Virtual Private Network Replacement Technologies
Added on 2021-10-04
5 Pages3994 Words500 Views
VPN REPLACEMENT TECHNOLOGIES
ABSTRACT – The main aim of this report is to understand about the virtual private network replacement
technologies. The virtual private network or VPN is the extension of private network across the public network.
This type of private network extension is majorly responsible for enabling the users in sending as well as receiving
the confidential data, across the shared or the public networks. The computing devices of these users are directly
connected to the respective private network. The applications that are running across the virtual private network
are extremely advantageous in respect to the functionalities, security as well as management of the specified
private networks. This technology of virtual private network is developed for allowing the remote users or branch
offices and providing access to the corporate resources and applications. The legacy virtual private networks or
VPNs comprises of some of the major and the most significant issues or problems. The IPsec based protocols of
VPN have now become completely obsolete. These specific IPsec based protocols of VPN are not at all familiar
with the firewalls, proxies or NATs. This report has properly explained about the several limitations or problems
that are previously existing in the legacy VPNs and even relevant or suitable solutions for these issues. Moreover,
the VPN security issue is also addressed in the report properly.
1. INTRODUCTION
The virtual private network or simply VPN can be
stated as the technology, which is responsible for
creating the safe as well as encrypted connection over
the lesser secured network like the Internet connectivity
[12]. This technology of virtual private network is
subsequently developed as the methodology for the
purpose of allowing the respective remote users or the
branch divisions for securely accessing the corporate
resources or applications. For ensuring safety, the
sensitive data travels through the secured tunnels. The
users of virtual private networks should utilize the
authenticated and authorized methods such as
passwords, unique identifying processes and tokens for
gaining proper access to the servers of virtual private
networks [15].
1.1 VIRTUAL PRIVATE NETWORKS
1.1.1. Background
The virtual private networks are also utilized by the
remote workers, who require the access to the
corporate resources and consumers, who might require
downloading the files or the business travellers, who
wish to log into the sites, which are substantially
restricted geographically. The VPN services are
extremely critical conduits, by which the data could be
transported securely and safely. The two extremely
common virtual private network types are site to site
VPNs and remote access VPNs [3]. The remote access
virtual private network utilizes the infrastructure of
public telecommunication such as the Internet for
providing remote users with the safe and secured access
to the organizational network. The client of virtual
private network on the computer or mobile device of the
remote user is connected to the gateway of virtual
private network within the network of the organization.
1.1.2. Details of Virtual Private Network
The following report will be outlining a brief discussion
regarding the replacement technologies of virtual private
networks. The gateway of these virtual private networks
usually needs a device for the purpose of authenticating
the identity [20]. Next, this gateway could eventually
create the network links back into the devices, which
allow them in reaching to the resources of internal
network like the printers, intranets and servers, since it
is registered to the network locally. The legacy virtual
private network generally relies on the IPsec or IP
security as well as SSL or secure sockets layer for the
purpose of securing the connection. However, the
secure socket layered virtual private networks are
completely focused on the supply of secured access to
one application and not on the complete internal
networks [1].
1.1.3. Legacy Virtual Private Networks
Few of the legacy VPNs give the layer 2 access for the
targeted network and they need the tunnelling protocols
such as the point to point tunnelling protocols and layer
2 tunnelling protocols that could run across the basic
connection of IPsec. There are some of the major
problems or drawbacks of the legacy VPNs. These
problems or issues might be extremely dangerous for
the users; however some of the solutions are also
present that could easily resolve them. Hence, few of the
technologies are implemented as the alternatives [9].
The most popular and significant technologies are
SoftEther VPN and Microsoft DirectAccess. The report
will be providing the detailed review of the VPN
technologies and their issues with relevant and suitable
solutions.
ABSTRACT – The main aim of this report is to understand about the virtual private network replacement
technologies. The virtual private network or VPN is the extension of private network across the public network.
This type of private network extension is majorly responsible for enabling the users in sending as well as receiving
the confidential data, across the shared or the public networks. The computing devices of these users are directly
connected to the respective private network. The applications that are running across the virtual private network
are extremely advantageous in respect to the functionalities, security as well as management of the specified
private networks. This technology of virtual private network is developed for allowing the remote users or branch
offices and providing access to the corporate resources and applications. The legacy virtual private networks or
VPNs comprises of some of the major and the most significant issues or problems. The IPsec based protocols of
VPN have now become completely obsolete. These specific IPsec based protocols of VPN are not at all familiar
with the firewalls, proxies or NATs. This report has properly explained about the several limitations or problems
that are previously existing in the legacy VPNs and even relevant or suitable solutions for these issues. Moreover,
the VPN security issue is also addressed in the report properly.
1. INTRODUCTION
The virtual private network or simply VPN can be
stated as the technology, which is responsible for
creating the safe as well as encrypted connection over
the lesser secured network like the Internet connectivity
[12]. This technology of virtual private network is
subsequently developed as the methodology for the
purpose of allowing the respective remote users or the
branch divisions for securely accessing the corporate
resources or applications. For ensuring safety, the
sensitive data travels through the secured tunnels. The
users of virtual private networks should utilize the
authenticated and authorized methods such as
passwords, unique identifying processes and tokens for
gaining proper access to the servers of virtual private
networks [15].
1.1 VIRTUAL PRIVATE NETWORKS
1.1.1. Background
The virtual private networks are also utilized by the
remote workers, who require the access to the
corporate resources and consumers, who might require
downloading the files or the business travellers, who
wish to log into the sites, which are substantially
restricted geographically. The VPN services are
extremely critical conduits, by which the data could be
transported securely and safely. The two extremely
common virtual private network types are site to site
VPNs and remote access VPNs [3]. The remote access
virtual private network utilizes the infrastructure of
public telecommunication such as the Internet for
providing remote users with the safe and secured access
to the organizational network. The client of virtual
private network on the computer or mobile device of the
remote user is connected to the gateway of virtual
private network within the network of the organization.
1.1.2. Details of Virtual Private Network
The following report will be outlining a brief discussion
regarding the replacement technologies of virtual private
networks. The gateway of these virtual private networks
usually needs a device for the purpose of authenticating
the identity [20]. Next, this gateway could eventually
create the network links back into the devices, which
allow them in reaching to the resources of internal
network like the printers, intranets and servers, since it
is registered to the network locally. The legacy virtual
private network generally relies on the IPsec or IP
security as well as SSL or secure sockets layer for the
purpose of securing the connection. However, the
secure socket layered virtual private networks are
completely focused on the supply of secured access to
one application and not on the complete internal
networks [1].
1.1.3. Legacy Virtual Private Networks
Few of the legacy VPNs give the layer 2 access for the
targeted network and they need the tunnelling protocols
such as the point to point tunnelling protocols and layer
2 tunnelling protocols that could run across the basic
connection of IPsec. There are some of the major
problems or drawbacks of the legacy VPNs. These
problems or issues might be extremely dangerous for
the users; however some of the solutions are also
present that could easily resolve them. Hence, few of the
technologies are implemented as the alternatives [9].
The most popular and significant technologies are
SoftEther VPN and Microsoft DirectAccess. The report
will be providing the detailed review of the VPN
technologies and their issues with relevant and suitable
solutions.

2. BACKGROUND/LITERATURE REVIEW
2.1. Drawbacks of Legacy VPNs
2.1.1 Lack of Reliability of VPN
According to Regola and Nitesh [5], the legacy virtual
private networks often undergo some of the most
important and significant issues that could be quite
distracting for the users of this technology. The major
limitation of the legacy VPN is that most of the reliable
virtual private networks are not of free charges. A
monthly subscription is to be paid for the safety reasons.
The data could be sold out from the online activities to
the respective ad providers [19].
2.1.2 Lesser Speed
Another specific limitation of the legacy VPN would be
that connection speed often becomes less than the usual
range. Although, there is scope for better data
transmission, the intake of resources is extremely slower
and thus this technology is often avoided by the users
[1]. However, with the help of paid connection, this
particular issue of legacy VPN is solved eventually.
2.1.3 Security
Security is the next noteworthy drawback of the
legacy virtual private networks. As per Kahate [16], the
blacklisting of the IP address and the IP spoofing are the
major examples of this security issue of VPN. Thus, it is
extremely important for subscribing to only to the
trustworthy as well as reputable virtual private
networks. The complexity of the legacy VPNs is yet
another significant drawback of this technology. The
intricate combination of hardware equipment, network
topologies and protocols help the service providers to
make up the distinct channel of virtual private network
[13]. The extra stress is given to these channels of VPN
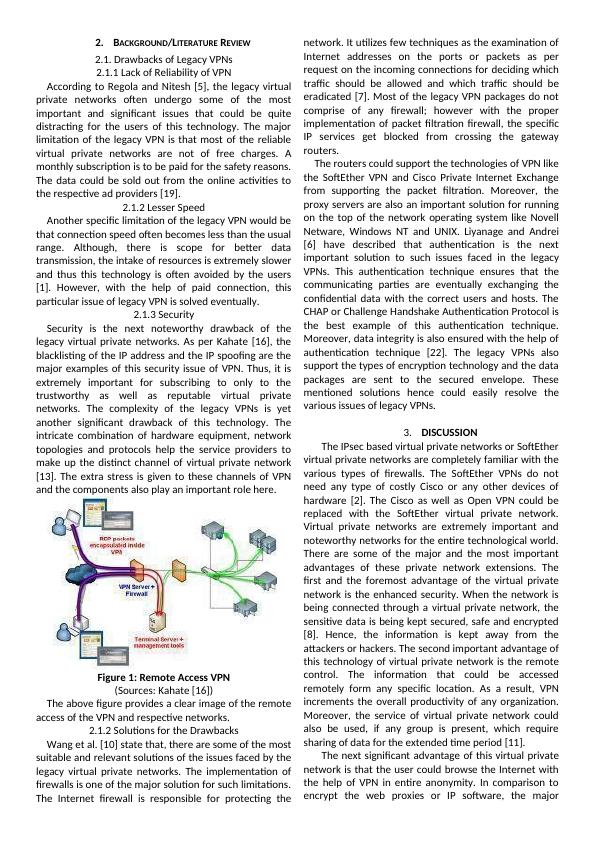
and the components also play an important role here.
Figure 1: Remote Access VPN
(Sources: Kahate [16])
The above figure provides a clear image of the remote
access of the VPN and respective networks.
2.1.2 Solutions for the Drawbacks
Wang et al. [10] state that, there are some of the most
suitable and relevant solutions of the issues faced by the
legacy virtual private networks. The implementation of
firewalls is one of the major solution for such limitations.
The Internet firewall is responsible for protecting the
network. It utilizes few techniques as the examination of
Internet addresses on the ports or packets as per
request on the incoming connections for deciding which
traffic should be allowed and which traffic should be
eradicated [7]. Most of the legacy VPN packages do not
comprise of any firewall; however with the proper
implementation of packet filtration firewall, the specific
IP services get blocked from crossing the gateway
routers.
The routers could support the technologies of VPN like
the SoftEther VPN and Cisco Private Internet Exchange
from supporting the packet filtration. Moreover, the
proxy servers are also an important solution for running
on the top of the network operating system like Novell
Netware, Windows NT and UNIX. Liyanage and Andrei
[6] have described that authentication is the next
important solution to such issues faced in the legacy
VPNs. This authentication technique ensures that the
communicating parties are eventually exchanging the
confidential data with the correct users and hosts. The
CHAP or Challenge Handshake Authentication Protocol is
the best example of this authentication technique.
Moreover, data integrity is also ensured with the help of
authentication technique [22]. The legacy VPNs also
support the types of encryption technology and the data
packages are sent to the secured envelope. These
mentioned solutions hence could easily resolve the
various issues of legacy VPNs.
3. DISCUSSION
The IPsec based virtual private networks or SoftEther
virtual private networks are completely familiar with the
various types of firewalls. The SoftEther VPNs do not
need any type of costly Cisco or any other devices of
hardware [2]. The Cisco as well as Open VPN could be
replaced with the SoftEther virtual private network.
Virtual private networks are extremely important and
noteworthy networks for the entire technological world.
There are some of the major and the most important
advantages of these private network extensions. The
first and the foremost advantage of the virtual private
network is the enhanced security. When the network is
being connected through a virtual private network, the
sensitive data is being kept secured, safe and encrypted
[8]. Hence, the information is kept away from the
attackers or hackers. The second important advantage of
this technology of virtual private network is the remote
control. The information that could be accessed
remotely form any specific location. As a result, VPN
increments the overall productivity of any organization.
Moreover, the service of virtual private network could
also be used, if any group is present, which require
sharing of data for the extended time period [11].
The next significant advantage of this virtual private
network is that the user could browse the Internet with
the help of VPN in entire anonymity. In comparison to
encrypt the web proxies or IP software, the major
2.1. Drawbacks of Legacy VPNs
2.1.1 Lack of Reliability of VPN
According to Regola and Nitesh [5], the legacy virtual
private networks often undergo some of the most
important and significant issues that could be quite
distracting for the users of this technology. The major
limitation of the legacy VPN is that most of the reliable
virtual private networks are not of free charges. A
monthly subscription is to be paid for the safety reasons.
The data could be sold out from the online activities to
the respective ad providers [19].
2.1.2 Lesser Speed
Another specific limitation of the legacy VPN would be
that connection speed often becomes less than the usual
range. Although, there is scope for better data
transmission, the intake of resources is extremely slower
and thus this technology is often avoided by the users
[1]. However, with the help of paid connection, this
particular issue of legacy VPN is solved eventually.
2.1.3 Security
Security is the next noteworthy drawback of the
legacy virtual private networks. As per Kahate [16], the
blacklisting of the IP address and the IP spoofing are the
major examples of this security issue of VPN. Thus, it is
extremely important for subscribing to only to the
trustworthy as well as reputable virtual private
networks. The complexity of the legacy VPNs is yet
another significant drawback of this technology. The
intricate combination of hardware equipment, network
topologies and protocols help the service providers to
make up the distinct channel of virtual private network
[13]. The extra stress is given to these channels of VPN
and the components also play an important role here.
Figure 1: Remote Access VPN
(Sources: Kahate [16])
The above figure provides a clear image of the remote
access of the VPN and respective networks.
2.1.2 Solutions for the Drawbacks
Wang et al. [10] state that, there are some of the most
suitable and relevant solutions of the issues faced by the
legacy virtual private networks. The implementation of
firewalls is one of the major solution for such limitations.
The Internet firewall is responsible for protecting the
network. It utilizes few techniques as the examination of
Internet addresses on the ports or packets as per
request on the incoming connections for deciding which
traffic should be allowed and which traffic should be
eradicated [7]. Most of the legacy VPN packages do not
comprise of any firewall; however with the proper
implementation of packet filtration firewall, the specific
IP services get blocked from crossing the gateway
routers.
The routers could support the technologies of VPN like
the SoftEther VPN and Cisco Private Internet Exchange
from supporting the packet filtration. Moreover, the
proxy servers are also an important solution for running
on the top of the network operating system like Novell
Netware, Windows NT and UNIX. Liyanage and Andrei
[6] have described that authentication is the next
important solution to such issues faced in the legacy
VPNs. This authentication technique ensures that the
communicating parties are eventually exchanging the
confidential data with the correct users and hosts. The
CHAP or Challenge Handshake Authentication Protocol is
the best example of this authentication technique.
Moreover, data integrity is also ensured with the help of
authentication technique [22]. The legacy VPNs also
support the types of encryption technology and the data
packages are sent to the secured envelope. These
mentioned solutions hence could easily resolve the
various issues of legacy VPNs.
3. DISCUSSION
The IPsec based virtual private networks or SoftEther
virtual private networks are completely familiar with the
various types of firewalls. The SoftEther VPNs do not
need any type of costly Cisco or any other devices of
hardware [2]. The Cisco as well as Open VPN could be
replaced with the SoftEther virtual private network.
Virtual private networks are extremely important and
noteworthy networks for the entire technological world.
There are some of the major and the most important
advantages of these private network extensions. The
first and the foremost advantage of the virtual private
network is the enhanced security. When the network is
being connected through a virtual private network, the
sensitive data is being kept secured, safe and encrypted
[8]. Hence, the information is kept away from the
attackers or hackers. The second important advantage of
this technology of virtual private network is the remote
control. The information that could be accessed
remotely form any specific location. As a result, VPN
increments the overall productivity of any organization.
Moreover, the service of virtual private network could
also be used, if any group is present, which require
sharing of data for the extended time period [11].
The next significant advantage of this virtual private
network is that the user could browse the Internet with
the help of VPN in entire anonymity. In comparison to
encrypt the web proxies or IP software, the major
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
RVPN advantages and its types.lg...
|5
|866
|22
Designing a Secure Virtual Private Network for Campus Environmentlg...
|25
|6319
|163
Project: Design Virtual Private Network Within Campus Environmentlg...
|25
|6320
|602
Report on Virtual Private Network 2022lg...
|12
|2383
|26
VPN Replacement Technologieslg...
|8
|472
|400
BN305 Virtual Private Networks Assignmentlg...
|13
|3826
|65
