Digital Security Fundamentals Lab Reflection Questions - Week 01-05
VerifiedAdded on 2019/09/30
|33
|6001
|366
Homework Assignment
AI Summary
This assignment comprises reflection questions and answers from five weeks of digital security labs, covering fundamental concepts and practical applications. The first week explores promiscuous mode, Wireshark, and network sniffing. Week two delves into NMAP, Zenmap, and TCP/UDP ports. Week three focuses on symmetric encryption and Linux file permissions, while week four examines asymmetric encryption, Telnet, SSH, and reverse shells. Finally, week five covers secure hash functions and proxy servers. The answers provide detailed explanations and insights into each topic, offering a comprehensive understanding of digital security principles and tools. This assignment aims to enhance the understanding of digital security concepts and their practical application in real-world scenarios, providing students with a solid foundation in cybersecurity fundamentals.

Week 01 - Lab Exercise Digital Security Fundamentals
Reflection questions:
1. What does promiscuous mode mean?
Promiscuous mode is a network security and monitoring technique that
enables access to entire network data packets by any configured network
adapter on a host system.It sets the mode for both a wired network interface
controller (NIC) or wireless network interface controller (WNIC) that causes
the controller to pass all traffic it receives to the central processing unit (CPU)
rather than passing only the frames that the controller is specifically
programmed to receive. This mode is normally used for packet sniffing that
takes place on a router or on a computer connected to a wired network or one
being part of a wireless LAN. Some Applications that use the Promiscuous
mode are NetScout Sniffer, Wireshark (formerly Ethereal),VMware’s VMnet
bridging ,Cryptanalysis.. etc
2. How do you set promiscuous mode in Linux?
• To set the promiscuous mode on the physical NIC, run the following
command:
# ifconfig eth0 promisc
Disable Promiscuous Mode
• To disable promiscuous mode on the physical NIC, run the following
command:
# ifconfig eth0 –promisc
Reflection questions:
1. What does promiscuous mode mean?
Promiscuous mode is a network security and monitoring technique that
enables access to entire network data packets by any configured network
adapter on a host system.It sets the mode for both a wired network interface
controller (NIC) or wireless network interface controller (WNIC) that causes
the controller to pass all traffic it receives to the central processing unit (CPU)
rather than passing only the frames that the controller is specifically
programmed to receive. This mode is normally used for packet sniffing that
takes place on a router or on a computer connected to a wired network or one
being part of a wireless LAN. Some Applications that use the Promiscuous
mode are NetScout Sniffer, Wireshark (formerly Ethereal),VMware’s VMnet
bridging ,Cryptanalysis.. etc
2. How do you set promiscuous mode in Linux?
• To set the promiscuous mode on the physical NIC, run the following
command:
# ifconfig eth0 promisc
Disable Promiscuous Mode
• To disable promiscuous mode on the physical NIC, run the following
command:
# ifconfig eth0 –promisc
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3.Does a network interface card on a sniffer need an IP address? And Why?
No, the sniffer doesn't require an IP address, it wants to remain invisible to the
other machines in order to intercept messages undetected.
4. What is APR traffic?
ARP stands for Address Resolution Protocol. When you try to ping an IP
address on your local network, say 192.168.1.1, your system has to turn the
IP address 192.168.1.1 into a MAC address. This involves using ARP to
resolve the address, hence its name.
Systems keep an ARP look-up table where they store information about what
IP addresses are associated with what MAC addresses. When trying to send
a packet to an IP address, the system will first consult this table to see if it
already knows the MAC address. If there is a value cached, ARP is not used.
5.How do you start Wireshark from a terminal in Linux?
To start Wireshark enter the command
wireshark -k
The -k option specifies that Wireshark should start capturing packets
immediately. This option requires the use of the -i parameter to specify the
interface that packet capture will occur from.
6.How do you choose the interface to capture traffic on in Wireshark?
To choose the interface to capture traffic we can do it by getting an overview
of available interfaces.
No, the sniffer doesn't require an IP address, it wants to remain invisible to the
other machines in order to intercept messages undetected.
4. What is APR traffic?
ARP stands for Address Resolution Protocol. When you try to ping an IP
address on your local network, say 192.168.1.1, your system has to turn the
IP address 192.168.1.1 into a MAC address. This involves using ARP to
resolve the address, hence its name.
Systems keep an ARP look-up table where they store information about what
IP addresses are associated with what MAC addresses. When trying to send
a packet to an IP address, the system will first consult this table to see if it
already knows the MAC address. If there is a value cached, ARP is not used.
5.How do you start Wireshark from a terminal in Linux?
To start Wireshark enter the command
wireshark -k
The -k option specifies that Wireshark should start capturing packets
immediately. This option requires the use of the -i parameter to specify the
interface that packet capture will occur from.
6.How do you choose the interface to capture traffic on in Wireshark?
To choose the interface to capture traffic we can do it by getting an overview
of available interfaces.
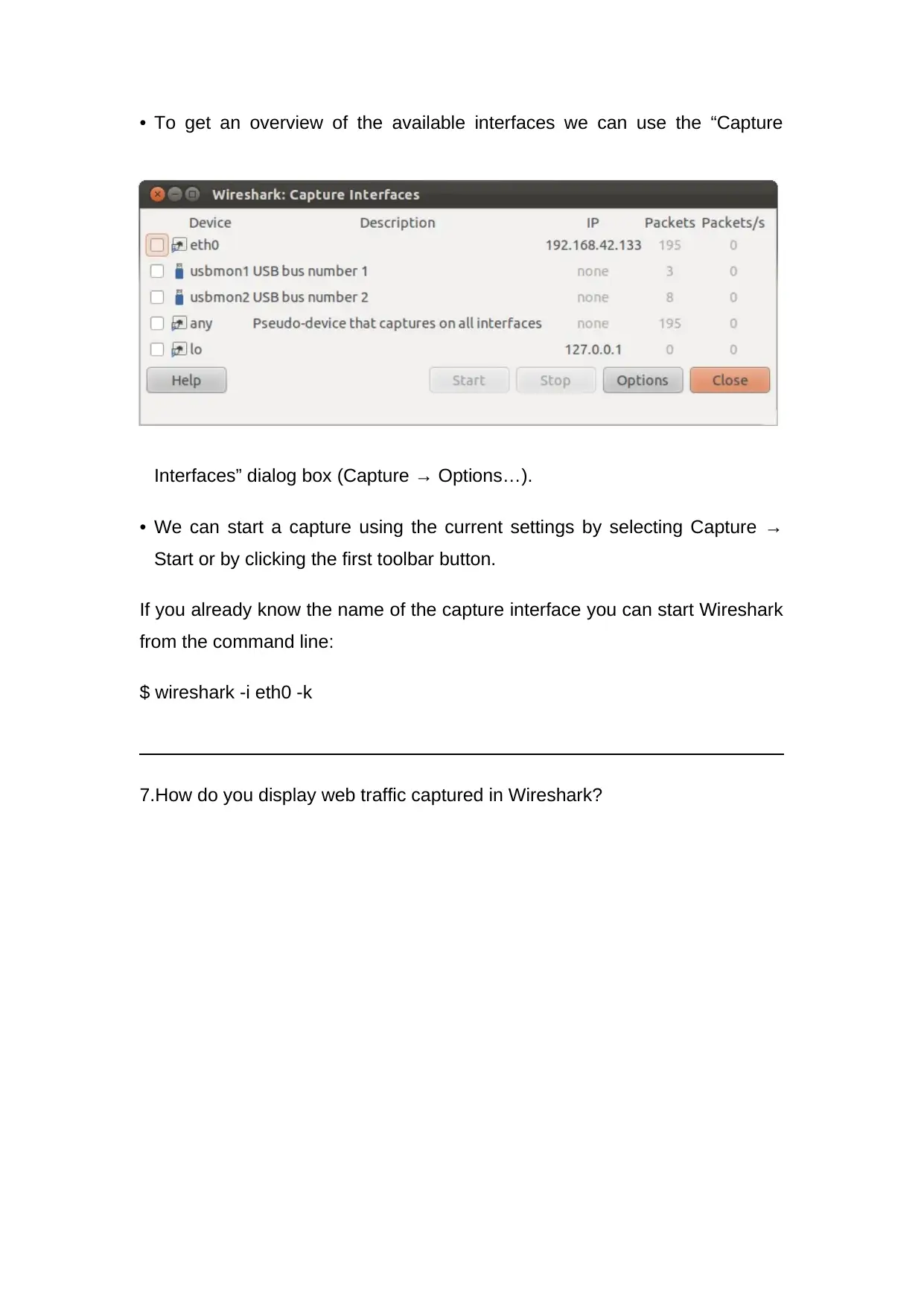
• To get an overview of the available interfaces we can use the “Capture
Interfaces” dialog box (Capture → Options…).
• We can start a capture using the current settings by selecting Capture →
Start or by clicking the first toolbar button.
If you already know the name of the capture interface you can start Wireshark
from the command line:
$ wireshark -i eth0 -k
7.How do you display web traffic captured in Wireshark?
Interfaces” dialog box (Capture → Options…).
• We can start a capture using the current settings by selecting Capture →
Start or by clicking the first toolbar button.
If you already know the name of the capture interface you can start Wireshark
from the command line:
$ wireshark -i eth0 -k
7.How do you display web traffic captured in Wireshark?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

To display the capture traffic, click your wireless interface. You can configure
advanced features by clicking Capture > Options,
As soon as you click the interface’s name, you’ll see the packets start to
appear in real time. Wireshark captures each packet sent to or from your
system.
8. Are FTP username and passwords encrypted?
No,In FTP both the command and data channels are unencrypted.The
username and passwords are unencrypted .So any data sent over these
channels can be intercepted and read.
9.Why would a network admin use a sniffer?
Network admin uses the Sniffer for the following reasons.
• To monitor and analyse data packets flowing over computer networks.
• To examine traffic on the network and to prevent traffic bottlenecks.
• To determine the health of network and diagnose network related issue.
advanced features by clicking Capture > Options,
As soon as you click the interface’s name, you’ll see the packets start to
appear in real time. Wireshark captures each packet sent to or from your
system.
8. Are FTP username and passwords encrypted?
No,In FTP both the command and data channels are unencrypted.The
username and passwords are unencrypted .So any data sent over these
channels can be intercepted and read.
9.Why would a network admin use a sniffer?
Network admin uses the Sniffer for the following reasons.
• To monitor and analyse data packets flowing over computer networks.
• To examine traffic on the network and to prevent traffic bottlenecks.
• To determine the health of network and diagnose network related issue.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10. What is the DVL Virtual Machine?
Damn Vulnerable Linux (DVL)is a learning tool for security. It is broken, ill-
configured, outdated, and exploitable software that makes it vulnerable to
attacks.DVL is a live CD available as a 150MB ISO.It contains older, easily
breakable versions of Apache, MySQL, PHP, and FTP and SSH daemons, as
well as several tools available to help you compile, debug, and break
applications running on these services, including GCC, GDB, NASM, strace,
ELF Shell, DDD, LDasm, LIDa, and more.
11.What did you do in today’s lab?
In todays lab i have learnt about promiscuous mode in Linux, Wireshark,
Sniffers.
Week 02 - Lab Exercise Introduction to Cryptographic Principles
Reflection questions:
1.Why is NMAP useful for people working in network security?
• Open-source tool for vulnerability scanning and network discovery.
• To identify what devices are running on their systems.
• To discover hosts that are available and the services they offer.
• To find open ports and detecting security risks.
• To monitor single hosts as well as vast networks
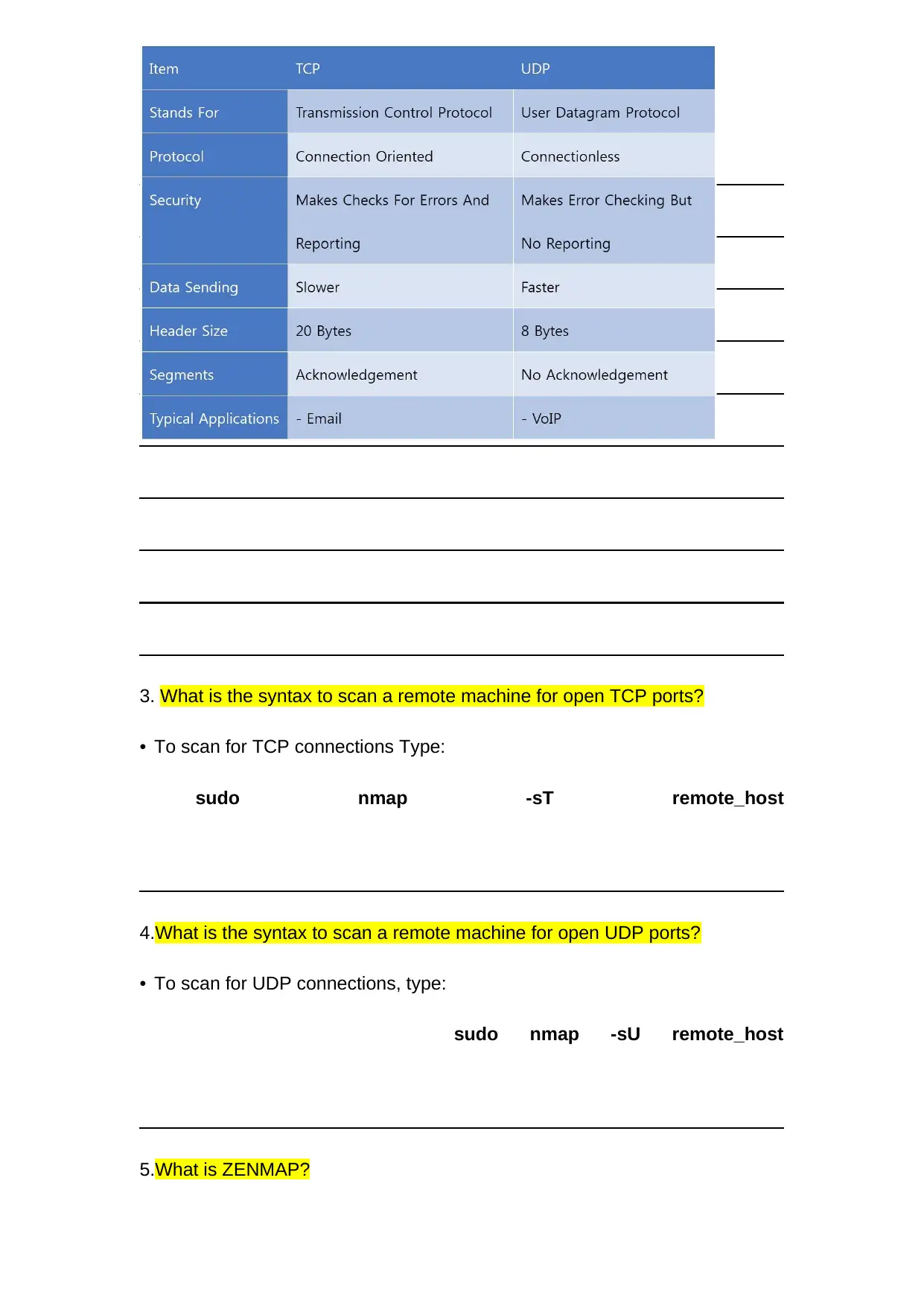
2. Compare and contrast UDP with TCP.
Damn Vulnerable Linux (DVL)is a learning tool for security. It is broken, ill-
configured, outdated, and exploitable software that makes it vulnerable to
attacks.DVL is a live CD available as a 150MB ISO.It contains older, easily
breakable versions of Apache, MySQL, PHP, and FTP and SSH daemons, as
well as several tools available to help you compile, debug, and break
applications running on these services, including GCC, GDB, NASM, strace,
ELF Shell, DDD, LDasm, LIDa, and more.
11.What did you do in today’s lab?
In todays lab i have learnt about promiscuous mode in Linux, Wireshark,
Sniffers.
Week 02 - Lab Exercise Introduction to Cryptographic Principles
Reflection questions:
1.Why is NMAP useful for people working in network security?
• Open-source tool for vulnerability scanning and network discovery.
• To identify what devices are running on their systems.
• To discover hosts that are available and the services they offer.
• To find open ports and detecting security risks.
• To monitor single hosts as well as vast networks
2. Compare and contrast UDP with TCP.
3. What is the syntax to scan a remote machine for open TCP ports?
• To scan for TCP connections Type:
sudo nmap -sT remote_host
4.What is the syntax to scan a remote machine for open UDP ports?
• To scan for UDP connections, type:
sudo nmap -sU remote_host
5.What is ZENMAP?
• To scan for TCP connections Type:
sudo nmap -sT remote_host
4.What is the syntax to scan a remote machine for open UDP ports?
• To scan for UDP connections, type:
sudo nmap -sU remote_host
5.What is ZENMAP?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
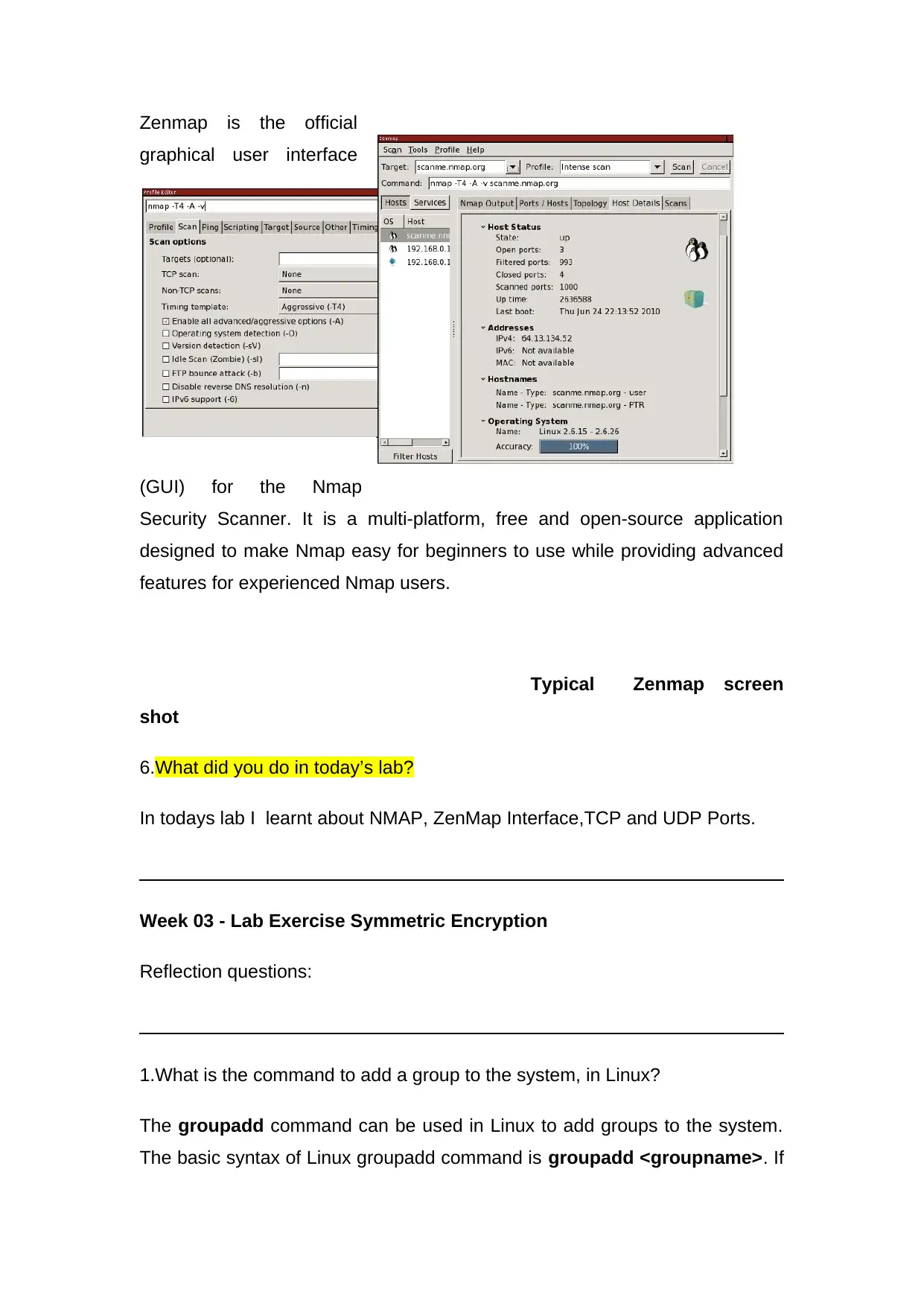
Zenmap is the official
graphical user interface
(GUI) for the Nmap
Security Scanner. It is a multi-platform, free and open-source application
designed to make Nmap easy for beginners to use while providing advanced
features for experienced Nmap users.
Typical Zenmap screen
shot
6.What did you do in today’s lab?
In todays lab I learnt about NMAP, ZenMap Interface,TCP and UDP Ports.
Week 03 - Lab Exercise Symmetric Encryption
Reflection questions:
1.What is the command to add a group to the system, in Linux?
The groupadd command can be used in Linux to add groups to the system.
The basic syntax of Linux groupadd command is groupadd <groupname>. If
graphical user interface
(GUI) for the Nmap
Security Scanner. It is a multi-platform, free and open-source application
designed to make Nmap easy for beginners to use while providing advanced
features for experienced Nmap users.
Typical Zenmap screen
shot
6.What did you do in today’s lab?
In todays lab I learnt about NMAP, ZenMap Interface,TCP and UDP Ports.
Week 03 - Lab Exercise Symmetric Encryption
Reflection questions:
1.What is the command to add a group to the system, in Linux?
The groupadd command can be used in Linux to add groups to the system.
The basic syntax of Linux groupadd command is groupadd <groupname>. If
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

no command-line options are used, the group is created with the next
available Group ID number (GID) above 499. To specify a GID, use the
groupadd -g <gid> <group-name> command.
[root@RHEL2 ~]# groupadd engineering
2.What is the command to give a user a password, in Linux?
Create password for an user
Passwd username
Example command:
root@linuxnix.com:/home/surendra# passwd krishan
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
3.What is the command to add a user to the system, in Linux?
available Group ID number (GID) above 499. To specify a GID, use the
groupadd -g <gid> <group-name> command.
[root@RHEL2 ~]# groupadd engineering
2.What is the command to give a user a password, in Linux?
Create password for an user
Passwd username
Example command:
root@linuxnix.com:/home/surendra# passwd krishan
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
3.What is the command to add a user to the system, in Linux?

To add/create a new user, all you’ve to follow the command ‘useradd‘
or ‘adduser‘ with ‘username’. The ‘username’ is a user login name, that is
used by user to login into the system.
Only one user can be added and that username must be unique (different
from other username already exists on the system).
For example, to add a new user called ‘tecmint‘, use the following command.
[root@tecmint ~]# useradd tecmint
4.Where is the users encrypted password hash stored, in Linux?
Linux encrypted passwords are stored in the /etc/shadow file. The Secure
Hash Algorithms (SHA) are a set of hash functions often used to hash
passwords.The algorithms supported are MD5 , Blowfish , SHA256 and
SHA512.
5.What is the command to give the GROUP READ and WRITE permissions
for the HR folder using symbolic permissions?
If you have a folder named HR, To add GROUP READ and WRITE
permissions
chmod d g+rx HR
6.What is the command to take away READ and EXECUTE permissions for
others for HR the folder using symbolic permissions?
chmod d o–rx HR
or ‘adduser‘ with ‘username’. The ‘username’ is a user login name, that is
used by user to login into the system.
Only one user can be added and that username must be unique (different
from other username already exists on the system).
For example, to add a new user called ‘tecmint‘, use the following command.
[root@tecmint ~]# useradd tecmint
4.Where is the users encrypted password hash stored, in Linux?
Linux encrypted passwords are stored in the /etc/shadow file. The Secure
Hash Algorithms (SHA) are a set of hash functions often used to hash
passwords.The algorithms supported are MD5 , Blowfish , SHA256 and
SHA512.
5.What is the command to give the GROUP READ and WRITE permissions
for the HR folder using symbolic permissions?
If you have a folder named HR, To add GROUP READ and WRITE
permissions
chmod d g+rx HR
6.What is the command to take away READ and EXECUTE permissions for
others for HR the folder using symbolic permissions?
chmod d o–rx HR
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7.What is the command to give the user, group and others, READ and WRITE
permissions for the HR folder using absolute permissions?
chmod ugo+rw HR
8.What is the command to give the user, group and others, READ and
EXECUTE permissions for the HR folder using absolute permissions?
Chmod ugo +rx HR
9. What did you learn in today’s lab?
In todays lab i learnt about the Linux commands and Linux file permissions for
the folder.
permissions for the HR folder using absolute permissions?
chmod ugo+rw HR
8.What is the command to give the user, group and others, READ and
EXECUTE permissions for the HR folder using absolute permissions?
Chmod ugo +rx HR
9. What did you learn in today’s lab?
In todays lab i learnt about the Linux commands and Linux file permissions for
the folder.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 04 - Lab Exercise Asymmetric Encryption
Reflection questions:
1.What is telnet?
Telnet (TN) is a networking protocol and software program used to access
remote computers and terminals over the Internet or a TCP/IP computer
network. A terminal emulation that enables a user to connect to a remote host
or device using a telnet client, usually over port 23. For example, typing telnet
hostname would connect a user to a host named hostname.
2.How do you start a telnet session?
To Start the Telnet Session
Open a command-line window on the network-management workstation, type
telnet 192.168.70.125, and press Enter. The IP address 192.168.70.125 is the
default IP address of the management module; if a new IP address has been
assigned to the management module, use that one instead. You can also
substitute a valid host name instead of using an IP address.
3.What tool could you use to crack telnet passwords?
Reflection questions:
1.What is telnet?
Telnet (TN) is a networking protocol and software program used to access
remote computers and terminals over the Internet or a TCP/IP computer
network. A terminal emulation that enables a user to connect to a remote host
or device using a telnet client, usually over port 23. For example, typing telnet
hostname would connect a user to a host named hostname.
2.How do you start a telnet session?
To Start the Telnet Session
Open a command-line window on the network-management workstation, type
telnet 192.168.70.125, and press Enter. The IP address 192.168.70.125 is the
default IP address of the management module; if a new IP address has been
assigned to the management module, use that one instead. You can also
substitute a valid host name instead of using an IP address.
3.What tool could you use to crack telnet passwords?

Tools used to crack telnet passwords
Hydra
Ncrack
Patator
Metasploit
4.Which is better to use: SSH or Telnet, and why?
SSH is better to use .The key difference between Telnet and SSH is that SSH
uses encryption, which means that all data transmitted over a network is
secure from eavesdropping. SSH uses the public key encryption for such
purposes.
5.What is a reverse shell?
A reverse shell is a type of shell in which the target machine communicates
back to the attacking machine. The attacking machine has a listener port on
which it receives the connection, which by using, code or command execution
is achieved.
It's a(n insecure) remote shell introduced by the target. That's the opposite of
a "normal" remote shell, that is introduced by the source.
Hydra
Ncrack
Patator
Metasploit
4.Which is better to use: SSH or Telnet, and why?
SSH is better to use .The key difference between Telnet and SSH is that SSH
uses encryption, which means that all data transmitted over a network is
secure from eavesdropping. SSH uses the public key encryption for such
purposes.
5.What is a reverse shell?
A reverse shell is a type of shell in which the target machine communicates
back to the attacking machine. The attacking machine has a listener port on
which it receives the connection, which by using, code or command execution
is achieved.
It's a(n insecure) remote shell introduced by the target. That's the opposite of
a "normal" remote shell, that is introduced by the source.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 33
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




