Wincap: An Open Source Software for Network Analysis and Packet Capture
26 Pages2719 Words142 Views
Added on 2023-04-22
Wincap: An Open Source Software for Network Analysis and Packet Capture
Added on 2023-04-22
ShareRelated Documents
MALWARE ANALYSIS 1
MALWARE ANALYSIS
Name
Instructor
Institution
Course
City
Date
MALWARE ANALYSIS
Name
Instructor
Institution
Course
City
Date

MALWARE ANALYSIS 2
Introduction
Wincap is an open source software, the program is used for network analysis and packet
capture. Most of the networked applications in organizations access network via the widely used
OS like sockets. Wincap software has been used widely to capture and at the same time transmit
network packets. The software consists of a driver which extends the OS so as to provide low-
level network access. This paper will use Wincap to capture packets and provide screenshots on
the same. In addition, the paper will explain what is SNORT, how it works, and its disadvantages
and advantages. Also, the screenshot on SNORT network analyzer will be provided.
Wincap
On September 15th, 2018 Riverbed released a new version of Wincap i.e. version 4.1.3.
The software has not been upgraded for many years since the 1990s. The version has the ability
to sniff loopback packets using windows filtering platform. One of the major purposes of the
current version of Wincap is to provide facilities to capture raw packets, both the one exchanged
by other host and the one destined to the machine where it is running. Second, Wincap is used to
filter packets according to the user-specified rules before even dispatching them to the
application [1]. In addition, Wincap is used to gather statistical information on the organization
network and transmit raw packets to the organization network. Wincap application is used by
lots of network tools for monitoring, security, and troubleshooting. Some of the classical tools
which rely on Wincap are network monitors, network and protocols analyzers, security tools,
traffic monitors, network scanners, security tools, and traffic loggers. In addition, Wincap only
sends and receives packets independently from host protocol.
The current Wincap i.e. is able to send back loopback packets using Winsock Kernel
technique. The look of the of the version is as shown by figure one below
Introduction
Wincap is an open source software, the program is used for network analysis and packet
capture. Most of the networked applications in organizations access network via the widely used
OS like sockets. Wincap software has been used widely to capture and at the same time transmit
network packets. The software consists of a driver which extends the OS so as to provide low-
level network access. This paper will use Wincap to capture packets and provide screenshots on
the same. In addition, the paper will explain what is SNORT, how it works, and its disadvantages
and advantages. Also, the screenshot on SNORT network analyzer will be provided.
Wincap
On September 15th, 2018 Riverbed released a new version of Wincap i.e. version 4.1.3.
The software has not been upgraded for many years since the 1990s. The version has the ability
to sniff loopback packets using windows filtering platform. One of the major purposes of the
current version of Wincap is to provide facilities to capture raw packets, both the one exchanged
by other host and the one destined to the machine where it is running. Second, Wincap is used to
filter packets according to the user-specified rules before even dispatching them to the
application [1]. In addition, Wincap is used to gather statistical information on the organization
network and transmit raw packets to the organization network. Wincap application is used by
lots of network tools for monitoring, security, and troubleshooting. Some of the classical tools
which rely on Wincap are network monitors, network and protocols analyzers, security tools,
traffic monitors, network scanners, security tools, and traffic loggers. In addition, Wincap only
sends and receives packets independently from host protocol.
The current Wincap i.e. is able to send back loopback packets using Winsock Kernel
technique. The look of the of the version is as shown by figure one below

MALWARE ANALYSIS 3
Figure 1: Wincap interface
Some disadvantages of Wincap is that it cannot be used to prevent an incident by itself
i.e. it does not prevent or even block attacks. Also, wincap does help in resolving any malware
issue it only assists in identifying malware. Lastly, the tool does not process encrypted packets.
How to use Winmap
First, one need to examine the interface of the software. By opening the software there
several profiles which is as shown by the screenshot shown below
Figure 2: Winmap profile
Figure 1: Wincap interface
Some disadvantages of Wincap is that it cannot be used to prevent an incident by itself
i.e. it does not prevent or even block attacks. Also, wincap does help in resolving any malware
issue it only assists in identifying malware. Lastly, the tool does not process encrypted packets.
How to use Winmap
First, one need to examine the interface of the software. By opening the software there
several profiles which is as shown by the screenshot shown below
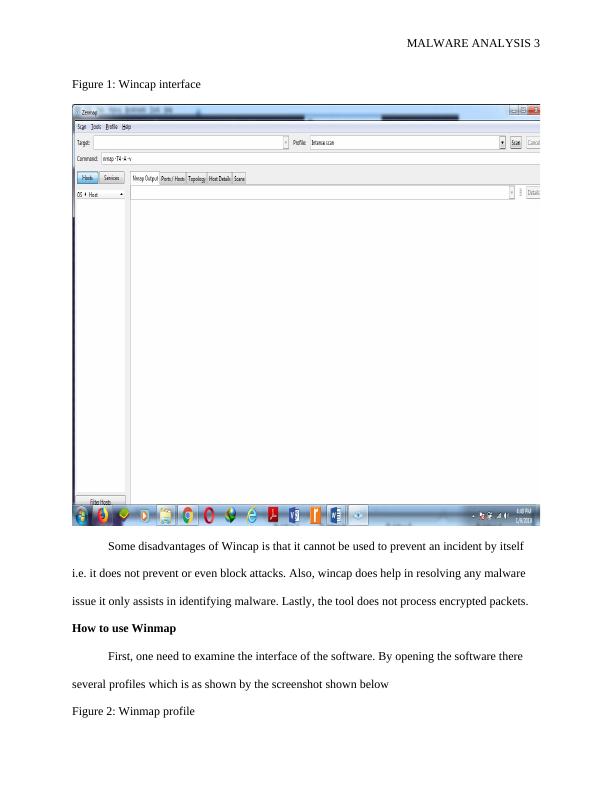
Figure 2: Winmap profile
MALWARE ANALYSIS 4
From the interface, there are four menus which are; scan, tools, profile, and help.
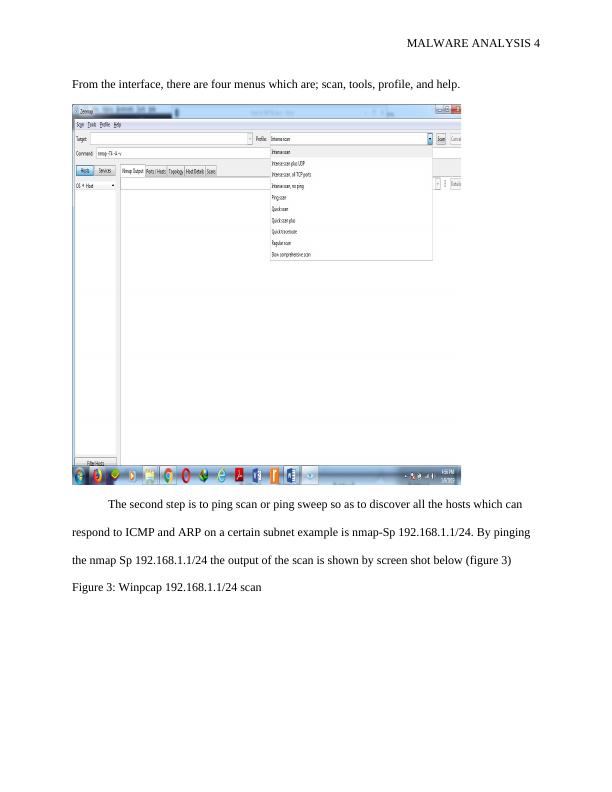
The second step is to ping scan or ping sweep so as to discover all the hosts which can
respond to ICMP and ARP on a certain subnet example is nmap-Sp 192.168.1.1/24. By pinging
the nmap Sp 192.168.1.1/24 the output of the scan is shown by screen shot below (figure 3)
Figure 3: Winpcap 192.168.1.1/24 scan
From the interface, there are four menus which are; scan, tools, profile, and help.
The second step is to ping scan or ping sweep so as to discover all the hosts which can
respond to ICMP and ARP on a certain subnet example is nmap-Sp 192.168.1.1/24. By pinging
the nmap Sp 192.168.1.1/24 the output of the scan is shown by screen shot below (figure 3)
Figure 3: Winpcap 192.168.1.1/24 scan
MALWARE ANALYSIS 5
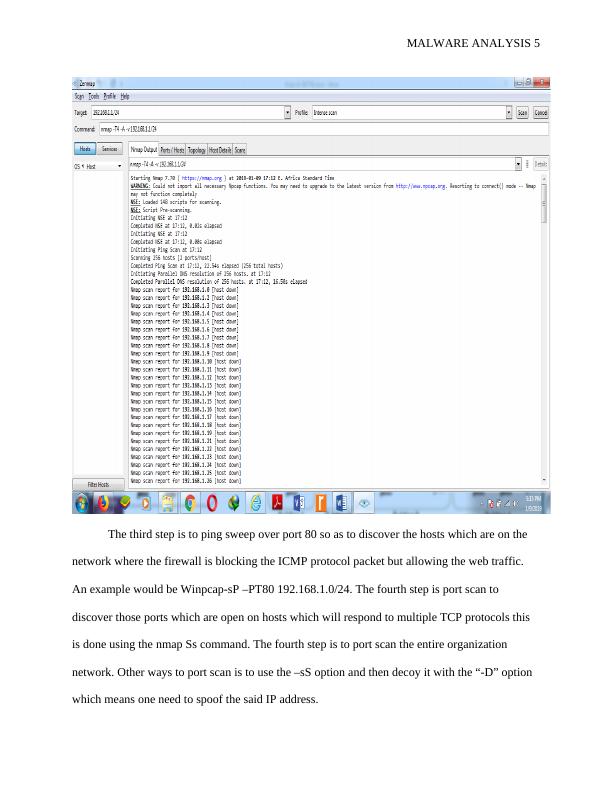
The third step is to ping sweep over port 80 so as to discover the hosts which are on the
network where the firewall is blocking the ICMP protocol packet but allowing the web traffic.
An example would be Winpcap-sP –PT80 192.168.1.0/24. The fourth step is port scan to
discover those ports which are open on hosts which will respond to multiple TCP protocols this
is done using the nmap Ss command. The fourth step is to port scan the entire organization
network. Other ways to port scan is to use the –sS option and then decoy it with the “-D” option
which means one need to spoof the said IP address.
The third step is to ping sweep over port 80 so as to discover the hosts which are on the
network where the firewall is blocking the ICMP protocol packet but allowing the web traffic.
An example would be Winpcap-sP –PT80 192.168.1.0/24. The fourth step is port scan to
discover those ports which are open on hosts which will respond to multiple TCP protocols this
is done using the nmap Ss command. The fourth step is to port scan the entire organization
network. Other ways to port scan is to use the –sS option and then decoy it with the “-D” option
which means one need to spoof the said IP address.
MALWARE ANALYSIS 6
SNORT network analysis tool
Snort is said to be a multi-mode packet analysis tool which is used to sniffer and packet
logger. The tool is also used as a forensic data analysis tool and a network intrusion detection
system. The tool is portable i.e. can be installed in Linux, Solaris, HP-UX, Mac OS, and
Windows. One of the advantages of the tool is that it is fast and has a high probability of
detection for a given network so long as it is on 100 Mbps network. In addition, one can be able
to configure the tool. Third, the tool is an open source software meaning that it is free hence one
can easily download it from the internet with a small file of up to 800k. The fourth advantage is
that it is a packet sniffing lightweight network analysis tool with a rule-based detection engine.
Fifth, with a plug-in, the tool is flexible. Sixth the tool offers a wide range of detection
capabilities as compared to other tools such as OS fingerprinting, CGO exploits, backdoors,
stealth scans, and buffer overflows. Seventh, the creation of new rules is simple when using
SNORT. The tool, also reports results from other tools.
Snort tool has three modes i.e. sniffer mode, intrusion detection, and as a packet logger.
As a packet sniffer one can use the tool as sniffer without having to turn on the tools detection
capabilities. In here one gets a live readout of the network packets without having to pass along
the organization network. As an intrusion detection mode one can invoke the analysis mode
which applies to a set of traffic rules. As a snort mode, the tool is able to perform a deeper
analysis of the network data which is collected by Snort [2].
SNORT network analysis tool
Snort is said to be a multi-mode packet analysis tool which is used to sniffer and packet
logger. The tool is also used as a forensic data analysis tool and a network intrusion detection
system. The tool is portable i.e. can be installed in Linux, Solaris, HP-UX, Mac OS, and
Windows. One of the advantages of the tool is that it is fast and has a high probability of
detection for a given network so long as it is on 100 Mbps network. In addition, one can be able
to configure the tool. Third, the tool is an open source software meaning that it is free hence one
can easily download it from the internet with a small file of up to 800k. The fourth advantage is
that it is a packet sniffing lightweight network analysis tool with a rule-based detection engine.
Fifth, with a plug-in, the tool is flexible. Sixth the tool offers a wide range of detection
capabilities as compared to other tools such as OS fingerprinting, CGO exploits, backdoors,
stealth scans, and buffer overflows. Seventh, the creation of new rules is simple when using
SNORT. The tool, also reports results from other tools.
Snort tool has three modes i.e. sniffer mode, intrusion detection, and as a packet logger.
As a packet sniffer one can use the tool as sniffer without having to turn on the tools detection
capabilities. In here one gets a live readout of the network packets without having to pass along
the organization network. As an intrusion detection mode one can invoke the analysis mode
which applies to a set of traffic rules. As a snort mode, the tool is able to perform a deeper
analysis of the network data which is collected by Snort [2].

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Definitive Guide to Nmap (Network Mapper)lg...
|11
|2038
|41
Ping scanning on the network based on Nmap (WIRESHARK)lg...
|3
|374
|388
Firewall and Configuration Report 2022lg...
|22
|1741
|23
