Wireless Networking Assignment: RFID, NFC, Security, Packet Tracer
VerifiedAdded on 2020/10/22
|21
|1732
|89
Homework Assignment
AI Summary
This assignment delves into wireless networking, exploring Radio Frequency Identification (RFID) and Near Field Communication (NFC) technologies. It examines the security considerations and challenges associated with these technologies, including eavesdropping and denial-of-service attacks. The assignment involves setting up a wireless network using Packet Tracer simulation software, configuring laptops and access points, and implementing WPA2-PSK security with AES encryption. The student analyzes the communication process, evaluates the impact of channel changes on access points, and investigates passphrase mismatches. The assignment also includes an overview of the network design, reasons for choosing specific wireless technologies, how the design meets project goals, and a discussion of technical trade-offs. The report concludes with references to relevant books and journals, and also includes a Packet Tracer file illustrating the network setup.

Wireless Networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
PART A...........................................................................................................................................3
Describe RFID and NFC network and explain security considerations and challenges.............3
a) Does every laptop ping every other laptop through the authenticated connections? Explain
the communication process.........................................................................................................4
b) What happens when the channel is changed on any of the access points...............................5
c) What happens if there is a passphrase mismatch between the clients and the access points..5
PART B............................................................................................................................................6
Overview of your design.............................................................................................................6
Reasons for proposed wireless technologies...............................................................................6
How it meets the specified project goals....................................................................................6
Discuss specific technical design issues or trade-offs that you have made in your design. .......6
CONCLUSION................................................................................................................................8
INTRODUCTION...........................................................................................................................2
INTRODUCTION...........................................................................................................................3
PART A...........................................................................................................................................3
Describe RFID and NFC network and explain security considerations and challenges.............3
a) Does every laptop ping every other laptop through the authenticated connections? Explain
the communication process.........................................................................................................4
b) What happens when the channel is changed on any of the access points...............................5
c) What happens if there is a passphrase mismatch between the clients and the access points..5
PART B............................................................................................................................................6
Overview of your design.............................................................................................................6
Reasons for proposed wireless technologies...............................................................................6
How it meets the specified project goals....................................................................................6
Discuss specific technical design issues or trade-offs that you have made in your design. .......6
CONCLUSION................................................................................................................................8
INTRODUCTION...........................................................................................................................2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Wireless networking is a type of method which help for communicating form one place
to another place by using communication device. This network will establish connection between
one node to another. Wireless network includes mobile phones, sensor, local area network and
satellite communication etc. This report will discuss about the RFID and NFC work in wireless
network. This report will describe Internet of things to establish connection and connect devices
in wirelessly.
PART A
Describe RFID and NFC network and explain security considerations and challenges
RFID is radio frequency identification and security method which help for wireless
network to maintain their signals effective manner. RFID is backbone of internet of things and
near field communication system. RF system is plays important role in data security and
counterfeiting issues while hardware embedded and on chip security based on physical functions.
The major aim of RFID is to use the latest technology and technique utilised the concept of
identifications and security respectively.
NFC is near filed communication technique for communicating with user and it also
useful for storing the details of credit card information of user. It is very important for securing
the private information so it required for use NFC technology to manage the information’s
effectively and efficiently. There is various type security attack such as data corruption, physical
thefts, interception attacks and NFC technique help for preventing by data breach.
Security considerations and challenges-
There are some important security challenges in Near Frequency communication network
discuss in followings:
Eavesdropping- This is the main security issue that affect the wireless network and NFC is
communication technology by using radio frequency waves etc.
Denial of services- This attack has done by exchanging data between two different devices and
data sent by sending devices that is decoded by second device.
Secure channel- Secure channel useful for NFC device to easily set up and protect their data
send form modifications. This protocol is help for communicating between parties to hold secret
key.
Wireless networking is a type of method which help for communicating form one place
to another place by using communication device. This network will establish connection between
one node to another. Wireless network includes mobile phones, sensor, local area network and
satellite communication etc. This report will discuss about the RFID and NFC work in wireless
network. This report will describe Internet of things to establish connection and connect devices
in wirelessly.
PART A
Describe RFID and NFC network and explain security considerations and challenges
RFID is radio frequency identification and security method which help for wireless
network to maintain their signals effective manner. RFID is backbone of internet of things and
near field communication system. RF system is plays important role in data security and
counterfeiting issues while hardware embedded and on chip security based on physical functions.
The major aim of RFID is to use the latest technology and technique utilised the concept of
identifications and security respectively.
NFC is near filed communication technique for communicating with user and it also
useful for storing the details of credit card information of user. It is very important for securing
the private information so it required for use NFC technology to manage the information’s
effectively and efficiently. There is various type security attack such as data corruption, physical
thefts, interception attacks and NFC technique help for preventing by data breach.
Security considerations and challenges-
There are some important security challenges in Near Frequency communication network
discuss in followings:
Eavesdropping- This is the main security issue that affect the wireless network and NFC is
communication technology by using radio frequency waves etc.
Denial of services- This attack has done by exchanging data between two different devices and
data sent by sending devices that is decoded by second device.
Secure channel- Secure channel useful for NFC device to easily set up and protect their data
send form modifications. This protocol is help for communicating between parties to hold secret
key.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
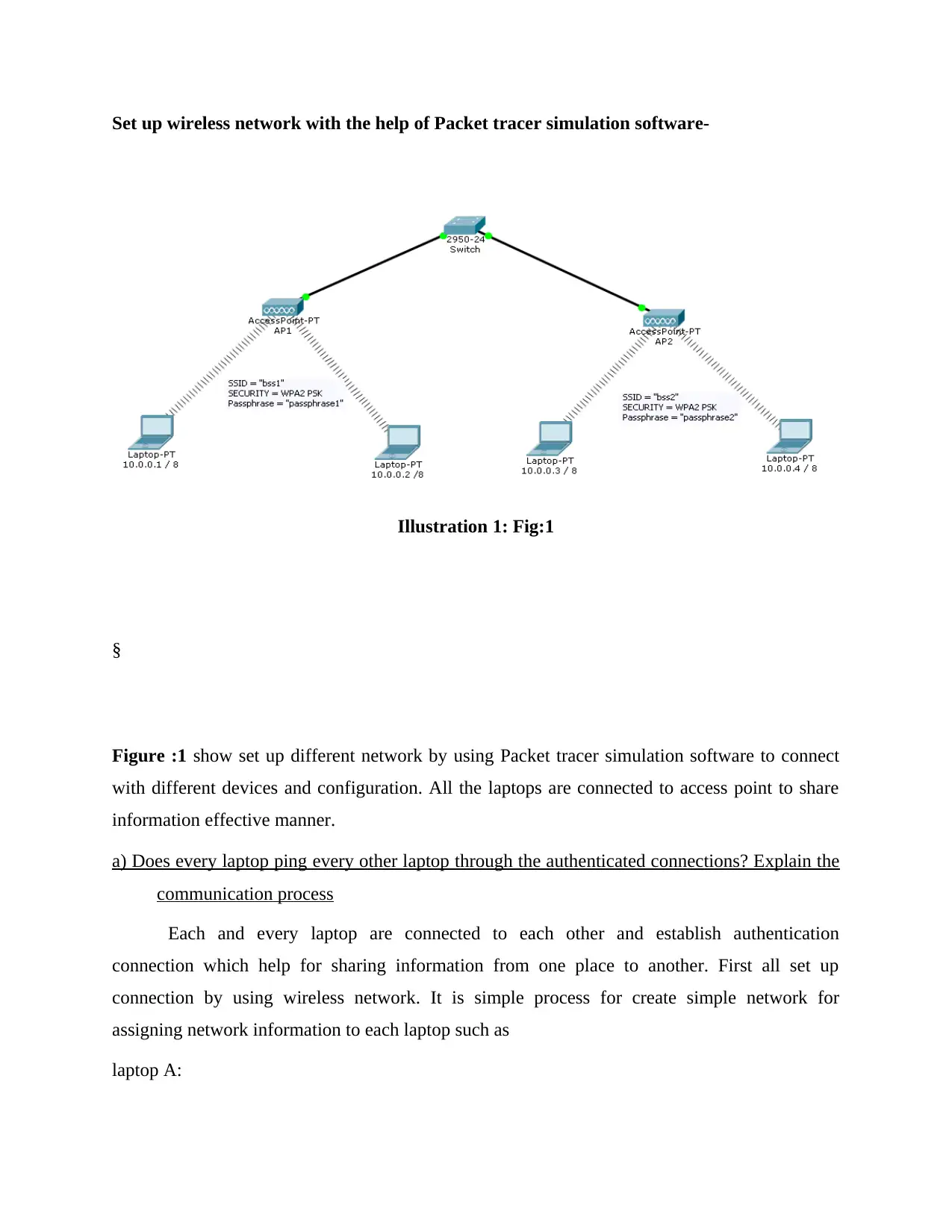
Set up wireless network with the help of Packet tracer simulation software-
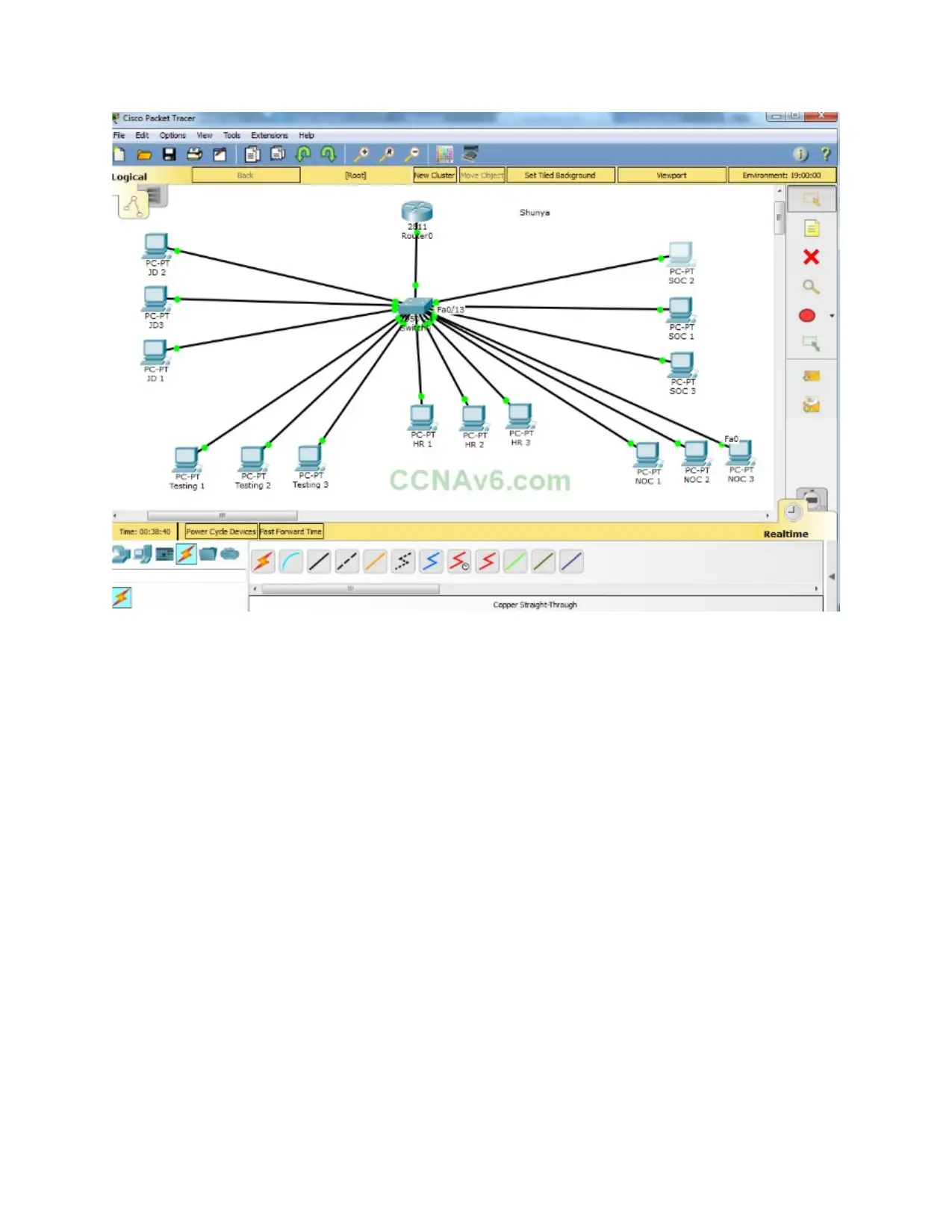
Illustration 1: Fig:1
§
Figure :1 show set up different network by using Packet tracer simulation software to connect
with different devices and configuration. All the laptops are connected to access point to share
information effective manner.
a) Does every laptop ping every other laptop through the authenticated connections? Explain the
communication process
Each and every laptop are connected to each other and establish authentication
connection which help for sharing information from one place to another. First all set up
connection by using wireless network. It is simple process for create simple network for
assigning network information to each laptop such as
laptop A:
Illustration 1: Fig:1
§
Figure :1 show set up different network by using Packet tracer simulation software to connect
with different devices and configuration. All the laptops are connected to access point to share
information effective manner.
a) Does every laptop ping every other laptop through the authenticated connections? Explain the
communication process
Each and every laptop are connected to each other and establish authentication
connection which help for sharing information from one place to another. First all set up
connection by using wireless network. It is simple process for create simple network for
assigning network information to each laptop such as
laptop A:

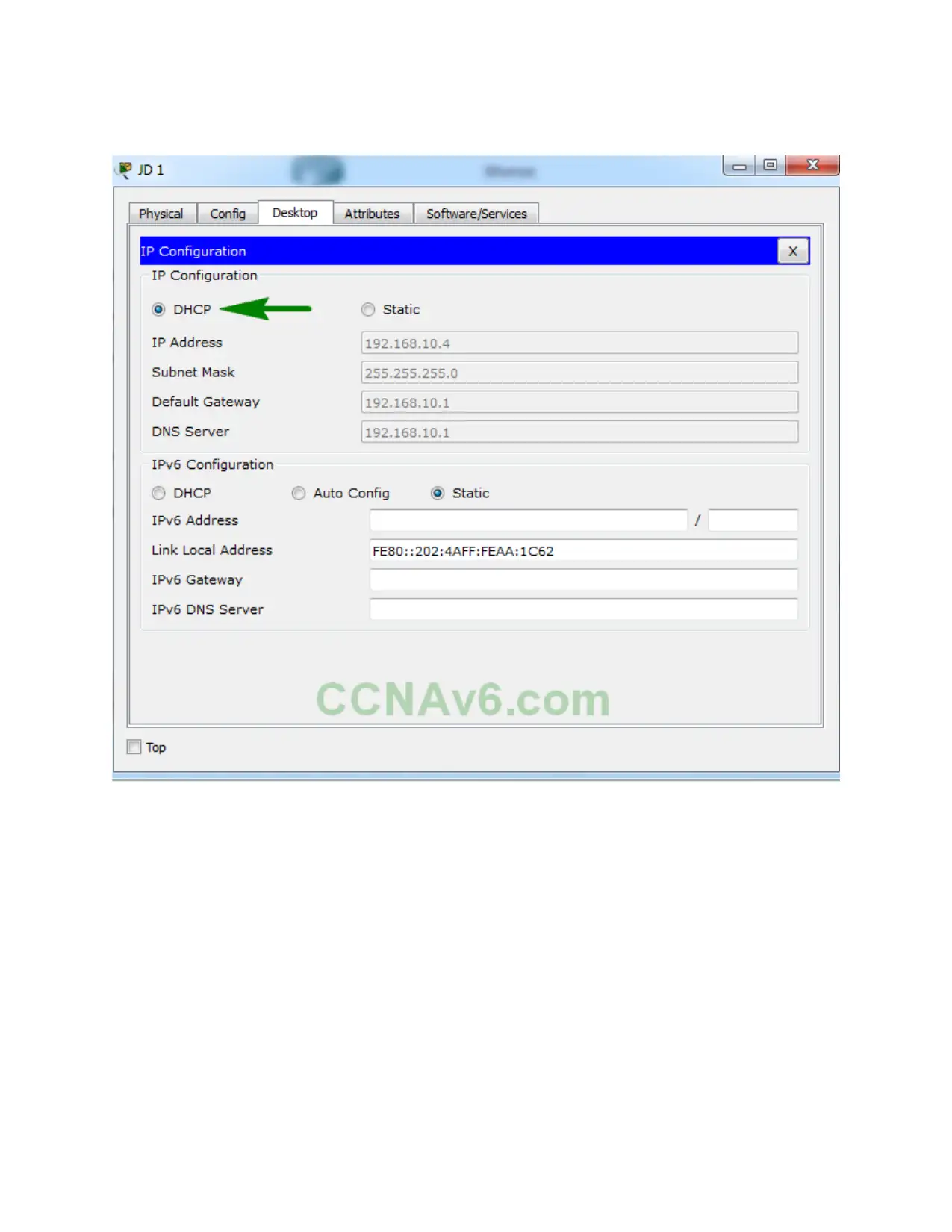
IP Address: 10.0.c.1/0
Subnet mask: 255.255.255.0
Laptop B:
IP Address: 10.0.02/8
Subnet mask: 255.255.255.0
Gateway:
DNS Servers:
The internet connection sharing information from one laptop to another, it will set the other
laptop to obtain an IP Address automatically and the laptop will able to access internet by using
wireless network and after completion configuration, laptop one can connect with another system
to share file by wireless network.
b) What happens when the channel is changed on any of the access points
Each and every wireless network has wide range and it is just for access points into
different wireless transmission specs. All devices that are configured to communicate using the
spec. Most of time, wireless network is creating default channel is move from one access point to
another access point.
Changing channel provide the limiting amount of broad caster in their local areas. By
limiting, the device gets clean the signals and increase the speed in different range. By changing
the channel so that eliminate the interferences and many routers will help to detect the
interference on default channel.
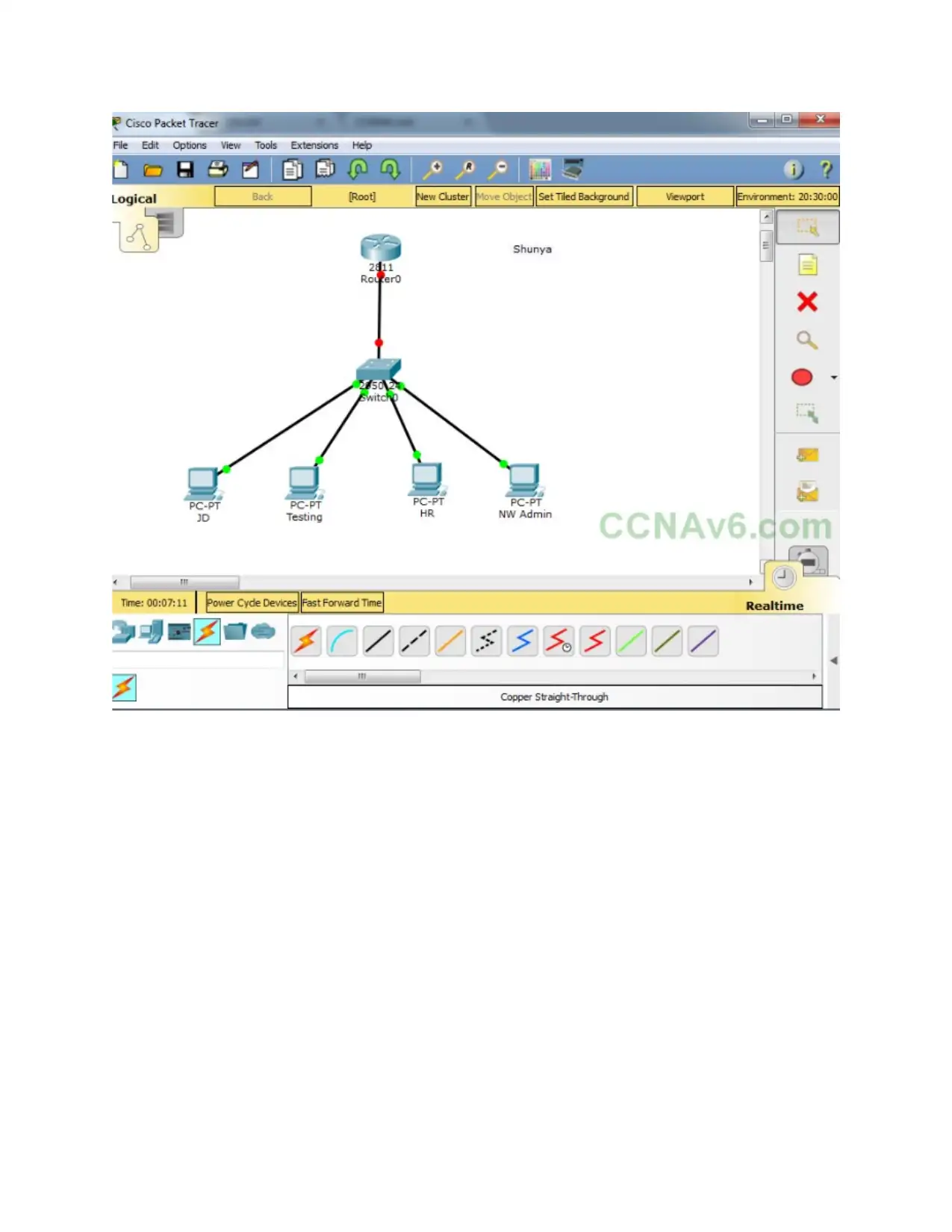
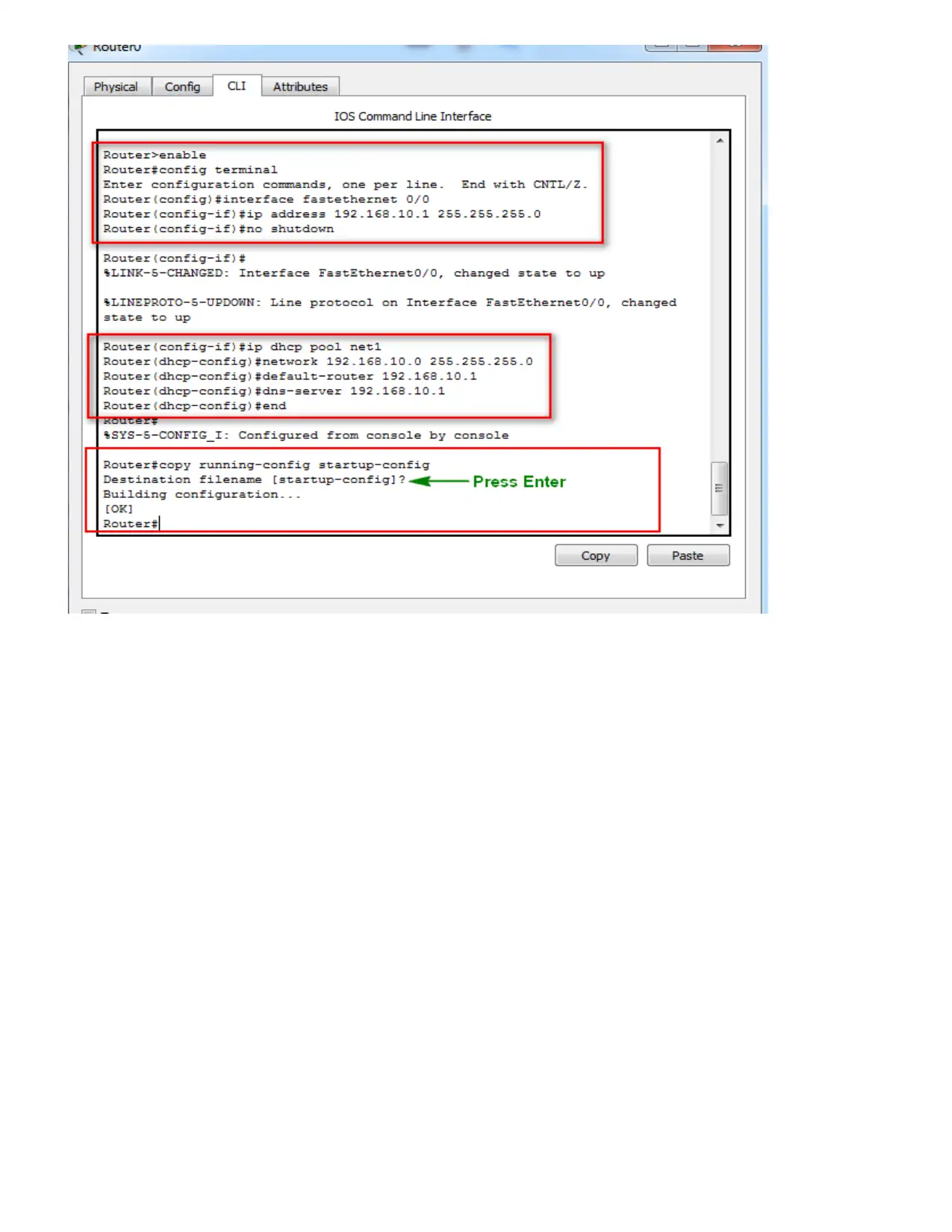
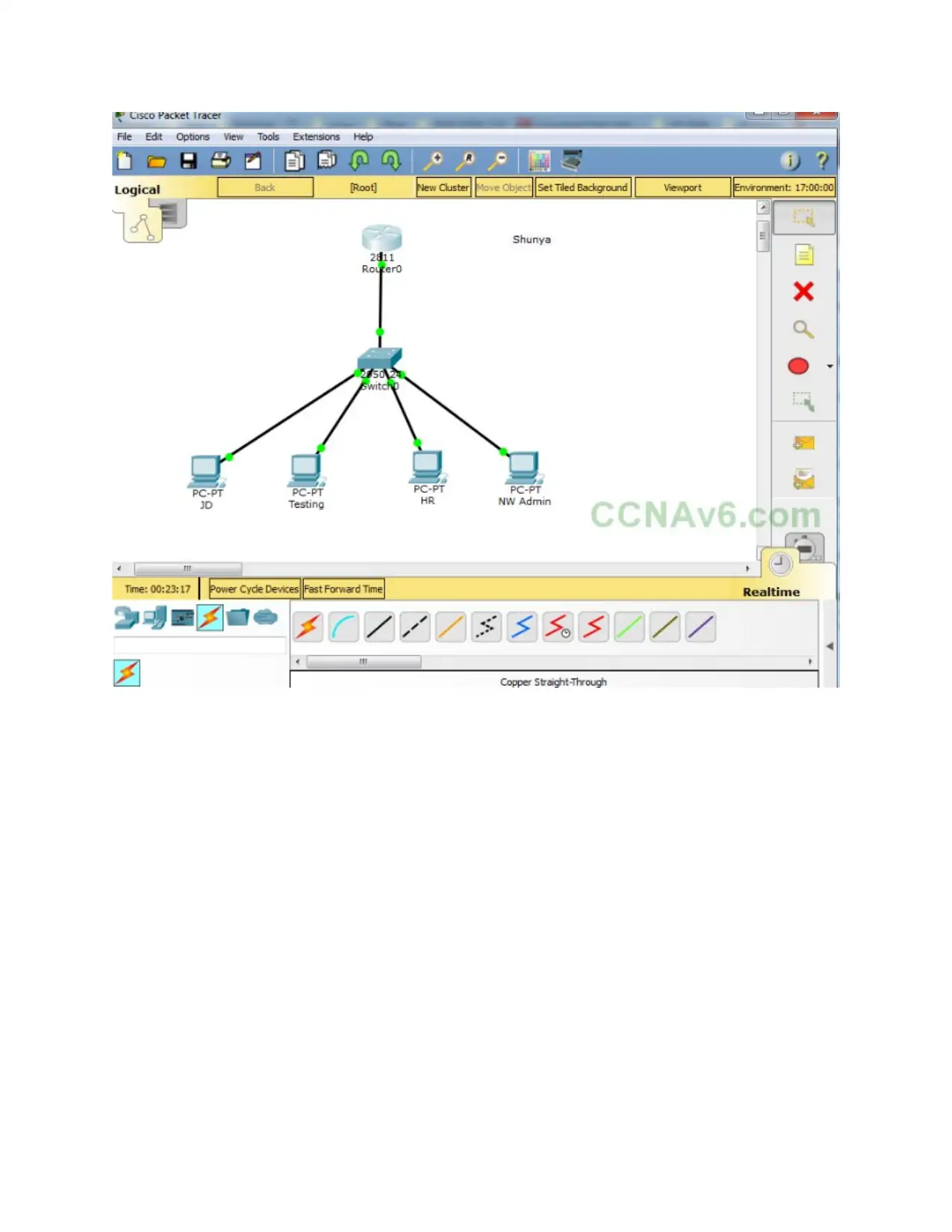
Design network by using Packet tracer software: -
This network is logical IP network that is dividing into different sub networks. It provides
the security which help for securing their data in proper manner. This network will important
part of organization for improving the performance of speed and capability. Design an efficient
network by using packet tracer software in given below:
Subnet mask: 255.255.255.0
Laptop B:
IP Address: 10.0.02/8
Subnet mask: 255.255.255.0
Gateway:
DNS Servers:
The internet connection sharing information from one laptop to another, it will set the other
laptop to obtain an IP Address automatically and the laptop will able to access internet by using
wireless network and after completion configuration, laptop one can connect with another system
to share file by wireless network.
b) What happens when the channel is changed on any of the access points
Each and every wireless network has wide range and it is just for access points into
different wireless transmission specs. All devices that are configured to communicate using the
spec. Most of time, wireless network is creating default channel is move from one access point to
another access point.
Changing channel provide the limiting amount of broad caster in their local areas. By
limiting, the device gets clean the signals and increase the speed in different range. By changing
the channel so that eliminate the interferences and many routers will help to detect the
interference on default channel.
Design network by using Packet tracer software: -
This network is logical IP network that is dividing into different sub networks. It provides
the security which help for securing their data in proper manner. This network will important
part of organization for improving the performance of speed and capability. Design an efficient
network by using packet tracer software in given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




