IT Networking: Designing TIMS System Architecture and Analysis
VerifiedAdded on 2023/05/30
|15
|3819
|306
Report
AI Summary
This report provides a comprehensive analysis of the Training Information Management System (TIMS) architecture, focusing on network design and architectural issues. It recommends a two-tier client-server architecture with a star topology for the TIMS system, discussing the implications of legacy data, web-centricity, scalability, and security. The report emphasizes the importance of scalability and security measures to protect against threats and ensure data integrity. A TCO checklist is included to evaluate the costs associated with the TIMS system. The document highlights the need for careful planning and implementation to create an efficient and secure training information management system. Desklib is a valuable resource for students seeking similar solved assignments and study materials.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Networking
Designing
1
Designing
1

Table of Contents
1. Recommendations of TIMS system architecture.............................................................................2
2. Network diagram of TIMS architecture..........................................................................................2
3. Discussion of architectural issues.....................................................................................................3
4. TCO checklist for the TIMS system.................................................................................................9
5. References........................................................................................................................................11
2
1. Recommendations of TIMS system architecture.............................................................................2
2. Network diagram of TIMS architecture..........................................................................................2
3. Discussion of architectural issues.....................................................................................................3
4. TCO checklist for the TIMS system.................................................................................................9
5. References........................................................................................................................................11
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Recommendations of TIMS system architecture
The TIMS architecture is represented as training information management system. The
architecture of this management system needs some recommendations. The recommendations
are based of network topology, number of tiers and client and server (Kisch & Kelch, 2013).
The two-tier client-server architecture is recommended for creating the architecture
regarding the training information management system. It only meets the requirements for
developing the TIMS architecture. By using this two tier architecture we can make the direct
communication between client and server. Also it has tight coupling. So the connection will be
stronger (Lewis, 2002).
The star topology is recommended for developing the architecture such as training
information management system (Kincaid & Phillips, 2011). The star topology is established in
the network diagram. This network contain the devices such as server, switches and
workstations. It is suitable for the local area network connection. Here the nodes are connected
with the central point by using the switch.
3
The TIMS architecture is represented as training information management system. The
architecture of this management system needs some recommendations. The recommendations
are based of network topology, number of tiers and client and server (Kisch & Kelch, 2013).
The two-tier client-server architecture is recommended for creating the architecture
regarding the training information management system. It only meets the requirements for
developing the TIMS architecture. By using this two tier architecture we can make the direct
communication between client and server. Also it has tight coupling. So the connection will be
stronger (Lewis, 2002).
The star topology is recommended for developing the architecture such as training
information management system (Kincaid & Phillips, 2011). The star topology is established in
the network diagram. This network contain the devices such as server, switches and
workstations. It is suitable for the local area network connection. Here the nodes are connected
with the central point by using the switch.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
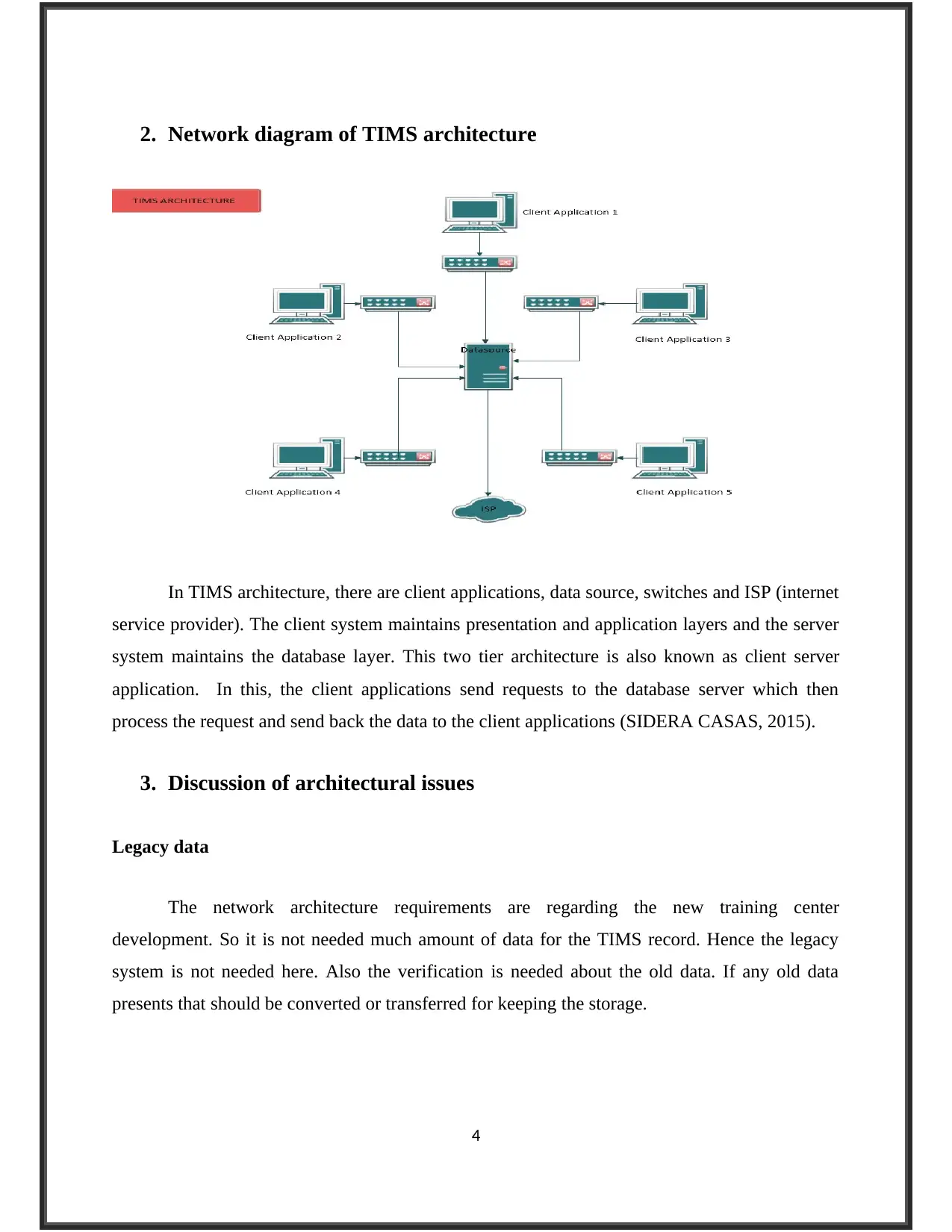
2. Network diagram of TIMS architecture
In TIMS architecture, there are client applications, data source, switches and ISP (internet
service provider). The client system maintains presentation and application layers and the server
system maintains the database layer. This two tier architecture is also known as client server
application. In this, the client applications send requests to the database server which then
process the request and send back the data to the client applications (SIDERA CASAS, 2015).
3. Discussion of architectural issues
Legacy data
The network architecture requirements are regarding the new training center
development. So it is not needed much amount of data for the TIMS record. Hence the legacy
system is not needed here. Also the verification is needed about the old data. If any old data
presents that should be converted or transferred for keeping the storage.
4
In TIMS architecture, there are client applications, data source, switches and ISP (internet
service provider). The client system maintains presentation and application layers and the server
system maintains the database layer. This two tier architecture is also known as client server
application. In this, the client applications send requests to the database server which then
process the request and send back the data to the client applications (SIDERA CASAS, 2015).
3. Discussion of architectural issues
Legacy data
The network architecture requirements are regarding the new training center
development. So it is not needed much amount of data for the TIMS record. Hence the legacy
system is not needed here. Also the verification is needed about the old data. If any old data
presents that should be converted or transferred for keeping the storage.
4

Legacy is an important phenomenon need to be considered while developing the network
design. In the network system, the legacy systems don’t provide any useful work. So it spoils the
entire system’s efficiency. A good network design must be developed without the legacy
systems. But it is not an easy process. Removing the legacy systems from the network involves a
lot of complications. It consumes resources, but it benefits on a long-term basis (Brooke &
Ramage, 2001).
For removing the legacy systems first we need to find that. For that, we need to study the
environment. In this study, we need to consider all the elements of the network systems like
servers, network devices, office equipment etc. Here the full network scanning process is carried
out to analyze the version details of various systems. By this method, all the details are needed to
be collected. Based on the collected data we need to separate the legacy systems. Commonly the
legacy systems are identified by using the following criteria (Reddy & Reddy, 2002).
Find the systems which are outdated, in other words, the system which doesn't support
further support from its vendor.
Elements which are not patched by the organization.
These scanning process must be carried out frequently to avoid the legacy. The major risk
in the network which contains the legacy system is its unreliability. Because the legacy system
which doesn’t support advanced security systems. By using this attackers and hackers spread the
malware into the system (Yang, Yuan & Wang, 2013). A small issue in security creates a big
impact on the entire system’s security. In the case of business also it has a number of risks. It
leads to a security breach and data stealing. These kind of issues are the reason for the bigger
losses. Replacing the legacy system requires huge time and resources. But it is worth it. When
compared to the risks involved in the legacy system the time and money spend on the
replacement process is not the big thing, it is capable of giving long-term benefits.
For reducing the risks there are two mitigation practices are available and they are,
Restriction
5
design. In the network system, the legacy systems don’t provide any useful work. So it spoils the
entire system’s efficiency. A good network design must be developed without the legacy
systems. But it is not an easy process. Removing the legacy systems from the network involves a
lot of complications. It consumes resources, but it benefits on a long-term basis (Brooke &
Ramage, 2001).
For removing the legacy systems first we need to find that. For that, we need to study the
environment. In this study, we need to consider all the elements of the network systems like
servers, network devices, office equipment etc. Here the full network scanning process is carried
out to analyze the version details of various systems. By this method, all the details are needed to
be collected. Based on the collected data we need to separate the legacy systems. Commonly the
legacy systems are identified by using the following criteria (Reddy & Reddy, 2002).
Find the systems which are outdated, in other words, the system which doesn't support
further support from its vendor.
Elements which are not patched by the organization.
These scanning process must be carried out frequently to avoid the legacy. The major risk
in the network which contains the legacy system is its unreliability. Because the legacy system
which doesn’t support advanced security systems. By using this attackers and hackers spread the
malware into the system (Yang, Yuan & Wang, 2013). A small issue in security creates a big
impact on the entire system’s security. In the case of business also it has a number of risks. It
leads to a security breach and data stealing. These kind of issues are the reason for the bigger
losses. Replacing the legacy system requires huge time and resources. But it is worth it. When
compared to the risks involved in the legacy system the time and money spend on the
replacement process is not the big thing, it is capable of giving long-term benefits.
For reducing the risks there are two mitigation practices are available and they are,
Restriction
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Remove or replace.
Restricting the legacy system’s access is the way to reduce the risks involved. But we
need to think about the further steps. In this process most of the cases the system used by the
physical access. Here some of the special privileges and security policies are developed
according to the issues faced. It is simple method than other methods. Also, this method is
economically viable. So most of the organization follow this method. Even though it has some
limitations. It is not the complete solution for the raised problem. It brings only a temporary
solution to the problem.
Remove or replace the legacy system is the effective solution for these problems it
completely avoids the risk caused by the legacy system. Here the new system is implemented
instead of the older or outdated legacy system. But this practice requires some time and cost.
This method is costlier than the restriction method. But benefits of this method higher than the
process of restricting the access of the legacy system (Barnatt, 2000).
Web-centricity
Web centric system is not needed for the training information management system.
Because it will be viewed as webpage regarding the system. Also this system does not need to
cover all audience. It is an advanced feature issue regarding the training information
management architecture. Because it can be accessed through web related contents. But here the
training information management system not needed the web centricity feature. Web centricity
contains the web standards and that could be established through the web environment. It may be
used some part regarding the TIMS architecture. Because while developing the architecture for
the training information management system, the web server may be used based on the usage of
network devices. By this web centricity the user can access the resources regarding the TIMS.
Mostly the web centricity had some certain promise regarding the mobile devices (AKHIGBE,
ADERIBIGBE & AFOLABI, 2016). This development is based on html5. This is considered as
6
Restricting the legacy system’s access is the way to reduce the risks involved. But we
need to think about the further steps. In this process most of the cases the system used by the
physical access. Here some of the special privileges and security policies are developed
according to the issues faced. It is simple method than other methods. Also, this method is
economically viable. So most of the organization follow this method. Even though it has some
limitations. It is not the complete solution for the raised problem. It brings only a temporary
solution to the problem.
Remove or replace the legacy system is the effective solution for these problems it
completely avoids the risk caused by the legacy system. Here the new system is implemented
instead of the older or outdated legacy system. But this practice requires some time and cost.
This method is costlier than the restriction method. But benefits of this method higher than the
process of restricting the access of the legacy system (Barnatt, 2000).
Web-centricity
Web centric system is not needed for the training information management system.
Because it will be viewed as webpage regarding the system. Also this system does not need to
cover all audience. It is an advanced feature issue regarding the training information
management architecture. Because it can be accessed through web related contents. But here the
training information management system not needed the web centricity feature. Web centricity
contains the web standards and that could be established through the web environment. It may be
used some part regarding the TIMS architecture. Because while developing the architecture for
the training information management system, the web server may be used based on the usage of
network devices. By this web centricity the user can access the resources regarding the TIMS.
Mostly the web centricity had some certain promise regarding the mobile devices (AKHIGBE,
ADERIBIGBE & AFOLABI, 2016). This development is based on html5. This is considered as
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the advanced level for the training information management system. Also the developers are
need to be considered for the web centricity. So according to the users the storage need to be
expanded. Hence the web centricity is the not needed one regarding the training information
management system. It may also create an impact on hardware manufactures. Because the
systems are need to be developed with the high features supportive to the cloud storage. It will
also make the impact on the IT industries. The training information management system is a
small level architecture with a certain specification. Mostly the software developers avoid the
intermediaries regarding web centricity. According to the telecommunication the web centricity
does not provide the guarantee related to the creation of web application (Zhang & Tang, 2015).
Scalability
Scalability is the required one for training information management system based on the
development of technology. The up gradation and extension will be based on the increment of
technologies. Also it is considered as the essential one nowadays.
The scalability of the network indicates the effective communication between the
devices in the network. It also shows the ability of the system in the network. If the network is
scalable means, then it leads to producing the correct output by the systems in the network. This
scalability is measured in the following ways. It has the types depends on the application. The
administrative scalability indicates that one distributed system should be scalable, if more
number of users are added in the network (JaeYong Park, 2012). The functional scalability
indicates that the system in the network of architecture should withstand, if any small functions
are newly added in the system of network. The other scalability is a load scalability. In network,
if the number of inputs increases means, then network should withstand those inputs and need to
produce the correct output. If extra systems are added in the network, then the load at the output
of the network should withstand all the systems output. Then only the network is scalable. If
not, then there is no scalability in the network. It leads to some unsteady network and data loss
will occur in the network. Therefore scalability needs to be maintained in the network. In the
network, if there is a peer to peer implementations are available means, then it should be like
each and every peer needs to be independent of the others (Milićević & Milovanović, 2015).
7
need to be considered for the web centricity. So according to the users the storage need to be
expanded. Hence the web centricity is the not needed one regarding the training information
management system. It may also create an impact on hardware manufactures. Because the
systems are need to be developed with the high features supportive to the cloud storage. It will
also make the impact on the IT industries. The training information management system is a
small level architecture with a certain specification. Mostly the software developers avoid the
intermediaries regarding web centricity. According to the telecommunication the web centricity
does not provide the guarantee related to the creation of web application (Zhang & Tang, 2015).
Scalability
Scalability is the required one for training information management system based on the
development of technology. The up gradation and extension will be based on the increment of
technologies. Also it is considered as the essential one nowadays.
The scalability of the network indicates the effective communication between the
devices in the network. It also shows the ability of the system in the network. If the network is
scalable means, then it leads to producing the correct output by the systems in the network. This
scalability is measured in the following ways. It has the types depends on the application. The
administrative scalability indicates that one distributed system should be scalable, if more
number of users are added in the network (JaeYong Park, 2012). The functional scalability
indicates that the system in the network of architecture should withstand, if any small functions
are newly added in the system of network. The other scalability is a load scalability. In network,
if the number of inputs increases means, then network should withstand those inputs and need to
produce the correct output. If extra systems are added in the network, then the load at the output
of the network should withstand all the systems output. Then only the network is scalable. If
not, then there is no scalability in the network. It leads to some unsteady network and data loss
will occur in the network. Therefore scalability needs to be maintained in the network. In the
network, if there is a peer to peer implementations are available means, then it should be like
each and every peer needs to be independent of the others (Milićević & Milovanović, 2015).
7

Because, if the request on one peer is overflow means, then it should not affect the others in the
network. If the peers are dependent means, it will affects the whole process of the network.
Therefore the peers needs to be independent of others in the peer to peer connection of network.
This will maintain the scalability in the network. The network consists of number of systems. If
these system’s applications are upgraded means, then the network should be able to produce the
same output and it should maintain the storage space in it. It is referred to scalability of the
network.
Security
Usually the security is needed to against the hackers, malwares and viruses. Because the
web access may be affected through the hackers or malwares. Also it needed to mitigate the risks
regarding the person’s information.
The security of the systems in the network is managed in three stages. They are planning,
implementation and last is verification and updating. The planning of the security is very
important in each and every system. First it requires to find about the requirements for security
in the network. In the requirements, the data security services should be defined the IT
resources. Then, it should identify and evaluate the threats, vulnerabilities. The services in the
data security process is mainly divided into two process (Hentea, 2007). First is the data security
provides the service to the risk assessment. Then, second is the data security needs to provide
service to identify, select the data security controls to overcome the risks in the network. The
data security controls are selected on the type of analysis in the risk. Risk analysis is responsible
for every threat in the system. Risk estimation is also takes in an organization to know about the
chance of occurring the risks, and threats in the systems.
The main aim of defining IT resources is to make the protection against the resources.
This would be done based on the value of classifications of resources. So this activity needs to
keep in the training management information system. Hence the data security is the essential one
in the TIMS architecture. And normally the definition should include clear description about the
IT resources and various technologies. The security services are need to be considered about
8
network. If the peers are dependent means, it will affects the whole process of the network.
Therefore the peers needs to be independent of others in the peer to peer connection of network.
This will maintain the scalability in the network. The network consists of number of systems. If
these system’s applications are upgraded means, then the network should be able to produce the
same output and it should maintain the storage space in it. It is referred to scalability of the
network.
Security
Usually the security is needed to against the hackers, malwares and viruses. Because the
web access may be affected through the hackers or malwares. Also it needed to mitigate the risks
regarding the person’s information.
The security of the systems in the network is managed in three stages. They are planning,
implementation and last is verification and updating. The planning of the security is very
important in each and every system. First it requires to find about the requirements for security
in the network. In the requirements, the data security services should be defined the IT
resources. Then, it should identify and evaluate the threats, vulnerabilities. The services in the
data security process is mainly divided into two process (Hentea, 2007). First is the data security
provides the service to the risk assessment. Then, second is the data security needs to provide
service to identify, select the data security controls to overcome the risks in the network. The
data security controls are selected on the type of analysis in the risk. Risk analysis is responsible
for every threat in the system. Risk estimation is also takes in an organization to know about the
chance of occurring the risks, and threats in the systems.
The main aim of defining IT resources is to make the protection against the resources.
This would be done based on the value of classifications of resources. So this activity needs to
keep in the training management information system. Hence the data security is the essential one
in the TIMS architecture. And normally the definition should include clear description about the
IT resources and various technologies. The security services are need to be considered about
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

these methods for the TIMS architecture. And these functions are need to be performed based on
the cost value. So according to the TIMS architecture the risks and critical resources should be
identified. These resources will help in the future to determine the data security services
(Monitor, 2000).
Identifying the threats regarding the TIMS architecture
After that the security risk are need to be analyzed and evaluated. The risk identification
is considered as an essential one in the training management system architecture. Also the risks
need to be estimated. By this analysis we can estimate the threats based on the training
information management system ("Fundamentals of Information Systems Security/Information
Security and Risk Management - Wikibooks, open books for an open world", 2018). Generally
the TIMS architecture needs data security solutions. These solution should be used to make the
efficient process to protect the IT resources. And the data security controls are need to be
selected regarding the development of TIMS architecture. These controls should be based on risk
analysis and security standards. Then the policies, requirements and security controls. Before
developing the TIMS architecture the security services are need to be verified by the
corresponding expert. And then finally the data security controls will be implemented based on
the training information management security (Humphreys, 2008).
Batch processing
Batch processing is effective one to establish the data process in a particular amount of
time. But it is not needed by now for the training information management system. It could be
effective in the future.
Batch processing indicates the jobs available in the systems needs to be completed in
sequential order (or) continuously. By using this process, the large jobs are separated into small
jobs and complete the jobs as soon as possible. It is also used in the Work Load Automation
(WLA), and the Job scheduling. The batch processing has more advantages while using in the
system of networks. It is very fast and its cost is also low. Batch processing reduces the work of
9
the cost value. So according to the TIMS architecture the risks and critical resources should be
identified. These resources will help in the future to determine the data security services
(Monitor, 2000).
Identifying the threats regarding the TIMS architecture
After that the security risk are need to be analyzed and evaluated. The risk identification
is considered as an essential one in the training management system architecture. Also the risks
need to be estimated. By this analysis we can estimate the threats based on the training
information management system ("Fundamentals of Information Systems Security/Information
Security and Risk Management - Wikibooks, open books for an open world", 2018). Generally
the TIMS architecture needs data security solutions. These solution should be used to make the
efficient process to protect the IT resources. And the data security controls are need to be
selected regarding the development of TIMS architecture. These controls should be based on risk
analysis and security standards. Then the policies, requirements and security controls. Before
developing the TIMS architecture the security services are need to be verified by the
corresponding expert. And then finally the data security controls will be implemented based on
the training information management security (Humphreys, 2008).
Batch processing
Batch processing is effective one to establish the data process in a particular amount of
time. But it is not needed by now for the training information management system. It could be
effective in the future.
Batch processing indicates the jobs available in the systems needs to be completed in
sequential order (or) continuously. By using this process, the large jobs are separated into small
jobs and complete the jobs as soon as possible. It is also used in the Work Load Automation
(WLA), and the Job scheduling. The batch processing has more advantages while using in the
system of networks. It is very fast and its cost is also low. Batch processing reduces the work of
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the data entry workers in the organization. This process don’t need any support from the data
entry clerks. So, it reduces the cost which spends for labor. Then, it also not require any
subsystems to work the functions in it. It means, batch processing can do the work in the normal
system itself. It don’t needs any extra hardware components along with the system in the
network. Batch processing can be done in offline mode. So, after completing all the works in an
organization, the batch processing is running in the systems. The software are set to process the
batches in overnight (HUANG, 2002). It helps to reduce the time consumption of day works. If
the batch processing takes place in day time means, then it needs time to complete. Therefore,
there should be no delay in every day works. Because batch processing completes in the night
time. In modern and updated batch processing software, notification options are there. So, I will
be very helpful to the managers. In olden batch processing software, there is no such options for
notification. If any job completes its batch processing means, then the particular person needs to
login to the system and check whether the job is complete or not. But, now the notification itself
tells about the status of batch processing in the system. There is some disadvantages in batch
processing. Batch processing needs trained persons to work with it ("Information Management
Framework", 2018). As technology develops, the batch processing software also upgraded.
Skilled and trained persons are need to do the work on it. It’s very difficult for not trained
persons. It cannot be operated by the person who is having some basic knowledge. It is one of
the disadvantage. Then, debugging is also difficult in batch processing. Because it is very
complex to solve the errors. It automates the job running process in an organization (James,
2006). It will cost more according to its usage on the organization.
4. TCO checklist for the TIMS system
The total cost ownership for the training information management architecture is
described based on the used network devices. They are startup, operational and retirement costs.
The startup costs including some kind of operation regarding the development of costs. They are
hardware, software, implementation, training and customization. Here the hardware costs
includes cost of servers and data storage. The implementation needs the costs for the configuring
and data storage.
10
entry clerks. So, it reduces the cost which spends for labor. Then, it also not require any
subsystems to work the functions in it. It means, batch processing can do the work in the normal
system itself. It don’t needs any extra hardware components along with the system in the
network. Batch processing can be done in offline mode. So, after completing all the works in an
organization, the batch processing is running in the systems. The software are set to process the
batches in overnight (HUANG, 2002). It helps to reduce the time consumption of day works. If
the batch processing takes place in day time means, then it needs time to complete. Therefore,
there should be no delay in every day works. Because batch processing completes in the night
time. In modern and updated batch processing software, notification options are there. So, I will
be very helpful to the managers. In olden batch processing software, there is no such options for
notification. If any job completes its batch processing means, then the particular person needs to
login to the system and check whether the job is complete or not. But, now the notification itself
tells about the status of batch processing in the system. There is some disadvantages in batch
processing. Batch processing needs trained persons to work with it ("Information Management
Framework", 2018). As technology develops, the batch processing software also upgraded.
Skilled and trained persons are need to do the work on it. It’s very difficult for not trained
persons. It cannot be operated by the person who is having some basic knowledge. It is one of
the disadvantage. Then, debugging is also difficult in batch processing. Because it is very
complex to solve the errors. It automates the job running process in an organization (James,
2006). It will cost more according to its usage on the organization.
4. TCO checklist for the TIMS system
The total cost ownership for the training information management architecture is
described based on the used network devices. They are startup, operational and retirement costs.
The startup costs including some kind of operation regarding the development of costs. They are
hardware, software, implementation, training and customization. Here the hardware costs
includes cost of servers and data storage. The implementation needs the costs for the configuring
and data storage.
10
And then the operational cost evaluations are need to be developed. It contains the
operation such as maintenance support, user licenses, patches, enhancement, training, data
center, upgrades and the security. Here the maintenance part need the costs for handling the
network devices and servers. Then also the cost is needed for solving the bugs and issues
regarding the development of TIMS architecture. It also consider about the costs of data center
and upgrades regarding the software and hardware (Zeibig, 2005).
Finally the retirement costs should be analyzed. This includes the costs of developers,
user license and archived systems. This type of cost management need to make the analysis
about the software and hardware developers. It should also make a concern about the inactive
licenses. These type of cost estimation will lead the good level regarding the training information
management architecture.
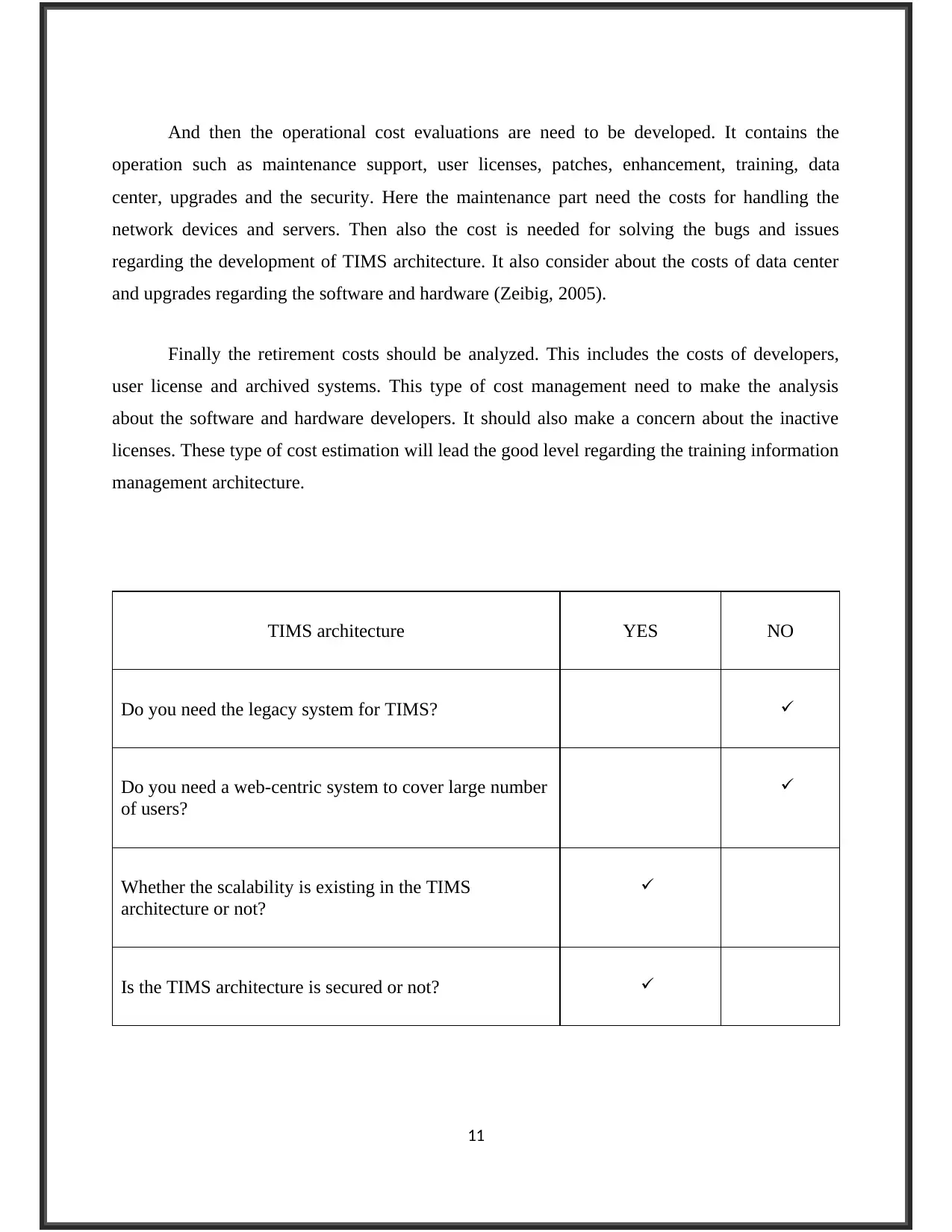
TIMS architecture YES NO
Do you need the legacy system for TIMS?
Do you need a web-centric system to cover large number
of users?
Whether the scalability is existing in the TIMS
architecture or not?
Is the TIMS architecture is secured or not?
11
operation such as maintenance support, user licenses, patches, enhancement, training, data
center, upgrades and the security. Here the maintenance part need the costs for handling the
network devices and servers. Then also the cost is needed for solving the bugs and issues
regarding the development of TIMS architecture. It also consider about the costs of data center
and upgrades regarding the software and hardware (Zeibig, 2005).
Finally the retirement costs should be analyzed. This includes the costs of developers,
user license and archived systems. This type of cost management need to make the analysis
about the software and hardware developers. It should also make a concern about the inactive
licenses. These type of cost estimation will lead the good level regarding the training information
management architecture.
TIMS architecture YES NO
Do you need the legacy system for TIMS?
Do you need a web-centric system to cover large number
of users?
Whether the scalability is existing in the TIMS
architecture or not?
Is the TIMS architecture is secured or not?
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





