IIBIT - ICTNWK607: Wireless Network Security Design & Implementation
VerifiedAdded on 2023/06/10
|15
|3912
|84
Report
AI Summary
This report presents a design and implementation plan for a secure wireless LAN, incorporating wireless security solutions with intrusion detection and prevention. The design utilizes a hierarchical model with core, distribution, and access layers. Key aspects include an RF plan and site survey, equipment procurement, authentication methods (802.1x EAP, mutual authentication), user password policies, and mobility issue mitigation. Encryption using WPA2 and network access control (NAC) are implemented for enhanced security. The report also addresses RF threats, such as rogue access points, and outlines a guest access policy. Desklib is a platform where students can find past papers and solved assignments.

Running head: ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
Advanced Diploma of Computer System Technology
Name of the Student
Name of the University
Author’s Note
Advanced Diploma of Computer System Technology
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
PART A
Introduction
The main purpose of this paper is to design and implement a wireless LAN which
would be including the wireless security solution along with intrusion detection and
prevention. The design would be consisting a wireless LAN security solution plan where the
user need to authenticate themselves with the organizations Active Directory Domain and
alsong with this the staffs of the organization would be provided with an managed device of
the organization whereas the students would also be encouraged to bring their own electronic
devices. The students would be allowed with a facility of getting connected to the wireless
LAN. The management of the organization would also allow the guest users to get connected
to the network whenever they visit the organization for attending meetings however for the
accessing the network they need not to have an active account Directory account of the
organization.
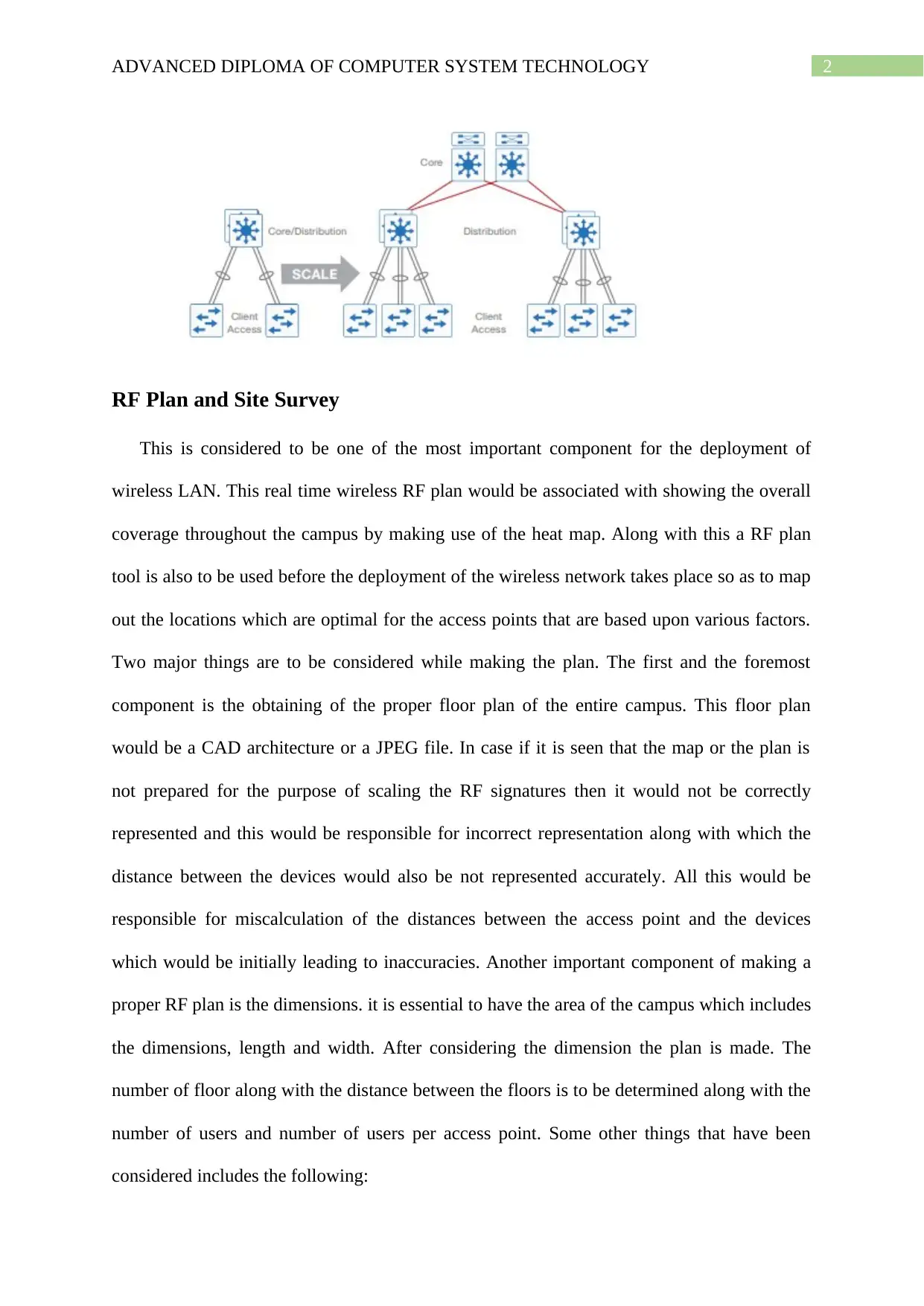
Topology and deployment Model
A hierarchical design model is used for the development of the wireless network and
the network is divided into core, distribution and access layer. The hierarchical design model
allows each of the layer in the network to perform specific function and simplifies the design.
It can also be used for scaling the network and increasing the consistency of the network. The
management of the hierarchical design model is simple and the faults in the network can
easily isolated and the resiliency can be improved.
The only disadvantage of this model is that the flexibility of the design is poor and if
there is a need for expansion of the network many of the network device needs to be
reconfigured.
PART A
Introduction
The main purpose of this paper is to design and implement a wireless LAN which
would be including the wireless security solution along with intrusion detection and
prevention. The design would be consisting a wireless LAN security solution plan where the
user need to authenticate themselves with the organizations Active Directory Domain and
alsong with this the staffs of the organization would be provided with an managed device of
the organization whereas the students would also be encouraged to bring their own electronic
devices. The students would be allowed with a facility of getting connected to the wireless
LAN. The management of the organization would also allow the guest users to get connected
to the network whenever they visit the organization for attending meetings however for the
accessing the network they need not to have an active account Directory account of the
organization.
Topology and deployment Model
A hierarchical design model is used for the development of the wireless network and
the network is divided into core, distribution and access layer. The hierarchical design model
allows each of the layer in the network to perform specific function and simplifies the design.
It can also be used for scaling the network and increasing the consistency of the network. The
management of the hierarchical design model is simple and the faults in the network can
easily isolated and the resiliency can be improved.
The only disadvantage of this model is that the flexibility of the design is poor and if
there is a need for expansion of the network many of the network device needs to be
reconfigured.
2ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
RF Plan and Site Survey
This is considered to be one of the most important component for the deployment of
wireless LAN. This real time wireless RF plan would be associated with showing the overall
coverage throughout the campus by making use of the heat map. Along with this a RF plan
tool is also to be used before the deployment of the wireless network takes place so as to map
out the locations which are optimal for the access points that are based upon various factors.
Two major things are to be considered while making the plan. The first and the foremost
component is the obtaining of the proper floor plan of the entire campus. This floor plan
would be a CAD architecture or a JPEG file. In case if it is seen that the map or the plan is
not prepared for the purpose of scaling the RF signatures then it would not be correctly
represented and this would be responsible for incorrect representation along with which the
distance between the devices would also be not represented accurately. All this would be
responsible for miscalculation of the distances between the access point and the devices
which would be initially leading to inaccuracies. Another important component of making a
proper RF plan is the dimensions. it is essential to have the area of the campus which includes
the dimensions, length and width. After considering the dimension the plan is made. The
number of floor along with the distance between the floors is to be determined along with the
number of users and number of users per access point. Some other things that have been
considered includes the following:
RF Plan and Site Survey
This is considered to be one of the most important component for the deployment of
wireless LAN. This real time wireless RF plan would be associated with showing the overall
coverage throughout the campus by making use of the heat map. Along with this a RF plan
tool is also to be used before the deployment of the wireless network takes place so as to map
out the locations which are optimal for the access points that are based upon various factors.
Two major things are to be considered while making the plan. The first and the foremost
component is the obtaining of the proper floor plan of the entire campus. This floor plan
would be a CAD architecture or a JPEG file. In case if it is seen that the map or the plan is
not prepared for the purpose of scaling the RF signatures then it would not be correctly
represented and this would be responsible for incorrect representation along with which the
distance between the devices would also be not represented accurately. All this would be
responsible for miscalculation of the distances between the access point and the devices
which would be initially leading to inaccuracies. Another important component of making a
proper RF plan is the dimensions. it is essential to have the area of the campus which includes
the dimensions, length and width. After considering the dimension the plan is made. The
number of floor along with the distance between the floors is to be determined along with the
number of users and number of users per access point. Some other things that have been
considered includes the following:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
Radio type(s)
Overlap Factor
The Desired data rates for the access points
Desired monitoring rates for AMs
Areas of your building(s) where it is necessary to have coverage
Areas of your building(s) where there is no need of deploying an Access point or
cannot be deployed
Areas of your building(s) where there is a need of deploying 802.1x Hotspot (Zone)
Any area where you want to deploy a fixed AP.
Procurement of Equipment
With the evaluation of the wireless network technology there has been a proliferation
in the offerings made by the manufacturer in terms of the equipment’s as well the tools
related to management. Besides this it is also very important to understand the fact that
different vendors are associated with providing different type of solutions which are having
differences with respect to their technical points. Along with this it is also essential to
consider the architecture provided by the vendor along with considering the hardware,
software and the management tools and how this components meet the requirements and
budget of the organization so it is recommended that the offerings from multiple vendors is to
be sought and combined with the quotations made by the various wireless system integrators.
All this are to be sought so as to provide the results which are the best in accordance to the
needs of the organization.
Radio type(s)
Overlap Factor
The Desired data rates for the access points
Desired monitoring rates for AMs
Areas of your building(s) where it is necessary to have coverage
Areas of your building(s) where there is no need of deploying an Access point or
cannot be deployed
Areas of your building(s) where there is a need of deploying 802.1x Hotspot (Zone)
Any area where you want to deploy a fixed AP.
Procurement of Equipment
With the evaluation of the wireless network technology there has been a proliferation
in the offerings made by the manufacturer in terms of the equipment’s as well the tools
related to management. Besides this it is also very important to understand the fact that
different vendors are associated with providing different type of solutions which are having
differences with respect to their technical points. Along with this it is also essential to
consider the architecture provided by the vendor along with considering the hardware,
software and the management tools and how this components meet the requirements and
budget of the organization so it is recommended that the offerings from multiple vendors is to
be sought and combined with the quotations made by the various wireless system integrators.
All this are to be sought so as to provide the results which are the best in accordance to the
needs of the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
Authentication
a. 802.1x EAP
The 802.1x is used for the purpose of funnelling the wireless traffic onto the LANs which
are virtual in nature which would be associated with reflecting the user or the group
permissions. This is also be helpful in the process of knowing the process involved in the
establishment of the critical link between the authentication and the authorization. In this the
packets would be provided with a tag whenever they enter the LA N in order to make sure
that the upstream devices become capable of applying the security or the QoS filters. Besides
this access points might also be capable of tagging the wireless traffic so as to make sure that
this traffic remains totally separated from the other network traffic whenever it moves
through the network. The 802.1x would be requiring a tree party authentication which
involves a supplicant, an authenticator and an authenticating server.
b. Mutual Authentication
Mutual Authentication or the two way authentication would be used where both the
entities who would present in the communication link would be associated with
authenticating each other, which means that the client would be authenticating the server and
the vice versa. By adaptation of this the users of the network would be assured about the fact
that they are allowing the legitimate entities to use the network and the server would also be
certain about the fact that the would-be users are making attempt to join the network for
legitimate purpose.
c. Client Settings
Access to the LAN is not provided by the 802.1x is not provided unless and until the
client is authenticated. The main components that are required to get authenticated in the
802.1x includes the EAP-cable client, 802.1x capable access point, and lastly an EAP Cable
Authentication
a. 802.1x EAP
The 802.1x is used for the purpose of funnelling the wireless traffic onto the LANs which
are virtual in nature which would be associated with reflecting the user or the group
permissions. This is also be helpful in the process of knowing the process involved in the
establishment of the critical link between the authentication and the authorization. In this the
packets would be provided with a tag whenever they enter the LA N in order to make sure
that the upstream devices become capable of applying the security or the QoS filters. Besides
this access points might also be capable of tagging the wireless traffic so as to make sure that
this traffic remains totally separated from the other network traffic whenever it moves
through the network. The 802.1x would be requiring a tree party authentication which
involves a supplicant, an authenticator and an authenticating server.
b. Mutual Authentication
Mutual Authentication or the two way authentication would be used where both the
entities who would present in the communication link would be associated with
authenticating each other, which means that the client would be authenticating the server and
the vice versa. By adaptation of this the users of the network would be assured about the fact
that they are allowing the legitimate entities to use the network and the server would also be
certain about the fact that the would-be users are making attempt to join the network for
legitimate purpose.
c. Client Settings
Access to the LAN is not provided by the 802.1x is not provided unless and until the
client is authenticated. The main components that are required to get authenticated in the
802.1x includes the EAP-cable client, 802.1x capable access point, and lastly an EAP Cable

5ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
Radius Server.Cisco LEAP 802.1x is to be used here which is a type of WLAN which is
supported by the Wi-Fi WPA and WPA2. This also supports mutual authentication between
the client and the RADIUS server by making use of the logon password. This also provides
dynamic per-user, per-session encryption keys which has the capability of fast securing.
d. User Password Policy
A user password policy is to be implemented which is a set of rule associated with the
enhancement of the security. This policy would be associated with encouraging the users to
make use of strong passwords along with using them in a proper way. Certain components
are included in the password policy which includes the following:
Length of the password and formation: A minimum password length is to be used.
The longer passwords are more secure.
Password duration: The passwords should be changed periodically.
Password blacklist: This would be including the list of passwords which would be
always blocked from usage.
e. Mobility Issues
The mobility issues can occur due to interference and uncontrollable overlapping of
the heterogeneous network. A handoff process is used by the mobile device when the device
goes beyond the coverage area of the access point and some latency is faced due to this and it
can be mitigated with the implementation of the location management. The handoff
mechanism should be configured such that the best access point is selected and the user can
enjoy continuous service. The mobility issues can also occur due to routing inefficiency and
quality of service. The restriction of the bandwidth and low level of reliability can hinder the
performance and the application of optimizing the protocol parameter can also reduce the
performance of the network. There are different mobility management model that can be used
Radius Server.Cisco LEAP 802.1x is to be used here which is a type of WLAN which is
supported by the Wi-Fi WPA and WPA2. This also supports mutual authentication between
the client and the RADIUS server by making use of the logon password. This also provides
dynamic per-user, per-session encryption keys which has the capability of fast securing.
d. User Password Policy
A user password policy is to be implemented which is a set of rule associated with the
enhancement of the security. This policy would be associated with encouraging the users to
make use of strong passwords along with using them in a proper way. Certain components
are included in the password policy which includes the following:
Length of the password and formation: A minimum password length is to be used.
The longer passwords are more secure.
Password duration: The passwords should be changed periodically.
Password blacklist: This would be including the list of passwords which would be
always blocked from usage.
e. Mobility Issues
The mobility issues can occur due to interference and uncontrollable overlapping of
the heterogeneous network. A handoff process is used by the mobile device when the device
goes beyond the coverage area of the access point and some latency is faced due to this and it
can be mitigated with the implementation of the location management. The handoff
mechanism should be configured such that the best access point is selected and the user can
enjoy continuous service. The mobility issues can also occur due to routing inefficiency and
quality of service. The restriction of the bandwidth and low level of reliability can hinder the
performance and the application of optimizing the protocol parameter can also reduce the
performance of the network. There are different mobility management model that can be used
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
for addressing the issue and connect the mobile agent with the wireless access point for
creating a cross layer coordination.
Encryption
The WPA2 encryption technique is to be used which is the replacement of the security
method for the WPA for the wireless network which would be associated with providing a
stronger data protection and network access control. This is associated with providing the
user with a high level of assurance which makes sure that only the authorized users are
capable of accessing he wireless network, this WPA2 is also associated with providing
government grade security by implication of the NIST or the National Institution of
Standards and Technology FIPS 140-2 compliant advanced encryption standard (AES)
encryption algorithm and 802.1X-based authentication
Authorization
NAC or the Network Access Control is the access control technique which is to be
implemented in order to be sure about the fact that who or what has the authorized permission
to get access to the network. This is associated with including the user as well as the devices.
The NAC woud be associated with the intercepting the requests to the connection which are
then authenticated against a designated identity and access management system. This in turn
would be associated with accepting or denying the access which is generally based upon the
parameters which are predetermined and according the policies that are programmed into the
system. The NAC would be associated with Authorization, authenticating and accounting the
network connections. Confidentiality and the containment of the intellectual property would
be done by enforcement of the policies. Besides this it would also be helping in the
management of the identity and the assets. The NAC would be associated with providing the
guests with an ability to get connected to the network associated with restricted access. NAC
for addressing the issue and connect the mobile agent with the wireless access point for
creating a cross layer coordination.
Encryption
The WPA2 encryption technique is to be used which is the replacement of the security
method for the WPA for the wireless network which would be associated with providing a
stronger data protection and network access control. This is associated with providing the
user with a high level of assurance which makes sure that only the authorized users are
capable of accessing he wireless network, this WPA2 is also associated with providing
government grade security by implication of the NIST or the National Institution of
Standards and Technology FIPS 140-2 compliant advanced encryption standard (AES)
encryption algorithm and 802.1X-based authentication
Authorization
NAC or the Network Access Control is the access control technique which is to be
implemented in order to be sure about the fact that who or what has the authorized permission
to get access to the network. This is associated with including the user as well as the devices.
The NAC woud be associated with the intercepting the requests to the connection which are
then authenticated against a designated identity and access management system. This in turn
would be associated with accepting or denying the access which is generally based upon the
parameters which are predetermined and according the policies that are programmed into the
system. The NAC would be associated with Authorization, authenticating and accounting the
network connections. Confidentiality and the containment of the intellectual property would
be done by enforcement of the policies. Besides this it would also be helping in the
management of the identity and the assets. The NAC would be associated with providing the
guests with an ability to get connected to the network associated with restricted access. NAC
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
continuously monitors the behaviour of the devices connected to the network along with the
collection of logs, flows and packets as well.
RF Threats
There exists various kind of threats and this mainly includes the following:
Rough Access Points: This is considered to be a Wireless access point that is installed
in a secure network without an explicit authorization from the local network
administrator weather it is done by the staffs or by any malicious attacker. The
attacker is associated with the installation of an access point which are capable of
running various type of vulnerability scanners which attacks the network remotely.
The wireless intrusion prevention system can be used which is associated with
monitoring the radio spectrum to detect the presence of any kind of unauthorized
access points which would be initially followed by taking of countermeasures
automatically.
Active attack is another major risk to the network where it is seen that the hacker is
making attempts to make certain amount of changes in the data present in the target
network or is associated with en routing of the data to the target.
Guest Access Policy
a. Identification of guest authentication methods
There are different methods that can be used for the authentication of the guest and
connect them with the wireless network for enabling them access the different service
provided by the network. The SSID for the wireless network should have a unique name and
it should be connected using a different vlan. The open authentication can be used with the
application of WEP for authenticating with the wireless network. The authenticated key
continuously monitors the behaviour of the devices connected to the network along with the
collection of logs, flows and packets as well.
RF Threats
There exists various kind of threats and this mainly includes the following:
Rough Access Points: This is considered to be a Wireless access point that is installed
in a secure network without an explicit authorization from the local network
administrator weather it is done by the staffs or by any malicious attacker. The
attacker is associated with the installation of an access point which are capable of
running various type of vulnerability scanners which attacks the network remotely.
The wireless intrusion prevention system can be used which is associated with
monitoring the radio spectrum to detect the presence of any kind of unauthorized
access points which would be initially followed by taking of countermeasures
automatically.
Active attack is another major risk to the network where it is seen that the hacker is
making attempts to make certain amount of changes in the data present in the target
network or is associated with en routing of the data to the target.
Guest Access Policy
a. Identification of guest authentication methods
There are different methods that can be used for the authentication of the guest and
connect them with the wireless network for enabling them access the different service
provided by the network. The SSID for the wireless network should have a unique name and
it should be connected using a different vlan. The open authentication can be used with the
application of WEP for authenticating with the wireless network. The authenticated key

8ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
management is also necessary for increasing the security of the guest network where the user
provides the pre shared key for connecting with the access point and the TKIP and the WEP
algorithm is used for the protection of the communication between the access point and the
client device.
b. Identification of protocols used for guest users
It is important to use an identity management for recording all the details of the guest
connected with the network. The guest can be classified according to the permission provided
to them to access the internal components of the network. The routing policies should be
analysed and the lightweight access point protocol is used for creating a centralized warless
architecture and it should be used for controlling the encapsulation format of data for the
cisco unified wireless network. For the configuration of the network the VLAN are
configured in the switch and it also used for the management of the interfaces and the
network services connected with the VLAN. The switch port mode trunk protocol is also
used for allowing the VLAN for communicating with the other vlan. Different guest access
accounts can be created in the firewall for the management of the network traffic and
blocking the guest to gain the access of the sensitive sites that can cause a negative impact on
the network.
c. Security restrictions applied in the network
The application of network security access control helps in controlling the flow of the
data traffic in the network and secures the network from the external agents to access the
internal resources of the network. The routers should be configured with access control list
such that the guest users can be blocked to access the internal server of the network and
security is maintained. A DMZ zone should be created for the installation of the server and
the physical access of the server to the user should be restricted such that the servers does not
management is also necessary for increasing the security of the guest network where the user
provides the pre shared key for connecting with the access point and the TKIP and the WEP
algorithm is used for the protection of the communication between the access point and the
client device.
b. Identification of protocols used for guest users
It is important to use an identity management for recording all the details of the guest
connected with the network. The guest can be classified according to the permission provided
to them to access the internal components of the network. The routing policies should be
analysed and the lightweight access point protocol is used for creating a centralized warless
architecture and it should be used for controlling the encapsulation format of data for the
cisco unified wireless network. For the configuration of the network the VLAN are
configured in the switch and it also used for the management of the interfaces and the
network services connected with the VLAN. The switch port mode trunk protocol is also
used for allowing the VLAN for communicating with the other vlan. Different guest access
accounts can be created in the firewall for the management of the network traffic and
blocking the guest to gain the access of the sensitive sites that can cause a negative impact on
the network.
c. Security restrictions applied in the network
The application of network security access control helps in controlling the flow of the
data traffic in the network and secures the network from the external agents to access the
internal resources of the network. The routers should be configured with access control list
such that the guest users can be blocked to access the internal server of the network and
security is maintained. A DMZ zone should be created for the installation of the server and
the physical access of the server to the user should be restricted such that the servers does not
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
gets infected with spyware or ransomware. The servers can be used by the attacker for
causing denial of service and making the resources unavailable to the intended users
connected in the network.
BYOD policy
BYOD or the Bring Your Own Device is considered to be a mainstay in any of the
organization. This would be associated with allowing the users to get connected to the
network by having their own devices which would be having the potential to wreak the
havocs. This is mainly due to the reason that it is difficult to control it by the IT department.
Along with having the BYOD it is very important to make sure that the employees are honest
about the devices that they are using for the purpose of getting connected to the network,
what applications are on those devices, and what security tools are used to protect them. In is
necessary to integrate the BYOD policy security policy and the acceptable use policy as well.
The structuring of the policies should be done so as to prevent the IT from having
unmanageable number of different type of device.
Conclusion
The entire network would be developed according the requirements of the
organization where the user need to authenticate themselves with the organizations Active
Directory Domain and along with this the staffs of the organization would be provided with
an managed device of the organization whereas the students would also be encouraged to
bring their own electronic devices. The students would be allowed with a facility of getting
connected to the wireless LAN. For doing so the risk are to the identified and the prevention
techniques as well. Encryption is also to be used in the network along with authorization so
as to secure the network. Other policies by user password policy is to be developed along
with the guest user policy. The appropriate encryption and authorization technique has been
gets infected with spyware or ransomware. The servers can be used by the attacker for
causing denial of service and making the resources unavailable to the intended users
connected in the network.
BYOD policy
BYOD or the Bring Your Own Device is considered to be a mainstay in any of the
organization. This would be associated with allowing the users to get connected to the
network by having their own devices which would be having the potential to wreak the
havocs. This is mainly due to the reason that it is difficult to control it by the IT department.
Along with having the BYOD it is very important to make sure that the employees are honest
about the devices that they are using for the purpose of getting connected to the network,
what applications are on those devices, and what security tools are used to protect them. In is
necessary to integrate the BYOD policy security policy and the acceptable use policy as well.
The structuring of the policies should be done so as to prevent the IT from having
unmanageable number of different type of device.
Conclusion
The entire network would be developed according the requirements of the
organization where the user need to authenticate themselves with the organizations Active
Directory Domain and along with this the staffs of the organization would be provided with
an managed device of the organization whereas the students would also be encouraged to
bring their own electronic devices. The students would be allowed with a facility of getting
connected to the wireless LAN. For doing so the risk are to the identified and the prevention
techniques as well. Encryption is also to be used in the network along with authorization so
as to secure the network. Other policies by user password policy is to be developed along
with the guest user policy. The appropriate encryption and authorization technique has been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
selected along with this. The BYOD or the Bring Your Own Device policy is also developed
so as to provide a secure access to the guests.
selected along with this. The BYOD or the Bring Your Own Device policy is also developed
so as to provide a secure access to the guests.
11ADVANCED DIPLOMA OF COMPUTER SYSTEM TECHNOLOGY
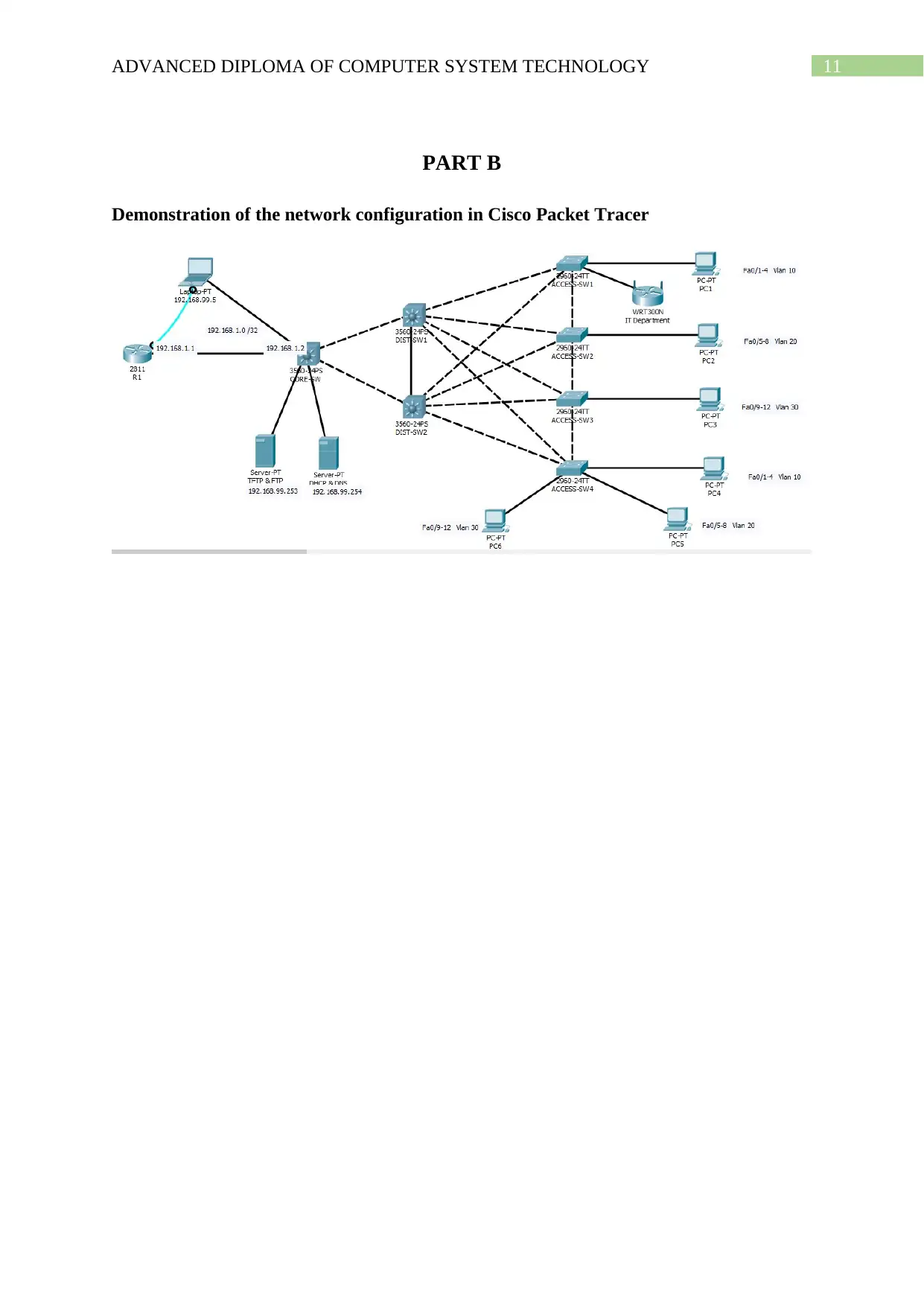
PART B
Demonstration of the network configuration in Cisco Packet Tracer
PART B
Demonstration of the network configuration in Cisco Packet Tracer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





