Design and Implementation of Voice Security System in Simulink
VerifiedAdded on 2023/05/28
|9
|1769
|254
Project
AI Summary
This project report details the design and implementation of a voice security system using Simulink. The student, acting as Chief Electronics Engineer, utilized AES-128 encryption and scrambling techniques to secure voice signals. The project involved designing the system, implementing the encryption and decryption features, and comparing the performance of AES encryption and scrambling. The student used Simulink for software integration and conducted surveys to evaluate the Mean Opinion Score (MOS) for voice quality. The report highlights the advantages and disadvantages of both methods, concluding that AES encryption provides higher security while scrambling offers better audio quality. The student also addressed issues encountered during the project, such as inconsistencies in the MOS survey results, and provided solutions. The project aimed to create an efficient and cost-effective voice security system, with the student's contributions including proposing the design and resolving project challenges. The report also includes an overview of the project, the student's contributions, and collaborative efforts within the team.

CE 2.1 Project Information
Name of the project: Design and Implementation of Voice Security System using
Simulink
Location of the project: Please fill
Project Duration: Please fill
Organization: Please fill
Role and Designation during the time: Chief Electronics Engineer
CE 2.2 Project Background
CE 2.2.1 Characteristics of the project
The voice security system helps in the easier detection of intrusion unauthorized entry
with the help of voice recognition system. It is considered as one of the easiest and efficient
system to cease any kind of problem related to security. In this project, I have designed as
well as implemented a voice security system with the help of Simulink. I have used two main
techniques of scrambling and AES-128 encryption algorithm. Comparison of these two
techniques is also done in respect to the degree of quality and confidentiality of output voice.
After this comparison, I found out that the scrambling algorithm has produced better quality
audio signal in comparison to AES encryption. However, in respect to security, AES
encryption gave better solutions. For software implementation I selected Simulink since it
was cost effective and gave appropriate results.
Name of the project: Design and Implementation of Voice Security System using
Simulink
Location of the project: Please fill
Project Duration: Please fill
Organization: Please fill
Role and Designation during the time: Chief Electronics Engineer
CE 2.2 Project Background
CE 2.2.1 Characteristics of the project
The voice security system helps in the easier detection of intrusion unauthorized entry
with the help of voice recognition system. It is considered as one of the easiest and efficient
system to cease any kind of problem related to security. In this project, I have designed as
well as implemented a voice security system with the help of Simulink. I have used two main
techniques of scrambling and AES-128 encryption algorithm. Comparison of these two
techniques is also done in respect to the degree of quality and confidentiality of output voice.
After this comparison, I found out that the scrambling algorithm has produced better quality
audio signal in comparison to AES encryption. However, in respect to security, AES
encryption gave better solutions. For software implementation I selected Simulink since it
was cost effective and gave appropriate results.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CE 2.2.2 Objectives developed for the project
In wireless communication, the channel in which the data is being transmitted by air.
Security is often a major threat for any type of system. The intruders could easily hack the
system and extract data for wrong actions. This type of information security is possible with
the proper implementation of a voice security system with the help of AES encryption and
scrambling method. I decided to propose the design of a voice security system with the help
of Simulink. Hence, to complete the project with utmost efficiency as well as priority, some
of the important objectives were developed by me.
To design a voice security system for encrypting or decrypting with the help of AES
128 encryption and scrambling or descrambling the voice signals.
To utilize Simulink for the software designing and implementation of the system.
To compare the overall performance of the digital encryption with AES 128 as well
as scrambling method.
To provide services at extremely lower costs in comparison to the other expensive
systems.
To make the system supported by each and every device and also provide a user-
friendly environment to the users.
To match and contrast the experimental result with my desired results.
CE 2.2.3 My area of work
Being a successful telecommunications engineer, it was quite easier for me to provide
the design of the voice security system and hence I was selected as the chief electronics
engineer. I had been experimenting with voice recognition security systems for several days
and thus, when I got the chance of executing such a project, I selected Simulink as the project
integration software. Since, I have excellent knowledge of encryption and decryption, I
In wireless communication, the channel in which the data is being transmitted by air.
Security is often a major threat for any type of system. The intruders could easily hack the
system and extract data for wrong actions. This type of information security is possible with
the proper implementation of a voice security system with the help of AES encryption and
scrambling method. I decided to propose the design of a voice security system with the help
of Simulink. Hence, to complete the project with utmost efficiency as well as priority, some
of the important objectives were developed by me.
To design a voice security system for encrypting or decrypting with the help of AES
128 encryption and scrambling or descrambling the voice signals.
To utilize Simulink for the software designing and implementation of the system.
To compare the overall performance of the digital encryption with AES 128 as well
as scrambling method.
To provide services at extremely lower costs in comparison to the other expensive
systems.
To make the system supported by each and every device and also provide a user-
friendly environment to the users.
To match and contrast the experimental result with my desired results.
CE 2.2.3 My area of work
Being a successful telecommunications engineer, it was quite easier for me to provide
the design of the voice security system and hence I was selected as the chief electronics
engineer. I had been experimenting with voice recognition security systems for several days
and thus, when I got the chance of executing such a project, I selected Simulink as the project
integration software. Since, I have excellent knowledge of encryption and decryption, I

Head of the
Department
Project Supervisor
Chief Electronics
Engineer (Me)
Team Member Team Member
merged my ideologies of security system and these two techniques of security. My project
supervisor has confidence on me and gave the core responsibility of designing the project.
CE 2.2.4 Project Group
Figure 1: People involved in the project
CE 2.2.5 My responsibilities throughout the project
During the accomplishment of the project, I comprised of various responsibilities. My
most noteworthy duty was to propose a proper design for this voice security system. My other
responsibility was to implement two distinct features of encryption and decryption within my
project so that the voice of the authorized user could access the data and could also lock it.
Similarly, that specific authorized and authenticated user could also transfer or transmit the
data to the receiver by decrypting it with the help of AES-128 and scramble/descramble a
voice signal. I implemented AES 28 encryption algorithm for ensuring that there is no loop
hole for the security. The receiver could only listen to the voice message after decrypting
Department
Project Supervisor
Chief Electronics
Engineer (Me)
Team Member Team Member
merged my ideologies of security system and these two techniques of security. My project
supervisor has confidence on me and gave the core responsibility of designing the project.
CE 2.2.4 Project Group
Figure 1: People involved in the project
CE 2.2.5 My responsibilities throughout the project
During the accomplishment of the project, I comprised of various responsibilities. My
most noteworthy duty was to propose a proper design for this voice security system. My other
responsibility was to implement two distinct features of encryption and decryption within my
project so that the voice of the authorized user could access the data and could also lock it.
Similarly, that specific authorized and authenticated user could also transfer or transmit the
data to the receiver by decrypting it with the help of AES-128 and scramble/descramble a
voice signal. I implemented AES 28 encryption algorithm for ensuring that there is no loop
hole for the security. The receiver could only listen to the voice message after decrypting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
with the help of decryption code. I even used Simulink for the software integration of the
project and hence I was able to obtain proper results from the voice security system.
CE 2.3 Distinctive Activity
CE 2.3.1 Comprehending the Theory of Project
In the project, I considered the theory of voice recognition system and security
system. I even applied the theory of encryption and subsequent algorithms in the work. In the
beginning, I proposed a design for the project.
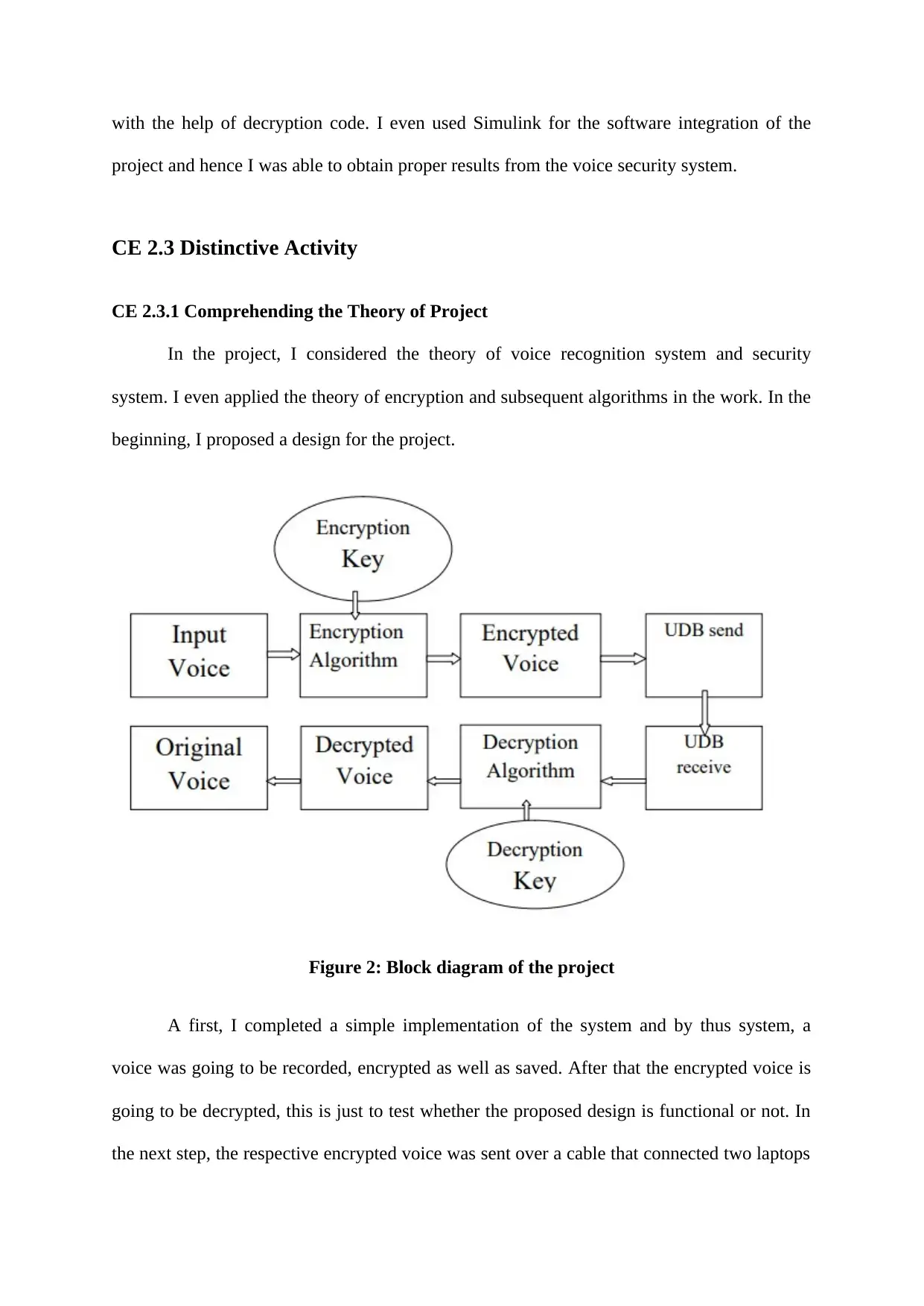
Figure 2: Block diagram of the project
A first, I completed a simple implementation of the system and by thus system, a
voice was going to be recorded, encrypted as well as saved. After that the encrypted voice is
going to be decrypted, this is just to test whether the proposed design is functional or not. In
the next step, the respective encrypted voice was sent over a cable that connected two laptops
project and hence I was able to obtain proper results from the voice security system.
CE 2.3 Distinctive Activity
CE 2.3.1 Comprehending the Theory of Project
In the project, I considered the theory of voice recognition system and security
system. I even applied the theory of encryption and subsequent algorithms in the work. In the
beginning, I proposed a design for the project.
Figure 2: Block diagram of the project
A first, I completed a simple implementation of the system and by thus system, a
voice was going to be recorded, encrypted as well as saved. After that the encrypted voice is
going to be decrypted, this is just to test whether the proposed design is functional or not. In
the next step, the respective encrypted voice was sent over a cable that connected two laptops
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

for testing the functionality. Finally, after testing, the decrypted output signal was sent to the
receiver. I selected two algorithms of AES 128 and scrambling designing. I noted that both
the algorithms have their own working process; the scrambling technique used audio cable
for sending data between the laptops and AES 128 encryption algorithm uses Ethernet cable
for this purpose. I considered the advantages and disadvantages of both the techniques to
ensure security and efficiency to the system. Regarding the software designing, I chose
Simulink software and obtained proper results.
CE 2.3.2 Engineering knowledge and skills applied in the project
To execute the project, I had applied my understanding of digital system designing for
this project. For making the voice security system efficient, I have utilized several techniques
and technologies of electronics engineering. I have checked the scrambled and descrambled
voice results and hence got significant outputs. For encrypting the project, I have applied my
knowledge of encryption and decryption with algorithms like AES 128 and scrambling. AES
accepts only unsinged integer 8data type, but voice is a composite of both negatives and
positives. To overcome this problem partially the voice signal was separated in two 8 high
bits and 8 low bits, in other words 8 MSB or most significant bits as well as 8 LSB or least
significant bits. I have also applied my knowledge of Simulink to complete the software
integration effectively.
CE 2.3.3 Accomplishment and Task Performed
I have successfully accomplished the project by comparing my results of AES voice
encryption with scrambling method. In AES encryption, before separating MSBs and LSBs
the negative part of the voice was removed by 2^15 which was 32768. After the decryption
process was completed the negatives were put back again and with that the AES
encryption/decryption process was completed.
receiver. I selected two algorithms of AES 128 and scrambling designing. I noted that both
the algorithms have their own working process; the scrambling technique used audio cable
for sending data between the laptops and AES 128 encryption algorithm uses Ethernet cable
for this purpose. I considered the advantages and disadvantages of both the techniques to
ensure security and efficiency to the system. Regarding the software designing, I chose
Simulink software and obtained proper results.
CE 2.3.2 Engineering knowledge and skills applied in the project
To execute the project, I had applied my understanding of digital system designing for
this project. For making the voice security system efficient, I have utilized several techniques
and technologies of electronics engineering. I have checked the scrambled and descrambled
voice results and hence got significant outputs. For encrypting the project, I have applied my
knowledge of encryption and decryption with algorithms like AES 128 and scrambling. AES
accepts only unsinged integer 8data type, but voice is a composite of both negatives and
positives. To overcome this problem partially the voice signal was separated in two 8 high
bits and 8 low bits, in other words 8 MSB or most significant bits as well as 8 LSB or least
significant bits. I have also applied my knowledge of Simulink to complete the software
integration effectively.
CE 2.3.3 Accomplishment and Task Performed
I have successfully accomplished the project by comparing my results of AES voice
encryption with scrambling method. In AES encryption, before separating MSBs and LSBs
the negative part of the voice was removed by 2^15 which was 32768. After the decryption
process was completed the negatives were put back again and with that the AES
encryption/decryption process was completed.
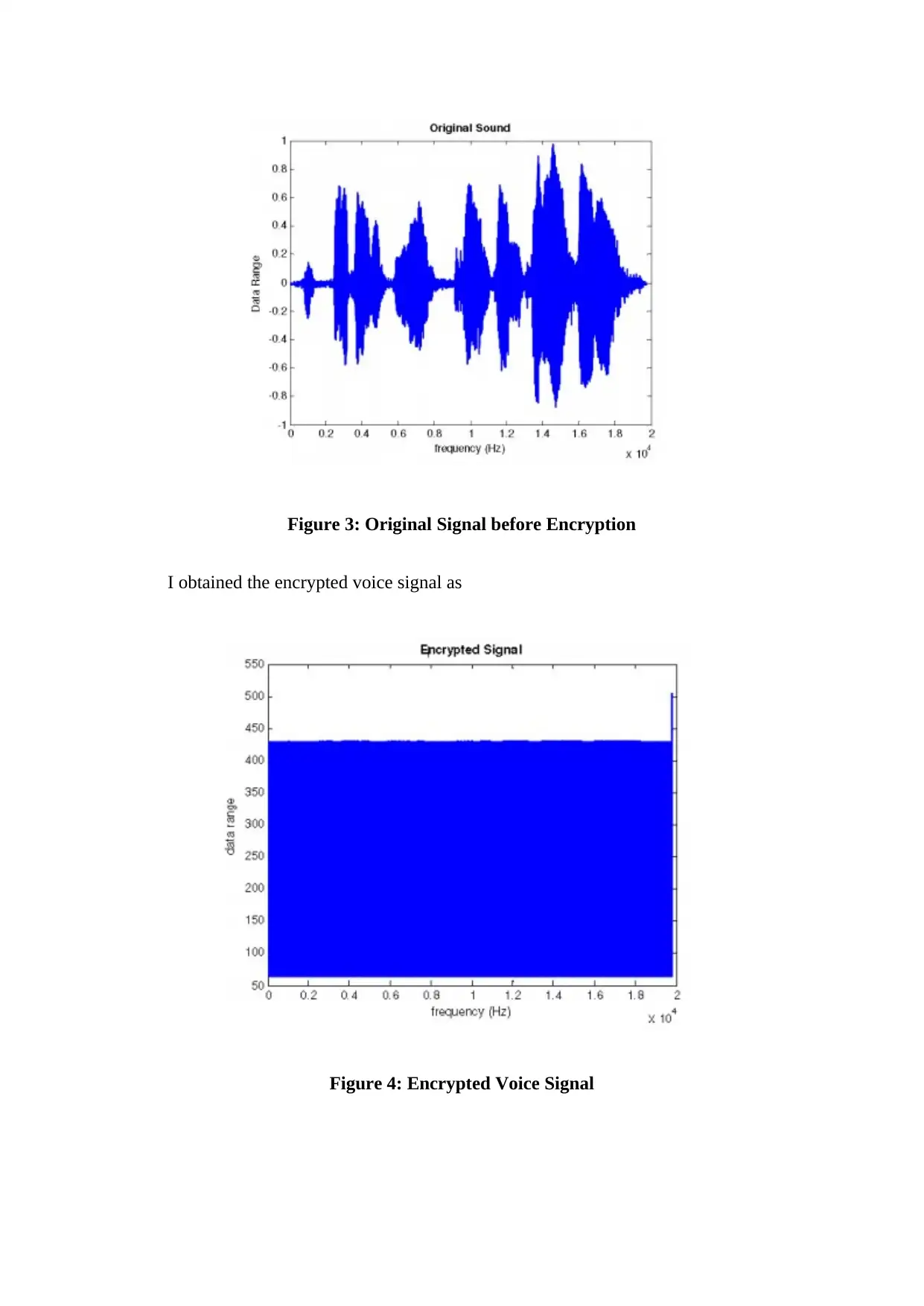
Figure 3: Original Signal before Encryption
I obtained the encrypted voice signal as
Figure 4: Encrypted Voice Signal
I obtained the encrypted voice signal as
Figure 4: Encrypted Voice Signal
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
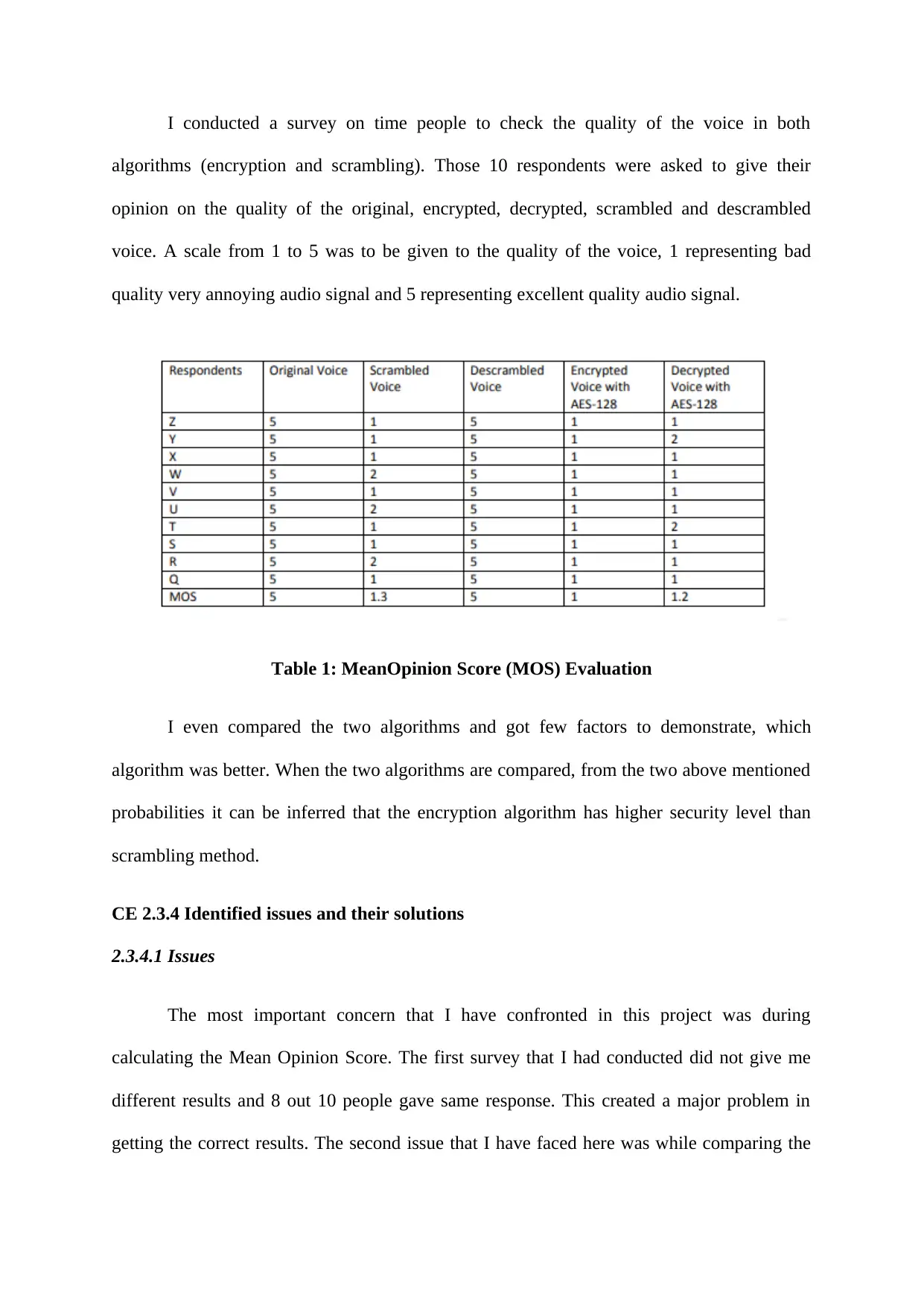
I conducted a survey on time people to check the quality of the voice in both
algorithms (encryption and scrambling). Those 10 respondents were asked to give their
opinion on the quality of the original, encrypted, decrypted, scrambled and descrambled
voice. A scale from 1 to 5 was to be given to the quality of the voice, 1 representing bad
quality very annoying audio signal and 5 representing excellent quality audio signal.
Table 1: MeanOpinion Score (MOS) Evaluation
I even compared the two algorithms and got few factors to demonstrate, which
algorithm was better. When the two algorithms are compared, from the two above mentioned
probabilities it can be inferred that the encryption algorithm has higher security level than
scrambling method.
CE 2.3.4 Identified issues and their solutions
2.3.4.1 Issues
The most important concern that I have confronted in this project was during
calculating the Mean Opinion Score. The first survey that I had conducted did not give me
different results and 8 out 10 people gave same response. This created a major problem in
getting the correct results. The second issue that I have faced here was while comparing the
algorithms (encryption and scrambling). Those 10 respondents were asked to give their
opinion on the quality of the original, encrypted, decrypted, scrambled and descrambled
voice. A scale from 1 to 5 was to be given to the quality of the voice, 1 representing bad
quality very annoying audio signal and 5 representing excellent quality audio signal.
Table 1: MeanOpinion Score (MOS) Evaluation
I even compared the two algorithms and got few factors to demonstrate, which
algorithm was better. When the two algorithms are compared, from the two above mentioned
probabilities it can be inferred that the encryption algorithm has higher security level than
scrambling method.
CE 2.3.4 Identified issues and their solutions
2.3.4.1 Issues
The most important concern that I have confronted in this project was during
calculating the Mean Opinion Score. The first survey that I had conducted did not give me
different results and 8 out 10 people gave same response. This created a major problem in
getting the correct results. The second issue that I have faced here was while comparing the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

performance of the digital encryption using AES-128 and scrambling method. Every time it
was proving that AES 128 was better than scrambling however after research I found out
there are few aspects, where, scrambling was better.
2.3.4.2 Solutions
For the first problem of Mean Opinion Score, I conducted another survey of 10 other
people. This time I was able to obtain my desired results and was able to evaluate Mean
Opinion Score properly. For the next issue, I decided to compare the AES 128 and
scrambling methods. I found out that scrambling algorithm produces a high quality voice
signal compared to AES encryption algorithm. However AES algorithm achieves higher
security level compared to scrambling technique. Finally, I was able to solve both the issues.
CE 2.3.5 Plan to produce creative and innovative work
For completing this project of the Design and Implementation of Voice Security
System using Simulink, I have to create the distinctive plan to produce outstanding design.
Being one of the electrical and electronics engineer, I had to make this design for the voice
security system.
CE 2.3.6 Collaborative Work
I had provided suggestions to my team to work altogether for becoming stress free for
each one of us for making this project effective. I also distributed different tasks equally
amongst my team members and then undertook regular work follow-ups.
was proving that AES 128 was better than scrambling however after research I found out
there are few aspects, where, scrambling was better.
2.3.4.2 Solutions
For the first problem of Mean Opinion Score, I conducted another survey of 10 other
people. This time I was able to obtain my desired results and was able to evaluate Mean
Opinion Score properly. For the next issue, I decided to compare the AES 128 and
scrambling methods. I found out that scrambling algorithm produces a high quality voice
signal compared to AES encryption algorithm. However AES algorithm achieves higher
security level compared to scrambling technique. Finally, I was able to solve both the issues.
CE 2.3.5 Plan to produce creative and innovative work
For completing this project of the Design and Implementation of Voice Security
System using Simulink, I have to create the distinctive plan to produce outstanding design.
Being one of the electrical and electronics engineer, I had to make this design for the voice
security system.
CE 2.3.6 Collaborative Work
I had provided suggestions to my team to work altogether for becoming stress free for
each one of us for making this project effective. I also distributed different tasks equally
amongst my team members and then undertook regular work follow-ups.

CE 2.4 Project Review
CE 2.4.1 Project Overview
The key purpose of this project was proposing a suitable design for voice security
system. For this particular purpose, I had to use my information of AES 128 and scrambling
method to encrypt and decrypt and Simulink software to integrate the design.
CE 2.4.2 My Contribution to work
I was assigned as the chief electronics engineer in this detailed project of Design and
Implementation of Voice Security System using Simulink. My chief contribution was
proposing the accurate design for this project and also solving the several issues faced by us.
CE 2.4.1 Project Overview
The key purpose of this project was proposing a suitable design for voice security
system. For this particular purpose, I had to use my information of AES 128 and scrambling
method to encrypt and decrypt and Simulink software to integrate the design.
CE 2.4.2 My Contribution to work
I was assigned as the chief electronics engineer in this detailed project of Design and
Implementation of Voice Security System using Simulink. My chief contribution was
proposing the accurate design for this project and also solving the several issues faced by us.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




