Case Study: INF80043 IS/IT Risk Management at CommDev Foundation
VerifiedAdded on 2023/06/03
|14
|4806
|131
Case Study
AI Summary
This case study provides an overview of IS/IT risk management within the context of CommDev, a not-for-profit organization focused on community development. It emphasizes the importance of information security, highlighting the CIA (Confidentiality, Integrity, and Availability) triangle. The study outlines a risk management process involving risk assessment, mitigation, and effectiveness assessment. It details how CommDev can assess risks by understanding asset value, system vulnerabilities, potential threats, and the likelihood and impact of successful attacks. The case study also touches on system characterization and threat assessment, providing practical steps for CommDev to mitigate risks and secure its data center and corporate systems.

Introduction
Information security of a given company should always be treated in a very serious way. The
security of such information if not handled well may lead to leakage or data being comprised
leading to the organisation losing its data confidentiality. It is very hard for a company to secure
their information and feel that they are fully satisfied with the method they have applied in
securing their information. It is mandatory for any company to set some risk management
strategies with regards to how such vulnerabilities and insecurity issues can be handled in cases
where they occur. It is common nowadays to hear or even see incidences where a specific
organisation security has been breached or comprised. In consideration to CommDev case study,
for instance a computer or a laptop at CommDev is lost or even stolen or a situation where their
data center which has servers is accessed without their authentication and authorization.
CommDev is an organisation which aims at supporting the needy children in the Pacific and
Asian regions and particularly in Australia where its headquarters are based. CommDev is an
organisation that is there to not to make profits but its main mission to doing charitable works
like helping the children to achieve their dreams in all aspects of what they do in schools
regardless of the ethnicity and race. The incidents may be net worth considering that the
confidentiality of data will be lost. A CommDev just like the modern society and companies has
entirely depended on the third party storage, transmission of data and the consumption of
information. Information at any organisation is always considered to be an asset which is
valuable and is supposed to be protected always at all times regardless of what entails.
Information security is known for comprising of a CIA triangle. The word CIA means
Confidentiality, Integrity and Availability of information respectively (adrofee, 2016).
Sometimes accountability is considered as an aspect too which plays a major role in protecting
the information.
Information security of a given company should always be treated in a very serious way. The
security of such information if not handled well may lead to leakage or data being comprised
leading to the organisation losing its data confidentiality. It is very hard for a company to secure
their information and feel that they are fully satisfied with the method they have applied in
securing their information. It is mandatory for any company to set some risk management
strategies with regards to how such vulnerabilities and insecurity issues can be handled in cases
where they occur. It is common nowadays to hear or even see incidences where a specific
organisation security has been breached or comprised. In consideration to CommDev case study,
for instance a computer or a laptop at CommDev is lost or even stolen or a situation where their
data center which has servers is accessed without their authentication and authorization.
CommDev is an organisation which aims at supporting the needy children in the Pacific and
Asian regions and particularly in Australia where its headquarters are based. CommDev is an
organisation that is there to not to make profits but its main mission to doing charitable works
like helping the children to achieve their dreams in all aspects of what they do in schools
regardless of the ethnicity and race. The incidents may be net worth considering that the
confidentiality of data will be lost. A CommDev just like the modern society and companies has
entirely depended on the third party storage, transmission of data and the consumption of
information. Information at any organisation is always considered to be an asset which is
valuable and is supposed to be protected always at all times regardless of what entails.
Information security is known for comprising of a CIA triangle. The word CIA means
Confidentiality, Integrity and Availability of information respectively (adrofee, 2016).
Sometimes accountability is considered as an aspect too which plays a major role in protecting
the information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
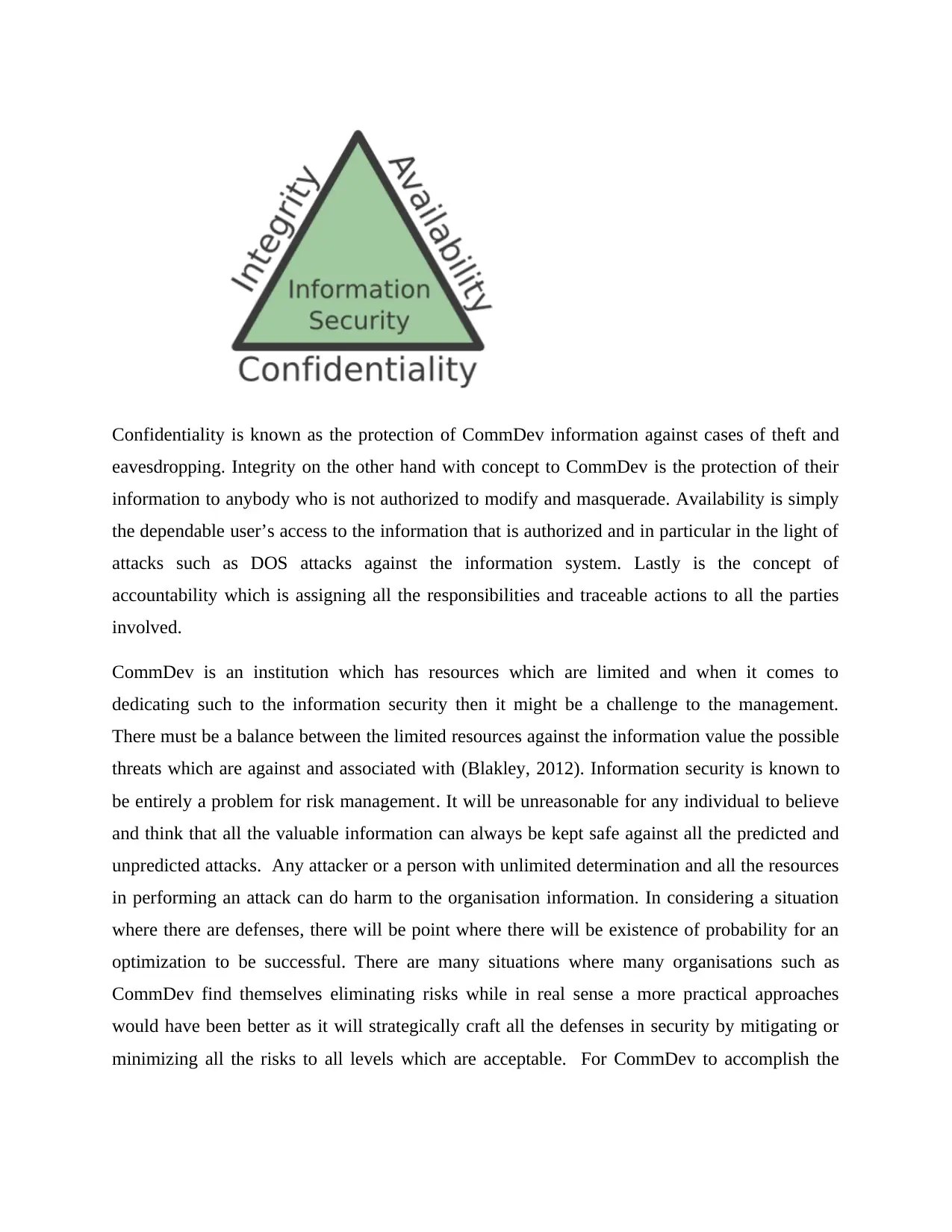
Confidentiality is known as the protection of CommDev information against cases of theft and
eavesdropping. Integrity on the other hand with concept to CommDev is the protection of their
information to anybody who is not authorized to modify and masquerade. Availability is simply
the dependable user’s access to the information that is authorized and in particular in the light of
attacks such as DOS attacks against the information system. Lastly is the concept of
accountability which is assigning all the responsibilities and traceable actions to all the parties
involved.
CommDev is an institution which has resources which are limited and when it comes to
dedicating such to the information security then it might be a challenge to the management.
There must be a balance between the limited resources against the information value the possible
threats which are against and associated with (Blakley, 2012). Information security is known to
be entirely a problem for risk management. It will be unreasonable for any individual to believe
and think that all the valuable information can always be kept safe against all the predicted and
unpredicted attacks. Any attacker or a person with unlimited determination and all the resources
in performing an attack can do harm to the organisation information. In considering a situation
where there are defenses, there will be point where there will be existence of probability for an
optimization to be successful. There are many situations where many organisations such as
CommDev find themselves eliminating risks while in real sense a more practical approaches
would have been better as it will strategically craft all the defenses in security by mitigating or
minimizing all the risks to all levels which are acceptable. For CommDev to accomplish the
eavesdropping. Integrity on the other hand with concept to CommDev is the protection of their
information to anybody who is not authorized to modify and masquerade. Availability is simply
the dependable user’s access to the information that is authorized and in particular in the light of
attacks such as DOS attacks against the information system. Lastly is the concept of
accountability which is assigning all the responsibilities and traceable actions to all the parties
involved.
CommDev is an institution which has resources which are limited and when it comes to
dedicating such to the information security then it might be a challenge to the management.
There must be a balance between the limited resources against the information value the possible
threats which are against and associated with (Blakley, 2012). Information security is known to
be entirely a problem for risk management. It will be unreasonable for any individual to believe
and think that all the valuable information can always be kept safe against all the predicted and
unpredicted attacks. Any attacker or a person with unlimited determination and all the resources
in performing an attack can do harm to the organisation information. In considering a situation
where there are defenses, there will be point where there will be existence of probability for an
optimization to be successful. There are many situations where many organisations such as
CommDev find themselves eliminating risks while in real sense a more practical approaches
would have been better as it will strategically craft all the defenses in security by mitigating or
minimizing all the risks to all levels which are acceptable. For CommDev to accomplish the

discussed goal, it will be necessary for them to perform a methodical analysis of the risks. This
chapter has entailed the overview of the risk management process.
Background
Risk management in an organization like CommDev may be so tricky and very wide. In this
concept risk management may be categorized in to three processes as shown in te diagram below
figure below.
Figure 1 risk management steps
As a researcher and a viewer of such management processes of risk in information security it will
be good for one to note there are no universal agreement which are made on the above three
processes, but in most cases the views will share the risk common elements which are to be
assessed and mitigated (Reinhard, 2011). Risk assessment is done and considered as the first
step where a risk must be assessed for one to confirm it for sure the risk can be a threat to the
information. After the risk has been assessed then if it may pose some threats to the organisation
then it will be wise to mitigate such risks and provide an effective evaluation. Risk assessment is
usually performed to help one understand the processing and system storage of the information
which is valuable, vulnerabilities of the system, some of the possible threats, impacts which are
likely posed by such threats and much more the risks which will emerge posing a threat to the
entire system.
Risk assessment is considered to be very simple and sometimes considered as an academic
exercise without inclusion of the mitigation of the risk process (navathe, 2012). The concept risk
mitigation means that a strategic plan that is used in prioritizing all the identified risks under any
constraints of the limited resources of organization. The third and last process is that of effective
chapter has entailed the overview of the risk management process.
Background
Risk management in an organization like CommDev may be so tricky and very wide. In this
concept risk management may be categorized in to three processes as shown in te diagram below
figure below.
Figure 1 risk management steps
As a researcher and a viewer of such management processes of risk in information security it will
be good for one to note there are no universal agreement which are made on the above three
processes, but in most cases the views will share the risk common elements which are to be
assessed and mitigated (Reinhard, 2011). Risk assessment is done and considered as the first
step where a risk must be assessed for one to confirm it for sure the risk can be a threat to the
information. After the risk has been assessed then if it may pose some threats to the organisation
then it will be wise to mitigate such risks and provide an effective evaluation. Risk assessment is
usually performed to help one understand the processing and system storage of the information
which is valuable, vulnerabilities of the system, some of the possible threats, impacts which are
likely posed by such threats and much more the risks which will emerge posing a threat to the
entire system.
Risk assessment is considered to be very simple and sometimes considered as an academic
exercise without inclusion of the mitigation of the risk process (navathe, 2012). The concept risk
mitigation means that a strategic plan that is used in prioritizing all the identified risks under any
constraints of the limited resources of organization. The third and last process is that of effective
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

assessment which has a goal of measuring and verifying the objectives of the risk mitigated if
they have been met accordingly and according to the to the organisation needs and requirements
with reference to information they need to be secured. If there is not clear then the other two
steps first and second that is risk assessment and mitigation must be updated accordingly for the
effects to reflect. Essentially, effectiveness assessment is meant for giving feedback to the first
and second processes and much more in ensuring correctness. The environment surrounding
CommDev environment as explained in the case study can be termed to be not static. CommDev
environment not being static has led them to have the need of having continuous process of
evaluation and updating the risk mitigated strategies with information which may be said to new
to the organisation.
Risk Assessment at CommDev.
It is not possible for an individual or an organisation to know when they will be attacked. Risks
is really explained on the basis on what is expected or might happen (jaquith, 2013). However,
threat may not be considered much of a risk in situations where the system that is protected is in
any way not vulnerable to the specific threats or the potential loss making it not to be significant.
Risk is known to be vulnerabilities functions and the impacts which are expected from the threats
available or posed. Risk assessment at CommDev may involve several steps in knowing and
understanding the assets value, vulnerabilities of the system, threats which are possible,
likelihoods of such threats and the impacts which are expected in case such attacks are
successful. The figure below is used to show the steps that CommDev can use in assessing the
risk in the organisation.
they have been met accordingly and according to the to the organisation needs and requirements
with reference to information they need to be secured. If there is not clear then the other two
steps first and second that is risk assessment and mitigation must be updated accordingly for the
effects to reflect. Essentially, effectiveness assessment is meant for giving feedback to the first
and second processes and much more in ensuring correctness. The environment surrounding
CommDev environment as explained in the case study can be termed to be not static. CommDev
environment not being static has led them to have the need of having continuous process of
evaluation and updating the risk mitigated strategies with information which may be said to new
to the organisation.
Risk Assessment at CommDev.
It is not possible for an individual or an organisation to know when they will be attacked. Risks
is really explained on the basis on what is expected or might happen (jaquith, 2013). However,
threat may not be considered much of a risk in situations where the system that is protected is in
any way not vulnerable to the specific threats or the potential loss making it not to be significant.
Risk is known to be vulnerabilities functions and the impacts which are expected from the threats
available or posed. Risk assessment at CommDev may involve several steps in knowing and
understanding the assets value, vulnerabilities of the system, threats which are possible,
likelihoods of such threats and the impacts which are expected in case such attacks are
successful. The figure below is used to show the steps that CommDev can use in assessing the
risk in the organisation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
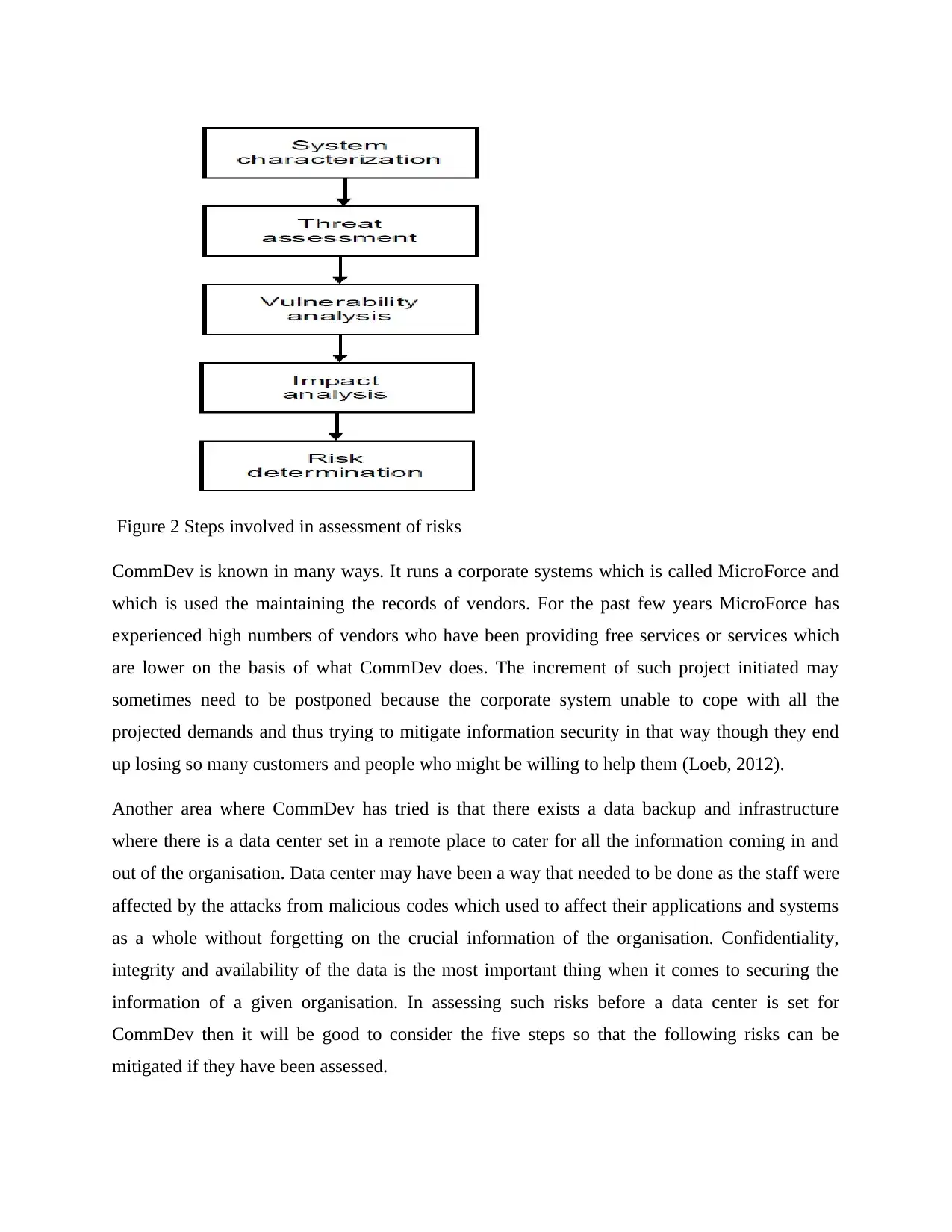
Figure 2 Steps involved in assessment of risks
CommDev is known in many ways. It runs a corporate systems which is called MicroForce and
which is used the maintaining the records of vendors. For the past few years MicroForce has
experienced high numbers of vendors who have been providing free services or services which
are lower on the basis of what CommDev does. The increment of such project initiated may
sometimes need to be postponed because the corporate system unable to cope with all the
projected demands and thus trying to mitigate information security in that way though they end
up losing so many customers and people who might be willing to help them (Loeb, 2012).
Another area where CommDev has tried is that there exists a data backup and infrastructure
where there is a data center set in a remote place to cater for all the information coming in and
out of the organisation. Data center may have been a way that needed to be done as the staff were
affected by the attacks from malicious codes which used to affect their applications and systems
as a whole without forgetting on the crucial information of the organisation. Confidentiality,
integrity and availability of the data is the most important thing when it comes to securing the
information of a given organisation. In assessing such risks before a data center is set for
CommDev then it will be good to consider the five steps so that the following risks can be
mitigated if they have been assessed.
CommDev is known in many ways. It runs a corporate systems which is called MicroForce and
which is used the maintaining the records of vendors. For the past few years MicroForce has
experienced high numbers of vendors who have been providing free services or services which
are lower on the basis of what CommDev does. The increment of such project initiated may
sometimes need to be postponed because the corporate system unable to cope with all the
projected demands and thus trying to mitigate information security in that way though they end
up losing so many customers and people who might be willing to help them (Loeb, 2012).
Another area where CommDev has tried is that there exists a data backup and infrastructure
where there is a data center set in a remote place to cater for all the information coming in and
out of the organisation. Data center may have been a way that needed to be done as the staff were
affected by the attacks from malicious codes which used to affect their applications and systems
as a whole without forgetting on the crucial information of the organisation. Confidentiality,
integrity and availability of the data is the most important thing when it comes to securing the
information of a given organisation. In assessing such risks before a data center is set for
CommDev then it will be good to consider the five steps so that the following risks can be
mitigated if they have been assessed.

System Characterization.
For any organization doing a risk assessment it will be necessary to do an identification of the
information that is to be protected, the value it has to CommDev and some of the system
elements such as the (software, hardware, people using such devices, the networks through
which data is transmitted and the processes) that are used in supporting the storage, to process
and transmit such information. Understanding the above will be termed as the concept of
information technology (IT). In making it simple it will be wise to say that the entire information
technology environment is said to be featured with terminologies such as the equipment’s, assets
and their value, the information flow and the responsibilities and duties of each personnel
(Kilner, 2010).
In most cases characterization of the system is done where one combines the method of data
gathering and collections such as one-on-one interviews which may be structured or semi-
structured or unstructured, use of questionnaires which may have open or close-ended questions,
documentation reviews, doing on-site inspections and the use of automated scanning. In
CommDev the on-site inspection and one-on-one interviews with personnel will work well as
method of gathering information. There are several tools which may be free while others are
commercial such as the scanning tools which may be available from the vendors who are
controlled by MicroForce such as the Cheops, Net-Scan-Tools, NMap, INETTools, Strobe tools,
WINSCAN and Sam-spade.
Threat Assessment
It may not be possible for one in devising a strategy without having to understand what one is
defending against. Threat is referred to as something potential which may cause damages or
troubles to the environment information technology. It will be useful for one in identifying all the
possible causes of threats origins or sources. However, malicious attacks like the malicious code
that affected the staff at CommDev may be caused by human sources which may from the human
minds first thought the threat originality or source is not entirely on the human. There are several
sources which may cause a threat such as those which are natural. A good example is when there
is bad weather, situations when there is flood due to heavy rains, earthquakes such as tsunami,
tornadoes, natural calamities such as avalanches and landslides. Other sources of threats can be
factored by the environment failures such as power issues (Kurtz, 2016).
For any organization doing a risk assessment it will be necessary to do an identification of the
information that is to be protected, the value it has to CommDev and some of the system
elements such as the (software, hardware, people using such devices, the networks through
which data is transmitted and the processes) that are used in supporting the storage, to process
and transmit such information. Understanding the above will be termed as the concept of
information technology (IT). In making it simple it will be wise to say that the entire information
technology environment is said to be featured with terminologies such as the equipment’s, assets
and their value, the information flow and the responsibilities and duties of each personnel
(Kilner, 2010).
In most cases characterization of the system is done where one combines the method of data
gathering and collections such as one-on-one interviews which may be structured or semi-
structured or unstructured, use of questionnaires which may have open or close-ended questions,
documentation reviews, doing on-site inspections and the use of automated scanning. In
CommDev the on-site inspection and one-on-one interviews with personnel will work well as
method of gathering information. There are several tools which may be free while others are
commercial such as the scanning tools which may be available from the vendors who are
controlled by MicroForce such as the Cheops, Net-Scan-Tools, NMap, INETTools, Strobe tools,
WINSCAN and Sam-spade.
Threat Assessment
It may not be possible for one in devising a strategy without having to understand what one is
defending against. Threat is referred to as something potential which may cause damages or
troubles to the environment information technology. It will be useful for one in identifying all the
possible causes of threats origins or sources. However, malicious attacks like the malicious code
that affected the staff at CommDev may be caused by human sources which may from the human
minds first thought the threat originality or source is not entirely on the human. There are several
sources which may cause a threat such as those which are natural. A good example is when there
is bad weather, situations when there is flood due to heavy rains, earthquakes such as tsunami,
tornadoes, natural calamities such as avalanches and landslides. Other sources of threats can be
factored by the environment failures such as power issues (Kurtz, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In many cases, human threats are the most worrying as the malicious attack is always driven by
intelligence and strategies set. It is not in all cases that the all threats caused by humans have a
malicious intention. A good example where such human threats may not have a malicious
intention is when a threat in CommDev emerges due to negligence for instance (when one forget
the default account of the computer) or accidentally (misconfiguring the firewall in a manner that
it will allow traffic which is unwanted) or lastly downloading software which is malicious
without knowing that they will harm the computer information or entire system.
It may be hard to categorize the human attackers as the motivations and actions anticipated and
involved may vary widely (Renaldo, 2017). When the motivations and actions which are
anticipated by the human attacker are scrutinized in CommDev it will be wise to say that
information technology human attackers can be classified in two divisions namely the internal
and external attackers. In terms of the internal classification, this may be an employee who is
disgruntled and may be seeking to revenge against CommDev or maybe a situation where there
is a dishonest staff who is snooping all the information which are proprietary and in other cases
information belonging to another employee.
The internal attacker may be so worrying in terms of the damages he or she can cause to the
organization because this person has login credentials and rights and thus giving him or her a
direct access to the organization assets which are valuable and perhaps interfering with the
accounts of computers which are of high privileges. In contrast, the external human attacker must
penetrate in the defenses of CommDev such as the firewalls in gaining access and then he or she
would be likely to have a lot of difficulties to gain access to the assets which are valuable to the
organization with accessing the roots and the privileges of admin.
External human attackers is known for the inclusion of amateur, hackers who are always
motivated by their curiosity or much more ego, other criminals who are professional who looks
to make profit, terrorist who aims at destroying and extortion, interests from military with a
motivation of national interest and maybe hired industrial spies who will attempt to steal the
information which is proprietary for the aim of making profit. External threats in many cases
might have the inclusion of malicious automated software’s such as the worms and viruses which
may entangle and spread themselves via the internet. In many cases, this might be feasible when
intelligence and strategies set. It is not in all cases that the all threats caused by humans have a
malicious intention. A good example where such human threats may not have a malicious
intention is when a threat in CommDev emerges due to negligence for instance (when one forget
the default account of the computer) or accidentally (misconfiguring the firewall in a manner that
it will allow traffic which is unwanted) or lastly downloading software which is malicious
without knowing that they will harm the computer information or entire system.
It may be hard to categorize the human attackers as the motivations and actions anticipated and
involved may vary widely (Renaldo, 2017). When the motivations and actions which are
anticipated by the human attacker are scrutinized in CommDev it will be wise to say that
information technology human attackers can be classified in two divisions namely the internal
and external attackers. In terms of the internal classification, this may be an employee who is
disgruntled and may be seeking to revenge against CommDev or maybe a situation where there
is a dishonest staff who is snooping all the information which are proprietary and in other cases
information belonging to another employee.
The internal attacker may be so worrying in terms of the damages he or she can cause to the
organization because this person has login credentials and rights and thus giving him or her a
direct access to the organization assets which are valuable and perhaps interfering with the
accounts of computers which are of high privileges. In contrast, the external human attacker must
penetrate in the defenses of CommDev such as the firewalls in gaining access and then he or she
would be likely to have a lot of difficulties to gain access to the assets which are valuable to the
organization with accessing the roots and the privileges of admin.
External human attackers is known for the inclusion of amateur, hackers who are always
motivated by their curiosity or much more ego, other criminals who are professional who looks
to make profit, terrorist who aims at destroying and extortion, interests from military with a
motivation of national interest and maybe hired industrial spies who will attempt to steal the
information which is proprietary for the aim of making profit. External threats in many cases
might have the inclusion of malicious automated software’s such as the worms and viruses which
may entangle and spread themselves via the internet. In many cases, this might be feasible when
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

it comes to the identification of such major external threats. However, there always exists a
possibility that a new unknown external threat will always arise.
Vulnerable Analysis.
Vulnerable analysis is referred to as how threats are supposed to be conceptualize in the context
of vulnerability. Vulnerability can be defined as the weaknesses which may be exploited in
future. A threat may not be important at all if the system is said to be not vulnerable to a given or
a specific threat.. A good example of such, in CommDev A threat may take an advantage to the
overflow of the buffer vulnerability which may be unique in Windows 95 which in other
organization may not be imported without using any version of Windows 95 (Microsoft, 2014).
Technical Vulnerabilities are one of the easiest when it comes to identification of vulnerabilities.
There are many vendors of computing and equipment’s used for networking which will always
be used to publish the bug’s bulletin and the associated vulnerabilities along with the patches
used for their products. There are some several websites which are known for maintaining
security advisories list about all the vulnerabilities known. Some of this websites are such as the
“http://www.securityfocus.com/archive/1” and “http://www.cert.org/advisories”. There are
several free and commercial scanners which are used for scanning tools in assessing the
operating system such as the SAINT, SARA, and Nessus among others. These commercial and
free software scanners may contain databases of vulnerabilities which are known and usually do
a system test by probing the possible vulnerabilities. Another method that is applied in
vulnerabilities discoveries in any system is the performance of a penetration testing which does
some simulation on the attacker actions. The conjecture is based on the attacks which are active
known for helping to reveal the weaknesses of the system defenses.
It is not in all cases that vulnerability technical or well-defined. Vulnerability may always arise
from security management. A good example is that the human resources at CommDev may be
insufficient in covering up of all the important responsibilities in the security, or the personnel
which has training which are insufficient. The policies which are set for insecurity management
may be unfinished, where the information system is exposed to probable optimizations. There
are other examples which are related to the system operations, for instance, supposing the
disposal of old Data CDs in to the trash which are accessed publicly. It may be easy for each
individual to retrieve the data which was discarded.
possibility that a new unknown external threat will always arise.
Vulnerable Analysis.
Vulnerable analysis is referred to as how threats are supposed to be conceptualize in the context
of vulnerability. Vulnerability can be defined as the weaknesses which may be exploited in
future. A threat may not be important at all if the system is said to be not vulnerable to a given or
a specific threat.. A good example of such, in CommDev A threat may take an advantage to the
overflow of the buffer vulnerability which may be unique in Windows 95 which in other
organization may not be imported without using any version of Windows 95 (Microsoft, 2014).
Technical Vulnerabilities are one of the easiest when it comes to identification of vulnerabilities.
There are many vendors of computing and equipment’s used for networking which will always
be used to publish the bug’s bulletin and the associated vulnerabilities along with the patches
used for their products. There are some several websites which are known for maintaining
security advisories list about all the vulnerabilities known. Some of this websites are such as the
“http://www.securityfocus.com/archive/1” and “http://www.cert.org/advisories”. There are
several free and commercial scanners which are used for scanning tools in assessing the
operating system such as the SAINT, SARA, and Nessus among others. These commercial and
free software scanners may contain databases of vulnerabilities which are known and usually do
a system test by probing the possible vulnerabilities. Another method that is applied in
vulnerabilities discoveries in any system is the performance of a penetration testing which does
some simulation on the attacker actions. The conjecture is based on the attacks which are active
known for helping to reveal the weaknesses of the system defenses.
It is not in all cases that vulnerability technical or well-defined. Vulnerability may always arise
from security management. A good example is that the human resources at CommDev may be
insufficient in covering up of all the important responsibilities in the security, or the personnel
which has training which are insufficient. The policies which are set for insecurity management
may be unfinished, where the information system is exposed to probable optimizations. There
are other examples which are related to the system operations, for instance, supposing the
disposal of old Data CDs in to the trash which are accessed publicly. It may be easy for each
individual to retrieve the data which was discarded.

Impact Analysis
The impact of the analyzed threats on CommDev organisation may depend on some of the
uncertain factors, likelihood of a threat occurring, successful threats causing a loss and the
frequency of threats recurring. Practically, the mentioned threats may be hard in estimating as
there are various ways through which an individual can do an estimation and thus combining the
impact analysis (NIST, 2013). The impact analysis can range from qualitative to quantitative
methods. It would be ideal for one to estimate the probability which is exact with regards to each
threat occurrence but in most cases, a rough approximate may be more credible and feasible.
Likelihood of the occurrence of a threat will depend on the nature of the threat. In analyzing the
human threats one has to consider the motivations of the attackers, their capabilities and the
resources. Nevertheless, in most cases an estimation might be used in classifying the threats into
three levels namely the unlikely, the moderately likely and those which are highly likely.
Risk Determination
For each and every threat, there is always a likelihood that it can be multiplied by the impacts in
which it can be used in determining the risk levels. The risk is equaled to that likelihood and the
impact. Risk= Likelihood*Impact. Some of the serious risks always possess both the likelihood
and the impacts which are very high. When there is a very low likelihood with regards to the
high impacts it may not be worth to be given any attention and likewise and vice versa while a
threat that is highly-likely to occur but has an impact which is low may be termed as less serious.
Based on the likelihood of the product and the associated impacts, a threat may be categorized to
different levels of threats. A good example of such is that simple classification of the threat of
CommDev may be of high, medium and low risk respectively. Another classification that may be
approached may obviously be possible on a scale of 0-10. The levels of risks may reflect on the
specific task priority. Risks which are high to occur are given highest priority and urgency in the
next risk management process. Risks which are medium should always be addressed by the risk
The impact of the analyzed threats on CommDev organisation may depend on some of the
uncertain factors, likelihood of a threat occurring, successful threats causing a loss and the
frequency of threats recurring. Practically, the mentioned threats may be hard in estimating as
there are various ways through which an individual can do an estimation and thus combining the
impact analysis (NIST, 2013). The impact analysis can range from qualitative to quantitative
methods. It would be ideal for one to estimate the probability which is exact with regards to each
threat occurrence but in most cases, a rough approximate may be more credible and feasible.
Likelihood of the occurrence of a threat will depend on the nature of the threat. In analyzing the
human threats one has to consider the motivations of the attackers, their capabilities and the
resources. Nevertheless, in most cases an estimation might be used in classifying the threats into
three levels namely the unlikely, the moderately likely and those which are highly likely.
Risk Determination
For each and every threat, there is always a likelihood that it can be multiplied by the impacts in
which it can be used in determining the risk levels. The risk is equaled to that likelihood and the
impact. Risk= Likelihood*Impact. Some of the serious risks always possess both the likelihood
and the impacts which are very high. When there is a very low likelihood with regards to the
high impacts it may not be worth to be given any attention and likewise and vice versa while a
threat that is highly-likely to occur but has an impact which is low may be termed as less serious.
Based on the likelihood of the product and the associated impacts, a threat may be categorized to
different levels of threats. A good example of such is that simple classification of the threat of
CommDev may be of high, medium and low risk respectively. Another classification that may be
approached may obviously be possible on a scale of 0-10. The levels of risks may reflect on the
specific task priority. Risks which are high to occur are given highest priority and urgency in the
next risk management process. Risks which are medium should always be addressed by the risk
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

mitigations but with a less urgency. Lastly is that the low risk are acceptable with or without
mitigation and they may be migrated even the resources are insufficient.
Risk Mitigation
This is safely assumed that CommDev has some limited resources in devoting to the security. It
may be infeasible for one to defend all the information against all the possible threats. There are
in some cases where there are is a certain risk levels being accepted. Mitigation is a process
where one strategically invest the resources which are limited in changing the risks which are
unacceptable in ones which are acceptable (Tomas, 2015). The technical changes involved are
such as security devices such as the cryptography, access controls, systems of intrusion
detection, backup’s devices, among others. When one is given an output for the processed risk
assessment, there is an assumption of the risk or mitigation of such risk. The assumption of the
risk refers to all the risks which are chosen and needs to be accepted. The risks which are
acceptable may be generally the low risks, but in a real sense,, there is need to do a careful
analysis on the cost-benefit which should be done in determining the risks that are to be
accepted. The following are some of the options when risk mitigations should be chosen.
1. Risk avoidance. This attempts in eliminating the cause of risks. A good example is when
one tries to eliminate the vulnerabilities and threat possibilities. A good example is the common
vulnerabilities which are remedied where the application of up-to-date patches are made.
2. Risk Limitation. This has been attempting the reduction of risks to levels which are
acceptable. This is done by implementation of controls which are used to reduce the impact and
the frequency expected. A good example is that the firewalls of CommDev and their access
controls are hardened in the manner that they will be so difficult for the attackers externally in
gaining the access to the organization network. The controls which are corrective may help in
reducing the attack effects. Detective controls may discover all the attacks and trigger all the
controls which are corrective (Boysone, 2010).
3. Risk transference. This may refer to the reassignment of the risk to other parties. In this
case, CommDev can use Insurance in reassigning its risks which will allow them in avoiding the
risk of potentially catastrophically losing all the exchanges of the fixed losses.
Risk Mitigation may be explained using the five steps which are explained as follows.
mitigation and they may be migrated even the resources are insufficient.
Risk Mitigation
This is safely assumed that CommDev has some limited resources in devoting to the security. It
may be infeasible for one to defend all the information against all the possible threats. There are
in some cases where there are is a certain risk levels being accepted. Mitigation is a process
where one strategically invest the resources which are limited in changing the risks which are
unacceptable in ones which are acceptable (Tomas, 2015). The technical changes involved are
such as security devices such as the cryptography, access controls, systems of intrusion
detection, backup’s devices, among others. When one is given an output for the processed risk
assessment, there is an assumption of the risk or mitigation of such risk. The assumption of the
risk refers to all the risks which are chosen and needs to be accepted. The risks which are
acceptable may be generally the low risks, but in a real sense,, there is need to do a careful
analysis on the cost-benefit which should be done in determining the risks that are to be
accepted. The following are some of the options when risk mitigations should be chosen.
1. Risk avoidance. This attempts in eliminating the cause of risks. A good example is when
one tries to eliminate the vulnerabilities and threat possibilities. A good example is the common
vulnerabilities which are remedied where the application of up-to-date patches are made.
2. Risk Limitation. This has been attempting the reduction of risks to levels which are
acceptable. This is done by implementation of controls which are used to reduce the impact and
the frequency expected. A good example is that the firewalls of CommDev and their access
controls are hardened in the manner that they will be so difficult for the attackers externally in
gaining the access to the organization network. The controls which are corrective may help in
reducing the attack effects. Detective controls may discover all the attacks and trigger all the
controls which are corrective (Boysone, 2010).
3. Risk transference. This may refer to the reassignment of the risk to other parties. In this
case, CommDev can use Insurance in reassigning its risks which will allow them in avoiding the
risk of potentially catastrophically losing all the exchanges of the fixed losses.
Risk Mitigation may be explained using the five steps which are explained as follows.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Actions prioritizations. All the risks with the associated corresponding levels if they are
identified through the process of assessment will be suggest the actions which are to be taken.
2. Identifying the possible controls. This step is for examining all the possible actions to be
applied in mitigating risks.
3. Cost-benefit analysis. In each organization, the main aim is to have benefits and in this
case, CommDev will do mitigation of risk as an exam of trading off between the expenses and
benefits all the related options used for controlling.
4. Select controls for all the implementation to be done. Previous explanation done on cost-
benefit was used in defining and deciding the controls to be applied in the implementation of
goals of the CommDev.
5. Assignment of responsibilities. Implementation of such will be depending on one person
with his or her appropriate skills. The personnel might be available in CommDev, but there are in
other cases such that the organization may opt to delegate its responsibilities to another party like
the way it has done with its corporate system via MicroForce. Another scenario where there have
delegated their web services to web services and hosting companies which have helped in them
updating their websites.
6. Implementation. The controls which are chosen must be implemented by the personnel
responsible for such tasks
Effective Evaluation
This is the process through which one can measure and verify all the risk objective which are
expected to be achieved. When assessment and mitigation risks which are discrete are done at
different times, the effectiveness of the evaluation in the process should simultaneously go on.
There are two practical reasons to as why this process exists in risk management.
Risk assessment may be entirely a science inexact. The related uncertainties to the real range of
threats, threats likelihood, their impacts, and frequency which is expected. In the risk process of
mitigation, there are some uncertainties in the cost estimation and the benefit associated with
each option of control. These uncertainties may result in one misjudging the plans of risk
mitigations. An assessment of either success or the failure in mitigation of risks plans is very
identified through the process of assessment will be suggest the actions which are to be taken.
2. Identifying the possible controls. This step is for examining all the possible actions to be
applied in mitigating risks.
3. Cost-benefit analysis. In each organization, the main aim is to have benefits and in this
case, CommDev will do mitigation of risk as an exam of trading off between the expenses and
benefits all the related options used for controlling.
4. Select controls for all the implementation to be done. Previous explanation done on cost-
benefit was used in defining and deciding the controls to be applied in the implementation of
goals of the CommDev.
5. Assignment of responsibilities. Implementation of such will be depending on one person
with his or her appropriate skills. The personnel might be available in CommDev, but there are in
other cases such that the organization may opt to delegate its responsibilities to another party like
the way it has done with its corporate system via MicroForce. Another scenario where there have
delegated their web services to web services and hosting companies which have helped in them
updating their websites.
6. Implementation. The controls which are chosen must be implemented by the personnel
responsible for such tasks
Effective Evaluation
This is the process through which one can measure and verify all the risk objective which are
expected to be achieved. When assessment and mitigation risks which are discrete are done at
different times, the effectiveness of the evaluation in the process should simultaneously go on.
There are two practical reasons to as why this process exists in risk management.
Risk assessment may be entirely a science inexact. The related uncertainties to the real range of
threats, threats likelihood, their impacts, and frequency which is expected. In the risk process of
mitigation, there are some uncertainties in the cost estimation and the benefit associated with
each option of control. These uncertainties may result in one misjudging the plans of risk
mitigations. An assessment of either success or the failure in mitigation of risks plans is very

much necessary. It offers provisions which are useful in giving feedback into the process which
will help in ensuring the correctness (Labuschagne, 2015).
Secondly, the environment of CommDev is not expected to remain static in any way. Over time
the organization such as CommDev network, computers, software platforms and personnel’s and
much more the policies all will change. Risk assessment and mitigation should be repeated and
updated simultaneously to help in keeping the system with the current status.
Conclusion.
Information security is an ongoing process which is used in managing of the risks. One may say
that risk management will be essential in making any decision in CommDev. Stages in the risk
assessment change are used and applied as the information collected as input and used when
making decisions. Mitigation of risks stage will be the actual decision making and implement the
strategy that results. Effectiveness evaluation is termed as the continual feedbacks into the
making of the decisions.
Although the methods which are currently used may have some room for improvement, the
management of risks may undoubtedly serve as a very valuable and the practical function for
CommDev. CommDev may be faced with needs which might be pressing such as the security
and risk management offering provisions of methods which are used in determining and
justifying the allocation of all the resources which are limited to needs of the security.
will help in ensuring the correctness (Labuschagne, 2015).
Secondly, the environment of CommDev is not expected to remain static in any way. Over time
the organization such as CommDev network, computers, software platforms and personnel’s and
much more the policies all will change. Risk assessment and mitigation should be repeated and
updated simultaneously to help in keeping the system with the current status.
Conclusion.
Information security is an ongoing process which is used in managing of the risks. One may say
that risk management will be essential in making any decision in CommDev. Stages in the risk
assessment change are used and applied as the information collected as input and used when
making decisions. Mitigation of risks stage will be the actual decision making and implement the
strategy that results. Effectiveness evaluation is termed as the continual feedbacks into the
making of the decisions.
Although the methods which are currently used may have some room for improvement, the
management of risks may undoubtedly serve as a very valuable and the practical function for
CommDev. CommDev may be faced with needs which might be pressing such as the security
and risk management offering provisions of methods which are used in determining and
justifying the allocation of all the resources which are limited to needs of the security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





