Wireless Network Protocols and Software-Defined Networks: An Overview
VerifiedAdded on 2024/07/24
|13
|2631
|329
AI Summary
This paper explores different types of antennas, their merits and demerits, and the security challenges faced by three wireless network protocols: WiGig, Bluetooth, and Apple iBeacon. It also delves into the concept of software-defined wireless networks, highlighting their advantages, disadvantages, and role in the evolution of mobile network services. The paper concludes by discussing the importance of SDN, network function virtualization, and mobile edge computing in shaping the future of 5G networks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
1 | P a g e
Assignment 1
Assignment 1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2 | P a g e
Table of Contents
1- Different types of antennas and their merits and demerits.......................................................4
2- Three different wireless network protocols. What security challenges they are facing?..........6
3- Software-defined wireless network.........................................................................................10
References....................................................................................................................................... 13
Table of Contents
1- Different types of antennas and their merits and demerits.......................................................4
2- Three different wireless network protocols. What security challenges they are facing?..........6
3- Software-defined wireless network.........................................................................................10
References....................................................................................................................................... 13

3 | P a g e
List of figures
Figure 1: Diagram of the Yagi antenna..................................................................................................4
Figure 2: Diagram of Horn antenna....................................................................................................... 4
Figure 3: Diagram of cellular antenna....................................................................................................5
Figure 4: Diagram of WiGig.................................................................................................................... 6
Figure 5: Diagram of Bluetooth.............................................................................................................7
Figure 6: Diagram of iBeacon.................................................................................................................8
Figure 7: SDN reference architecture.................................................................................................. 10
Figure 8: Simple SDN architecture.......................................................................................................11
Figure 9: Arrangement of current table access in SD switch...............................................................11
List of figures
Figure 1: Diagram of the Yagi antenna..................................................................................................4
Figure 2: Diagram of Horn antenna....................................................................................................... 4
Figure 3: Diagram of cellular antenna....................................................................................................5
Figure 4: Diagram of WiGig.................................................................................................................... 6
Figure 5: Diagram of Bluetooth.............................................................................................................7
Figure 6: Diagram of iBeacon.................................................................................................................8
Figure 7: SDN reference architecture.................................................................................................. 10
Figure 8: Simple SDN architecture.......................................................................................................11
Figure 9: Arrangement of current table access in SD switch...............................................................11
4 | P a g e
1- Different types of antennas and their merits and demerits.
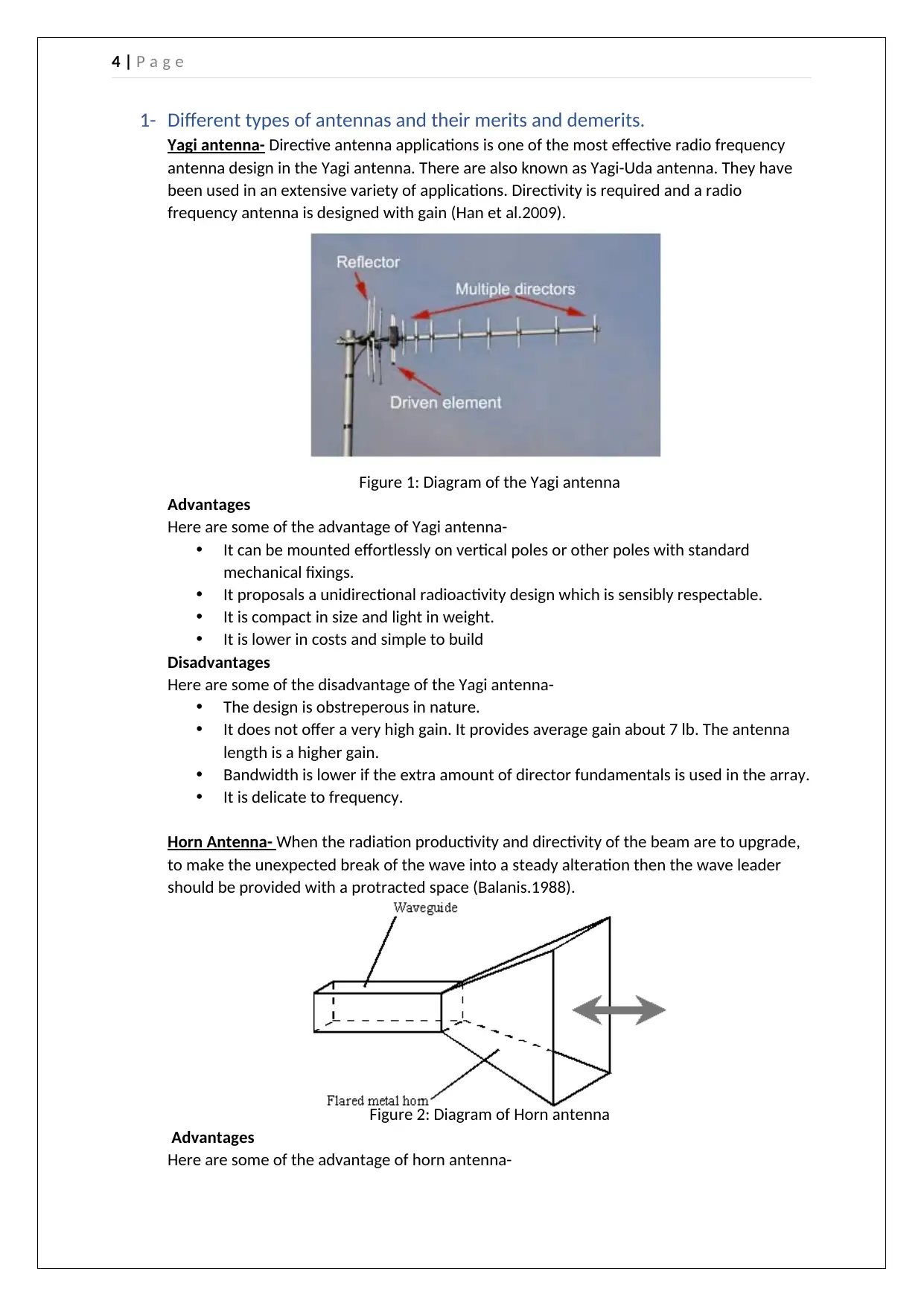
Yagi antenna- Directive antenna applications is one of the most effective radio frequency
antenna design in the Yagi antenna. There are also known as Yagi-Uda antenna. They have
been used in an extensive variety of applications. Directivity is required and a radio
frequency antenna is designed with gain (Han et al.2009).
Figure 1: Diagram of the Yagi antenna
Advantages
Here are some of the advantage of Yagi antenna-
It can be mounted effortlessly on vertical poles or other poles with standard
mechanical fixings.
It proposals a unidirectional radioactivity design which is sensibly respectable.
It is compact in size and light in weight.
It is lower in costs and simple to build
Disadvantages
Here are some of the disadvantage of the Yagi antenna-
The design is obstreperous in nature.
It does not offer a very high gain. It provides average gain about 7 lb. The antenna
length is a higher gain.
Bandwidth is lower if the extra amount of director fundamentals is used in the array.
It is delicate to frequency.
Horn Antenna- When the radiation productivity and directivity of the beam are to upgrade,
to make the unexpected break of the wave into a steady alteration then the wave leader
should be provided with a protracted space (Balanis.1988).
Figure 2: Diagram of Horn antenna
Advantages
Here are some of the advantage of horn antenna-
1- Different types of antennas and their merits and demerits.
Yagi antenna- Directive antenna applications is one of the most effective radio frequency
antenna design in the Yagi antenna. There are also known as Yagi-Uda antenna. They have
been used in an extensive variety of applications. Directivity is required and a radio
frequency antenna is designed with gain (Han et al.2009).
Figure 1: Diagram of the Yagi antenna
Advantages
Here are some of the advantage of Yagi antenna-
It can be mounted effortlessly on vertical poles or other poles with standard
mechanical fixings.
It proposals a unidirectional radioactivity design which is sensibly respectable.
It is compact in size and light in weight.
It is lower in costs and simple to build
Disadvantages
Here are some of the disadvantage of the Yagi antenna-
The design is obstreperous in nature.
It does not offer a very high gain. It provides average gain about 7 lb. The antenna
length is a higher gain.
Bandwidth is lower if the extra amount of director fundamentals is used in the array.
It is delicate to frequency.
Horn Antenna- When the radiation productivity and directivity of the beam are to upgrade,
to make the unexpected break of the wave into a steady alteration then the wave leader
should be provided with a protracted space (Balanis.1988).
Figure 2: Diagram of Horn antenna
Advantages
Here are some of the advantage of horn antenna-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
5 | P a g e
Standing waves are avoided
Greater directivity
Impedance matching is good
Small minor lobes are formed
Narrower beam width
Disadvantages
Here are some of the advantage of horn antenna-
Length of the flare should not be easy very small and flare angle
Designing of decides the directivity, flare angle.
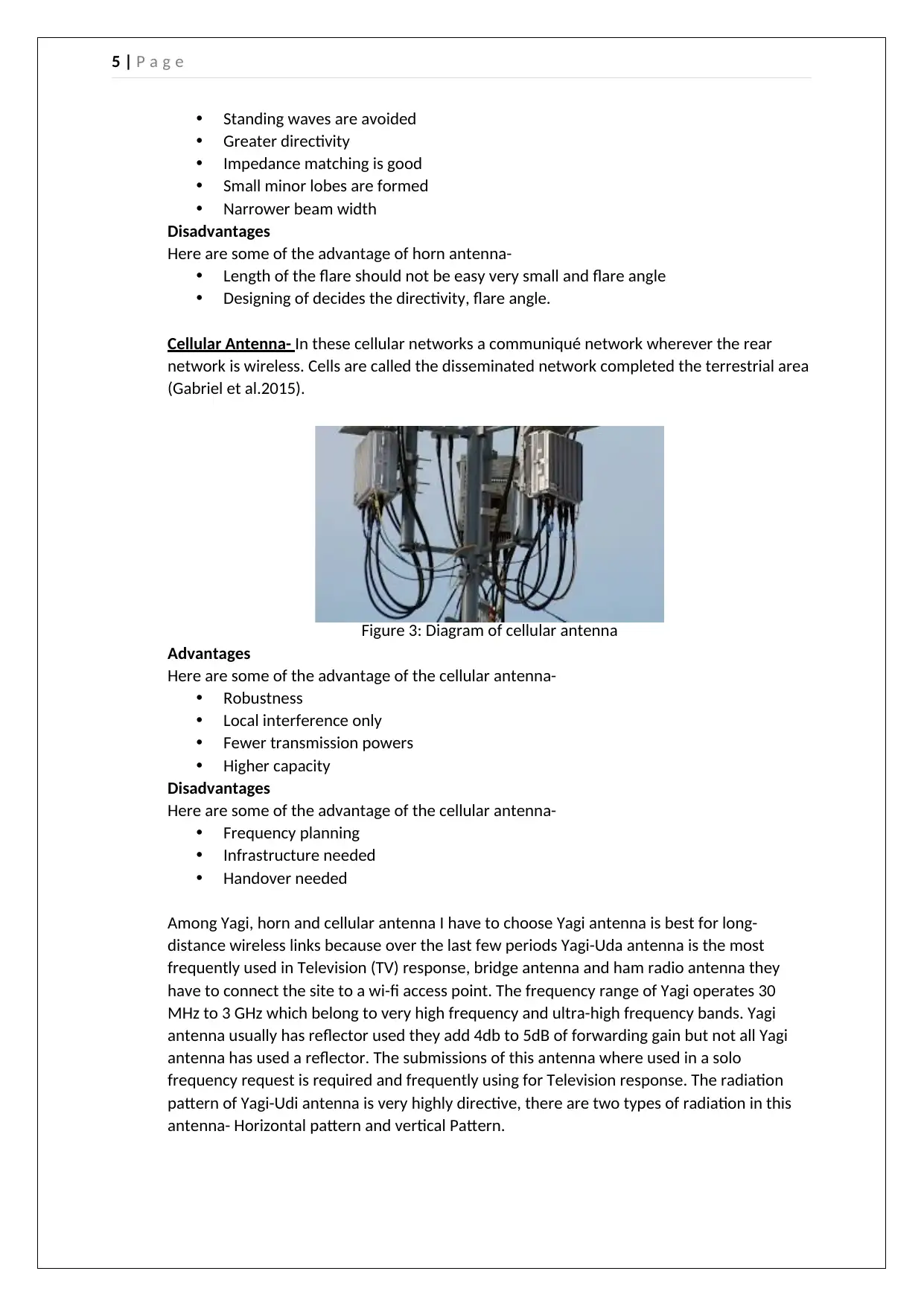
Cellular Antenna- In these cellular networks a communiqué network wherever the rear
network is wireless. Cells are called the disseminated network completed the terrestrial area
(Gabriel et al.2015).
Figure 3: Diagram of cellular antenna
Advantages
Here are some of the advantage of the cellular antenna-
Robustness
Local interference only
Fewer transmission powers
Higher capacity
Disadvantages
Here are some of the advantage of the cellular antenna-
Frequency planning
Infrastructure needed
Handover needed
Among Yagi, horn and cellular antenna I have to choose Yagi antenna is best for long-
distance wireless links because over the last few periods Yagi-Uda antenna is the most
frequently used in Television (TV) response, bridge antenna and ham radio antenna they
have to connect the site to a wi-fi access point. The frequency range of Yagi operates 30
MHz to 3 GHz which belong to very high frequency and ultra-high frequency bands. Yagi
antenna usually has reflector used they add 4db to 5dB of forwarding gain but not all Yagi
antenna has used a reflector. The submissions of this antenna where used in a solo
frequency request is required and frequently using for Television response. The radiation
pattern of Yagi-Udi antenna is very highly directive, there are two types of radiation in this
antenna- Horizontal pattern and vertical Pattern.
Standing waves are avoided
Greater directivity
Impedance matching is good
Small minor lobes are formed
Narrower beam width
Disadvantages
Here are some of the advantage of horn antenna-
Length of the flare should not be easy very small and flare angle
Designing of decides the directivity, flare angle.
Cellular Antenna- In these cellular networks a communiqué network wherever the rear
network is wireless. Cells are called the disseminated network completed the terrestrial area
(Gabriel et al.2015).
Figure 3: Diagram of cellular antenna
Advantages
Here are some of the advantage of the cellular antenna-
Robustness
Local interference only
Fewer transmission powers
Higher capacity
Disadvantages
Here are some of the advantage of the cellular antenna-
Frequency planning
Infrastructure needed
Handover needed
Among Yagi, horn and cellular antenna I have to choose Yagi antenna is best for long-
distance wireless links because over the last few periods Yagi-Uda antenna is the most
frequently used in Television (TV) response, bridge antenna and ham radio antenna they
have to connect the site to a wi-fi access point. The frequency range of Yagi operates 30
MHz to 3 GHz which belong to very high frequency and ultra-high frequency bands. Yagi
antenna usually has reflector used they add 4db to 5dB of forwarding gain but not all Yagi
antenna has used a reflector. The submissions of this antenna where used in a solo
frequency request is required and frequently using for Television response. The radiation
pattern of Yagi-Udi antenna is very highly directive, there are two types of radiation in this
antenna- Horizontal pattern and vertical Pattern.

6 | P a g e
2- Three different wireless network protocols. What security challenges they are
facing?
1. WiGig- High-Speed Wireless- They uses 60GHz radio band and 10 Gbps speed is the
latest Wi-Fir protocol. 802.11ad is the high-speed wireless technology in technical
spec. Due to this high-speed wireless technology, they use 40 GHz radio band and it
connects up to 1GBps. In multi-stored business houses, it is relatively tough to
monitor each of the corners. It will make to easy the connect the thread due to the
installing of high definition video cameras with this high speed of wi-fi systems
(Tagasovska et al.2014).
Figure 4: Diagram of WiGig
Advantage
There are some following benefits of WiGig –
Very low latency time (~ 10 microseconds)
Instant wireless synchronization
A wired connection can be eliminated
Automatically switching between bands
No interference with other low brand frequency
Disadvantage
There are some following drawbacks of WiGig –
No readily built into common devices
Due to the frequency of 60 GHz, the range is small, but this might be
effortlessly secure with a cheap Wi-Fi range extender device.
They are facing problems in large scale like campus-
Security- Spread over the network which is additional delicate data is
refined so that they are placing wireless networks with the increased
amount of reliability in higher learning institutions. To secure the data
dormancy networks do not the ability to provide the security of data.
Coverage- colleges and universities are large so that they have lots of
building blocks spread over land and they also spread their land to cities too.
Students have access to use in building blocks but when they went to
campus the coverage of the Wi-Fi is lost. For full coverage, the Apps is
connected to the backbone.
Density- If you want to solve the coverage problem, the main capacity of AP
poses another challenge. Like lecturer hall and auditorium these are they
are which can handle by AP.
2. Bluetooth- Today advanced wireless technology and most common technology is
Bluetooth. Bluetooth used to share the files from your device to another computer,
laptops if they are using smartphones around you. Each characteristic of Bluetooth is
2- Three different wireless network protocols. What security challenges they are
facing?
1. WiGig- High-Speed Wireless- They uses 60GHz radio band and 10 Gbps speed is the
latest Wi-Fir protocol. 802.11ad is the high-speed wireless technology in technical
spec. Due to this high-speed wireless technology, they use 40 GHz radio band and it
connects up to 1GBps. In multi-stored business houses, it is relatively tough to
monitor each of the corners. It will make to easy the connect the thread due to the
installing of high definition video cameras with this high speed of wi-fi systems
(Tagasovska et al.2014).
Figure 4: Diagram of WiGig
Advantage
There are some following benefits of WiGig –
Very low latency time (~ 10 microseconds)
Instant wireless synchronization
A wired connection can be eliminated
Automatically switching between bands
No interference with other low brand frequency
Disadvantage
There are some following drawbacks of WiGig –
No readily built into common devices
Due to the frequency of 60 GHz, the range is small, but this might be
effortlessly secure with a cheap Wi-Fi range extender device.
They are facing problems in large scale like campus-
Security- Spread over the network which is additional delicate data is
refined so that they are placing wireless networks with the increased
amount of reliability in higher learning institutions. To secure the data
dormancy networks do not the ability to provide the security of data.
Coverage- colleges and universities are large so that they have lots of
building blocks spread over land and they also spread their land to cities too.
Students have access to use in building blocks but when they went to
campus the coverage of the Wi-Fi is lost. For full coverage, the Apps is
connected to the backbone.
Density- If you want to solve the coverage problem, the main capacity of AP
poses another challenge. Like lecturer hall and auditorium these are they
are which can handle by AP.
2. Bluetooth- Today advanced wireless technology and most common technology is
Bluetooth. Bluetooth used to share the files from your device to another computer,
laptops if they are using smartphones around you. Each characteristic of Bluetooth is

7 | P a g e
different from another and there are different types of versions are available in
Bluetooth. Nowadays, the most progressive and current version of Bluetooth
protocols are (Osterhage .2010)-
Bluetooth high speed
Classic Bluetooth
Bluetooth Low energy
Figure 5: Diagram of Bluetooth
Advantage
There are some following benefits of Bluetooth-
In-car system, keyboard, webcam, GPS system, the printer is the technology
is approved in many products.
The Bluetooth is used for voice and data transfer
It avoids interface from other wireless networks
If the device via installed via Bluetooth you can use free
It has lower power consumption
No lines of sight hence can connect through any obstacles
It is easily upgradeable
They are available at a very cheap cost
It has range better than infrared communication
Disadvantage
There are some following drawbacks of Bluetooth-
Security is a very key aspect as it can be hacked
It can lose connection in certain conditions
It has low bandwidth as compares to Wi-Fi
It allows only short-range communication between devices
What security challenges Bluetooth are facing?
Inside attacks may be conceivable via ad-hoc transmission
Information might be removed deprived of recognition after indecorously
arranged strategies.
Delicate information might be dishonoured throughout indecorous
management
Delicate material that is not encoded (or that is encoded by underprivileged
cryptographic procedures) and that is communicated among two wireless
strategies might be interrupted and revealed.
Malevolent objects might usage a third party, untrusted wireless network
facilities to improvement contact to an intervention’s or additional
governments system properties.
Malicious entities might improvement illegal contact to an intervention’s
processor network over wireless influences, avoiding, any firewall defenses.
different from another and there are different types of versions are available in
Bluetooth. Nowadays, the most progressive and current version of Bluetooth
protocols are (Osterhage .2010)-
Bluetooth high speed
Classic Bluetooth
Bluetooth Low energy
Figure 5: Diagram of Bluetooth
Advantage
There are some following benefits of Bluetooth-
In-car system, keyboard, webcam, GPS system, the printer is the technology
is approved in many products.
The Bluetooth is used for voice and data transfer
It avoids interface from other wireless networks
If the device via installed via Bluetooth you can use free
It has lower power consumption
No lines of sight hence can connect through any obstacles
It is easily upgradeable
They are available at a very cheap cost
It has range better than infrared communication
Disadvantage
There are some following drawbacks of Bluetooth-
Security is a very key aspect as it can be hacked
It can lose connection in certain conditions
It has low bandwidth as compares to Wi-Fi
It allows only short-range communication between devices
What security challenges Bluetooth are facing?
Inside attacks may be conceivable via ad-hoc transmission
Information might be removed deprived of recognition after indecorously
arranged strategies.
Delicate information might be dishonoured throughout indecorous
management
Delicate material that is not encoded (or that is encoded by underprivileged
cryptographic procedures) and that is communicated among two wireless
strategies might be interrupted and revealed.
Malevolent objects might usage a third party, untrusted wireless network
facilities to improvement contact to an intervention’s or additional
governments system properties.
Malicious entities might improvement illegal contact to an intervention’s
processor network over wireless influences, avoiding, any firewall defenses.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8 | P a g e
Information might be removed deprived of recognition from unsuitably
arranged strategies.
DoS outbreak might be absorbed at wireless influences or strategies.
Intruders, after confidential or obtainable, might be able to improvement
connectivity to network organization panels and thus incapacitate or disturb
processes.
3. Apple iBeacon- The name is clearly notified you that this is a most advanced wireless
network which was related by iPad and iPhones. To retailing services of iBeacon is a
division of smart Bluetooth. This means that within a short distance or short time of
period if you have an Apple smartphone with you, you can market related
information around you. You will get everything to your phone from the discount
and products information (Newman.2014).
Figure 6: Diagram of iBeacon
Advantage
There are some following benefits of Apple iBeacon –
Micro-location
Tracking
Cost-effectiveness
Automation
Disadvantage
There are some following benefits of Apple iBeacon –
Investment
Privacy
Security
Store traffic
What security challenges Apple iBeacon are facing?
Hijacking- To the formation layer of the iBeacon hijacking includes an
unauthorized third-party acquisition access. In iBeacon they allow them to
control the operative situations, as well as University Unique Identifier.
Hijacking is allowed to the attacker to complete any of the two earlier
attacks, by altering the verification data of the specific beacon holder with
the extra potential to lock out.
Spoofing- It is a most commonly known vulnerability. When the beacon is
published its University Unique Identifier publicly, to capture a specific
beacon’s University Unique Identifier the third party may utilize some similar
tools like spoofing.
Information might be removed deprived of recognition from unsuitably
arranged strategies.
DoS outbreak might be absorbed at wireless influences or strategies.
Intruders, after confidential or obtainable, might be able to improvement
connectivity to network organization panels and thus incapacitate or disturb
processes.
3. Apple iBeacon- The name is clearly notified you that this is a most advanced wireless
network which was related by iPad and iPhones. To retailing services of iBeacon is a
division of smart Bluetooth. This means that within a short distance or short time of
period if you have an Apple smartphone with you, you can market related
information around you. You will get everything to your phone from the discount
and products information (Newman.2014).
Figure 6: Diagram of iBeacon
Advantage
There are some following benefits of Apple iBeacon –
Micro-location
Tracking
Cost-effectiveness
Automation
Disadvantage
There are some following benefits of Apple iBeacon –
Investment
Privacy
Security
Store traffic
What security challenges Apple iBeacon are facing?
Hijacking- To the formation layer of the iBeacon hijacking includes an
unauthorized third-party acquisition access. In iBeacon they allow them to
control the operative situations, as well as University Unique Identifier.
Hijacking is allowed to the attacker to complete any of the two earlier
attacks, by altering the verification data of the specific beacon holder with
the extra potential to lock out.
Spoofing- It is a most commonly known vulnerability. When the beacon is
published its University Unique Identifier publicly, to capture a specific
beacon’s University Unique Identifier the third party may utilize some similar
tools like spoofing.

9 | P a g e
Denial of services- The denial of services is in the framework of iBeacon can
be divided into two groups- crashing the Bluetooth track and battery drain
attacks. In another case, the device non-operational is the end goal to
render. Most of the Beacon are stand-alone devices, usages to organize the
beacon they stood a formation layer in accumulation to the publicity layer
that a retailer exact application usage to arrange the beacon.
Denial of services- The denial of services is in the framework of iBeacon can
be divided into two groups- crashing the Bluetooth track and battery drain
attacks. In another case, the device non-operational is the end goal to
render. Most of the Beacon are stand-alone devices, usages to organize the
beacon they stood a formation layer in accumulation to the publicity layer
that a retailer exact application usage to arrange the beacon.
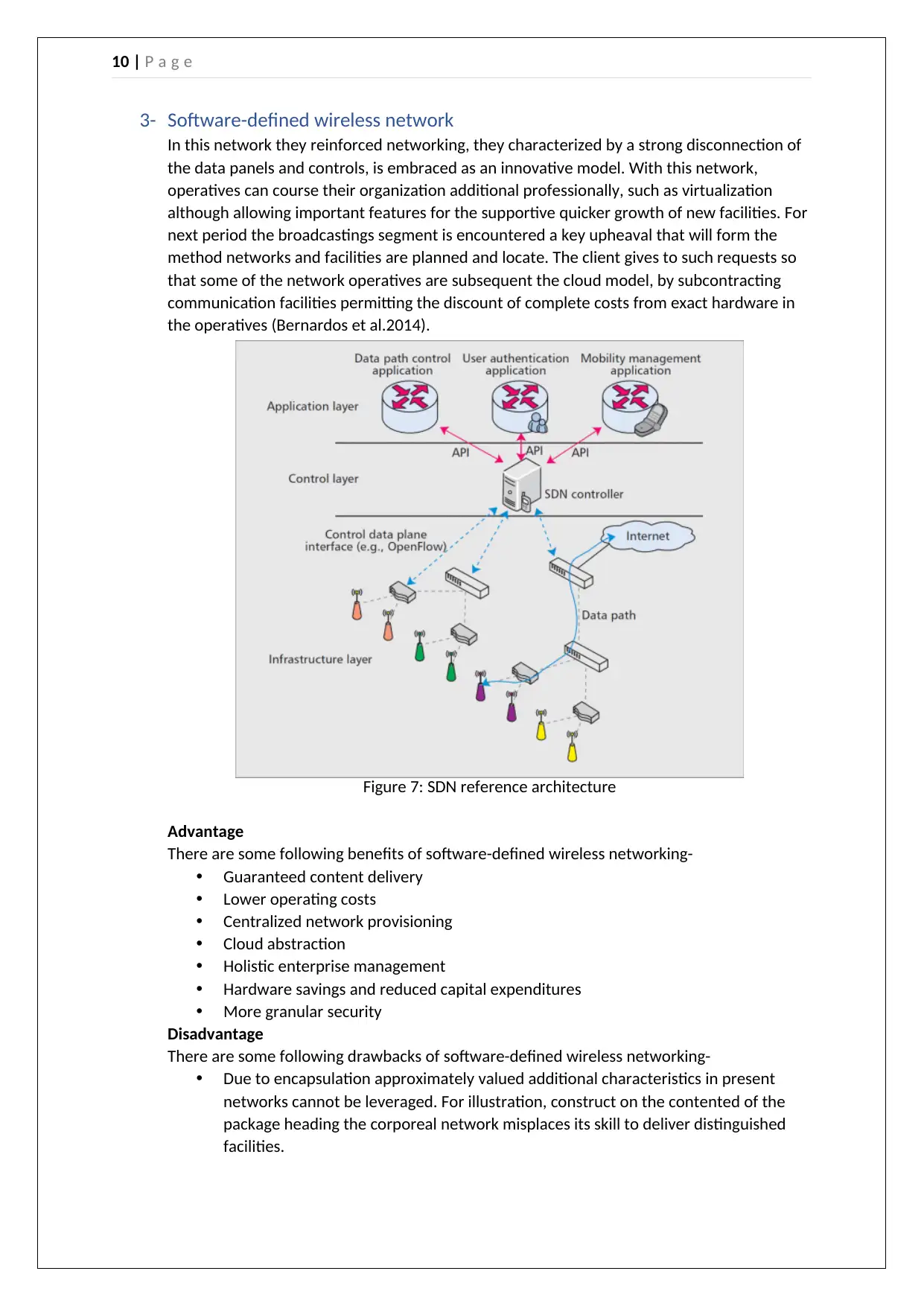
10 | P a g e
3- Software-defined wireless network
In this network they reinforced networking, they characterized by a strong disconnection of
the data panels and controls, is embraced as an innovative model. With this network,
operatives can course their organization additional professionally, such as virtualization
although allowing important features for the supportive quicker growth of new facilities. For
next period the broadcastings segment is encountered a key upheaval that will form the
method networks and facilities are planned and locate. The client gives to such requests so
that some of the network operatives are subsequent the cloud model, by subcontracting
communication facilities permitting the discount of complete costs from exact hardware in
the operatives (Bernardos et al.2014).
Figure 7: SDN reference architecture
Advantage
There are some following benefits of software-defined wireless networking-
Guaranteed content delivery
Lower operating costs
Centralized network provisioning
Cloud abstraction
Holistic enterprise management
Hardware savings and reduced capital expenditures
More granular security
Disadvantage
There are some following drawbacks of software-defined wireless networking-
Due to encapsulation approximately valued additional characteristics in present
networks cannot be leveraged. For illustration, construct on the contented of the
package heading the corporeal network misplaces its skill to deliver distinguished
facilities.
3- Software-defined wireless network
In this network they reinforced networking, they characterized by a strong disconnection of
the data panels and controls, is embraced as an innovative model. With this network,
operatives can course their organization additional professionally, such as virtualization
although allowing important features for the supportive quicker growth of new facilities. For
next period the broadcastings segment is encountered a key upheaval that will form the
method networks and facilities are planned and locate. The client gives to such requests so
that some of the network operatives are subsequent the cloud model, by subcontracting
communication facilities permitting the discount of complete costs from exact hardware in
the operatives (Bernardos et al.2014).
Figure 7: SDN reference architecture
Advantage
There are some following benefits of software-defined wireless networking-
Guaranteed content delivery
Lower operating costs
Centralized network provisioning
Cloud abstraction
Holistic enterprise management
Hardware savings and reduced capital expenditures
More granular security
Disadvantage
There are some following drawbacks of software-defined wireless networking-
Due to encapsulation approximately valued additional characteristics in present
networks cannot be leveraged. For illustration, construct on the contented of the
package heading the corporeal network misplaces its skill to deliver distinguished
facilities.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
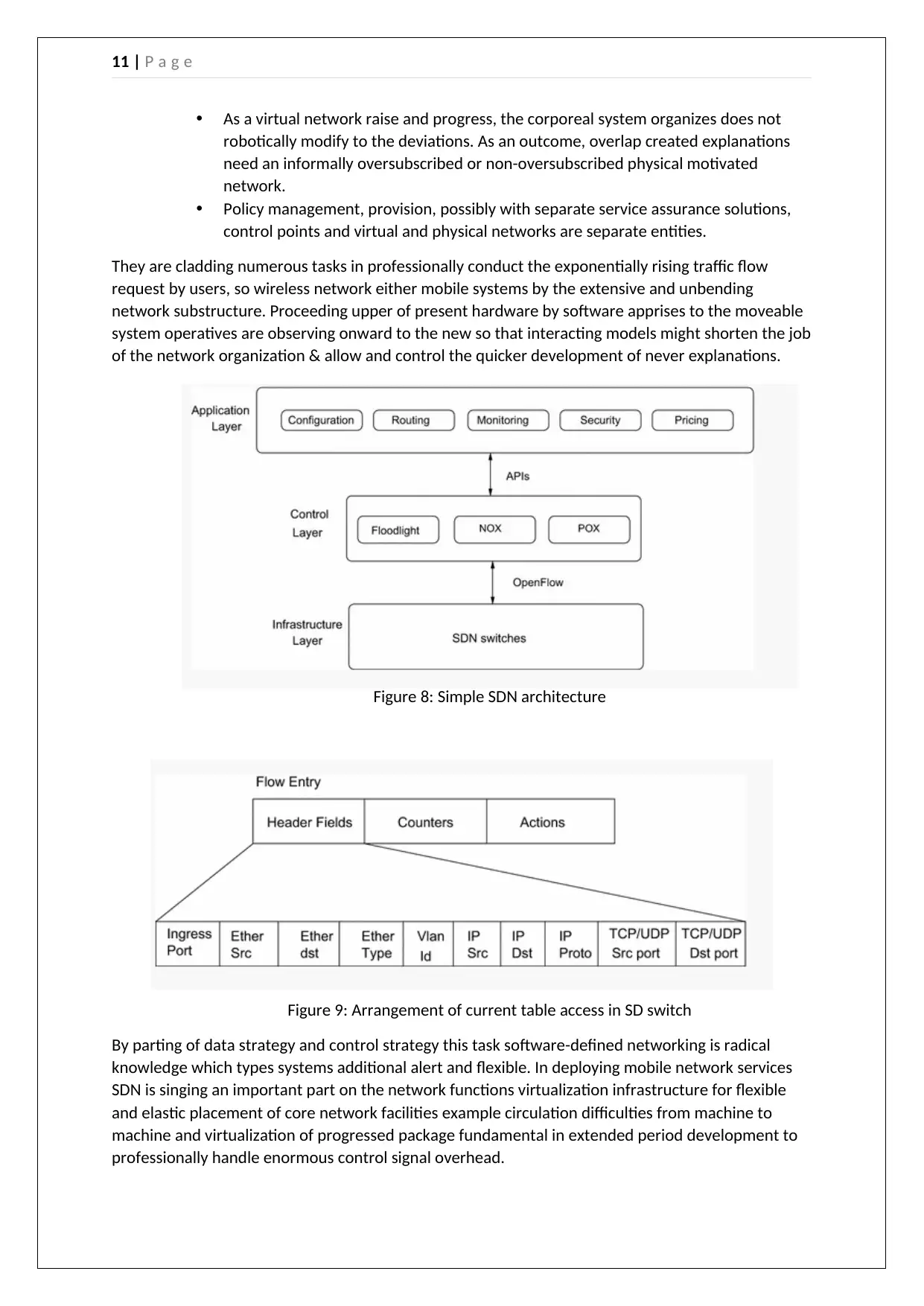
11 | P a g e
As a virtual network raise and progress, the corporeal system organizes does not
robotically modify to the deviations. As an outcome, overlap created explanations
need an informally oversubscribed or non-oversubscribed physical motivated
network.
Policy management, provision, possibly with separate service assurance solutions,
control points and virtual and physical networks are separate entities.
They are cladding numerous tasks in professionally conduct the exponentially rising traffic flow
request by users, so wireless network either mobile systems by the extensive and unbending
network substructure. Proceeding upper of present hardware by software apprises to the moveable
system operatives are observing onward to the new so that interacting models might shorten the job
of the network organization & allow and control the quicker development of never explanations.
Figure 8: Simple SDN architecture
Figure 9: Arrangement of current table access in SD switch
By parting of data strategy and control strategy this task software-defined networking is radical
knowledge which types systems additional alert and flexible. In deploying mobile network services
SDN is singing an important part on the network functions virtualization infrastructure for flexible
and elastic placement of core network facilities example circulation difficulties from machine to
machine and virtualization of progressed package fundamental in extended period development to
professionally handle enormous control signal overhead.
As a virtual network raise and progress, the corporeal system organizes does not
robotically modify to the deviations. As an outcome, overlap created explanations
need an informally oversubscribed or non-oversubscribed physical motivated
network.
Policy management, provision, possibly with separate service assurance solutions,
control points and virtual and physical networks are separate entities.
They are cladding numerous tasks in professionally conduct the exponentially rising traffic flow
request by users, so wireless network either mobile systems by the extensive and unbending
network substructure. Proceeding upper of present hardware by software apprises to the moveable
system operatives are observing onward to the new so that interacting models might shorten the job
of the network organization & allow and control the quicker development of never explanations.
Figure 8: Simple SDN architecture
Figure 9: Arrangement of current table access in SD switch
By parting of data strategy and control strategy this task software-defined networking is radical
knowledge which types systems additional alert and flexible. In deploying mobile network services
SDN is singing an important part on the network functions virtualization infrastructure for flexible
and elastic placement of core network facilities example circulation difficulties from machine to
machine and virtualization of progressed package fundamental in extended period development to
professionally handle enormous control signal overhead.

12 | P a g e
For unbending accessible middleboxes is network function virtualization and software-defined
network are proposals elastic, contribution and flexible network facility binding stages as an
auxiliary.
IT services and cloud computing for contribution conclusion employer’s networks alert explanations
and facilities of MEC (Mobile edge computing) is an original connecting stage they carry together
and form the IT facilities. In this research paper, founded on the wireless networks we catalog
several challenges and problems in scheming software-defined network and for 4G/5G of evaluation
of numerous SDN founded on influential answers. In conclusion, this investigation offering the part
of MEC, Software defined network, and network functions virtualization in scheming 5G networks
(Rangisetti et al.2017).
For unbending accessible middleboxes is network function virtualization and software-defined
network are proposals elastic, contribution and flexible network facility binding stages as an
auxiliary.
IT services and cloud computing for contribution conclusion employer’s networks alert explanations
and facilities of MEC (Mobile edge computing) is an original connecting stage they carry together
and form the IT facilities. In this research paper, founded on the wireless networks we catalog
several challenges and problems in scheming software-defined network and for 4G/5G of evaluation
of numerous SDN founded on influential answers. In conclusion, this investigation offering the part
of MEC, Software defined network, and network functions virtualization in scheming 5G networks
(Rangisetti et al.2017).

13 | P a g e
References
Han, K., Nguyen, T., Park, I., & Han, H. (2009). Terahertz Yagi-Uda Antenna for High Input
Resistance. Journal Of Infrared, Millimeter, And Terahertz Waves. doi: 10.1007/s10762-009-9596-1
Balanis, C. (1988). Horn Antennas. Antenna Handbook, 431-516. doi: 10.1007/978-1-4615-6459-1_8
Gabriel, R., & Geissler, M. (2015). Antenna Systems for Cellular Base Stations. Handbook Of Antenna
Technologies, 1-63. doi: 10.1007/978-981-4560-75-7_88-1
Tagasovska, N., Grnarova, P., Tentov, A., & Efnusheva, D. (2014). Performances of LEON3 IP Core in
WiGig Environment on Receiving Side. Lecture Notes In Electrical Engineering, 243-251. doi:
10.1007/978-3-319-06764-3_31
Osterhage, W. (2010). Bluetooth. Sicher & Mobil, 133-148. doi: 10.1007/978-3-642-03083-3_8
Newman, N. (2014). Apple iBeacon technology briefing. Journal Of Direct, Data And Digital
Marketing Practice, 15(3), 222-225. doi: 10.1057/dddmp.2014.7
Bernardos, C. J., Oliva, A. d. l., Serrano, P., Banchs, A., Contreras, L. M., Jin, H., & Zuniga, J. C. (2014).
An architecture for software defined wireless networking. IEEE Wireless Communications, 21(3), 52-
61. doi: 10.1109/MWC.2014.6845049
Rangisetti, A. K., & Tamma, B. R. (2017). Software Defined Wireless Networks: A Survey of Issues and
Solutions. Wireless Personal Communications, 97(4), 6019- 6053. doi: 10.1007/s11277-017-4825-8
References
Han, K., Nguyen, T., Park, I., & Han, H. (2009). Terahertz Yagi-Uda Antenna for High Input
Resistance. Journal Of Infrared, Millimeter, And Terahertz Waves. doi: 10.1007/s10762-009-9596-1
Balanis, C. (1988). Horn Antennas. Antenna Handbook, 431-516. doi: 10.1007/978-1-4615-6459-1_8
Gabriel, R., & Geissler, M. (2015). Antenna Systems for Cellular Base Stations. Handbook Of Antenna
Technologies, 1-63. doi: 10.1007/978-981-4560-75-7_88-1
Tagasovska, N., Grnarova, P., Tentov, A., & Efnusheva, D. (2014). Performances of LEON3 IP Core in
WiGig Environment on Receiving Side. Lecture Notes In Electrical Engineering, 243-251. doi:
10.1007/978-3-319-06764-3_31
Osterhage, W. (2010). Bluetooth. Sicher & Mobil, 133-148. doi: 10.1007/978-3-642-03083-3_8
Newman, N. (2014). Apple iBeacon technology briefing. Journal Of Direct, Data And Digital
Marketing Practice, 15(3), 222-225. doi: 10.1057/dddmp.2014.7
Bernardos, C. J., Oliva, A. d. l., Serrano, P., Banchs, A., Contreras, L. M., Jin, H., & Zuniga, J. C. (2014).
An architecture for software defined wireless networking. IEEE Wireless Communications, 21(3), 52-
61. doi: 10.1109/MWC.2014.6845049
Rangisetti, A. K., & Tamma, B. R. (2017). Software Defined Wireless Networks: A Survey of Issues and
Solutions. Wireless Personal Communications, 97(4), 6019- 6053. doi: 10.1007/s11277-017-4825-8
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




