Digital Forensics: Comprehensive Investigation of the Enron Scandal
VerifiedAdded on 2022/10/04
|19
|2905
|48
Report
AI Summary
This report presents a digital forensics investigation of the Enron scandal, focusing on the causes of its collapse. The analysis examines various aspects, including the use of forensic tools such as Aid4Mail, Autopsy, and Magnet AXIOM to analyze employee emails and identify crucial evidence. The investigation involved downloading the Enron EDRM data set, using these tools to analyze email data, identify hidden data, and decrypt encrypted files. The report details the techniques used, including string searching and graphic image analysis to uncover key information related to the scandal. Findings reveal violations of banking rules, fraudulent activities, and corporate mismanagement, highlighting the role of key individuals like Kenneth Lay. The conclusion emphasizes the importance of proper management and ethical practices in preventing such financial disasters, providing a detailed account of the investigation and the insights gained from analyzing the Enron case.

Running head: DIGITAL FORENSICS
Digital Forensics
Name of the Student
Name of the University
Authors’ Note
Digital Forensics
Name of the Student
Name of the University
Authors’ Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DIGITAL FORENSICS
Executive Summary
This report consists of the investigated details of the Enron scandal so that the reason of the
collapse can be examined. Enron was one of the fastest growing and largest Companies. The
services that were provided by Enron were broadband services, wholesale services, services of
retail energy and services of transportation. Enron got more famous because of its scandal
incident which was the result of bankruptcy. This incident got acknowledged by every investors
and other companies. The corporate world got to know about the activities after that a
revolutionary change was observed in the corporate world. The analysis that has been conducted
is to find the details of the items that were found during the investigation. Relevant programs has
been used to find the details of the items which are the files associated to the transactions, some
deleted files, keywords that were searched over the Internet, etc. The steps that has been carried
out is discussed in detail in this report which will provide the details of the investigation.
Appropriate tools were used during the analysis of the emails that has been shared and for the
analysis of the evidences. The remaining part of the report is structured as: the description of the
report, incident, analysis of the found items, tools that were used and findings. Lastly the report
concludes with the result that were obtained.
DIGITAL FORENSICS
Executive Summary
This report consists of the investigated details of the Enron scandal so that the reason of the
collapse can be examined. Enron was one of the fastest growing and largest Companies. The
services that were provided by Enron were broadband services, wholesale services, services of
retail energy and services of transportation. Enron got more famous because of its scandal
incident which was the result of bankruptcy. This incident got acknowledged by every investors
and other companies. The corporate world got to know about the activities after that a
revolutionary change was observed in the corporate world. The analysis that has been conducted
is to find the details of the items that were found during the investigation. Relevant programs has
been used to find the details of the items which are the files associated to the transactions, some
deleted files, keywords that were searched over the Internet, etc. The steps that has been carried
out is discussed in detail in this report which will provide the details of the investigation.
Appropriate tools were used during the analysis of the emails that has been shared and for the
analysis of the evidences. The remaining part of the report is structured as: the description of the
report, incident, analysis of the found items, tools that were used and findings. Lastly the report
concludes with the result that were obtained.

2
DIGITAL FORENSICS
Table of Contents
Introduction......................................................................................................................................3
Analysis Conducted.........................................................................................................................4
Findings.........................................................................................................................................13
Conclusion.....................................................................................................................................15
Bibliography..................................................................................................................................17
DIGITAL FORENSICS
Table of Contents
Introduction......................................................................................................................................3
Analysis Conducted.........................................................................................................................4
Findings.........................................................................................................................................13
Conclusion.....................................................................................................................................15
Bibliography..................................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
DIGITAL FORENSICS
Introduction
The Enron Scandal led to bankruptcy in October 2001, the founder of the Enron Company
was Kenneth Lay. It was the fastest growing Company and the accounting firms that were
associated are, Delloitte, Ernst & Young, PwC and KPMG and Arthur Anderson. They were
responsible for the auditing of the financial data. All the shareholders who lost their money were
the victims of the crime committed by Enron and Arthur Anderson. The information they were
using to purchase the Stock was promised to be accurate but in reality it was far from it. At the
time Enron’s bankruptcy was the largest bankruptcy that ever occurred to American history
which makes this one of the biggest scandals in American history.
The forensic tools that has been used to examine the e-mail of the employees are, Aid4mail,
Autopsy and Magnet AXIOM. Aid4mail is considered to be the essential tool for digital
forensics which supports over 40 formats of email. It has helped me in saving time, it is easy to
use and provides accurate solutions. With the help of Autopsy software, major files can be
analyzed such as HFS+, Ext3, Ext4, etc. through the process of hashing. It helps in unloading the
standard zipped files as well as extracting the exchangeable image file format. The back end of
Autopsy includes Perl language which is runnable in LINUX, UNIX, Windows and Mac-OS.
Magnet AXIOM helps me in determining the evidences as it has the capability of decrypting the
full disk and helps in accessing the file system data. For examining the evidences, artifact
explorer, registry and file system explorers, source linking methods are involved.
The files what I have got as evidences are of larger size and I have used metadata to get the
information about these files. Some files are in encrypted form therefore I have used Autopsy for
hashing decryption. I have also used the String searching procedures to find the relevant details
DIGITAL FORENSICS
Introduction
The Enron Scandal led to bankruptcy in October 2001, the founder of the Enron Company
was Kenneth Lay. It was the fastest growing Company and the accounting firms that were
associated are, Delloitte, Ernst & Young, PwC and KPMG and Arthur Anderson. They were
responsible for the auditing of the financial data. All the shareholders who lost their money were
the victims of the crime committed by Enron and Arthur Anderson. The information they were
using to purchase the Stock was promised to be accurate but in reality it was far from it. At the
time Enron’s bankruptcy was the largest bankruptcy that ever occurred to American history
which makes this one of the biggest scandals in American history.
The forensic tools that has been used to examine the e-mail of the employees are, Aid4mail,
Autopsy and Magnet AXIOM. Aid4mail is considered to be the essential tool for digital
forensics which supports over 40 formats of email. It has helped me in saving time, it is easy to
use and provides accurate solutions. With the help of Autopsy software, major files can be
analyzed such as HFS+, Ext3, Ext4, etc. through the process of hashing. It helps in unloading the
standard zipped files as well as extracting the exchangeable image file format. The back end of
Autopsy includes Perl language which is runnable in LINUX, UNIX, Windows and Mac-OS.
Magnet AXIOM helps me in determining the evidences as it has the capability of decrypting the
full disk and helps in accessing the file system data. For examining the evidences, artifact
explorer, registry and file system explorers, source linking methods are involved.
The files what I have got as evidences are of larger size and I have used metadata to get the
information about these files. Some files are in encrypted form therefore I have used Autopsy for
hashing decryption. I have also used the String searching procedures to find the relevant details
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
DIGITAL FORENSICS
of the files. The files consists of some numeric data as well as many information for which I
have to apply the String search method. The findings that have been discovered includes some
evidences which are internet related and ownership indicator details. I have followed all
procedures to make sure that all the findings are investigated properly. Through String search I
have got to know about the information of various words related to the case. The indicators were
analyzed properly to determine the ownership. Few emails are there which consist of bankruptcy
discussion and about bad credit. Some passwords have also been exchanged by them through
emails and it has been found that data or information were in encrypted for which cryptographic
calculations have been applied to retrieve the original information. For the analysis purpose
different software and associated steps has been followed to examine the emails. All the
processes or mechanism that have been maintained to design this report has assisted in gaining
the ethical perspective of investigation. Moreover, the data that have been collected from the
emails consist of original form.
Analysis Conducted
Relevant programs
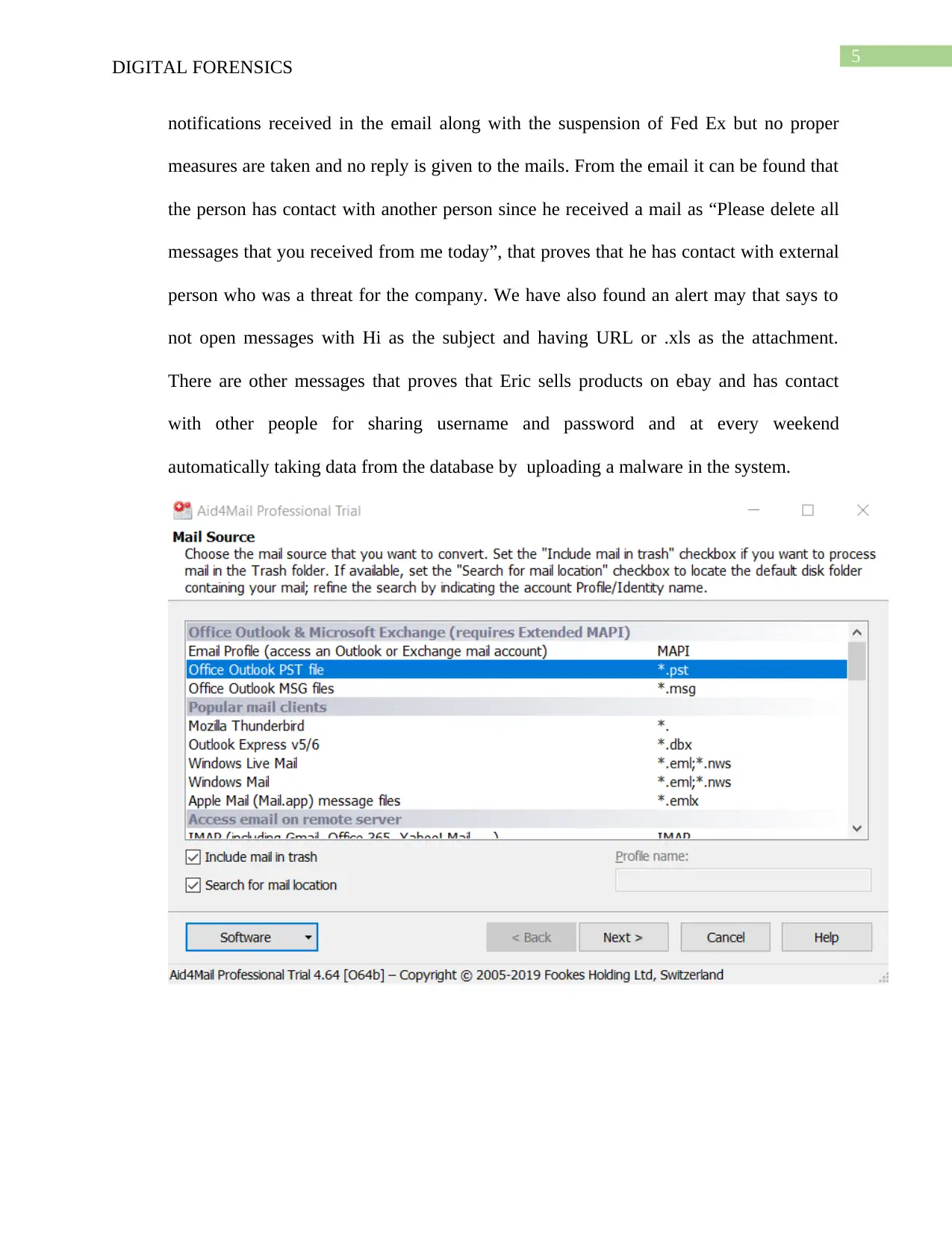
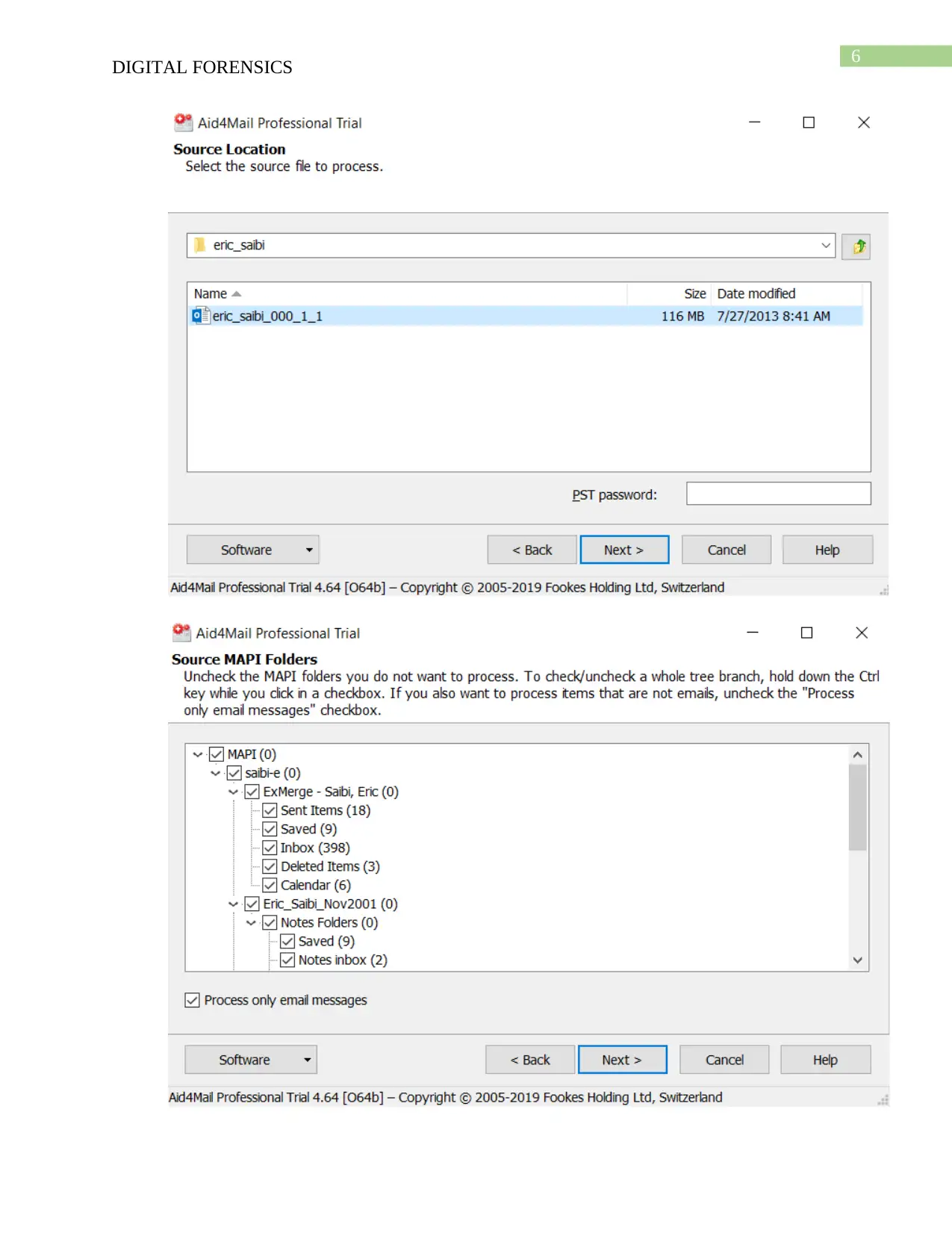
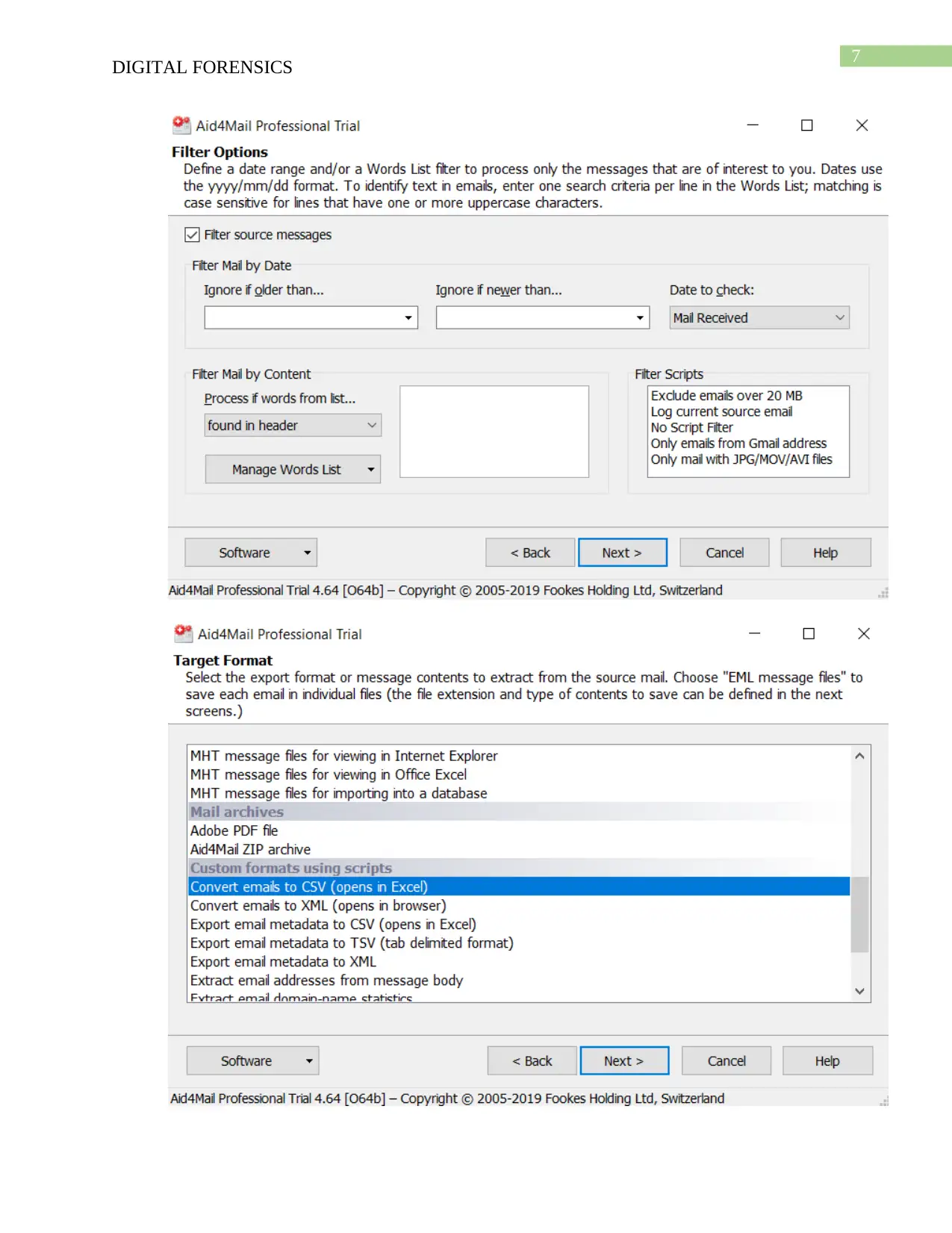
To examine the emails of the employees of Enron firstly Aid4Mail is used for which I
have to create folders and respective subfolders to install the Aid4Mail in the system. The
Enron EDRM data set is of size 18GB which I have downloaded and uncompressed the
files. The file of ‘.pst’ format have been downloaded then sequential steps were followed
which includes Source MAPI folders window, selection of the range of data, etc. Then in
the Target Setting consists of all the work folders and sub folders in which I have
included the CSV files, these files are the converted form of the emails. I have examined
the emails for getting the cause of the bankruptcy and found that there are system outrage
DIGITAL FORENSICS
of the files. The files consists of some numeric data as well as many information for which I
have to apply the String search method. The findings that have been discovered includes some
evidences which are internet related and ownership indicator details. I have followed all
procedures to make sure that all the findings are investigated properly. Through String search I
have got to know about the information of various words related to the case. The indicators were
analyzed properly to determine the ownership. Few emails are there which consist of bankruptcy
discussion and about bad credit. Some passwords have also been exchanged by them through
emails and it has been found that data or information were in encrypted for which cryptographic
calculations have been applied to retrieve the original information. For the analysis purpose
different software and associated steps has been followed to examine the emails. All the
processes or mechanism that have been maintained to design this report has assisted in gaining
the ethical perspective of investigation. Moreover, the data that have been collected from the
emails consist of original form.
Analysis Conducted
Relevant programs
To examine the emails of the employees of Enron firstly Aid4Mail is used for which I
have to create folders and respective subfolders to install the Aid4Mail in the system. The
Enron EDRM data set is of size 18GB which I have downloaded and uncompressed the
files. The file of ‘.pst’ format have been downloaded then sequential steps were followed
which includes Source MAPI folders window, selection of the range of data, etc. Then in
the Target Setting consists of all the work folders and sub folders in which I have
included the CSV files, these files are the converted form of the emails. I have examined
the emails for getting the cause of the bankruptcy and found that there are system outrage
5
DIGITAL FORENSICS
notifications received in the email along with the suspension of Fed Ex but no proper
measures are taken and no reply is given to the mails. From the email it can be found that
the person has contact with another person since he received a mail as “Please delete all
messages that you received from me today”, that proves that he has contact with external
person who was a threat for the company. We have also found an alert may that says to
not open messages with Hi as the subject and having URL or .xls as the attachment.
There are other messages that proves that Eric sells products on ebay and has contact
with other people for sharing username and password and at every weekend
automatically taking data from the database by uploading a malware in the system.
DIGITAL FORENSICS
notifications received in the email along with the suspension of Fed Ex but no proper
measures are taken and no reply is given to the mails. From the email it can be found that
the person has contact with another person since he received a mail as “Please delete all
messages that you received from me today”, that proves that he has contact with external
person who was a threat for the company. We have also found an alert may that says to
not open messages with Hi as the subject and having URL or .xls as the attachment.
There are other messages that proves that Eric sells products on ebay and has contact
with other people for sharing username and password and at every weekend
automatically taking data from the database by uploading a malware in the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
DIGITAL FORENSICS
DIGITAL FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
DIGITAL FORENSICS
DIGITAL FORENSICS
8
DIGITAL FORENSICS
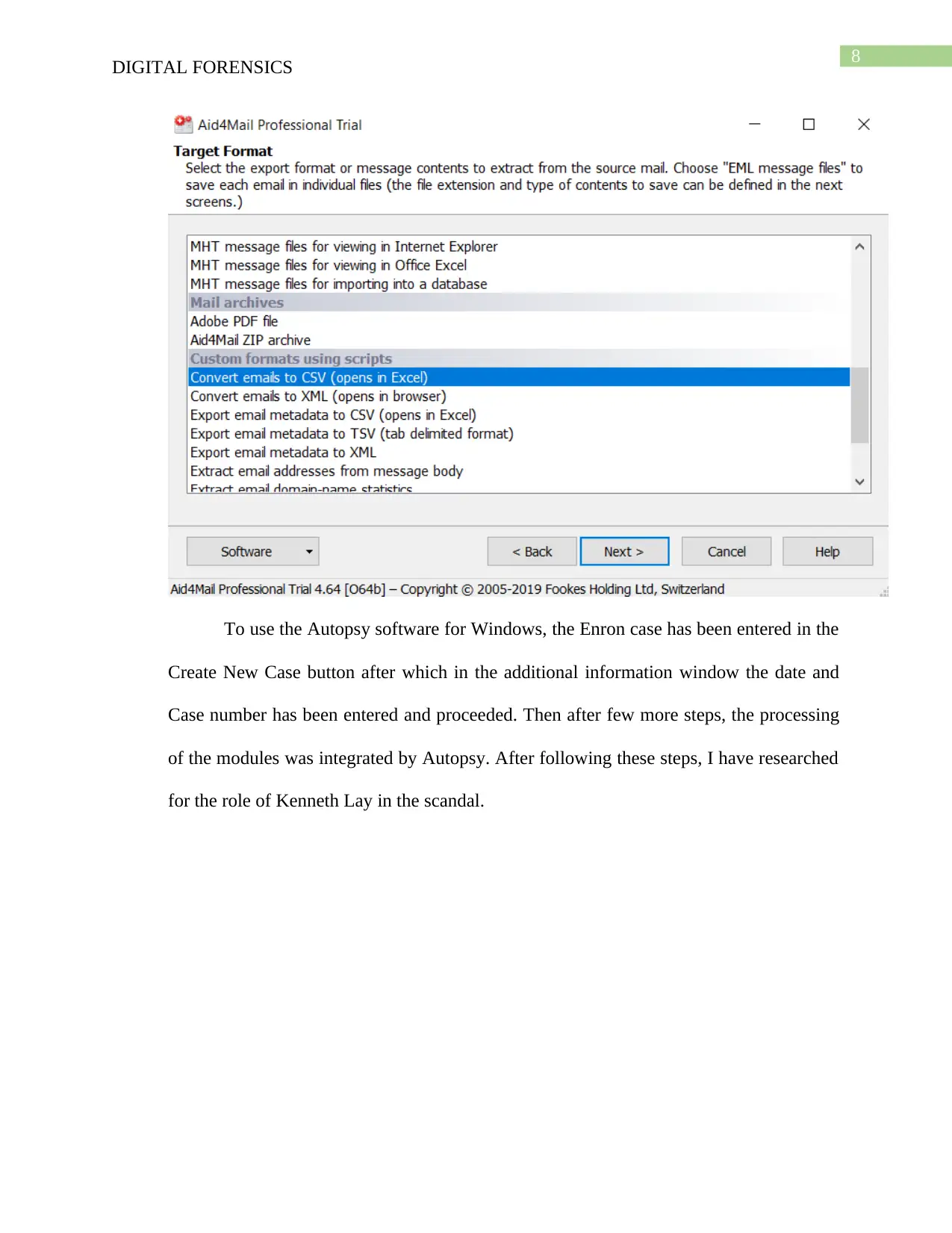
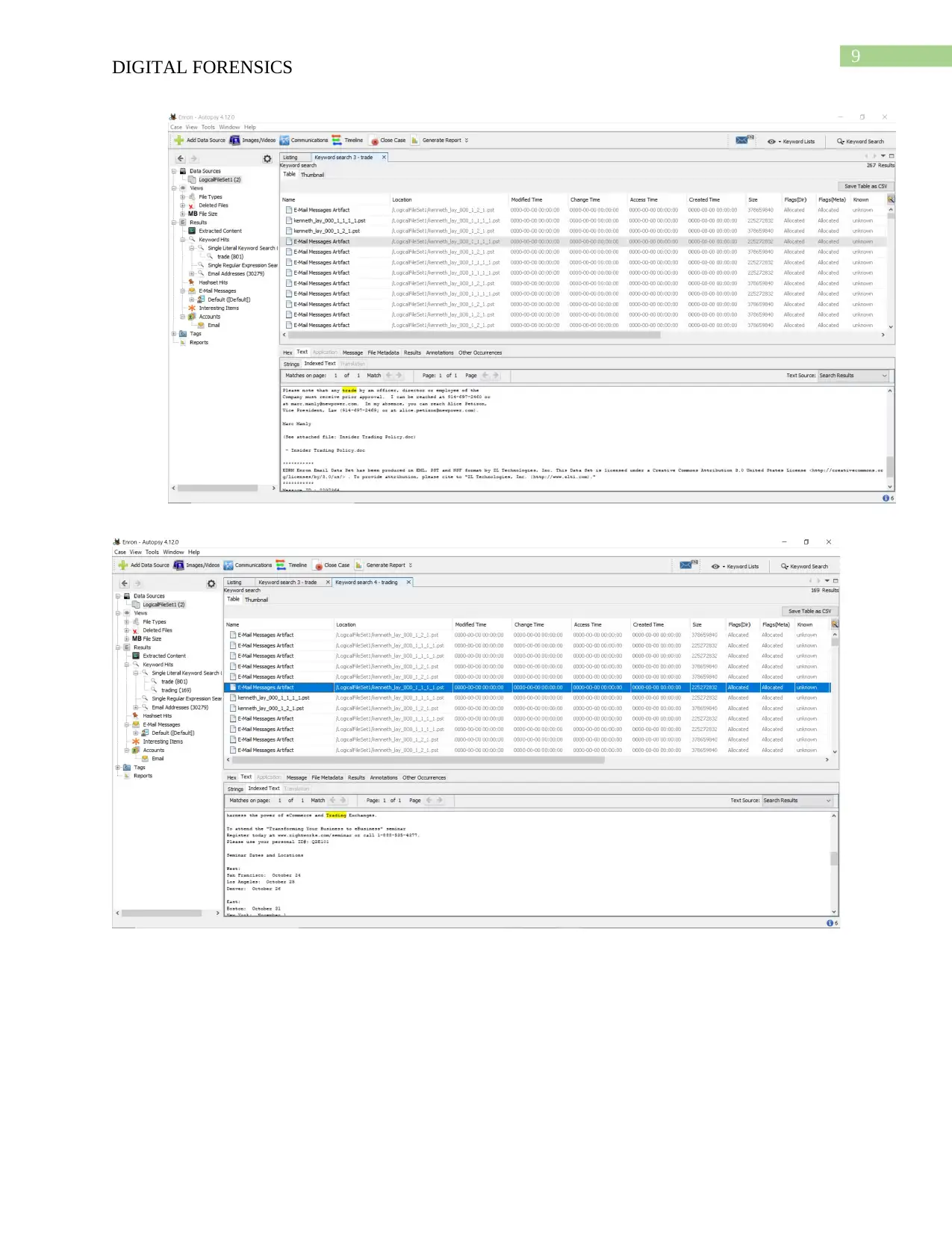
To use the Autopsy software for Windows, the Enron case has been entered in the
Create New Case button after which in the additional information window the date and
Case number has been entered and proceeded. Then after few more steps, the processing
of the modules was integrated by Autopsy. After following these steps, I have researched
for the role of Kenneth Lay in the scandal.
DIGITAL FORENSICS
To use the Autopsy software for Windows, the Enron case has been entered in the
Create New Case button after which in the additional information window the date and
Case number has been entered and proceeded. Then after few more steps, the processing
of the modules was integrated by Autopsy. After following these steps, I have researched
for the role of Kenneth Lay in the scandal.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
DIGITAL FORENSICS
DIGITAL FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
DIGITAL FORENSICS
DIGITAL FORENSICS

11
DIGITAL FORENSICS
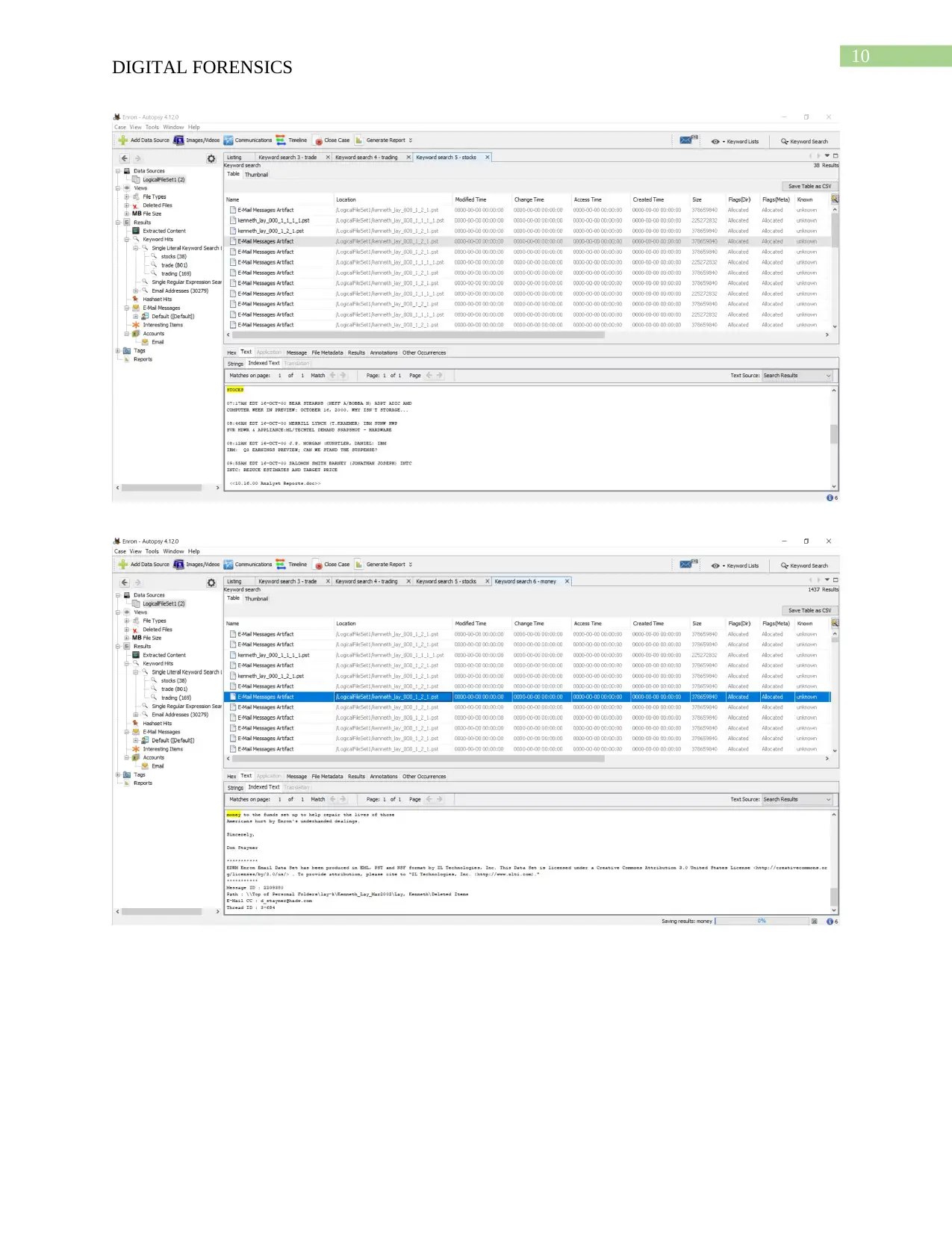
The above screenshot proves that Ken Lay has earned 100 million by selling the
stocks and is known by his co-worker Chris Moore. The message was deleted by Ken
Lay after he received it and it proves him guilty for the downfall of Enron.
By using the Magnet AXIOM I have extracted the histogram view of the shared
emails due to which I was able to identify the frequencies of data occurred in the dataset.
Visualization of the huge datasets and became easier therefore, it got easier to interpret
the data.
DIGITAL FORENSICS
The above screenshot proves that Ken Lay has earned 100 million by selling the
stocks and is known by his co-worker Chris Moore. The message was deleted by Ken
Lay after he received it and it proves him guilty for the downfall of Enron.
By using the Magnet AXIOM I have extracted the histogram view of the shared
emails due to which I was able to identify the frequencies of data occurred in the dataset.
Visualization of the huge datasets and became easier therefore, it got easier to interpret
the data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




