Wireless Sensor Networks: A Review
VerifiedAdded on 2020/03/23
|17
|2296
|458
AI Summary
This assignment provides a comprehensive review of energy harvesting techniques used in wireless sensor networks (WSNs). It explores different types of energy sources, such as solar, vibration, and RF energy, and discusses their suitability for powering WSNs. The review also examines the challenges associated with energy harvesting and various strategies employed to overcome them. Additionally, it highlights recent advancements and future directions in this field.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: WIRELESS COMMUNICATION
Wireless communication
Name of the student
Name of the University
Author Note
Wireless communication
Name of the student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1WIRELESS COMMUNICATION
Answer to question 1:
The technology known as the WiMAX, known as the Worldwide Interoperability for
Microwave Access, is used to facilitate wireless connectivity among devices by using the IEEE
802.16 standard. The technology is used to command a wide ranges in connection by using the
core principles of multiple input multiple outputs (MIMO) and orthogonal frequency division
multiplexing (OFDM) techniques (Rengaraju, Lung and Srinivasan 2012). The less time for
feasibility and the fewer requirements in cost is the main motivational need for the acceptance of
this technology. The main encryption standards for these technologies are the DES, TripleDES
and RC2.
DES:
The Data Encryption Standard (DES) is termed as a symmetric key algorithm which is
used for the encryption of the data. The main use of the technology is in the application of
cryptography. The operational method of DES includes the transformation of a text bit of a
specific length to a cipher bit text of the same length. The cipher block size is 64 bits. The
method of encryption includes the presence of a key for decrypting the ciphered texts
(Rengaraju, Lung and Srinivasan 2012).
TripleDES:
The symmetric key algorithm of the TripleDES is the same as that of the DES with the
sole difference in its mode of operation. The application of encryption is usually done three
times. The concept of this technology is used to cause an increase in the key size without
applying any changes in the algorithms. This method uses two different keys (j, k) and
applications of encryption are done by each of them (Kamali, Bennett and Cox 2012). As the two
Answer to question 1:
The technology known as the WiMAX, known as the Worldwide Interoperability for
Microwave Access, is used to facilitate wireless connectivity among devices by using the IEEE
802.16 standard. The technology is used to command a wide ranges in connection by using the
core principles of multiple input multiple outputs (MIMO) and orthogonal frequency division
multiplexing (OFDM) techniques (Rengaraju, Lung and Srinivasan 2012). The less time for
feasibility and the fewer requirements in cost is the main motivational need for the acceptance of
this technology. The main encryption standards for these technologies are the DES, TripleDES
and RC2.
DES:
The Data Encryption Standard (DES) is termed as a symmetric key algorithm which is
used for the encryption of the data. The main use of the technology is in the application of
cryptography. The operational method of DES includes the transformation of a text bit of a
specific length to a cipher bit text of the same length. The cipher block size is 64 bits. The
method of encryption includes the presence of a key for decrypting the ciphered texts
(Rengaraju, Lung and Srinivasan 2012).
TripleDES:
The symmetric key algorithm of the TripleDES is the same as that of the DES with the
sole difference in its mode of operation. The application of encryption is usually done three
times. The concept of this technology is used to cause an increase in the key size without
applying any changes in the algorithms. This method uses two different keys (j, k) and
applications of encryption are done by each of them (Kamali, Bennett and Cox 2012). As the two
2WIRELESS COMMUNICATION
key methods are vulnerable to middle key threats and risks, the use for three keys is adopted to
mitigate them.
RC2:
The RC2 algorithm is also termed as a symmetric key algorithm for encryption standards.
However, the size of the key is 40 bits. The main developer of this standard is Ron Rivest. The
size of the key is supposed to be variable (Kamali, Bennett and Cox 2012). The main
specifications of the standards are the presence of 18 rounds where 16 of them are of one type
and the remaining two are of another type. The two types are either MIXING or MASHING.
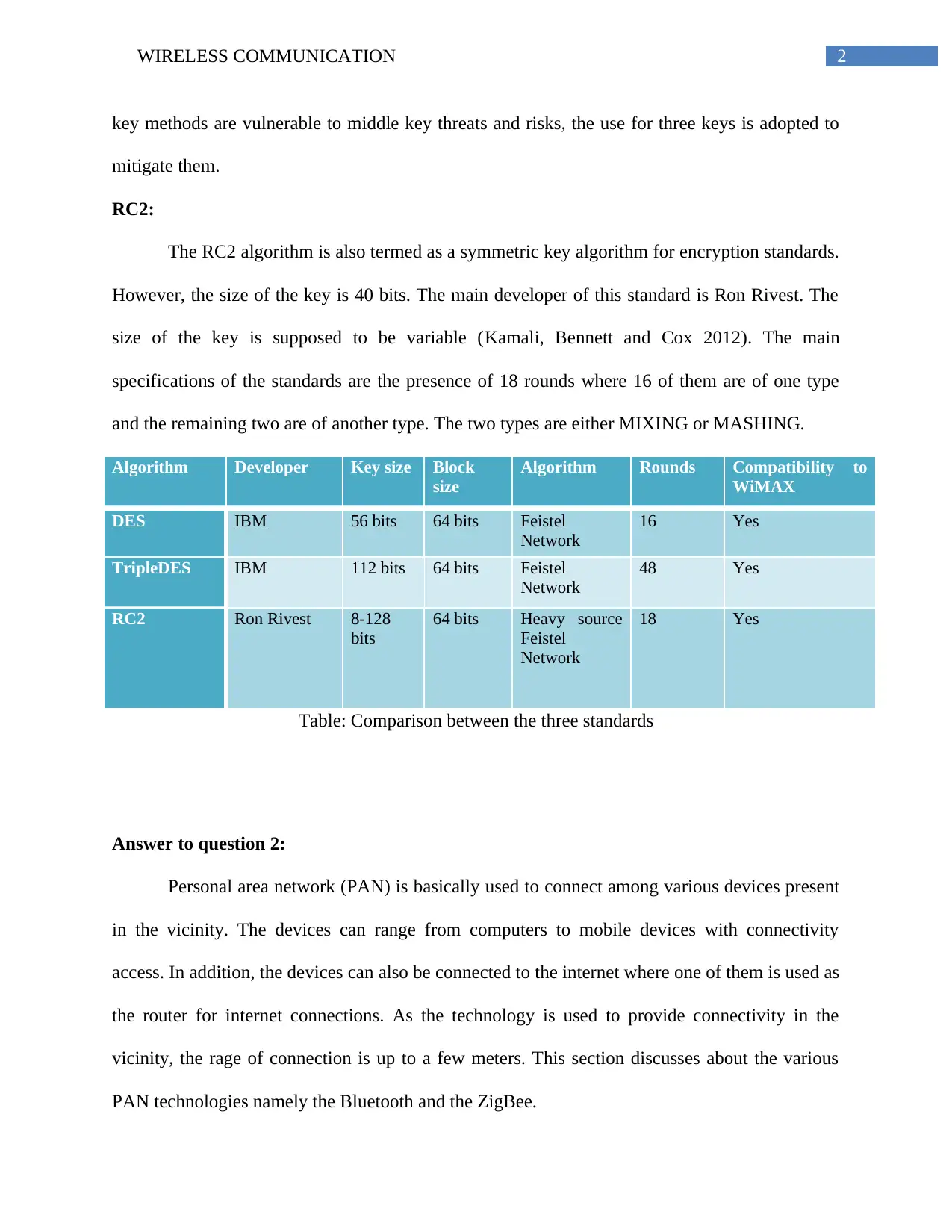
Algorithm Developer Key size Block
size
Algorithm Rounds Compatibility to
WiMAX
DES IBM 56 bits 64 bits Feistel
Network
16 Yes
TripleDES IBM 112 bits 64 bits Feistel
Network
48 Yes
RC2 Ron Rivest 8-128
bits
64 bits Heavy source
Feistel
Network
18 Yes
Table: Comparison between the three standards
Answer to question 2:
Personal area network (PAN) is basically used to connect among various devices present
in the vicinity. The devices can range from computers to mobile devices with connectivity
access. In addition, the devices can also be connected to the internet where one of them is used as
the router for internet connections. As the technology is used to provide connectivity in the
vicinity, the rage of connection is up to a few meters. This section discusses about the various
PAN technologies namely the Bluetooth and the ZigBee.
key methods are vulnerable to middle key threats and risks, the use for three keys is adopted to
mitigate them.
RC2:
The RC2 algorithm is also termed as a symmetric key algorithm for encryption standards.
However, the size of the key is 40 bits. The main developer of this standard is Ron Rivest. The
size of the key is supposed to be variable (Kamali, Bennett and Cox 2012). The main
specifications of the standards are the presence of 18 rounds where 16 of them are of one type
and the remaining two are of another type. The two types are either MIXING or MASHING.
Algorithm Developer Key size Block
size
Algorithm Rounds Compatibility to
WiMAX
DES IBM 56 bits 64 bits Feistel
Network
16 Yes
TripleDES IBM 112 bits 64 bits Feistel
Network
48 Yes
RC2 Ron Rivest 8-128
bits
64 bits Heavy source
Feistel
Network
18 Yes
Table: Comparison between the three standards
Answer to question 2:
Personal area network (PAN) is basically used to connect among various devices present
in the vicinity. The devices can range from computers to mobile devices with connectivity
access. In addition, the devices can also be connected to the internet where one of them is used as
the router for internet connections. As the technology is used to provide connectivity in the
vicinity, the rage of connection is up to a few meters. This section discusses about the various
PAN technologies namely the Bluetooth and the ZigBee.

3WIRELESS COMMUNICATION
Bluetooth:
The use of ultra high frequency (UHF) band is used to provide communication features
accepting a short range in connectivity. The range used for communication is 2.4 GHZ and the
modulation techniques used is the Gaussian Frequency shift keying (GFSK) and 8DPSK.
Due to the advancement in technologies, the presence of various risks is evident in
communicating with Bluetooth (Carpenter, Fowler & Adler, 2012). These are default
configuration of the device, loss or theft, person-in-the-middle, denial of service and service
mapping.
The default configuration is the presence of pre-installed configurations in the system
which is already applied by the manufacturers during its development. Due to the complex
nature of the configuration, people often neglect their reconfiguration. When the Bluetooth is in
ON mode, the BD_ADDR and clock will be noticed by the other devices present in the vicinity
of the user. This is the main problem where unethical attackers can get access to the systems to
steal information.
Loss or theft of information is another concern for risks in the systems. A Bluetooth
device always stores the access keys of the other devices in their memory. In case a device falls
into wrong hands, it can be used to get access to all the paired devices (Versichele et al. 2012).
This is a main concern and the security implications are to be addressed. This can also be used to
eavesdrop into the systems and steal information.
The person-in-the-middle attack is also another security challenge of Bluetooth. Due to
the advancements in technologies, attackers can get access to the private keys of devices in the
vicinity. Their device can then be used to get access to the other devices in vicinity. The main
mode of operation includes the mimicry of the attacker’s device to act like normal devices. When
Bluetooth:
The use of ultra high frequency (UHF) band is used to provide communication features
accepting a short range in connectivity. The range used for communication is 2.4 GHZ and the
modulation techniques used is the Gaussian Frequency shift keying (GFSK) and 8DPSK.
Due to the advancement in technologies, the presence of various risks is evident in
communicating with Bluetooth (Carpenter, Fowler & Adler, 2012). These are default
configuration of the device, loss or theft, person-in-the-middle, denial of service and service
mapping.
The default configuration is the presence of pre-installed configurations in the system
which is already applied by the manufacturers during its development. Due to the complex
nature of the configuration, people often neglect their reconfiguration. When the Bluetooth is in
ON mode, the BD_ADDR and clock will be noticed by the other devices present in the vicinity
of the user. This is the main problem where unethical attackers can get access to the systems to
steal information.
Loss or theft of information is another concern for risks in the systems. A Bluetooth
device always stores the access keys of the other devices in their memory. In case a device falls
into wrong hands, it can be used to get access to all the paired devices (Versichele et al. 2012).
This is a main concern and the security implications are to be addressed. This can also be used to
eavesdrop into the systems and steal information.
The person-in-the-middle attack is also another security challenge of Bluetooth. Due to
the advancements in technologies, attackers can get access to the private keys of devices in the
vicinity. Their device can then be used to get access to the other devices in vicinity. The main
mode of operation includes the mimicry of the attacker’s device to act like normal devices. When
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4WIRELESS COMMUNICATION
they try to establish connection to the other device, it is usually seemed to be a known device and
thus connection is established. This is also another reason for unethical access and
eavesdropping.
The denial of service (DOS) attacks, are another risks of Bluetooth technologies.
Although these attacks are not reported, it can be used to lock a user from accessing their
devices. This implies that the device will not be able to do the normal operations. In addition,
due to the presence of various home appliances in the system, the signal jamming is a common
method for use against such devices. Moreover, the attacker may also try to drain out the battery
of the device by sending constant requests to connect.
The last method of attacking includes the service mapping techniques. In general, when a
device has to connect, it sends out signals to connect to look for an open signal. This is mainly
done by the service discovery protocol (SDP) which is the most universal method used by all
devices (Versichele et al. 2012). This technique can be used to get the lists of devices in the
vicinity and connect accordingly. However, for this attack to work, the attacker needs to stay
close to the devices.
ZigBee:
ZigBee technologies have compliance to the IEEE 802.15.4 standards to facilitate small
range connectivity. The main applications of these technologies are in home automations.
The security implications of the ZigBee technologies are the absence of any security in
physical access. In case a device is stolen, it can be used to get access to the home network
(Rohitha et a., 2012). The technology mainly integrates the key in the physical hardware of the
device which is used to get access. Thus, this is a big problem for the ZigBee network.
they try to establish connection to the other device, it is usually seemed to be a known device and
thus connection is established. This is also another reason for unethical access and
eavesdropping.
The denial of service (DOS) attacks, are another risks of Bluetooth technologies.
Although these attacks are not reported, it can be used to lock a user from accessing their
devices. This implies that the device will not be able to do the normal operations. In addition,
due to the presence of various home appliances in the system, the signal jamming is a common
method for use against such devices. Moreover, the attacker may also try to drain out the battery
of the device by sending constant requests to connect.
The last method of attacking includes the service mapping techniques. In general, when a
device has to connect, it sends out signals to connect to look for an open signal. This is mainly
done by the service discovery protocol (SDP) which is the most universal method used by all
devices (Versichele et al. 2012). This technique can be used to get the lists of devices in the
vicinity and connect accordingly. However, for this attack to work, the attacker needs to stay
close to the devices.
ZigBee:
ZigBee technologies have compliance to the IEEE 802.15.4 standards to facilitate small
range connectivity. The main applications of these technologies are in home automations.
The security implications of the ZigBee technologies are the absence of any security in
physical access. In case a device is stolen, it can be used to get access to the home network
(Rohitha et a., 2012). The technology mainly integrates the key in the physical hardware of the
device which is used to get access. Thus, this is a big problem for the ZigBee network.

5WIRELESS COMMUNICATION
The key attacks are other security implications of the technology. The technology uses
two types of keys, the pre-shared keys and the over the air keys. Due to the lack of security
measures and intruder detection in the IEEE 802.15.4 standard, access is easily acquisitioned.
Answer to question 3:
1. Energy harvesting in wireless sensor networks:
The devices now-a-days need to utilize the various energy coefficients required for
implementing the internet of things concept. As the presence of vulnerabilities and threats are
increasing with each modernization trends, it is required for the devices to stay under working
conditions for a long time (Energy harvesting in wireless sensor networks: A comprehensive
review, 2017). The need for harvesting the surrounding energy is the main aim for an energy
harnesser. In case when a certain node of a particular device goes offline, the work to be done is
also removed. This creates a need for the devices to stay in working conditions for a long time.
In addition, the provide source tells about the various sources for the energy harvesting. These
sources are either natural or man-made. Moreover, the disadvantages of the systems are also
considered in the document. The main considerations along with their installation,
implementation of prototypes and compliance to the various standards or protocol are to be
considered before commencing with the development of the technology required (Energy
harvesting in wireless sensor networks: A comprehensive review, 2017). Furthermore, the
journal concludes by showing the various advantages of the applied systems.
2. Energy Harvesting Wireless Communications: A Review of Recent Advances
The different contributions in the area of wireless communications are talked about in the
journal. Along with this, the conceptual networks for implementing the connections as well as
the resources needed and their compliance with the existing standards and policies are also
The key attacks are other security implications of the technology. The technology uses
two types of keys, the pre-shared keys and the over the air keys. Due to the lack of security
measures and intruder detection in the IEEE 802.15.4 standard, access is easily acquisitioned.
Answer to question 3:
1. Energy harvesting in wireless sensor networks:
The devices now-a-days need to utilize the various energy coefficients required for
implementing the internet of things concept. As the presence of vulnerabilities and threats are
increasing with each modernization trends, it is required for the devices to stay under working
conditions for a long time (Energy harvesting in wireless sensor networks: A comprehensive
review, 2017). The need for harvesting the surrounding energy is the main aim for an energy
harnesser. In case when a certain node of a particular device goes offline, the work to be done is
also removed. This creates a need for the devices to stay in working conditions for a long time.
In addition, the provide source tells about the various sources for the energy harvesting. These
sources are either natural or man-made. Moreover, the disadvantages of the systems are also
considered in the document. The main considerations along with their installation,
implementation of prototypes and compliance to the various standards or protocol are to be
considered before commencing with the development of the technology required (Energy
harvesting in wireless sensor networks: A comprehensive review, 2017). Furthermore, the
journal concludes by showing the various advantages of the applied systems.
2. Energy Harvesting Wireless Communications: A Review of Recent Advances
The different contributions in the area of wireless communications are talked about in the
journal. Along with this, the conceptual networks for implementing the connections as well as
the resources needed and their compliance with the existing standards and policies are also

6WIRELESS COMMUNICATION
included in the journal. In addition, the theoretical calculations for the process are also
referenced in the provided journal (Energy Harvesting Wireless Communications: A Review of
Recent Advances, 2017). In addition, the provide source tells about the various sources for
energy harvesting which includes either natural or man-made sources. The main objectives of
these advancements are their applications in the areas of medical science, environmental and
safety related aspects. The summary of the theoretical recommendations are included in section 2
whereas the section 3 discusses the throughput optimization (Energy Harvesting Wireless
Communications: A Review of Recent Advances, 2017). Moreover, the various considerations to
be taken care of are referenced in the next sections in a sequential order.
Answer to question 4:
Slide 1
included in the journal. In addition, the theoretical calculations for the process are also
referenced in the provided journal (Energy Harvesting Wireless Communications: A Review of
Recent Advances, 2017). In addition, the provide source tells about the various sources for
energy harvesting which includes either natural or man-made sources. The main objectives of
these advancements are their applications in the areas of medical science, environmental and
safety related aspects. The summary of the theoretical recommendations are included in section 2
whereas the section 3 discusses the throughput optimization (Energy Harvesting Wireless
Communications: A Review of Recent Advances, 2017). Moreover, the various considerations to
be taken care of are referenced in the next sections in a sequential order.
Answer to question 4:
Slide 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS COMMUNICATION
Slide 2
Slide 3
Slide 2
Slide 3

8WIRELESS COMMUNICATION
Slide 4
Slide 4

9WIRELESS COMMUNICATION
Slide 5
Slide 6
Slide 5
Slide 6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10WIRELESS COMMUNICATION
Slide 7
Slide 8
Slide 7
Slide 8

11WIRELESS COMMUNICATION
Slide 9
Slide 9
12WIRELESS COMMUNICATION
Slide 10
Slide 11
Slide 10
Slide 11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13WIRELESS COMMUNICATION
Slide 12
Slide 12

14WIRELESS COMMUNICATION
Slide 13
Slide 13

15WIRELESS COMMUNICATION
References:
Carpenter, C., Fowler, M. & Adler, T., 2012. Generating route-specific origin-destination tables
using Bluetooth technology. Transportation Research Record: Journal of the
Transportation Research Board, (2308), pp.96-102.
Energy harvesting in wireless sensor networks: A comprehensive review. (2017). [ebook] Faisal
Karim Shaikh a,b,n , Sherali Zeadally c. Available at:
http://1712033_1136814880_2016Energyharvestinginwireless.pdf [Accessed 22 Sep.
2017].
Energy Harvesting Wireless Communications: A Review of Recent Advances. (2017). [ebook]
Available at: http://1712034_414472103_2015EnergyHarvestReview.pdf [Accessed 22
Sep. 2017].
Kamali, B., Bennett, R.A. & Cox, D.C., 2012. Understanding WiMAX: An IEEE-802.16
standard-based wireless technology. IEEE Potentials, 31(5), pp.23-27.
Li, S.H., Cheng, K.A., Lu, W.H. & Lin, T.C., 2012. Developing an active emergency medical
service system based on WiMAX technology. Journal of medical systems, 36(5),
pp.3177-3193.
More, S. & Mishra, D.K., 2012, November. 4G revolution: WiMAX technology. In Internet
(AH-ICI), 2012 Third Asian Himalayas International Conference on (pp. 1-4). IEEE.
Olexandr, L. & Sergiy, G., 2013, April. Slot allocation model and data burst scheduling in
downlink WiMAX technology. In Electronics and Nanotechnology (ELNANO), 2013
IEEE XXXIII International Scientific Conference (pp. 455-459). IEEE.
Rengaraju, P., Lung, C.H. & Srinivasan, A., 2012, August. Communication requirements and
analysis of distribution networks using WiMAX technology for smart grids. In Wireless
References:
Carpenter, C., Fowler, M. & Adler, T., 2012. Generating route-specific origin-destination tables
using Bluetooth technology. Transportation Research Record: Journal of the
Transportation Research Board, (2308), pp.96-102.
Energy harvesting in wireless sensor networks: A comprehensive review. (2017). [ebook] Faisal
Karim Shaikh a,b,n , Sherali Zeadally c. Available at:
http://1712033_1136814880_2016Energyharvestinginwireless.pdf [Accessed 22 Sep.
2017].
Energy Harvesting Wireless Communications: A Review of Recent Advances. (2017). [ebook]
Available at: http://1712034_414472103_2015EnergyHarvestReview.pdf [Accessed 22
Sep. 2017].
Kamali, B., Bennett, R.A. & Cox, D.C., 2012. Understanding WiMAX: An IEEE-802.16
standard-based wireless technology. IEEE Potentials, 31(5), pp.23-27.
Li, S.H., Cheng, K.A., Lu, W.H. & Lin, T.C., 2012. Developing an active emergency medical
service system based on WiMAX technology. Journal of medical systems, 36(5),
pp.3177-3193.
More, S. & Mishra, D.K., 2012, November. 4G revolution: WiMAX technology. In Internet
(AH-ICI), 2012 Third Asian Himalayas International Conference on (pp. 1-4). IEEE.
Olexandr, L. & Sergiy, G., 2013, April. Slot allocation model and data burst scheduling in
downlink WiMAX technology. In Electronics and Nanotechnology (ELNANO), 2013
IEEE XXXIII International Scientific Conference (pp. 455-459). IEEE.
Rengaraju, P., Lung, C.H. & Srinivasan, A., 2012, August. Communication requirements and
analysis of distribution networks using WiMAX technology for smart grids. In Wireless
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16WIRELESS COMMUNICATION
Communications and Mobile Computing Conference (IWCMC), 2012 8th
International (pp. 666-670). IEEE.
Rohitha, P., Kumar, P.R., Adinarayana, N., Venkat, T. & Narayana, R., 2012. Wireless
networking through ZigBee technology. International Journal of Advanced Research in
Computer Science and Software Engineering, 2(7).
Sergey, G. & Abed, A.H., 2013, February. Slot allocation model and data burst scheduling in
downlink WiMAX technology. In Experience of Designing and Application of CAD
Systems in Microelectronics (CADSM), 2013 12th International Conference on the (pp.
97-100). IEEE.
Talaviya, G., Ramteke, R. & Shete, A.K., 2013. Wireless fingerprint based college attendance
system using Zigbee technology. International Journal of Engineering and Advanced
Technology (IJEAT) ISSN, 2249, p.8958.
Versichele, M., Neutens, T., Delafontaine, M. & Van de Weghe, N., 2012. The use of Bluetooth
for analysing spatiotemporal dynamics of human movement at mass events: A case study
of the Ghent Festivities. Applied Geography, 32(2), pp.208-220.
Communications and Mobile Computing Conference (IWCMC), 2012 8th
International (pp. 666-670). IEEE.
Rohitha, P., Kumar, P.R., Adinarayana, N., Venkat, T. & Narayana, R., 2012. Wireless
networking through ZigBee technology. International Journal of Advanced Research in
Computer Science and Software Engineering, 2(7).
Sergey, G. & Abed, A.H., 2013, February. Slot allocation model and data burst scheduling in
downlink WiMAX technology. In Experience of Designing and Application of CAD
Systems in Microelectronics (CADSM), 2013 12th International Conference on the (pp.
97-100). IEEE.
Talaviya, G., Ramteke, R. & Shete, A.K., 2013. Wireless fingerprint based college attendance
system using Zigbee technology. International Journal of Engineering and Advanced
Technology (IJEAT) ISSN, 2249, p.8958.
Versichele, M., Neutens, T., Delafontaine, M. & Van de Weghe, N., 2012. The use of Bluetooth
for analysing spatiotemporal dynamics of human movement at mass events: A case study
of the Ghent Festivities. Applied Geography, 32(2), pp.208-220.
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





