Report: Implementing Security Controls for FNU Network Infrastructure
VerifiedAdded on 2020/04/13
|24
|6349
|50
Report
AI Summary
This report details the implementation of security controls for First National University (FNU), focusing on network access control and DMZ zone configurations. The report outlines the objective of access control, which involves limiting network access through tools like intrusion detection systems (IDS). It describes the resources used, including routers, firewalls, and various software and hardware components, along with the development of control strategies using IP addresses and access lists. The report also explains the deployment of packet filtering firewalls, their configuration, and the use of access control lists. Furthermore, it addresses the objective of DMZ implementation, which aims to isolate sensitive data from unauthorized access, detailing resources like firewalls and servers. The report discusses the configuration of DMZs and their role in enhancing network security. The report includes block diagrams, system configurations, and test plan designs for both access control and DMZ implementations. The report concludes by highlighting the importance of these security measures in protecting FNU's sensitive data from external threats and ensuring the integrity of its network infrastructure.

Technology Implementation of Security Controls
Overview
The following report has been made for forming a network connection among all the branch
offices of First National University (FNU) and the remote locations with requirement for data
access including the Campus location. The security considerations are being deployed for
forming the list for the alignment of the various technologies supporting the implication of the
effective implementation. The existing network would be modified for aligning with the
deployment model supporting the utilization of the advanced security development. The
university would require the security of their sensitive and crucial data from external infiltration.
The utilization of the security functions would help in easing the deployment of the effective
tools for protecting the data. The implication of the tools and operations for security would be
aligned with the development of the successive innovation models. The deployment of the
activities for security would require considering the factors of implication of the improved
development of cyber security, physical security, and personal security. The alignment of the
security policies would be deployed with the security functions and alignment of the operations.
Network Security – Access Control
Objective of Control
The network access control is a function useful for the implication of the effective control
strategies for the network (Kaur et al. 2014). The network security is deployed for aligning the
implication of the limited access in the system. The access control would be deployed for listing
the implication of the improved operation development levelling the alignment of the activities.
The control of the access in the network can be implied by installing IDS or intrusion detection
system. The unauthorised users would be prevented from entering the system and protection of
the system via tools would be achievable.
Resources Used
The resources required for the execution of the security implication are router, radius server,
firewall, radius client, and security protocols. The hardware and software consideration for the
Overview
The following report has been made for forming a network connection among all the branch
offices of First National University (FNU) and the remote locations with requirement for data
access including the Campus location. The security considerations are being deployed for
forming the list for the alignment of the various technologies supporting the implication of the
effective implementation. The existing network would be modified for aligning with the
deployment model supporting the utilization of the advanced security development. The
university would require the security of their sensitive and crucial data from external infiltration.
The utilization of the security functions would help in easing the deployment of the effective
tools for protecting the data. The implication of the tools and operations for security would be
aligned with the development of the successive innovation models. The deployment of the
activities for security would require considering the factors of implication of the improved
development of cyber security, physical security, and personal security. The alignment of the
security policies would be deployed with the security functions and alignment of the operations.
Network Security – Access Control
Objective of Control
The network access control is a function useful for the implication of the effective control
strategies for the network (Kaur et al. 2014). The network security is deployed for aligning the
implication of the limited access in the system. The access control would be deployed for listing
the implication of the improved operation development levelling the alignment of the activities.
The control of the access in the network can be implied by installing IDS or intrusion detection
system. The unauthorised users would be prevented from entering the system and protection of
the system via tools would be achievable.
Resources Used
The resources required for the execution of the security implication are router, radius server,
firewall, radius client, and security protocols. The hardware and software consideration for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

project would be limited with the development of the effective utilization of the software and
hardware requirements as mentioned in the table below,
Hardware Software
RAM for the computer system (4GB
preferable)
CPU with 2 or more cores
Hardware for Wi-Fi with WPA support
Windows Server 2012 R2
Server Certificate
Developing the control
The IP address is defined by the configuration of the network devices and the implementation of
an access list. The access list would allow the development of the effective control for the
information (Curiac 2016). The IP address and host name would be entered for allowing the
access in the network. The other types of control would result in forming the problems for the
deployment of the network access in the system. The implication of the firewall security would
assist in forming the implication of the activities forming control of the data packets. The
limitation of the network devices would allow the alignment of the activities forming the
implication of the improved operation development. The following reasons are considered for
the deployment of the network security,
Security plan would be used for protecting the hosts and the internal network of the FNU
Reducing the probability of the occurrence of the network infiltration via the cloud based
due to the alignment of wireless access
Data stored in the network is crucial for the alignment of the operations for FNU as very
sensitive and crucial information is stored in the cloud network
Denial of Service DoS attack is a major network flaw that is used by the hackers and the
FNU must use stern protection against this type of attack
hardware requirements as mentioned in the table below,
Hardware Software
RAM for the computer system (4GB
preferable)
CPU with 2 or more cores
Hardware for Wi-Fi with WPA support
Windows Server 2012 R2
Server Certificate
Developing the control
The IP address is defined by the configuration of the network devices and the implementation of
an access list. The access list would allow the development of the effective control for the
information (Curiac 2016). The IP address and host name would be entered for allowing the
access in the network. The other types of control would result in forming the problems for the
deployment of the network access in the system. The implication of the firewall security would
assist in forming the implication of the activities forming control of the data packets. The
limitation of the network devices would allow the alignment of the activities forming the
implication of the improved operation development. The following reasons are considered for
the deployment of the network security,
Security plan would be used for protecting the hosts and the internal network of the FNU
Reducing the probability of the occurrence of the network infiltration via the cloud based
due to the alignment of wireless access
Data stored in the network is crucial for the alignment of the operations for FNU as very
sensitive and crucial information is stored in the cloud network
Denial of Service DoS attack is a major network flaw that is used by the hackers and the
FNU must use stern protection against this type of attack

The attack on internal data would be required for being prevented due to the probability
of misusing the data and illegal access in the system
The network of the FNU can be improved with the alignment of the security via application of
the level gateway, packet filtering options, and circuit level gateway. These functions can be
aligned with the network for ensuring the implication of the activities favouring the network
security.
Description of the System
The packet filtering firewall would be aligned for the development of the network security and
the deployment of the effective implication of the network security. The router connection with
the internal network connection would be deployed for the implication of the effective
implication of the packet filtering firewall (Booth and Andersson 2015). The inspection of the
data packets would be assisted by the process of inspection. The source, IP address, port number,
and protocol are used for deployment of network blocking and accessing for the network for the
FNU. The allowance of the data packets or its blocking would be deployed based on the TCP
SYN, ACK bits, and ICMP message. The criteria of selection and the action field are the rules
for the data packet filtering used,
Selection Criteria: The selection criteria would be deployed for the utilization of the effective
implication and development models.
Action Field: The action field is deployed for the executing the points identified in the selection
criteria.
The application of the packet data filtering is deployed for ensuring that the operations would
form the utilization of the access control list. The traffic is passed through the firewall after the
securitization with the access control list is done for checking the permission or denial of
permission.
of misusing the data and illegal access in the system
The network of the FNU can be improved with the alignment of the security via application of
the level gateway, packet filtering options, and circuit level gateway. These functions can be
aligned with the network for ensuring the implication of the activities favouring the network
security.
Description of the System
The packet filtering firewall would be aligned for the development of the network security and
the deployment of the effective implication of the network security. The router connection with
the internal network connection would be deployed for the implication of the effective
implication of the packet filtering firewall (Booth and Andersson 2015). The inspection of the
data packets would be assisted by the process of inspection. The source, IP address, port number,
and protocol are used for deployment of network blocking and accessing for the network for the
FNU. The allowance of the data packets or its blocking would be deployed based on the TCP
SYN, ACK bits, and ICMP message. The criteria of selection and the action field are the rules
for the data packet filtering used,
Selection Criteria: The selection criteria would be deployed for the utilization of the effective
implication and development models.
Action Field: The action field is deployed for the executing the points identified in the selection
criteria.
The application of the packet data filtering is deployed for ensuring that the operations would
form the utilization of the access control list. The traffic is passed through the firewall after the
securitization with the access control list is done for checking the permission or denial of
permission.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Block Diagram
The diagram shows that the data connection to the device would be dependent on the access
control list. The access request would be passed through the firewall of the network for gaining
access to information. The passing through the firewall would be dependent on the implication of
the effective utilization of the operations for forming the alignment of the data pass. The logical
diagram for the network security via implication model would be implied for the alignment of
the successive alignment of the activities.
The logical diagram would be formed for listing the alignment of the effective network diagram
for the allocation of the successive development model. The devices used for the creation of the
network diagram are,
Cisco 2811 router
Radius Server
Radius Client User
Database
The diagram shows that the data connection to the device would be dependent on the access
control list. The access request would be passed through the firewall of the network for gaining
access to information. The passing through the firewall would be dependent on the implication of
the effective utilization of the operations for forming the alignment of the data pass. The logical
diagram for the network security via implication model would be implied for the alignment of
the successive alignment of the activities.
The logical diagram would be formed for listing the alignment of the effective network diagram
for the allocation of the successive development model. The devices used for the creation of the
network diagram are,
Cisco 2811 router
Radius Server
Radius Client User
Database
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
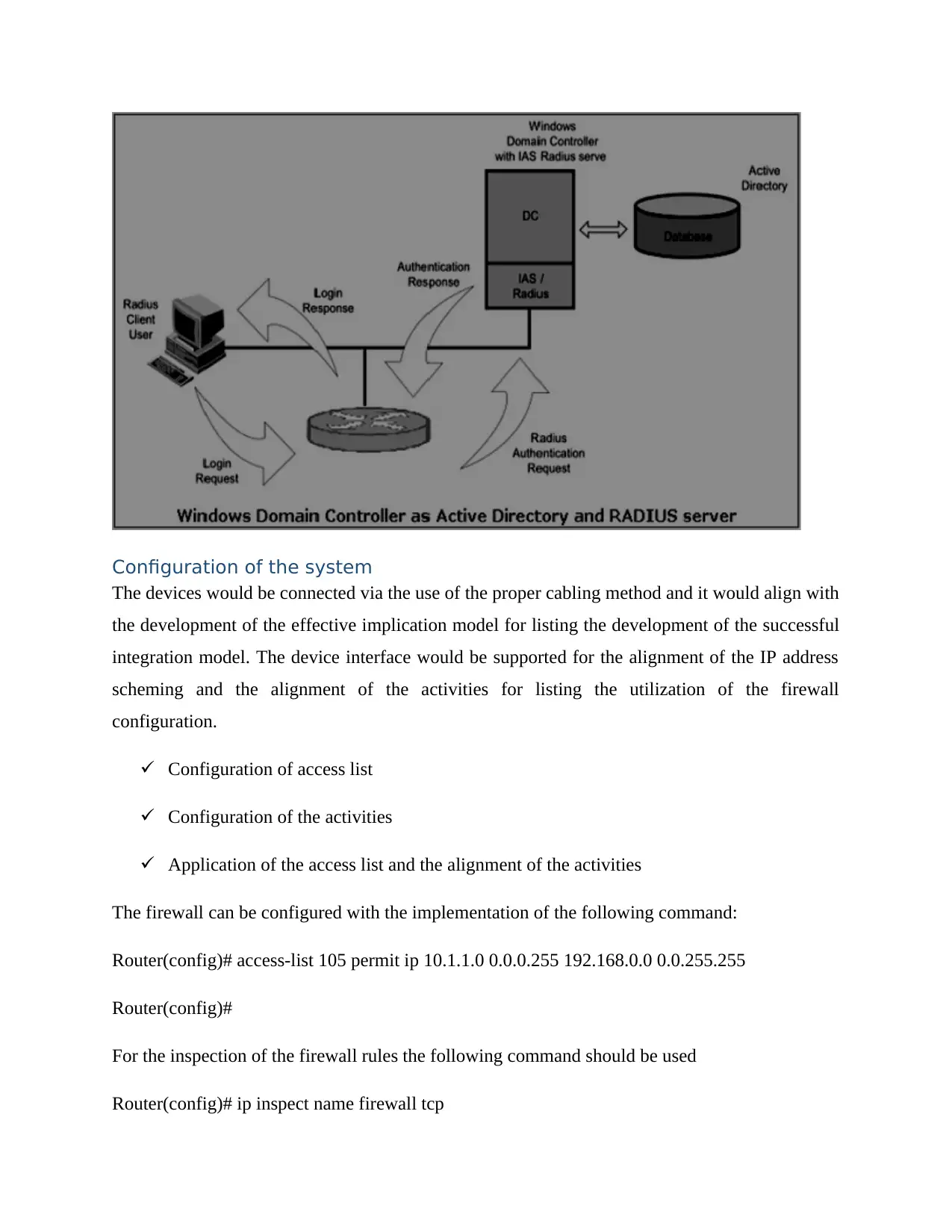
Configuration of the system
The devices would be connected via the use of the proper cabling method and it would align with
the development of the effective implication model for listing the development of the successful
integration model. The device interface would be supported for the alignment of the IP address
scheming and the alignment of the activities for listing the utilization of the firewall
configuration.
Configuration of access list
Configuration of the activities
Application of the access list and the alignment of the activities
The firewall can be configured with the implementation of the following command:
Router(config)# access-list 105 permit ip 10.1.1.0 0.0.0.255 192.168.0.0 0.0.255.255
Router(config)#
For the inspection of the firewall rules the following command should be used
Router(config)# ip inspect name firewall tcp
The devices would be connected via the use of the proper cabling method and it would align with
the development of the effective implication model for listing the development of the successful
integration model. The device interface would be supported for the alignment of the IP address
scheming and the alignment of the activities for listing the utilization of the firewall
configuration.
Configuration of access list
Configuration of the activities
Application of the access list and the alignment of the activities
The firewall can be configured with the implementation of the following command:
Router(config)# access-list 105 permit ip 10.1.1.0 0.0.0.255 192.168.0.0 0.0.255.255
Router(config)#
For the inspection of the firewall rules the following command should be used
Router(config)# ip inspect name firewall tcp

Router(config)#
For the application of the access list and the rules of inspection of the network interface the
following command should be used:
Router_Firewall(config)# interface g 0/1
Router_Firewall(config-if)#
Router_Firewall(config-if)# ip access-group 103 in
Router_Firewall(config-if)#
Router_Firewall(config-if)# exit
Router_Firewall(config)#
Test Plan Design
The test plan would be aligned for the utilization of the activities and deploying effective
alignment of the operations favouring the implication of the improved functional development.
The alignment would be formed for listing the alignment of the successive development model.
The remote connection would be supported for the formation of the interface development (Obio
and Mutale 2015). The listing of the operations would be aligned for forming the deployment of
the activities for network security. The test case would be used for defining the number of steps
favourable for the deployment of the effective operation development.
Test Plan Implementation
The enlisting of the activities would be supported for the formation of the improved operation
development. The alignment would be formed for developing the integration of the operations
for listing the development. The test plan would be aligned for the scheduling of the activities
and it would be assisted by the allowance of the design material. The remote host would be
formed for aligning the development of the successive integration model.
Test Results and Analysis
The alignment of the activities had formed for verification of the effective utilization of the
activities favouring the implication of the test process execution. The results for the adjusting of
For the application of the access list and the rules of inspection of the network interface the
following command should be used:
Router_Firewall(config)# interface g 0/1
Router_Firewall(config-if)#
Router_Firewall(config-if)# ip access-group 103 in
Router_Firewall(config-if)#
Router_Firewall(config-if)# exit
Router_Firewall(config)#
Test Plan Design
The test plan would be aligned for the utilization of the activities and deploying effective
alignment of the operations favouring the implication of the improved functional development.
The alignment would be formed for listing the alignment of the successive development model.
The remote connection would be supported for the formation of the interface development (Obio
and Mutale 2015). The listing of the operations would be aligned for forming the deployment of
the activities for network security. The test case would be used for defining the number of steps
favourable for the deployment of the effective operation development.
Test Plan Implementation
The enlisting of the activities would be supported for the formation of the improved operation
development. The alignment would be formed for developing the integration of the operations
for listing the development. The test plan would be aligned for the scheduling of the activities
and it would be assisted by the allowance of the design material. The remote host would be
formed for aligning the development of the successive integration model.
Test Results and Analysis
The alignment of the activities had formed for verification of the effective utilization of the
activities favouring the implication of the test process execution. The results for the adjusting of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the system would be aligned for the implication of the effective implication and development.
The test would run for the alignment of the effective implication of the process.
Network Security – DMZ Zone
Objective of Control
The main objective of the network security implication would be aligned for favouring the
development of the effective control of the information and data for the FNU. A demilitarized
zone is a specific area of network that is kept aloof from any normal method of access. The staff
and local users of the network would not be able to get into the system for extracting information
from the database (Dabbagh et al. 2015). The alignment of the effective database would be
aligned for forming the utilization of the effective implication of the information processing. The
DMZ forms a layer of security for the network making it impossible for getting into the system.
The existing network would be modified for aligning with the deployment model supporting the
utilization of the advanced security development. The FNU would require the security of their
sensitive and crucial data from external infiltration. The utilization of the security functions
would help in easing the deployment of the effective tools for protecting the data. The
implication of the tools and operations for security would be aligned with the development of the
successive innovation models (Inukollu, Arsi and Ravuri 2014). The deployment of the activities
for security would require considering the factors of implication of the improved development of
cyber security, physical security, and personal security.
Resources Used
DMZs are easily configured over the Linkys router and the creation of the DMZ would be
helpful for following the DMZ firewall rules for protecting the data from infiltration. Firewalls,
servers, etc are also used for setting the DMZ. The control of the network using DMZ can be
implied for successfully aligning the deployment of the operations and it would also be helpful
for forming the utilization of the effective development model.
Developing the control
The utilization of the activities would also be formed for aligning with the development of the
effective implication method. The integration of the effective development would be supported
by the alignment of the activities favouring the limitation of the email server for passing the
incoming and outgoing information (Krishna 2017). The existing network would be modified for
The test would run for the alignment of the effective implication of the process.
Network Security – DMZ Zone
Objective of Control
The main objective of the network security implication would be aligned for favouring the
development of the effective control of the information and data for the FNU. A demilitarized
zone is a specific area of network that is kept aloof from any normal method of access. The staff
and local users of the network would not be able to get into the system for extracting information
from the database (Dabbagh et al. 2015). The alignment of the effective database would be
aligned for forming the utilization of the effective implication of the information processing. The
DMZ forms a layer of security for the network making it impossible for getting into the system.
The existing network would be modified for aligning with the deployment model supporting the
utilization of the advanced security development. The FNU would require the security of their
sensitive and crucial data from external infiltration. The utilization of the security functions
would help in easing the deployment of the effective tools for protecting the data. The
implication of the tools and operations for security would be aligned with the development of the
successive innovation models (Inukollu, Arsi and Ravuri 2014). The deployment of the activities
for security would require considering the factors of implication of the improved development of
cyber security, physical security, and personal security.
Resources Used
DMZs are easily configured over the Linkys router and the creation of the DMZ would be
helpful for following the DMZ firewall rules for protecting the data from infiltration. Firewalls,
servers, etc are also used for setting the DMZ. The control of the network using DMZ can be
implied for successfully aligning the deployment of the operations and it would also be helpful
for forming the utilization of the effective development model.
Developing the control
The utilization of the activities would also be formed for aligning with the development of the
effective implication method. The integration of the effective development would be supported
by the alignment of the activities favouring the limitation of the email server for passing the
incoming and outgoing information (Krishna 2017). The existing network would be modified for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

aligning with the deployment model supporting the utilization of the advanced security
development. The FNU would require the security of their sensitive and crucial data from
external infiltration. The utilization of the DMZ security functions would help in easing the
deployment of the effective tools for protecting the data. The implication of the tools and
operations for security would be aligned with the development of the successive innovation
models. The deployment of the activities for security would require considering the factors of
implication of the improved development of cyber security, physical security, and personal
security.
Description of the System
DMZ is a specific area of network that is kept aloof from any normal method of access. The staff
and local users of the network would not be able to get into the system for extracting information
from the database. The DMZ forms a layer of security for the network making it impossible for
getting into the system. The existing network would be modified for aligning with the
deployment model supporting the utilization of the advanced security development. DMZ can be
formed by using a single firewall or two firewalls at once.
Configuration of the system
DMZ can be configured using the connection of the first network interface with the external
network for limiting the access. The second interface would also be connected to the internal
network of the FNU. The DMZ would be formed at the third interface of the network making the
handling of the information on the network easy. The colour codes would be helpful for
indicating the network traffic over the network. Two firewalls would be helpful for protecting
the information more effectively.
Test Plan Design
The different brands of firewalls should be used for implementing at the entry and exits points of
the network. It would help in lowering the probability of errors in network configuration. The
test plan design would be helpful for forming the implication of the effective and improved
activity development. The test plan would be aligned for listing the utilization of the improved
functional development. The penetration testing can be used for configuring the implementation
of the DMZ.
development. The FNU would require the security of their sensitive and crucial data from
external infiltration. The utilization of the DMZ security functions would help in easing the
deployment of the effective tools for protecting the data. The implication of the tools and
operations for security would be aligned with the development of the successive innovation
models. The deployment of the activities for security would require considering the factors of
implication of the improved development of cyber security, physical security, and personal
security.
Description of the System
DMZ is a specific area of network that is kept aloof from any normal method of access. The staff
and local users of the network would not be able to get into the system for extracting information
from the database. The DMZ forms a layer of security for the network making it impossible for
getting into the system. The existing network would be modified for aligning with the
deployment model supporting the utilization of the advanced security development. DMZ can be
formed by using a single firewall or two firewalls at once.
Configuration of the system
DMZ can be configured using the connection of the first network interface with the external
network for limiting the access. The second interface would also be connected to the internal
network of the FNU. The DMZ would be formed at the third interface of the network making the
handling of the information on the network easy. The colour codes would be helpful for
indicating the network traffic over the network. Two firewalls would be helpful for protecting
the information more effectively.
Test Plan Design
The different brands of firewalls should be used for implementing at the entry and exits points of
the network. It would help in lowering the probability of errors in network configuration. The
test plan design would be helpful for forming the implication of the effective and improved
activity development. The test plan would be aligned for listing the utilization of the improved
functional development. The penetration testing can be used for configuring the implementation
of the DMZ.

Test Plan Implementation
Various network monitoring tools can be used for identifying the vulnerabilities of the network
and the implication of the testing process for the network of the FNU.
Test Results and Analysis
Secured network configuration had been observed at the network development by DMZ and it
would form the implication of the effective activity development. The alignment of the improved
activity development would be supported by the utilization of the activities favouring the
implication of the successive activity development.
Network Security – RADIUS Server
Objective of Control
RADIUS in a network server is helpful for the utilization of the management process for the
network connection developing the implication of the effective utilization of the operations
(Rashid et al. 2014). The alignment would also be helpful for forming the development of the
activities favouring the utilization of the improved functional development. The internal and
wireless network would be supported by the utilization of the improved functional development.
The integrated email server would be formed for aligning with the deployment of the successive
implication of the activities.
Resources Used
The computer system with all necessary configurations favourable for the radius server execution
would be required for the development of the final project execution. It would serve as the main
resource for the RADIUS integration.
Developing the control
The authentication by RADIUS would be aligned for forming the implication of the
improved functional development. The utilization of the activities would be aligned for the
implication of the activities forming the alignment of the successive management of the
activities. The utilization of the improved functional development would be formed for listing
the IPv4 and IPv6 server address following the implication of the improved functional
development. The control development would be supported by the utilization of the activities
forming the implication of the successive development of the activities.
Various network monitoring tools can be used for identifying the vulnerabilities of the network
and the implication of the testing process for the network of the FNU.
Test Results and Analysis
Secured network configuration had been observed at the network development by DMZ and it
would form the implication of the effective activity development. The alignment of the improved
activity development would be supported by the utilization of the activities favouring the
implication of the successive activity development.
Network Security – RADIUS Server
Objective of Control
RADIUS in a network server is helpful for the utilization of the management process for the
network connection developing the implication of the effective utilization of the operations
(Rashid et al. 2014). The alignment would also be helpful for forming the development of the
activities favouring the utilization of the improved functional development. The internal and
wireless network would be supported by the utilization of the improved functional development.
The integrated email server would be formed for aligning with the deployment of the successive
implication of the activities.
Resources Used
The computer system with all necessary configurations favourable for the radius server execution
would be required for the development of the final project execution. It would serve as the main
resource for the RADIUS integration.
Developing the control
The authentication by RADIUS would be aligned for forming the implication of the
improved functional development. The utilization of the activities would be aligned for the
implication of the activities forming the alignment of the successive management of the
activities. The utilization of the improved functional development would be formed for listing
the IPv4 and IPv6 server address following the implication of the improved functional
development. The control development would be supported by the utilization of the activities
forming the implication of the successive development of the activities.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Description of the System
RADIUS stands for Remote Authentication Dial-In User Survey for the alignment of the
effective utilization of the activities (Vanerio and Casas 2017). The integration of the activities
would also be helpful for forming the utilization of the activities forming the implication of the
successive development model. The system allows the organization for forming the listing of the
activities supporting the development of the successive development method. It allows the dial in
users followed by the authentication method for providing better service.
Configuration of the system:
CLI quick configuration can be attained by copying various commands to the text file and
removing the line breaks for developing the system. The GUI step by step process would be
helpful for forming the implication of the RADIUS server as per various system authentications.
Test Plan Design:
Documents supporting the schedules, resources, and scopes would be included for the
development of the effective implication. The configuration of the server would be tested for
aligning the implication of the effective communication process. The estimation also plays a
significant role for the implication of the RADIUS test processes. The design must incorporate
all these functions for ensuring the development of the RADIUS.
Test Plan Implementation
The configuration of the server would be tested for aligning the implication of the effective
communication process. The estimation also plays a significant role for the implication of the
RADIUS test processes. The test managers would play a significant role for the execution of the
effective project activities.
Test Results and Analysis
Test results have shown that the network can be secured using the RADIUS functional server
and it would help in dealing with the vulnerabilities of the network.
Network Security – IPS
Objective of Control
The implication of the IPS network configuration would be supported for the alignment of the
activities favouring the implication of the effective implication model. The security consideration
would be supported by the development of the improved activities (Nepal and Jamasb 2015).
RADIUS stands for Remote Authentication Dial-In User Survey for the alignment of the
effective utilization of the activities (Vanerio and Casas 2017). The integration of the activities
would also be helpful for forming the utilization of the activities forming the implication of the
successive development model. The system allows the organization for forming the listing of the
activities supporting the development of the successive development method. It allows the dial in
users followed by the authentication method for providing better service.
Configuration of the system:
CLI quick configuration can be attained by copying various commands to the text file and
removing the line breaks for developing the system. The GUI step by step process would be
helpful for forming the implication of the RADIUS server as per various system authentications.
Test Plan Design:
Documents supporting the schedules, resources, and scopes would be included for the
development of the effective implication. The configuration of the server would be tested for
aligning the implication of the effective communication process. The estimation also plays a
significant role for the implication of the RADIUS test processes. The design must incorporate
all these functions for ensuring the development of the RADIUS.
Test Plan Implementation
The configuration of the server would be tested for aligning the implication of the effective
communication process. The estimation also plays a significant role for the implication of the
RADIUS test processes. The test managers would play a significant role for the execution of the
effective project activities.
Test Results and Analysis
Test results have shown that the network can be secured using the RADIUS functional server
and it would help in dealing with the vulnerabilities of the network.
Network Security – IPS
Objective of Control
The implication of the IPS network configuration would be supported for the alignment of the
activities favouring the implication of the effective implication model. The security consideration
would be supported by the development of the improved activities (Nepal and Jamasb 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The IPS network connection works as the alignment for the formation of the improved security
development. The IPS network connection would form the implication of the prevention in the
system. The IPS works successfully for forming the implication of the operations. The alignment
of the activities would be deployed for forming the utilization of the actions forming the
utilization of the successive modification tools. It is important for the alignment of the
operations. The IPS is very helpful for creating an effective implication of the operations. The
development of the operations would also form the implication of the activities for forming the
utilization of the operations. The vulnerabilities would be aligned for listing the penetration
testing and the utilization of the improved communication method (Vukolic 2015). The sensitive
and effective communication would be achieved with the alignment of the security for the
sensitive information process.
Resources Used:
The remote code, buffer overrun, SQL injection, and authentication bypass can be used by the
attacker for harming the system development. The mitigation of the risk process can be implied
for effective implication of the activities favouring the utilization of the security configuration.
The mitigation of the risk factors would result in forming the integration of the third part
installation. The various points for the communication would be supported for the allotment of
the activities.
Developing the control
The IPS network security would form the analysis of the vulnerability of the network research
and alignment of the operations. The alignment of the activities would be deployed for forming
the utilization of the actions forming the utilization of the successive modification tools. It is
important for the alignment of the operations. The IPS is very helpful for creating an effective
implication of the operations (Iwashita et al. 2016). The development of the operations would
also form the implication of the activities for forming the utilization of the operations. The
vulnerabilities would be aligned for listing the penetration testing and the utilization of the
improved communication method. The utilization of the activities would align the implication of
the operations. The flaws in programming would be aligned for the development of the activities
and utilization of the operations. The flaws in programming would be supported by the reduction
development. The IPS network connection would form the implication of the prevention in the
system. The IPS works successfully for forming the implication of the operations. The alignment
of the activities would be deployed for forming the utilization of the actions forming the
utilization of the successive modification tools. It is important for the alignment of the
operations. The IPS is very helpful for creating an effective implication of the operations. The
development of the operations would also form the implication of the activities for forming the
utilization of the operations. The vulnerabilities would be aligned for listing the penetration
testing and the utilization of the improved communication method (Vukolic 2015). The sensitive
and effective communication would be achieved with the alignment of the security for the
sensitive information process.
Resources Used:
The remote code, buffer overrun, SQL injection, and authentication bypass can be used by the
attacker for harming the system development. The mitigation of the risk process can be implied
for effective implication of the activities favouring the utilization of the security configuration.
The mitigation of the risk factors would result in forming the integration of the third part
installation. The various points for the communication would be supported for the allotment of
the activities.
Developing the control
The IPS network security would form the analysis of the vulnerability of the network research
and alignment of the operations. The alignment of the activities would be deployed for forming
the utilization of the actions forming the utilization of the successive modification tools. It is
important for the alignment of the operations. The IPS is very helpful for creating an effective
implication of the operations (Iwashita et al. 2016). The development of the operations would
also form the implication of the activities for forming the utilization of the operations. The
vulnerabilities would be aligned for listing the penetration testing and the utilization of the
improved communication method. The utilization of the activities would align the implication of
the operations. The flaws in programming would be aligned for the development of the activities
and utilization of the operations. The flaws in programming would be supported by the reduction

of the effective risk process for the open source network alignment. The presence of the rootkit
would be formed for the increment of the effective vulnerability and implicational development.
Description of the System:
The creation of trap in the network is being carried on with the help of honeypots and it allows
the logging activity for the alignment of the improved functional development. The various
levels of communication would be supported by the alignment of the activities. The research
honey pots would be formed for aligning the implication of the operations for forming the
utilization of the operations. The alignment of the activities would be deployed for forming the
utilization of the actions forming the utilization of the successive modification tools. It is
important for the alignment of the operations. The IPS is very helpful for creating an effective
implication of the operations (Mansfield-Devine 2015). The development of the operations
would also form the implication of the activities for forming the utilization of the operations. The
virtual machines would be helpful for supporting the hosting of the honeypots for protecting the
main server from the occurrence of the unauthorized access.
Configuration of the system:
Step 1: Pentbox would be downloaded for the setting of the Kali Linux nectar pot and the
introduction of the terminal framework. The Pentbox would be installed in the system
Step 2: The pentbox index and ./pentbox.rb cna be summoned for being utilized in running for
the pentbox for the compact disc pentbox 1.8
would be formed for the increment of the effective vulnerability and implicational development.
Description of the System:
The creation of trap in the network is being carried on with the help of honeypots and it allows
the logging activity for the alignment of the improved functional development. The various
levels of communication would be supported by the alignment of the activities. The research
honey pots would be formed for aligning the implication of the operations for forming the
utilization of the operations. The alignment of the activities would be deployed for forming the
utilization of the actions forming the utilization of the successive modification tools. It is
important for the alignment of the operations. The IPS is very helpful for creating an effective
implication of the operations (Mansfield-Devine 2015). The development of the operations
would also form the implication of the activities for forming the utilization of the operations. The
virtual machines would be helpful for supporting the hosting of the honeypots for protecting the
main server from the occurrence of the unauthorized access.
Configuration of the system:
Step 1: Pentbox would be downloaded for the setting of the Kali Linux nectar pot and the
introduction of the terminal framework. The Pentbox would be installed in the system
Step 2: The pentbox index and ./pentbox.rb cna be summoned for being utilized in running for
the pentbox for the compact disc pentbox 1.8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




