PICT808 Case Study: WannaCry Ransomware Attack, Impact, & Prevention
VerifiedAdded on 2023/04/21
|11
|2953
|469
Case Study
AI Summary
This case study report delves into the WannaCry ransomware attack, a significant cyber warfare event that affected numerous organizations worldwide in May 2017. The report outlines the problems caused by the ransomware, identifies affected computers and organizations, explores the motives behind the attack, and examines the victims. It discusses the risk identification of the attack and proposes possible solutions to prevent similar incidents in the future, emphasizing the importance of security risk assessments and requirement analysis. The report highlights the ransomware's encryption of data and demand for ransom payments in Bitcoin, causing an estimated $4 billion in losses across 150 countries. It also explores non-cyber aspects, such as the impact on customer trust in operating systems and cloud systems, and provides recommendations for organizations to protect themselves from ransomware attacks, including system updates, ransomware blockers, and security risk assessment procedures.

Running head: WANNACRY, A CYBER-WARFARE IN MODERN TIMES
Wannacry, a cyber-warfare in modern times
Name of the student:
Name of the university:
Author Note:
Wannacry, a cyber-warfare in modern times
Name of the student:
Name of the university:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WANNACRY, A CYBER-WARFARE IN MODERN TIMES
In recent years, ransomware has evolved as one of the most important cyber frauds,
which affected the business organisations. This report will deal with the most important
attack in the history of cyber-warfare that is the WannaCry Ransomware attack (Mohurle and
Patil 2017). This report will explain the problems faced due to the ransomware attack, the
affected computers/organisation, the motives for the attack, the victims of this attack, risk
identification of the attack as well as the possible solutions to the prevent this type of attack
in the near future. This report will also seek for some security risk assessments as well as
some requirement analysis, which will incorporate and provide better solutions to protect any
computer/organisation from the attacks of ransomware.
Ransomware is a malware or a malicious software that are designed for blocking the
access of a computer system until an adequate amount of money is paid. This malware firstly
infects the computer systems by taking the total control of its access as well as of the whole
core operating system with the help of locking mechanisms and take the possession of the
user’s data by encryption. Then the user is asked to make a payment as ransom to the person
or to the organisation who is responsible for the attack, on the condition that after the
successful payment of the ransom the user’s computer will be unlocked of the malicious
program. However, in some cases after paying the ransom also the user was not provided to
access its data.
The unexpected Ransomware attack in the history of IT systems took place in May
2017 worldwide. This was WannaCry Ransomware attack, which mainly targeted the PC
Systems with operating systems of Microsoft Windows. This attack happened all over the
world and the data of the affected PC has been encrypted. Moreover, a demand of ransom
payments were asked for decryption of the data in the form of Bitcoin Crypto currency. This
attack targeted many computers worldwide and the losses may had reached approximately $4
billion. This attack took place in around 150 countries making this incident the most
In recent years, ransomware has evolved as one of the most important cyber frauds,
which affected the business organisations. This report will deal with the most important
attack in the history of cyber-warfare that is the WannaCry Ransomware attack (Mohurle and
Patil 2017). This report will explain the problems faced due to the ransomware attack, the
affected computers/organisation, the motives for the attack, the victims of this attack, risk
identification of the attack as well as the possible solutions to the prevent this type of attack
in the near future. This report will also seek for some security risk assessments as well as
some requirement analysis, which will incorporate and provide better solutions to protect any
computer/organisation from the attacks of ransomware.
Ransomware is a malware or a malicious software that are designed for blocking the
access of a computer system until an adequate amount of money is paid. This malware firstly
infects the computer systems by taking the total control of its access as well as of the whole
core operating system with the help of locking mechanisms and take the possession of the
user’s data by encryption. Then the user is asked to make a payment as ransom to the person
or to the organisation who is responsible for the attack, on the condition that after the
successful payment of the ransom the user’s computer will be unlocked of the malicious
program. However, in some cases after paying the ransom also the user was not provided to
access its data.
The unexpected Ransomware attack in the history of IT systems took place in May
2017 worldwide. This was WannaCry Ransomware attack, which mainly targeted the PC
Systems with operating systems of Microsoft Windows. This attack happened all over the
world and the data of the affected PC has been encrypted. Moreover, a demand of ransom
payments were asked for decryption of the data in the form of Bitcoin Crypto currency. This
attack targeted many computers worldwide and the losses may had reached approximately $4
billion. This attack took place in around 150 countries making this incident the most
2WANNACRY, A CYBER-WARFARE IN MODERN TIMES
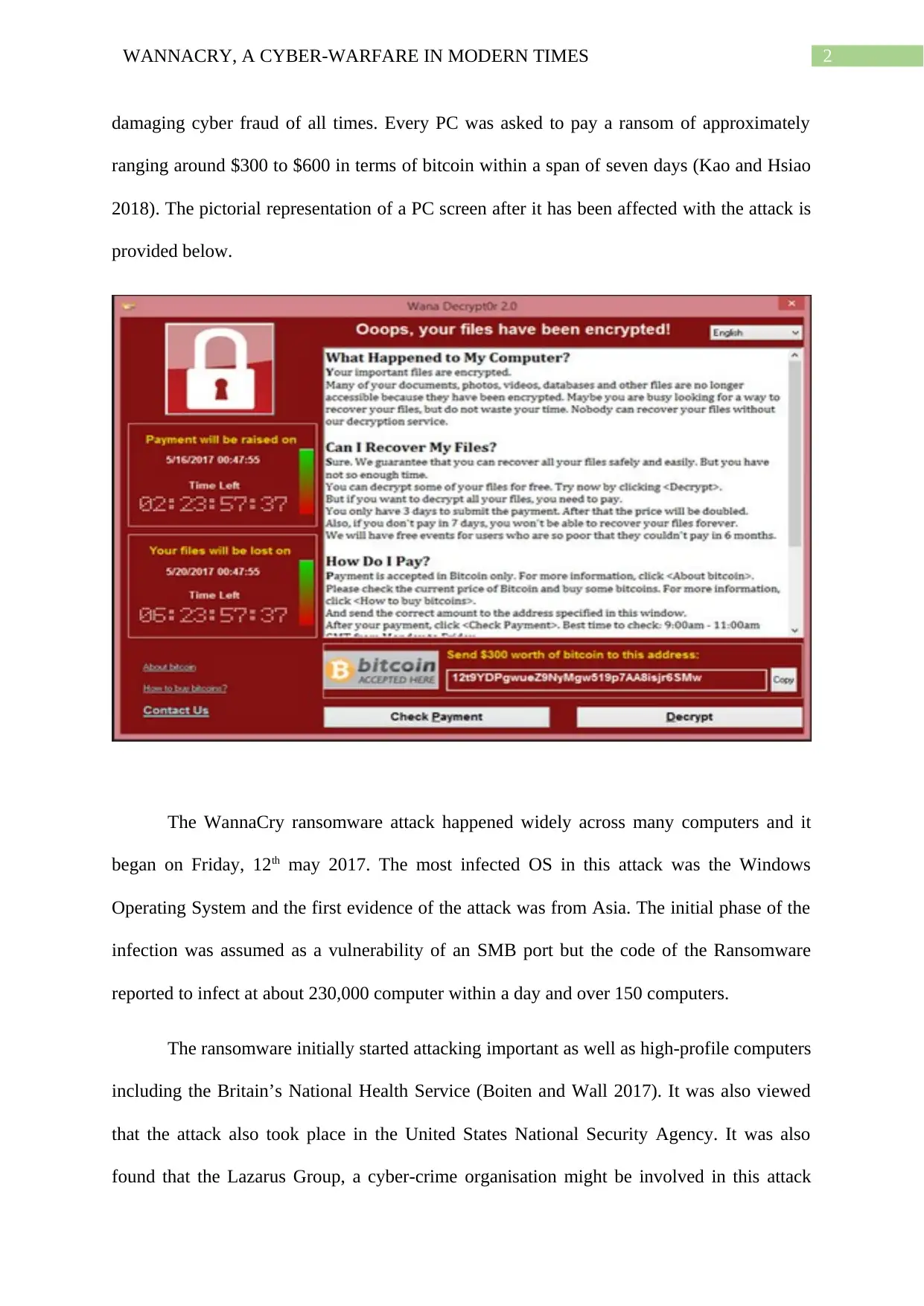
damaging cyber fraud of all times. Every PC was asked to pay a ransom of approximately
ranging around $300 to $600 in terms of bitcoin within a span of seven days (Kao and Hsiao
2018). The pictorial representation of a PC screen after it has been affected with the attack is
provided below.
The WannaCry ransomware attack happened widely across many computers and it
began on Friday, 12th may 2017. The most infected OS in this attack was the Windows
Operating System and the first evidence of the attack was from Asia. The initial phase of the
infection was assumed as a vulnerability of an SMB port but the code of the Ransomware
reported to infect at about 230,000 computer within a day and over 150 computers.
The ransomware initially started attacking important as well as high-profile computers
including the Britain’s National Health Service (Boiten and Wall 2017). It was also viewed
that the attack also took place in the United States National Security Agency. It was also
found that the Lazarus Group, a cyber-crime organisation might be involved in this attack
damaging cyber fraud of all times. Every PC was asked to pay a ransom of approximately
ranging around $300 to $600 in terms of bitcoin within a span of seven days (Kao and Hsiao
2018). The pictorial representation of a PC screen after it has been affected with the attack is
provided below.
The WannaCry ransomware attack happened widely across many computers and it
began on Friday, 12th may 2017. The most infected OS in this attack was the Windows
Operating System and the first evidence of the attack was from Asia. The initial phase of the
infection was assumed as a vulnerability of an SMB port but the code of the Ransomware
reported to infect at about 230,000 computer within a day and over 150 computers.
The ransomware initially started attacking important as well as high-profile computers
including the Britain’s National Health Service (Boiten and Wall 2017). It was also viewed
that the attack also took place in the United States National Security Agency. It was also
found that the Lazarus Group, a cyber-crime organisation might be involved in this attack
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WANNACRY, A CYBER-WARFARE IN MODERN TIMES
which is connected to North Korean government. By the end of December 2017, countries
like United States, United Kingdom as well as Australia formally reported the involvement of
North Korea behind the WannaCry Ransomware attack.
The chronology of the Ransomware attack is as follows
12th May 2017 (Friday): In morning, Telefonica, a Mobile operator of Spain firstly
reported about the attacks of the WannaCry.
By the late morning, many hospitals over UK started reporting about the attack to
their national cyber incident response centre.
After that Renault, the French carmaker was also hit by the attacks of WannaCry.
In Russia, the interior ministry as well as MegaFon and Sberbank also experienced the
attack of the WannaCry Ransomware.
In US FedEx was the most probable high profile victim.
The predictable motive of the WannaCry Ransomware attack is to collect money in
terms of currency or crypto-currency (Kalita 2017). As this attack so not continued for long,
the motives of this ransomware attack can be stated as follows:
Destructive: Despite of the financial terminology, the cybercriminals associated with
the attack had an intention to create a disruption in the business whose servers are
infected by the WannaCry Ransomware attack.
Financial motivation: This is the motivation of the criminals, which initiated them to
think to extract as much as financial reward or ransom, which is possible (Koopman
2017).
Crypto-currency manipulation: As the ransom was taken in terms of crypto
currencies, it is the best way to make money in illegal manner.
which is connected to North Korean government. By the end of December 2017, countries
like United States, United Kingdom as well as Australia formally reported the involvement of
North Korea behind the WannaCry Ransomware attack.
The chronology of the Ransomware attack is as follows
12th May 2017 (Friday): In morning, Telefonica, a Mobile operator of Spain firstly
reported about the attacks of the WannaCry.
By the late morning, many hospitals over UK started reporting about the attack to
their national cyber incident response centre.
After that Renault, the French carmaker was also hit by the attacks of WannaCry.
In Russia, the interior ministry as well as MegaFon and Sberbank also experienced the
attack of the WannaCry Ransomware.
In US FedEx was the most probable high profile victim.
The predictable motive of the WannaCry Ransomware attack is to collect money in
terms of currency or crypto-currency (Kalita 2017). As this attack so not continued for long,
the motives of this ransomware attack can be stated as follows:
Destructive: Despite of the financial terminology, the cybercriminals associated with
the attack had an intention to create a disruption in the business whose servers are
infected by the WannaCry Ransomware attack.
Financial motivation: This is the motivation of the criminals, which initiated them to
think to extract as much as financial reward or ransom, which is possible (Koopman
2017).
Crypto-currency manipulation: As the ransom was taken in terms of crypto
currencies, it is the best way to make money in illegal manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WANNACRY, A CYBER-WARFARE IN MODERN TIMES
Misdirection: One of the most important way to get away after the cybercrime
includes that misdirecting the focus of the affected systems in ransomware whereas
the main motive was to cause a disaster to the personal data of the users.
The WannaCry ransomware attack mainly targeted the high profile systems of the big
sized industries so that the ransom can be achieved at a greater level. Moreover, the systems
using the windows operating system are more affected with the attacks using a Trojan virus
as an attachment with other links in the system.
The initial infection of the WannaCry Ransomware is still under assessment, but the
st5arting of this attack may be predicted that the attackers use an unsolicited design of email,
which provokes the user to open the attachment that is infected with the Trojan virus (Sahi
2017). Once the attachment has been executed, the WannaCry ransomware searches for the
flaws of the windows operating system in the system. With the help of that flaw, it replicates
itself and starts to spread quickly all over the computer system as well as in the network to
which the PC is connected. It then starts infecting the vulnerable machines present in the
network system. The ransomware simultaneously encrypts the files present in the system.
Moreover, it starts to show the warning message that states the amount of the ransom in
Bitcoin for which is not paid will delete all the data present in the system as well as in the
network server (Hsiao and Kao 2018).
Although WannaCry Ransomware attack has many cyber aspects regarding the cyber-
warfare attacks, it has some non-cyber aspects too. As most of the computers that were
affected by the attack were MS-Windows based the customers who run their PC’s with this
operating system can lose a trust on it (Mansfield-Devine 2016). This will highly affect the
customers trust with the company thus resulting in the negative effect of the customer loyalty.
Moreover, the data loss from the server can also put an adverse effect on the customer’s
Misdirection: One of the most important way to get away after the cybercrime
includes that misdirecting the focus of the affected systems in ransomware whereas
the main motive was to cause a disaster to the personal data of the users.
The WannaCry ransomware attack mainly targeted the high profile systems of the big
sized industries so that the ransom can be achieved at a greater level. Moreover, the systems
using the windows operating system are more affected with the attacks using a Trojan virus
as an attachment with other links in the system.
The initial infection of the WannaCry Ransomware is still under assessment, but the
st5arting of this attack may be predicted that the attackers use an unsolicited design of email,
which provokes the user to open the attachment that is infected with the Trojan virus (Sahi
2017). Once the attachment has been executed, the WannaCry ransomware searches for the
flaws of the windows operating system in the system. With the help of that flaw, it replicates
itself and starts to spread quickly all over the computer system as well as in the network to
which the PC is connected. It then starts infecting the vulnerable machines present in the
network system. The ransomware simultaneously encrypts the files present in the system.
Moreover, it starts to show the warning message that states the amount of the ransom in
Bitcoin for which is not paid will delete all the data present in the system as well as in the
network server (Hsiao and Kao 2018).
Although WannaCry Ransomware attack has many cyber aspects regarding the cyber-
warfare attacks, it has some non-cyber aspects too. As most of the computers that were
affected by the attack were MS-Windows based the customers who run their PC’s with this
operating system can lose a trust on it (Mansfield-Devine 2016). This will highly affect the
customers trust with the company thus resulting in the negative effect of the customer loyalty.
Moreover, the data loss from the server can also put an adverse effect on the customer’s

5WANNACRY, A CYBER-WARFARE IN MODERN TIMES
security and privacy of data thus losing the faith of the customers from keeping their data
using the cloud systems.
The National Health Service (NHS) of the UK is identified as one of the high profile
victims of the WannaCry ransomware attacks who lost at about $100 million followed by the
prime Russian banks and more than 29000 organizations of China falling into this attack. The
car manufacturing company, Renault was also one of the prime victims of this attack.
After the WannaCry ransomware has hit the NHS of UK, it has affected more than
200,000 computer systems in the organization (Collier 2017). The NHS was bound to provide
the ransom in terms of bitcoin, which cost them around £20m. The WannaCry easily affected
the systems of the NHS as they were using outdated systems that are quite vulnerable to the
cyber-attacks. After the attack, the NHS started upgrading its systems, which cost them
around £72m. However, it can be said that with this upgrade the organization will be
protected from the future cyber-attacks (Gayle et al. 2017).
The next organization, which was affected by the attack, was the prime Russian
Banks. The data of the customers were at risk due to this cyber-attack (Richardson and North
2017). To recover the files the bank authority provided a large amount of ransom but then
also the data files were not recovered. After the attack, the resources of the organization were
compromised. However, Reuters does not accept this incident of cyber-attack.
Telefonica, another high profile farm has also hit with the Ransomware attack. After
the attack happened, the security teams as well as the large financial teams of the
organizations took help from the executives of the private security farms to avoid the usage
of the data by the ransomware attackers (Laszka, Farhang and Grossklags 2017).
security and privacy of data thus losing the faith of the customers from keeping their data
using the cloud systems.
The National Health Service (NHS) of the UK is identified as one of the high profile
victims of the WannaCry ransomware attacks who lost at about $100 million followed by the
prime Russian banks and more than 29000 organizations of China falling into this attack. The
car manufacturing company, Renault was also one of the prime victims of this attack.
After the WannaCry ransomware has hit the NHS of UK, it has affected more than
200,000 computer systems in the organization (Collier 2017). The NHS was bound to provide
the ransom in terms of bitcoin, which cost them around £20m. The WannaCry easily affected
the systems of the NHS as they were using outdated systems that are quite vulnerable to the
cyber-attacks. After the attack, the NHS started upgrading its systems, which cost them
around £72m. However, it can be said that with this upgrade the organization will be
protected from the future cyber-attacks (Gayle et al. 2017).
The next organization, which was affected by the attack, was the prime Russian
Banks. The data of the customers were at risk due to this cyber-attack (Richardson and North
2017). To recover the files the bank authority provided a large amount of ransom but then
also the data files were not recovered. After the attack, the resources of the organization were
compromised. However, Reuters does not accept this incident of cyber-attack.
Telefonica, another high profile farm has also hit with the Ransomware attack. After
the attack happened, the security teams as well as the large financial teams of the
organizations took help from the executives of the private security farms to avoid the usage
of the data by the ransomware attackers (Laszka, Farhang and Grossklags 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WANNACRY, A CYBER-WARFARE IN MODERN TIMES
The organization could have been well prepared before, for the avoidance of the
Ransomware attacks (Brewer 2016). Therefore, there are certain steps that the organizations
could have adapted to prevent the Ransomware cyber-attacks.
Firstly, a security risk assessment procedure could have been adapted for the
prevention. This security risk assessment follows the four steps:
1. Identification: Initially, the critical assets of the technological infrastructure are
to be determined. Lastly, the sensitive data is properly diagnosed and a risk profile
for each is to be created (Quinkert et al. 2018).
2. Assessment: This methodology is used to analyse the relation between assets, the
threats, the vulnerabilities and controlling mitigation.
3. Mitigation: Companies need to define mitigation approach and security controls
in terms of each risk is to be enforced.
4. Prevention: implementation of tools as well as methods should be adapted to
minimize vulnerabilities and threats from trespassing into the business
organisation.
These security risk-assessment methods can help an organization to
Identify the assets, which are present within the organisation.
Properly assess the risk profiles of each asset
Understand which data are to be stored, transmitted or generated by the assets
Critically assess the operations related to business
Measure the risk for every assets and set them accordingly to their risk ranking
The other relevant steps that can be taken by the organizations to avoid their business
from ransomware attacks are:
The organization could have been well prepared before, for the avoidance of the
Ransomware attacks (Brewer 2016). Therefore, there are certain steps that the organizations
could have adapted to prevent the Ransomware cyber-attacks.
Firstly, a security risk assessment procedure could have been adapted for the
prevention. This security risk assessment follows the four steps:
1. Identification: Initially, the critical assets of the technological infrastructure are
to be determined. Lastly, the sensitive data is properly diagnosed and a risk profile
for each is to be created (Quinkert et al. 2018).
2. Assessment: This methodology is used to analyse the relation between assets, the
threats, the vulnerabilities and controlling mitigation.
3. Mitigation: Companies need to define mitigation approach and security controls
in terms of each risk is to be enforced.
4. Prevention: implementation of tools as well as methods should be adapted to
minimize vulnerabilities and threats from trespassing into the business
organisation.
These security risk-assessment methods can help an organization to
Identify the assets, which are present within the organisation.
Properly assess the risk profiles of each asset
Understand which data are to be stored, transmitted or generated by the assets
Critically assess the operations related to business
Measure the risk for every assets and set them accordingly to their risk ranking
The other relevant steps that can be taken by the organizations to avoid their business
from ransomware attacks are:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WANNACRY, A CYBER-WARFARE IN MODERN TIMES
The proper system update should be done for the PC’s running in the business as
Microsoft provides patches for preventing the ransomware attacks (Kshetri and Voas
2017).
A dedicated ransomware blocker should be installed in the server computer to avoid
the cyber-attack.
The security analyst of the server could block the port 445 of the TCP to prevent the
vulnerability of the Ransomware attacks (Pope 2016).
A constant check should be maintained on the server system for any occurrence of
vulnerability.
Intercept X is a software, which is especially developed as a preventive measure of
ransomware. This software can detect as well as prevent the before-never-seen strains
of ransomware. This software must be installed in the server so that the network is
quite secure from attacks of Ransomware (Formby, Durbha and Beyah 2017).
Avoiding payment of the ransom in any condition as the regain of data cannot be
guaranteed. As there is, no surety of getting the encrypted data back the ransom should not be
paid at any circumstances (Salvi and Kerkar 2016).
The security risk assessment analysis should be carried out in a regular manner (Tuttle
2016).
Regular changes in the network environment is to be carried out to build a strong
defence against the ransomware.
Next generation protection methodologies should be used to prevent the malware
components, including the ransomware.
Utilization of MTP’s in the cloud are very necessary in order to prevent the Trojan
viruses entering into the cloud.
The proper system update should be done for the PC’s running in the business as
Microsoft provides patches for preventing the ransomware attacks (Kshetri and Voas
2017).
A dedicated ransomware blocker should be installed in the server computer to avoid
the cyber-attack.
The security analyst of the server could block the port 445 of the TCP to prevent the
vulnerability of the Ransomware attacks (Pope 2016).
A constant check should be maintained on the server system for any occurrence of
vulnerability.
Intercept X is a software, which is especially developed as a preventive measure of
ransomware. This software can detect as well as prevent the before-never-seen strains
of ransomware. This software must be installed in the server so that the network is
quite secure from attacks of Ransomware (Formby, Durbha and Beyah 2017).
Avoiding payment of the ransom in any condition as the regain of data cannot be
guaranteed. As there is, no surety of getting the encrypted data back the ransom should not be
paid at any circumstances (Salvi and Kerkar 2016).
The security risk assessment analysis should be carried out in a regular manner (Tuttle
2016).
Regular changes in the network environment is to be carried out to build a strong
defence against the ransomware.
Next generation protection methodologies should be used to prevent the malware
components, including the ransomware.
Utilization of MTP’s in the cloud are very necessary in order to prevent the Trojan
viruses entering into the cloud.

8WANNACRY, A CYBER-WARFARE IN MODERN TIMES
Many business organisations are struggling for the prevention of Ransomware. As
from the research, the security issues related to WannaCry Ransomware attacks can be
identified and possible measures or solutions are recommended to some extent (Branch et al.
2018). Still, it can be concluded that the business organisations should come up with
innovative techniques to put an end up to the attacks as well as to the issues or else it will
continue like a never-ending process. Apart from these, the companies should also focus on
the development of firewall, ransomware blockers that could prevent these attacks.
Many business organisations are struggling for the prevention of Ransomware. As
from the research, the security issues related to WannaCry Ransomware attacks can be
identified and possible measures or solutions are recommended to some extent (Branch et al.
2018). Still, it can be concluded that the business organisations should come up with
innovative techniques to put an end up to the attacks as well as to the issues or else it will
continue like a never-ending process. Apart from these, the companies should also focus on
the development of firewall, ransomware blockers that could prevent these attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9WANNACRY, A CYBER-WARFARE IN MODERN TIMES
References
Boiten, E.A. and Wall, D.S., 2017. WannaCry report shows NHS chiefs knew of security
danger, but management took no action.
Branch, L.E., Eller, W.S., Bias, T.K., McCawley, M.A., Myers, D.J., Gerber, B.J. and
Bassler, J.R., 2018. Trends in Malware Attacks against United States Healthcare
Organizations. Cyber Threats and Healthcare Organizations: A Public Health Preparedness
Perspective, p.29.
Brewer, R., 2016. Ransomware attacks: detection, prevention and cure. Network security,
2016(9), pp.5-9.
Collier, R., 2017. NHS ransomware attack spreads worldwide.
Formby, D., Durbha, S. and Beyah, R., 2017. Out of control: Ransomware for industrial
control systems. In Proc. RSA Conf. (p. 8).
Gayle, D., Topping, A., Sample, I., Marsh, S. and Dodd, V., 2017. NHS seeks to recover
from global cyber-attack as security concerns resurface. The Guardian, 13.
Hsiao, S.C. and Kao, D.Y., 2018, February. The static analysis of WannaCry ransomware. In
2018 20th International Conference on Advanced Communication Technology (ICACT) (pp.
153-158). IEEE.
Kalita, E., 2017. WannaCry Ransomware Attack: Protect Yourself from WannaCry
Ransomware Cyber Risk and Cyber War.
Kao, D.Y. and Hsiao, S.C., 2018, February. The dynamic analysis of WannaCry ransomware.
In 2018 20th International Conference on Advanced Communication Technology (ICACT)
(pp. 159-166). IEEE.
References
Boiten, E.A. and Wall, D.S., 2017. WannaCry report shows NHS chiefs knew of security
danger, but management took no action.
Branch, L.E., Eller, W.S., Bias, T.K., McCawley, M.A., Myers, D.J., Gerber, B.J. and
Bassler, J.R., 2018. Trends in Malware Attacks against United States Healthcare
Organizations. Cyber Threats and Healthcare Organizations: A Public Health Preparedness
Perspective, p.29.
Brewer, R., 2016. Ransomware attacks: detection, prevention and cure. Network security,
2016(9), pp.5-9.
Collier, R., 2017. NHS ransomware attack spreads worldwide.
Formby, D., Durbha, S. and Beyah, R., 2017. Out of control: Ransomware for industrial
control systems. In Proc. RSA Conf. (p. 8).
Gayle, D., Topping, A., Sample, I., Marsh, S. and Dodd, V., 2017. NHS seeks to recover
from global cyber-attack as security concerns resurface. The Guardian, 13.
Hsiao, S.C. and Kao, D.Y., 2018, February. The static analysis of WannaCry ransomware. In
2018 20th International Conference on Advanced Communication Technology (ICACT) (pp.
153-158). IEEE.
Kalita, E., 2017. WannaCry Ransomware Attack: Protect Yourself from WannaCry
Ransomware Cyber Risk and Cyber War.
Kao, D.Y. and Hsiao, S.C., 2018, February. The dynamic analysis of WannaCry ransomware.
In 2018 20th International Conference on Advanced Communication Technology (ICACT)
(pp. 159-166). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10WANNACRY, A CYBER-WARFARE IN MODERN TIMES
Koopman, M., 2017. Preventing Ransomware on the Internet of Things.
Kshetri, N. and Voas, J., 2017. Do crypto-currencies fuel ransomware?. IT professional,
19(5), pp.11-15.
Laszka, A., Farhang, S. and Grossklags, J., 2017, October. On the economics of ransomware.
In International Conference on Decision and Game Theory for Security (pp. 397-417).
Springer, Cham.
Mansfield-Devine, S., 2016. Ransomware: taking businesses hostage. Network Security,
2016(10), pp.8-17.
Mohurle, S. and Patil, M., 2017. A brief study of wannacry threat: Ransomware attack 2017.
International Journal of Advanced Research in Computer Science, 8(5).
Pope, J., 2016. Ransomware: minimizing the risks. Innovations in clinical neuroscience,
13(11-12), p.37.
Quinkert, F., Holz, T., Hossain, K.S.M., Ferrara, E. and Lerman, K., 2018. RAPTOR:
Ransomware Attack PredicTOR. arXiv preprint arXiv:1803.01598.
Richardson, R. and North, M.M., 2017. Ransomware: Evolution, mitigation and prevention.
International Management Review, 13(1), p.10.
Sahi, S.K., 2017. A Study of WannaCry Ransomware Attack. International Journal of
Engineering Research in Computer Science and Engineering, 4(9), pp.5-7.
Salvi, M.H.U. and Kerkar, M.R.V., 2016. Ransomware: A cyber extortion. ASIAN JOURNAL
FOR CONVERGENCE IN TECHNOLOGY (AJCT)-UGC LISTED, 2.
Tuttle, H., 2016. Ransomware attacks pose growing threat. Risk Management, 63(4), p.4.
Koopman, M., 2017. Preventing Ransomware on the Internet of Things.
Kshetri, N. and Voas, J., 2017. Do crypto-currencies fuel ransomware?. IT professional,
19(5), pp.11-15.
Laszka, A., Farhang, S. and Grossklags, J., 2017, October. On the economics of ransomware.
In International Conference on Decision and Game Theory for Security (pp. 397-417).
Springer, Cham.
Mansfield-Devine, S., 2016. Ransomware: taking businesses hostage. Network Security,
2016(10), pp.8-17.
Mohurle, S. and Patil, M., 2017. A brief study of wannacry threat: Ransomware attack 2017.
International Journal of Advanced Research in Computer Science, 8(5).
Pope, J., 2016. Ransomware: minimizing the risks. Innovations in clinical neuroscience,
13(11-12), p.37.
Quinkert, F., Holz, T., Hossain, K.S.M., Ferrara, E. and Lerman, K., 2018. RAPTOR:
Ransomware Attack PredicTOR. arXiv preprint arXiv:1803.01598.
Richardson, R. and North, M.M., 2017. Ransomware: Evolution, mitigation and prevention.
International Management Review, 13(1), p.10.
Sahi, S.K., 2017. A Study of WannaCry Ransomware Attack. International Journal of
Engineering Research in Computer Science and Engineering, 4(9), pp.5-7.
Salvi, M.H.U. and Kerkar, M.R.V., 2016. Ransomware: A cyber extortion. ASIAN JOURNAL
FOR CONVERGENCE IN TECHNOLOGY (AJCT)-UGC LISTED, 2.
Tuttle, H., 2016. Ransomware attacks pose growing threat. Risk Management, 63(4), p.4.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





