Analyzing Offense/Defense Balance in Cyberspace with AI
VerifiedAdded on 2020/04/21
|20
|4185
|257
Report
AI Summary
This report delves into the critical role of Artificial Intelligence (AI) in balancing the offense and defense dynamics within cyberspace. It begins by defining AI and its applications, emphasizing its potential to analyze vast amounts of data and enhance cybersecurity. The report explores the concept of cyberspace, the evolution of offense-defense strategies, and the challenges of attribution in cyberattacks. It highlights the current dominance of offense in cyberspace and how AI can be leveraged to strengthen defense mechanisms. The report presents examples of AI applications, such as IBM's Watson, and discusses their contributions to threat detection, response times, and security intelligence. It also examines specific examples of cyberattacks, like ransomware and malware, and how AI can mitigate their impact. The report highlights examples of AI such as Showan, IBM's Watson, and Google’s Deepmind and discusses how they are contributing to balancing the cyber offense defense. Overall, the report underscores the importance of AI in shaping the future of cybersecurity and maintaining stability in the digital world.

Running head: THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
The Offense/Defence Balance in Cyberspace
Name of the Student
Name of the University
Author Note
The Offense/Defence Balance in Cyberspace
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Table of Contents
Introduction......................................................................................................................................2
Role of Artificial Intelligence in Cyberspace..................................................................................3
Artificial Intelligence...................................................................................................................3
Cyberspace...................................................................................................................................3
Offense-Defense Strategy............................................................................................................4
Cyberspace is currentlyaDefense Dominant Domain......................................................................5
Examples of Artificial Intelligence..................................................................................................7
Offense-Defense Theory for International Stability........................................................................8
Conclusion.....................................................................................................................................10
References......................................................................................................................................11
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Table of Contents
Introduction......................................................................................................................................2
Role of Artificial Intelligence in Cyberspace..................................................................................3
Artificial Intelligence...................................................................................................................3
Cyberspace...................................................................................................................................3
Offense-Defense Strategy............................................................................................................4
Cyberspace is currentlyaDefense Dominant Domain......................................................................5
Examples of Artificial Intelligence..................................................................................................7
Offense-Defense Theory for International Stability........................................................................8
Conclusion.....................................................................................................................................10
References......................................................................................................................................11

2
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Introduction
Technology is continuously evolving, cyber-attacks and cyber security also being
advanced and evolving at the same pace as technology. Cybersecurity threat’s graphs are
continuously increasing and most of the threats generally become undetectable unless it harms in
the real world. For a general human, it is a very complex matter to analyse all the data saved in
the system1. This report focuses on the role of Artificial Intelligence in balancing the Offense
and Defense in cyberspace. AI is not a very new technology as robots have been around since
1950's of which, many practical applications are available in our daily life. This report presents
the objectives related to the cybersecurity and emphasizes on cyberattacks those are becoming a
common factor for the data and information saved in the system either offline or online. The
Internet has become an integral part of the life living for almost every human being and saving
data or information on the internet makes them vulnerable to cyberattacks. This report presents
an idea of how AI could change the face of the cybersecurity and contribute to the Defense
through a debate. Watson, GoogleDeepmind, and Showan are some of the examples of AI those
are contributing to enhancing the cybersecurity. The Offense-Defence Balance (ODB) theory has
been discussed in this report with regard to the international stability and how AI could be
implemented and used for the good cause.
1 Kasprick, Robert, Jordan Hoffman, Jeremy Straub, and Eunjin Kim. "Cyber Security Artificial Intelligence Expert
System." (2016).
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Introduction
Technology is continuously evolving, cyber-attacks and cyber security also being
advanced and evolving at the same pace as technology. Cybersecurity threat’s graphs are
continuously increasing and most of the threats generally become undetectable unless it harms in
the real world. For a general human, it is a very complex matter to analyse all the data saved in
the system1. This report focuses on the role of Artificial Intelligence in balancing the Offense
and Defense in cyberspace. AI is not a very new technology as robots have been around since
1950's of which, many practical applications are available in our daily life. This report presents
the objectives related to the cybersecurity and emphasizes on cyberattacks those are becoming a
common factor for the data and information saved in the system either offline or online. The
Internet has become an integral part of the life living for almost every human being and saving
data or information on the internet makes them vulnerable to cyberattacks. This report presents
an idea of how AI could change the face of the cybersecurity and contribute to the Defense
through a debate. Watson, GoogleDeepmind, and Showan are some of the examples of AI those
are contributing to enhancing the cybersecurity. The Offense-Defence Balance (ODB) theory has
been discussed in this report with regard to the international stability and how AI could be
implemented and used for the good cause.
1 Kasprick, Robert, Jordan Hoffman, Jeremy Straub, and Eunjin Kim. "Cyber Security Artificial Intelligence Expert
System." (2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Role of Artificial Intelligence in Cyberspace
Artificial Intelligence
John McCarthy defined this as, “The science and engineering of making intelligent
machines, especially intelligent computer programs.” It can be described as a way of making the
software, computer, and computer-controlled robot much smarter, similar to the human
intelligence. Various researchers are trying to implement such thinking for decades and success
is leading to various attempts2. It can be described as the mixture of Philosophy, computer
science, neuron science, biology, psychology, math, and sociology. There are various
applications of AI in the current world including games, expert systems, speech recognition,
natural language processing, intelligent robots, handwriting recognition and much more3.
Artificial Intelligence (AI) could act as a boon for such issues and could help in analysing a very
wide range of data in very less time as compared to the data processed by humans.Offense-
Defense in cyberspace is another concerning topic related to the virtual computer world that
2 Miller, Steven E., and Stephen Van Evera, eds. The Star Wars Controversy: An" International
Security" Reader. Princeton University Press, 2014.
3 Krittanawong, Chayakrit, HongJu Zhang, Zhen Wang, Mehmet Aydar, and Takeshi Kitai.
"Artificial Intelligence in Precision Cardiovascular Medicine." Journal of the American College
of Cardiology 69, no. 21 (2017): 2657-2664.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Role of Artificial Intelligence in Cyberspace
Artificial Intelligence
John McCarthy defined this as, “The science and engineering of making intelligent
machines, especially intelligent computer programs.” It can be described as a way of making the
software, computer, and computer-controlled robot much smarter, similar to the human
intelligence. Various researchers are trying to implement such thinking for decades and success
is leading to various attempts2. It can be described as the mixture of Philosophy, computer
science, neuron science, biology, psychology, math, and sociology. There are various
applications of AI in the current world including games, expert systems, speech recognition,
natural language processing, intelligent robots, handwriting recognition and much more3.
Artificial Intelligence (AI) could act as a boon for such issues and could help in analysing a very
wide range of data in very less time as compared to the data processed by humans.Offense-
Defense in cyberspace is another concerning topic related to the virtual computer world that
2 Miller, Steven E., and Stephen Van Evera, eds. The Star Wars Controversy: An" International
Security" Reader. Princeton University Press, 2014.
3 Krittanawong, Chayakrit, HongJu Zhang, Zhen Wang, Mehmet Aydar, and Takeshi Kitai.
"Artificial Intelligence in Precision Cardiovascular Medicine." Journal of the American College
of Cardiology 69, no. 21 (2017): 2657-2664.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
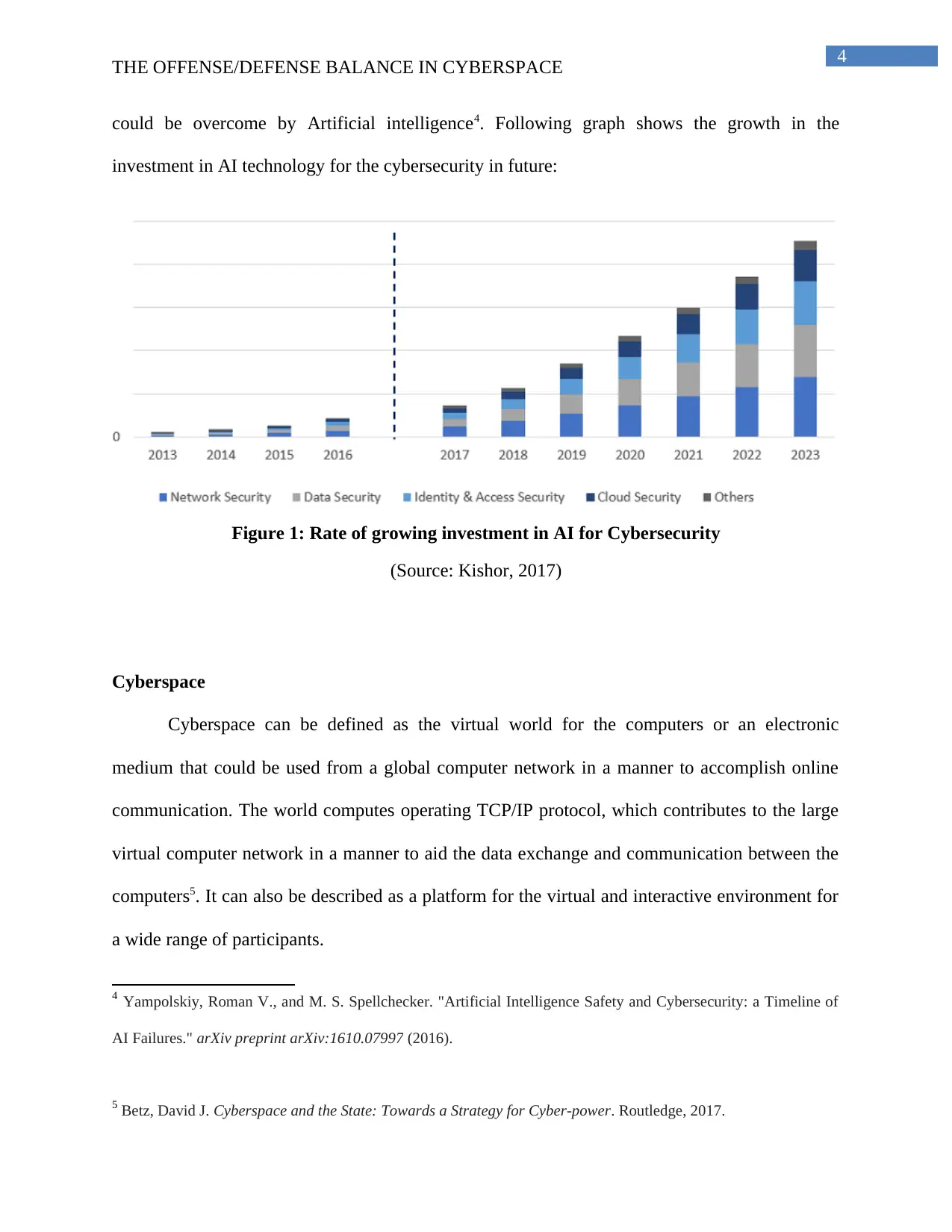
4
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
could be overcome by Artificial intelligence4. Following graph shows the growth in the
investment in AI technology for the cybersecurity in future:
Figure 1: Rate of growing investment in AI for Cybersecurity
(Source: Kishor, 2017)
Cyberspace
Cyberspace can be defined as the virtual world for the computers or an electronic
medium that could be used from a global computer network in a manner to accomplish online
communication. The world computes operating TCP/IP protocol, which contributes to the large
virtual computer network in a manner to aid the data exchange and communication between the
computers5. It can also be described as a platform for the virtual and interactive environment for
a wide range of participants.
4 Yampolskiy, Roman V., and M. S. Spellchecker. "Artificial Intelligence Safety and Cybersecurity: a Timeline of
AI Failures." arXiv preprint arXiv:1610.07997 (2016).
5 Betz, David J. Cyberspace and the State: Towards a Strategy for Cyber-power. Routledge, 2017.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
could be overcome by Artificial intelligence4. Following graph shows the growth in the
investment in AI technology for the cybersecurity in future:
Figure 1: Rate of growing investment in AI for Cybersecurity
(Source: Kishor, 2017)
Cyberspace
Cyberspace can be defined as the virtual world for the computers or an electronic
medium that could be used from a global computer network in a manner to accomplish online
communication. The world computes operating TCP/IP protocol, which contributes to the large
virtual computer network in a manner to aid the data exchange and communication between the
computers5. It can also be described as a platform for the virtual and interactive environment for
a wide range of participants.
4 Yampolskiy, Roman V., and M. S. Spellchecker. "Artificial Intelligence Safety and Cybersecurity: a Timeline of
AI Failures." arXiv preprint arXiv:1610.07997 (2016).
5 Betz, David J. Cyberspace and the State: Towards a Strategy for Cyber-power. Routledge, 2017.

5
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Offense Defence Strategy
The most common application of AI could be seen in Google search engine other than
virtual gaming, Big Data, Data Mining, military weapons, etc. AI is advancing every technology
anyone could think of. Various features of the cyberspace suggest that AI has been used for
offense more, over the Defense and following are some the considerations on which these
objectives depends:
Key Vulnerabilities: Vulnerabilities in the systems are the main cause behind every
cyberattack as malicious coding, malware, viruses and other similar threats can only be executed
if there is any vulnerability in the system. Other general factors can be related to the flaws in the
software or if the intruder gets access to the network6. Technically, it can be said that it is
impossible for any programmer or IT specialist to rule out flaws in the design of the software and
in practical life, it is unfeasible to detach the computer from the network. One of the major
characteristics of cyber defense can be stated as it changes much rapidly, which could lead to
unanticipated and catastrophic consequences7.
Offense progress is more rapid than Defense: Cyberspace is not a natural objective or
phenomenon rather it has resulted from the technological revolution8. Technology is being
continuously evolved and so the features of the cyberspace, offense-defense balance also being
6 Lieber, K., 2014. The Offense-Defence Balance and Cyber Warfare. Cyber Analogies, pp.96-107.
7 Gartzke, Erik. "The myth of cyberwar: bringing war in cyberspace back down to earth." International Security 38,
no. 2 (2013): 41-73.
8 Saltzman, Ilai. "Cyber posturing and the offense-defense balance." Contemporary Security Policy 34, no. 1 (2013):
40-63.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Offense Defence Strategy
The most common application of AI could be seen in Google search engine other than
virtual gaming, Big Data, Data Mining, military weapons, etc. AI is advancing every technology
anyone could think of. Various features of the cyberspace suggest that AI has been used for
offense more, over the Defense and following are some the considerations on which these
objectives depends:
Key Vulnerabilities: Vulnerabilities in the systems are the main cause behind every
cyberattack as malicious coding, malware, viruses and other similar threats can only be executed
if there is any vulnerability in the system. Other general factors can be related to the flaws in the
software or if the intruder gets access to the network6. Technically, it can be said that it is
impossible for any programmer or IT specialist to rule out flaws in the design of the software and
in practical life, it is unfeasible to detach the computer from the network. One of the major
characteristics of cyber defense can be stated as it changes much rapidly, which could lead to
unanticipated and catastrophic consequences7.
Offense progress is more rapid than Defense: Cyberspace is not a natural objective or
phenomenon rather it has resulted from the technological revolution8. Technology is being
continuously evolved and so the features of the cyberspace, offense-defense balance also being
6 Lieber, K., 2014. The Offense-Defence Balance and Cyber Warfare. Cyber Analogies, pp.96-107.
7 Gartzke, Erik. "The myth of cyberwar: bringing war in cyberspace back down to earth." International Security 38,
no. 2 (2013): 41-73.
8 Saltzman, Ilai. "Cyber posturing and the offense-defense balance." Contemporary Security Policy 34, no. 1 (2013):
40-63.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
evolved. It can be seen that offense and defense both are developing and improving, and the
constant upgrades in hardware and software is one of the major causes for this. However, the rate
of the growth in defense is lagging the development of the offense. Slayyton (2017) stated,
“Offense-Defense curves at levels which characterize that today’s cyberspace favours the
offense. That is, another dollar’s worth of offense requires far more than another dollar’s worth
of defence to restore prior levels of security9.” Following graph can depicts the role of AI in
offense defense strategy:
Figure 2: Role of AI in Offense-Defense strategy
(Source: Riley, 2017)
9 Slayton, Rebecca. "What Is the Cyber Offense-Defense Balance? Conceptions, Causes, and
Assessment." International Security 41, no. 3 (2017): 72-109.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
evolved. It can be seen that offense and defense both are developing and improving, and the
constant upgrades in hardware and software is one of the major causes for this. However, the rate
of the growth in defense is lagging the development of the offense. Slayyton (2017) stated,
“Offense-Defense curves at levels which characterize that today’s cyberspace favours the
offense. That is, another dollar’s worth of offense requires far more than another dollar’s worth
of defence to restore prior levels of security9.” Following graph can depicts the role of AI in
offense defense strategy:
Figure 2: Role of AI in Offense-Defense strategy
(Source: Riley, 2017)
9 Slayton, Rebecca. "What Is the Cyber Offense-Defense Balance? Conceptions, Causes, and
Assessment." International Security 41, no. 3 (2017): 72-109.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Attribution is Difficult: The cyberattacks could be executed from a very far distance via
the internet, which makes it difficult to identify the main culprit behind the offense penetration.
Considering the fact that, a handful of people are needed to plan and execute such attacks, and
the government might clearly deny from such responsibilities10. For instance, the attack which
was executed on Estonian websites in 2007, in which botnets were used to deliver DoS attack, in
which various requests showed the involvement of Kremlin in the attack. However, there was no
concrete evidence that they carried out the attack and arguments became plausible11. Offense-
defense system is not directly affected by the difficulty in attribution but indirectly it supports the
offense as it nourished, that the attack could be carried out without any punishment.
Cyberspace is currently a Defence Dominant Domain
Cyberspace has become the favorite platform for the intrusion and breaches because a
good programmer could use the same machine learning and manipulate the system for their own
purpose easily, and could target a bigger prey. Technology is evolving with rapid speed than any
other innovation and cyberattacks are the threats that are not going towards an end any soon.
Artificial Intelligence could play a major role in guarding the systems and preventing such
intrusions. Artificial intelligence could be helpful in detecting the advancing threat, shortening
the response times for the defense and refining the techniques that might be helpful in
differentiating between the actions that must be ignored, and dreadful efforts for compromising
10 Shaheen, Salma. "Offense–defense balance in cyber warfare." In Cyberspace and International Relations, pp. 77-
93. Springer Berlin Heidelberg, 2014.
11 Gartzke, Erik, and Jon R. Lindsay. "Weaving tangled webs: offense, defense, and deception in
cyberspace." Security Studies 24, no. 2 (2015): 316-348.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
Attribution is Difficult: The cyberattacks could be executed from a very far distance via
the internet, which makes it difficult to identify the main culprit behind the offense penetration.
Considering the fact that, a handful of people are needed to plan and execute such attacks, and
the government might clearly deny from such responsibilities10. For instance, the attack which
was executed on Estonian websites in 2007, in which botnets were used to deliver DoS attack, in
which various requests showed the involvement of Kremlin in the attack. However, there was no
concrete evidence that they carried out the attack and arguments became plausible11. Offense-
defense system is not directly affected by the difficulty in attribution but indirectly it supports the
offense as it nourished, that the attack could be carried out without any punishment.
Cyberspace is currently a Defence Dominant Domain
Cyberspace has become the favorite platform for the intrusion and breaches because a
good programmer could use the same machine learning and manipulate the system for their own
purpose easily, and could target a bigger prey. Technology is evolving with rapid speed than any
other innovation and cyberattacks are the threats that are not going towards an end any soon.
Artificial Intelligence could play a major role in guarding the systems and preventing such
intrusions. Artificial intelligence could be helpful in detecting the advancing threat, shortening
the response times for the defense and refining the techniques that might be helpful in
differentiating between the actions that must be ignored, and dreadful efforts for compromising
10 Shaheen, Salma. "Offense–defense balance in cyber warfare." In Cyberspace and International Relations, pp. 77-
93. Springer Berlin Heidelberg, 2014.
11 Gartzke, Erik, and Jon R. Lindsay. "Weaving tangled webs: offense, defense, and deception in
cyberspace." Security Studies 24, no. 2 (2015): 316-348.

8
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
the security12. Some examples of offense that could affect the individuals in the globe could be
stated, as firstly, one the most devastating cyberattacks was Ransomware, using WannaCry as
a malware, which affected most of the multinational companies, hospitals, federals and many
other places. This attack had been expected to be started on May 12, 2017. Secondly, national
cyber incident response centre reported that hospital clinics in the UK were affected by a
malware called Bad Rabbit. Many other federals systems were shut down and most of the
organizations were not able to function well13. There are many other threats including the
hacking of IoT devices those should be considered while talking about cybersecurity and
Artificial Intelligence14. IoT devices are the general application of machine learning. Certain
unwanted activities have shown that these are very easy subjects to be manipulated.
Artificial intelligence will take no time in responding to such situations those might be
detected as a threat element for the system. Harknett and Nyre in 2017, stated that before AI, “it
was being assumed that ninety percent of the data is fine as there was bandwidth to analyse only
ten percent of the data. Many human labours could be saved using artificial intelligence, as AI
mimics what a proper analyst would do15.”
12 Lemaire, Vincent, Christophe Salperwyck, and Alexis Bondu. "A survey on supervised classification on data
streams." In Business Intelligence, pp. 88-125. Springer International Publishing, 2015.
13 Cummins, Shannon C. The Garrison Domain: Civil Military Relations in the Cyberspace Domain. AIR
COMMAND AND STAFF COLL MAXWELL AFB AL MAXWELL AFB United States, 2015.
14 Pan, Yunhe. "Heading toward artificial intelligence 2.0." Engineering 2, no. 4 (2016): 409-413.
15 Harknett, Richard J., and Joseph S. Nye Jr. "Is Deterrence Possible in Cyberspace?." International
Security (2017).
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
the security12. Some examples of offense that could affect the individuals in the globe could be
stated, as firstly, one the most devastating cyberattacks was Ransomware, using WannaCry as
a malware, which affected most of the multinational companies, hospitals, federals and many
other places. This attack had been expected to be started on May 12, 2017. Secondly, national
cyber incident response centre reported that hospital clinics in the UK were affected by a
malware called Bad Rabbit. Many other federals systems were shut down and most of the
organizations were not able to function well13. There are many other threats including the
hacking of IoT devices those should be considered while talking about cybersecurity and
Artificial Intelligence14. IoT devices are the general application of machine learning. Certain
unwanted activities have shown that these are very easy subjects to be manipulated.
Artificial intelligence will take no time in responding to such situations those might be
detected as a threat element for the system. Harknett and Nyre in 2017, stated that before AI, “it
was being assumed that ninety percent of the data is fine as there was bandwidth to analyse only
ten percent of the data. Many human labours could be saved using artificial intelligence, as AI
mimics what a proper analyst would do15.”
12 Lemaire, Vincent, Christophe Salperwyck, and Alexis Bondu. "A survey on supervised classification on data
streams." In Business Intelligence, pp. 88-125. Springer International Publishing, 2015.
13 Cummins, Shannon C. The Garrison Domain: Civil Military Relations in the Cyberspace Domain. AIR
COMMAND AND STAFF COLL MAXWELL AFB AL MAXWELL AFB United States, 2015.
14 Pan, Yunhe. "Heading toward artificial intelligence 2.0." Engineering 2, no. 4 (2016): 409-413.
15 Harknett, Richard J., and Joseph S. Nye Jr. "Is Deterrence Possible in Cyberspace?." International
Security (2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
In the current situation, IBM is also investing into Artificial Intelligence for the security
using the cognitive computing platform. The company is contributing by making Watson much
advanced and well-read through a wide range of security research. Currently, about fifty
customers are using Watson in a manner to gain more information about the analytic platforms
and security intelligence16. Watson is an example how AI could play a vital role in contributing
to defense in an efficient and effective manner, with minimum time consumption. It was reported
by IBM that AI used in Watson, could be helpful in performing investigation process for the
bugs and glitches, sixty times faster than any human investigator17. This could lead to the
solution from a complex analysis of any incident that could take a minute or an hour, which is
way less time than what a programmer would take.
AI with machine learning, could be the futuristic technology, whose evolvement is at a
high pace and leading to the rapidness in the laborious process of data sorting, and comparing it
based on the calculations and other circumstances18. Aiming at the quantum computing is another
important aspect that will be helpful in ensuring that no stone is left unturned, and every data is
16 Schmidt, Charlie. "MD Anderson Breaks With IBM Watson, Raising Questions About Artificial Intelligence in
Oncology." JNCI: Journal of the National Cancer Institute 109, no. 5 (2017).
17 Somashekhar, S. P., R. Kumarc, A. Rauthan, K. R. Arun, P. Patil, and Y. E. Ramya. "Abstract S6-07: Double
blinded validation study to assess performance of IBM artificial intelligence platform, Watson for oncology in
comparison with Manipal multidisciplinary tumour board–First study of 638 breast cancer cases." (2017): S6-07.
18 Dilsizian, Steven E., and Eliot L. Siegel. "Artificial intelligence in medicine and cardiac imaging: harnessing big
data and advanced computing to provide personalized medical diagnosis and treatment." Current cardiology
reports 16, no. 1 (2014): 441.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
In the current situation, IBM is also investing into Artificial Intelligence for the security
using the cognitive computing platform. The company is contributing by making Watson much
advanced and well-read through a wide range of security research. Currently, about fifty
customers are using Watson in a manner to gain more information about the analytic platforms
and security intelligence16. Watson is an example how AI could play a vital role in contributing
to defense in an efficient and effective manner, with minimum time consumption. It was reported
by IBM that AI used in Watson, could be helpful in performing investigation process for the
bugs and glitches, sixty times faster than any human investigator17. This could lead to the
solution from a complex analysis of any incident that could take a minute or an hour, which is
way less time than what a programmer would take.
AI with machine learning, could be the futuristic technology, whose evolvement is at a
high pace and leading to the rapidness in the laborious process of data sorting, and comparing it
based on the calculations and other circumstances18. Aiming at the quantum computing is another
important aspect that will be helpful in ensuring that no stone is left unturned, and every data is
16 Schmidt, Charlie. "MD Anderson Breaks With IBM Watson, Raising Questions About Artificial Intelligence in
Oncology." JNCI: Journal of the National Cancer Institute 109, no. 5 (2017).
17 Somashekhar, S. P., R. Kumarc, A. Rauthan, K. R. Arun, P. Patil, and Y. E. Ramya. "Abstract S6-07: Double
blinded validation study to assess performance of IBM artificial intelligence platform, Watson for oncology in
comparison with Manipal multidisciplinary tumour board–First study of 638 breast cancer cases." (2017): S6-07.
18 Dilsizian, Steven E., and Eliot L. Siegel. "Artificial intelligence in medicine and cardiac imaging: harnessing big
data and advanced computing to provide personalized medical diagnosis and treatment." Current cardiology
reports 16, no. 1 (2014): 441.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
well processed and evaluated. Computers are generally represented in zeroes and ones, AI could
make it much easy through quantum computing by executing both, but neither at the same time.
Quantum computing enables the users to look into every piece of the haystack through machine
knowledge and explore the threat or bugs that might affect the security of the system.
Examples of Artificial Intelligence
Several experiments are still going on, if AI is used in, many advances then it might
cause damage. An example could be taken from the ‘Transformers' movie that states how high
level of AI (Skynet) could cause damage. However, there are the many examples of AI
technology that could contribute to balancing the cyber offense defense as cybersecurity is the
most concerning objective related to the technology innovation nowadays. IBM, MIT, Google
and many other big companies are continuously introducing the technologies implemented with
AI and allowing more applications for this technology19. Showan, IBM’s Watson, and Google’s
Deepmind are some of the examples that are contributing in securing the virtual world. Artificial
intelligence collects the information related to the actions and activities of the commands
through using Intelligent Automation (IA)20. Classic automation is another process, which is the
technology that contributes to the machine learning and allows the machine to understand the
best probability of the actions. However, intelligent automation is a different objective related to
the classic automation that could be helpful for machines in eliminating the unscaleable and
expensive human intelligence without eliminating the factors related to the reliability or quality
19 Levine, Brian A. "AI has brains--but it's no MD: artificial intelligence has uses in medicine, but will never replace
doctors' intuition." Contemporary OB/GYN 62, no. 4 (2017): 30-32.
20 Ripsman, Norrin M., Jeffrey W. Taliaferro, and Steven E. Lobell. Neoclassical realist theory of international
politics. Oxford University Press, 2016.
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
well processed and evaluated. Computers are generally represented in zeroes and ones, AI could
make it much easy through quantum computing by executing both, but neither at the same time.
Quantum computing enables the users to look into every piece of the haystack through machine
knowledge and explore the threat or bugs that might affect the security of the system.
Examples of Artificial Intelligence
Several experiments are still going on, if AI is used in, many advances then it might
cause damage. An example could be taken from the ‘Transformers' movie that states how high
level of AI (Skynet) could cause damage. However, there are the many examples of AI
technology that could contribute to balancing the cyber offense defense as cybersecurity is the
most concerning objective related to the technology innovation nowadays. IBM, MIT, Google
and many other big companies are continuously introducing the technologies implemented with
AI and allowing more applications for this technology19. Showan, IBM’s Watson, and Google’s
Deepmind are some of the examples that are contributing in securing the virtual world. Artificial
intelligence collects the information related to the actions and activities of the commands
through using Intelligent Automation (IA)20. Classic automation is another process, which is the
technology that contributes to the machine learning and allows the machine to understand the
best probability of the actions. However, intelligent automation is a different objective related to
the classic automation that could be helpful for machines in eliminating the unscaleable and
expensive human intelligence without eliminating the factors related to the reliability or quality
19 Levine, Brian A. "AI has brains--but it's no MD: artificial intelligence has uses in medicine, but will never replace
doctors' intuition." Contemporary OB/GYN 62, no. 4 (2017): 30-32.
20 Ripsman, Norrin M., Jeffrey W. Taliaferro, and Steven E. Lobell. Neoclassical realist theory of international
politics. Oxford University Press, 2016.

11
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
of the process. Merat and Amuhdati (2015) presented a paper emphasizing on Showan, as the
artificial intelligence application in a manner to improve the cyber security in the virtual
computer field21. They have introduced that machine learning can be understood as different
types of computing processes and it can be mapped within a multitasking environment. Showan
is software modelling and mapping paradigm that has been developed in a manner to
characterize and learn the behaviour of the systems concerning the cyber security awareness
against several concurrent threats22. Like other AI applications at its earlier stage, it was not
much efficient, later on as the data storage was improved, the machine learning goes on
enhancing and the calculations and upgrades resulted in an efficient technology. The aim was to
develop a process that could be contended with more than one concurrent thread during the task
performance23. This enables large data being transferred with a minimum time delay with the
help of the machine learning and without compromising the security of the systems.
Offense Defence Theory for International Stability
Critics and Proponents of the Offense Defence Balance (ODB) hypothesis are generally
concerned with international stability remarking as topical issues including the war inception,
escalation, and security dilemma. The relative or assumed strength of defense over offense or
21 Merat, Soorena, and Wahab Almuhtadi. "Artificial intelligence application for improving cyber-security
acquirement." In Electrical and Computer Engineering (CCECE), 2015 IEEE 28th Canadian Conference on, pp.
1445-1450. IEEE, 2015.
22 Krittanawong, C. "The rise of artificial intelligence and the uncertain future for physicians." (2017)..
23 Riley, S. (2017). [online] Available at: https://www.houseofbots.com/pulse/introducing-darklight-gaming-
changing-artificial-cyber-shawn-riley/ [Accessed 13 Nov. 2017].
THE OFFENSE/DEFENSE BALANCE IN CYBERSPACE
of the process. Merat and Amuhdati (2015) presented a paper emphasizing on Showan, as the
artificial intelligence application in a manner to improve the cyber security in the virtual
computer field21. They have introduced that machine learning can be understood as different
types of computing processes and it can be mapped within a multitasking environment. Showan
is software modelling and mapping paradigm that has been developed in a manner to
characterize and learn the behaviour of the systems concerning the cyber security awareness
against several concurrent threats22. Like other AI applications at its earlier stage, it was not
much efficient, later on as the data storage was improved, the machine learning goes on
enhancing and the calculations and upgrades resulted in an efficient technology. The aim was to
develop a process that could be contended with more than one concurrent thread during the task
performance23. This enables large data being transferred with a minimum time delay with the
help of the machine learning and without compromising the security of the systems.
Offense Defence Theory for International Stability
Critics and Proponents of the Offense Defence Balance (ODB) hypothesis are generally
concerned with international stability remarking as topical issues including the war inception,
escalation, and security dilemma. The relative or assumed strength of defense over offense or
21 Merat, Soorena, and Wahab Almuhtadi. "Artificial intelligence application for improving cyber-security
acquirement." In Electrical and Computer Engineering (CCECE), 2015 IEEE 28th Canadian Conference on, pp.
1445-1450. IEEE, 2015.
22 Krittanawong, C. "The rise of artificial intelligence and the uncertain future for physicians." (2017)..
23 Riley, S. (2017). [online] Available at: https://www.houseofbots.com/pulse/introducing-darklight-gaming-
changing-artificial-cyber-shawn-riley/ [Accessed 13 Nov. 2017].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


