Enhancing Network Efficiency with Virtualization Technologies
VerifiedAdded on 2023/06/13
|6
|1297
|174
Report
AI Summary
This report discusses virtualization technologies and their impact on network efficiency and server management. It highlights key attributes for increasing virtual machine efficiency, such as VMware certification and optimized network architecture. The report explains how virtual machines enhance network management by offering portability, backup capabilities, and disaster recovery solutions. It also differentiates between virtual appliances and vApps, advising against upgrading RENet to a virtual appliance due to compatibility issues with its Windows Server 2008 environment. Instead, it suggests a fresh installation within a virtual machine to improve redundancy and resource availability. A virtual network architecture diagram is included to illustrate the concepts.

Running head: VIRTUALIZATION TECHNOLOGIES
Virtualization Technologies
Name of the Student
Name of the University
Author’s Note
Virtualization Technologies
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
VIRTUALIZATION TECHNOLOGIES
Answer to Question 2:
a. The key attributes that should be followed for increasing the efficiency of the virtual machine
are listed below:
VMware certification – The virtualization is adopted at a rapid rate and for backing up
the software and the protecting the virtual machine the VMware certificate should be verified.
The implementation of VMware vSphere can be used for protecting the data with the application
of vStorage APIs (Huh & Seo, 2016). There are different data protection challenges for the
virtual environment and the APIs should be preferred that are supported and certified.
Network Architecture – The current framework of the organization should be analyzed
for the installation of the virtual machine and handling the current request of the users. The use
of the virtual machine reduces the loads on the physical server and reduces the waiting time of
the user. Load balancing is important and virtualization increases the efficiency of the resource
utilization.
Scalability and Efficiency – Backup software should be used for creation of a
lightweight architecture and elimination of the needs for competition with the physical server
and reducing the overhead cost of the network (Klement, 2017). The vSphere can be used for
backing up the memory, jobs and the streams offer a catalog such that the virtual machine can be
searched for meeting the eDiscovery request.
b. In the virtual machine several operating system and applications can run utilizing the common
physical hardware. The virtual machines are independent of the hardware configurations and it
can be moved from one physical server to another without any complexity. The virtual machine
installed on a physical server can be copied using flash drives or external hard drives and
VIRTUALIZATION TECHNOLOGIES
Answer to Question 2:
a. The key attributes that should be followed for increasing the efficiency of the virtual machine
are listed below:
VMware certification – The virtualization is adopted at a rapid rate and for backing up
the software and the protecting the virtual machine the VMware certificate should be verified.
The implementation of VMware vSphere can be used for protecting the data with the application
of vStorage APIs (Huh & Seo, 2016). There are different data protection challenges for the
virtual environment and the APIs should be preferred that are supported and certified.
Network Architecture – The current framework of the organization should be analyzed
for the installation of the virtual machine and handling the current request of the users. The use
of the virtual machine reduces the loads on the physical server and reduces the waiting time of
the user. Load balancing is important and virtualization increases the efficiency of the resource
utilization.
Scalability and Efficiency – Backup software should be used for creation of a
lightweight architecture and elimination of the needs for competition with the physical server
and reducing the overhead cost of the network (Klement, 2017). The vSphere can be used for
backing up the memory, jobs and the streams offer a catalog such that the virtual machine can be
searched for meeting the eDiscovery request.
b. In the virtual machine several operating system and applications can run utilizing the common
physical hardware. The virtual machines are independent of the hardware configurations and it
can be moved from one physical server to another without any complexity. The virtual machine
installed on a physical server can be copied using flash drives or external hard drives and

2
VIRTUALIZATION TECHNOLOGIES
replicated in another machine for increasing the availability of the resources (Kumar & Charu,
2015). Thus using the virtual machine as a server can help in increasing the efficiency of the
management of the network. Since the VM are portable it is easy to backup and it can be restored
to another server for handling the emergency conditions.
The use of virtual machine as a server is important because it helps in balancing the
virtual infrastructure and it can be used for increasing the redundancy of the data for serving
more number of users at a time. It can be helpful for disaster recovery and the software can be
cloned for migrating it to the cloud servers for protecting the resources of the organization
(Wolke et al., 2015). It can reduce the downtime faced by the users during the server
maintenance process and distribute the resources evenly in the network.
Answer to Question 3:
a. Difference between the virtual appliance and vApp
The vApp is used as a term for the application that is encapsulated in a vApp pool that
can work both on the hypervisors and vSphere. The performance or resource pool, requirement
of the firewall, IP address policy can be defined using the vApp. The DRS should be enabled in
the vSphere for running the vApp and it can be a group of virtual machine that are working
together for performing a specific function (Malhotra, Agarwal & Jaiswal, 2014). For example
the webserver, DNS server and the management servers can be combined to run a website.
The virtual appliance is used for describing a special type of virtual machine that can be
utilized as an application. The virtual appliance works as a virtual machine and it should be used
for lifecycle management, user interface, configuration management, do particular type of work,
have interoperability with the other application, etc. For lifecycle management the users are able
VIRTUALIZATION TECHNOLOGIES
replicated in another machine for increasing the availability of the resources (Kumar & Charu,
2015). Thus using the virtual machine as a server can help in increasing the efficiency of the
management of the network. Since the VM are portable it is easy to backup and it can be restored
to another server for handling the emergency conditions.
The use of virtual machine as a server is important because it helps in balancing the
virtual infrastructure and it can be used for increasing the redundancy of the data for serving
more number of users at a time. It can be helpful for disaster recovery and the software can be
cloned for migrating it to the cloud servers for protecting the resources of the organization
(Wolke et al., 2015). It can reduce the downtime faced by the users during the server
maintenance process and distribute the resources evenly in the network.
Answer to Question 3:
a. Difference between the virtual appliance and vApp
The vApp is used as a term for the application that is encapsulated in a vApp pool that
can work both on the hypervisors and vSphere. The performance or resource pool, requirement
of the firewall, IP address policy can be defined using the vApp. The DRS should be enabled in
the vSphere for running the vApp and it can be a group of virtual machine that are working
together for performing a specific function (Malhotra, Agarwal & Jaiswal, 2014). For example
the webserver, DNS server and the management servers can be combined to run a website.
The virtual appliance is used for describing a special type of virtual machine that can be
utilized as an application. The virtual appliance works as a virtual machine and it should be used
for lifecycle management, user interface, configuration management, do particular type of work,
have interoperability with the other application, etc. For lifecycle management the users are able
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
VIRTUALIZATION TECHNOLOGIES
to install or delete application within the limitation of the virtual machine (Yang, 2015). For
acting as an user interface cmd, graphical user interface, web interface can be used in the user
end browser. The application of the virtual machine should be customizable for supporting the
needs of the users and do a particular type of job.
b. The upgrade of the RENet to a virtual Appliance creates limits on the user interaction because
it is used for saving space and thus windows system are not used as an appliance. The upgrade
and patch management of the server is done inside the operating system and thus cannot be used
as a normal application. The appliance is best suitable for the different types of server
applications such as Tomcat Server, MySQL server, etc (Xia et al., 2017). Since the RENet
Client Property and CRM application currently runs on Windows Server 2008 environment it is
not recommended to upgrade it using the virtual appliance.
VIRTUALIZATION TECHNOLOGIES
to install or delete application within the limitation of the virtual machine (Yang, 2015). For
acting as an user interface cmd, graphical user interface, web interface can be used in the user
end browser. The application of the virtual machine should be customizable for supporting the
needs of the users and do a particular type of job.
b. The upgrade of the RENet to a virtual Appliance creates limits on the user interaction because
it is used for saving space and thus windows system are not used as an appliance. The upgrade
and patch management of the server is done inside the operating system and thus cannot be used
as a normal application. The appliance is best suitable for the different types of server
applications such as Tomcat Server, MySQL server, etc (Xia et al., 2017). Since the RENet
Client Property and CRM application currently runs on Windows Server 2008 environment it is
not recommended to upgrade it using the virtual appliance.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
VIRTUALIZATION TECHNOLOGIES
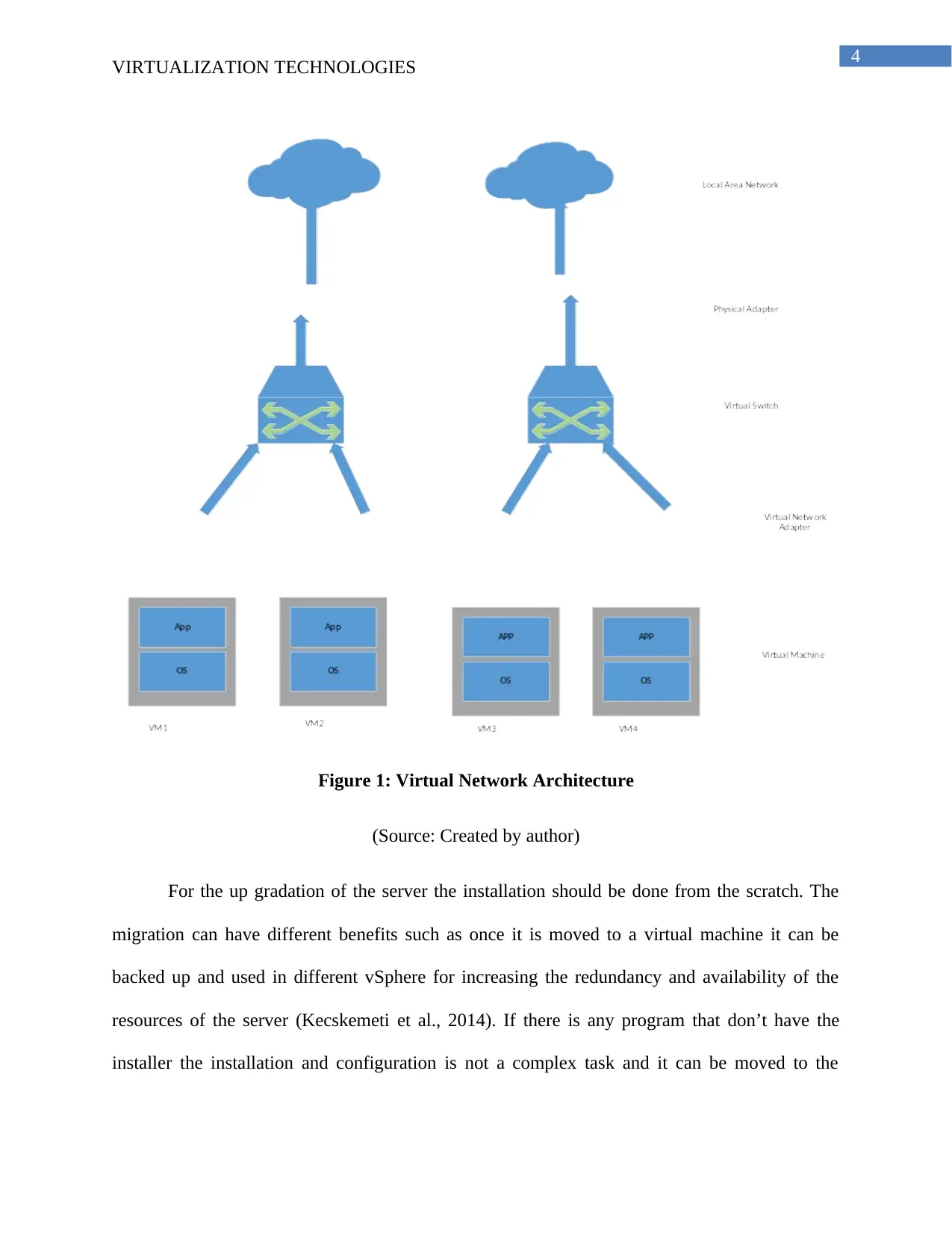
Figure 1: Virtual Network Architecture
(Source: Created by author)
For the up gradation of the server the installation should be done from the scratch. The
migration can have different benefits such as once it is moved to a virtual machine it can be
backed up and used in different vSphere for increasing the redundancy and availability of the
resources of the server (Kecskemeti et al., 2014). If there is any program that don’t have the
installer the installation and configuration is not a complex task and it can be moved to the
VIRTUALIZATION TECHNOLOGIES
Figure 1: Virtual Network Architecture
(Source: Created by author)
For the up gradation of the server the installation should be done from the scratch. The
migration can have different benefits such as once it is moved to a virtual machine it can be
backed up and used in different vSphere for increasing the redundancy and availability of the
resources of the server (Kecskemeti et al., 2014). If there is any program that don’t have the
installer the installation and configuration is not a complex task and it can be moved to the

5
VIRTUALIZATION TECHNOLOGIES
virtual machine for increasing the efficiency of the current architecture of the network of ACL
reality.
References
Huh, J. H., & Seo, K. (2016). Design and test bed experiments of server operation system using
virtualization technology. Human-centric Computing and Information Sciences, 6(1), 1.
Kecskemeti, G., Terstyanszky, G., Kacsuk, P., & Nemeth, Z. (2014). Towards efficient virtual
appliance delivery with minimal manageable virtual appliances. IEEE Transactions on
Services Computing, 7(2), 279-292.
Klement, M. (2017). Models of integration of virtualization in education: Virtualization
technology and possibilities of its use in education. Computers & Education, 105, 31-43.
Kumar, R., & Charu, S. (2015). An importance of using virtualization technology in cloud
computing. Global Journal of Computers & Technology, 1(2).
Malhotra, L., Agarwal, D., & Jaiswal, A. (2014). Virtualization in cloud computing. J. Inform.
Tech. Softw. Eng, 4(2).
Wolke, A., Tsend-Ayush, B., Pfeiffer, C., & Bichler, M. (2015). More than bin packing:
Dynamic resource allocation strategies in cloud data centers. Information Systems, 52,
83-95.
Xia, Y., Liu, Y., Guan, H., Chen, Y., Chen, T., Zang, B., & Chen, H. (2017). Secure outsourcing
of virtual appliance. IEEE Transactions on Cloud Computing, 5(3), 390-404.
Yang, H. S. (2015). A study on attack information collection using virtualization
technology. Multimedia Tools and Applications, 74(20), 8791-8799.
VIRTUALIZATION TECHNOLOGIES
virtual machine for increasing the efficiency of the current architecture of the network of ACL
reality.
References
Huh, J. H., & Seo, K. (2016). Design and test bed experiments of server operation system using
virtualization technology. Human-centric Computing and Information Sciences, 6(1), 1.
Kecskemeti, G., Terstyanszky, G., Kacsuk, P., & Nemeth, Z. (2014). Towards efficient virtual
appliance delivery with minimal manageable virtual appliances. IEEE Transactions on
Services Computing, 7(2), 279-292.
Klement, M. (2017). Models of integration of virtualization in education: Virtualization
technology and possibilities of its use in education. Computers & Education, 105, 31-43.
Kumar, R., & Charu, S. (2015). An importance of using virtualization technology in cloud
computing. Global Journal of Computers & Technology, 1(2).
Malhotra, L., Agarwal, D., & Jaiswal, A. (2014). Virtualization in cloud computing. J. Inform.
Tech. Softw. Eng, 4(2).
Wolke, A., Tsend-Ayush, B., Pfeiffer, C., & Bichler, M. (2015). More than bin packing:
Dynamic resource allocation strategies in cloud data centers. Information Systems, 52,
83-95.
Xia, Y., Liu, Y., Guan, H., Chen, Y., Chen, T., Zang, B., & Chen, H. (2017). Secure outsourcing
of virtual appliance. IEEE Transactions on Cloud Computing, 5(3), 390-404.
Yang, H. S. (2015). A study on attack information collection using virtualization
technology. Multimedia Tools and Applications, 74(20), 8791-8799.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





