Setting up Virtual Machine and Configuring Windows Server 2016 for a Local Photography Studio
VerifiedAdded on 2023/06/11
|30
|2776
|138
AI Summary
This guide provides step-by-step instructions on how to set up a virtual machine and configure Windows Server 2016 for a local photography studio. It covers web hosting, remote shell access configuration, HTTP and HTTP services configuration, network sharing configuration, and data duplication configuration. The guide also discusses the advantages of Windows Server 2016 and the importance of authentication. Course code and college/university are not mentioned.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

IT Concepts 1
Student Name
Student ID
Course
Institutional Affiliation
Student Name
Student ID
Course
Institutional Affiliation
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Concepts 2
Table of Contents
Introduction......................................................................................................................................3
Background Information..................................................................................................................3
Setting up virtual machine using windows server 2016..................................................................4
Web Hosting/Remote Shell Access Configuration..........................................................................8
HTTP and HTTP services Configuration......................................................................................15
Network Sharing Configuration....................................................................................................18
Configuring Data Duplication.......................................................................................................24
Justifications..................................................................................................................................27
Advantages of Windows Sever 2016.........................................................................................27
Importance of Authentication....................................................................................................27
Conclusion.....................................................................................................................................28
Reference List................................................................................................................................29
Table of Contents
Introduction......................................................................................................................................3
Background Information..................................................................................................................3
Setting up virtual machine using windows server 2016..................................................................4
Web Hosting/Remote Shell Access Configuration..........................................................................8
HTTP and HTTP services Configuration......................................................................................15
Network Sharing Configuration....................................................................................................18
Configuring Data Duplication.......................................................................................................24
Justifications..................................................................................................................................27
Advantages of Windows Sever 2016.........................................................................................27
Importance of Authentication....................................................................................................27
Conclusion.....................................................................................................................................28
Reference List................................................................................................................................29

IT Concepts 3
Introduction
A server is a very important part for any organization to facilitate smooth flow of operations and
processes. It processes the requests from the client computers on a local network or over the internet.
There are many types of servers available in the market, for example, print server, file server, web server,
mail server, and many more. It is high-powered computers with large memories, storage, and great
processing speed. Its functions by pulling and pushing data over the network.
A virtual machine is more like a physical computer, but is not, which runs applications and operating
systems. The virtual machine is made up of configuration files and specifications and is supported by
physical resources of the host. The key components that makes up a virtual machine include NVRAM
setting file, configuration file, log file, and virtual disk file.
Background Information
A local photography studio needs a server to be set up that addresses its current IT needs. The studio
needs to create a network that allows photographers to store all the pictures in one place and can be
accessed by all the employees and supports data redundancy to make sure that the work is secured.
Additionally, they would like to host a web server from which customers can be able to access the photos
after been given the rights to access them. The solution is as discussed in the subsequent sections.
Introduction
A server is a very important part for any organization to facilitate smooth flow of operations and
processes. It processes the requests from the client computers on a local network or over the internet.
There are many types of servers available in the market, for example, print server, file server, web server,
mail server, and many more. It is high-powered computers with large memories, storage, and great
processing speed. Its functions by pulling and pushing data over the network.
A virtual machine is more like a physical computer, but is not, which runs applications and operating
systems. The virtual machine is made up of configuration files and specifications and is supported by
physical resources of the host. The key components that makes up a virtual machine include NVRAM
setting file, configuration file, log file, and virtual disk file.
Background Information
A local photography studio needs a server to be set up that addresses its current IT needs. The studio
needs to create a network that allows photographers to store all the pictures in one place and can be
accessed by all the employees and supports data redundancy to make sure that the work is secured.
Additionally, they would like to host a web server from which customers can be able to access the photos
after been given the rights to access them. The solution is as discussed in the subsequent sections.
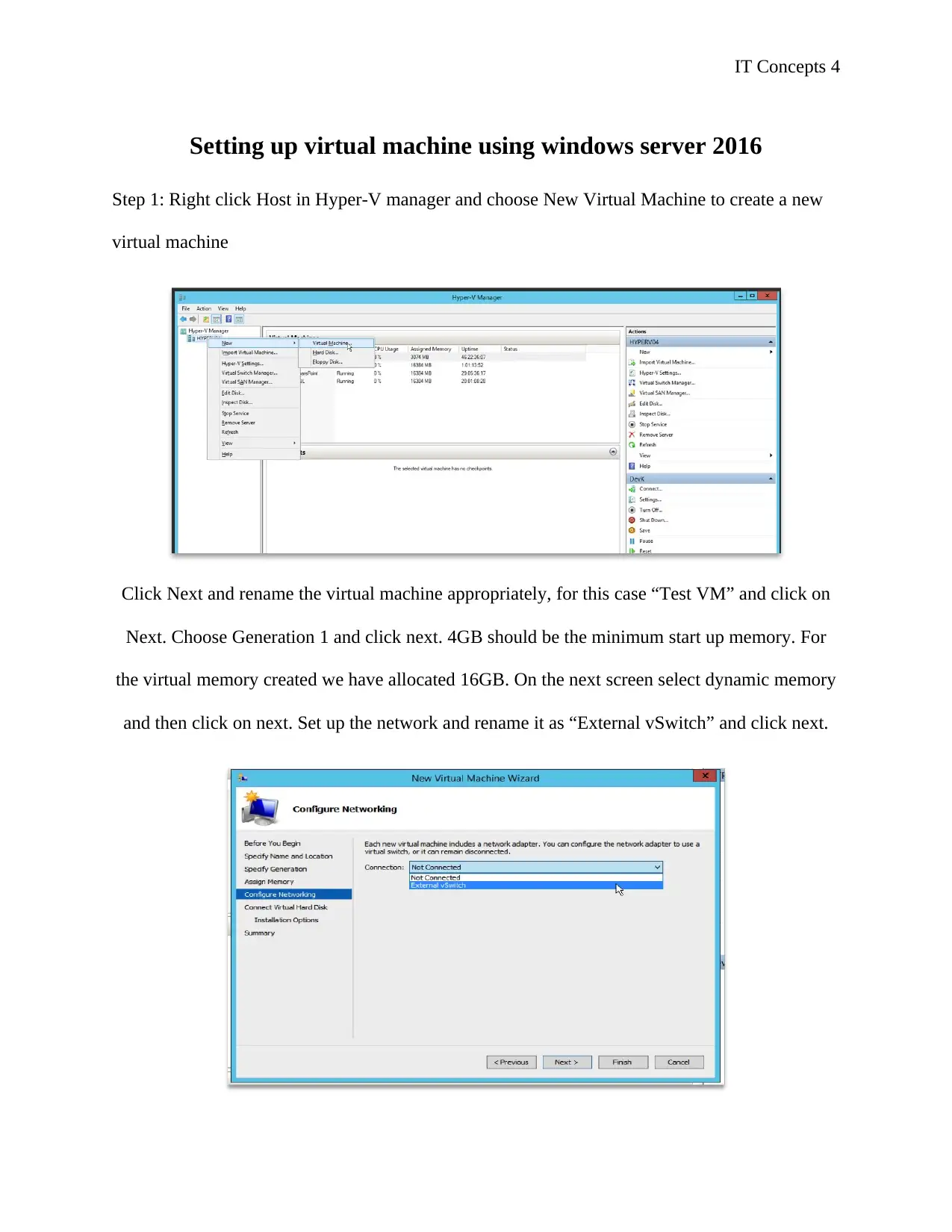
IT Concepts 4
Setting up virtual machine using windows server 2016
Step 1: Right click Host in Hyper-V manager and choose New Virtual Machine to create a new
virtual machine
Click Next and rename the virtual machine appropriately, for this case “Test VM” and click on
Next. Choose Generation 1 and click next. 4GB should be the minimum start up memory. For
the virtual memory created we have allocated 16GB. On the next screen select dynamic memory
and then click on next. Set up the network and rename it as “External vSwitch” and click next.
Setting up virtual machine using windows server 2016
Step 1: Right click Host in Hyper-V manager and choose New Virtual Machine to create a new
virtual machine
Click Next and rename the virtual machine appropriately, for this case “Test VM” and click on
Next. Choose Generation 1 and click next. 4GB should be the minimum start up memory. For
the virtual memory created we have allocated 16GB. On the next screen select dynamic memory
and then click on next. Set up the network and rename it as “External vSwitch” and click next.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
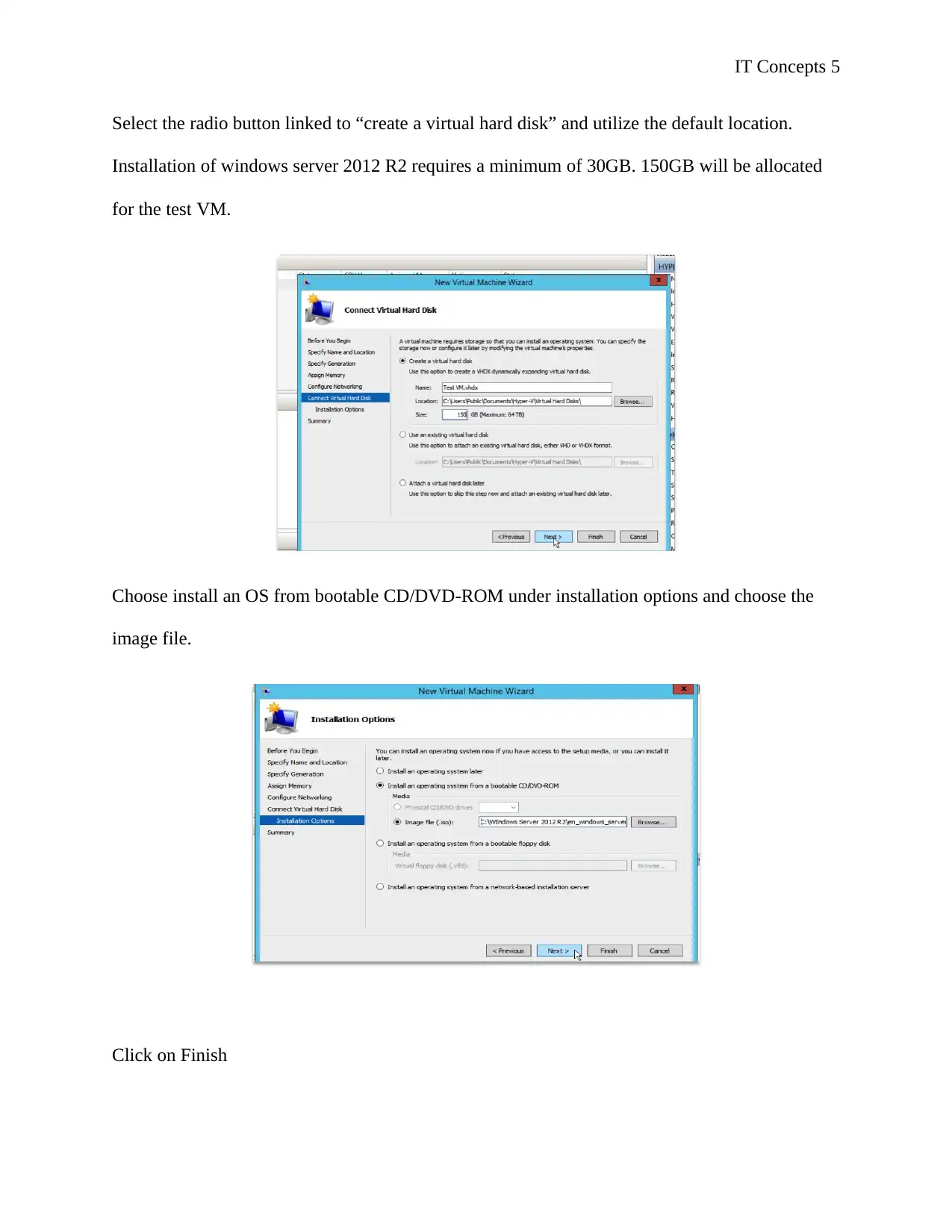
IT Concepts 5
Select the radio button linked to “create a virtual hard disk” and utilize the default location.
Installation of windows server 2012 R2 requires a minimum of 30GB. 150GB will be allocated
for the test VM.
Choose install an OS from bootable CD/DVD-ROM under installation options and choose the
image file.
Click on Finish
Select the radio button linked to “create a virtual hard disk” and utilize the default location.
Installation of windows server 2012 R2 requires a minimum of 30GB. 150GB will be allocated
for the test VM.
Choose install an OS from bootable CD/DVD-ROM under installation options and choose the
image file.
Click on Finish
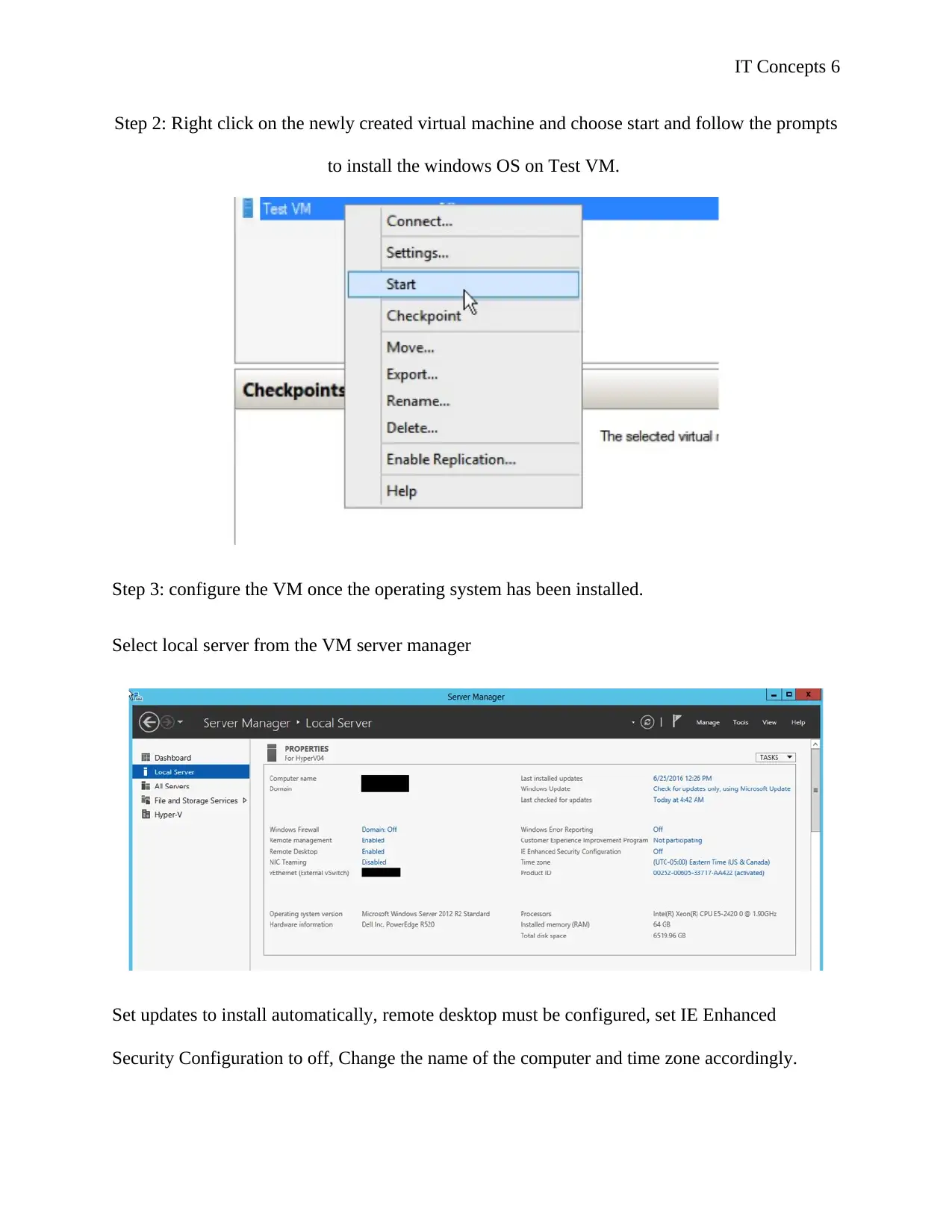
IT Concepts 6
Step 2: Right click on the newly created virtual machine and choose start and follow the prompts
to install the windows OS on Test VM.
Step 3: configure the VM once the operating system has been installed.
Select local server from the VM server manager
Set updates to install automatically, remote desktop must be configured, set IE Enhanced
Security Configuration to off, Change the name of the computer and time zone accordingly.
Step 2: Right click on the newly created virtual machine and choose start and follow the prompts
to install the windows OS on Test VM.
Step 3: configure the VM once the operating system has been installed.
Select local server from the VM server manager
Set updates to install automatically, remote desktop must be configured, set IE Enhanced
Security Configuration to off, Change the name of the computer and time zone accordingly.
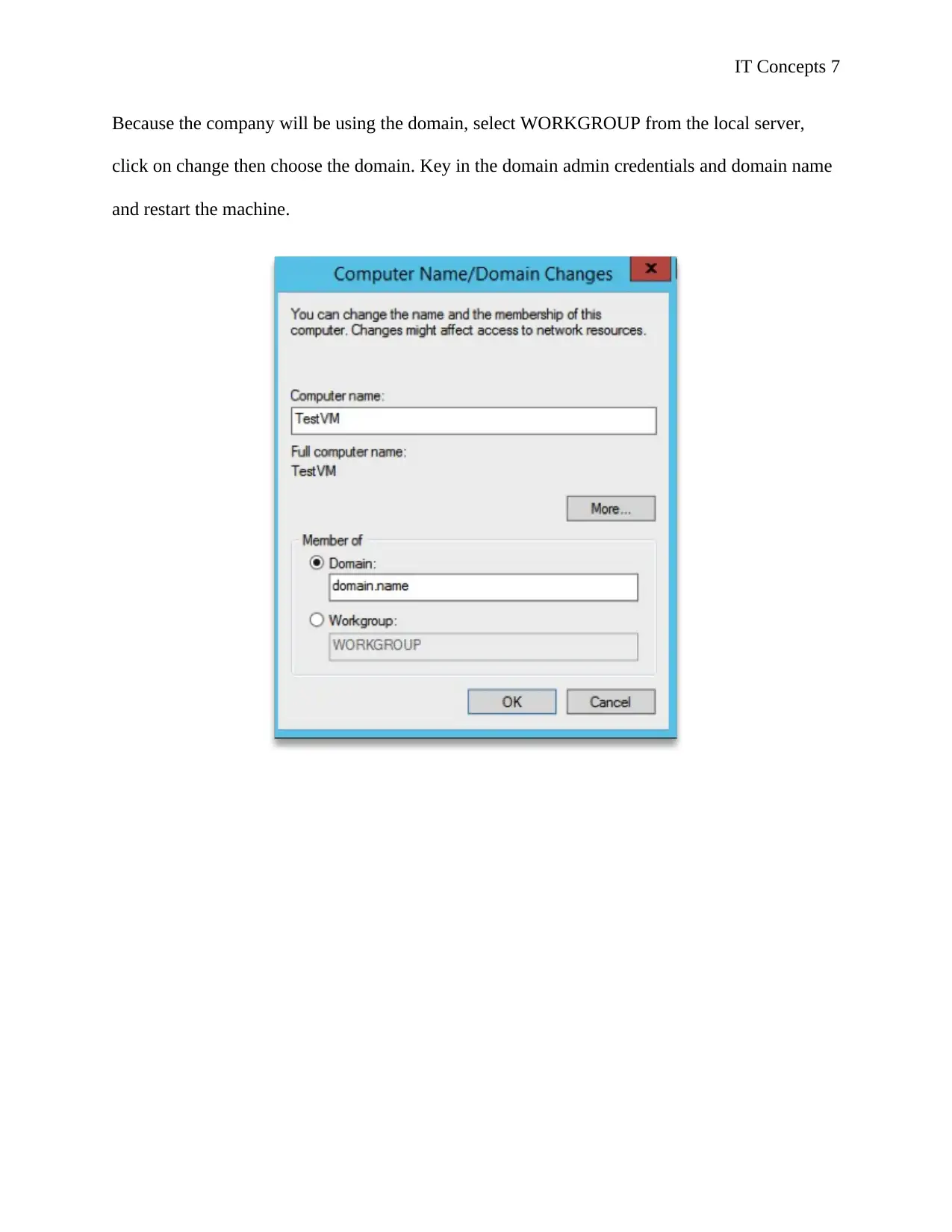
IT Concepts 7
Because the company will be using the domain, select WORKGROUP from the local server,
click on change then choose the domain. Key in the domain admin credentials and domain name
and restart the machine.
Because the company will be using the domain, select WORKGROUP from the local server,
click on change then choose the domain. Key in the domain admin credentials and domain name
and restart the machine.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 8
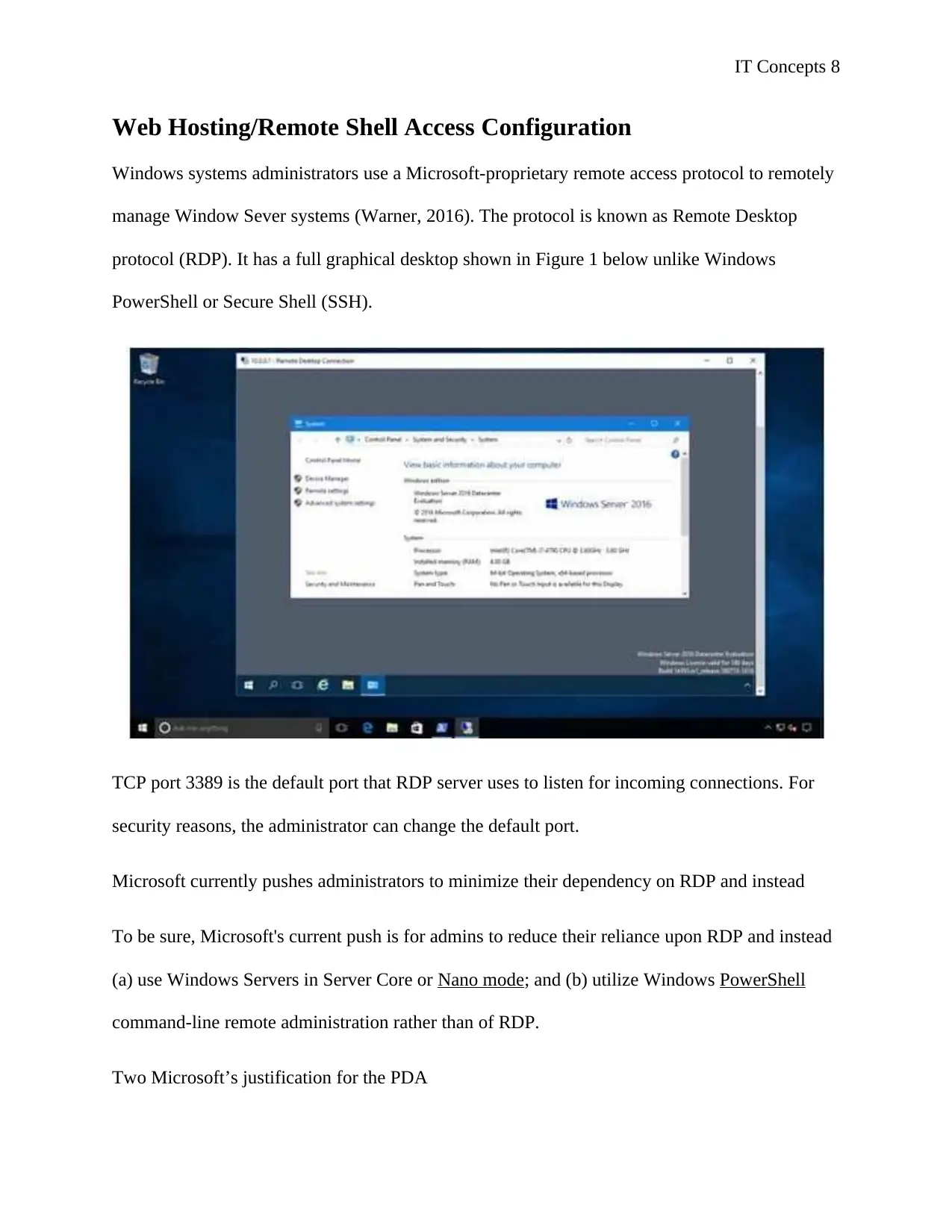
Web Hosting/Remote Shell Access Configuration
Windows systems administrators use a Microsoft-proprietary remote access protocol to remotely
manage Window Sever systems (Warner, 2016). The protocol is known as Remote Desktop
protocol (RDP). It has a full graphical desktop shown in Figure 1 below unlike Windows
PowerShell or Secure Shell (SSH).
TCP port 3389 is the default port that RDP server uses to listen for incoming connections. For
security reasons, the administrator can change the default port.
Microsoft currently pushes administrators to minimize their dependency on RDP and instead
To be sure, Microsoft's current push is for admins to reduce their reliance upon RDP and instead
(a) use Windows Servers in Server Core or Nano mode; and (b) utilize Windows PowerShell
command-line remote administration rather than of RDP.
Two Microsoft’s justification for the PDA
Web Hosting/Remote Shell Access Configuration
Windows systems administrators use a Microsoft-proprietary remote access protocol to remotely
manage Window Sever systems (Warner, 2016). The protocol is known as Remote Desktop
protocol (RDP). It has a full graphical desktop shown in Figure 1 below unlike Windows
PowerShell or Secure Shell (SSH).
TCP port 3389 is the default port that RDP server uses to listen for incoming connections. For
security reasons, the administrator can change the default port.
Microsoft currently pushes administrators to minimize their dependency on RDP and instead
To be sure, Microsoft's current push is for admins to reduce their reliance upon RDP and instead
(a) use Windows Servers in Server Core or Nano mode; and (b) utilize Windows PowerShell
command-line remote administration rather than of RDP.
Two Microsoft’s justification for the PDA
IT Concepts 9
A GUI interface uses unnecessary system resources
A GUI interface broadens the attack surface of your servers
Irrespective, many administrators are used to RDB- based remote administration and likely to do
the same in the recently released Windows Server 2016 Operating System (Cisco, 2016). The
procedure of enabling RDP in Server 2016 is as follows (the procedure is the same to that of
windows server 2012 R2).
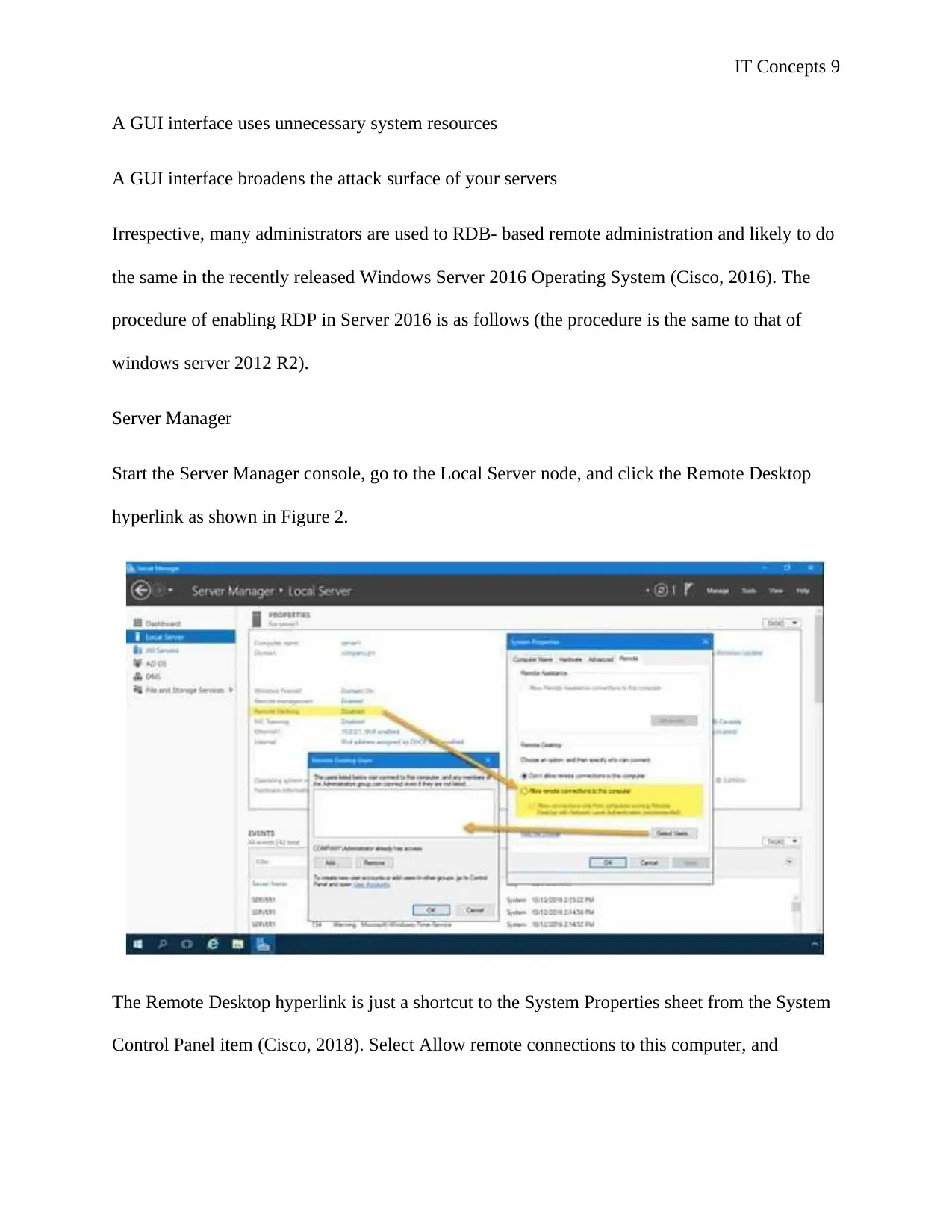
Server Manager
Start the Server Manager console, go to the Local Server node, and click the Remote Desktop
hyperlink as shown in Figure 2.
The Remote Desktop hyperlink is just a shortcut to the System Properties sheet from the System
Control Panel item (Cisco, 2018). Select Allow remote connections to this computer, and
A GUI interface uses unnecessary system resources
A GUI interface broadens the attack surface of your servers
Irrespective, many administrators are used to RDB- based remote administration and likely to do
the same in the recently released Windows Server 2016 Operating System (Cisco, 2016). The
procedure of enabling RDP in Server 2016 is as follows (the procedure is the same to that of
windows server 2012 R2).
Server Manager
Start the Server Manager console, go to the Local Server node, and click the Remote Desktop
hyperlink as shown in Figure 2.
The Remote Desktop hyperlink is just a shortcut to the System Properties sheet from the System
Control Panel item (Cisco, 2018). Select Allow remote connections to this computer, and

IT Concepts 10
optionally enable Allow connections only from computers running Remote Desktop with
Network Level Authentication (recommended).
Windows Server is protected against Denial of Service Attacks by the Network Authentication
(NLA).
Before any the server establishes any graphical session, it requires authentication to take place
(Markle, 2017). The NLA also allows the Server to conserve system resource.
Windows PowerShell
From a lower-point of view, incoming RDP connections can be enabled on using two Registry
values and a Windows Firewall rule on the server. Run the following commands after opening an
elevated Windows PowerShell session.
This create the fDenyTSConnections value and set it to 0 (off). This is important as we don't
want to reject Terminal Services (TS) connections.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal Server' -Name
'fDenyTSConnections' -Value 0 -PropertyType dword -Force
UserAuthentication valu (NLA) is created and enabled by the second command. Network Layer
Authentication is important and should be enabled by default in the server.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal
ServerWinStationsRDP-Tcp' -Name 'UserAuthentication' -Value 1 -PropertyType dword -Force
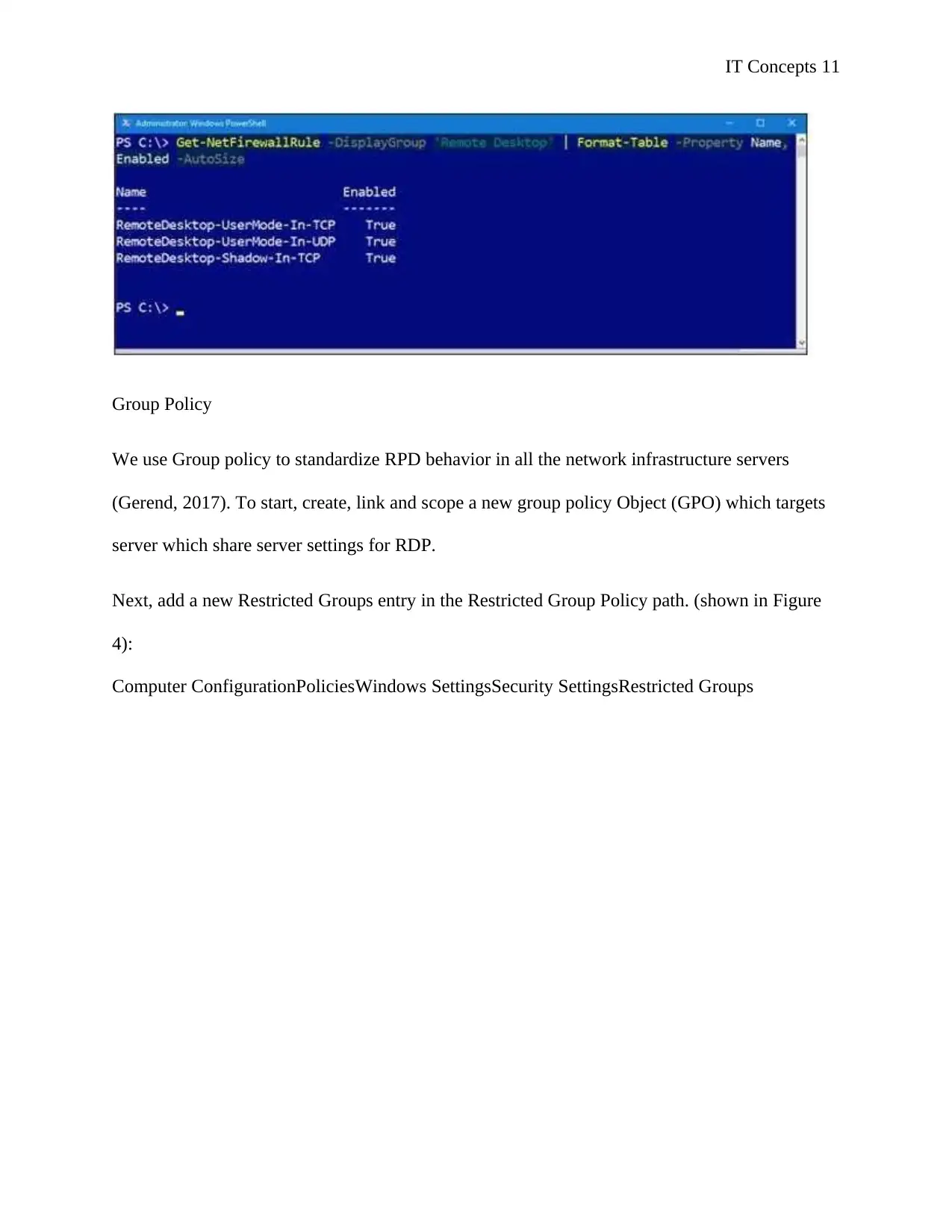
Use the next command to enable Predefined “Remote Desktop” windows firewall rule. This can
be then invoked by the Get-NetFirewallRule PowerShell cmdlet to verify as shown in Figure 3.
Enable-NetFirewallRule -DisplayGroup 'Remote Desktop'
optionally enable Allow connections only from computers running Remote Desktop with
Network Level Authentication (recommended).
Windows Server is protected against Denial of Service Attacks by the Network Authentication
(NLA).
Before any the server establishes any graphical session, it requires authentication to take place
(Markle, 2017). The NLA also allows the Server to conserve system resource.
Windows PowerShell
From a lower-point of view, incoming RDP connections can be enabled on using two Registry
values and a Windows Firewall rule on the server. Run the following commands after opening an
elevated Windows PowerShell session.
This create the fDenyTSConnections value and set it to 0 (off). This is important as we don't
want to reject Terminal Services (TS) connections.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal Server' -Name
'fDenyTSConnections' -Value 0 -PropertyType dword -Force
UserAuthentication valu (NLA) is created and enabled by the second command. Network Layer
Authentication is important and should be enabled by default in the server.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal
ServerWinStationsRDP-Tcp' -Name 'UserAuthentication' -Value 1 -PropertyType dword -Force
Use the next command to enable Predefined “Remote Desktop” windows firewall rule. This can
be then invoked by the Get-NetFirewallRule PowerShell cmdlet to verify as shown in Figure 3.
Enable-NetFirewallRule -DisplayGroup 'Remote Desktop'
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IT Concepts 11
Group Policy
We use Group policy to standardize RPD behavior in all the network infrastructure servers
(Gerend, 2017). To start, create, link and scope a new group policy Object (GPO) which targets
server which share server settings for RDP.
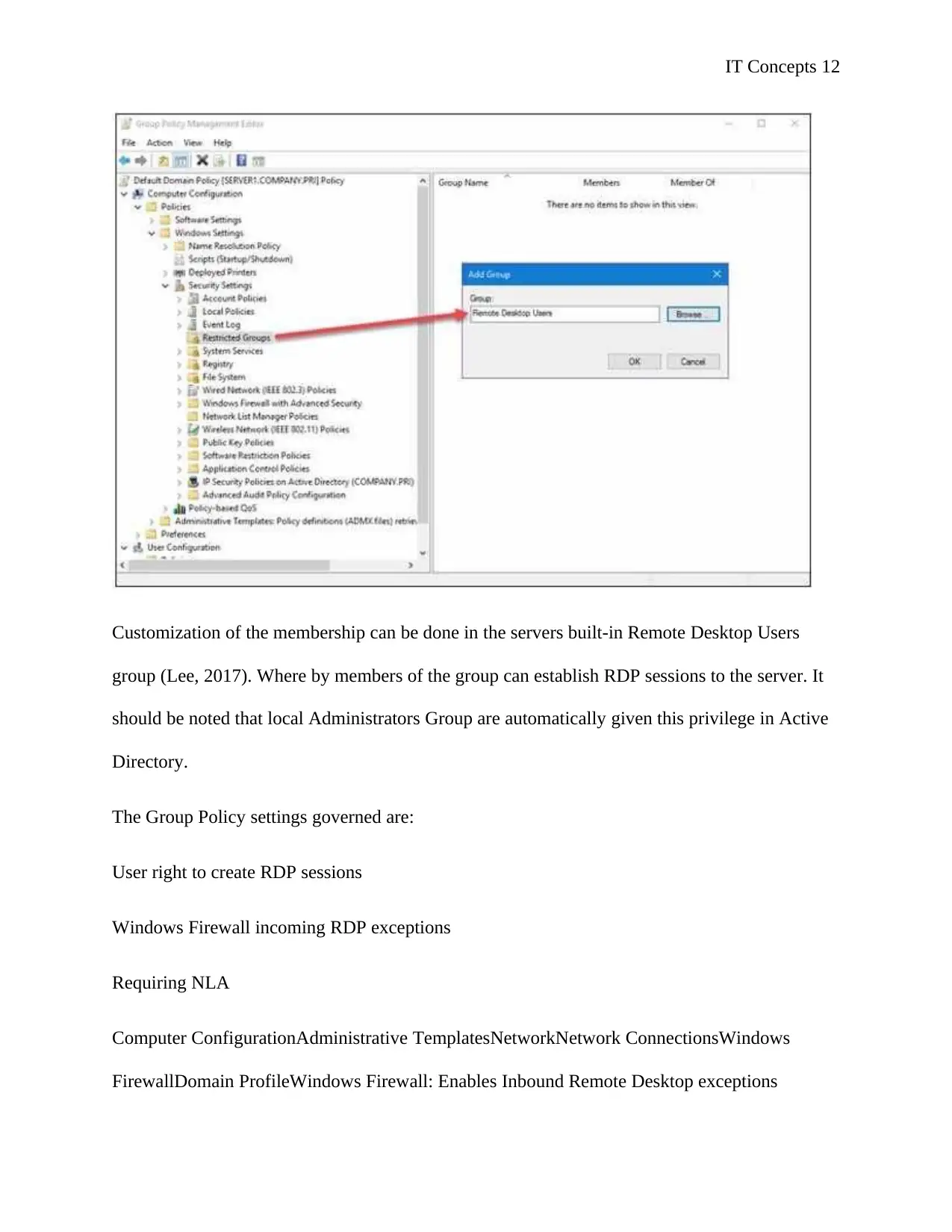
Next, add a new Restricted Groups entry in the Restricted Group Policy path. (shown in Figure
4):
Computer ConfigurationPoliciesWindows SettingsSecurity SettingsRestricted Groups
Group Policy
We use Group policy to standardize RPD behavior in all the network infrastructure servers
(Gerend, 2017). To start, create, link and scope a new group policy Object (GPO) which targets
server which share server settings for RDP.
Next, add a new Restricted Groups entry in the Restricted Group Policy path. (shown in Figure
4):
Computer ConfigurationPoliciesWindows SettingsSecurity SettingsRestricted Groups
IT Concepts 12
Customization of the membership can be done in the servers built-in Remote Desktop Users
group (Lee, 2017). Where by members of the group can establish RDP sessions to the server. It
should be noted that local Administrators Group are automatically given this privilege in Active
Directory.
The Group Policy settings governed are:
User right to create RDP sessions
Windows Firewall incoming RDP exceptions
Requiring NLA
Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows
FirewallDomain ProfileWindows Firewall: Enables Inbound Remote Desktop exceptions
Customization of the membership can be done in the servers built-in Remote Desktop Users
group (Lee, 2017). Where by members of the group can establish RDP sessions to the server. It
should be noted that local Administrators Group are automatically given this privilege in Active
Directory.
The Group Policy settings governed are:
User right to create RDP sessions
Windows Firewall incoming RDP exceptions
Requiring NLA
Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows
FirewallDomain ProfileWindows Firewall: Enables Inbound Remote Desktop exceptions

IT Concepts 13
Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop
ServicesRemote Desktop Session HostConnections enables the user to connect remotely in the
Remote Desktop Services.
Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop
ServicesRemote Desktop Session HostSecurityRequire authenticates users for remote
connections using Network Layer Authentication.
Creating the Client Connection
Microsoft RDP client is included in both Windows Server and Windows Client, and it is called
Remote Desktop Connection. The best way to invoke this tool is as follows:
Press WINDOWS KEY+R
Type mstsc (Microsoft Terminal Services Client)
Press ENTER
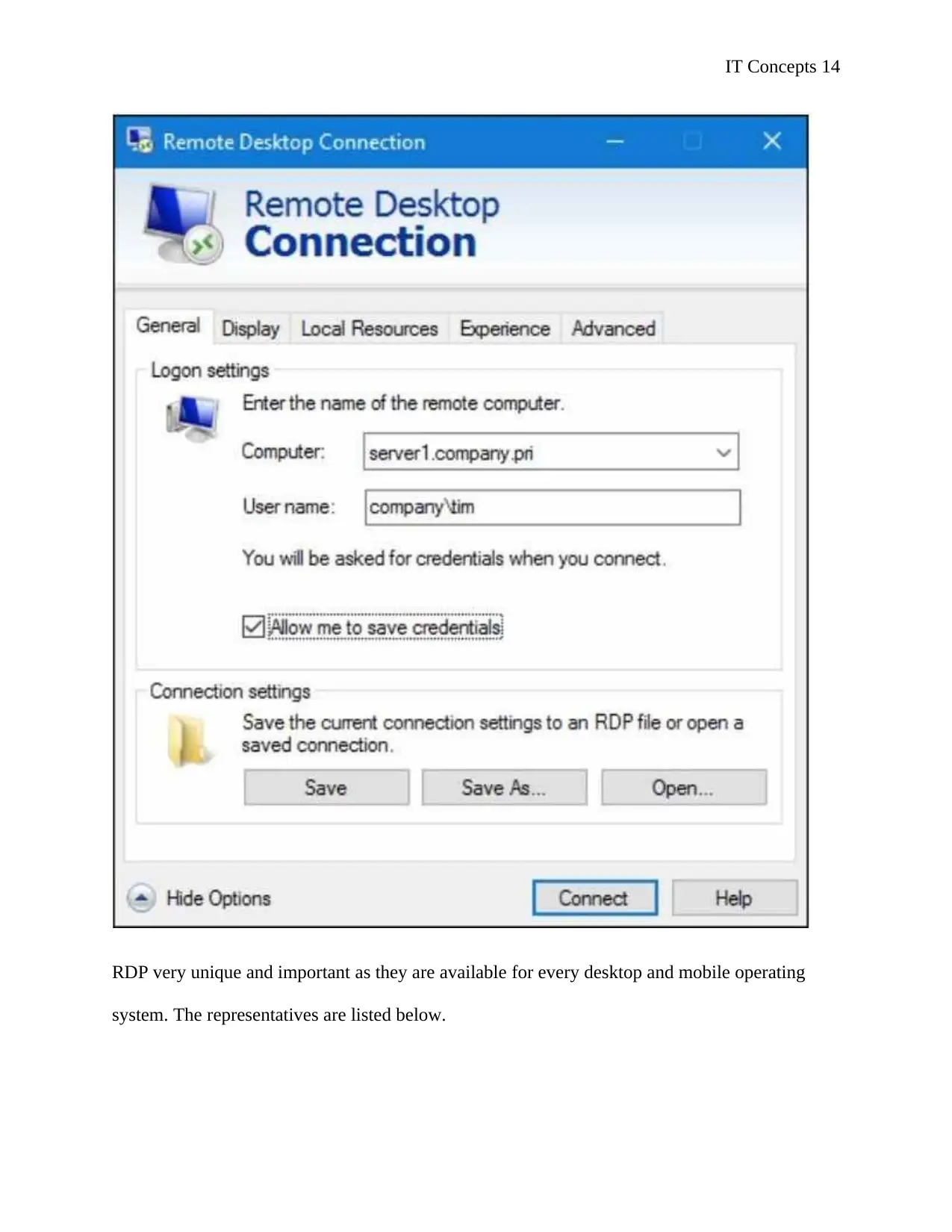
Figure 5 below is the Remote Desktop Connection interface for the user.
Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop
ServicesRemote Desktop Session HostConnections enables the user to connect remotely in the
Remote Desktop Services.
Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop
ServicesRemote Desktop Session HostSecurityRequire authenticates users for remote
connections using Network Layer Authentication.
Creating the Client Connection
Microsoft RDP client is included in both Windows Server and Windows Client, and it is called
Remote Desktop Connection. The best way to invoke this tool is as follows:
Press WINDOWS KEY+R
Type mstsc (Microsoft Terminal Services Client)
Press ENTER
Figure 5 below is the Remote Desktop Connection interface for the user.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 14
RDP very unique and important as they are available for every desktop and mobile operating
system. The representatives are listed below.
RDP very unique and important as they are available for every desktop and mobile operating
system. The representatives are listed below.

IT Concepts 15
iOS: Microsoft Remote Desktop
Android: Microsoft Remote Desktop
HTTP and HTTP services Configuration
Make sure that you have copied the —–BEGIN CERTIFICATE—– and —–END
CERTIFICATE—– when copying the SSL certificate. Confirm that there are no white spaces, no
line breaks and no additional characters. Using a text editor like as Notepad, paste the certificate
content and save it with an extension .p7b (if you are using a Windows system the icon should
change into an icon of the certificate.
Step 2: Installing the SSL Certificate
Navigate to Start, then administrative tools and then to internet information services (IIS)
Manager
Click the server name on the left menu.
Double click the Server Certificates located in the middle of the pane under security.
Select Complete Certificate Request at the Right Action pane.
iOS: Microsoft Remote Desktop
Android: Microsoft Remote Desktop
HTTP and HTTP services Configuration
Make sure that you have copied the —–BEGIN CERTIFICATE—– and —–END
CERTIFICATE—– when copying the SSL certificate. Confirm that there are no white spaces, no
line breaks and no additional characters. Using a text editor like as Notepad, paste the certificate
content and save it with an extension .p7b (if you are using a Windows system the icon should
change into an icon of the certificate.
Step 2: Installing the SSL Certificate
Navigate to Start, then administrative tools and then to internet information services (IIS)
Manager
Click the server name on the left menu.
Double click the Server Certificates located in the middle of the pane under security.
Select Complete Certificate Request at the Right Action pane.
IT Concepts 16
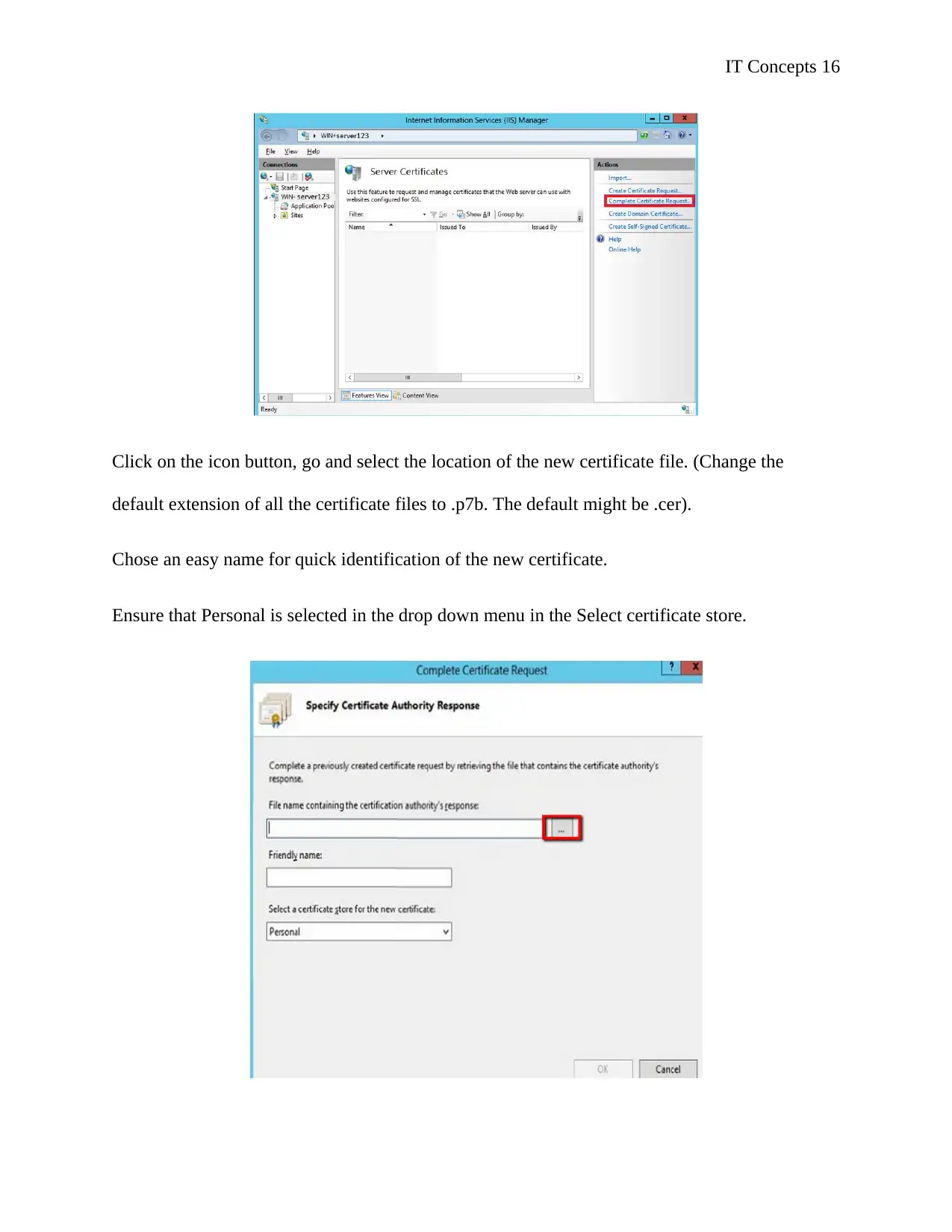
Click on the icon button, go and select the location of the new certificate file. (Change the
default extension of all the certificate files to .p7b. The default might be .cer).
Chose an easy name for quick identification of the new certificate.
Ensure that Personal is selected in the drop down menu in the Select certificate store.
Click on the icon button, go and select the location of the new certificate file. (Change the
default extension of all the certificate files to .p7b. The default might be .cer).
Chose an easy name for quick identification of the new certificate.
Ensure that Personal is selected in the drop down menu in the Select certificate store.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IT Concepts 17
NOTE: during the system installation you may receive an error message. A glitch with the IIS 7
to IIS 8 series causes it.
To acknowledge the error message, click Ok and then Cancel out of the Complete Certificate
Request Wizard.
Press the F5 button on the keyboard to in order to refresh the IIs console. The new certificate will
appear under the Server Certificates in the middle pane. It might not have the name you chose.
The installation will be successful if you are able to see the new certificate.
Note: The CSR request was not created if you can see the new certificate or the private key was
damaged as a result. To correct this, generate a new CSr request and reissue the certificate.
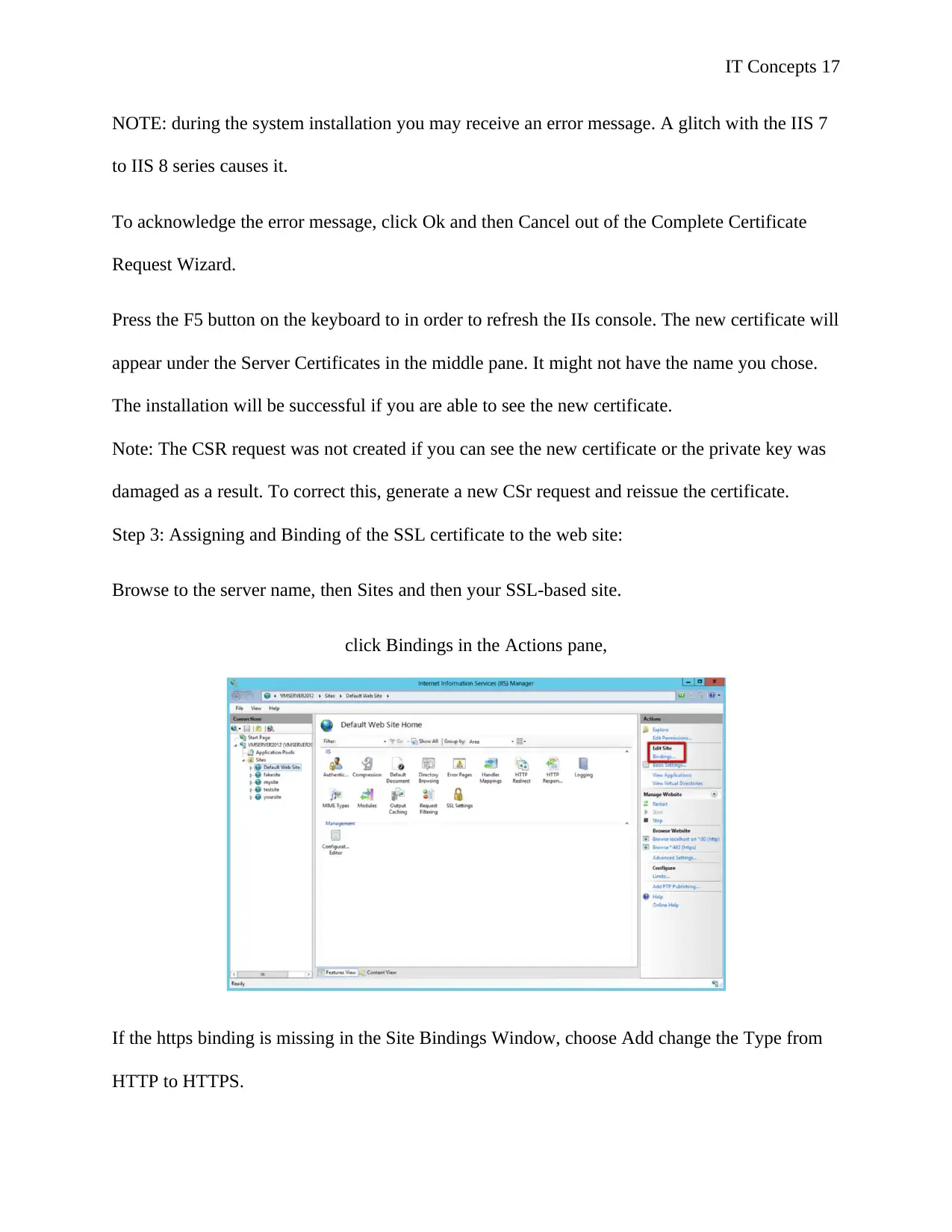
Step 3: Assigning and Binding of the SSL certificate to the web site:
Browse to the server name, then Sites and then your SSL-based site.
click Bindings in the Actions pane,
If the https binding is missing in the Site Bindings Window, choose Add change the Type from
HTTP to HTTPS.
NOTE: during the system installation you may receive an error message. A glitch with the IIS 7
to IIS 8 series causes it.
To acknowledge the error message, click Ok and then Cancel out of the Complete Certificate
Request Wizard.
Press the F5 button on the keyboard to in order to refresh the IIs console. The new certificate will
appear under the Server Certificates in the middle pane. It might not have the name you chose.
The installation will be successful if you are able to see the new certificate.
Note: The CSR request was not created if you can see the new certificate or the private key was
damaged as a result. To correct this, generate a new CSr request and reissue the certificate.
Step 3: Assigning and Binding of the SSL certificate to the web site:
Browse to the server name, then Sites and then your SSL-based site.
click Bindings in the Actions pane,
If the https binding is missing in the Site Bindings Window, choose Add change the Type from
HTTP to HTTPS.
IT Concepts 18
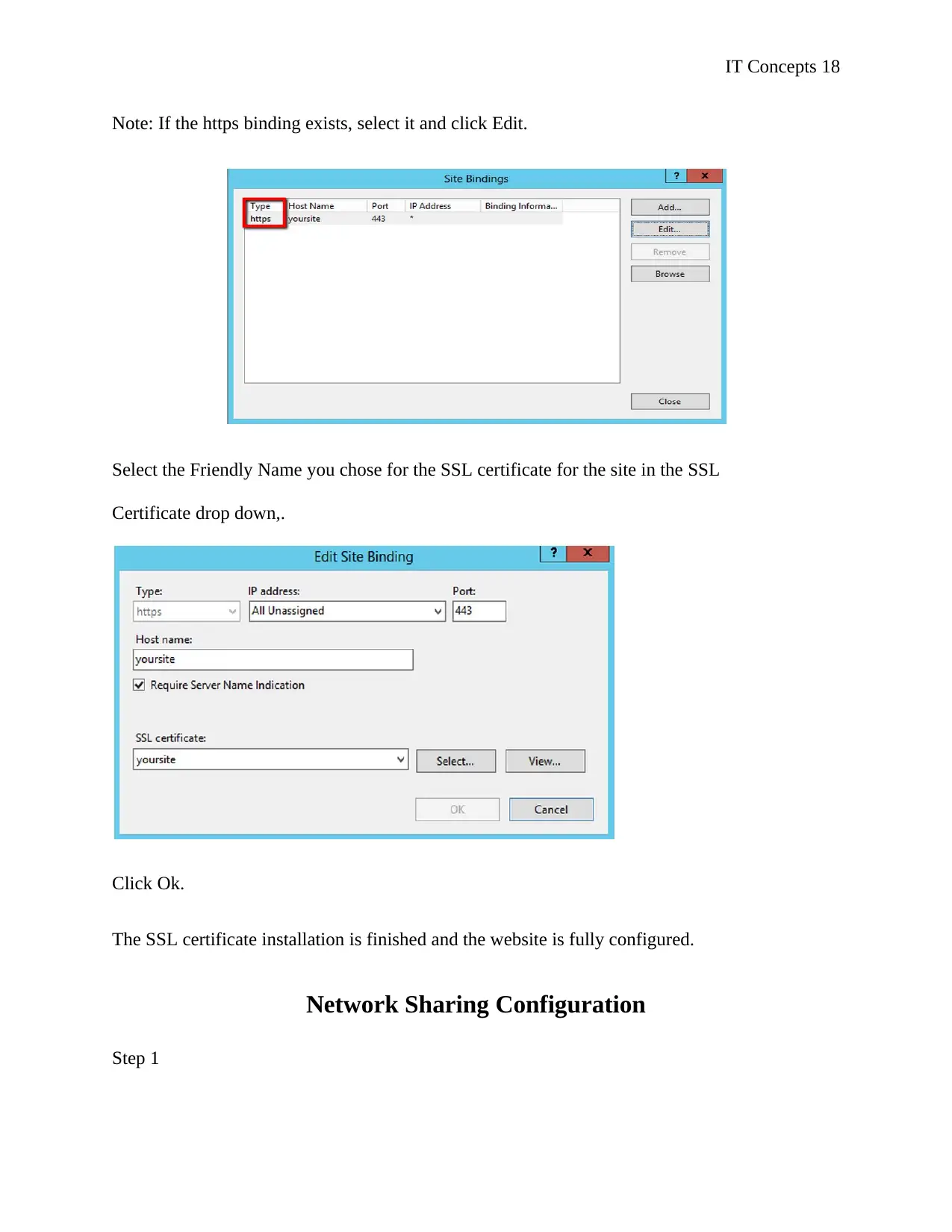
Note: If the https binding exists, select it and click Edit.
Select the Friendly Name you chose for the SSL certificate for the site in the SSL
Certificate drop down,.
Click Ok.
The SSL certificate installation is finished and the website is fully configured.
Network Sharing Configuration
Step 1
Note: If the https binding exists, select it and click Edit.
Select the Friendly Name you chose for the SSL certificate for the site in the SSL
Certificate drop down,.
Click Ok.
The SSL certificate installation is finished and the website is fully configured.
Network Sharing Configuration
Step 1
IT Concepts 19
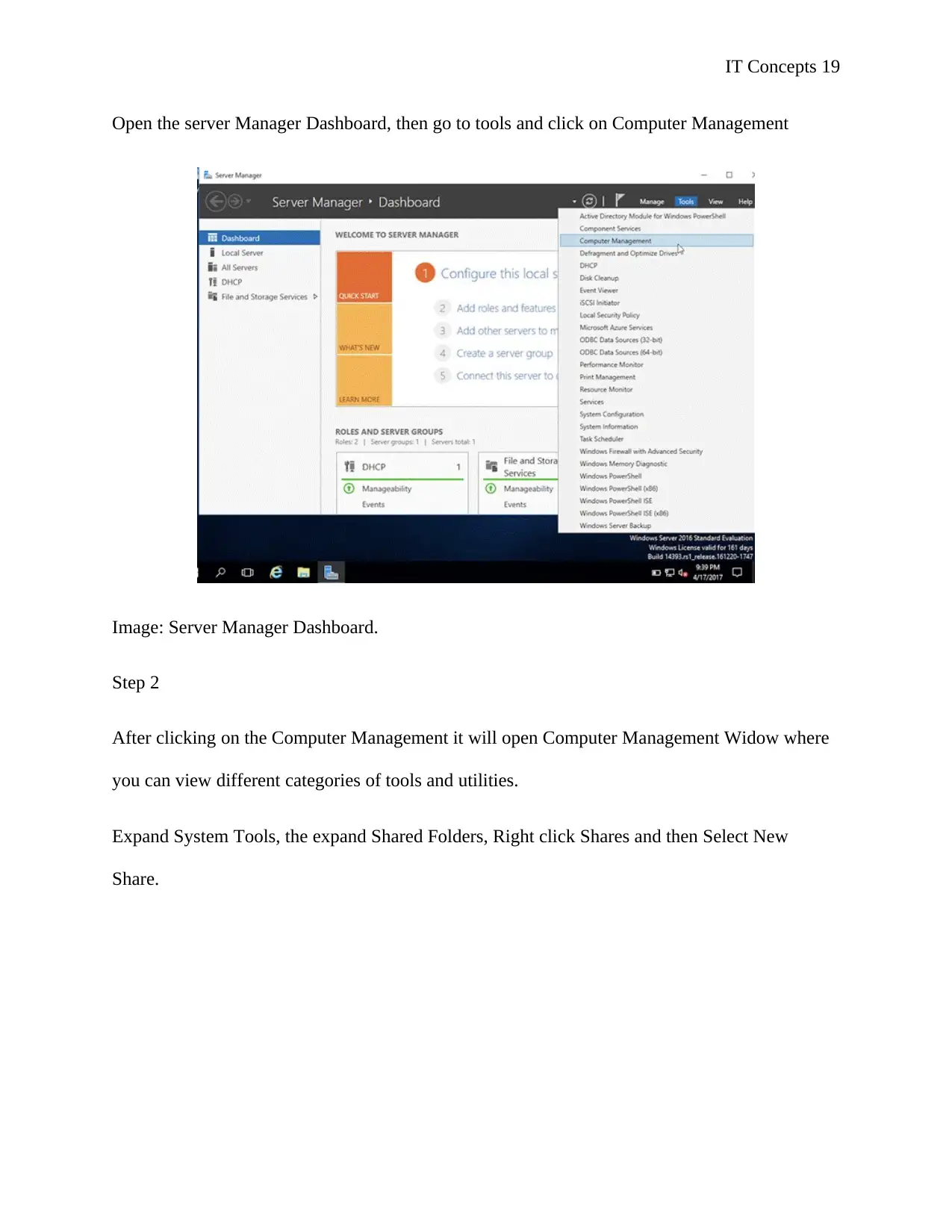
Open the server Manager Dashboard, then go to tools and click on Computer Management
Image: Server Manager Dashboard.
Step 2
After clicking on the Computer Management it will open Computer Management Widow where
you can view different categories of tools and utilities.
Expand System Tools, the expand Shared Folders, Right click Shares and then Select New
Share.
Open the server Manager Dashboard, then go to tools and click on Computer Management
Image: Server Manager Dashboard.
Step 2
After clicking on the Computer Management it will open Computer Management Widow where
you can view different categories of tools and utilities.
Expand System Tools, the expand Shared Folders, Right click Shares and then Select New
Share.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 20
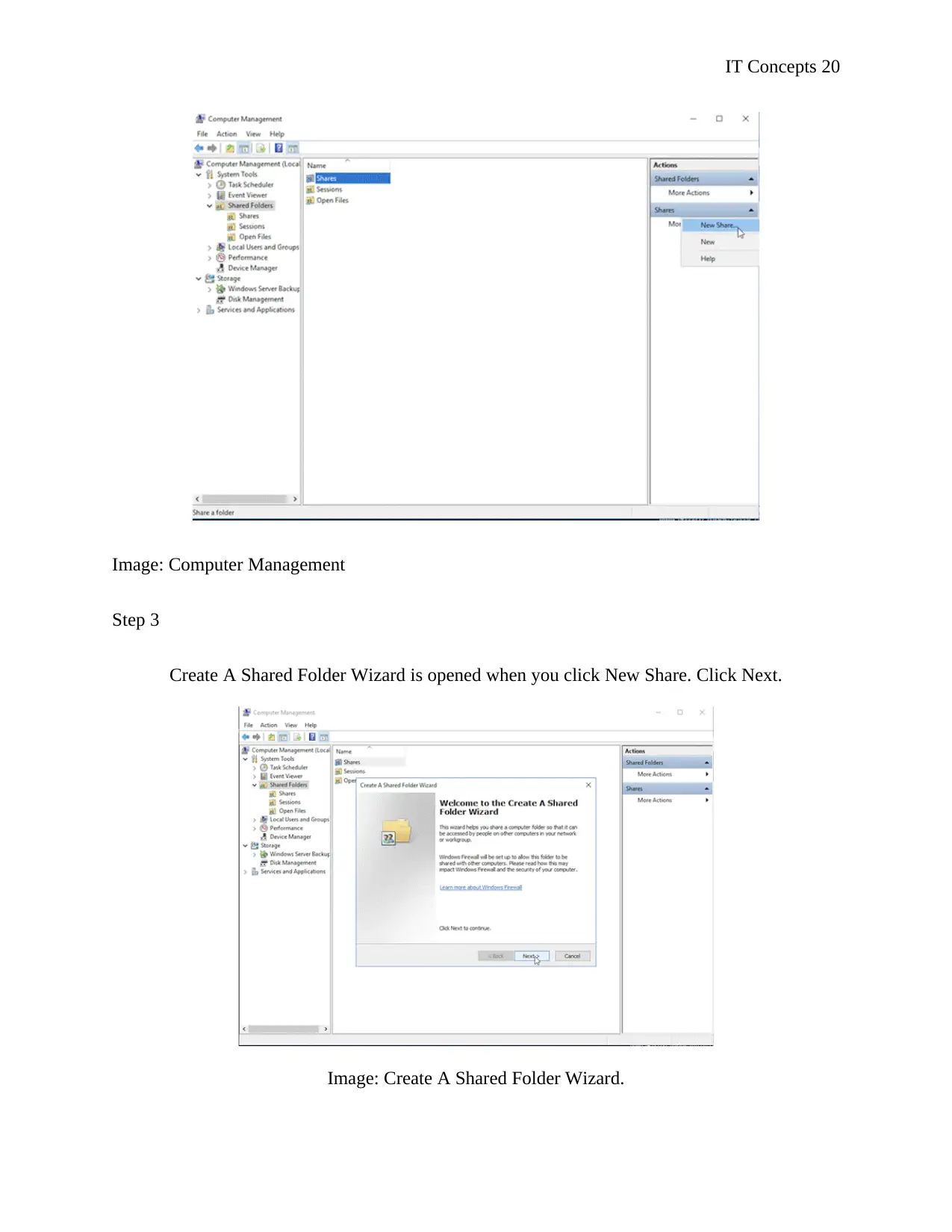
Image: Computer Management
Step 3
Create A Shared Folder Wizard is opened when you click New Share. Click Next.
Image: Create A Shared Folder Wizard.
Image: Computer Management
Step 3
Create A Shared Folder Wizard is opened when you click New Share. Click Next.
Image: Create A Shared Folder Wizard.
IT Concepts 21
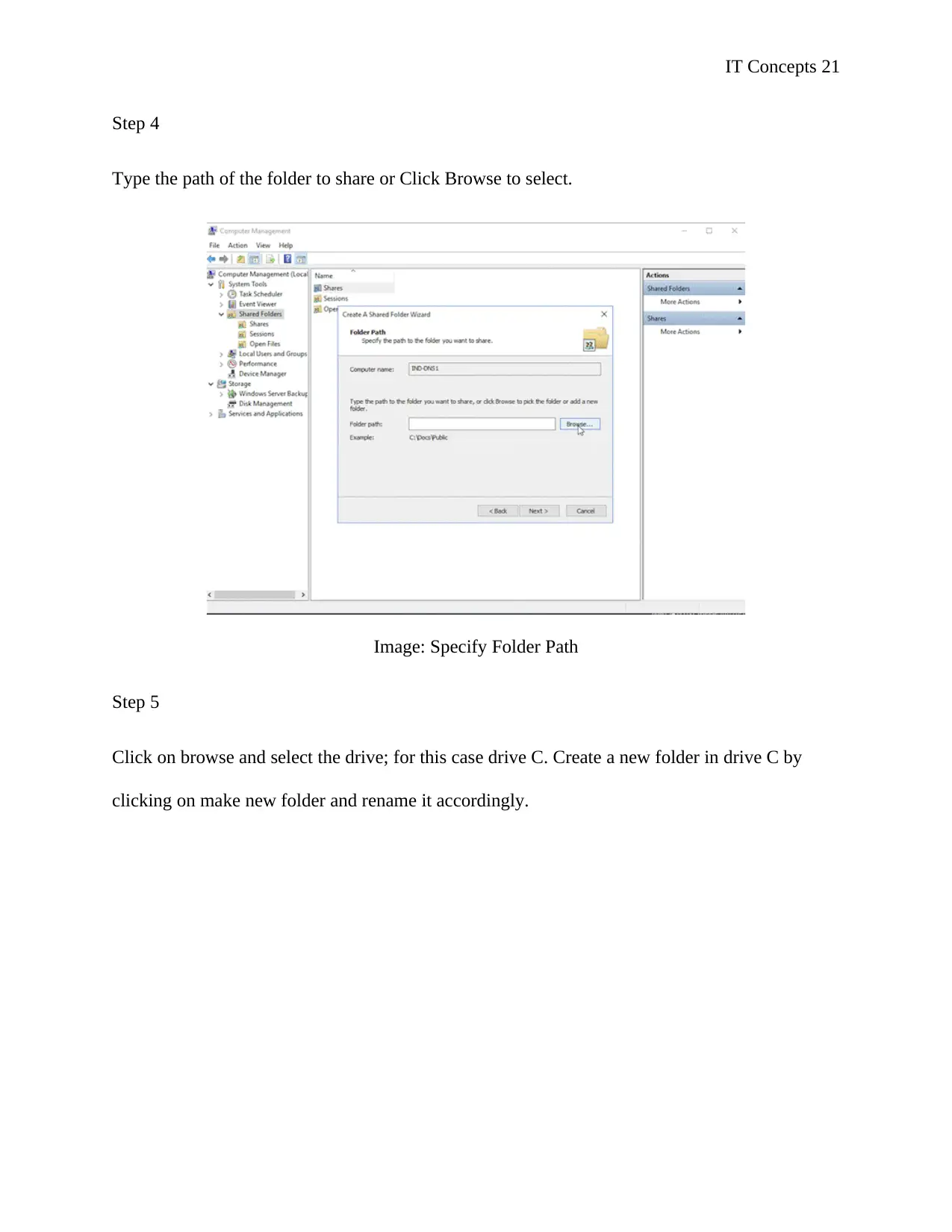
Step 4
Type the path of the folder to share or Click Browse to select.
Image: Specify Folder Path
Step 5
Click on browse and select the drive; for this case drive C. Create a new folder in drive C by
clicking on make new folder and rename it accordingly.
Step 4
Type the path of the folder to share or Click Browse to select.
Image: Specify Folder Path
Step 5
Click on browse and select the drive; for this case drive C. Create a new folder in drive C by
clicking on make new folder and rename it accordingly.
IT Concepts 22
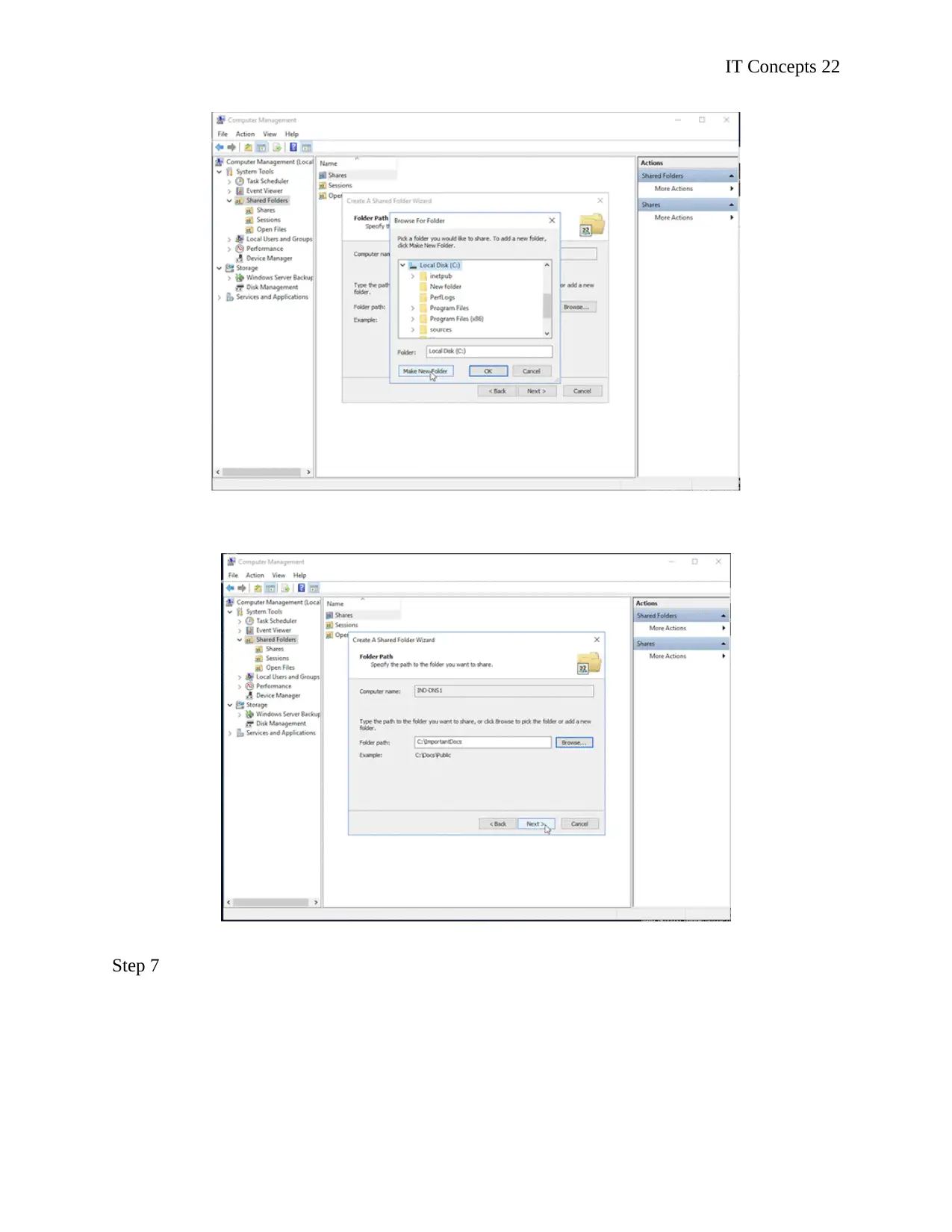
Step 7
Step 7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IT Concepts 23
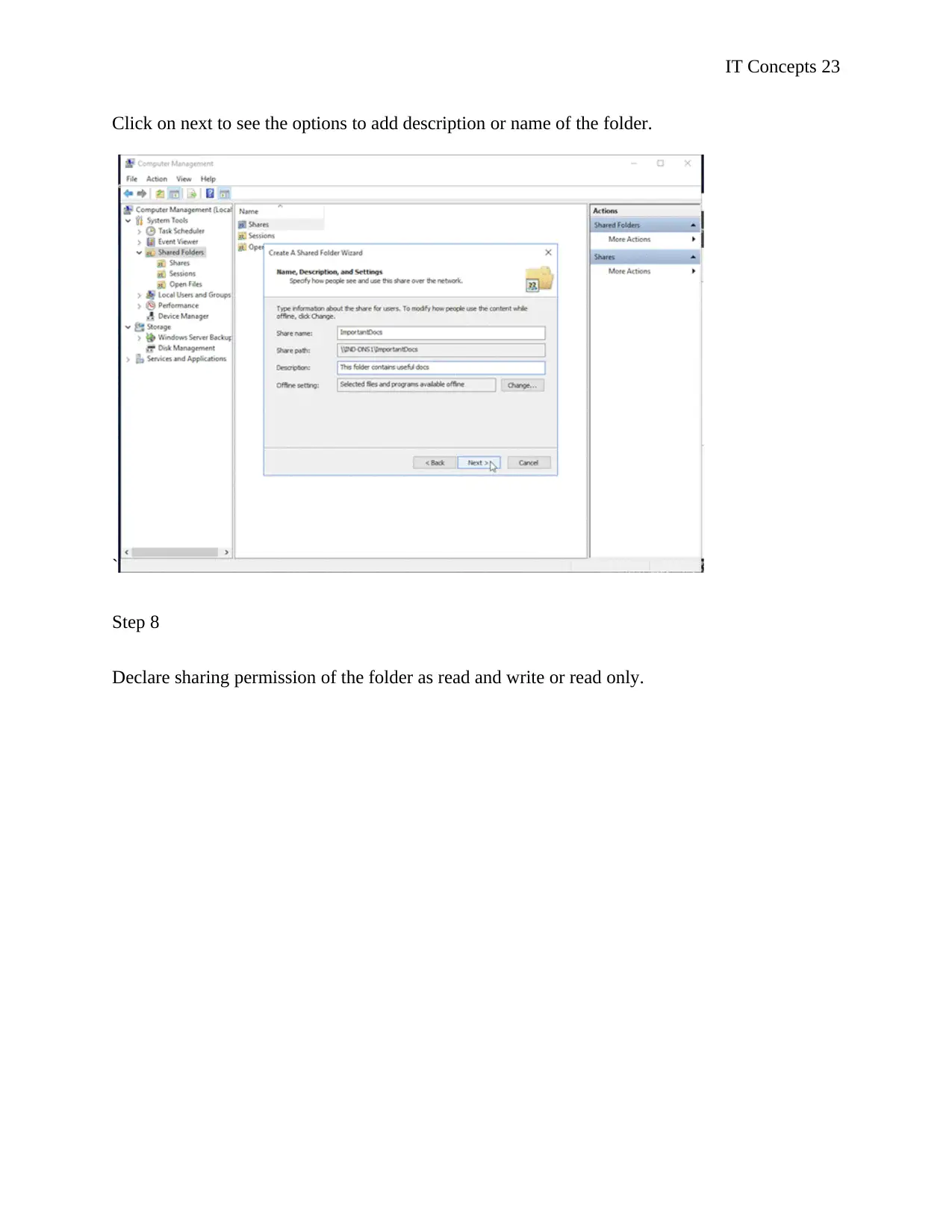
Click on next to see the options to add description or name of the folder.
`
Step 8
Declare sharing permission of the folder as read and write or read only.
Click on next to see the options to add description or name of the folder.
`
Step 8
Declare sharing permission of the folder as read and write or read only.
IT Concepts 24
Configuring Data Duplication
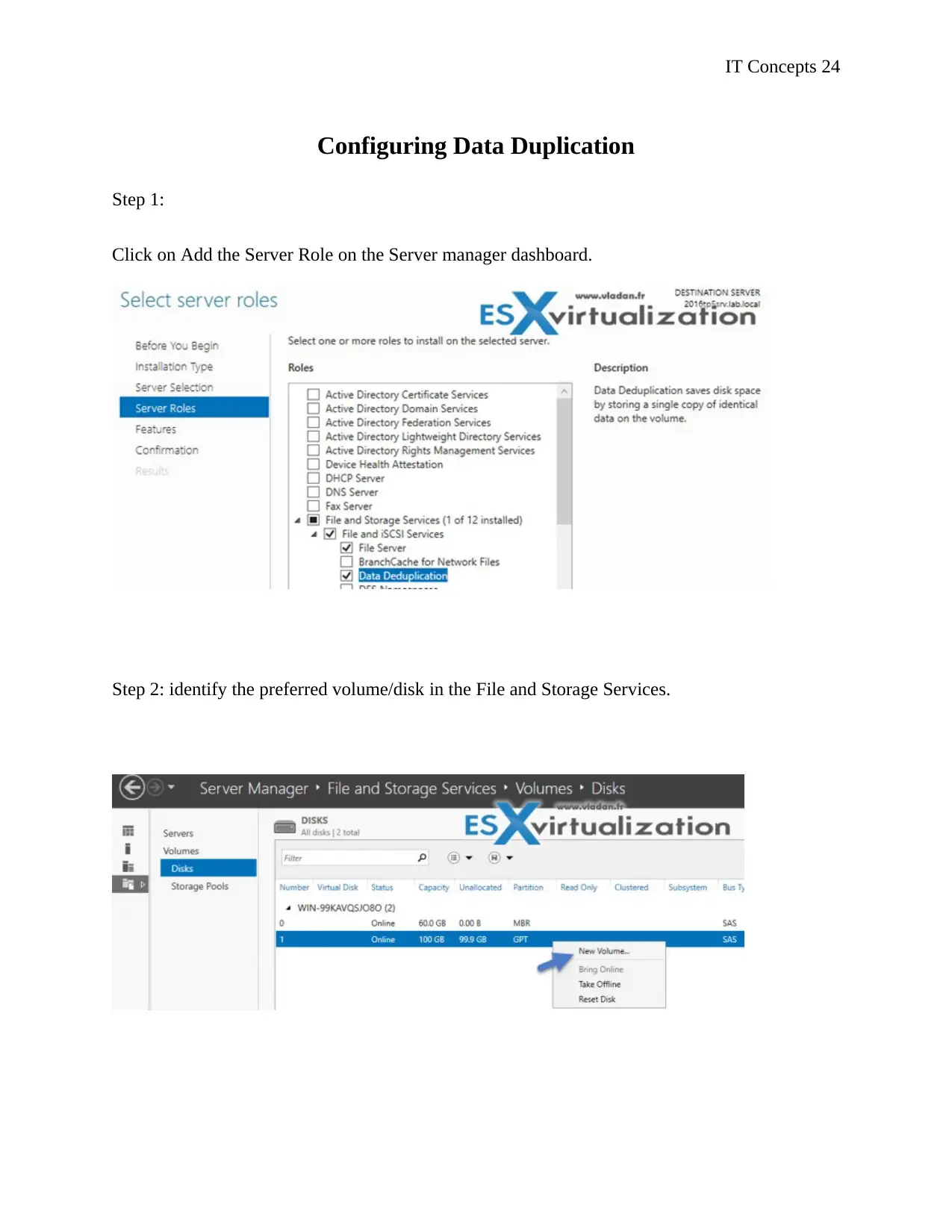
Step 1:
Click on Add the Server Role on the Server manager dashboard.
Step 2: identify the preferred volume/disk in the File and Storage Services.
Configuring Data Duplication
Step 1:
Click on Add the Server Role on the Server manager dashboard.
Step 2: identify the preferred volume/disk in the File and Storage Services.
IT Concepts 25
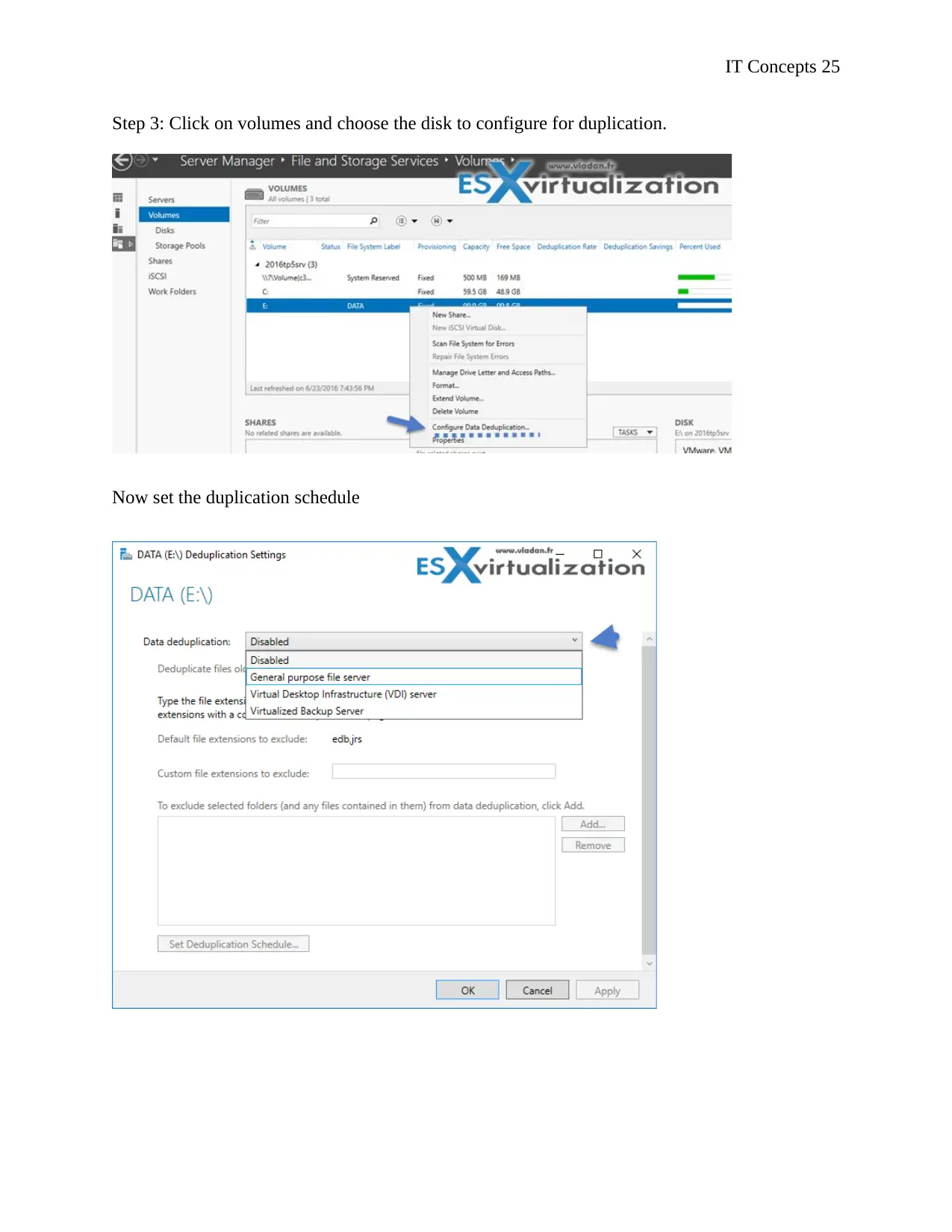
Step 3: Click on volumes and choose the disk to configure for duplication.
Now set the duplication schedule
Step 3: Click on volumes and choose the disk to configure for duplication.
Now set the duplication schedule
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 26
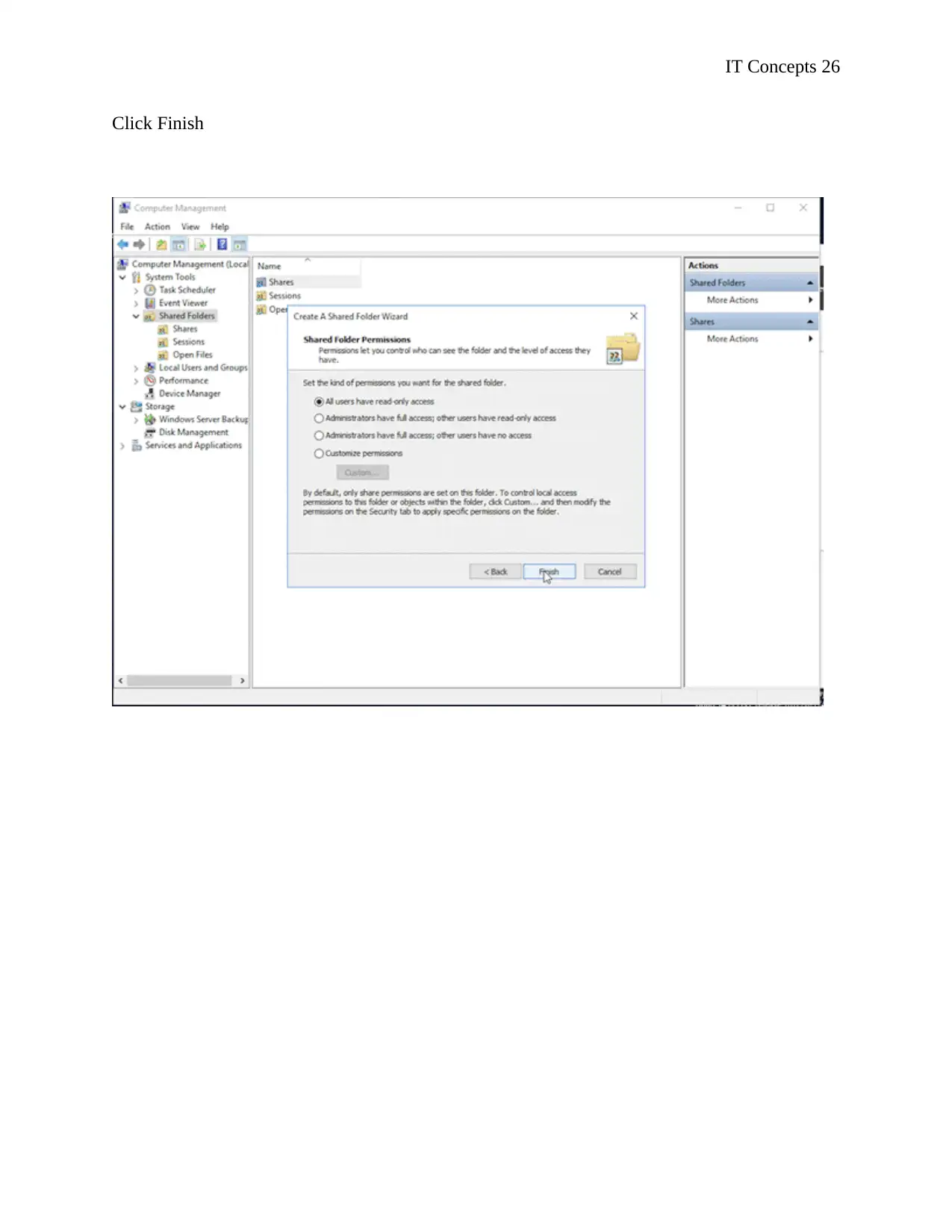
Click Finish
Click Finish
IT Concepts 27
Justifications
Advantages of Windows Sever 2016
Windows server 2016 has new layers of security to enhance privilege identity protection, secure
virtualization, and breach resistance. In addition, it has software defined data centers which are
enterprise ready and affordable, built-in SDDC functionalities, and Azure-inspired infrastructure
(Richard, 2016). Additionally, it offers cloud-ready application environment like microservices,
cloud-native and traditional applications among others.
Importance of Authentication
It is important to only allow authorized users to access the resources with their rights. As such, it is
important for the server to have authentication capabilities so as to be able to allow authorize users
and block unauthorized ones. Authentication also allows clients to determine if the server is what it
Justifications
Advantages of Windows Sever 2016
Windows server 2016 has new layers of security to enhance privilege identity protection, secure
virtualization, and breach resistance. In addition, it has software defined data centers which are
enterprise ready and affordable, built-in SDDC functionalities, and Azure-inspired infrastructure
(Richard, 2016). Additionally, it offers cloud-ready application environment like microservices,
cloud-native and traditional applications among others.
Importance of Authentication
It is important to only allow authorized users to access the resources with their rights. As such, it is
important for the server to have authentication capabilities so as to be able to allow authorize users
and block unauthorized ones. Authentication also allows clients to determine if the server is what it

IT Concepts 28
claims to be (Zhelezko, 2017). Giving the users usernames and passwords to access the server will
help to secure the server and keep logs on who is using the server and the time.
Conclusion
Hypervisor-specific and specialized hardware is not required for the virtual machine. However,
more bandwidth, processing ability, and storage is required by the virtual machine as compared
to the physical computers. One advantage of the VMs is that it can be reassigned, copied, or
moved easily between hosts servers to enhance utilization of resources.
claims to be (Zhelezko, 2017). Giving the users usernames and passwords to access the server will
help to secure the server and keep logs on who is using the server and the time.
Conclusion
Hypervisor-specific and specialized hardware is not required for the virtual machine. However,
more bandwidth, processing ability, and storage is required by the virtual machine as compared
to the physical computers. One advantage of the VMs is that it can be reassigned, copied, or
moved easily between hosts servers to enhance utilization of resources.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Concepts 29
Reference List
Cisco, C. (2016). HTTP Services Configuration Guide - HTTP/HTTPS 1.1 Web Server and
Client [Cisco ASR 1000 Series Aggregation Services Routers]. [online] Cisco. Available at:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/https/configuration/xe-16/https-xe-16-book/
HTTP_1-1_Web_Server_and_Client.html [Accessed 29 Jun. 2018].
Cisco, C. (2018). HTTP Services Configuration Guide - HTTPS--HTTP Server and Client with
SSL 3.0 [Cisco ASR 1000 Series Aggregation Services Routers]. [online] Cisco. Available at:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/https/configuration/xe-16/https-xe-16-book/
HTTPS--HTTP_Server_and_Client_with_SSL_3-0.html [Accessed 29 Jun. 2018].
Gerend, J. (2017). Installing and enabling Data Deduplication. [online] Docs.microsoft.com.
Available at: https://docs.microsoft.com/en-us/windows-server/storage/data-deduplication/
install-enable [Accessed 29 Jun. 2018].
Lee, B. (2017). Creating and Configuring VMs in Windows Server 2016 Hyper-V. [online]
Official NAKIVO Blog. Available at: https://www.nakivo.com/blog/creating-configuring-vms-
in-windows-server-2016-hyper-v/ [Accessed 29 Jun. 2018].
Markle, B. (2017). What is Shell (SSH) Access? | InMotion Hosting. [online]
Inmotionhosting.com. Available at: https://www.inmotionhosting.com/support/website/ssh/what-
is-shell-access [Accessed 29 Jun. 2018].
Richard, A. (2016). Windows Server 2016 Using VirtualBox - Getting Ready for Docker. [online]
Miles to go 4.0 ... Available at: http://blog.arungupta.me/windows-server-2016-virtualbox-
getting-ready-docker/ [Accessed 29 Jun. 2018].
Reference List
Cisco, C. (2016). HTTP Services Configuration Guide - HTTP/HTTPS 1.1 Web Server and
Client [Cisco ASR 1000 Series Aggregation Services Routers]. [online] Cisco. Available at:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/https/configuration/xe-16/https-xe-16-book/
HTTP_1-1_Web_Server_and_Client.html [Accessed 29 Jun. 2018].
Cisco, C. (2018). HTTP Services Configuration Guide - HTTPS--HTTP Server and Client with
SSL 3.0 [Cisco ASR 1000 Series Aggregation Services Routers]. [online] Cisco. Available at:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/https/configuration/xe-16/https-xe-16-book/
HTTPS--HTTP_Server_and_Client_with_SSL_3-0.html [Accessed 29 Jun. 2018].
Gerend, J. (2017). Installing and enabling Data Deduplication. [online] Docs.microsoft.com.
Available at: https://docs.microsoft.com/en-us/windows-server/storage/data-deduplication/
install-enable [Accessed 29 Jun. 2018].
Lee, B. (2017). Creating and Configuring VMs in Windows Server 2016 Hyper-V. [online]
Official NAKIVO Blog. Available at: https://www.nakivo.com/blog/creating-configuring-vms-
in-windows-server-2016-hyper-v/ [Accessed 29 Jun. 2018].
Markle, B. (2017). What is Shell (SSH) Access? | InMotion Hosting. [online]
Inmotionhosting.com. Available at: https://www.inmotionhosting.com/support/website/ssh/what-
is-shell-access [Accessed 29 Jun. 2018].
Richard, A. (2016). Windows Server 2016 Using VirtualBox - Getting Ready for Docker. [online]
Miles to go 4.0 ... Available at: http://blog.arungupta.me/windows-server-2016-virtualbox-
getting-ready-docker/ [Accessed 29 Jun. 2018].

IT Concepts 30
Warner, T. (2016). How to Create a File Share in Windows Server 2016. [online] Tom's IT Pro.
Available at: http://www.tomsitpro.com/articles/create-file-share-windows-server-2016,1-
3364.html [Accessed 29 Jun. 2018].
Zhelezko, A. (2017). Data deduplication using both Windows Server 2016 and Veeam. [online]
Veeam Software Official Blog. Available at: https://www.veeam.com/blog/data-deduplication-
windows-server-veeam.html [Accessed 29 Jun. 2018].
Warner, T. (2016). How to Create a File Share in Windows Server 2016. [online] Tom's IT Pro.
Available at: http://www.tomsitpro.com/articles/create-file-share-windows-server-2016,1-
3364.html [Accessed 29 Jun. 2018].
Zhelezko, A. (2017). Data deduplication using both Windows Server 2016 and Veeam. [online]
Veeam Software Official Blog. Available at: https://www.veeam.com/blog/data-deduplication-
windows-server-veeam.html [Accessed 29 Jun. 2018].
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




