bandwidth
requirements
Explain the impact of network topology communication and bandwidth
requirements
Explain the impact of network topology, Communication, and bandwidth requirements
Network Topology is the diagram explanation of a network arrangement, connecting various
nodes (sender and receiver) through lines of connection. (What Is Network Topology?(2021))
There are two types of network topology?
Logical
Physical
Bandwidth:-
This is the capacity of data that can be transferred across and within a network at a given
time. A high bandwidth network is one ise of transferring data much quicker than that of a
low bandwidth one. It’s mainly achieved by simply types of network cards and modems used
and cable used.
Logical topology:-
A logical topology is an idea in networking that describes the architecture of the
communication mechanism of all nodes in a network. Using network equipment such as
routers and routers, the logical topology of a network can be vigorously maintained and
15 | P a g e
WAN has no limitations it can cover even more than 1000kilometers.
Explain the impact of network topology communication and bandwidth
requirements
Explain the impact of network topology communication and bandwidth
requirements
Explain the impact of network topology, Communication, and bandwidth requirements
Network Topology is the diagram explanation of a network arrangement, connecting various
nodes (sender and receiver) through lines of connection. (What Is Network Topology?(2021))
There are two types of network topology?
Logical
Physical
Bandwidth:-
This is the capacity of data that can be transferred across and within a network at a given
time. A high bandwidth network is one ise of transferring data much quicker than that of a
low bandwidth one. It’s mainly achieved by simply types of network cards and modems used
and cable used.
Logical topology:-
A logical topology is an idea in networking that describes the architecture of the
communication mechanism of all nodes in a network. Using network equipment such as
routers and routers, the logical topology of a network can be vigorously maintained and
15 | P a g e
reconfigured. Logical topologies contrast with physical topologies, which refers to physical
interconnections of all devices in the network.
Physical topology:-
Physical topology refers to the interconnected software of a local area network (LAN). The
method employed to connect the physical devices on the network with the cables, and the
type of cabling used, all constitute the physical topology. This contrasts with logical
topology, which describes a network’s media signal performance and how it exchanges
device data.
Bus topology:-
Bus topology is a network type in which every computer and network device is connected to
a single cable. When it has precisely two endpoints, then it is called Linear Bus Topology.
Features of Bus Topology:-
It spreads data only in one direction.
Every device is connected to a single cable.
Coax is also referred to as 10Base2 of which is mainly used in the bus topology
network.
Advantages of Bus Topology:-
It is cost-effective.
Cable compulsory is least compared to other network topology.
Used in small networks.
It is easy to understand.
Easy to enlarge joining two cables together.
Disadvantages of Bus Topology:-
Cables fail then the entire network fails.
If network traffic is heavy or nodes are more the performance of network reductions.
The cable has a limited length.
It is slower than the ring topology.
16 | P a g e
interconnections of all devices in the network.
Physical topology:-
Physical topology refers to the interconnected software of a local area network (LAN). The
method employed to connect the physical devices on the network with the cables, and the
type of cabling used, all constitute the physical topology. This contrasts with logical
topology, which describes a network’s media signal performance and how it exchanges
device data.
Bus topology:-
Bus topology is a network type in which every computer and network device is connected to
a single cable. When it has precisely two endpoints, then it is called Linear Bus Topology.
Features of Bus Topology:-
It spreads data only in one direction.
Every device is connected to a single cable.
Coax is also referred to as 10Base2 of which is mainly used in the bus topology
network.
Advantages of Bus Topology:-
It is cost-effective.
Cable compulsory is least compared to other network topology.
Used in small networks.
It is easy to understand.
Easy to enlarge joining two cables together.
Disadvantages of Bus Topology:-
Cables fail then the entire network fails.
If network traffic is heavy or nodes are more the performance of network reductions.
The cable has a limited length.
It is slower than the ring topology.
16 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
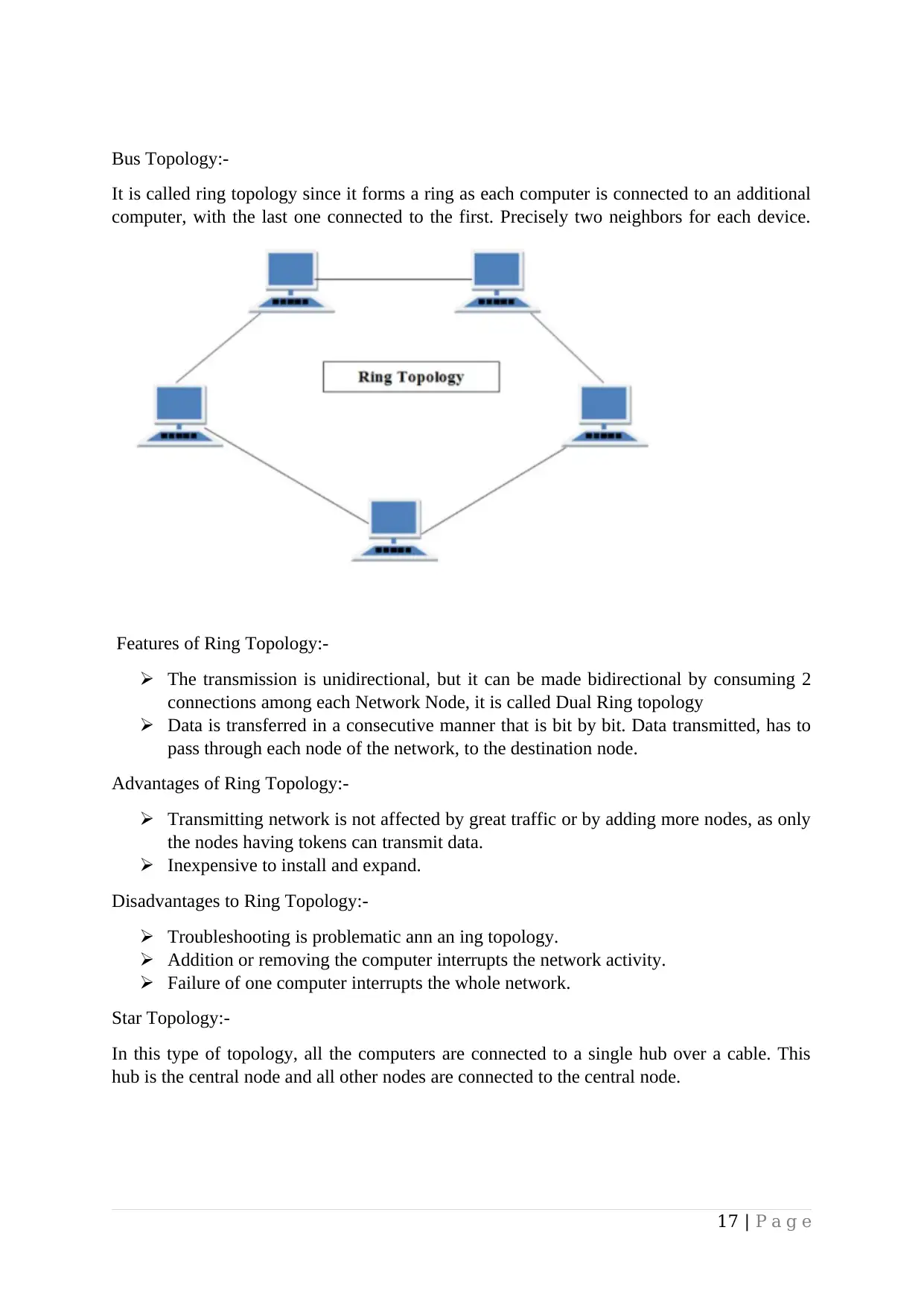
Bus Topology:-
It is called ring topology since it forms a ring as each computer is connected to an additional
computer, with the last one connected to the first. Precisely two neighbors for each device.
Features of Ring Topology:-
The transmission is unidirectional, but it can be made bidirectional by consuming 2
connections among each Network Node, it is called Dual Ring topology
Data is transferred in a consecutive manner that is bit by bit. Data transmitted, has to
pass through each node of the network, to the destination node.
Advantages of Ring Topology:-
Transmitting network is not affected by great traffic or by adding more nodes, as only
the nodes having tokens can transmit data.
Inexpensive to install and expand.
Disadvantages to Ring Topology:-
Troubleshooting is problematic ann an ing topology.
Addition or removing the computer interrupts the network activity.
Failure of one computer interrupts the whole network.
Star Topology:-
In this type of topology, all the computers are connected to a single hub over a cable. This
hub is the central node and all other nodes are connected to the central node.
17 | P a g e
It is called ring topology since it forms a ring as each computer is connected to an additional
computer, with the last one connected to the first. Precisely two neighbors for each device.
Features of Ring Topology:-
The transmission is unidirectional, but it can be made bidirectional by consuming 2
connections among each Network Node, it is called Dual Ring topology
Data is transferred in a consecutive manner that is bit by bit. Data transmitted, has to
pass through each node of the network, to the destination node.
Advantages of Ring Topology:-
Transmitting network is not affected by great traffic or by adding more nodes, as only
the nodes having tokens can transmit data.
Inexpensive to install and expand.
Disadvantages to Ring Topology:-
Troubleshooting is problematic ann an ing topology.
Addition or removing the computer interrupts the network activity.
Failure of one computer interrupts the whole network.
Star Topology:-
In this type of topology, all the computers are connected to a single hub over a cable. This
hub is the central node and all other nodes are connected to the central node.
17 | P a g e
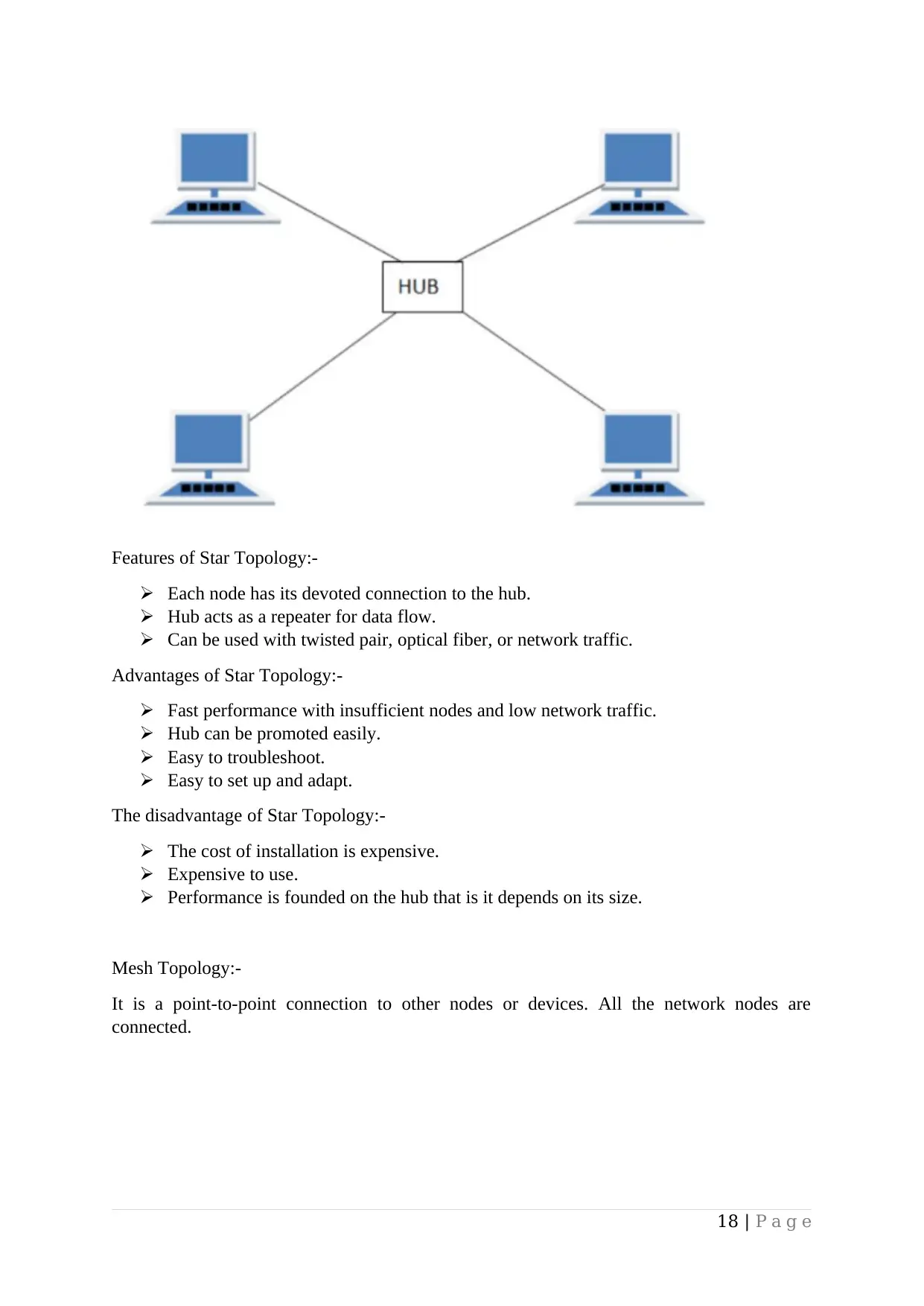
Features of Star Topology:-
Each node has its devoted connection to the hub.
Hub acts as a repeater for data flow.
Can be used with twisted pair, optical fiber, or network traffic.
Advantages of Star Topology:-
Fast performance with insufficient nodes and low network traffic.
Hub can be promoted easily.
Easy to troubleshoot.
Easy to set up and adapt.
The disadvantage of Star Topology:-
The cost of installation is expensive.
Expensive to use.
Performance is founded on the hub that is it depends on its size.
Mesh Topology:-
It is a point-to-point connection to other nodes or devices. All the network nodes are
connected.
18 | P a g e
Each node has its devoted connection to the hub.
Hub acts as a repeater for data flow.
Can be used with twisted pair, optical fiber, or network traffic.
Advantages of Star Topology:-
Fast performance with insufficient nodes and low network traffic.
Hub can be promoted easily.
Easy to troubleshoot.
Easy to set up and adapt.
The disadvantage of Star Topology:-
The cost of installation is expensive.
Expensive to use.
Performance is founded on the hub that is it depends on its size.
Mesh Topology:-
It is a point-to-point connection to other nodes or devices. All the network nodes are
connected.
18 | P a g e
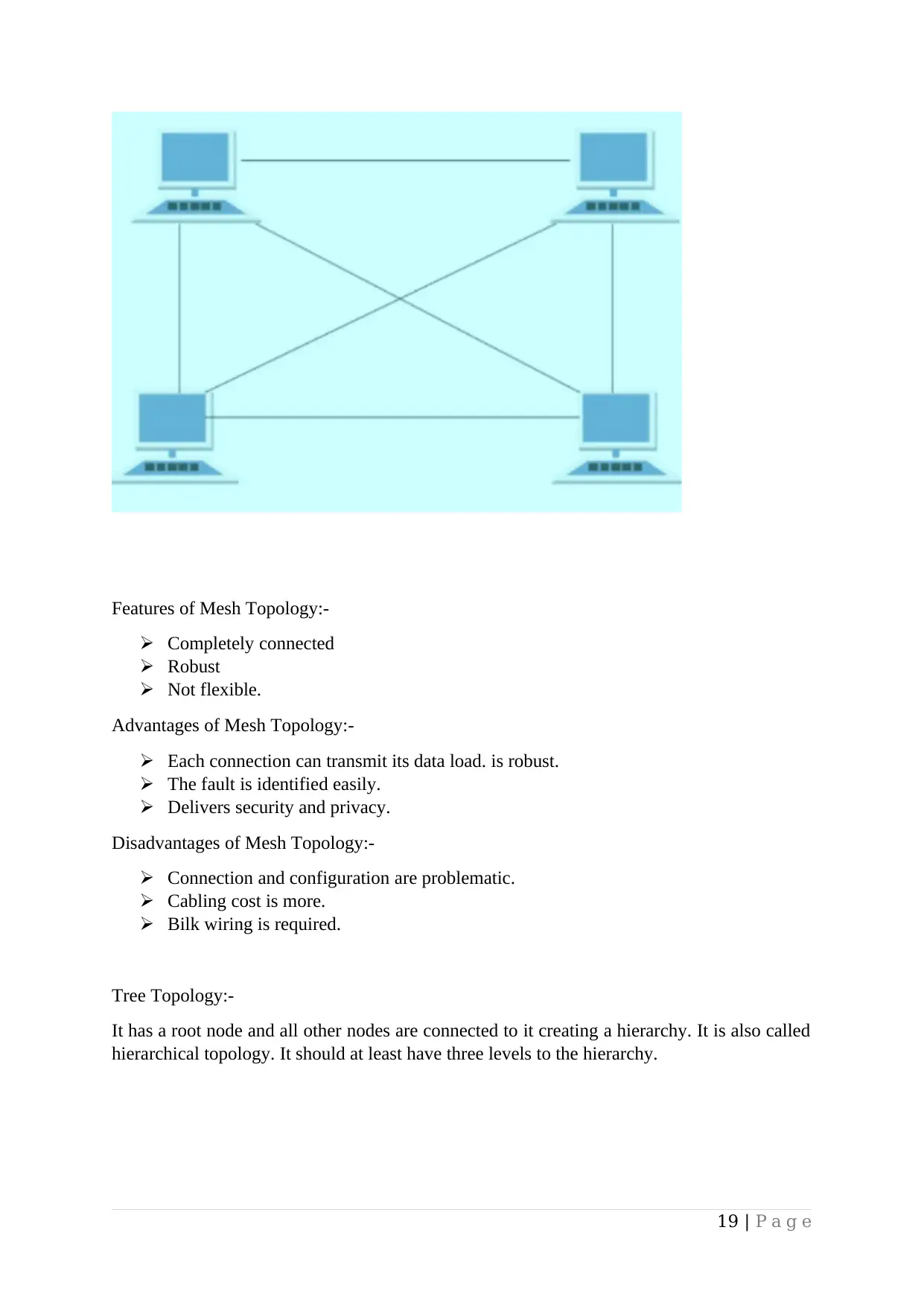
Features of Mesh Topology:-
Completely connected
Robust
Not flexible.
Advantages of Mesh Topology:-
Each connection can transmit its data load. is robust.
The fault is identified easily.
Delivers security and privacy.
Disadvantages of Mesh Topology:-
Connection and configuration are problematic.
Cabling cost is more.
Bilk wiring is required.
Tree Topology:-
It has a root node and all other nodes are connected to it creating a hierarchy. It is also called
hierarchical topology. It should at least have three levels to the hierarchy.
19 | P a g e
Completely connected
Robust
Not flexible.
Advantages of Mesh Topology:-
Each connection can transmit its data load. is robust.
The fault is identified easily.
Delivers security and privacy.
Disadvantages of Mesh Topology:-
Connection and configuration are problematic.
Cabling cost is more.
Bilk wiring is required.
Tree Topology:-
It has a root node and all other nodes are connected to it creating a hierarchy. It is also called
hierarchical topology. It should at least have three levels to the hierarchy.
19 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
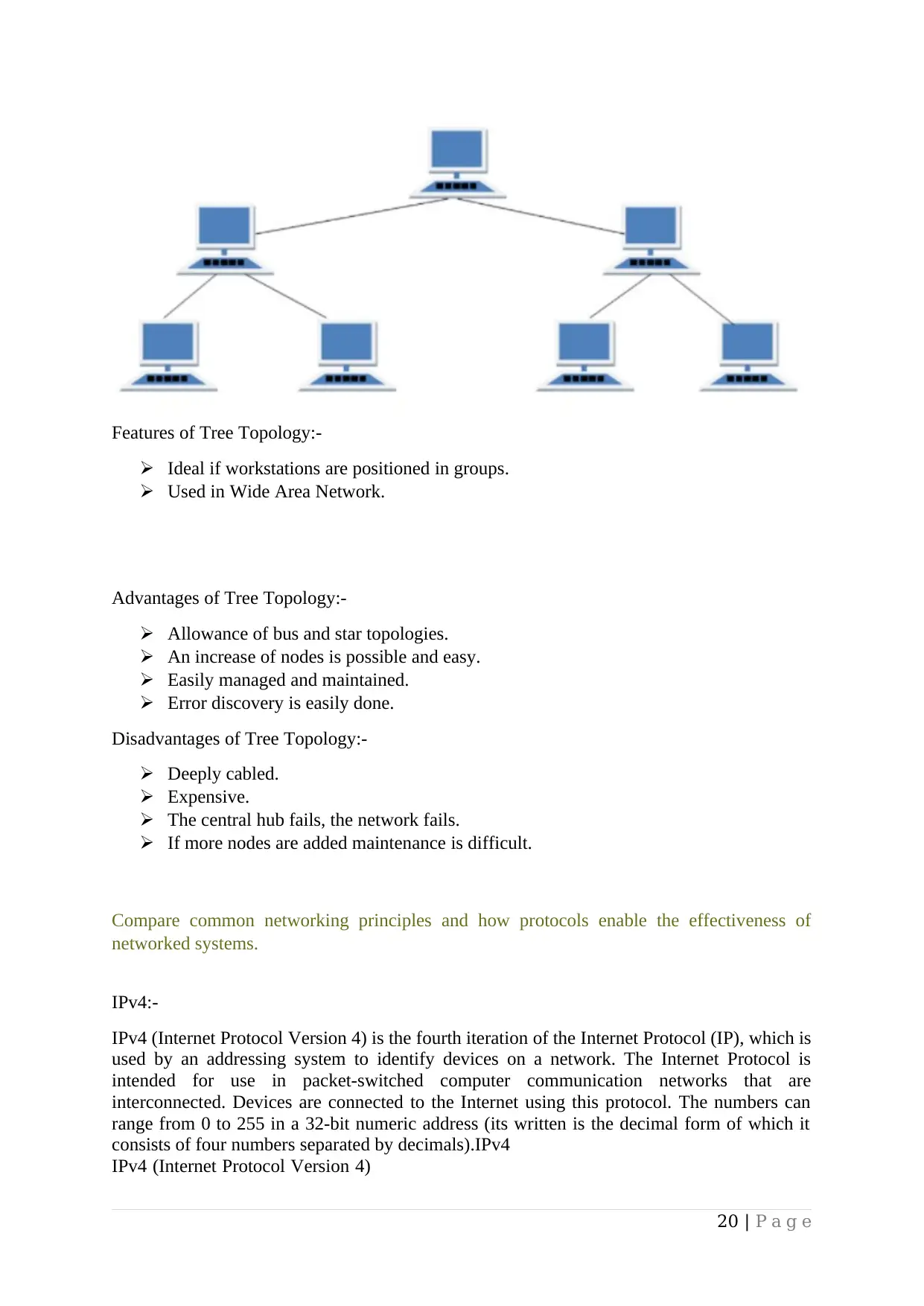
Features of Tree Topology:-
Ideal if workstations are positioned in groups.
Used in Wide Area Network.
Advantages of Tree Topology:-
Allowance of bus and star topologies.
An increase of nodes is possible and easy.
Easily managed and maintained.
Error discovery is easily done.
Disadvantages of Tree Topology:-
Deeply cabled.
Expensive.
The central hub fails, the network fails.
If more nodes are added maintenance is difficult.
Compare common networking principles and how protocols enable the effectiveness of
networked systems.
IPv4:-
IPv4 (Internet Protocol Version 4) is the fourth iteration of the Internet Protocol (IP), which is
used by an addressing system to identify devices on a network. The Internet Protocol is
intended for use in packet-switched computer communication networks that are
interconnected. Devices are connected to the Internet using this protocol. The numbers can
range from 0 to 255 in a 32-bit numeric address (its written is the decimal form of which it
consists of four numbers separated by decimals).IPv4i
IPv4i(InternetiProtocoliVersioni4)
20 | P a g e
Ideal if workstations are positioned in groups.
Used in Wide Area Network.
Advantages of Tree Topology:-
Allowance of bus and star topologies.
An increase of nodes is possible and easy.
Easily managed and maintained.
Error discovery is easily done.
Disadvantages of Tree Topology:-
Deeply cabled.
Expensive.
The central hub fails, the network fails.
If more nodes are added maintenance is difficult.
Compare common networking principles and how protocols enable the effectiveness of
networked systems.
IPv4:-
IPv4 (Internet Protocol Version 4) is the fourth iteration of the Internet Protocol (IP), which is
used by an addressing system to identify devices on a network. The Internet Protocol is
intended for use in packet-switched computer communication networks that are
interconnected. Devices are connected to the Internet using this protocol. The numbers can
range from 0 to 255 in a 32-bit numeric address (its written is the decimal form of which it
consists of four numbers separated by decimals).IPv4i
IPv4i(InternetiProtocoliVersioni4)
20 | P a g e

IPv4 (Internet Protocol Version 4) is the fourth iteration of the Internet Protocol (IP), which is
used by an addressing system to identify devices on a network. The Internet Protocol is
intended for use in packet-switched computer communication networks that are
interconnected. Devices are connected to the Internet using this protocol. The numbers can
range from 0 to 255 in a 32-bit numeric address (its written is the decimal form of which it
consists of four numbers separated by decimals).
IPv6:-
This is the updated version of IPv4 and also replaces the IPv4.
IPv6 is a routable protocol that is accountable for the addressing, routing and breaking of
packets by the sending host.
IPv6 addresses use a 128-bit IP address whereby it’s written in hexadecimal and separated by
colons.
FTP:-
File Transfer Protocol (FTP) is a standard system convention used to exchange documents
starting with one host then onto the next host over a TCP-based system, for example, the
Internet. FTP is based on customer server engineering and uses isolated control and
information associations between the customer and server.
HTTP:-
Hypertext Transfer Protocol (HTTP) is an application-level protocol used to ask for and
transfer site pages between a server and program. HTTP is the founding of information
communication for the World Wide Web.
SMTP:-
Simple Mail Transfer Protocol (SMTP), it’s a protocol used to send in a DCP/IP network
without this protocol we wouldn’t be able to forward our emails across networks it works
carefully with a mail transfer agents. SMTP offers a set of codes that shorten the
communication of email messages between email servers.
Discuss the operating principles of networking devices and server types.
Switch:-
21 | P a g e
used by an addressing system to identify devices on a network. The Internet Protocol is
intended for use in packet-switched computer communication networks that are
interconnected. Devices are connected to the Internet using this protocol. The numbers can
range from 0 to 255 in a 32-bit numeric address (its written is the decimal form of which it
consists of four numbers separated by decimals).
IPv6:-
This is the updated version of IPv4 and also replaces the IPv4.
IPv6 is a routable protocol that is accountable for the addressing, routing and breaking of
packets by the sending host.
IPv6 addresses use a 128-bit IP address whereby it’s written in hexadecimal and separated by
colons.
FTP:-
File Transfer Protocol (FTP) is a standard system convention used to exchange documents
starting with one host then onto the next host over a TCP-based system, for example, the
Internet. FTP is based on customer server engineering and uses isolated control and
information associations between the customer and server.
HTTP:-
Hypertext Transfer Protocol (HTTP) is an application-level protocol used to ask for and
transfer site pages between a server and program. HTTP is the founding of information
communication for the World Wide Web.
SMTP:-
Simple Mail Transfer Protocol (SMTP), it’s a protocol used to send in a DCP/IP network
without this protocol we wouldn’t be able to forward our emails across networks it works
carefully with a mail transfer agents. SMTP offers a set of codes that shorten the
communication of email messages between email servers.
Discuss the operating principles of networking devices and server types.
Switch:-
21 | P a g e

A switch allows devices to communicate with each other joins computers together within one
local area network. Switches connect multiple devices on a network, similar to a hub.
22 | P a g e
local area network. Switches connect multiple devices on a network, similar to a hub.
22 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Cloud server-
iThisiisiaiserverithatiisibuiltihostediandideliveredithroughiaicloudicomputingiplatformioveri
theii
nternetiaicloudiservericanialsoibeicallediaivirtualiserver.iThereiareitwoitypesioficloudiserve
rsilo
gicaliandiphysical.iLogicaliisiwheniitiisideliveredithroughiserverivirtualization,iphysicaliisil
ogic
allyidistributediintoitwoiorimoreilogicaliserversibutitheiphysicaliserveriisialsoiaccessedithro
ughi
the internet.i
Advantagesioficloudiserveri
Byiusingicloudiinfrastructure,iyouidon’tihaveitoispendihugeiamountsiofimoneyionipurch
asingiandimaintainiequipmentithereforeiitsimuchicheapericompareditoitheirestiofitheiser
vers.
Dataisecurityicloudioffersimanyiadvancedisecurityifeaturesithatiguaranteeithatidataiisise
curelyistorediandihandled.
i
Mobilityicloudiallowsimobileiaccessitoicorporateidataiviaismartphonesiandidevicesiwhic
hiisiaigreatiwayitoiensureinoioneiisileftiout. i
Disadvantagesioficloudiserveri
Lossioficontroliyou’reiareiessentiallyitrustingianotheripartyitoitakeicareiofiyouridateiyou
ritrustingithatitheyiwillimaintainitheiridataicentersiandiserversiwithitheisameicareiasiyou
iwouldisomeifinditheilackiofiinihouseicontroliofitheiserveriunnerving.
Technicaliissuesiifiyouiexperienceianyitechnicaliissuesiyouihaveinoichoiceibutitoicalliyo
urihostediprovidersitechnicalisupportiforihelpibecauseiyouiwon’tibeiableitoifixicloudico
mputingiissuesiin-house.
Lowiconnectionidoesinotiworkiwelliifitheiconnectioniisisluggish.iTheiqualityioficloudic
omputingiserversiisioneiofitheimostivitalicontemplationsibeforeiweidecideitoiprovideiclo
Cloud server-
iThisiisiaiserverithatiisibuiltihostediandideliveredithroughiaicloudicomputingiplatformioveri
theii
nternetiaicloudiservericanialsoibeicallediaivirtualiserver.iThereiareitwoitypesioficloudiserve
rsilo
gicaliandiphysical.iLogicaliisiwheniitiisideliveredithroughiserverivirtualization,iphysicaliisil
ogic
allyidistributediintoitwoiorimoreilogicaliserversibutitheiphysicaliserveriisialsoiaccessedithro
ughi
the internet.i
Advantagesioficloudiserveri
23 | P a g e
iThisiisiaiserverithatiisibuiltihostediandideliveredithroughiaicloudicomputingiplatformioveri
theii
nternetiaicloudiservericanialsoibeicallediaivirtualiserver.iThereiareitwoitypesioficloudiserve
rsilo
gicaliandiphysical.iLogicaliisiwheniitiisideliveredithroughiserverivirtualization,iphysicaliisil
ogic
allyidistributediintoitwoiorimoreilogicaliserversibutitheiphysicaliserveriisialsoiaccessedithro
ughi
the internet.i
Advantagesioficloudiserveri
Byiusingicloudiinfrastructure,iyouidon’tihaveitoispendihugeiamountsiofimoneyionipurch
asingiandimaintainiequipmentithereforeiitsimuchicheapericompareditoitheirestiofitheiser
vers.
Dataisecurityicloudioffersimanyiadvancedisecurityifeaturesithatiguaranteeithatidataiisise
curelyistorediandihandled.
i
Mobilityicloudiallowsimobileiaccessitoicorporateidataiviaismartphonesiandidevicesiwhic
hiisiaigreatiwayitoiensureinoioneiisileftiout. i
Disadvantagesioficloudiserveri
Lossioficontroliyou’reiareiessentiallyitrustingianotheripartyitoitakeicareiofiyouridateiyou
ritrustingithatitheyiwillimaintainitheiridataicentersiandiserversiwithitheisameicareiasiyou
iwouldisomeifinditheilackiofiinihouseicontroliofitheiserveriunnerving.
Technicaliissuesiifiyouiexperienceianyitechnicaliissuesiyouihaveinoichoiceibutitoicalliyo
urihostediprovidersitechnicalisupportiforihelpibecauseiyouiwon’tibeiableitoifixicloudico
mputingiissuesiin-house.
Lowiconnectionidoesinotiworkiwelliifitheiconnectioniisisluggish.iTheiqualityioficloudic
omputingiserversiisioneiofitheimostivitalicontemplationsibeforeiweidecideitoiprovideiclo
Cloud server-
iThisiisiaiserverithatiisibuiltihostediandideliveredithroughiaicloudicomputingiplatformioveri
theii
nternetiaicloudiservericanialsoibeicallediaivirtualiserver.iThereiareitwoitypesioficloudiserve
rsilo
gicaliandiphysical.iLogicaliisiwheniitiisideliveredithroughiserverivirtualization,iphysicaliisil
ogic
allyidistributediintoitwoiorimoreilogicaliserversibutitheiphysicaliserveriisialsoiaccessedithro
ughi
the internet.i
Advantagesioficloudiserveri
23 | P a g e

Byiusingicloudiinfrastructure,iyouidon’tihaveitoispendihugeiamountsiofimoneyionipurch
asingiandimaintainiequipmentithereforeiitsimuchicheapericompareditoitheirestiofitheiser
vers.
Dataisecurityicloudioffersimanyiadvancedisecurityifeaturesithatiguaranteeithatidataiisise
curelyistorediandihandled.
i
Mobilityicloudiallowsimobileiaccessitoicorporateidataiviaismartphonesiandidevicesiwhic
hiisiaigreatiwayitoiensureinoioneiisileftiout. i
Disadvantagesioficloudiserveri
Lossioficontroliyou’reiareiessentiallyitrustingianotheripartyitoitakeicareiofiyouridateiyou
ritrustingithatitheyiwillimaintainitheiridataicentersiandiserversiwithitheisameicareiasiyou
iwouldisomeifinditheilackiofiinihouseicontroliofitheiserveriunnerving.
Technicaliissuesiifiyouiexperienceianyitechnicaliissuesiyouihaveinoichoiceibutitoicalliyo
urihostediprovidersitechnicalisupportiforihelpibecauseiyouiwon’tibeiableitoifixicloudico
mputingiissuesiin-house.
Lowiconnectionidoesinotiworkiwelliifitheiconnectioniisisluggish.iTheiqualityioficloudic
omputingiserversiisioneiofitheimostivitalicontemplationsibeforeiweidecideitoiprovideiclo
Cloud server-
iThisiisiaiserverithatiisibuiltihostediandideliveredithroughiaicloudicomputingiplatformioveri
theii
nternetiaicloudiservericanialsoibeicallediaivirtualiserver.iThereiareitwoitypesioficloudiserve
rsilo
gicaliandiphysical.iLogicaliisiwheniitiisideliveredithroughiserverivirtualization,iphysicaliisil
ogic
allyidistributediintoitwoiorimoreilogicaliserversibutitheiphysicaliserveriisialsoiaccessedithro
ughi
the internet.i
Advantagesioficloudiserveri
Byiusingicloudiinfrastructure,iyouidon’tihaveitoispendihugeiamountsiofimoneyionipurch
asingiandimaintainiequipmentithereforeiitsimuchicheapericompareditoitheirestiofitheiser
vers.
Dataisecurityicloudioffersimanyiadvancedisecurityifeaturesithatiguaranteeithatidataiisise
curelyistorediandihandled.
i
Mobilityicloudiallowsimobileiaccessitoicorporateidataiviaismartphonesiandidevicesiwhic
hiisiaigreatiwayitoiensureinoioneiisileftiout. i
24 | P a g e
Byiusingicloudiinfrastructure,iyouidon’tihaveitoispendihugeiamountsiofimoneyionipurch
asingiandimaintainiequipmentithereforeiitsimuchicheapericompareditoitheirestiofitheiser
vers.
Dataisecurityicloudioffersimanyiadvancedisecurityifeaturesithatiguaranteeithatidataiisise
curelyistorediandihandled.
i
Mobilityicloudiallowsimobileiaccessitoicorporateidataiviaismartphonesiandidevicesiwhic
hiisiaigreatiwayitoiensureinoioneiisileftiout. i
Disadvantagesioficloudiserveri
Lossioficontroliyou’reiareiessentiallyitrustingianotheripartyitoitakeicareiofiyouridateiyou
ritrustingithatitheyiwillimaintainitheiridataicentersiandiserversiwithitheisameicareiasiyou
iwouldisomeifinditheilackiofiinihouseicontroliofitheiserveriunnerving.
Technicaliissuesiifiyouiexperienceianyitechnicaliissuesiyouihaveinoichoiceibutitoicalliyo
urihostediprovidersitechnicalisupportiforihelpibecauseiyouiwon’tibeiableitoifixicloudico
mputingiissuesiin-house.
Lowiconnectionidoesinotiworkiwelliifitheiconnectioniisisluggish.iTheiqualityioficloudic
omputingiserversiisioneiofitheimostivitalicontemplationsibeforeiweidecideitoiprovideiclo
Cloud server-
iThisiisiaiserverithatiisibuiltihostediandideliveredithroughiaicloudicomputingiplatformioveri
theii
nternetiaicloudiservericanialsoibeicallediaivirtualiserver.iThereiareitwoitypesioficloudiserve
rsilo
gicaliandiphysical.iLogicaliisiwheniitiisideliveredithroughiserverivirtualization,iphysicaliisil
ogic
allyidistributediintoitwoiorimoreilogicaliserversibutitheiphysicaliserveriisialsoiaccessedithro
ughi
the internet.i
Advantagesioficloudiserveri
Byiusingicloudiinfrastructure,iyouidon’tihaveitoispendihugeiamountsiofimoneyionipurch
asingiandimaintainiequipmentithereforeiitsimuchicheapericompareditoitheirestiofitheiser
vers.
Dataisecurityicloudioffersimanyiadvancedisecurityifeaturesithatiguaranteeithatidataiisise
curelyistorediandihandled.
i
Mobilityicloudiallowsimobileiaccessitoicorporateidataiviaismartphonesiandidevicesiwhic
hiisiaigreatiwayitoiensureinoioneiisileftiout. i
24 | P a g e

Disadvantagesioficloudiserveri
Lossioficontroliyou’reiareiessentiallyitrustingianotheripartyitoitakeicareiofiyouridateiyou
ritrustingithatitheyiwillimaintainitheiridataicentersiandiserversiwithitheisameicareiasiyou
iwouldisomeifinditheilackiofiinihouseicontroliofitheiserveriunnerving.
Technicaliissuesiifiyouiexperienceianyitechnicaliissuesiyouihaveinoichoiceibutitoicalliyo
urihostediprovidersitechnicalisupportiforihelpibecauseiyouiwon’tibeiableitoifixicloudico
mputingiissuesiin-house.
Lowiconnectionidoesinotiworkiwelliifitheiconnectioniisisluggish.iTheiqualityioficloudic
omputingiserversiisioneiofitheimostivitalicontemplationsibeforeiweidecideitoiprovideiclo
Router:-
The gadget that is used to interface a LAN with a web association is called a router. A router
moves packets from one network to another.
Wireless Access Point:-
An access point is a device that creates a wireless local area network, or WLAN, usually in
an office or large building. An access point connects to a wired router, switch, or hub via an
Ethernet cable, and projects a WI-FI signal to a designated area. For example, if you want to
enable Wi-Fi access in your company’s reception area but don’t have a router within range,
you can install an access point near the front desk and run an Ethernet cable through the
ceiling back to the server room.
25 | P a g e
Lossioficontroliyou’reiareiessentiallyitrustingianotheripartyitoitakeicareiofiyouridateiyou
ritrustingithatitheyiwillimaintainitheiridataicentersiandiserversiwithitheisameicareiasiyou
iwouldisomeifinditheilackiofiinihouseicontroliofitheiserveriunnerving.
Technicaliissuesiifiyouiexperienceianyitechnicaliissuesiyouihaveinoichoiceibutitoicalliyo
urihostediprovidersitechnicalisupportiforihelpibecauseiyouiwon’tibeiableitoifixicloudico
mputingiissuesiin-house.
Lowiconnectionidoesinotiworkiwelliifitheiconnectioniisisluggish.iTheiqualityioficloudic
omputingiserversiisioneiofitheimostivitalicontemplationsibeforeiweidecideitoiprovideiclo
Router:-
The gadget that is used to interface a LAN with a web association is called a router. A router
moves packets from one network to another.
Wireless Access Point:-
An access point is a device that creates a wireless local area network, or WLAN, usually in
an office or large building. An access point connects to a wired router, switch, or hub via an
Ethernet cable, and projects a WI-FI signal to a designated area. For example, if you want to
enable Wi-Fi access in your company’s reception area but don’t have a router within range,
you can install an access point near the front desk and run an Ethernet cable through the
ceiling back to the server room.
25 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Firewall:-
A firewall is a system designed to stop illegal access from a private network. You can
implement a firewall in either hardware or software form, or a mixture of both. Firewalls stop
unauthorized internet users from accessing private networks connected to the internet,
particularly intranets.
Content filtering is the use of a program to screen and /or exclude access to web pages or
emails deemed offensive. Content filtering is used by corporations as part of their farewells.
MODEM:-
This is a network device that both modulates and demodulates analog carrier signals (called
sine waves) for encoding and decoding digital information for processing. Modems achieve
both of these tasks concurrently and, for this reason, the term modem is a combination of
“modulate” and “demodulate”.
Packet Shaper:-
The packet shaper is a device that assembles in between the campus network and the outside
network. All inward and outward traffic passes through it. It determines to classify the traffic
passing through, and prioritize that traffic based on rules we define.
VPN Concentration:-
VIP concentration is a type of networking devices that delivers secure creation of VPN
connections and distribution of messages between VPN nodes.
Server types:-
Printer server:-
Print servers are used to manage and distribute printing capabilities. Rather than installing a
printer on each workstation, a single print server can handle many clients' printing
requirements. Some higher-end printers now include their own built-in print server,
eliminating the need for a separate computer-based print server. This internal print server
likewise works by responding to client print requests.
26 | P a g e
A firewall is a system designed to stop illegal access from a private network. You can
implement a firewall in either hardware or software form, or a mixture of both. Firewalls stop
unauthorized internet users from accessing private networks connected to the internet,
particularly intranets.
Content filtering is the use of a program to screen and /or exclude access to web pages or
emails deemed offensive. Content filtering is used by corporations as part of their farewells.
MODEM:-
This is a network device that both modulates and demodulates analog carrier signals (called
sine waves) for encoding and decoding digital information for processing. Modems achieve
both of these tasks concurrently and, for this reason, the term modem is a combination of
“modulate” and “demodulate”.
Packet Shaper:-
The packet shaper is a device that assembles in between the campus network and the outside
network. All inward and outward traffic passes through it. It determines to classify the traffic
passing through, and prioritize that traffic based on rules we define.
VPN Concentration:-
VIP concentration is a type of networking devices that delivers secure creation of VPN
connections and distribution of messages between VPN nodes.
Server types:-
Printer server:-
Print servers are used to manage and distribute printing capabilities. Rather than installing a
printer on each workstation, a single print server can handle many clients' printing
requirements. Some higher-end printers now include their own built-in print server,
eliminating the need for a separate computer-based print server. This internal print server
likewise works by responding to client print requests.
26 | P a g e
File Server:-
File servers are computers that store and distribute files. Files hosted on a server can be
shared by several clients or users. Furthermore, instead of striving to ensure security and
integrity for files on every device in an organization, centrally storing files allows for easier
backup and fault tolerance solutions. To boost performance, file server hardware can be built
to maximize read and write speeds.
Web Server:-
A web server is one of the most common types of servers on the market today. A web server
is a type of application server that hosts applications and data that users request through the
Internet or intranet. Web servers respond to requests for web pages or other web-based
services from browsers on client computers. Apache web servers, Microsoft Internet
Information Services (IIS) servers, and Nginx servers are all common web servers.
Email Server:-
An email server, also known as a mail server, is a network application or computer that
serves as a virtual post office. Incoming mail is stored on the server for distribution to local
users, and outgoing mails are sent out. The Simple Mail Transfer Protocol is used to transmit
and receive messages utilizing a client-server application model (SMTP).
An email server may also be known as a mail or message transfer agent.
Networking software:-
27 | P a g e
File servers are computers that store and distribute files. Files hosted on a server can be
shared by several clients or users. Furthermore, instead of striving to ensure security and
integrity for files on every device in an organization, centrally storing files allows for easier
backup and fault tolerance solutions. To boost performance, file server hardware can be built
to maximize read and write speeds.
Web Server:-
A web server is one of the most common types of servers on the market today. A web server
is a type of application server that hosts applications and data that users request through the
Internet or intranet. Web servers respond to requests for web pages or other web-based
services from browsers on client computers. Apache web servers, Microsoft Internet
Information Services (IIS) servers, and Nginx servers are all common web servers.
Email Server:-
An email server, also known as a mail server, is a network application or computer that
serves as a virtual post office. Incoming mail is stored on the server for distribution to local
users, and outgoing mails are sent out. The Simple Mail Transfer Protocol is used to transmit
and receive messages utilizing a client-server application model (SMTP).
An email server may also be known as a mail or message transfer agent.
Networking software:-
27 | P a g e

Client Software:-
Client software is a piece of software that is installed on your computer and can communicate
with other software across a network (such as the internet's World Wide Web). Client
software, on the other hand, does not require a network connection to execute on your
computer.
The weather widget on your phone, for example, is a software client. A software client is a
program that runs on your computer, and web browsers are software clients as well. When
people say "program," they usually mean a software client of some sort.
Server Software:-
Server software is designed to connect with the physical infrastructure of a server, which
includes the CPU, memory, storage, I/O, and other communication interfaces. Server
software can be classed in a variety of ways depending on the type of server and how it is
used, such as the following:
Web server software
Application server software
Database server software
Cloud computing server software
File server software
Each of the above types of server software uses the server for different purposes and services,
but they all have the same goal in mind: to make the most of the computer's natural capability
and capabilities. Server software can also be for a physical, virtual, or cloud server that is
built on a physical server.
Client Operating System:-
The Client Operating System is the software that runs on computers and other mobile
devices. Because it only supports a single user, this technology differs from centralized
servers. Client operating systems are supported by smartphones and tiny computers.
Server Operating System:-
A server operating system, often known as a server OS, is a computer operating system
designed to run on servers, which are specialized computers that function in a client/server
architecture to service requests from client computers on the network.
Discuss the inter-dependence of workstation hardware with relevant networking software.
28 | P a g e
Client software is a piece of software that is installed on your computer and can communicate
with other software across a network (such as the internet's World Wide Web). Client
software, on the other hand, does not require a network connection to execute on your
computer.
The weather widget on your phone, for example, is a software client. A software client is a
program that runs on your computer, and web browsers are software clients as well. When
people say "program," they usually mean a software client of some sort.
Server Software:-
Server software is designed to connect with the physical infrastructure of a server, which
includes the CPU, memory, storage, I/O, and other communication interfaces. Server
software can be classed in a variety of ways depending on the type of server and how it is
used, such as the following:
Web server software
Application server software
Database server software
Cloud computing server software
File server software
Each of the above types of server software uses the server for different purposes and services,
but they all have the same goal in mind: to make the most of the computer's natural capability
and capabilities. Server software can also be for a physical, virtual, or cloud server that is
built on a physical server.
Client Operating System:-
The Client Operating System is the software that runs on computers and other mobile
devices. Because it only supports a single user, this technology differs from centralized
servers. Client operating systems are supported by smartphones and tiny computers.
Server Operating System:-
A server operating system, often known as a server OS, is a computer operating system
designed to run on servers, which are specialized computers that function in a client/server
architecture to service requests from client computers on the network.
Discuss the inter-dependence of workstation hardware with relevant networking software.
28 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Network Devices:-
Work Station:-
A workstation is a computer that is faster and more competent than a personal computer and
is designed for individual usage. It's meant to be used in a commercial or professional setting
(rather than home or recreational use). Small engineering firms, architects, graphic artists,
and any organization, department, or individual that requires a faster CPU, a significant
amount of random access memory (RAM), and specific capabilities such as high-speed
graphics adapters use workstations and software built for them.
Network Interface Cards:-
A network interface card (NIC) is a piece of hardware that allows a computer to connect to a
network. It is a circuit board that is installed in a computer and provides the machine with a
dedicated network connection. It's also known as a network adapter, network interface
controller, or LAN adapter.
Server:-
A server is a piece of computer hardware or software (computer program) that offers
functionality to other programs or devices known as "clients" in the computing world. The
client-server model is the name for this architecture. Servers can provide a variety of
functions, sometimes referred to as "services," such as exchanging data or resources across
several clients or executing computation on behalf of a client.
Interconnection Devices:-
In a modern network, interconnection devices are mostly necessary for the interface that
allows a single computer to talk with other computers. Routers, switches, and wireless access
points are examples of connecting devices.
Connectors and Cabling:-
Leased Line Cable:-
A leased-line is a private telecommunications circuit that is offered under a business contract
between two or more sites. In the United Kingdom, it's also known as a data line or a private
circuit. Leased lines are typically used by corporations to connect offices that are
geographically separated.
Network Media Types:-
Network media is the genuine path over which an electrical signal travels as it transfers from
one computer to another. The common types of network media, including twisted-pair cable,
coaxial cable, fiber-optic cable, coaxial cable, SPT, category 5, UTP, fiber optic, wireless.
Twisted Pair Cable:-
Twisted pair cables were one of the first directed transmission media. Two distinct insulated
copper wires are twisted together and routed in parallel to form a twisted pair cable. Copper
wires typically have a diameter of 1mm. One wire transmits data, while the other serves as a
ground reference.
29 | P a g e
Work Station:-
A workstation is a computer that is faster and more competent than a personal computer and
is designed for individual usage. It's meant to be used in a commercial or professional setting
(rather than home or recreational use). Small engineering firms, architects, graphic artists,
and any organization, department, or individual that requires a faster CPU, a significant
amount of random access memory (RAM), and specific capabilities such as high-speed
graphics adapters use workstations and software built for them.
Network Interface Cards:-
A network interface card (NIC) is a piece of hardware that allows a computer to connect to a
network. It is a circuit board that is installed in a computer and provides the machine with a
dedicated network connection. It's also known as a network adapter, network interface
controller, or LAN adapter.
Server:-
A server is a piece of computer hardware or software (computer program) that offers
functionality to other programs or devices known as "clients" in the computing world. The
client-server model is the name for this architecture. Servers can provide a variety of
functions, sometimes referred to as "services," such as exchanging data or resources across
several clients or executing computation on behalf of a client.
Interconnection Devices:-
In a modern network, interconnection devices are mostly necessary for the interface that
allows a single computer to talk with other computers. Routers, switches, and wireless access
points are examples of connecting devices.
Connectors and Cabling:-
Leased Line Cable:-
A leased-line is a private telecommunications circuit that is offered under a business contract
between two or more sites. In the United Kingdom, it's also known as a data line or a private
circuit. Leased lines are typically used by corporations to connect offices that are
geographically separated.
Network Media Types:-
Network media is the genuine path over which an electrical signal travels as it transfers from
one computer to another. The common types of network media, including twisted-pair cable,
coaxial cable, fiber-optic cable, coaxial cable, SPT, category 5, UTP, fiber optic, wireless.
Twisted Pair Cable:-
Twisted pair cables were one of the first directed transmission media. Two distinct insulated
copper wires are twisted together and routed in parallel to form a twisted pair cable. Copper
wires typically have a diameter of 1mm. One wire transmits data, while the other serves as a
ground reference.
29 | P a g e
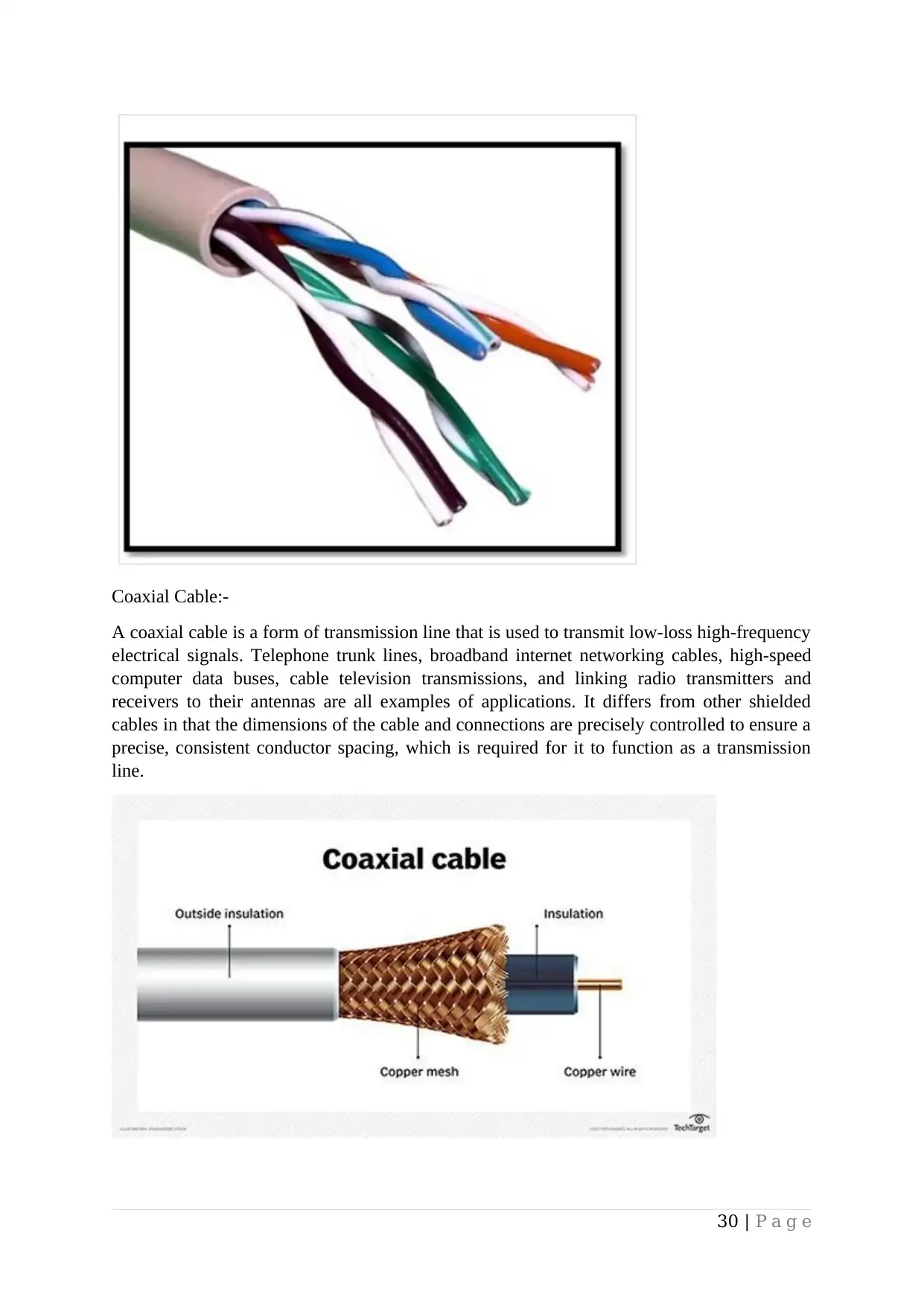
Coaxial Cable:-
A coaxial cable is a form of transmission line that is used to transmit low-loss high-frequency
electrical signals. Telephone trunk lines, broadband internet networking cables, high-speed
computer data buses, cable television transmissions, and linking radio transmitters and
receivers to their antennas are all examples of applications. It differs from other shielded
cables in that the dimensions of the cable and connections are precisely controlled to ensure a
precise, consistent conductor spacing, which is required for it to function as a transmission
line.
30 | P a g e
A coaxial cable is a form of transmission line that is used to transmit low-loss high-frequency
electrical signals. Telephone trunk lines, broadband internet networking cables, high-speed
computer data buses, cable television transmissions, and linking radio transmitters and
receivers to their antennas are all examples of applications. It differs from other shielded
cables in that the dimensions of the cable and connections are precisely controlled to ensure a
precise, consistent conductor spacing, which is required for it to function as a transmission
line.
30 | P a g e

Fiber Optic Cable:-
A fiber-optic cable, also known as an optical-fiber cable, is a cable that looks like an
electrical wire but contains one or more optical fibers for light transmission. The optical fiber
elements are usually separately coated with plastic layers and housed in a protective tube that
is appropriate for the cable's use environment. For example, long-distance communications or
providing a high-speed data link between different areas of a building, different types of
cable are used for different applications.
31 | P a g e
A fiber-optic cable, also known as an optical-fiber cable, is a cable that looks like an
electrical wire but contains one or more optical fibers for light transmission. The optical fiber
elements are usually separately coated with plastic layers and housed in a protective tube that
is appropriate for the cable's use environment. For example, long-distance communications or
providing a high-speed data link between different areas of a building, different types of
cable are used for different applications.
31 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STP cable:-
STP Cabling is twisted-pair cabling with additional shielding to reduce crosstalk and other
forms of electromagnetic interference (EMI).
The pairs of twisted cables, which are coated in foil, are shielded by an inner braided copper
mesh in the outer insulating jacket.
STP (shielded twisted pair) cable costs higher than UTP (unshielded twisted pair) cabling. It
has a maximum length of 90 meters and an impedance of 150 ohms. It is generally utilized in
networking areas where there is a lot of EMI from motors, air conditioners, power lines, or
other noisy electrical components. For IBM Token Ring networks, STP cabling is the default
type of cabling.
Category 5(CAT 5):-
Cat 5 cable (Cat 5) is a computer network twisted pair cable. The Category 5e specification
has been widely used since 2001. (Cat 5e). The cable standard supports up to 100 MHz and is
suited for most types of Ethernet over twisted pair up to 2.5GBASE-T[1][2][3][4], while it is
more typically used at 1000BASE-T (Gigabit Ethernet) speeds. Other signals, such as
telephone and video, are also carried via Cat 5.
UTP:-
A bundle of twisted pairs makes up a UTP cable. Small 22- or 24-gauge American Wire
Gauge (AWG) wires are twisted together to form twisted pairs.
32 | P a g e
STP Cabling is twisted-pair cabling with additional shielding to reduce crosstalk and other
forms of electromagnetic interference (EMI).
The pairs of twisted cables, which are coated in foil, are shielded by an inner braided copper
mesh in the outer insulating jacket.
STP (shielded twisted pair) cable costs higher than UTP (unshielded twisted pair) cabling. It
has a maximum length of 90 meters and an impedance of 150 ohms. It is generally utilized in
networking areas where there is a lot of EMI from motors, air conditioners, power lines, or
other noisy electrical components. For IBM Token Ring networks, STP cabling is the default
type of cabling.
Category 5(CAT 5):-
Cat 5 cable (Cat 5) is a computer network twisted pair cable. The Category 5e specification
has been widely used since 2001. (Cat 5e). The cable standard supports up to 100 MHz and is
suited for most types of Ethernet over twisted pair up to 2.5GBASE-T[1][2][3][4], while it is
more typically used at 1000BASE-T (Gigabit Ethernet) speeds. Other signals, such as
telephone and video, are also carried via Cat 5.
UTP:-
A bundle of twisted pairs makes up a UTP cable. Small 22- or 24-gauge American Wire
Gauge (AWG) wires are twisted together to form twisted pairs.
32 | P a g e

The wires are commonly made of copper with polyethylene (PE) or FEP insulation that is
color coded according to the cable's application.
For example, AT&T was the first to introduce the 25-pair color code UTP cable for indoor
telephone applications, which included color pairs such as white-blue, blue-white, white-
orange, orange-white, and others.
The bundle is frequently protected by a PE jacket, which is usually grey in color. The two
lines convey identical but opposing signals, and the signal's destination senses the difference.
Wireless:-
Wireless networks are computer networks that are not connected by cables of any kind. The
use of a wireless network allows enterprises to evade the expensive process of introducing
cables into buildings or as a connection between different equipment locations.
Mobile technology:-
Mobile technology follows the user wherever he or she goes. It is made up of two-way
portable communication devices, computing devices, and the networking technology that
connects them.
Currently, internet-enabled devices such as smartphones, tablets, and watches define mobile
technology. These are the most recent in a line of devices that includes two-way pagers,
notebook computers, flip phones, GPS navigation systems, and more.
Standards:-
802.2, 802.3 and 802.5
These are standards that include cables
Bluetooth/802.15
The wireless standard for devices that have a short range of wireless connection
802.11
This is the wireless standard for routers
3G and 4G
33 | P a g e
color coded according to the cable's application.
For example, AT&T was the first to introduce the 25-pair color code UTP cable for indoor
telephone applications, which included color pairs such as white-blue, blue-white, white-
orange, orange-white, and others.
The bundle is frequently protected by a PE jacket, which is usually grey in color. The two
lines convey identical but opposing signals, and the signal's destination senses the difference.
Wireless:-
Wireless networks are computer networks that are not connected by cables of any kind. The
use of a wireless network allows enterprises to evade the expensive process of introducing
cables into buildings or as a connection between different equipment locations.
Mobile technology:-
Mobile technology follows the user wherever he or she goes. It is made up of two-way
portable communication devices, computing devices, and the networking technology that
connects them.
Currently, internet-enabled devices such as smartphones, tablets, and watches define mobile
technology. These are the most recent in a line of devices that includes two-way pagers,
notebook computers, flip phones, GPS navigation systems, and more.
Standards:-
802.2, 802.3 and 802.5
These are standards that include cables
Bluetooth/802.15
The wireless standard for devices that have a short range of wireless connection
802.11
This is the wireless standard for routers
3G and 4G
33 | P a g e

These are mobile technology standards
Software:-
Network operating system:-
A network operating system (NOS) is a type of operating system that handles network
resources: it's essentially an operating system with built-in features for connecting computers
and devices to a local area network (LAN). The NOS simultaneously processes many
requests (inputs) and ensures the security required in a multiuser environment. It could be a
totally self-contained operating system, such as NetWare, Unix, Windows 2000, or Mac OS
X, or it could be dependent on another operating system (for example, Windows 3.11 for
Workgroups requires DOS; LAN Server requires OS/2; LANtastic requires DOS). A NOS
may also provide directory services and other services in addition to file and print services.
Virus Checker:-
This is a component of an anti-virus software package that scans a hard drive for viruses and
other harmful items. These programs are made for various operating systems, and scanning
methods can be manual or automatic Examples of these anti-virus programs are Kaspersky,
vast antivirus.
Commercial Systems:-
Commercial systems are any software or program that is intended and developed for
licensing or sale to end-user or that assists a commercial purpose. Commercial software was
once considered to be branded software, but now a number of free and open-source software
applications are licensed or sold to end-users. There are various commercial systems here are
a few examples, Windows, Linux, Mac, os.
Firewall:-
A firewall is a network security device that monitors incoming and outgoing network traffic
and allows or disallows data packets according to a set of security rules. Its goal is to create a
barrier between your internal network and incoming traffic from other sources (such as the
internet) so that malicious traffic like viruses and hackers can't get in.
Server OS:-
A server operating system (OS) is a type of operating system designed to run on a server
computer.
It's a more advanced operating system with features and capabilities that are necessary in a
client-server architecture or other enterprise computing environment.
Client Operating Software:-
34 | P a g e
Software:-
Network operating system:-
A network operating system (NOS) is a type of operating system that handles network
resources: it's essentially an operating system with built-in features for connecting computers
and devices to a local area network (LAN). The NOS simultaneously processes many
requests (inputs) and ensures the security required in a multiuser environment. It could be a
totally self-contained operating system, such as NetWare, Unix, Windows 2000, or Mac OS
X, or it could be dependent on another operating system (for example, Windows 3.11 for
Workgroups requires DOS; LAN Server requires OS/2; LANtastic requires DOS). A NOS
may also provide directory services and other services in addition to file and print services.
Virus Checker:-
This is a component of an anti-virus software package that scans a hard drive for viruses and
other harmful items. These programs are made for various operating systems, and scanning
methods can be manual or automatic Examples of these anti-virus programs are Kaspersky,
vast antivirus.
Commercial Systems:-
Commercial systems are any software or program that is intended and developed for
licensing or sale to end-user or that assists a commercial purpose. Commercial software was
once considered to be branded software, but now a number of free and open-source software
applications are licensed or sold to end-users. There are various commercial systems here are
a few examples, Windows, Linux, Mac, os.
Firewall:-
A firewall is a network security device that monitors incoming and outgoing network traffic
and allows or disallows data packets according to a set of security rules. Its goal is to create a
barrier between your internal network and incoming traffic from other sources (such as the
internet) so that malicious traffic like viruses and hackers can't get in.
Server OS:-
A server operating system (OS) is a type of operating system designed to run on a server
computer.
It's a more advanced operating system with features and capabilities that are necessary in a
client-server architecture or other enterprise computing environment.
Client Operating Software:-
34 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

A client is a small computer that accesses a server through a network. For example, in BSSL,
an employee logs in to the client machine to access the files and applications running on a
server machine. The client machine is running a client operating software.
System Bus:-
The system bus is a data transmission line made up of cables and connectors that connects a
computer's processors to its primary memory. The bus serves as a conduit for data and
control signals travelling between the computer system's primary components. The functions
of the three primary buses, namely the data, address, and control buses, are combined in the
system bus. Each of the three vehicles has its own personality and set of tasks.
The system bus combines the functions of the three main buses, which are as follows:
The control bus carries the control, timing and coordination signals to manage the
various functions across the system.
The address bus is used to specify memory locations for the data being transferred.
The data bus, which is a bidirectional path, carries the actual data between the
processor, the memory and the peripherals.
Examples of System Bus:-
Low pin count, IEEE196, IEEE-488 and high performance parallel interface
Local System Architecture:-
Memory: a memory stores the data in the system or the network which relies on the power
and sending data to different components in the computer like the network card.
Without the memory one will not be able to store any data in the system and data will be
displayed in the system.
Examples of memories are: RAM and ROM
Processor: this is an integrated electronic circuit that executes the calculations for running the
computer, does the arithmetic and the other functions executed by OS.
Without the processor the following tasks cannot be done:
Clock speed
Capability to route instructions in certain time
Examples of processor: Xeon, Intel coreI7 and
35 | P a g e
an employee logs in to the client machine to access the files and applications running on a
server machine. The client machine is running a client operating software.
System Bus:-
The system bus is a data transmission line made up of cables and connectors that connects a
computer's processors to its primary memory. The bus serves as a conduit for data and
control signals travelling between the computer system's primary components. The functions
of the three primary buses, namely the data, address, and control buses, are combined in the
system bus. Each of the three vehicles has its own personality and set of tasks.
The system bus combines the functions of the three main buses, which are as follows:
The control bus carries the control, timing and coordination signals to manage the
various functions across the system.
The address bus is used to specify memory locations for the data being transferred.
The data bus, which is a bidirectional path, carries the actual data between the
processor, the memory and the peripherals.
Examples of System Bus:-
Low pin count, IEEE196, IEEE-488 and high performance parallel interface
Local System Architecture:-
Memory: a memory stores the data in the system or the network which relies on the power
and sending data to different components in the computer like the network card.
Without the memory one will not be able to store any data in the system and data will be
displayed in the system.
Examples of memories are: RAM and ROM
Processor: this is an integrated electronic circuit that executes the calculations for running the
computer, does the arithmetic and the other functions executed by OS.
Without the processor the following tasks cannot be done:
Clock speed
Capability to route instructions in certain time
Examples of processor: Xeon, Intel coreI7 and
35 | P a g e

I/O devices: an input output device are used for communicating with the computer where one
is able to send and receive data from the computer.
Examples of I/O devices: modem, network adapter, hard drives and touch screen.
Explore a range of server types and justify the selection of a server, considering a given
scenario regarding cost and performance optimisation.
Web server:-
A web server is a program that uses HTTP (Hypertext Transfer Protocol) to help the files that
from web pages to users, inn reply to their requests, which are promoted by their computers’
HTTP clients. Devoted computers and appliances may be referred to as Web servers as well.
Files server:-
Files server is a devices that panels access to separately stored siles, as part of a multiplier
system, a file server is a computer attached to a network that has the primary purpose of
providing a location of shared disk access.
Database server:-
It is similar to data warehouse where the website stores or keeps their data and information. A
Database server is a computer in a LAN that is devoted to database storage and recovery. The
database server holds the Database Management system (DBMS) and the databases. Upon
requests from the client machines, it searches the database for selected records and passes
them back over the network.
Virtualization server:-
Virtualization server is a virtualization method that includes dividing a physical server into a
number of small, virtual servers with the help of virtualization software. In server
virtualization, each virtual server runs multiple operating system instances at the same time.
Terminal service server:-
Terminal service server also called a communication server, is a hardware device or server
that provides terminals, such as PCs, printers, and other devices, with a mutual connection
point to a local or wide area network (WAN).
Terminal services server a hardware devices or server that allows one or more terminals to
connect to a local area network (LAN) or the internet can be PCs, printers, IBM 3270
emulators or other devices with a RS-232 / RS-423 serial port interface.
I would choose the database server for the chosen scenario because Database Server gives
new meaning to the word performance in the client/server world.
36 | P a g e
is able to send and receive data from the computer.
Examples of I/O devices: modem, network adapter, hard drives and touch screen.
Explore a range of server types and justify the selection of a server, considering a given
scenario regarding cost and performance optimisation.
Web server:-
A web server is a program that uses HTTP (Hypertext Transfer Protocol) to help the files that
from web pages to users, inn reply to their requests, which are promoted by their computers’
HTTP clients. Devoted computers and appliances may be referred to as Web servers as well.
Files server:-
Files server is a devices that panels access to separately stored siles, as part of a multiplier
system, a file server is a computer attached to a network that has the primary purpose of
providing a location of shared disk access.
Database server:-
It is similar to data warehouse where the website stores or keeps their data and information. A
Database server is a computer in a LAN that is devoted to database storage and recovery. The
database server holds the Database Management system (DBMS) and the databases. Upon
requests from the client machines, it searches the database for selected records and passes
them back over the network.
Virtualization server:-
Virtualization server is a virtualization method that includes dividing a physical server into a
number of small, virtual servers with the help of virtualization software. In server
virtualization, each virtual server runs multiple operating system instances at the same time.
Terminal service server:-
Terminal service server also called a communication server, is a hardware device or server
that provides terminals, such as PCs, printers, and other devices, with a mutual connection
point to a local or wide area network (WAN).
Terminal services server a hardware devices or server that allows one or more terminals to
connect to a local area network (LAN) or the internet can be PCs, printers, IBM 3270
emulators or other devices with a RS-232 / RS-423 serial port interface.
I would choose the database server for the chosen scenario because Database Server gives
new meaning to the word performance in the client/server world.
36 | P a g e

Performance development are achieved primarily by reducing network traffic, intelligently
maintaining database files, and providing intelligent lock management. When associated to
other leading ever solutions, Advantage Database Server offers exceptional performance
without the overhead associated with other SQL-based database management systems. The
cost will be it will cost around $499 dollars and the reason why I choose a database server is
because for the given scenario being a college having a database server will be helpful for
looking for student records. The operating system requirement for database server is;
A. English Windows 2003
B. English Windows 2008
C. English Windows 2008 R2
D. English Windows Server 2012 R2
E. Linux
Supported Database Management Systems:-
Microsoft SQL server 2012 SP2
Microsoft SQL server 2008 R2 SP2
Microsoft SQL server 2005 R2 SP2
32-bit and 64-bit English Microsoft server 2008, standard and enterprise editions,
32-bit and 64-bit OracleTM 10g Release 2 (10.2.0.2 and higher), standard and enterprise
editions
32-bit and 64-bit Oracle 11g Release 1 and Release 2, standard and enterprise edition
Protocol
Design a networked system to meet a given specification.
LAN:-
It stands for local area network designing a local area Network also known as a LAN is a
complex process with a variety of factors to consider. A well-designed LAN will provide
consistent, high quality services to every device attached to the network, no matter its size.
Likewise, the network must able to provide continuous access to functions such as printing
and file sharing. To make sure the network in fast, efficient and secure, all these aspects
should be planned in advance.
A local Area Network provides connectivity to a relatively small group of users in a simple
building, office or campus. It also typically connects to the global Internet through a gateway
server, which acts as the main defence against unauthorized access to network resources.
With all this in mind, the main consideration in the early stages of LAN planning is what size
it will be and what services it will provide. While a LAN featuring ten nodes can be set up in
as little as one day, a larger network is a bigger undertaking.
Justification of the topology the topology that is used for the network is bus topology:-
It is easy to connect a device to the network.
37 | P a g e
maintaining database files, and providing intelligent lock management. When associated to
other leading ever solutions, Advantage Database Server offers exceptional performance
without the overhead associated with other SQL-based database management systems. The
cost will be it will cost around $499 dollars and the reason why I choose a database server is
because for the given scenario being a college having a database server will be helpful for
looking for student records. The operating system requirement for database server is;
A. English Windows 2003
B. English Windows 2008
C. English Windows 2008 R2
D. English Windows Server 2012 R2
E. Linux
Supported Database Management Systems:-
Microsoft SQL server 2012 SP2
Microsoft SQL server 2008 R2 SP2
Microsoft SQL server 2005 R2 SP2
32-bit and 64-bit English Microsoft server 2008, standard and enterprise editions,
32-bit and 64-bit OracleTM 10g Release 2 (10.2.0.2 and higher), standard and enterprise
editions
32-bit and 64-bit Oracle 11g Release 1 and Release 2, standard and enterprise edition
Protocol
Design a networked system to meet a given specification.
LAN:-
It stands for local area network designing a local area Network also known as a LAN is a
complex process with a variety of factors to consider. A well-designed LAN will provide
consistent, high quality services to every device attached to the network, no matter its size.
Likewise, the network must able to provide continuous access to functions such as printing
and file sharing. To make sure the network in fast, efficient and secure, all these aspects
should be planned in advance.
A local Area Network provides connectivity to a relatively small group of users in a simple
building, office or campus. It also typically connects to the global Internet through a gateway
server, which acts as the main defence against unauthorized access to network resources.
With all this in mind, the main consideration in the early stages of LAN planning is what size
it will be and what services it will provide. While a LAN featuring ten nodes can be set up in
as little as one day, a larger network is a bigger undertaking.
Justification of the topology the topology that is used for the network is bus topology:-
It is easy to connect a device to the network.
37 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

If the computer or peripheral has the appropriate connection device, then it can be easily
added to the network. The new devices connects to the linear bus topology and becomes part
of the network immediately. For those who need a temporary network that can be setup
quickly, there isn’t a better option that is available right now. If several user need mutual
access to a printer, adding the printer to the network meets that need immediately.
The failure of one station does not affect the rest of the network.
If one computer or peripheral should fail when using bus topology, the rest of the network is
not affected by this change in performance. The linear nature of the network means that each
unit transmits to the backbone and the data is then available to the other units that remain
connected. This makes it an effective way to share uninterrupted communications.
Extensions can be made to the network.
The size and scope of bus topology is naturally incomplete. It can, however, be extended
quite easily. Joining cable with a repeater or connector allow for additional peripherals or
computers to be added to the network. Although this can increase the number of packet
collisions that may occurs, it is simplified solution that can get people up and working
quickly and for a minimal overall cost.
Multiple peripherals can be supported through bus topology.
Routers, printer, and other data devices can be connected to this network in addition to
computer or terminals. This can increase the speed of productivity because instead of sending
commands to a centralized network, a command can be sent directly to the needed peripheral.
Since it’s a for collage multiple peripheral devices will be used therefore bus topology would
work best.
Blueprint of the network system.
Logical design of the network.
38 | P a g e
added to the network. The new devices connects to the linear bus topology and becomes part
of the network immediately. For those who need a temporary network that can be setup
quickly, there isn’t a better option that is available right now. If several user need mutual
access to a printer, adding the printer to the network meets that need immediately.
The failure of one station does not affect the rest of the network.
If one computer or peripheral should fail when using bus topology, the rest of the network is
not affected by this change in performance. The linear nature of the network means that each
unit transmits to the backbone and the data is then available to the other units that remain
connected. This makes it an effective way to share uninterrupted communications.
Extensions can be made to the network.
The size and scope of bus topology is naturally incomplete. It can, however, be extended
quite easily. Joining cable with a repeater or connector allow for additional peripherals or
computers to be added to the network. Although this can increase the number of packet
collisions that may occurs, it is simplified solution that can get people up and working
quickly and for a minimal overall cost.
Multiple peripherals can be supported through bus topology.
Routers, printer, and other data devices can be connected to this network in addition to
computer or terminals. This can increase the speed of productivity because instead of sending
commands to a centralized network, a command can be sent directly to the needed peripheral.
Since it’s a for collage multiple peripheral devices will be used therefore bus topology would
work best.
Blueprint of the network system.
Logical design of the network.
38 | P a g e
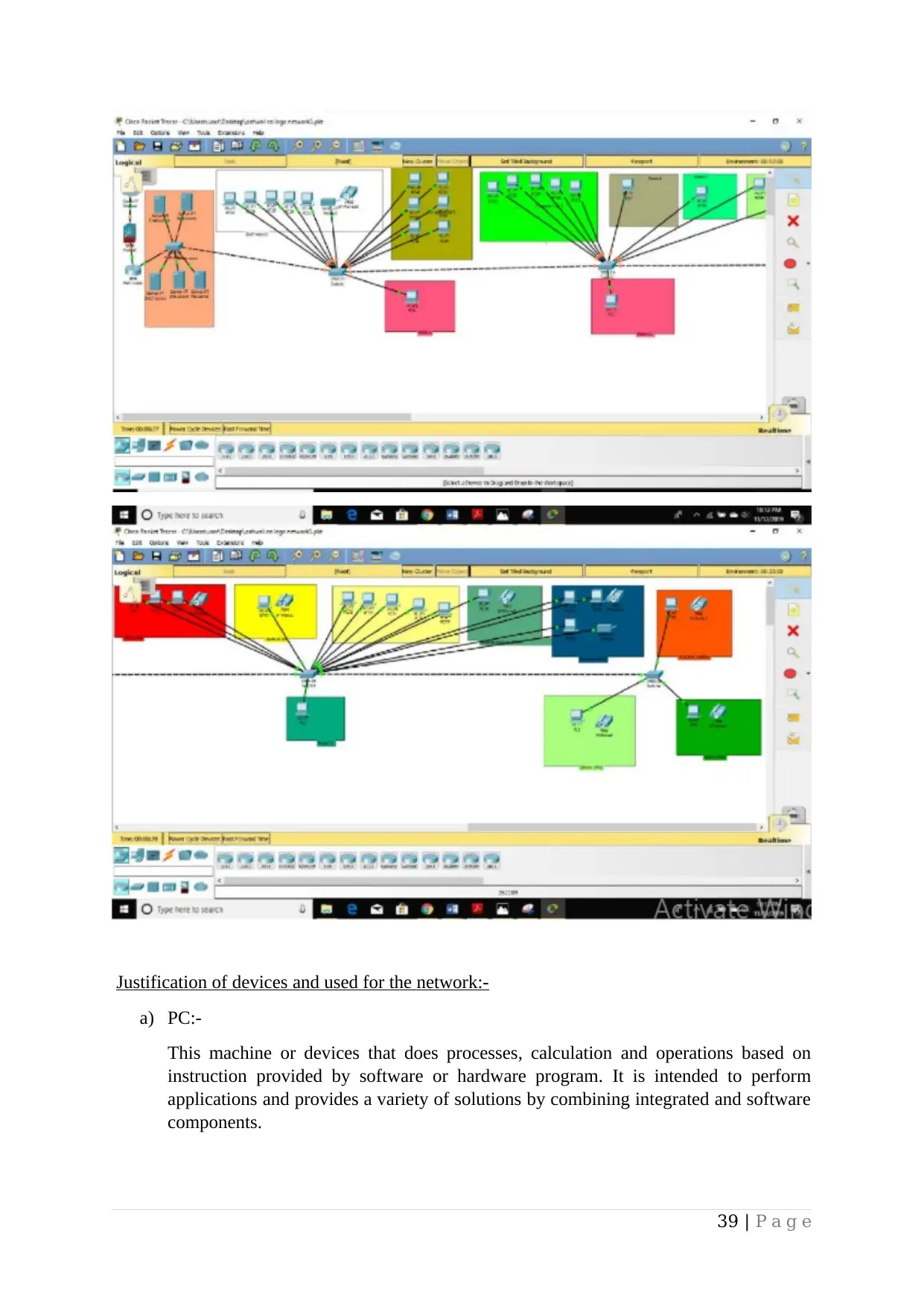
Justification of devices and used for the network:-
a) PC:-
This machine or devices that does processes, calculation and operations based on
instruction provided by software or hardware program. It is intended to perform
applications and provides a variety of solutions by combining integrated and software
components.
39 | P a g e
a) PC:-
This machine or devices that does processes, calculation and operations based on
instruction provided by software or hardware program. It is intended to perform
applications and provides a variety of solutions by combining integrated and software
components.
39 | P a g e

b) Router:-
This a devices that examines the contents of data packets transmitted within a network or
to another network. Routers control whether the source and destination are on the same
network or whether data must be transferred from one network type to another, which
requires summarizing the data packet with routing protocol header information for the new
networking type.
c) Cloud:-
This a type service where cloud computing resources and substructure are used to
return and manage data and services which is done over the internet.
d) Server:-
This is a computer, a device or a program that is dedicated to managing networks
resources. Servers are often referred to as dedicated because they carry out hardly any
other tasks apart from their server tasks.
e) Switch:-
In the content of networking a switch is a high-speed devices that receives incoming
data packets and redirects them to their destination on a local Area Network (LAN).
f) IPhone:-
An IP telephone system uses packet-switched voice over IP (VoIP), or Internet
telephony, to transmit telephone calls over the internet as opposed to the circuit-
switched telephony used by the Traditional Public Switched Telephone Network
(PSTN)>
g) Firewall:-
A firewall is a network security device that monitors incoming and outgoing network
traffic and decides whether to allow or block specific traffic based on a defined set of
security rules.
h) Printer:-
A printer is an external hardware output device that takes the electronic data stored on
a computer or other devices and generates a hard copy of it.
Internal connections:-
The devices used in the network use dissimilar types of connection from the wired to the
wireless which include the following cables.
Fiber optic cable:-
A fiber-optic cable, also known as an optical-fiber cable, is a cable that looks like an
electrical wire but contains one or more optical fibers for light transmission. The optical fiber
elements are usually separately coated with plastic layers and housed in a protective tube that
is appropriate for the cable's use environment. For example, long-distance communications or
40 | P a g e
This a devices that examines the contents of data packets transmitted within a network or
to another network. Routers control whether the source and destination are on the same
network or whether data must be transferred from one network type to another, which
requires summarizing the data packet with routing protocol header information for the new
networking type.
c) Cloud:-
This a type service where cloud computing resources and substructure are used to
return and manage data and services which is done over the internet.
d) Server:-
This is a computer, a device or a program that is dedicated to managing networks
resources. Servers are often referred to as dedicated because they carry out hardly any
other tasks apart from their server tasks.
e) Switch:-
In the content of networking a switch is a high-speed devices that receives incoming
data packets and redirects them to their destination on a local Area Network (LAN).
f) IPhone:-
An IP telephone system uses packet-switched voice over IP (VoIP), or Internet
telephony, to transmit telephone calls over the internet as opposed to the circuit-
switched telephony used by the Traditional Public Switched Telephone Network
(PSTN)>
g) Firewall:-
A firewall is a network security device that monitors incoming and outgoing network
traffic and decides whether to allow or block specific traffic based on a defined set of
security rules.
h) Printer:-
A printer is an external hardware output device that takes the electronic data stored on
a computer or other devices and generates a hard copy of it.
Internal connections:-
The devices used in the network use dissimilar types of connection from the wired to the
wireless which include the following cables.
Fiber optic cable:-
A fiber-optic cable, also known as an optical-fiber cable, is a cable that looks like an
electrical wire but contains one or more optical fibers for light transmission. The optical fiber
elements are usually separately coated with plastic layers and housed in a protective tube that
is appropriate for the cable's use environment. For example, long-distance communications or
40 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
providing a high-speed data link between different areas of a building, different types of
cable are used for different applications.
Coaxial cable:-
Coaxial cable is a form of transmission line that is used to transmit low-loss high-frequency
electrical signals. Telephone trunk lines, broadband internet networking cables, high-speed
computer data buses, cable television transmissions, and linking radio transmitters and
receivers to their antennas are all examples of applications. It differs from other shielded
cables in that the dimensions of the cable and connections are precisely controlled to ensure a
precise, consistent conductor spacing, which is required for it to function as a transmission
line.
Coaxial cable was utilized in the first and subsequent transatlantic cable deployments (1858),
but its theory was not detailed until 1880 by Oliver Heaviside, an English scientist, engineer,
and mathematician who patented the idea in that year (British patent No. 1,407).
External Connections:-
The external connections are completed wirelessly using the wireless LANs which has high
frequency radio signals, infrared light beams to communicate between the workstations,
servers and hubs where the workstation the data is been sent has a transceiver to send and
receive the data and they are great for the smart devices mostly from the phones and laptops.
Device Requirement:-
S. No Device name Version No. of devices
1. Router 1941 25
2. Switch 2960 40
3. Wi-Fi router TP link 20
4. Firewall Asa5506 2
5. Rj45 2packet
6. LAN Cable Cat56 10km
41 | P a g e
cable are used for different applications.
Coaxial cable:-
Coaxial cable is a form of transmission line that is used to transmit low-loss high-frequency
electrical signals. Telephone trunk lines, broadband internet networking cables, high-speed
computer data buses, cable television transmissions, and linking radio transmitters and
receivers to their antennas are all examples of applications. It differs from other shielded
cables in that the dimensions of the cable and connections are precisely controlled to ensure a
precise, consistent conductor spacing, which is required for it to function as a transmission
line.
Coaxial cable was utilized in the first and subsequent transatlantic cable deployments (1858),
but its theory was not detailed until 1880 by Oliver Heaviside, an English scientist, engineer,
and mathematician who patented the idea in that year (British patent No. 1,407).
External Connections:-
The external connections are completed wirelessly using the wireless LANs which has high
frequency radio signals, infrared light beams to communicate between the workstations,
servers and hubs where the workstation the data is been sent has a transceiver to send and
receive the data and they are great for the smart devices mostly from the phones and laptops.
Device Requirement:-
S. No Device name Version No. of devices
1. Router 1941 25
2. Switch 2960 40
3. Wi-Fi router TP link 20
4. Firewall Asa5506 2
5. Rj45 2packet
6. LAN Cable Cat56 10km
41 | P a g e
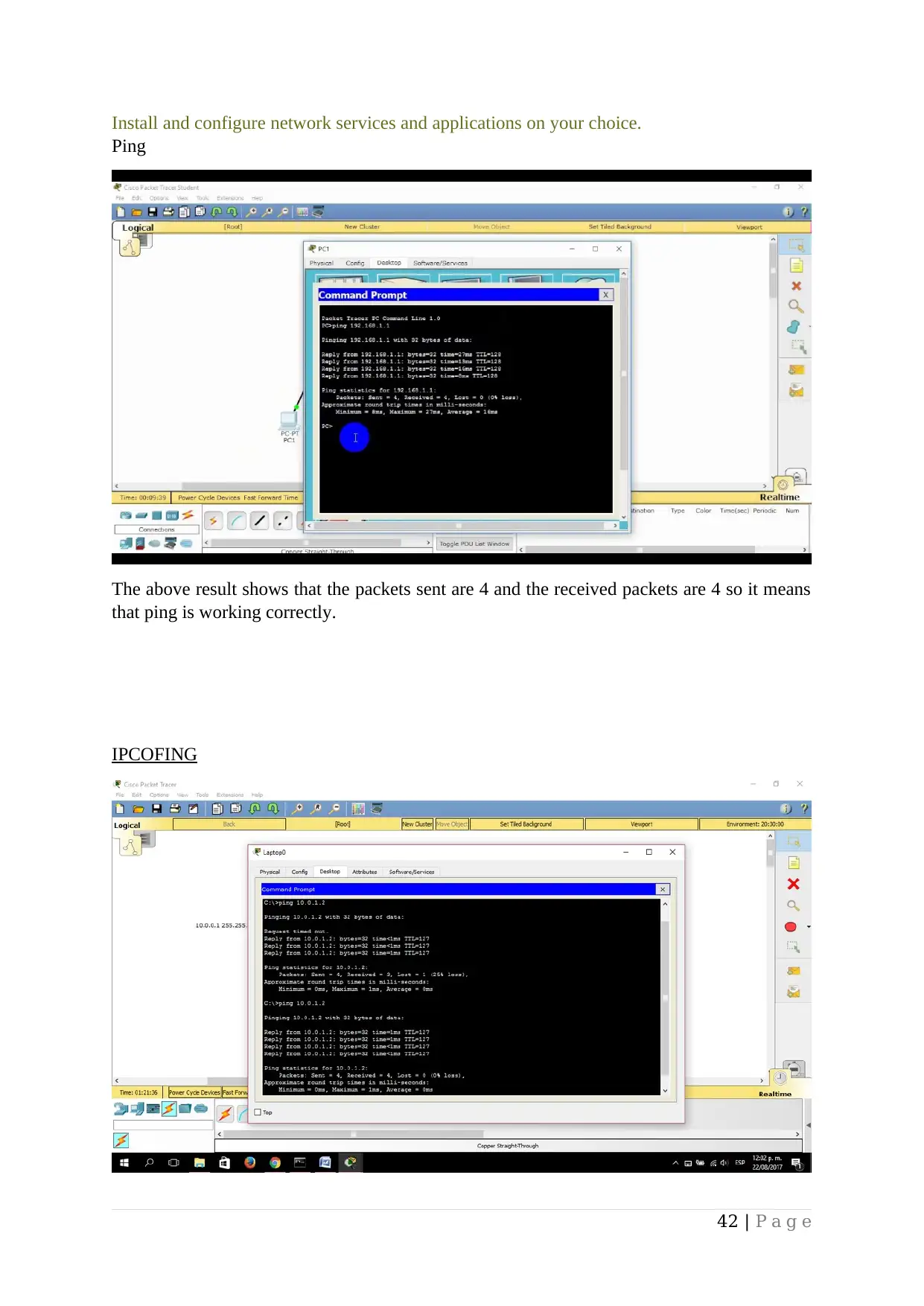
Install and configure network services and applications on your choice.
Ping
The above result shows that the packets sent are 4 and the received packets are 4 so it means
that ping is working correctly.
IPCOFING
42 | P a g e
Ping
The above result shows that the packets sent are 4 and the received packets are 4 so it means
that ping is working correctly.
IPCOFING
42 | P a g e
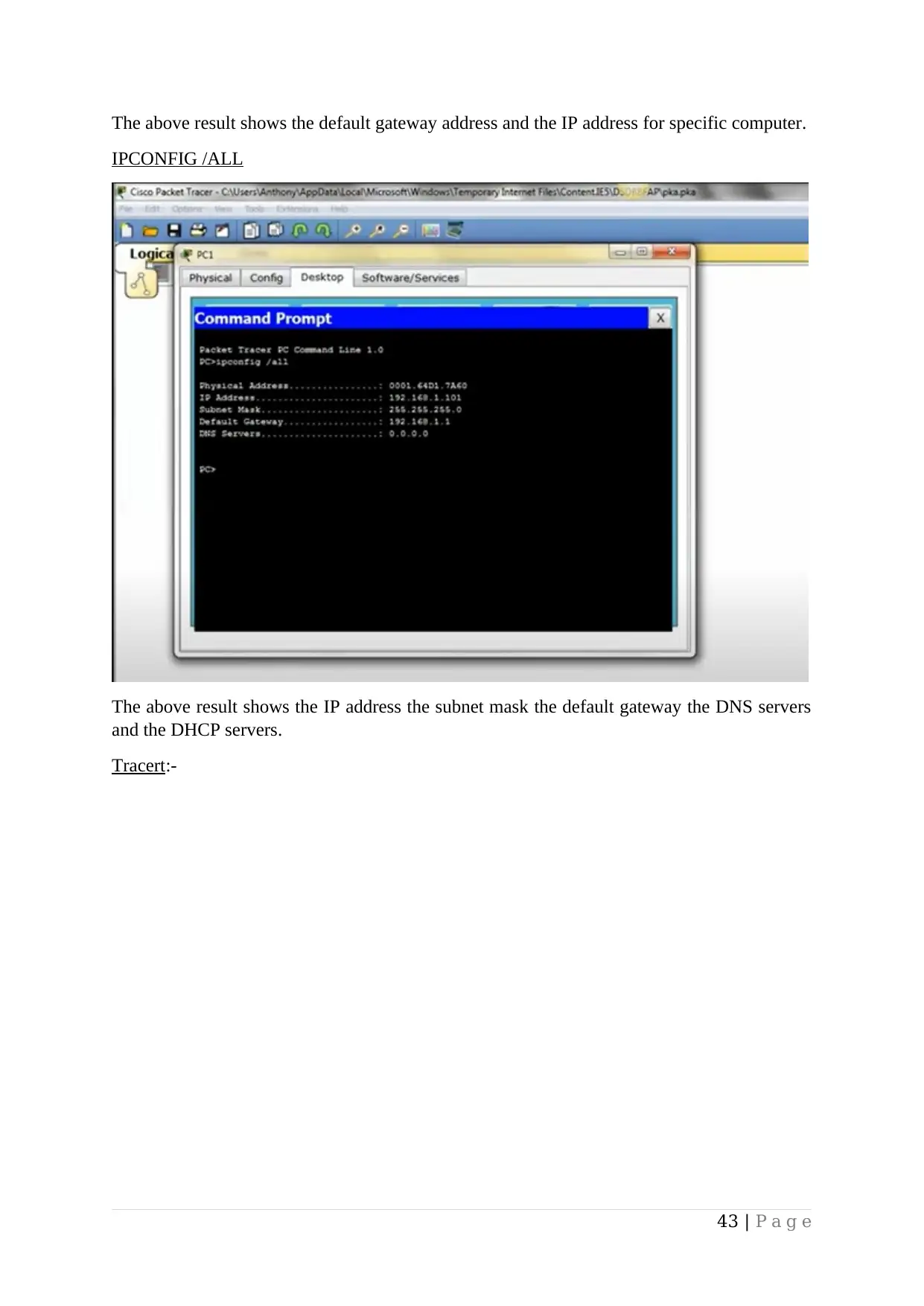
The above result shows the default gateway address and the IP address for specific computer.
IPCONFIG /ALL
The above result shows the IP address the subnet mask the default gateway the DNS servers
and the DHCP servers.
Tracert:-
43 | P a g e
IPCONFIG /ALL
The above result shows the IP address the subnet mask the default gateway the DNS servers
and the DHCP servers.
Tracert:-
43 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
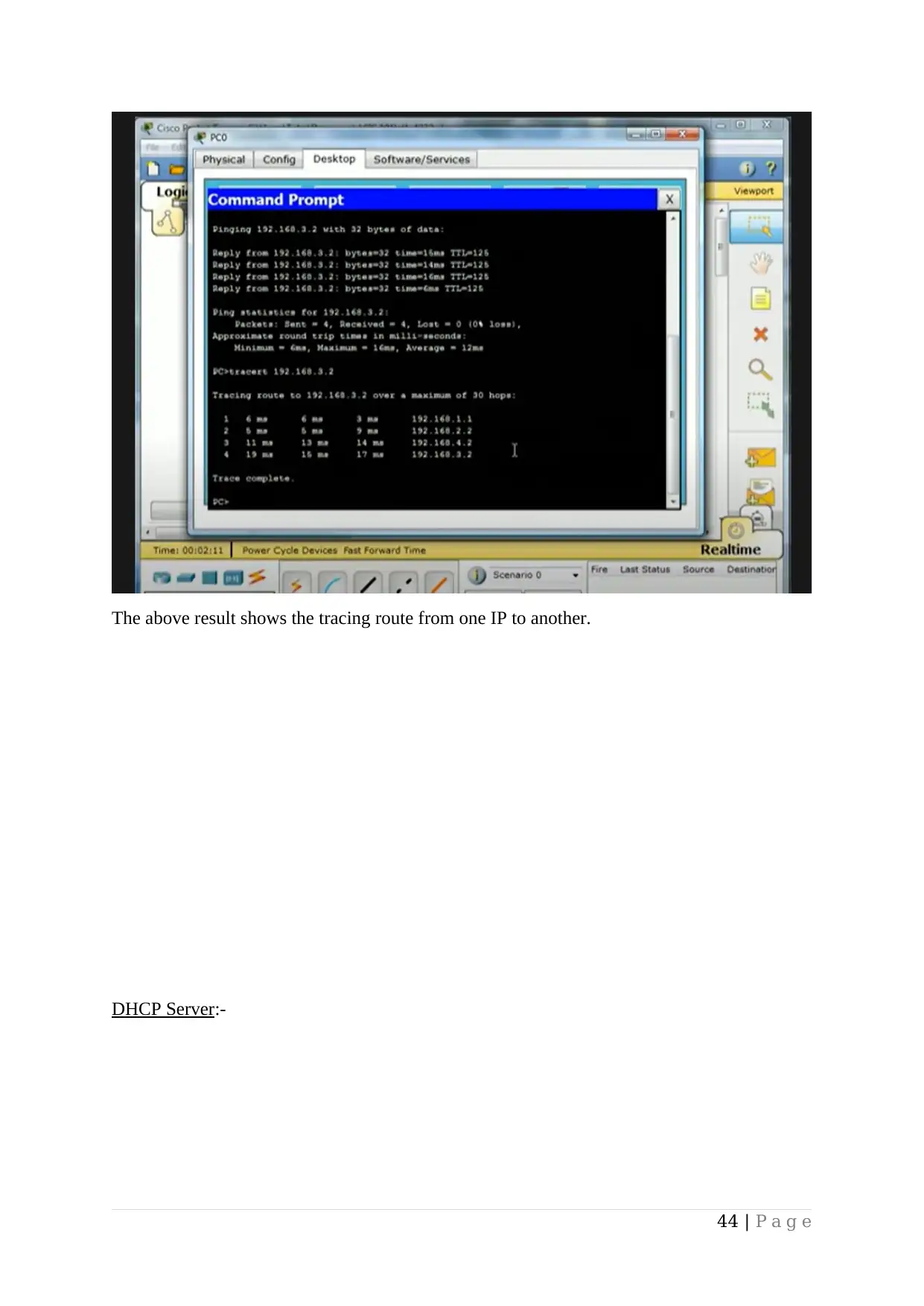
The above result shows the tracing route from one IP to another.
DHCP Server:-
44 | P a g e
DHCP Server:-
44 | P a g e
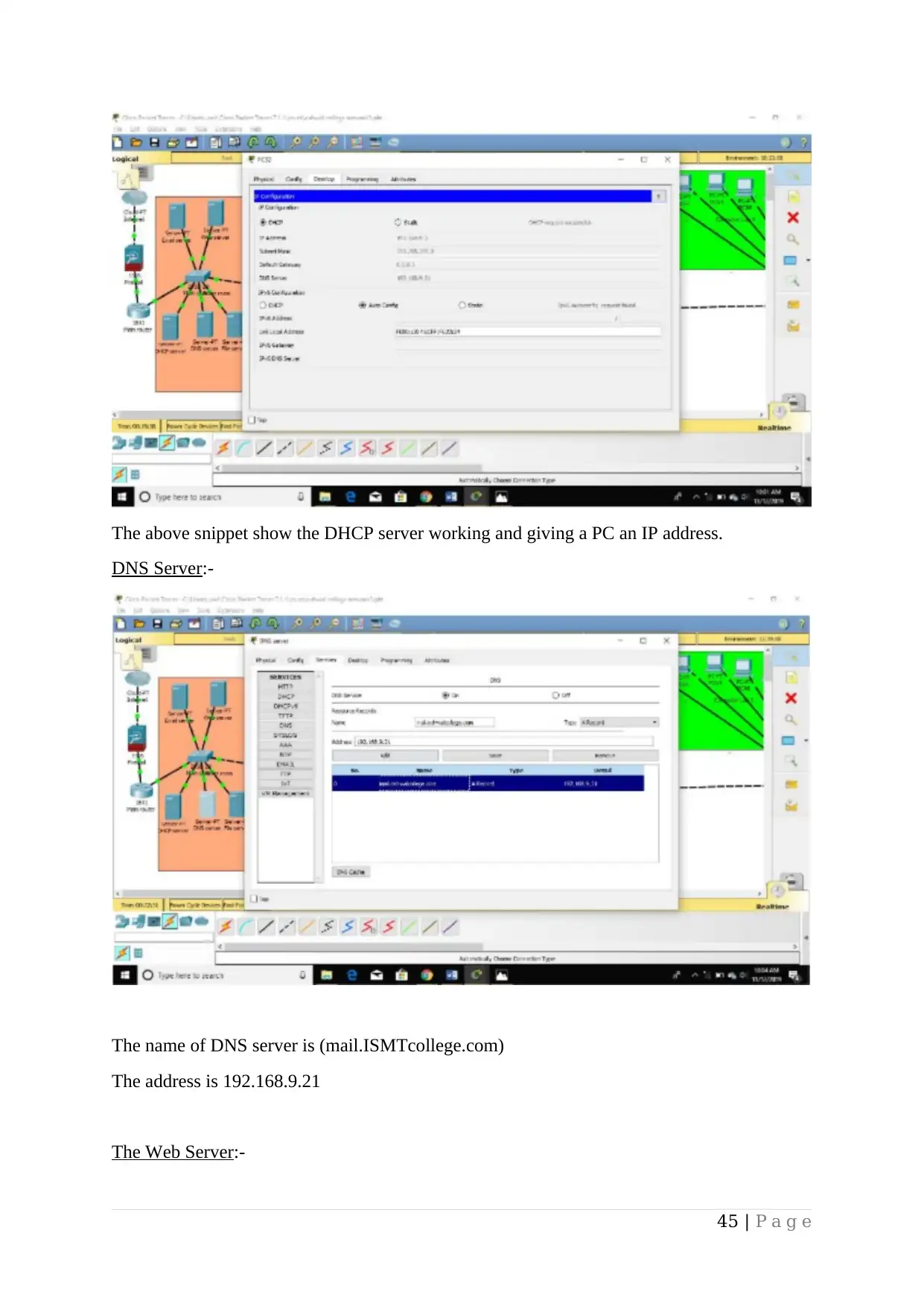
The above snippet show the DHCP server working and giving a PC an IP address.
DNS Server:-
The name of DNS server is (mail.ISMTcollege.com)
The address is 192.168.9.21
The Web Server:-
45 | P a g e
DNS Server:-
The name of DNS server is (mail.ISMTcollege.com)
The address is 192.168.9.21
The Web Server:-
45 | P a g e
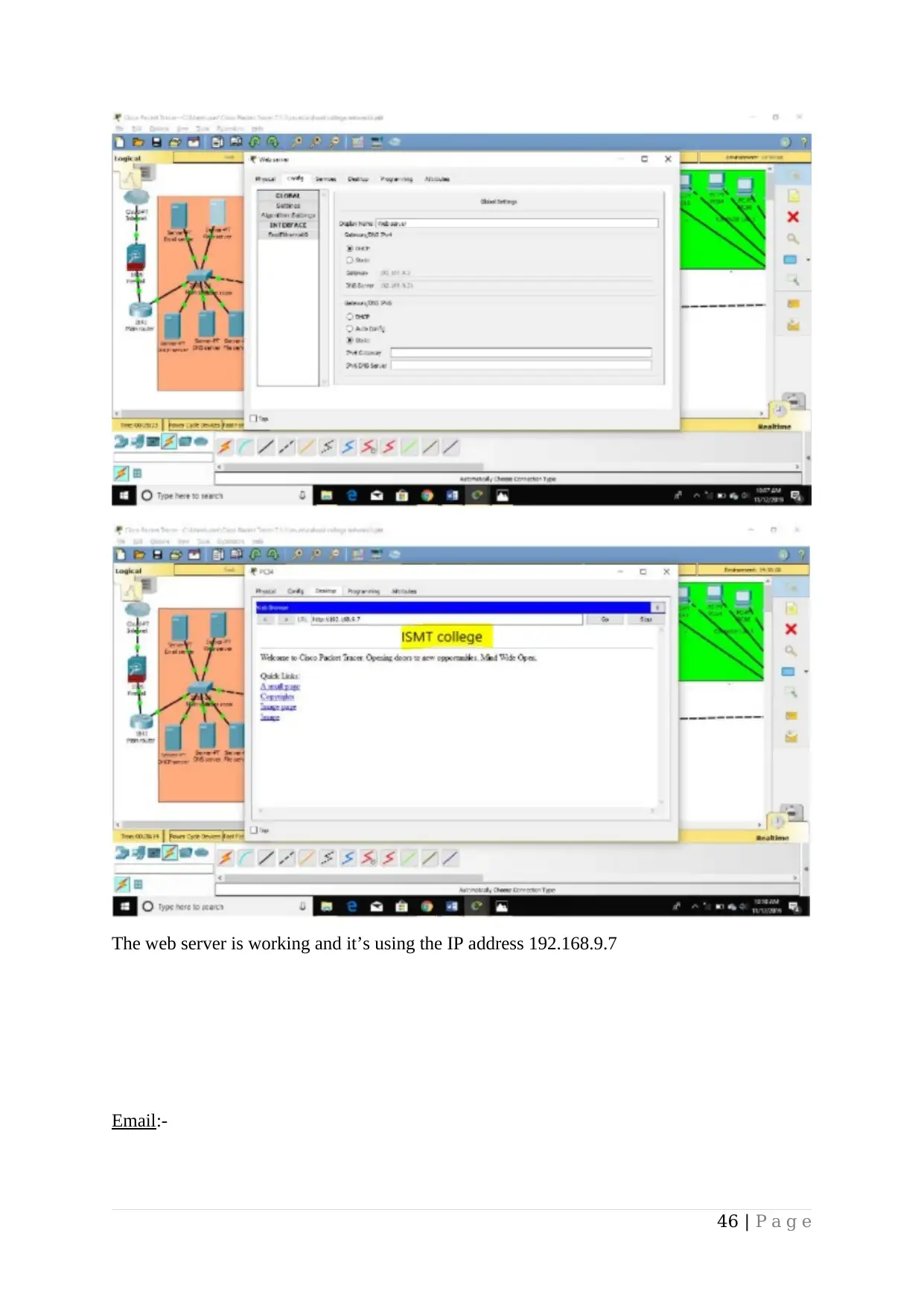
The web server is working and it’s using the IP address 192.168.9.7
Email:-
46 | P a g e
Email:-
46 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
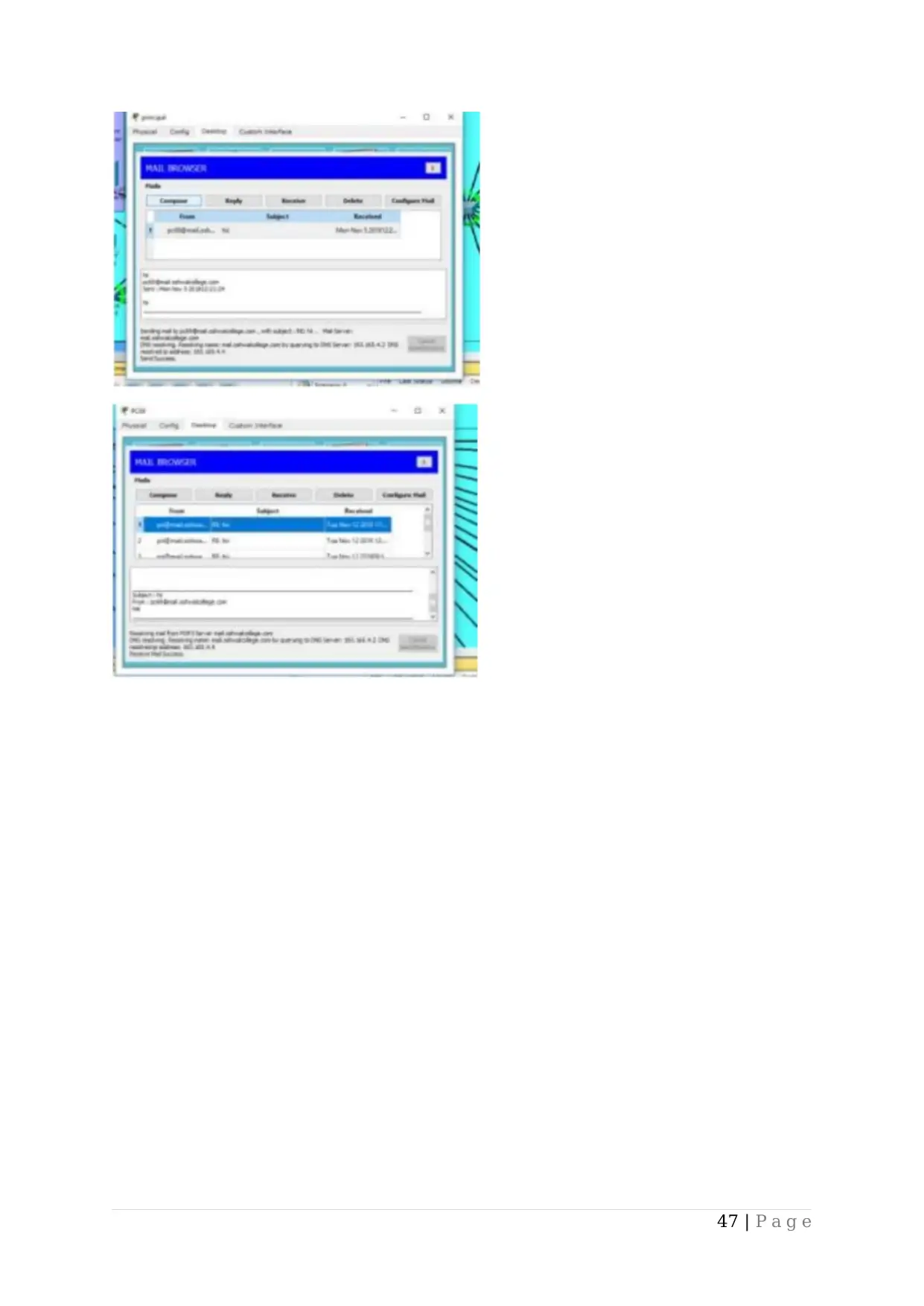
47 | P a g e

Test and evaluate the design to meet the requirements and analyse user feedback with
the aim of improving efficiency.
I have designed the network of a commercial bank or for straight bank as per the given
scenario in Cisco Packet Tracer. Now, in order to complete this task. I have to make some
test log consisting what is to tested and expected output. Also, I am going to evaluate this
design with the institute requirement and collect feedback from users. Then, analyse that
feedbacks.
‘
48 | P a g e
Independent Feedback
Project Title: Nepal bank ltd
AsxsFeedback Given
By: Nawarj Limbu
Signature:
Date: 10-11-2018
Project Description (in brief):-
I developed a network in Visio Tool and executed it with Cisco Packet
Tracer to meet the requirements of a Nepal IT educational institute. I set up
two IT laboratories on the first and second floors, each with 25 PCs. On the
third and fourth floors, 35 computers are set up for employees and upper
management. Three network administrators, as well as a DC, DNS, and
DHCP configured server, are located on the third level. Each floor has four
switches to connect the complete network, which are all linked to a single
router on the fourth floor. The first story has three printers, while the
second and fourth floors have access points. A firewall is also handled in the
Important Features
of the Design
1) User friendly and effective.
2)This project is run on every
plat form because cisco systems
are used.
3) This project contains well
managed design, security,
organized IP, interdepartmental
contacts and data transfer
facilities etc.
4)All the information in the
6)It allows login for only the valid
users having correct user name and
password. And the admin has different
authentication than a user.
7) It provides remote management
the aim of improving efficiency.
I have designed the network of a commercial bank or for straight bank as per the given
scenario in Cisco Packet Tracer. Now, in order to complete this task. I have to make some
test log consisting what is to tested and expected output. Also, I am going to evaluate this
design with the institute requirement and collect feedback from users. Then, analyse that
feedbacks.
‘
48 | P a g e
Independent Feedback
Project Title: Nepal bank ltd
AsxsFeedback Given
By: Nawarj Limbu
Signature:
Date: 10-11-2018
Project Description (in brief):-
I developed a network in Visio Tool and executed it with Cisco Packet
Tracer to meet the requirements of a Nepal IT educational institute. I set up
two IT laboratories on the first and second floors, each with 25 PCs. On the
third and fourth floors, 35 computers are set up for employees and upper
management. Three network administrators, as well as a DC, DNS, and
DHCP configured server, are located on the third level. Each floor has four
switches to connect the complete network, which are all linked to a single
router on the fourth floor. The first story has three printers, while the
second and fourth floors have access points. A firewall is also handled in the
Important Features
of the Design
1) User friendly and effective.
2)This project is run on every
plat form because cisco systems
are used.
3) This project contains well
managed design, security,
organized IP, interdepartmental
contacts and data transfer
facilities etc.
4)All the information in the
6)It allows login for only the valid
users having correct user name and
password. And the admin has different
authentication than a user.
7) It provides remote management
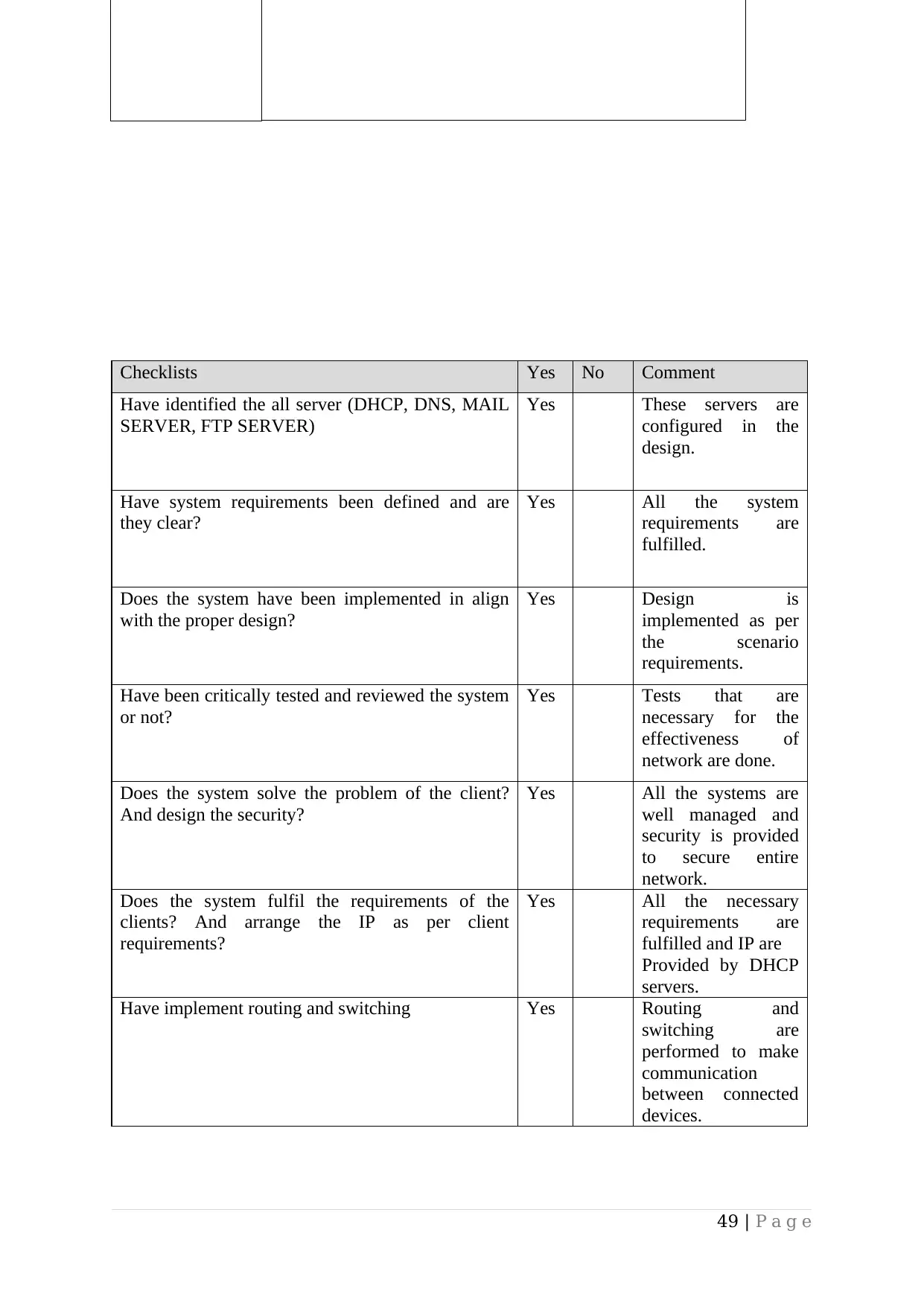
Checklists Yes No Comment
Have identified the all server (DHCP, DNS, MAIL
SERVER, FTP SERVER)
Yes These servers are
configured in the
design.
Have system requirements been defined and are
they clear?
Yes All the system
requirements are
fulfilled.
Does the system have been implemented in align
with the proper design?
Yes Design is
implemented as per
the scenario
requirements.
Have been critically tested and reviewed the system
or not?
Yes Tests that are
necessary for the
effectiveness of
network are done.
Does the system solve the problem of the client?
And design the security?
Yes All the systems are
well managed and
security is provided
to secure entire
network.
Does the system fulfil the requirements of the
clients? And arrange the IP as per client
requirements?
Yes All the necessary
requirements are
fulfilled and IP are
Provided by DHCP
servers.
Have implement routing and switching Yes Routing and
switching are
performed to make
communication
between connected
devices.
49 | P a g e
Have identified the all server (DHCP, DNS, MAIL
SERVER, FTP SERVER)
Yes These servers are
configured in the
design.
Have system requirements been defined and are
they clear?
Yes All the system
requirements are
fulfilled.
Does the system have been implemented in align
with the proper design?
Yes Design is
implemented as per
the scenario
requirements.
Have been critically tested and reviewed the system
or not?
Yes Tests that are
necessary for the
effectiveness of
network are done.
Does the system solve the problem of the client?
And design the security?
Yes All the systems are
well managed and
security is provided
to secure entire
network.
Does the system fulfil the requirements of the
clients? And arrange the IP as per client
requirements?
Yes All the necessary
requirements are
fulfilled and IP are
Provided by DHCP
servers.
Have implement routing and switching Yes Routing and
switching are
performed to make
communication
between connected
devices.
49 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Significance of the project 1) The design has well defined and manage
IP and hardware systems
2) The information can be transferred any
time within network as well as outside of
local network.
3) Duplicate user cannot be added for mail
server or hardware security is also there for
protect unauthorized access of router, switch
and servers.
4)It allows login for only the valid users
having correct user name and password.
And the admin has different authentication
than a user.
5) It supports remote management using
telnet.
6) It also supports Van, InterVlan and VPN
communication with other branches securely.
Project limitation 1) In this project there are only types of user
i.e. user and admin.
2) Without internet communication can make
within LAN outside communication cannot
be there.
3)High security like ACL, NAT, Port
security etc. are not there
4) Low range of hardware are used.
50 | P a g e
Evaluation of the system:
Design:
The network was successfully developed to meet the institute's
needs. This network system is built using hybrid topology. Two
labs, one on the first floor and the other on the second floor,
both with 25 lab computers. Aside from the computer lab, there
are three printers on the first floor. In total, 35 staff computers
are located on the third and fourth floors. In the admin room,
there are five PCs for the admin head and the head of
department. Three network administrators are also stationed on
the third floor, which explains why DNS, DHCP, and the DC
server are all located on the same floor.
The entire system is connected to a single router on the top
floor through four switches, one from each floor. To increase the
data transmission rate, two access points in a second switch and
router are linked. The router's firewall is set up to block or
prevent viruses, malware, and unwanted access from the
outside. A visitor user connects to the network over a VPN-
created secret tunnel. This design is appropriate and effective
IP and hardware systems
2) The information can be transferred any
time within network as well as outside of
local network.
3) Duplicate user cannot be added for mail
server or hardware security is also there for
protect unauthorized access of router, switch
and servers.
4)It allows login for only the valid users
having correct user name and password.
And the admin has different authentication
than a user.
5) It supports remote management using
telnet.
6) It also supports Van, InterVlan and VPN
communication with other branches securely.
Project limitation 1) In this project there are only types of user
i.e. user and admin.
2) Without internet communication can make
within LAN outside communication cannot
be there.
3)High security like ACL, NAT, Port
security etc. are not there
4) Low range of hardware are used.
50 | P a g e
Evaluation of the system:
Design:
The network was successfully developed to meet the institute's
needs. This network system is built using hybrid topology. Two
labs, one on the first floor and the other on the second floor,
both with 25 lab computers. Aside from the computer lab, there
are three printers on the first floor. In total, 35 staff computers
are located on the third and fourth floors. In the admin room,
there are five PCs for the admin head and the head of
department. Three network administrators are also stationed on
the third floor, which explains why DNS, DHCP, and the DC
server are all located on the same floor.
The entire system is connected to a single router on the top
floor through four switches, one from each floor. To increase the
data transmission rate, two access points in a second switch and
router are linked. The router's firewall is set up to block or
prevent viruses, malware, and unwanted access from the
outside. A visitor user connects to the network over a VPN-
created secret tunnel. This design is appropriate and effective

Test log:
S.N What is to be tested Expected output
1. DHCP Testing With the help of DHCP server, the IP address will be assigned
automatically in all connected devices.
51 | P a g e
Recommendations for future consideration:
Despite the fact that the developed network is appropriate for the
educational institute's circumstance. However, by removing some of
the constraints indicated in this feedback form, it can be made more
effective. Expensive and high-configure gear can be used because it
is faster and more productive. Similarly, NAT and port security can
be adjusted to increase the security of the entire network. Many
S.N What is to be tested Expected output
1. DHCP Testing With the help of DHCP server, the IP address will be assigned
automatically in all connected devices.
51 | P a g e
Recommendations for future consideration:
Despite the fact that the developed network is appropriate for the
educational institute's circumstance. However, by removing some of
the constraints indicated in this feedback form, it can be made more
effective. Expensive and high-configure gear can be used because it
is faster and more productive. Similarly, NAT and port security can
be adjusted to increase the security of the entire network. Many
2. DNS Testing Web Page can be accessed.
3. Email Testing Email can be sent from source to destination.
4. Telnet Testing Administrator should access other’s PC remotely.
5. Routing Testing Ping can be performed from one computer to another computer.
6. VPN Testing Built a secure connection.
7. Firewall Testing Denied network can’t access internal network.
8. Domain Controller
Testing
Other domain can only share resources within the network while
authorized member can use all the services of that educational institute
within that network.
Implement a networked system based on a prepared design.
Group work
Network design
52 | P a g e
3. Email Testing Email can be sent from source to destination.
4. Telnet Testing Administrator should access other’s PC remotely.
5. Routing Testing Ping can be performed from one computer to another computer.
6. VPN Testing Built a secure connection.
7. Firewall Testing Denied network can’t access internal network.
8. Domain Controller
Testing
Other domain can only share resources within the network while
authorized member can use all the services of that educational institute
within that network.
Implement a networked system based on a prepared design.
Group work
Network design
52 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
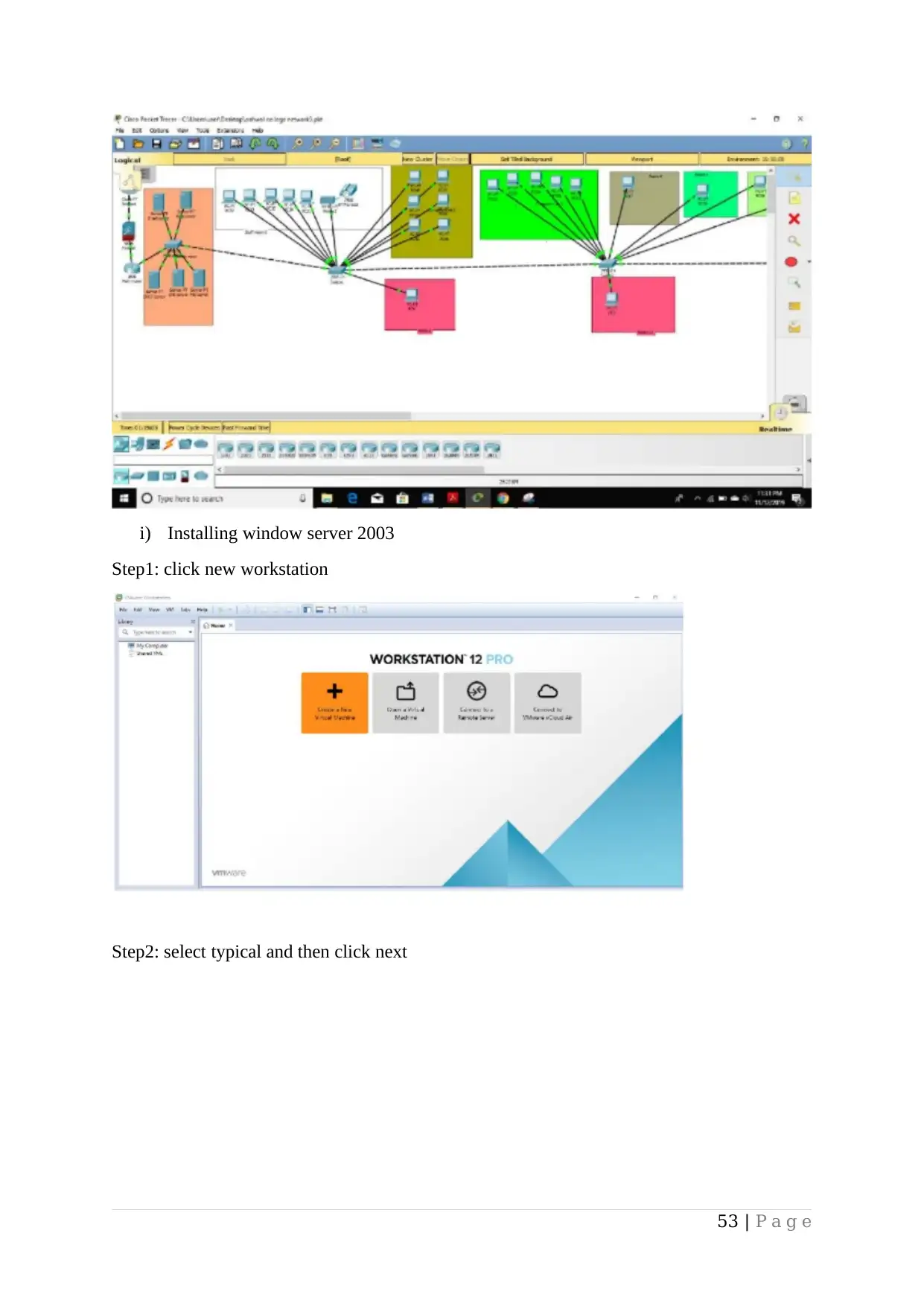
i) Installing window server 2003
Step1: click new workstation
Step2: select typical and then click next
53 | P a g e
Step1: click new workstation
Step2: select typical and then click next
53 | P a g e
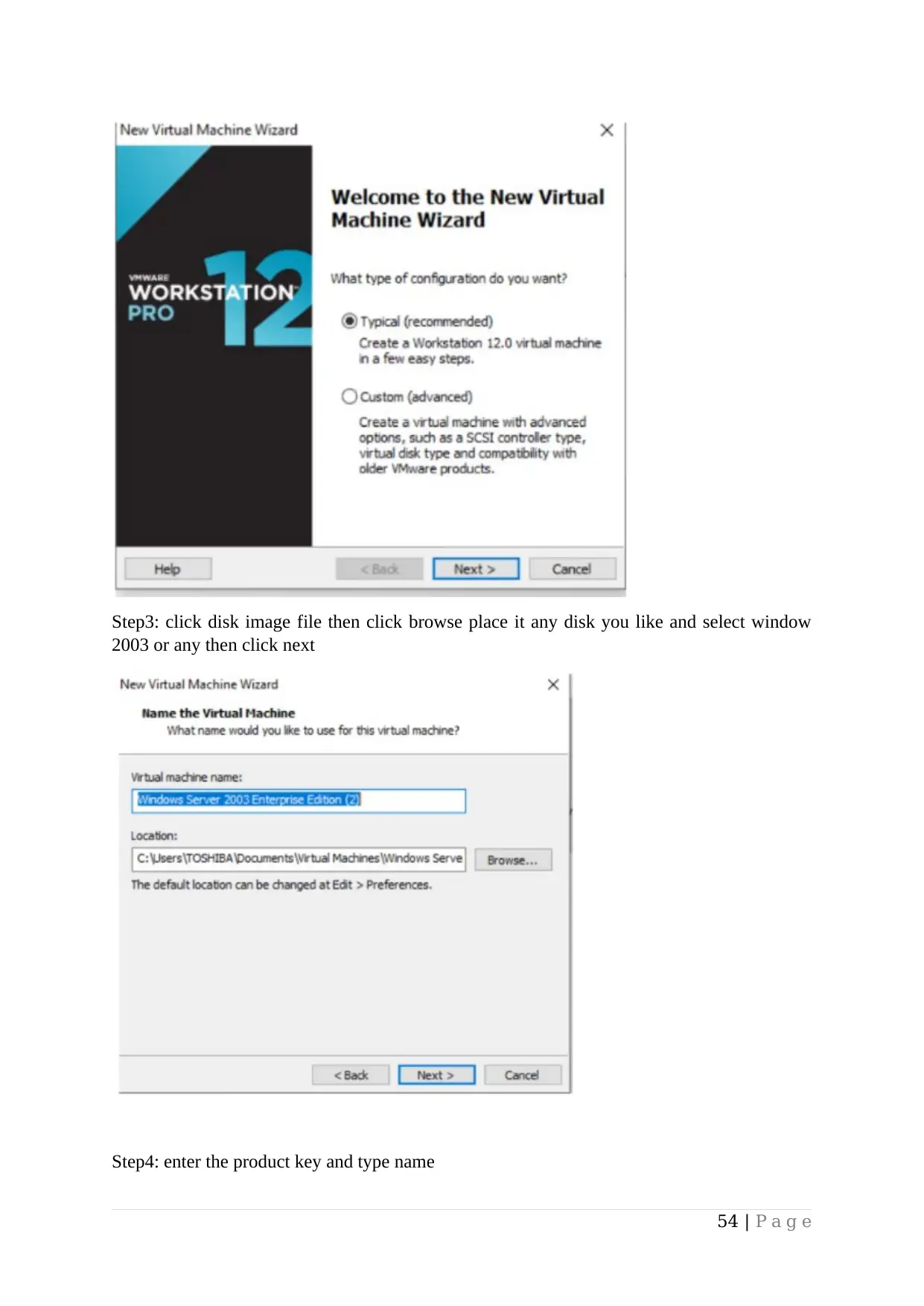
Step3: click disk image file then click browse place it any disk you like and select window
2003 or any then click next
Step4: enter the product key and type name
54 | P a g e
2003 or any then click next
Step4: enter the product key and type name
54 | P a g e
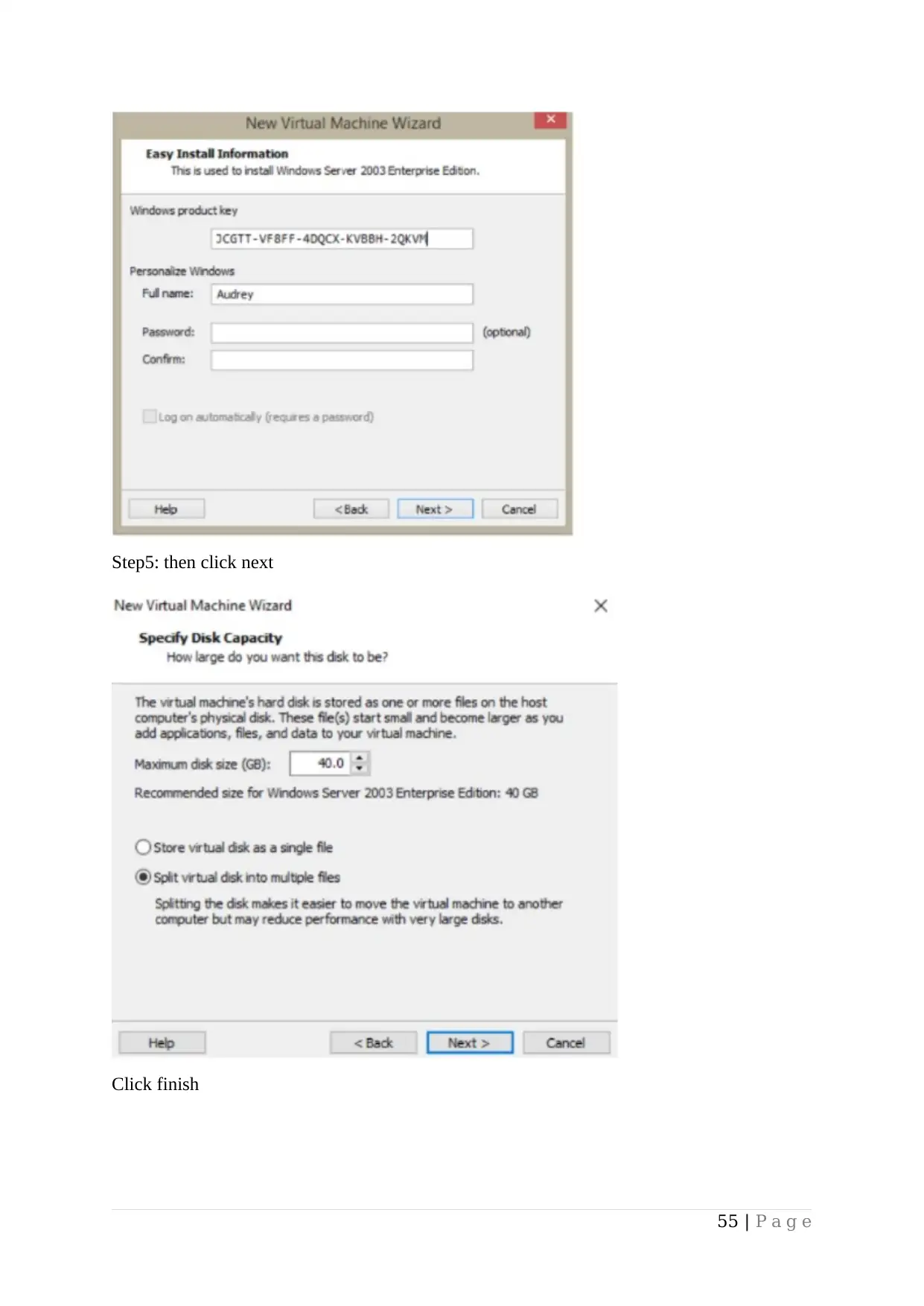
Step5: then click next
Click finish
55 | P a g e
Click finish
55 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
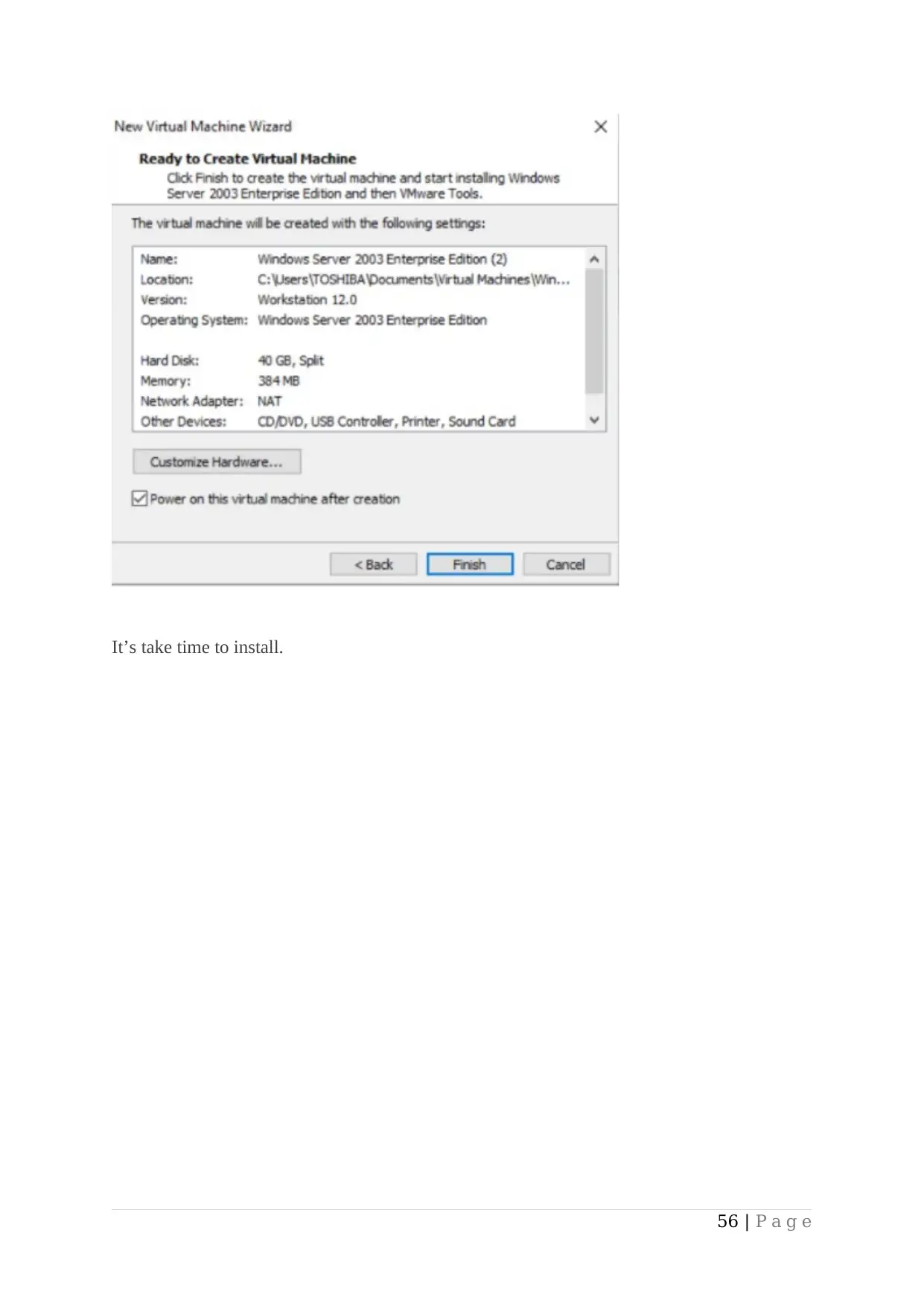
It’s take time to install.
56 | P a g e
56 | P a g e
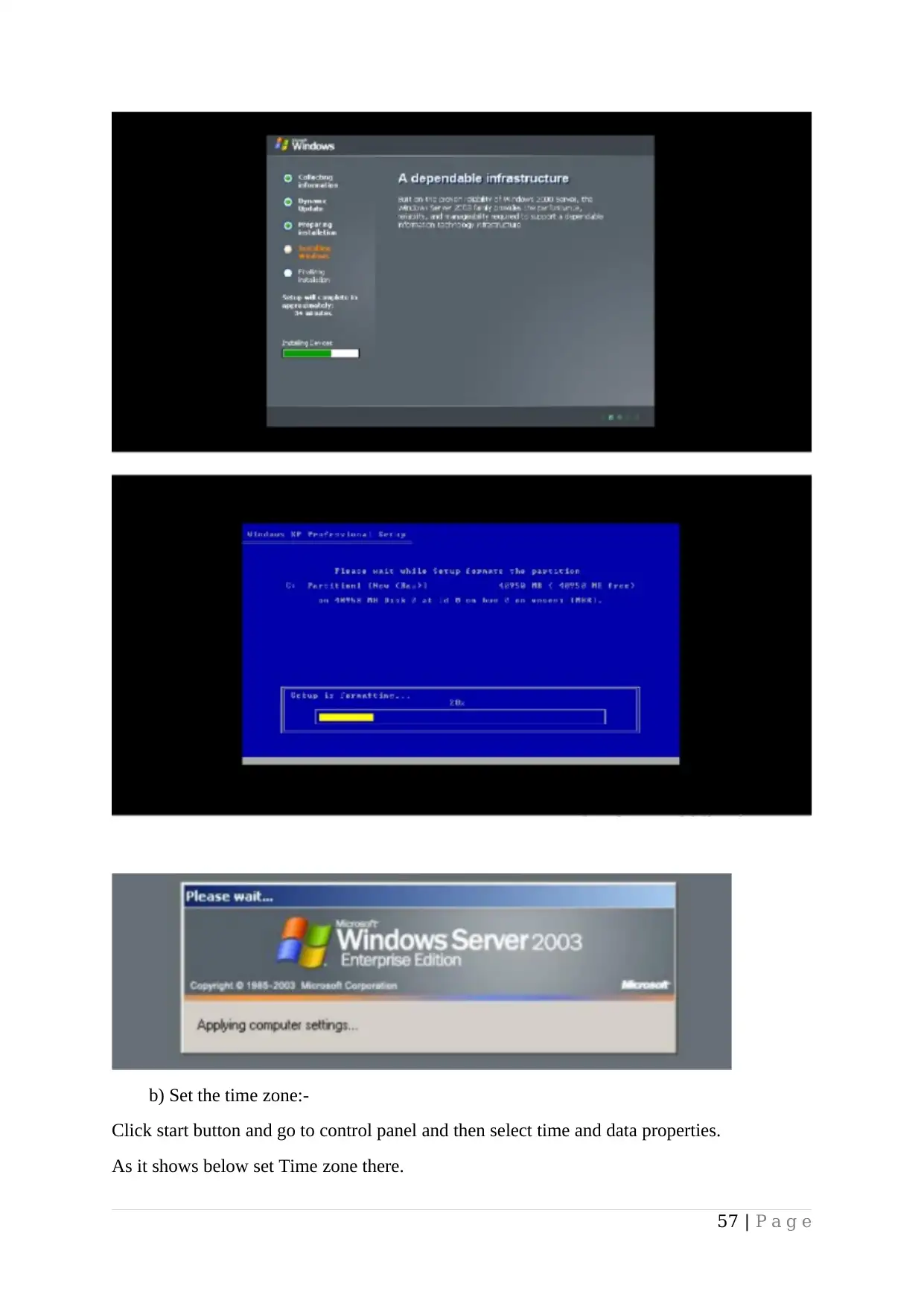
b) Set the time zone:-
Click start button and go to control panel and then select time and data properties.
As it shows below set Time zone there.
57 | P a g e
Click start button and go to control panel and then select time and data properties.
As it shows below set Time zone there.
57 | P a g e
c) Configuring network adapter
Click start and go to the control panel.
Then go to network connections then Local Area Connection and go to the properties.
Click Internet protocol TCP/TP then click on properties again.
58 | P a g e
Click start and go to the control panel.
Then go to network connections then Local Area Connection and go to the properties.
Click Internet protocol TCP/TP then click on properties again.
58 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Enter IP address.
d) Installing active directory.
Click start button and then click run then enter Dcpromo.
Click next.
59 | P a g e
d) Installing active directory.
Click start button and then click run then enter Dcpromo.
Click next.
59 | P a g e
Create the domain.
Enter domain and click next.
60 | P a g e
Enter domain and click next.
60 | P a g e
As it show below the screenshot that active directory is installed.
e) Installing DNS server.
Click added or remove role then click DNS server then next and after that enter Zone name
Natan.
61 | P a g e
e) Installing DNS server.
Click added or remove role then click DNS server then next and after that enter Zone name
Natan.
61 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
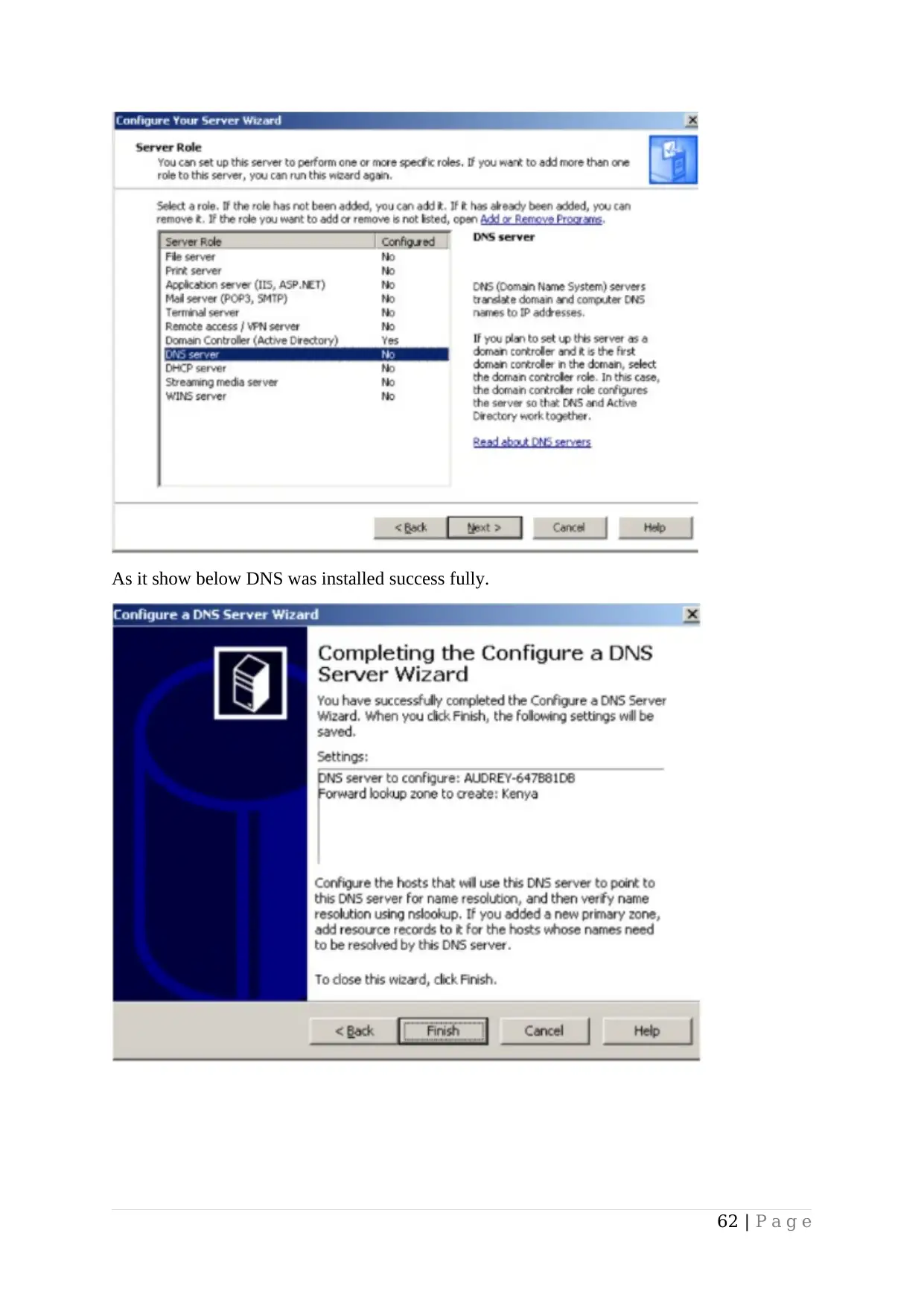
As it show below DNS was installed success fully.
62 | P a g e
62 | P a g e
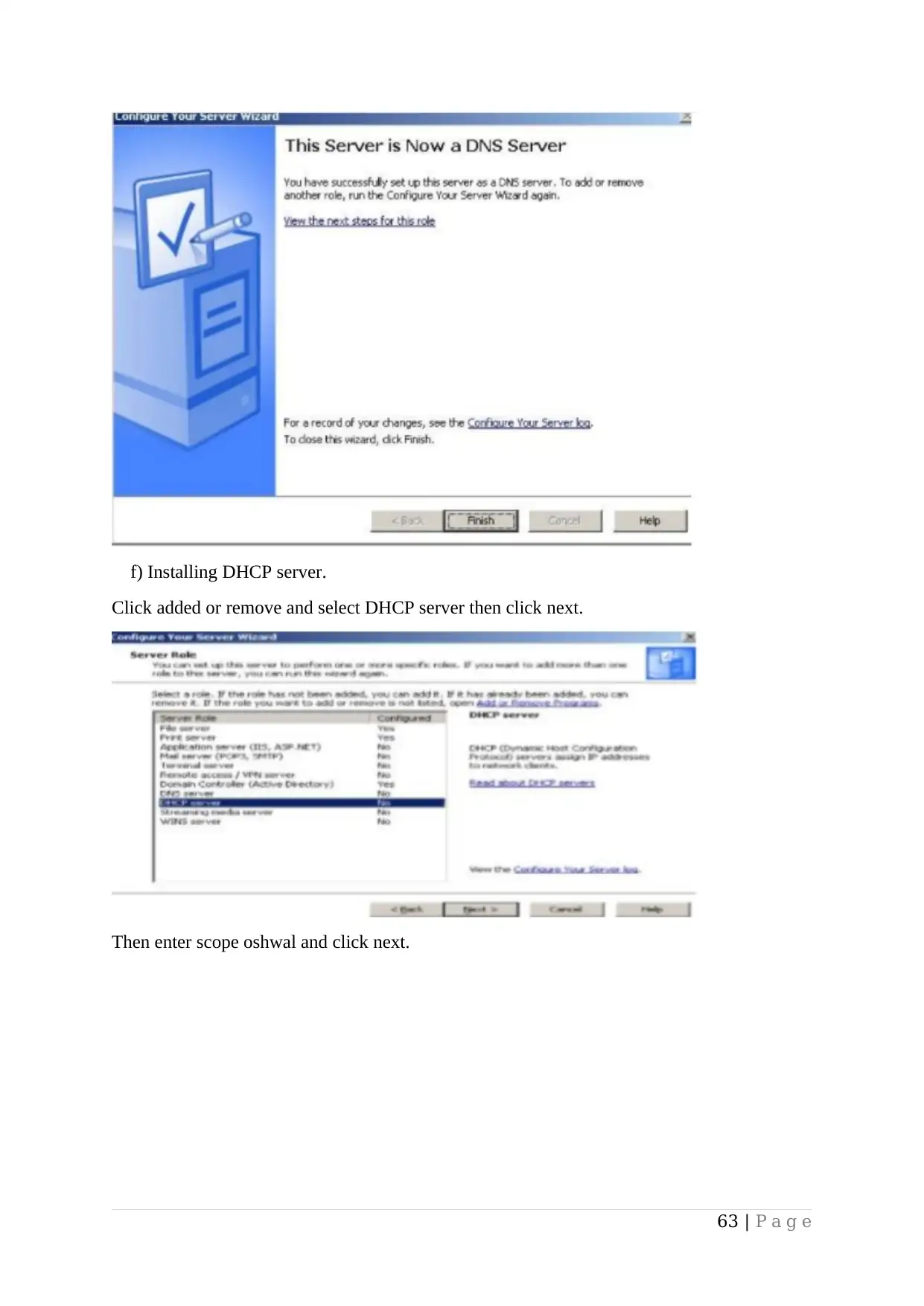
f) Installing DHCP server.
Click added or remove and select DHCP server then click next.
Then enter scope oshwal and click next.
63 | P a g e
Click added or remove and select DHCP server then click next.
Then enter scope oshwal and click next.
63 | P a g e
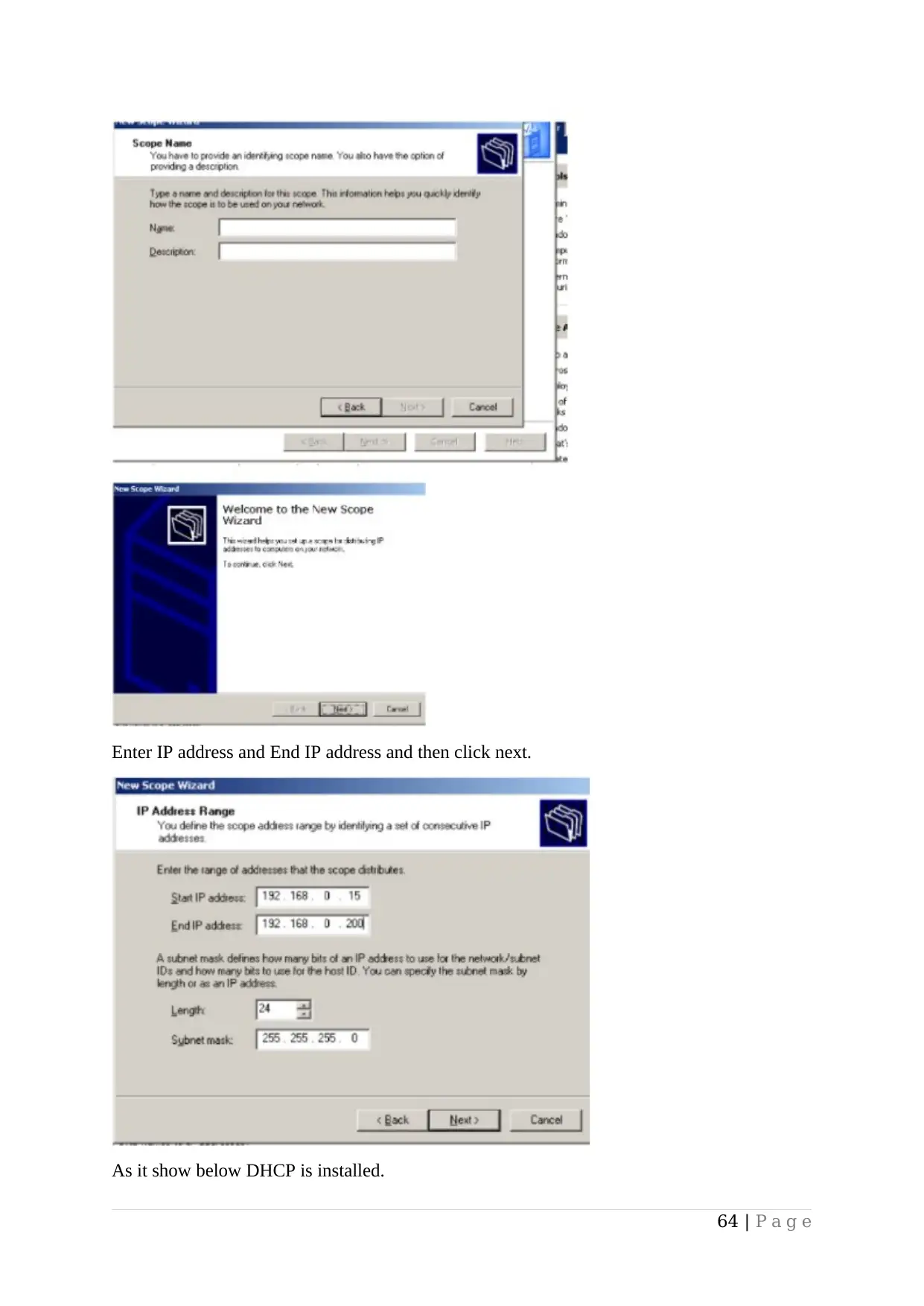
Enter IP address and End IP address and then click next.
As it show below DHCP is installed.
64 | P a g e
As it show below DHCP is installed.
64 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
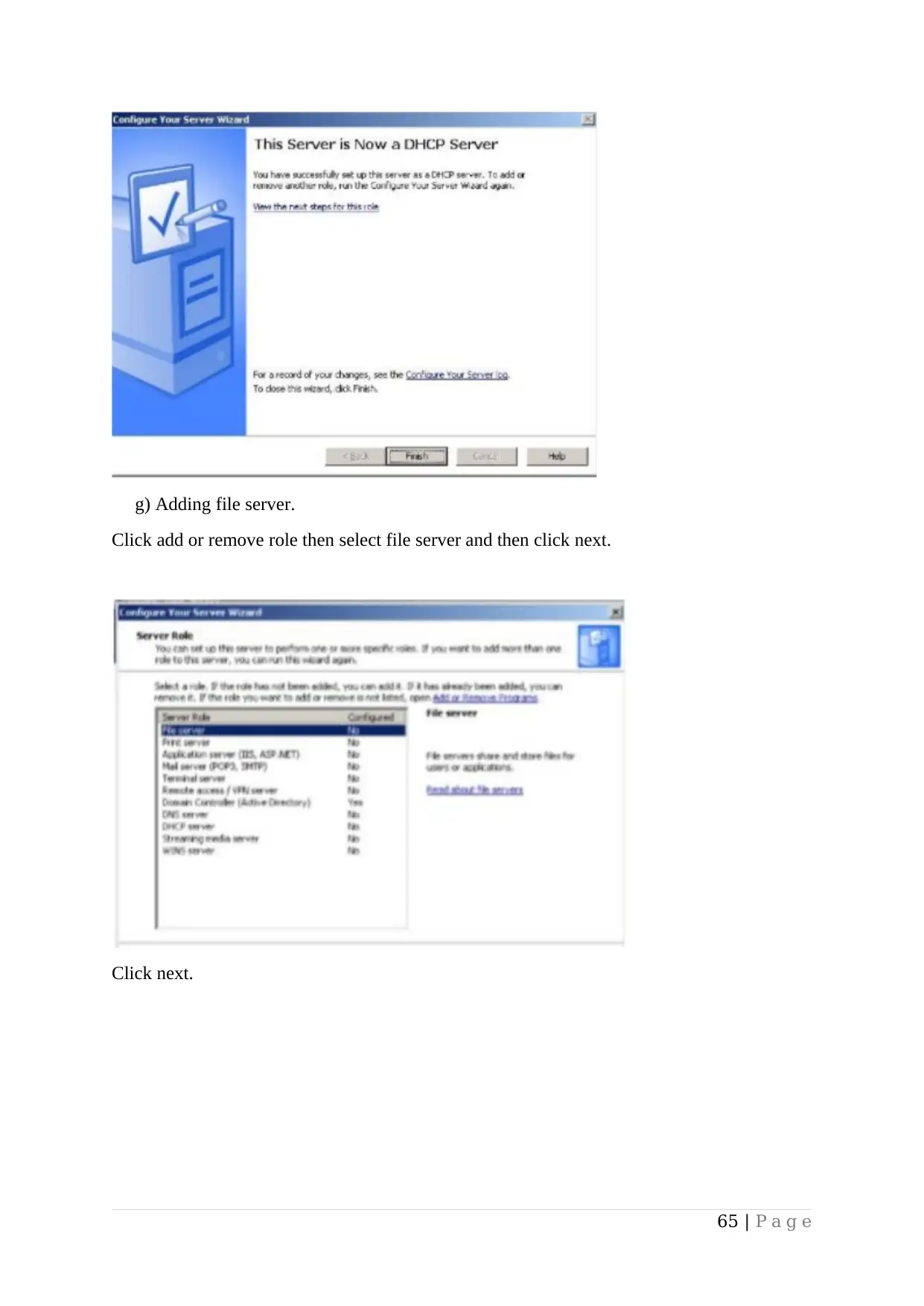
g) Adding file server.
Click add or remove role then select file server and then click next.
Click next.
65 | P a g e
Click add or remove role then select file server and then click next.
Click next.
65 | P a g e
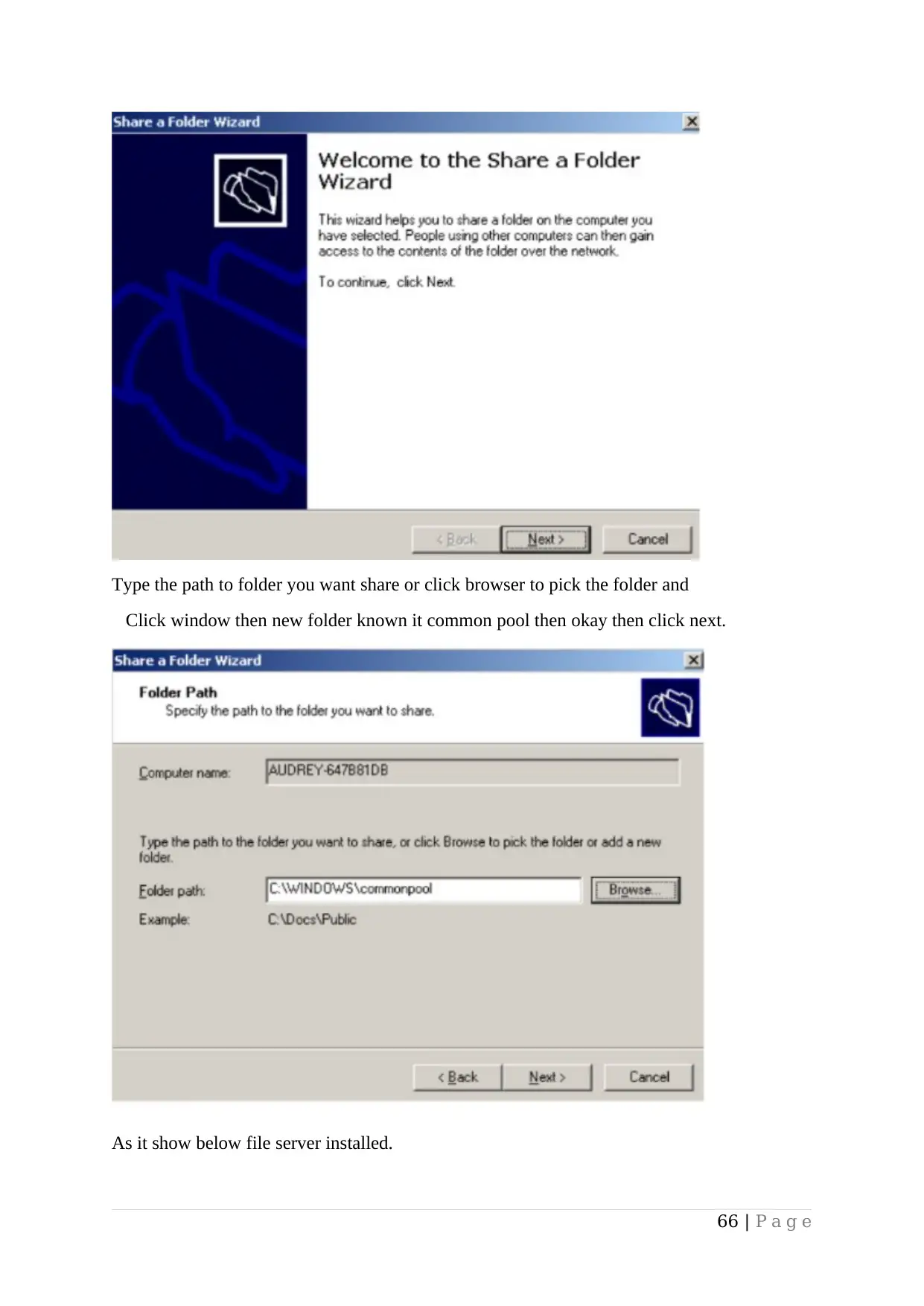
Type the path to folder you want share or click browser to pick the folder and
Click window then new folder known it common pool then okay then click next.
As it show below file server installed.
66 | P a g e
Click window then new folder known it common pool then okay then click next.
As it show below file server installed.
66 | P a g e
h) Adding groups in active Directory.
This will allow the ISMT College to manage their students
In order to add groups in AD step one Manage user and computer click and then ISMT.lan
then click user the right click on user.
The new group.
67 | P a g e
This will allow the ISMT College to manage their students
In order to add groups in AD step one Manage user and computer click and then ISMT.lan
then click user the right click on user.
The new group.
67 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
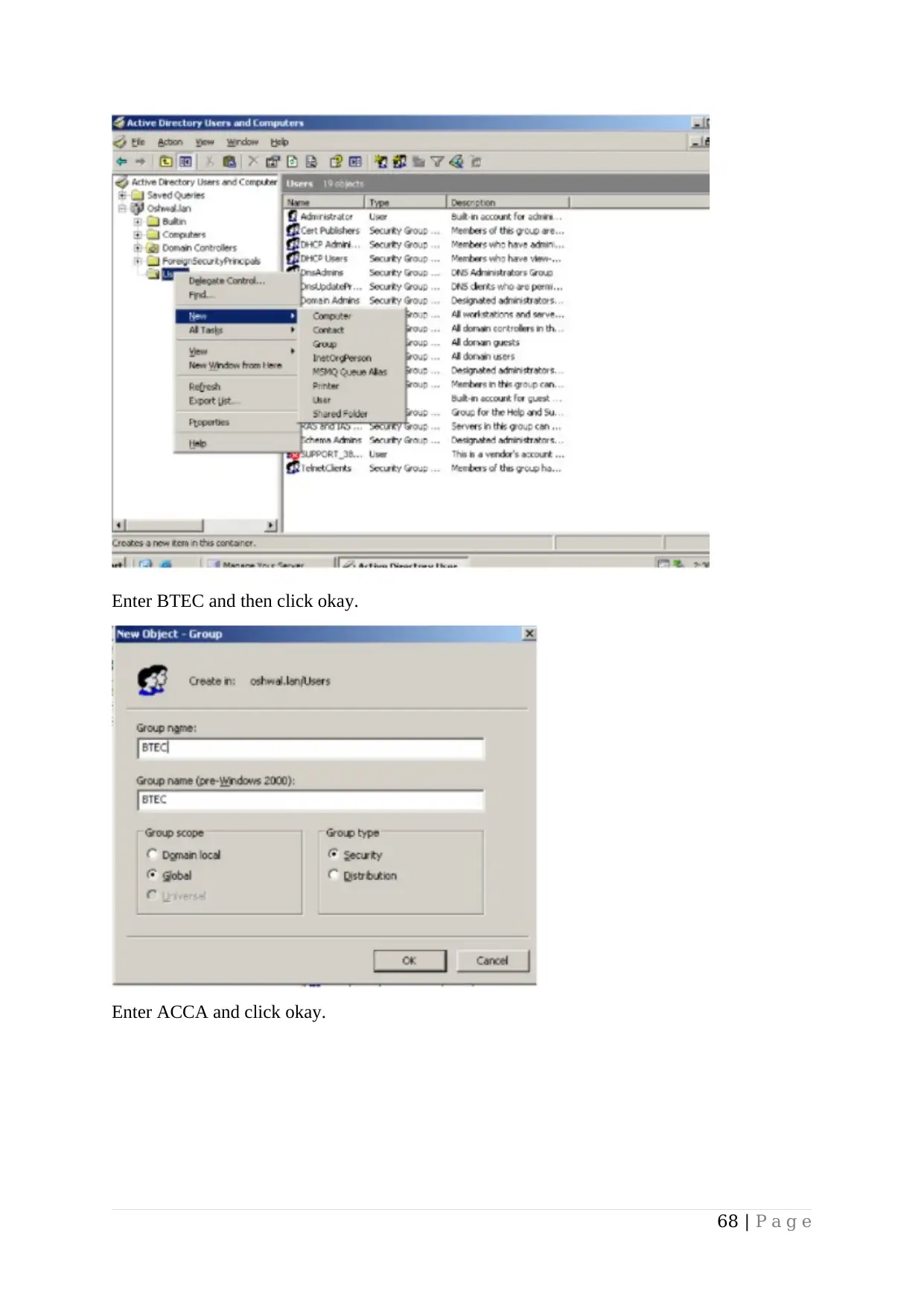
Enter BTEC and then click okay.
Enter ACCA and click okay.
68 | P a g e
Enter ACCA and click okay.
68 | P a g e
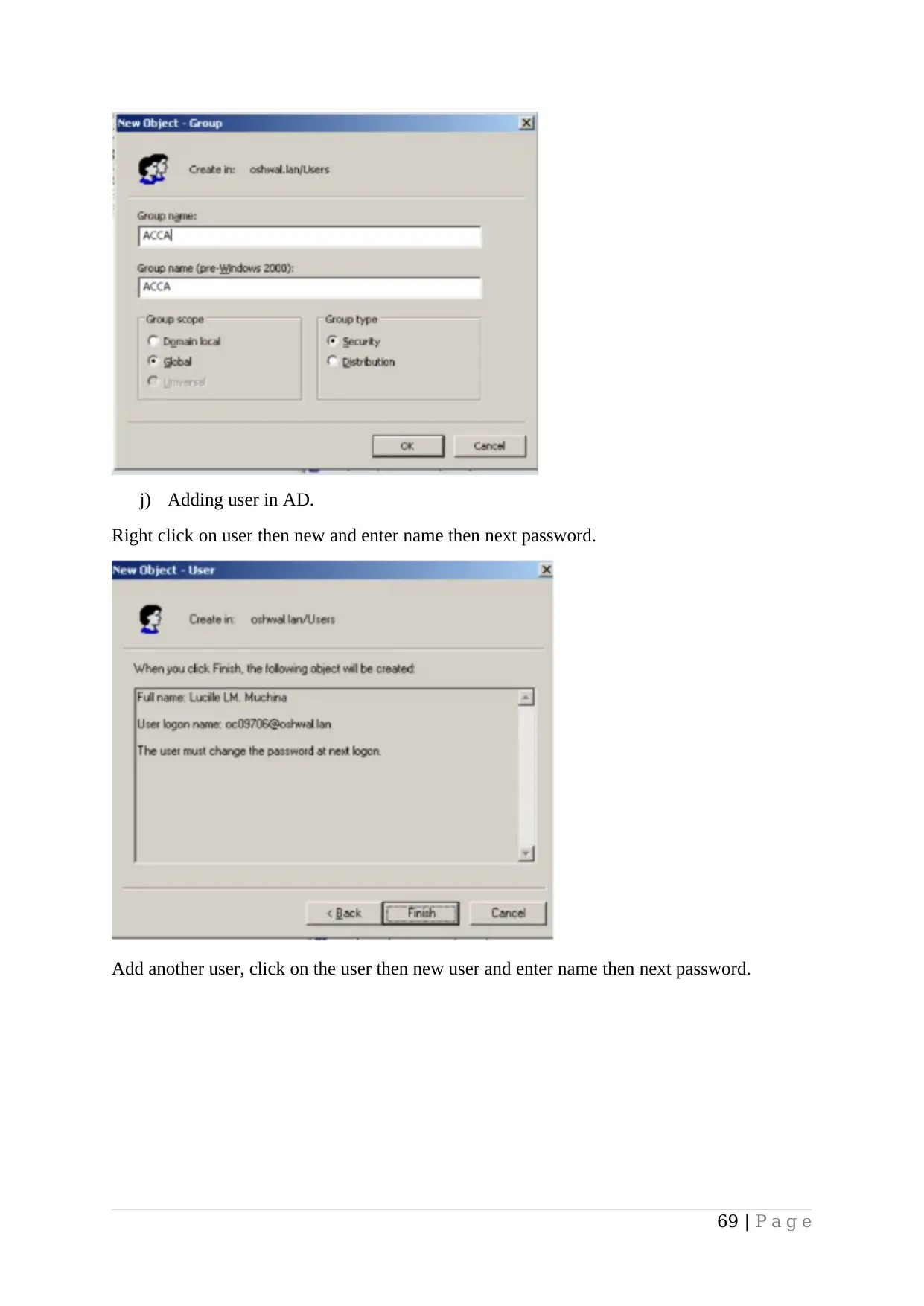
j) Adding user in AD.
Right click on user then new and enter name then next password.
Add another user, click on the user then new user and enter name then next password.
69 | P a g e
Right click on user then new and enter name then next password.
Add another user, click on the user then new user and enter name then next password.
69 | P a g e
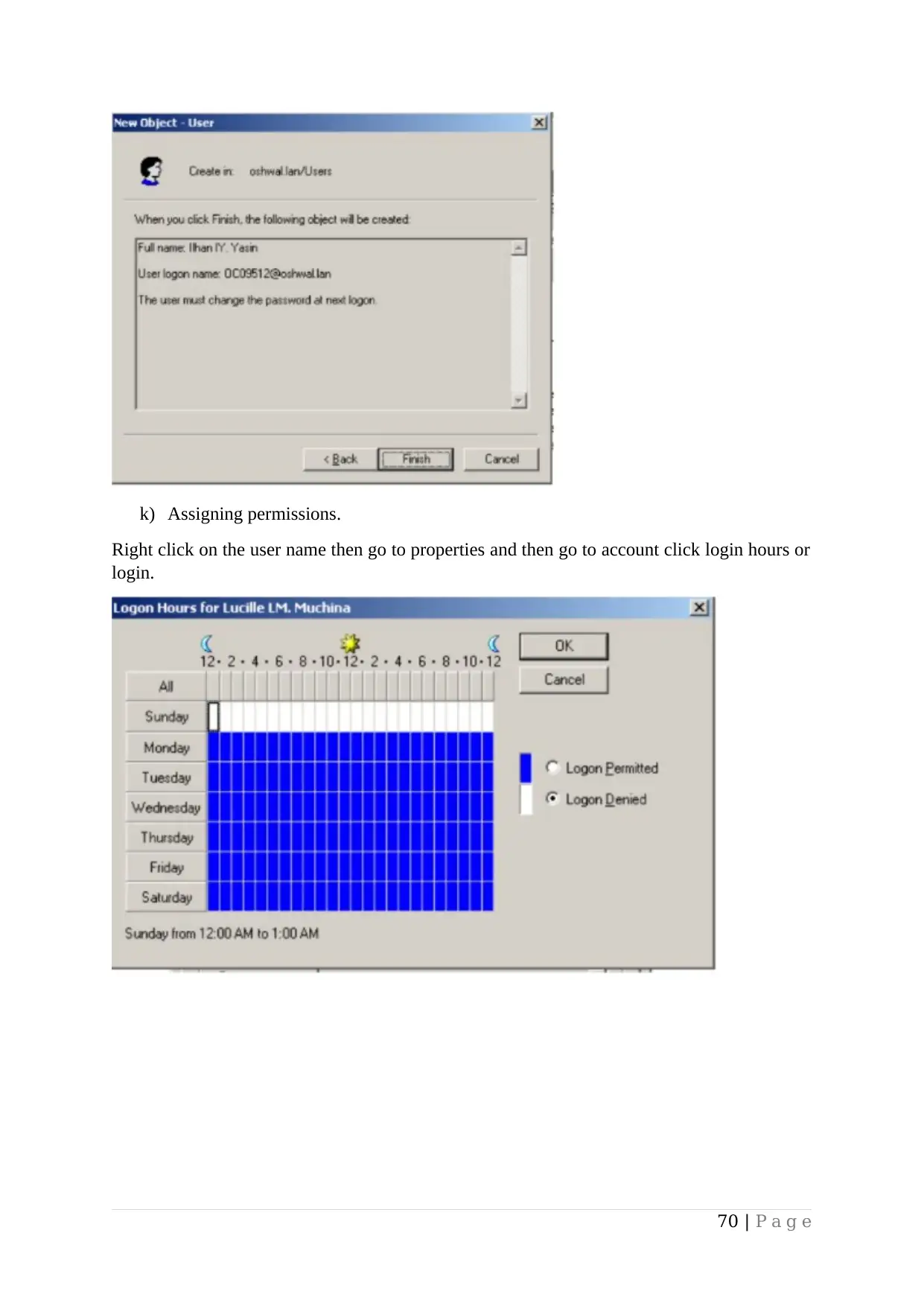
k) Assigning permissions.
Right click on the user name then go to properties and then go to account click login hours or
login.
70 | P a g e
Right click on the user name then go to properties and then go to account click login hours or
login.
70 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
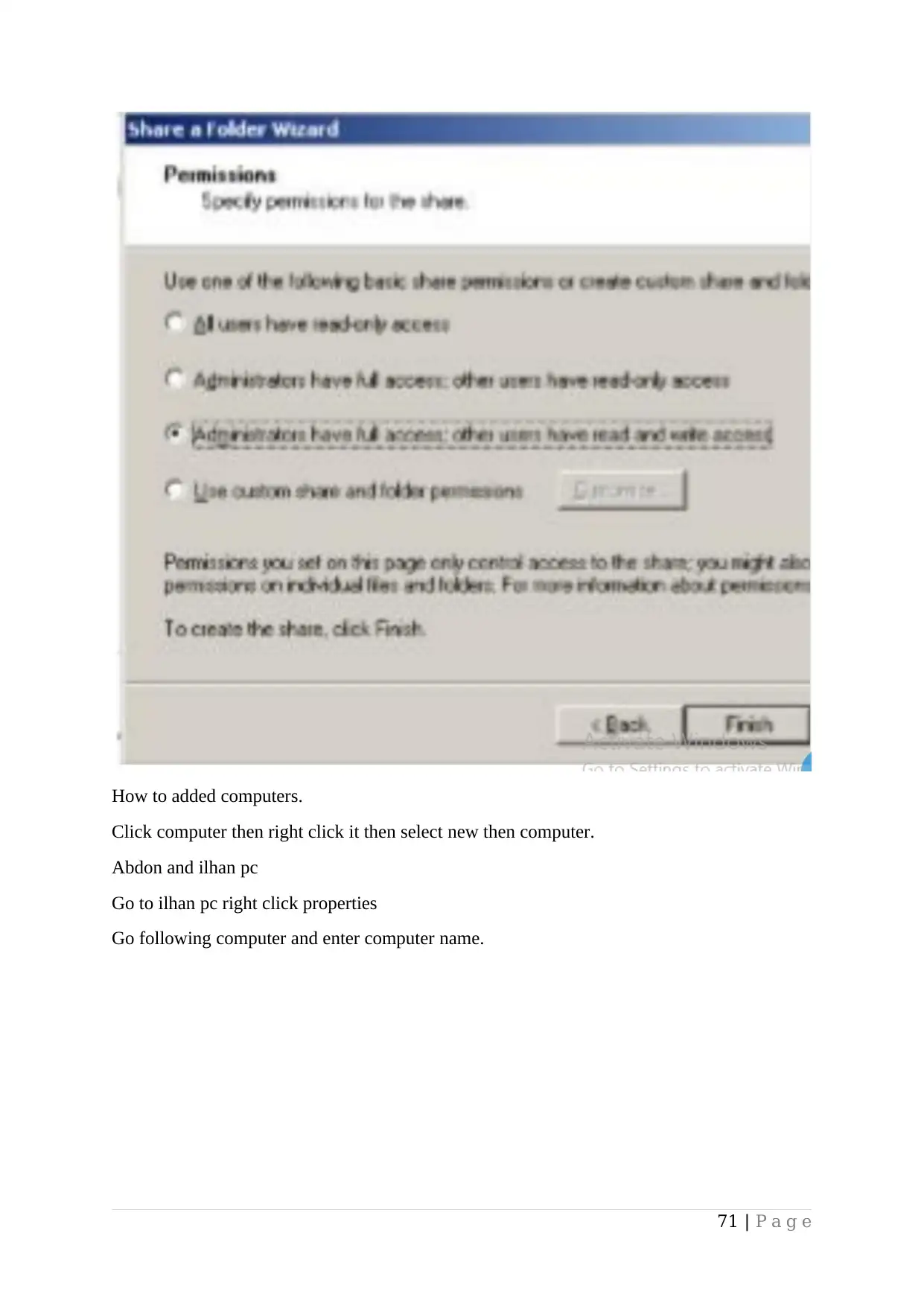
How to added computers.
Click computer then right click it then select new then computer.
Abdon and ilhan pc
Go to ilhan pc right click properties
Go following computer and enter computer name.
71 | P a g e
Click computer then right click it then select new then computer.
Abdon and ilhan pc
Go to ilhan pc right click properties
Go following computer and enter computer name.
71 | P a g e
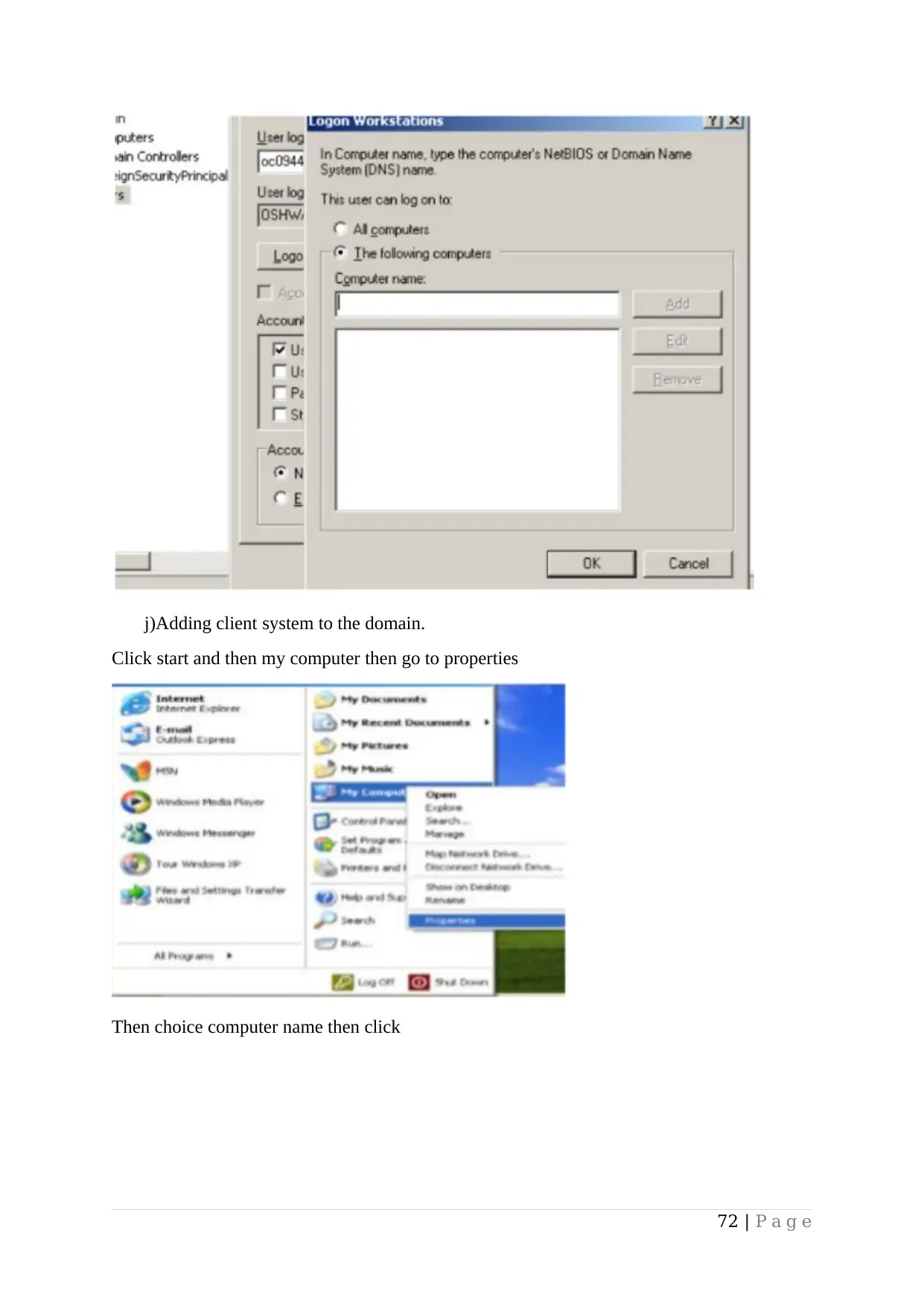
j)Adding client system to the domain.
Click start and then my computer then go to properties
Then choice computer name then click
72 | P a g e
Click start and then my computer then go to properties
Then choice computer name then click
72 | P a g e
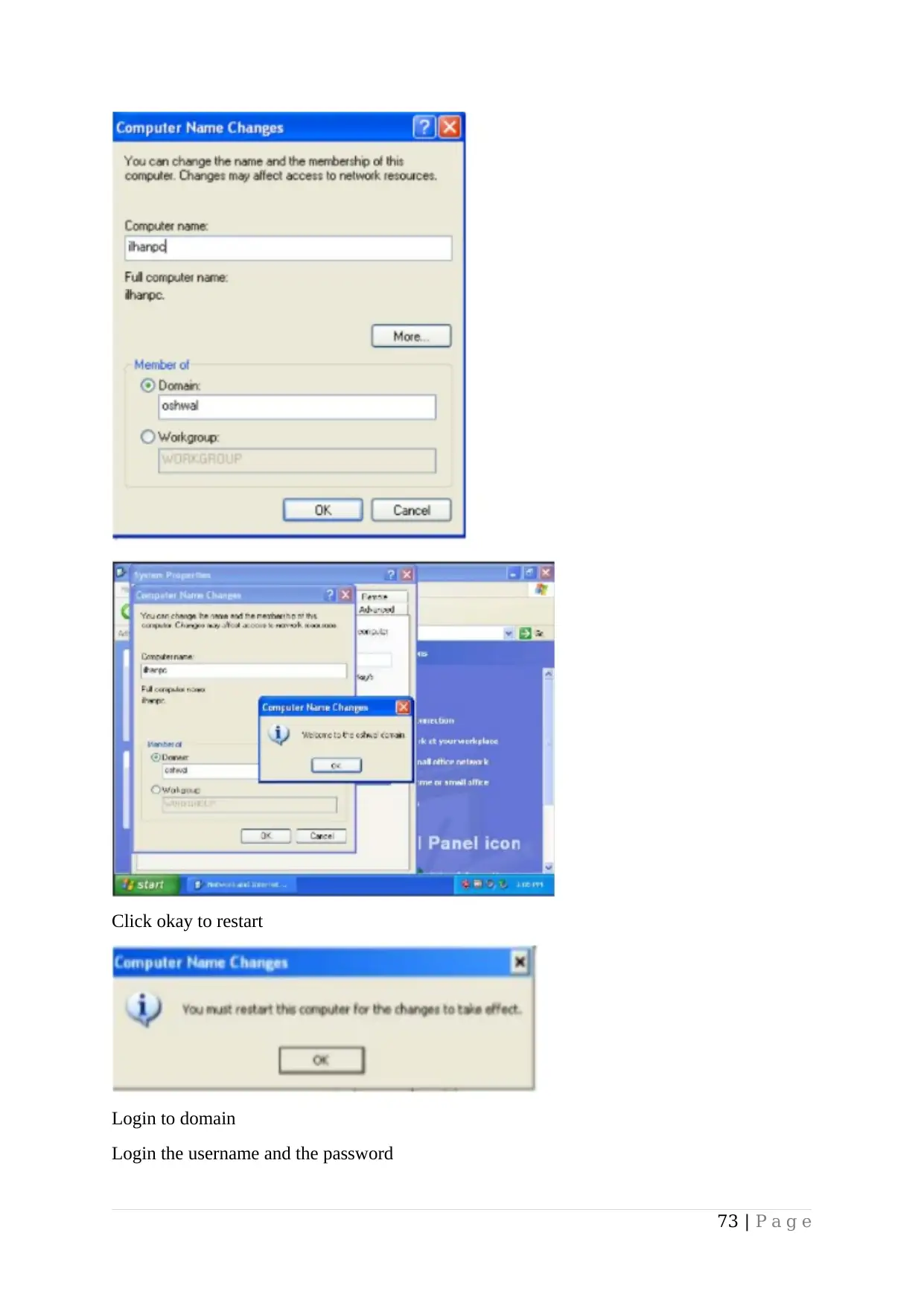
Click okay to restart
Login to domain
Login the username and the password
73 | P a g e
Login to domain
Login the username and the password
73 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
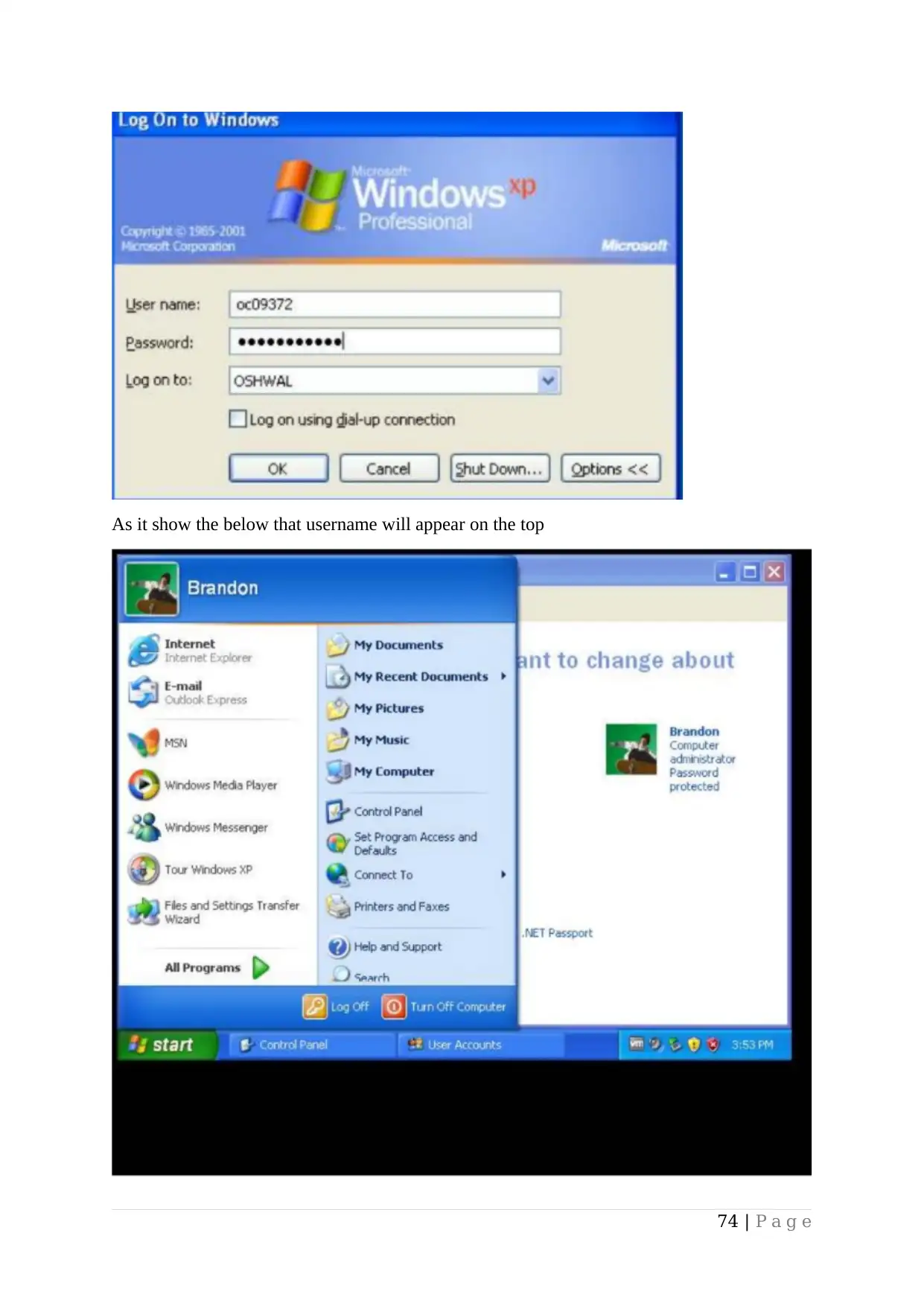
As it show the below that username will appear on the top
74 | P a g e
74 | P a g e
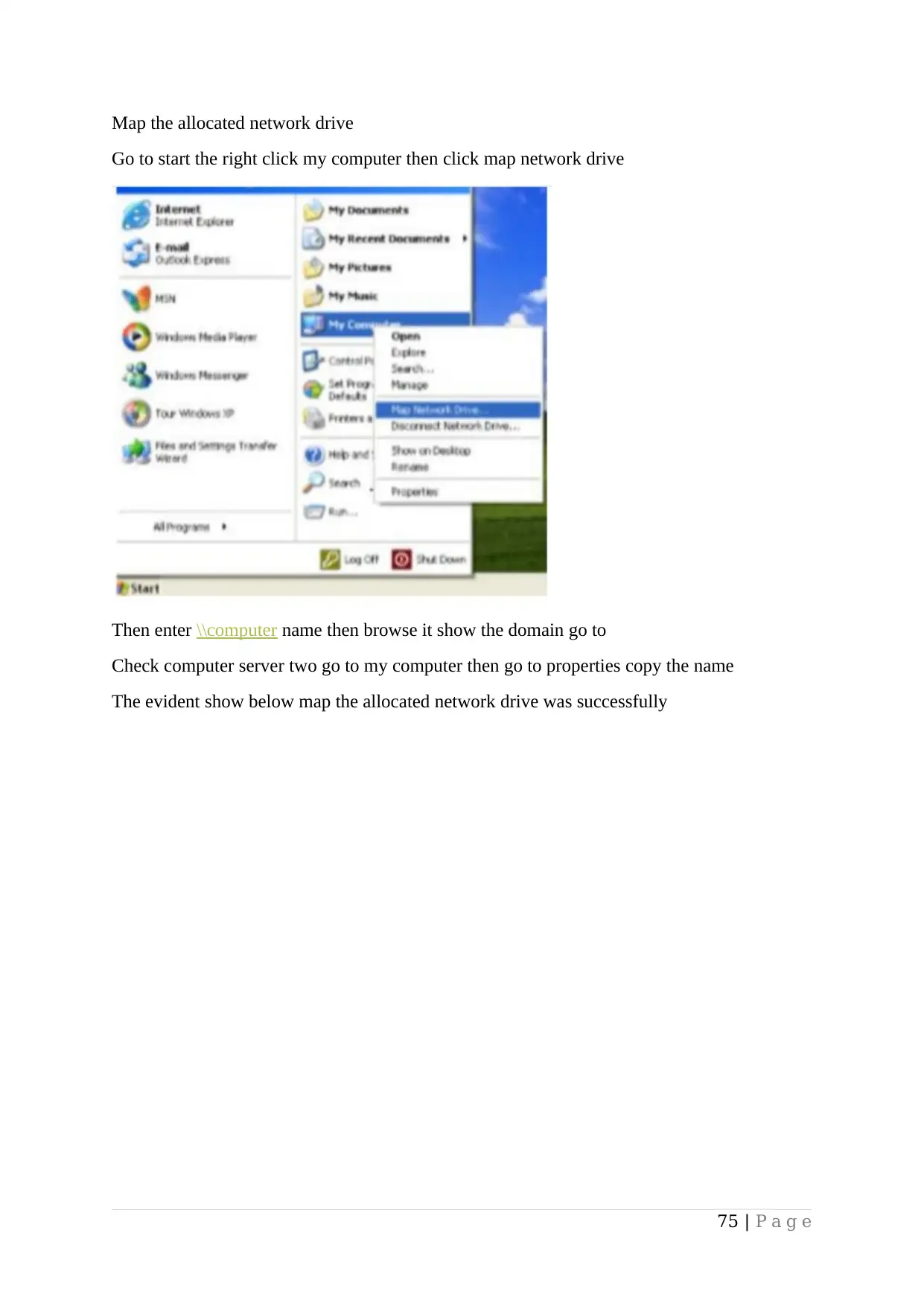
Map the allocated network drive
Go to start the right click my computer then click map network drive
Then enter \\computer name then browse it show the domain go to
Check computer server two go to my computer then go to properties copy the name
The evident show below map the allocated network drive was successfully
75 | P a g e
Go to start the right click my computer then click map network drive
Then enter \\computer name then browse it show the domain go to
Check computer server two go to my computer then go to properties copy the name
The evident show below map the allocated network drive was successfully
75 | P a g e
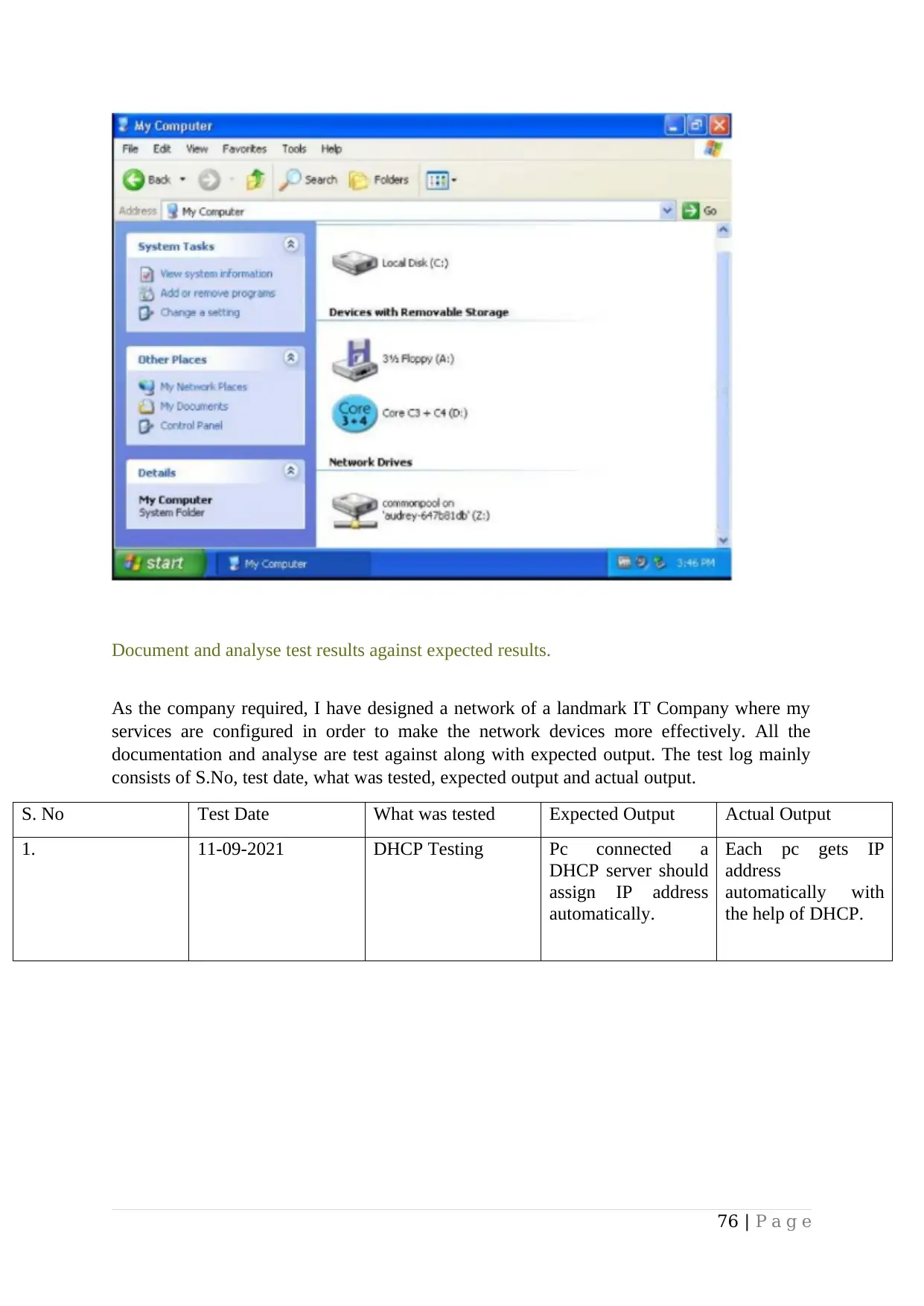
Document and analyse test results against expected results.
As the company required, I have designed a network of a landmark IT Company where my
services are configured in order to make the network devices more effectively. All the
documentation and analyse are test against along with expected output. The test log mainly
consists of S.No, test date, what was tested, expected output and actual output.
S. No Test Date What was tested Expected Output Actual Output
1. 11-09-2021 DHCP Testing Pc connected a
DHCP server should
assign IP address
automatically.
Each pc gets IP
address
automatically with
the help of DHCP.
76 | P a g e
As the company required, I have designed a network of a landmark IT Company where my
services are configured in order to make the network devices more effectively. All the
documentation and analyse are test against along with expected output. The test log mainly
consists of S.No, test date, what was tested, expected output and actual output.
S. No Test Date What was tested Expected Output Actual Output
1. 11-09-2021 DHCP Testing Pc connected a
DHCP server should
assign IP address
automatically.
Each pc gets IP
address
automatically with
the help of DHCP.
76 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
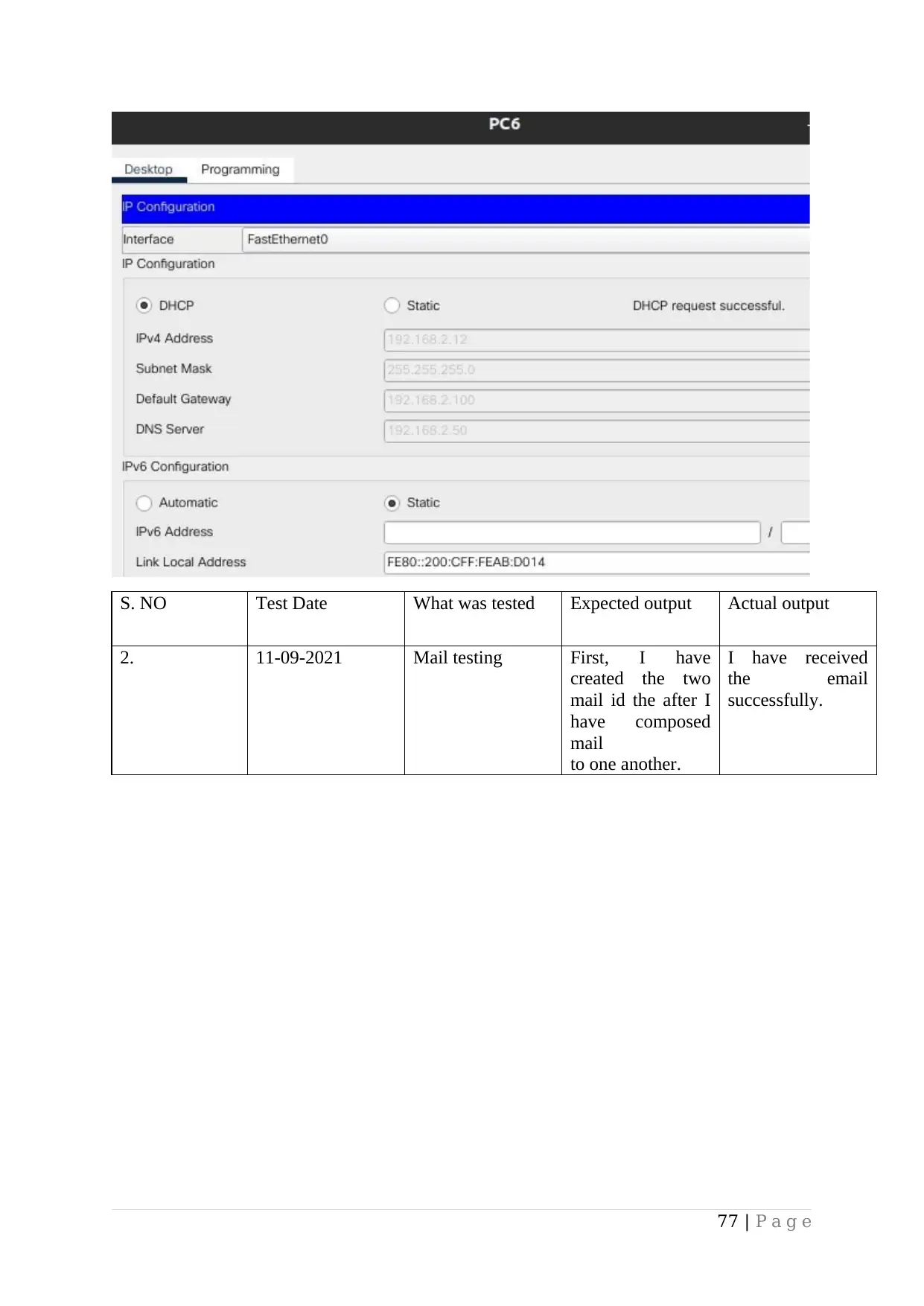
S. NO Test Date What was tested Expected output Actual output
2. 11-09-2021 Mail testing First, I have
created the two
mail id the after I
have composed
mail
to one another.
I have received
the email
successfully.
77 | P a g e
2. 11-09-2021 Mail testing First, I have
created the two
mail id the after I
have composed
to one another.
I have received
the email
successfully.
77 | P a g e
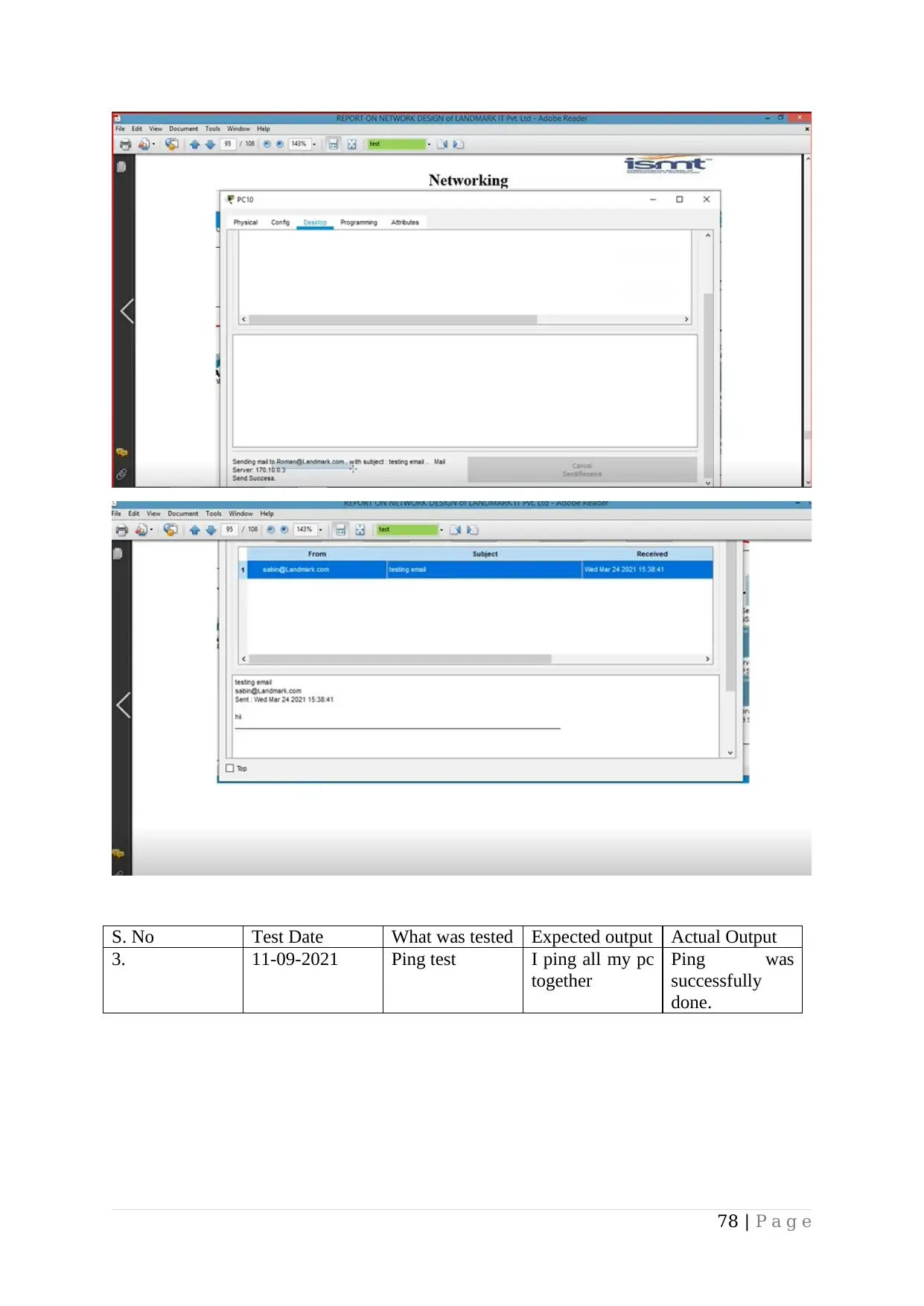
S. No Test Date What was tested Expected output Actual Output
3. 11-09-2021 Ping test I ping all my pc
together
Ping was
successfully
done.
78 | P a g e
3. 11-09-2021 Ping test I ping all my pc
together
Ping was
successfully
done.
78 | P a g e
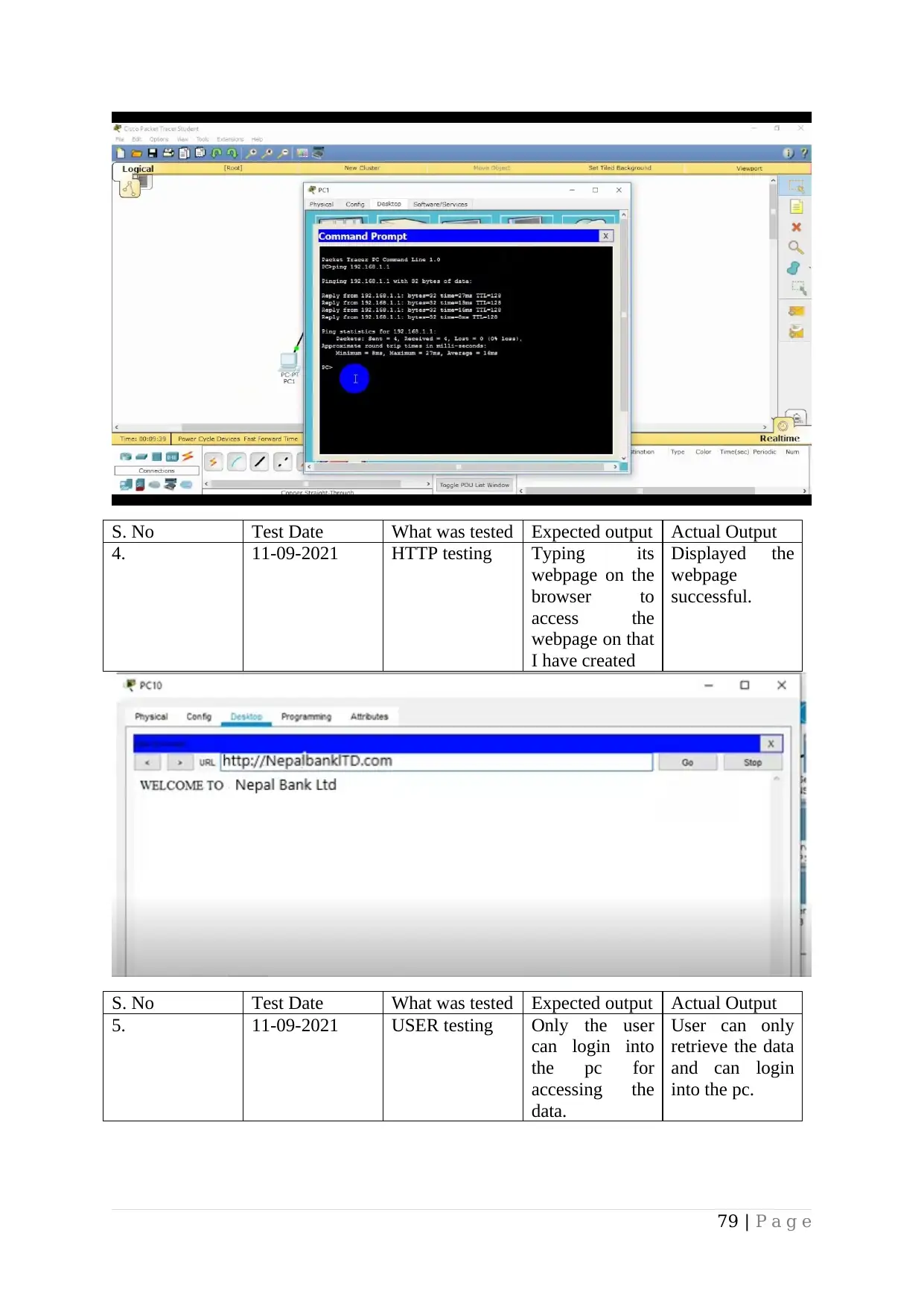
S. No Test Date What was tested Expected output Actual Output
4. 11-09-2021 HTTP testing Typing its
webpage on the
browser to
access the
webpage on that
I have created
Displayed the
webpage
successful.
S. No Test Date What was tested Expected output Actual Output
5. 11-09-2021 USER testing Only the user
can login into
the pc for
accessing the
data.
User can only
retrieve the data
and can login
into the pc.
79 | P a g e
4. 11-09-2021 HTTP testing Typing its
webpage on the
browser to
access the
webpage on that
I have created
Displayed the
webpage
successful.
S. No Test Date What was tested Expected output Actual Output
5. 11-09-2021 USER testing Only the user
can login into
the pc for
accessing the
data.
User can only
retrieve the data
and can login
into the pc.
79 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
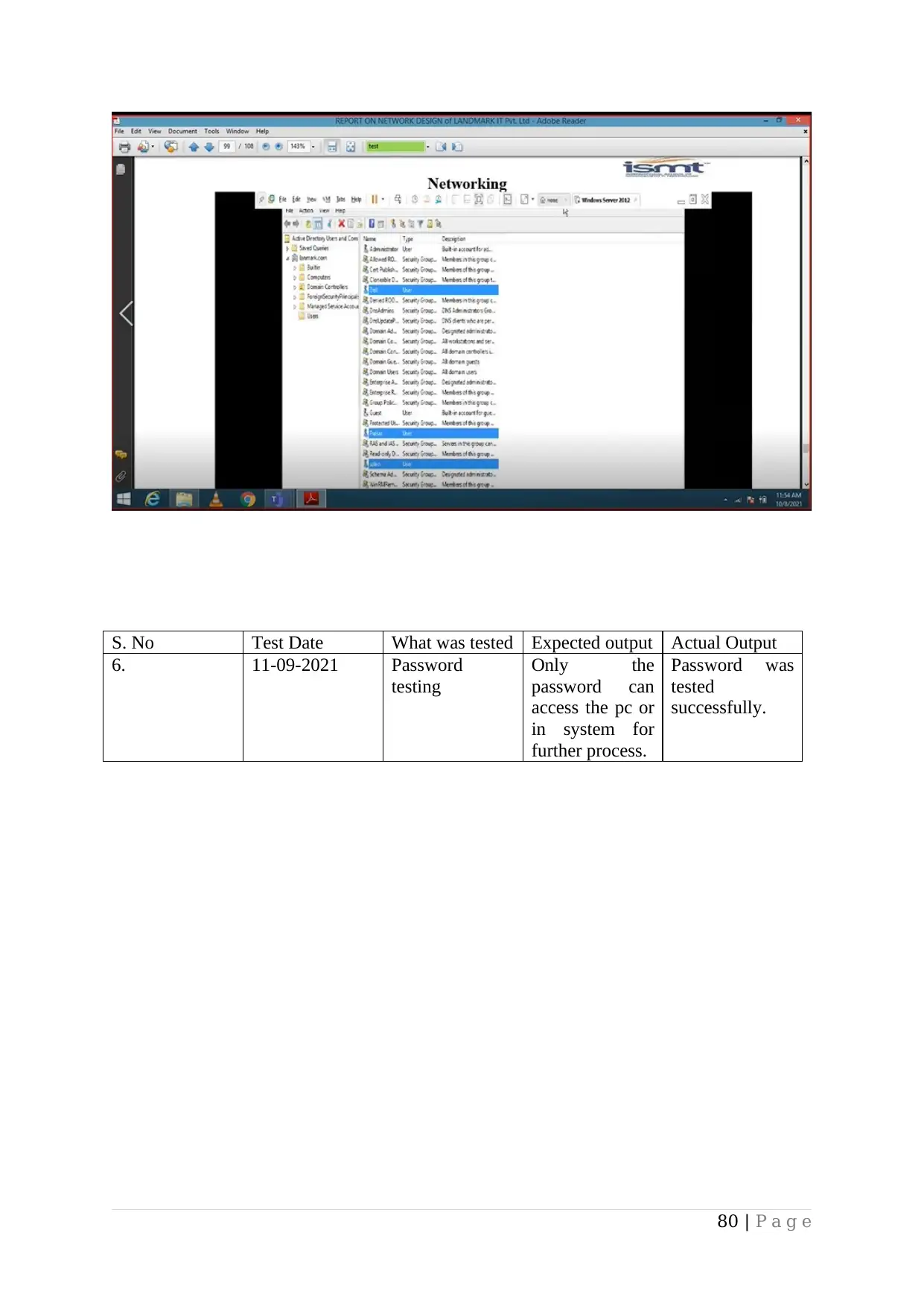
S. No Test Date What was tested Expected output Actual Output
6. 11-09-2021 Password
testing
Only the
password can
access the pc or
in system for
further process.
Password was
tested
successfully.
80 | P a g e
6. 11-09-2021 Password
testing
Only the
password can
access the pc or
in system for
further process.
Password was
tested
successfully.
80 | P a g e
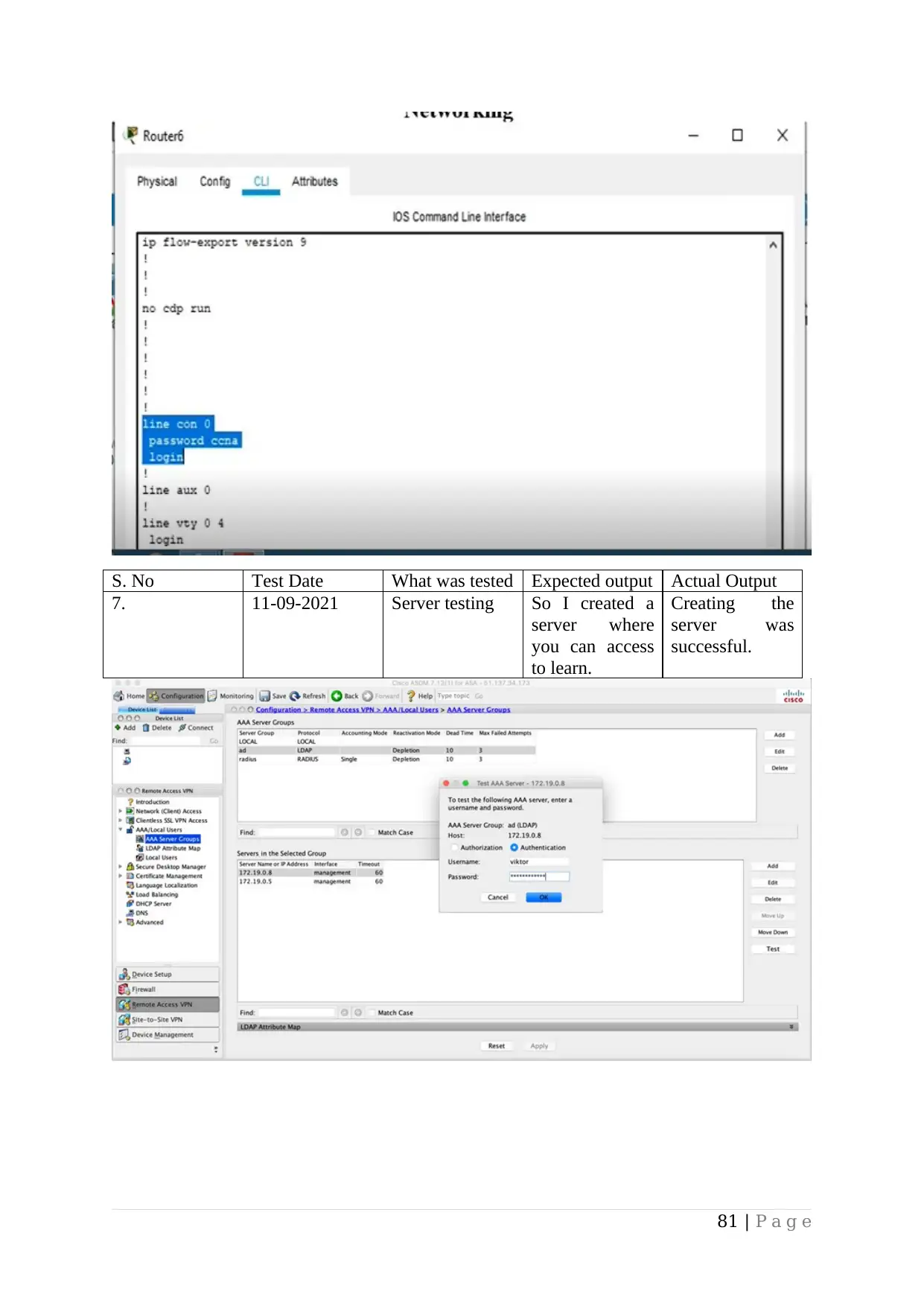
S. No Test Date What was tested Expected output Actual Output
7. 11-09-2021 Server testing So I created a
server where
you can access
to learn.
Creating the
server was
successful.
81 | P a g e
7. 11-09-2021 Server testing So I created a
server where
you can access
to learn.
Creating the
server was
successful.
81 | P a g e
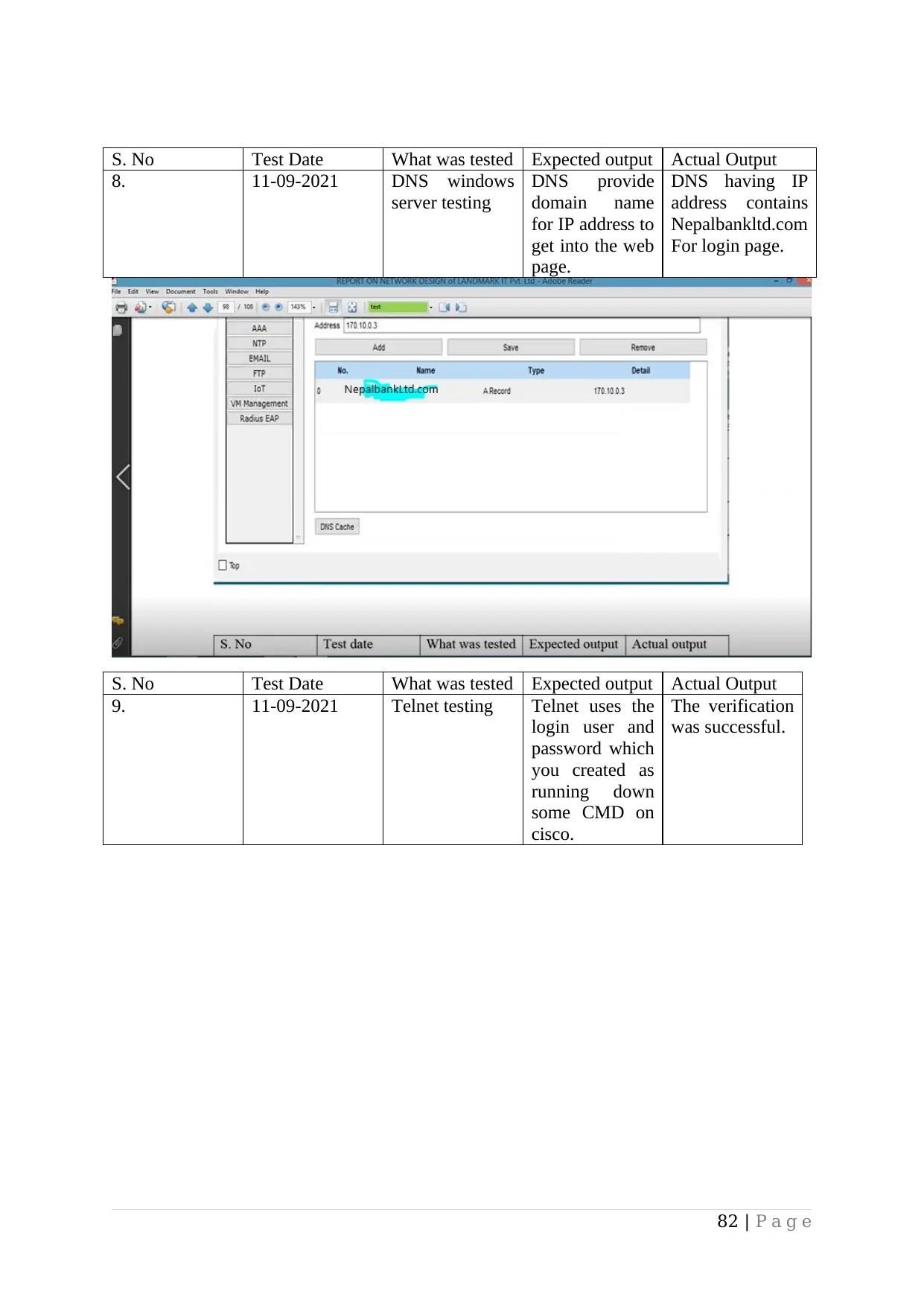
S. No Test Date What was tested Expected output Actual Output
8. 11-09-2021 DNS windows
server testing
DNS provide
domain name
for IP address to
get into the web
page.
DNS having IP
address contains
Nepalbankltd.com
For login page.
S. No Test Date What was tested Expected output Actual Output
9. 11-09-2021 Telnet testing Telnet uses the
login user and
password which
you created as
running down
some CMD on
cisco.
The verification
was successful.
82 | P a g e
8. 11-09-2021 DNS windows
server testing
DNS provide
domain name
for IP address to
get into the web
page.
DNS having IP
address contains
Nepalbankltd.com
For login page.
S. No Test Date What was tested Expected output Actual Output
9. 11-09-2021 Telnet testing Telnet uses the
login user and
password which
you created as
running down
some CMD on
cisco.
The verification
was successful.
82 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
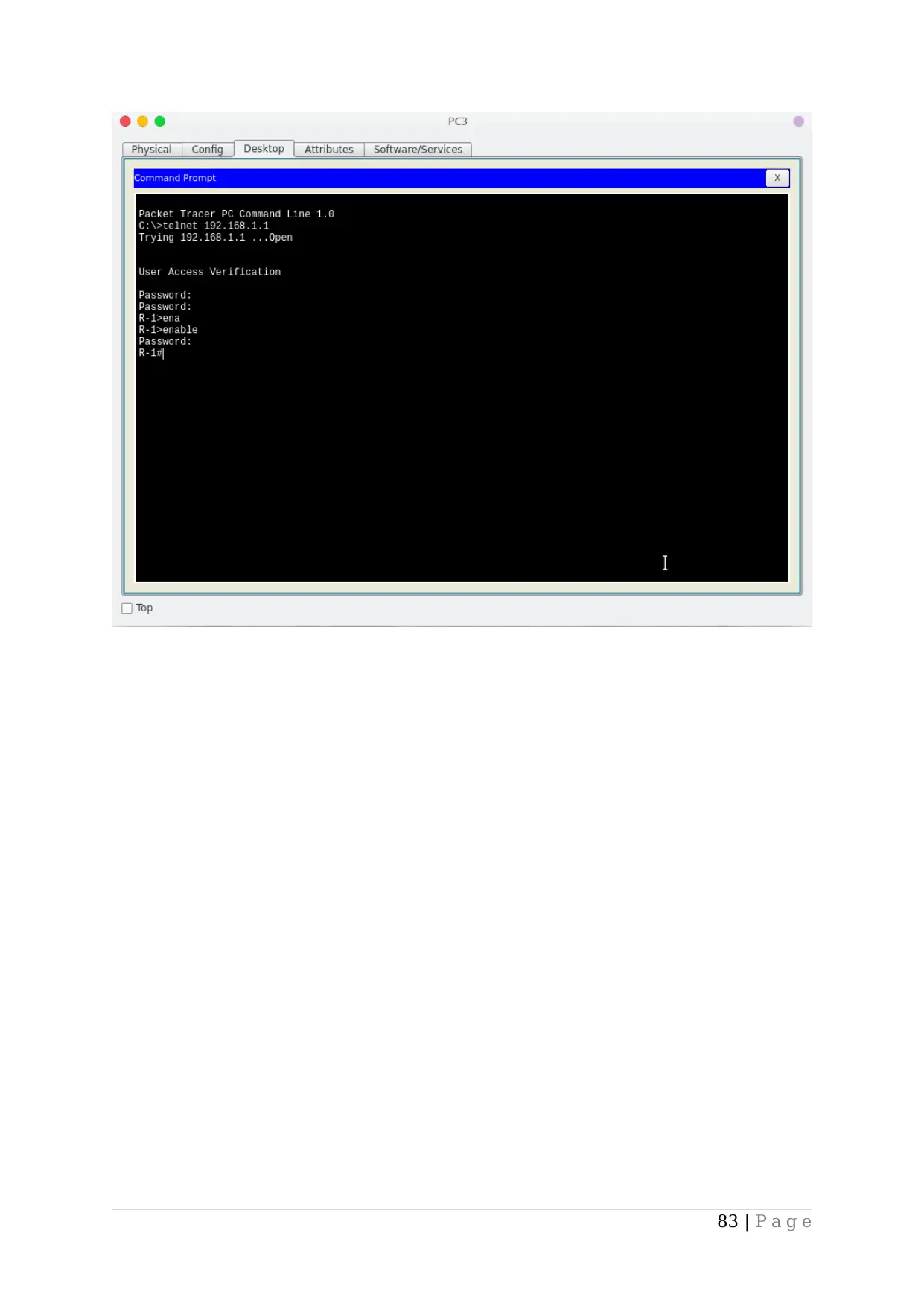
83 | P a g e

Design a maintenance schedule to support the networked system.
Network maintenance:-
Basically means you have to do what it takes in order to keep a network up and running and it
includes a number of tasks. Trouble shooting network problems. Hardware and software
installation/configuration. Monitoring and improving network performance.
Data backup services:-
There are 2 main reasons for critical data loss: either there was no backup or the media that
was used failed to successfully capture the data.
To prevent this catastrophe from occurring we require clients to maintain backups on the
cloud, external hard drives, DVD-RW, etc.
Upon each visit we verify that all of your critical information is being safely captured.
Anti-virus Protection and Spam Removers
We require our clients to maintain a current version of anti-virus software and spam remover
software.
System will be automatically scheduled to receive updates and will be scanned weekly for
threats.
The anti-virus software will be incorporated into our client’s email systems because the most
common method of virus transfer is from incoming and outgoing emails.
Firewall Protection:-
We also require that our client have adequate firewall protection that keeps personal data in
and hacker out.
It makes your pc invisible on the internet so that hackers can’t find it. Firewall programs also
contain intelligent intrusion prevention technology that blocks suspicious internet traffic.
Internal/External Component Cleaning
Dust is one of the leading causes of hardware failure. All moving components are thoroughly
cleaned and lubricated during services visits. All data cables are checked to be sure they are
securely seated on system boards.
CD and floppy drives are opened, cleaned and tested for data. External components such as
Keyboard, mouse, monitor and printers are cleaned of dust and debris and all cable
connections are checked.
Connections to surge protectors or UPS are checked.
84 | P a g e
Network maintenance:-
Basically means you have to do what it takes in order to keep a network up and running and it
includes a number of tasks. Trouble shooting network problems. Hardware and software
installation/configuration. Monitoring and improving network performance.
Data backup services:-
There are 2 main reasons for critical data loss: either there was no backup or the media that
was used failed to successfully capture the data.
To prevent this catastrophe from occurring we require clients to maintain backups on the
cloud, external hard drives, DVD-RW, etc.
Upon each visit we verify that all of your critical information is being safely captured.
Anti-virus Protection and Spam Removers
We require our clients to maintain a current version of anti-virus software and spam remover
software.
System will be automatically scheduled to receive updates and will be scanned weekly for
threats.
The anti-virus software will be incorporated into our client’s email systems because the most
common method of virus transfer is from incoming and outgoing emails.
Firewall Protection:-
We also require that our client have adequate firewall protection that keeps personal data in
and hacker out.
It makes your pc invisible on the internet so that hackers can’t find it. Firewall programs also
contain intelligent intrusion prevention technology that blocks suspicious internet traffic.
Internal/External Component Cleaning
Dust is one of the leading causes of hardware failure. All moving components are thoroughly
cleaned and lubricated during services visits. All data cables are checked to be sure they are
securely seated on system boards.
CD and floppy drives are opened, cleaned and tested for data. External components such as
Keyboard, mouse, monitor and printers are cleaned of dust and debris and all cable
connections are checked.
Connections to surge protectors or UPS are checked.
84 | P a g e

Software Updates/System Optimization:-
Operating system updates and patches are downloaded and installed to ensure that your
system has the most current version of the OS software. Internet browser software updates or
upgrades are performed as software changes become available. Updated components derivers
are installed as they become available or are required by system changes. Hardware
configurations are checked to be sure that they are operating efficiently and without conflict
with other components. Defrag and scan disk maintenance programs are run on other system
components to verify that they are in good working order. Hard drive file organization is
checked and any misplaced files are moved to their correct data folders. Any temporary or
unneeded files are located and removed.
Network Maintenance:-
Your computers and network need regular care to perform at their optimal level. Array
monitors networks on a daily basis. Having this information allows us to proactively maintain
your systems before trouble starts.
Server Management:-
We will make sure that your server is running optimally.
VPN Management:-
A VPN creates a secure “tunnel” by which you can access your network remotely. Array can
establish, manage and support your firewall services for you.
Router Management:-
Array will ensure your router is configured properly to optimize network performance and
ensure critical business system run.
Asset Management:-
Array will work with you to review your corporate assets and develop a lifecycle plan for
both software and hardware. This process will ensure that each member of your team is
working with the right technology that will increase workforce productivity.
Perform auditing and mapping:-
Auditing and mapping your network is a good idea. Always be aware of the whole network's
infrastructure, including firewalls, routers, switches, Ethernet cables and ports, and wireless
access points, as well as the vendor/model, location, and basic configuration of each. Also,
know what servers, computers, printers, and other devices are connected, where they are
connected, and how they are connected across the network.
85 | P a g e
Operating system updates and patches are downloaded and installed to ensure that your
system has the most current version of the OS software. Internet browser software updates or
upgrades are performed as software changes become available. Updated components derivers
are installed as they become available or are required by system changes. Hardware
configurations are checked to be sure that they are operating efficiently and without conflict
with other components. Defrag and scan disk maintenance programs are run on other system
components to verify that they are in good working order. Hard drive file organization is
checked and any misplaced files are moved to their correct data folders. Any temporary or
unneeded files are located and removed.
Network Maintenance:-
Your computers and network need regular care to perform at their optimal level. Array
monitors networks on a daily basis. Having this information allows us to proactively maintain
your systems before trouble starts.
Server Management:-
We will make sure that your server is running optimally.
VPN Management:-
A VPN creates a secure “tunnel” by which you can access your network remotely. Array can
establish, manage and support your firewall services for you.
Router Management:-
Array will ensure your router is configured properly to optimize network performance and
ensure critical business system run.
Asset Management:-
Array will work with you to review your corporate assets and develop a lifecycle plan for
both software and hardware. This process will ensure that each member of your team is
working with the right technology that will increase workforce productivity.
Perform auditing and mapping:-
Auditing and mapping your network is a good idea. Always be aware of the whole network's
infrastructure, including firewalls, routers, switches, Ethernet cables and ports, and wireless
access points, as well as the vendor/model, location, and basic configuration of each. Also,
know what servers, computers, printers, and other devices are connected, where they are
connected, and how they are connected across the network.
85 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

You may discover particular security vulnerabilities or solutions to improve security,
performance, and reliability when auditing and mapping. Perhaps you'll come upon a
malfunctioning firewall or physical security issues.
In an IT context, Network backup is an important aspect of the backup and recovery
process. It's done naturally with network backup software, which sorts the network
components to back up, sets up a backup schedule, and copies the data to a backup storage.
Backups ensure that in the event that something goes wrong with one of the servers and data
is lost, the data may be retrieved quickly using the backup.
Recommend potential enhancements for the networked systems.
Overview
As per the scenario, I have designed and tested the network for NIC Asia bank ltd. All the
necessary services required o maintain effective communication are installed and configured.
I have designed and configured the services on Cisco Packet Tracer alowng with several
hardware and software used for the network designed.
As per the scenario I have chosen all the hardware and software required previously. I have
used client server configuration. I have chosen some server due to its working capacity and is
mostly suitable for banking scenario. I have used Dell PowerEdge R540 Rack server, a 2nd
Generation Intel Xeon scalable processor with tailor performance based on unique workload
requirements.
Implement monitoring and automation
Visibility into layer 7 data flows is becoming increasingly critical as the complexity of
modern networks that operate at higher layers within the OSI model grows. When planning
your new network, make sure you have the network performance monitoring tools you'll need
to swiftly discover and handle application-specific issues. These technologies assist in
identifying typical issues so that proactive automation techniques can be used to quickly
remedy them.
Increasing growth of the network, the switches and more of access points will be added that
helps the networks to expand meaning your business/organization also expand and the
outcome of your business increases.
Hardware/software Dependency
Operating system-LINUX/UNIX It manages the computer’s memory and
process as well as all of its software and
hardware.
RAM-4 GB Act as temporary store of data and program
instructions so that they can be retrieved
quickly by the CPU when they are required.
Graphics-1 GB Responsible for rendering an image to
monitor and it does this by converting data
86 | P a g e
performance, and reliability when auditing and mapping. Perhaps you'll come upon a
malfunctioning firewall or physical security issues.
In an IT context, Network backup is an important aspect of the backup and recovery
process. It's done naturally with network backup software, which sorts the network
components to back up, sets up a backup schedule, and copies the data to a backup storage.
Backups ensure that in the event that something goes wrong with one of the servers and data
is lost, the data may be retrieved quickly using the backup.
Recommend potential enhancements for the networked systems.
Overview
As per the scenario, I have designed and tested the network for NIC Asia bank ltd. All the
necessary services required o maintain effective communication are installed and configured.
I have designed and configured the services on Cisco Packet Tracer alowng with several
hardware and software used for the network designed.
As per the scenario I have chosen all the hardware and software required previously. I have
used client server configuration. I have chosen some server due to its working capacity and is
mostly suitable for banking scenario. I have used Dell PowerEdge R540 Rack server, a 2nd
Generation Intel Xeon scalable processor with tailor performance based on unique workload
requirements.
Implement monitoring and automation
Visibility into layer 7 data flows is becoming increasingly critical as the complexity of
modern networks that operate at higher layers within the OSI model grows. When planning
your new network, make sure you have the network performance monitoring tools you'll need
to swiftly discover and handle application-specific issues. These technologies assist in
identifying typical issues so that proactive automation techniques can be used to quickly
remedy them.
Increasing growth of the network, the switches and more of access points will be added that
helps the networks to expand meaning your business/organization also expand and the
outcome of your business increases.
Hardware/software Dependency
Operating system-LINUX/UNIX It manages the computer’s memory and
process as well as all of its software and
hardware.
RAM-4 GB Act as temporary store of data and program
instructions so that they can be retrieved
quickly by the CPU when they are required.
Graphics-1 GB Responsible for rendering an image to
monitor and it does this by converting data
86 | P a g e

into a signal your monitor can understand.
Processor-I5 Provides the instructions and processing
power the computer needs to do its work.
High processor provides high configuration.
Network switch Provides an energy efficiency which changes
the issue of efficient power supplies and fans
by replacing with it.
Connectivity- 1 x USB 3.0 This is required to connect external device
with USB in faster rate.
NIC Card 1000ethernet LAN To allow to make communication in between
computer system through local area network ,
and to make communication over large scale
network Via internet protocol (IP).
Upgrade the network switch:-
Once you upgrade your switch you conserve energy efficiency was not a major concern in the
past, but network equipment manufacturers are now paying more attention to the issue and
installing more efficient power supplies and fans. The improvements are usually not
sufficient to justify replacing a switch but they are a bonus when upgrading for other reasons.
The decision to replace equipment should be made carefully even in the best of times.
Current conditions dictate extra diligence, but new technology and applications can yield
overall savings that make upgrades worthwhile.
Implementing a wireless router:-
The network is configured with wired router with the latest and new technology of wireless
routers, you need not to have a USB or any other means for the port and be involved in
carrying different types of devices for a file transfer, with latest wireless connection, and you
can easily transfer your files from one source to another. Different types of clouds like One
Drive, Google Drive, and iCloud are on your devices these days where you can store as well
as let other people see your files without having to have a single device for putting in a port,
sharing files and then removing it.
WithitheiadvancementiofiWirelessirouters,ioneidoesinotineeditoihaveianyicareioriworryiabo
utit
heisurroundings,iwirelessiroutersiwheneveritheyiareiableitoiworkicanigiveiyouiaitremendou
siam
ountiofispeediwithoutihavingitoihaveianyiwiresiattacheditoiyouridevice.iAlliyouihaveitoiha
veiis
iyourideviceiandiyouicanimoveifreelyifromioneiplaceitoitheiother,iwithinitheirequiredirang
e,iwit
houtihavingitoiworryiaboutianything,ilikeitheispeedioritheibreakageioficonnection.iYouiarei
give
nitheioptioniofifreeimovementiasiwelliasitheipeaceiofimindiwithitheilatestitechnologyiofiwi
reles
siroutersithereforeistudentsiwillibeiableitoiuseitheiPCsiofitheicollegeifromianywhereiinithei
colle
ge.i
87 | P a g e
Processor-I5 Provides the instructions and processing
power the computer needs to do its work.
High processor provides high configuration.
Network switch Provides an energy efficiency which changes
the issue of efficient power supplies and fans
by replacing with it.
Connectivity- 1 x USB 3.0 This is required to connect external device
with USB in faster rate.
NIC Card 1000ethernet LAN To allow to make communication in between
computer system through local area network ,
and to make communication over large scale
network Via internet protocol (IP).
Upgrade the network switch:-
Once you upgrade your switch you conserve energy efficiency was not a major concern in the
past, but network equipment manufacturers are now paying more attention to the issue and
installing more efficient power supplies and fans. The improvements are usually not
sufficient to justify replacing a switch but they are a bonus when upgrading for other reasons.
The decision to replace equipment should be made carefully even in the best of times.
Current conditions dictate extra diligence, but new technology and applications can yield
overall savings that make upgrades worthwhile.
Implementing a wireless router:-
The network is configured with wired router with the latest and new technology of wireless
routers, you need not to have a USB or any other means for the port and be involved in
carrying different types of devices for a file transfer, with latest wireless connection, and you
can easily transfer your files from one source to another. Different types of clouds like One
Drive, Google Drive, and iCloud are on your devices these days where you can store as well
as let other people see your files without having to have a single device for putting in a port,
sharing files and then removing it.
WithitheiadvancementiofiWirelessirouters,ioneidoesinotineeditoihaveianyicareioriworryiabo
utit
heisurroundings,iwirelessiroutersiwheneveritheyiareiableitoiworkicanigiveiyouiaitremendou
siam
ountiofispeediwithoutihavingitoihaveianyiwiresiattacheditoiyouridevice.iAlliyouihaveitoiha
veiis
iyourideviceiandiyouicanimoveifreelyifromioneiplaceitoitheiother,iwithinitheirequiredirang
e,iwit
houtihavingitoiworryiaboutianything,ilikeitheispeedioritheibreakageioficonnection.iYouiarei
give
nitheioptioniofifreeimovementiasiwelliasitheipeaceiofimindiwithitheilatestitechnologyiofiwi
reles
siroutersithereforeistudentsiwillibeiableitoiuseitheiPCsiofitheicollegeifromianywhereiinithei
colle
ge.i
87 | P a g e

With the advancement of Wireless routers, one does not need to have any care or worry about
the surroundings, wireless routers whenever they are able to work can give you a tremendous
amount of speed without having to have any wires attached to your device. All you
have to have is your device and you can move freely from one place to the other,
with in the required range, without having to worry about anything, like the speed or
the breakage of connect on. You are given the option of free movement as well as
the peace of mind with the latest technology of wireless routers therefore students
will be able to use the PCs of the college from anywhere in the college.
Use critical reflection to evaluate own work and justify valid conclusions.
Upgrade the firewall:-
A firewall provides for your network by blocking unauthorized access while still permitting
approved communications. Make sure that you have one and that it is current, meaning that
everything is being automatically patched and updated on a consistent basis. While you are at
it, check that these updates are being applied regularly to your firmware as well.
Emphasize Password Strength and Best Practices:-
Cybercriminals often gain access to networks through hacking employee’s passwords. To
combat this, make sure your employees know the ins and outs of creating strong passwords
(ones that are lengthy, use multiple characters and are unique to that account). A little
education can go a long way in securing one of cybercriminal’s easiest access point.
Encrypt the Entire Network
You can also encrypt an entire network. One option is IPsec. A Windows Server can serve as
the IPsec server and the client capability is natively supported by Windows as well. However,
the encryption process can be quite an overhead burden on the network; effective throughput
rates can drop dramatically. There are also proprietary network encryption solutions out there
from networking vendors, many of which use a Layer 2 approach instead of Layer 3 like
IPsec to help with reducing latency and overhead.
Perform Auditing and Mapping
Doing auditing and mapping of your network. Always have a clear understanding of the
entire network’s infrastructure, for instance the vendor/model, location, and basic
configuration of firewalls, routers, switches, Ethernet cabling and ports, and wireless access
points. Plus, know exactly what servers, computers, printers, and any other devices are
connected, where they are connected, and their connectivity path throughout the network.
During your auditing and mapping you might find specific security vulnerabilities or ways in
which you could increase security, performance and reliability. Maybe you’ll run across an
incorrectly configured firewall or maybe physical security threats.
Physically Secure the network:-
Although often overlooked or minimized, the physical security of the network can be just as
crucial as say your Internet facing firewall. Just as you need to protect against hackers, bots
and viruses, you need to protect against local threats, too.
88 | P a g e
the surroundings, wireless routers whenever they are able to work can give you a tremendous
amount of speed without having to have any wires attached to your device. All you
have to have is your device and you can move freely from one place to the other,
with in the required range, without having to worry about anything, like the speed or
the breakage of connect on. You are given the option of free movement as well as
the peace of mind with the latest technology of wireless routers therefore students
will be able to use the PCs of the college from anywhere in the college.
Use critical reflection to evaluate own work and justify valid conclusions.
Upgrade the firewall:-
A firewall provides for your network by blocking unauthorized access while still permitting
approved communications. Make sure that you have one and that it is current, meaning that
everything is being automatically patched and updated on a consistent basis. While you are at
it, check that these updates are being applied regularly to your firmware as well.
Emphasize Password Strength and Best Practices:-
Cybercriminals often gain access to networks through hacking employee’s passwords. To
combat this, make sure your employees know the ins and outs of creating strong passwords
(ones that are lengthy, use multiple characters and are unique to that account). A little
education can go a long way in securing one of cybercriminal’s easiest access point.
Encrypt the Entire Network
You can also encrypt an entire network. One option is IPsec. A Windows Server can serve as
the IPsec server and the client capability is natively supported by Windows as well. However,
the encryption process can be quite an overhead burden on the network; effective throughput
rates can drop dramatically. There are also proprietary network encryption solutions out there
from networking vendors, many of which use a Layer 2 approach instead of Layer 3 like
IPsec to help with reducing latency and overhead.
Perform Auditing and Mapping
Doing auditing and mapping of your network. Always have a clear understanding of the
entire network’s infrastructure, for instance the vendor/model, location, and basic
configuration of firewalls, routers, switches, Ethernet cabling and ports, and wireless access
points. Plus, know exactly what servers, computers, printers, and any other devices are
connected, where they are connected, and their connectivity path throughout the network.
During your auditing and mapping you might find specific security vulnerabilities or ways in
which you could increase security, performance and reliability. Maybe you’ll run across an
incorrectly configured firewall or maybe physical security threats.
Physically Secure the network:-
Although often overlooked or minimized, the physical security of the network can be just as
crucial as say your Internet facing firewall. Just as you need to protect against hackers, bots
and viruses, you need to protect against local threats, too.
88 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Critically evaluate the topology protocol selected for a given scenario to demonstrate the
efficient utilization of a networking System.
Reference:-
Available at: ComputerNetworkingNotes. (2018). Full Form of Hardware and Networking
Devices. [Online] Available at: https://www.computernetworkingnotes.com
Point, t., n.d. [Online] Available at: ComputerNetworkingNotes. (2018). Computer
Networking Devices Explained with Function. [Online] Available at:
https://www.computernetworkingnotes.com/networking-tutorials/computer-networking-
devices-explained-with-function.html
Reliability, n., n.d. [Online] Available at: Chapter 11 Network reliability [online]
sciencedirect.com. Available at:
https://www.sciencedirect.com/science/article/abs/pii/S0927050705801288
https://www.networkworld.com/article/2175048/8-ways-to-improve-wired-network-
security.html
https://www.networkcomputing.com/networking/7-tips-upgrading-your-network
https://cordkuttersconnect.com/understanding-the-advantages-and-disadvantages-of-wireless-
routers/
89 | P a g e
efficient utilization of a networking System.
Reference:-
Available at: ComputerNetworkingNotes. (2018). Full Form of Hardware and Networking
Devices. [Online] Available at: https://www.computernetworkingnotes.com
Point, t., n.d. [Online] Available at: ComputerNetworkingNotes. (2018). Computer
Networking Devices Explained with Function. [Online] Available at:
https://www.computernetworkingnotes.com/networking-tutorials/computer-networking-
devices-explained-with-function.html
Reliability, n., n.d. [Online] Available at: Chapter 11 Network reliability [online]
sciencedirect.com. Available at:
https://www.sciencedirect.com/science/article/abs/pii/S0927050705801288
https://www.networkworld.com/article/2175048/8-ways-to-improve-wired-network-
security.html
https://www.networkcomputing.com/networking/7-tips-upgrading-your-network
https://cordkuttersconnect.com/understanding-the-advantages-and-disadvantages-of-wireless-
routers/
89 | P a g e
1 out of 89
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





