Vendor Products and Equipments - Desklib
VerifiedAdded on 2023/04/25
|15
|2886
|367
AI Summary
This document discusses the requirements for vendor products and equipments, operating system requirements, cost-benefit analysis, and more. It also covers the importance of international standards for ICT, approaches for understanding client business domain before selecting vendor products, and different copyright licenses. The subject covered is not mentioned, but it seems to be related to IT or computer science. The document type is an assignment. The output is in JSON format.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: VENDOR PRODUCTS AND EQUIPMENTS
VENDOR PRODUCTS AND EQUIPMENTS
Name of the Student
Name of the University
Author note
VENDOR PRODUCTS AND EQUIPMENTS
Name of the Student
Name of the University
Author note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VENDOR PRODUCTS AND EQUIPMENTS
Table of Contents
Assignments 1......................................................................................................................3
PC Requirement...............................................................................................................3
Operating System requirement........................................................................................4
CBA.................................................................................................................................6
Assumption......................................................................................................................8
Assignment 2.......................................................................................................................9
1. International standard is important for ICT to bridge the digital device from various
vendors for common principal.....................................................................................................9
2. Approach for understanding client business domain before selecting vendor
product?.....................................................................................................................................10
3. Explain briefly the following terms and give example where appropriate?..............10
4. Australian Computer Society (ACS) Code of ethics.................................................12
References..........................................................................................................................14
Table of Contents
Assignments 1......................................................................................................................3
PC Requirement...............................................................................................................3
Operating System requirement........................................................................................4
CBA.................................................................................................................................6
Assumption......................................................................................................................8
Assignment 2.......................................................................................................................9
1. International standard is important for ICT to bridge the digital device from various
vendors for common principal.....................................................................................................9
2. Approach for understanding client business domain before selecting vendor
product?.....................................................................................................................................10
3. Explain briefly the following terms and give example where appropriate?..............10
4. Australian Computer Society (ACS) Code of ethics.................................................12
References..........................................................................................................................14

VENDOR PRODUCTS AND EQUIPMENTS
Assignments 1
PC Requirement
Maximum Requirement
Processor - dual core 2.4 GHz+ (i5 or i7 series Intel processor or equivalent AMD)
RAM - 16 GB
Hard Drive - 256 GB or larger solid state hard drive
Graphics Card - any with DisplayPort/HDMI or DVI support - desktop only
Wireless (for laptops) - 802.11ac (WPA2 support required)
Monitor - 23" widescreen LCD with DisplayPort/HDMI or DVI support - desktop only
Operating System - Windows 10 Home or Professional editions, or Apple OS X 10.12.3
Warranty - 3 year warranty - desktop only
Warranty - 4 year warranty with accidental damage protection - laptop only
Backup Device - External hard drive and/or USB Flash Drive
Minimum Requirement
Processor - dual core @ 2.4 GHz (i5 or i7 Intel processor or equivalent AMD)
RAM - 8 GB
Hard Drive - 320 GB 5400 RPM hard drive
Wireless (for laptops) - 802.11g/n (WPA2 support required)
Monitor - 19" LCD - desktop only
Operating System - Windows 7 with Service Pack 1 or Apple OS X 10.11
Backup Device - External hard drive and/or USB Flash Drive
Assignments 1
PC Requirement
Maximum Requirement
Processor - dual core 2.4 GHz+ (i5 or i7 series Intel processor or equivalent AMD)
RAM - 16 GB
Hard Drive - 256 GB or larger solid state hard drive
Graphics Card - any with DisplayPort/HDMI or DVI support - desktop only
Wireless (for laptops) - 802.11ac (WPA2 support required)
Monitor - 23" widescreen LCD with DisplayPort/HDMI or DVI support - desktop only
Operating System - Windows 10 Home or Professional editions, or Apple OS X 10.12.3
Warranty - 3 year warranty - desktop only
Warranty - 4 year warranty with accidental damage protection - laptop only
Backup Device - External hard drive and/or USB Flash Drive
Minimum Requirement
Processor - dual core @ 2.4 GHz (i5 or i7 Intel processor or equivalent AMD)
RAM - 8 GB
Hard Drive - 320 GB 5400 RPM hard drive
Wireless (for laptops) - 802.11g/n (WPA2 support required)
Monitor - 19" LCD - desktop only
Operating System - Windows 7 with Service Pack 1 or Apple OS X 10.11
Backup Device - External hard drive and/or USB Flash Drive

VENDOR PRODUCTS AND EQUIPMENTS
Operating System requirement
The following advantages Windows 10 will provide to the proposed system
Secure Your Organization: Data and people are the livelihood of any organization.
Enhanced Windows 10 security features allow businesses to keep their data, devices and users
protected 24x7. The OS makes it easier than ever for a small or mid-sized business to get the
Windows 10 benefits of enterprise-grade security and control without complexity or unrealistic
costs. AppLocker management, for example, is a tool that helps administrators determine which
applications and files users can run on a device. Device Guard employs rigorous access controls
that help protect the Windows system core and prevent untrusted apps and executables from
starting and Credential Guard protects employee identities by storing user access tokens within a
secure environment. With Windows 10 Enterprise, endpoints can be managed from one interface
allowing businesses to get a full picture of the computing environment from one control panel,
included threat status, installed applications as well as running applications.
Enable Secure Productivity: Technology, no matter how secure, is rendered useless in
the workplace unless it enables productivity. The combination of Windows 10 Enterprise's
loaded security features with the OS' power and productivity capabilities enable a protected and
productive environment. A few factors give Windows 10 a leg up when it comes to enabling
productivity: universal Windows app functionality which allows for a seamless experience
across multiple devices, adjustable Snap which lets users have more than two windows side-by-
side on the same screen, and cloud support for Azure Active Directory which basically enables
users to login to their cloud based services like Office 365 without having to enter credentials,
eliminating the need to remember multiple IDs and passwords. With Windows 10, Microsoft
Operating System requirement
The following advantages Windows 10 will provide to the proposed system
Secure Your Organization: Data and people are the livelihood of any organization.
Enhanced Windows 10 security features allow businesses to keep their data, devices and users
protected 24x7. The OS makes it easier than ever for a small or mid-sized business to get the
Windows 10 benefits of enterprise-grade security and control without complexity or unrealistic
costs. AppLocker management, for example, is a tool that helps administrators determine which
applications and files users can run on a device. Device Guard employs rigorous access controls
that help protect the Windows system core and prevent untrusted apps and executables from
starting and Credential Guard protects employee identities by storing user access tokens within a
secure environment. With Windows 10 Enterprise, endpoints can be managed from one interface
allowing businesses to get a full picture of the computing environment from one control panel,
included threat status, installed applications as well as running applications.
Enable Secure Productivity: Technology, no matter how secure, is rendered useless in
the workplace unless it enables productivity. The combination of Windows 10 Enterprise's
loaded security features with the OS' power and productivity capabilities enable a protected and
productive environment. A few factors give Windows 10 a leg up when it comes to enabling
productivity: universal Windows app functionality which allows for a seamless experience
across multiple devices, adjustable Snap which lets users have more than two windows side-by-
side on the same screen, and cloud support for Azure Active Directory which basically enables
users to login to their cloud based services like Office 365 without having to enter credentials,
eliminating the need to remember multiple IDs and passwords. With Windows 10, Microsoft
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VENDOR PRODUCTS AND EQUIPMENTS
aimed to combine the best aspects of the user experience from Windows 8.1 and Windows 7,
making its use straightforward and simple.
Scalability and Affordability: Most businesses have an ebb and flow of personnel.
People come and go and so should their workplace technology. With Windows 10 Enterprise
through a cloud solution provider (CSP), you get the benefits of a pay-as-you-go subscription
model. This means per-user, per-month pricing giving small businesses the flexibility to scale up
or down, from month-to-month, as needs change. This also means that a Cloud Solution Provider
(like iCorps) can onboard new employees and reassign licenses as needed. Windows 10
Enterprise gives SMBs the ability to access enterprise-grade security features and productivity
for as little as the price of a venti Starbucks latte and blueberry scone. Windows 10 Enterprise
ranges in cost from $7 per user to $14 per user depending on which security features your
business needs.
Software and hardware requirement for supporting. This is clearly aimed at computer
makers. It’s thus worth adding that the Windows 10 technical preview has these requirements:
i. Processor: 1 gigahertz (GHz) or faster
ii. RAM: 1 gigabyte (GB) (32-bit) or 2 GB (64-bit)
iii. Free hard disk space: 16 GB
iv. Graphics card: Microsoft DirectX 9 graphics device with WDDM driver
v. A Microsoft account and Internet access
The Office 365 Premium Package can be used as the Microsoft Office Package for
the business management: Anytime anywhere access to emails, documents, contacts, and
calendars on any device. You can access the services seamlessly from your desktop, notebook, or
aimed to combine the best aspects of the user experience from Windows 8.1 and Windows 7,
making its use straightforward and simple.
Scalability and Affordability: Most businesses have an ebb and flow of personnel.
People come and go and so should their workplace technology. With Windows 10 Enterprise
through a cloud solution provider (CSP), you get the benefits of a pay-as-you-go subscription
model. This means per-user, per-month pricing giving small businesses the flexibility to scale up
or down, from month-to-month, as needs change. This also means that a Cloud Solution Provider
(like iCorps) can onboard new employees and reassign licenses as needed. Windows 10
Enterprise gives SMBs the ability to access enterprise-grade security features and productivity
for as little as the price of a venti Starbucks latte and blueberry scone. Windows 10 Enterprise
ranges in cost from $7 per user to $14 per user depending on which security features your
business needs.
Software and hardware requirement for supporting. This is clearly aimed at computer
makers. It’s thus worth adding that the Windows 10 technical preview has these requirements:
i. Processor: 1 gigahertz (GHz) or faster
ii. RAM: 1 gigabyte (GB) (32-bit) or 2 GB (64-bit)
iii. Free hard disk space: 16 GB
iv. Graphics card: Microsoft DirectX 9 graphics device with WDDM driver
v. A Microsoft account and Internet access
The Office 365 Premium Package can be used as the Microsoft Office Package for
the business management: Anytime anywhere access to emails, documents, contacts, and
calendars on any device. You can access the services seamlessly from your desktop, notebook, or
VENDOR PRODUCTS AND EQUIPMENTS
mobile phone. Complete offering of solutions including desktop productivity applications
(Office Web Apps), online portals, extranets, external web site, instant messaging, voice and
video conferencing, Web conferencing, e-mail, voice mail and unified messaging. Simple easy to
use communication and collaboration with colleagues and partners. Integrates seamlessly with
Microsoft Office and other Microsoft programs. Flexible pricing options that gives you
predictability and flexibility for all or part of an organization. Convert Capex into Opex.
Business-class service including IT admin phone support, financially-backed 99.9% uptime
guarantee, geo-redundant data centers, disaster recovery, robust security, privacy controls and
standards. Latest version of software being upgraded at no additional cost. Single sign on –
running in the system tray of each user’s machine, storing their password to avoid constant sign
in.
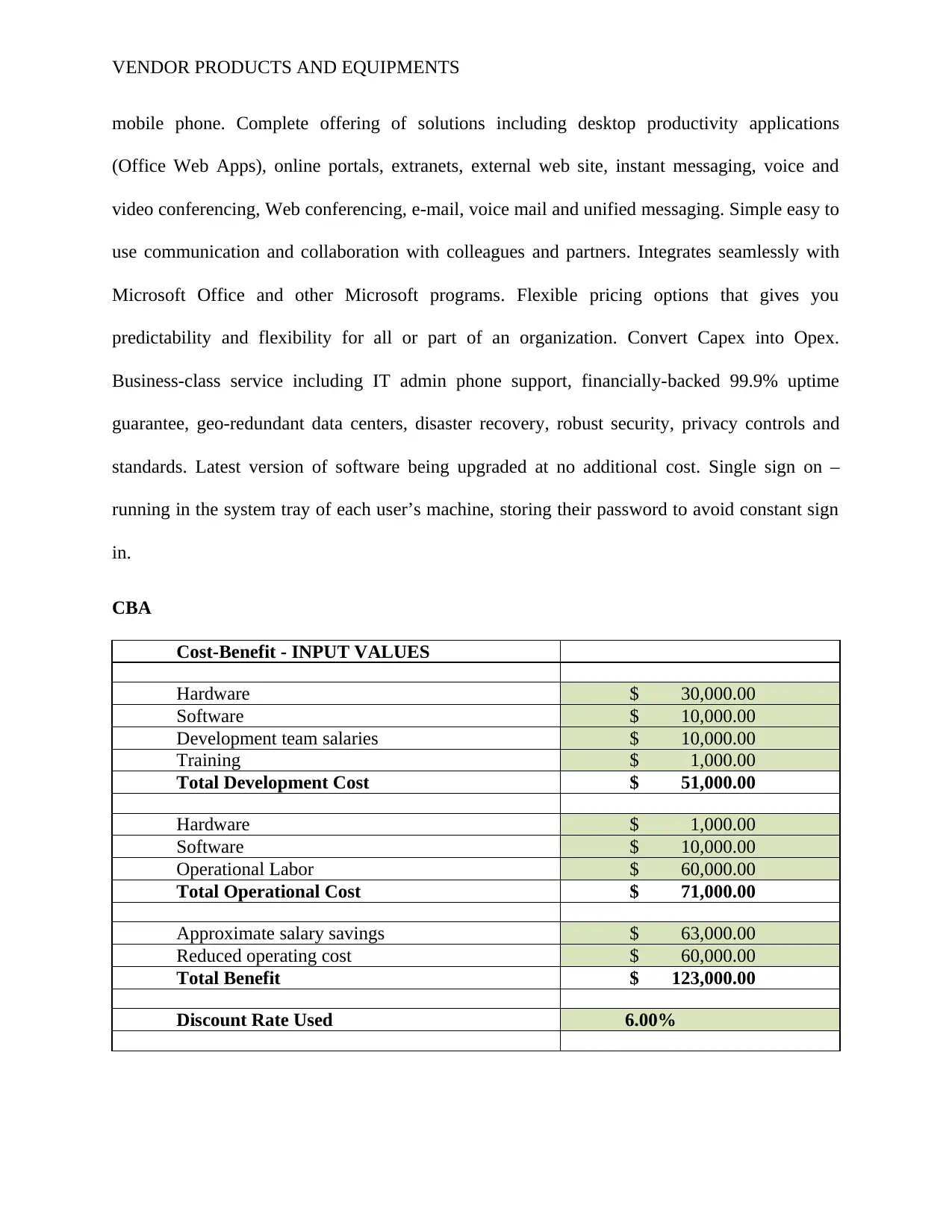
CBA
Cost-Benefit - INPUT VALUES
Hardware $ 30,000.00
Software $ 10,000.00
Development team salaries $ 10,000.00
Training $ 1,000.00
Total Development Cost $ 51,000.00
Hardware $ 1,000.00
Software $ 10,000.00
Operational Labor $ 60,000.00
Total Operational Cost $ 71,000.00
Approximate salary savings $ 63,000.00
Reduced operating cost $ 60,000.00
Total Benefit $ 123,000.00
Discount Rate Used 6.00%
mobile phone. Complete offering of solutions including desktop productivity applications
(Office Web Apps), online portals, extranets, external web site, instant messaging, voice and
video conferencing, Web conferencing, e-mail, voice mail and unified messaging. Simple easy to
use communication and collaboration with colleagues and partners. Integrates seamlessly with
Microsoft Office and other Microsoft programs. Flexible pricing options that gives you
predictability and flexibility for all or part of an organization. Convert Capex into Opex.
Business-class service including IT admin phone support, financially-backed 99.9% uptime
guarantee, geo-redundant data centers, disaster recovery, robust security, privacy controls and
standards. Latest version of software being upgraded at no additional cost. Single sign on –
running in the system tray of each user’s machine, storing their password to avoid constant sign
in.
CBA
Cost-Benefit - INPUT VALUES
Hardware $ 30,000.00
Software $ 10,000.00
Development team salaries $ 10,000.00
Training $ 1,000.00
Total Development Cost $ 51,000.00
Hardware $ 1,000.00
Software $ 10,000.00
Operational Labor $ 60,000.00
Total Operational Cost $ 71,000.00
Approximate salary savings $ 63,000.00
Reduced operating cost $ 60,000.00
Total Benefit $ 123,000.00
Discount Rate Used 6.00%
VENDOR PRODUCTS AND EQUIPMENTS
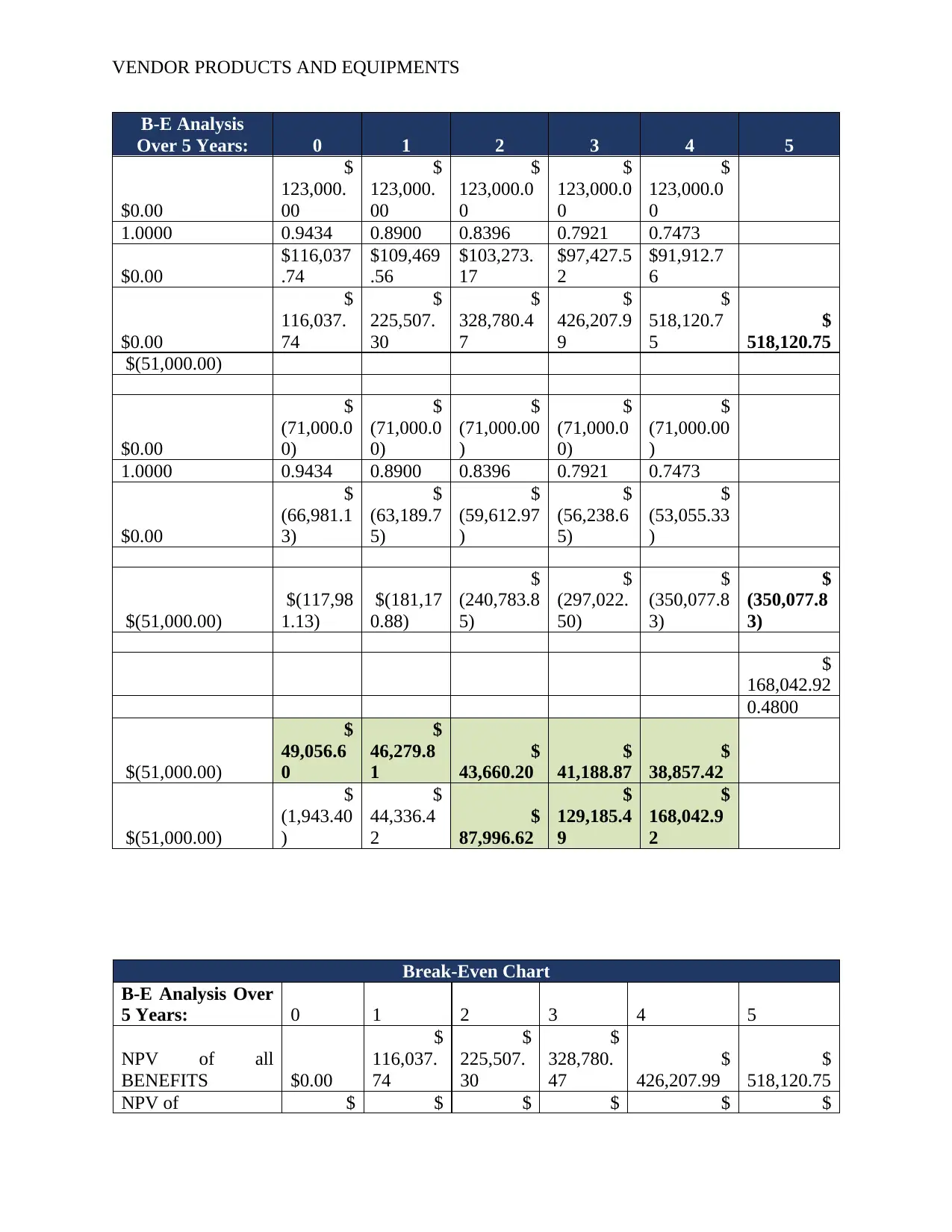
B-E Analysis
Over 5 Years: 0 1 2 3 4 5
$0.00
$
123,000.
00
$
123,000.
00
$
123,000.0
0
$
123,000.0
0
$
123,000.0
0
1.0000 0.9434 0.8900 0.8396 0.7921 0.7473
$0.00
$116,037
.74
$109,469
.56
$103,273.
17
$97,427.5
2
$91,912.7
6
$0.00
$
116,037.
74
$
225,507.
30
$
328,780.4
7
$
426,207.9
9
$
518,120.7
5
$
518,120.75
$(51,000.00)
$0.00
$
(71,000.0
0)
$
(71,000.0
0)
$
(71,000.00
)
$
(71,000.0
0)
$
(71,000.00
)
1.0000 0.9434 0.8900 0.8396 0.7921 0.7473
$0.00
$
(66,981.1
3)
$
(63,189.7
5)
$
(59,612.97
)
$
(56,238.6
5)
$
(53,055.33
)
$(51,000.00)
$(117,98
1.13)
$(181,17
0.88)
$
(240,783.8
5)
$
(297,022.
50)
$
(350,077.8
3)
$
(350,077.8
3)
$
168,042.92
0.4800
$(51,000.00)
$
49,056.6
0
$
46,279.8
1
$
43,660.20
$
41,188.87
$
38,857.42
$(51,000.00)
$
(1,943.40
)
$
44,336.4
2
$
87,996.62
$
129,185.4
9
$
168,042.9
2
Break-Even Chart
B-E Analysis Over
5 Years: 0 1 2 3 4 5
NPV of all
BENEFITS $0.00
$
116,037.
74
$
225,507.
30
$
328,780.
47
$
426,207.99
$
518,120.75
NPV of $ $ $ $ $ $
B-E Analysis
Over 5 Years: 0 1 2 3 4 5
$0.00
$
123,000.
00
$
123,000.
00
$
123,000.0
0
$
123,000.0
0
$
123,000.0
0
1.0000 0.9434 0.8900 0.8396 0.7921 0.7473
$0.00
$116,037
.74
$109,469
.56
$103,273.
17
$97,427.5
2
$91,912.7
6
$0.00
$
116,037.
74
$
225,507.
30
$
328,780.4
7
$
426,207.9
9
$
518,120.7
5
$
518,120.75
$(51,000.00)
$0.00
$
(71,000.0
0)
$
(71,000.0
0)
$
(71,000.00
)
$
(71,000.0
0)
$
(71,000.00
)
1.0000 0.9434 0.8900 0.8396 0.7921 0.7473
$0.00
$
(66,981.1
3)
$
(63,189.7
5)
$
(59,612.97
)
$
(56,238.6
5)
$
(53,055.33
)
$(51,000.00)
$(117,98
1.13)
$(181,17
0.88)
$
(240,783.8
5)
$
(297,022.
50)
$
(350,077.8
3)
$
(350,077.8
3)
$
168,042.92
0.4800
$(51,000.00)
$
49,056.6
0
$
46,279.8
1
$
43,660.20
$
41,188.87
$
38,857.42
$(51,000.00)
$
(1,943.40
)
$
44,336.4
2
$
87,996.62
$
129,185.4
9
$
168,042.9
2
Break-Even Chart
B-E Analysis Over
5 Years: 0 1 2 3 4 5
NPV of all
BENEFITS $0.00
$
116,037.
74
$
225,507.
30
$
328,780.
47
$
426,207.99
$
518,120.75
NPV of $ $ $ $ $ $
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VENDOR PRODUCTS AND EQUIPMENTS
all COSTS
51,000.
00
117,981.
13
181,170.
88
240,783.
85 297,022.50 350,077.83
0 1 2 3 4 5 0
$0.00
$100,000.00
$200,000.00
$300,000.00
$400,000.00
$500,000.00
$600,000.00
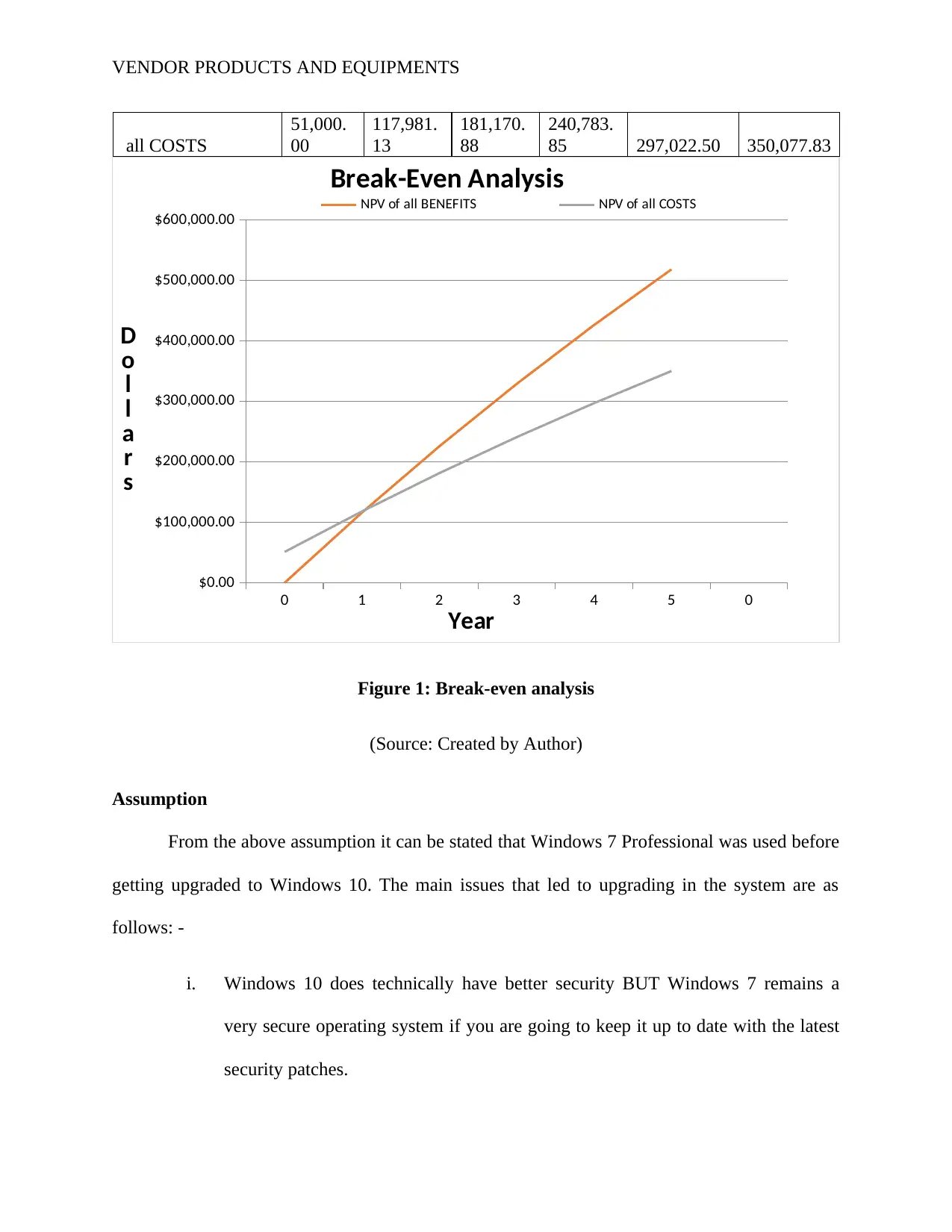
Break-Even Analysis
NPV of all BENEFITS NPV of all COSTS
Year
D
o
l
l
a
r
s
Figure 1: Break-even analysis
(Source: Created by Author)
Assumption
From the above assumption it can be stated that Windows 7 Professional was used before
getting upgraded to Windows 10. The main issues that led to upgrading in the system are as
follows: -
i. Windows 10 does technically have better security BUT Windows 7 remains a
very secure operating system if you are going to keep it up to date with the latest
security patches.
all COSTS
51,000.
00
117,981.
13
181,170.
88
240,783.
85 297,022.50 350,077.83
0 1 2 3 4 5 0
$0.00
$100,000.00
$200,000.00
$300,000.00
$400,000.00
$500,000.00
$600,000.00
Break-Even Analysis
NPV of all BENEFITS NPV of all COSTS
Year
D
o
l
l
a
r
s
Figure 1: Break-even analysis
(Source: Created by Author)
Assumption
From the above assumption it can be stated that Windows 7 Professional was used before
getting upgraded to Windows 10. The main issues that led to upgrading in the system are as
follows: -
i. Windows 10 does technically have better security BUT Windows 7 remains a
very secure operating system if you are going to keep it up to date with the latest
security patches.

VENDOR PRODUCTS AND EQUIPMENTS
ii. Windows 7 doesn’t support the latest AMD, Intel and Qualcomm chipsets but that
is ONLY because Microsoft chose to make them incompatible. In the history of
Windows this was an unprecedented step and designed to push users to Windows
10.
iii. Technically Windows Store apps are only compatible with Windows 10 but I’ve
seen ZERO evidence any hardware or software companies are no longer
supporting Windows 7. It would make no sense, Windows 7 is still by far the
most popular and widely used operating system in the world.
Assignment 2
1. International standard is important for ICT to bridge the digital device from
various vendors for common principal.
a. Discuss the importance of the international standard specifically for ICT.
There are three key elements for the ICT solution to bridge the digital divide created
due to culture and language.
ICT Literacy
Interoperability
Availability
b. Discuss the implication it would have when selecting multiple vendor products from
different parts of the earth?
Methods are as follows: -
ii. Windows 7 doesn’t support the latest AMD, Intel and Qualcomm chipsets but that
is ONLY because Microsoft chose to make them incompatible. In the history of
Windows this was an unprecedented step and designed to push users to Windows
10.
iii. Technically Windows Store apps are only compatible with Windows 10 but I’ve
seen ZERO evidence any hardware or software companies are no longer
supporting Windows 7. It would make no sense, Windows 7 is still by far the
most popular and widely used operating system in the world.
Assignment 2
1. International standard is important for ICT to bridge the digital device from
various vendors for common principal.
a. Discuss the importance of the international standard specifically for ICT.
There are three key elements for the ICT solution to bridge the digital divide created
due to culture and language.
ICT Literacy
Interoperability
Availability
b. Discuss the implication it would have when selecting multiple vendor products from
different parts of the earth?
Methods are as follows: -

VENDOR PRODUCTS AND EQUIPMENTS
Making trust an ongoing component of the third-party provider engagement
process
Preparing for incidents amongst multiple providers
Establishing and maintaining clear visibility of security risks with each IT
provider
2. Approach for understanding client business domain before selecting vendor
product?
A mission statement states the main purpose of the organisation and usually
incorporates its financial, social and/or environmental goals.
Organisation charts can provide a graphical representation of the business in
terms of how it is organised to fulfil its core business.
3. Explain briefly the following terms and give example where appropriate?
a. Full copyright: A full copyright is a form of protection provided by the laws of the
United States to authors of "original works of authorship." This includes literary,
dramatic, musical, artistic and certain other creative works. Material not protected by
copyright (or otherwise protected) is available for use by anyone without the author's
consent. A copyright holder can prevent others from copying, performing or
otherwise using the work without his or her consent. For example: Original
compilations of facts, such as a field guide
b. Outline and describe different copyright licenses: Different copyright licenses are as
follows: -
Making trust an ongoing component of the third-party provider engagement
process
Preparing for incidents amongst multiple providers
Establishing and maintaining clear visibility of security risks with each IT
provider
2. Approach for understanding client business domain before selecting vendor
product?
A mission statement states the main purpose of the organisation and usually
incorporates its financial, social and/or environmental goals.
Organisation charts can provide a graphical representation of the business in
terms of how it is organised to fulfil its core business.
3. Explain briefly the following terms and give example where appropriate?
a. Full copyright: A full copyright is a form of protection provided by the laws of the
United States to authors of "original works of authorship." This includes literary,
dramatic, musical, artistic and certain other creative works. Material not protected by
copyright (or otherwise protected) is available for use by anyone without the author's
consent. A copyright holder can prevent others from copying, performing or
otherwise using the work without his or her consent. For example: Original
compilations of facts, such as a field guide
b. Outline and describe different copyright licenses: Different copyright licenses are as
follows: -
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VENDOR PRODUCTS AND EQUIPMENTS
Attribution CC BY: This license lets others distribute, remix, tweak, and build upon
your work, even commercially, as long as they credit you for the original creation. This is the
most accommodating of licenses offered. Recommended for maximum dissemination and use of
licensed materials.
Attribution-ShareAlike CC BY-SA: This license lets others remix, tweak, and build
upon your work even for commercial purposes, as long as they credit you and license their new
creations under the identical terms. This license is often compared to “copyleft” free and open
source software licenses. All new works based on yours will carry the same license, so any
derivatives will also allow commercial use
Attribution-NoDerivs CC BY-ND: This license allows for redistribution, commercial
and non-commercial, as long as it is passed along unchanged and in whole, with credit to you.
Attribution-NonCommercial-ShareAlike CC BY-NC-SA: This license lets others
remix, tweak, and build upon your work non-commercially, as long as they credit you and
license their new creations under the identical terms.
Attribution-NonCommercial-NoDerivs CC BY-NC-ND: This license is the most
restrictive of our six main licenses, only allowing others to download your works and share them
with others as long as they credit you, but they can’t change them in any way or use them
commercially.
Attribution-NonCommercial CC BY-NC: This license lets others remix, tweak, and
build upon your work non-commercially, and although their new works must also acknowledge
you and be non-commercial, they don’t have to license their derivative works on the same terms.
Attribution CC BY: This license lets others distribute, remix, tweak, and build upon
your work, even commercially, as long as they credit you for the original creation. This is the
most accommodating of licenses offered. Recommended for maximum dissemination and use of
licensed materials.
Attribution-ShareAlike CC BY-SA: This license lets others remix, tweak, and build
upon your work even for commercial purposes, as long as they credit you and license their new
creations under the identical terms. This license is often compared to “copyleft” free and open
source software licenses. All new works based on yours will carry the same license, so any
derivatives will also allow commercial use
Attribution-NoDerivs CC BY-ND: This license allows for redistribution, commercial
and non-commercial, as long as it is passed along unchanged and in whole, with credit to you.
Attribution-NonCommercial-ShareAlike CC BY-NC-SA: This license lets others
remix, tweak, and build upon your work non-commercially, as long as they credit you and
license their new creations under the identical terms.
Attribution-NonCommercial-NoDerivs CC BY-NC-ND: This license is the most
restrictive of our six main licenses, only allowing others to download your works and share them
with others as long as they credit you, but they can’t change them in any way or use them
commercially.
Attribution-NonCommercial CC BY-NC: This license lets others remix, tweak, and
build upon your work non-commercially, and although their new works must also acknowledge
you and be non-commercial, they don’t have to license their derivative works on the same terms.

VENDOR PRODUCTS AND EQUIPMENTS
c. Intellectual property (IP): Intellectual property refers to the ownership of intangible
and non-physical goods. This includes ideas, names, designs, symbols, artwork, writings, and
other creations. It also refers to digital media, such as audio and video clips that can be
downloaded online.
4. Australian Computer Society (ACS) Code of ethics
a. Outline and briefly explain in your own words ACS code of ethics: As an ACS
member you must uphold and advance the honour, dignity and effectiveness of being a
professional. This entails, in addition to being a good citizen and acting within the law, your
conformance to the following ACS values.
The Primacy of the Public Interest: You will place the interests of the public above
those of personal, business or sectional interests.
The Enhancement of Quality of Life: You will strive to enhance the quality of life of
those affected by your work.
Honesty you will be honest in: Your representation of skills, knowledge, services and
products.
Competence: You will work competently and diligently for your stakeholders.
Professional Development: You will enhance your own professional development, and
that of your staff.
Professionalism: You will enhance the integrity of the ACS and the respect of its
members for each other.
c. Intellectual property (IP): Intellectual property refers to the ownership of intangible
and non-physical goods. This includes ideas, names, designs, symbols, artwork, writings, and
other creations. It also refers to digital media, such as audio and video clips that can be
downloaded online.
4. Australian Computer Society (ACS) Code of ethics
a. Outline and briefly explain in your own words ACS code of ethics: As an ACS
member you must uphold and advance the honour, dignity and effectiveness of being a
professional. This entails, in addition to being a good citizen and acting within the law, your
conformance to the following ACS values.
The Primacy of the Public Interest: You will place the interests of the public above
those of personal, business or sectional interests.
The Enhancement of Quality of Life: You will strive to enhance the quality of life of
those affected by your work.
Honesty you will be honest in: Your representation of skills, knowledge, services and
products.
Competence: You will work competently and diligently for your stakeholders.
Professional Development: You will enhance your own professional development, and
that of your staff.
Professionalism: You will enhance the integrity of the ACS and the respect of its
members for each other.

VENDOR PRODUCTS AND EQUIPMENTS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VENDOR PRODUCTS AND EQUIPMENTS
References
Challenger, M., Mernik, M., Kardas, G. and Kosar, T., 2016. Declarative specifications for the
development of multi-agent systems. Computer Standards & Interfaces, 43, pp.91-115.
Collberg, C. and Proebsting, T.A., 2016. Repeatability in computer systems
research. Communications of the ACM, 59(3), pp.62-69.
Gehr, T., Dimitrov, D. and Vechev, M., 2015, July. Learning commutativity specifications.
In International Conference on Computer Aided Verification (pp. 307-323). Springer, Cham.
Gulia, S. and Choudhury, T., 2016, January. An efficient automated design to generate UML
diagram from Natural Language Specifications. In Cloud System and Big Data Engineering
(Confluence), 2016 6th International Conference(pp. 641-648). IEEE.
Hibbeln, M., Jenkins, J.L., Schneider, C., Valacich, J.S. and Weinmann, M., 2017. How is your
user feeling? Inferring emotion through human–computer interaction devices. Group, 1000,
p.248.
Jana, S., Kang, Y.J., Roth, S. and Ray, B., 2016, August. Automatically Detecting Error
Handling Bugs Using Error Specifications. In USENIX Security Symposium (pp. 345-362).
Laki, S., Horpácsi, D., Vörös, P., Kitlei, R., Leskó, D. and Tejfel, M., 2016, August. High speed
packet forwarding compiled from protocol independent data plane specifications. In Proceedings
of the 2016 ACM SIGCOMM Conference (pp. 629-630). ACM.
Schatz, P., Ybarra, V. and Leitner, D., 2015. Validating the accuracy of reaction time assessment
on computer-based tablet devices. Assessment, 22(4), pp.405-410.
Turner, R., 2018. Computational artifacts: Towards a philosophy of computer science. Springer.
References
Challenger, M., Mernik, M., Kardas, G. and Kosar, T., 2016. Declarative specifications for the
development of multi-agent systems. Computer Standards & Interfaces, 43, pp.91-115.
Collberg, C. and Proebsting, T.A., 2016. Repeatability in computer systems
research. Communications of the ACM, 59(3), pp.62-69.
Gehr, T., Dimitrov, D. and Vechev, M., 2015, July. Learning commutativity specifications.
In International Conference on Computer Aided Verification (pp. 307-323). Springer, Cham.
Gulia, S. and Choudhury, T., 2016, January. An efficient automated design to generate UML
diagram from Natural Language Specifications. In Cloud System and Big Data Engineering
(Confluence), 2016 6th International Conference(pp. 641-648). IEEE.
Hibbeln, M., Jenkins, J.L., Schneider, C., Valacich, J.S. and Weinmann, M., 2017. How is your
user feeling? Inferring emotion through human–computer interaction devices. Group, 1000,
p.248.
Jana, S., Kang, Y.J., Roth, S. and Ray, B., 2016, August. Automatically Detecting Error
Handling Bugs Using Error Specifications. In USENIX Security Symposium (pp. 345-362).
Laki, S., Horpácsi, D., Vörös, P., Kitlei, R., Leskó, D. and Tejfel, M., 2016, August. High speed
packet forwarding compiled from protocol independent data plane specifications. In Proceedings
of the 2016 ACM SIGCOMM Conference (pp. 629-630). ACM.
Schatz, P., Ybarra, V. and Leitner, D., 2015. Validating the accuracy of reaction time assessment
on computer-based tablet devices. Assessment, 22(4), pp.405-410.
Turner, R., 2018. Computational artifacts: Towards a philosophy of computer science. Springer.

VENDOR PRODUCTS AND EQUIPMENTS
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





