MGNT309 Cyber Security Report: Small Business Threats and Solutions
VerifiedAdded on 2023/05/30
|8
|1423
|253
Report
AI Summary
This report delves into the critical realm of cyber security, focusing on the vulnerabilities and challenges faced by small businesses. It begins with an executive summary highlighting the core issues and the increasing threat of cybercrime in today's digital landscape. The introduction emphasizes the importance of information system security and the risks associated with data breaches. The report then explores cyber security specifically for small businesses, detailing the risks they face, such as data integrity issues, malware, and financial losses. A key component of the report is a SWOT analysis, which evaluates the strengths, weaknesses, opportunities, and threats related to cyber security in small businesses. The report also discusses essential security concepts like password management, network monitoring, and data backup. Furthermore, it provides insights into selecting the right cyber security provider and the different security fields available, such as endpoint security and application security. The report concludes by reiterating the significant advantages of information technology for small businesses but also the associated costs and risks, emphasizing the importance of proactive cyber security measures, including SCADA systems, to mitigate these risks.
Running Head: CYBER SECURITY 0
Cyber Security
Report
Student name
Cyber Security
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 1
Table of Contents
Executive Summary.....................................................................................................................................2
Introduction.................................................................................................................................................3
Cyber security for small business................................................................................................................3
Table 1: SWOT analysis: Small businesses...........................................................................................4
The right fit for small business.....................................................................................................................5
Conclusion...................................................................................................................................................6
References...................................................................................................................................................6
Table of Contents
Executive Summary.....................................................................................................................................2
Introduction.................................................................................................................................................3
Cyber security for small business................................................................................................................3
Table 1: SWOT analysis: Small businesses...........................................................................................4
The right fit for small business.....................................................................................................................5
Conclusion...................................................................................................................................................6
References...................................................................................................................................................6

Cyber Security 2
Executive Summary
Cyber security is big concern for the small business in present scenario. Small businesses are
implement their operations on the computer networks, but it are also requires security from the cyber-
attacks. It will discuss about the security issues for the small business in this report. Cybercrime is
increasing day by day, still information systems are used by the different organization. This report will
explain about the cost effects and cyber security issues.
This report will discuss about understanding of strength and weaknesses of small business using
SWOT analysis. It is also discuss about the basic security concepts for prevention of cyber-attacks.
Executive Summary
Cyber security is big concern for the small business in present scenario. Small businesses are
implement their operations on the computer networks, but it are also requires security from the cyber-
attacks. It will discuss about the security issues for the small business in this report. Cybercrime is
increasing day by day, still information systems are used by the different organization. This report will
explain about the cost effects and cyber security issues.
This report will discuss about understanding of strength and weaknesses of small business using
SWOT analysis. It is also discuss about the basic security concepts for prevention of cyber-attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 3
Introduction
Business process are requires security from outsides, as they have confidential information. In
last two decades, many organization are uses information systems for handling different operations of
business. So it is a necessary task to secure there information system from outside attacks on their data.
Cyber security is main concern of organizations (Andrijcic & Horowitz, 2016). There are so many risk
factors in organization management. Information systems are already having so much cost, and if they
are hacked then it will be a great issue for the organization. A question arises that ‘is information
systems are an opportunity or a risk’ (Arlitsch & Edelman, 2014). In next part of this report, it will
discuss about the risk assessment, cyber security, and strength and weakness of business in context of
cyber security.
Cyber security for small business
Small businesses are facing so many problem of using information system, as they are not fully
protect from risks. Every business is requires help of computer systems, and other social media help for
promotion and business process. It is so critical condition, when an information system of small business
is crash from cyber-attacks. There are so many ways to break the security of an information system, if
they are not fully protected (Bhagat, 2012). Small businesses are crucial part of daily life of people in
different terms. Small businesses are connected from each other through the internet or LANs. It is for
betterment of business. However, there are risk issues of confidentiality, unlawful information
connected with their operations. With connection, becoming business requires to protect against cyber
security attacks like misuse of information, phishing attacks, and disseminating defamatory (Chen,
Chiang, & Storey, 2012).
Some issues are occurs in front of business are data integrity, frauds, malware, ransomware, and
reputation damage. Many organizations are having solution of these problems from the third party
organization. They provide different solutions for cyber security, such as monitoring, data analysis,
information management, and policies (Cherdantseva, Burnap, Blyth, Eden, & Jones, 2016).
There are some basic security concepts for prevention is:
Policies for accessing the system
Risk assessment
Introduction
Business process are requires security from outsides, as they have confidential information. In
last two decades, many organization are uses information systems for handling different operations of
business. So it is a necessary task to secure there information system from outside attacks on their data.
Cyber security is main concern of organizations (Andrijcic & Horowitz, 2016). There are so many risk
factors in organization management. Information systems are already having so much cost, and if they
are hacked then it will be a great issue for the organization. A question arises that ‘is information
systems are an opportunity or a risk’ (Arlitsch & Edelman, 2014). In next part of this report, it will
discuss about the risk assessment, cyber security, and strength and weakness of business in context of
cyber security.
Cyber security for small business
Small businesses are facing so many problem of using information system, as they are not fully
protect from risks. Every business is requires help of computer systems, and other social media help for
promotion and business process. It is so critical condition, when an information system of small business
is crash from cyber-attacks. There are so many ways to break the security of an information system, if
they are not fully protected (Bhagat, 2012). Small businesses are crucial part of daily life of people in
different terms. Small businesses are connected from each other through the internet or LANs. It is for
betterment of business. However, there are risk issues of confidentiality, unlawful information
connected with their operations. With connection, becoming business requires to protect against cyber
security attacks like misuse of information, phishing attacks, and disseminating defamatory (Chen,
Chiang, & Storey, 2012).
Some issues are occurs in front of business are data integrity, frauds, malware, ransomware, and
reputation damage. Many organizations are having solution of these problems from the third party
organization. They provide different solutions for cyber security, such as monitoring, data analysis,
information management, and policies (Cherdantseva, Burnap, Blyth, Eden, & Jones, 2016).
There are some basic security concepts for prevention is:
Policies for accessing the system
Risk assessment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 4
Identify secure and safe domains
Network monitoring
Classify confidential data
Protect all workstations
Educate workers
SWOT analysis is helpful for an organization to secure them from cyber-attacks.
Table 1: SWOT analysis: Small businesses
Strength Weakness Opportunity Threats
Organization status
Better Communication
Vendors information
Usability on daily
bases
Less controls
Not specific access
Less business
information
Improperly
monitoring
Can reach a new
customer
Can create best
marketing approach
Lack of trust
Unsafe platform
Malicious programs
Financial loss
Losing liability
Unaffordable cost
Policies for security
All the things are helping to business for securing there system from cyber-attacks. Cyber-crime
is increasing day by day, so it is most important thing for small business. There is a big problem, which is
cost of all these security essentials. In Large size business, there are proper system is managed for
monitoring all the activities from outsides, such as Supervisory Control and Data Acquisition (SCADA).
SCADA provides risk assessment of an organization from cyber-attacks (Gordon & Loeb, 2006).
Identify secure and safe domains
Network monitoring
Classify confidential data
Protect all workstations
Educate workers
SWOT analysis is helpful for an organization to secure them from cyber-attacks.
Table 1: SWOT analysis: Small businesses
Strength Weakness Opportunity Threats
Organization status
Better Communication
Vendors information
Usability on daily
bases
Less controls
Not specific access
Less business
information
Improperly
monitoring
Can reach a new
customer
Can create best
marketing approach
Lack of trust
Unsafe platform
Malicious programs
Financial loss
Losing liability
Unaffordable cost
Policies for security
All the things are helping to business for securing there system from cyber-attacks. Cyber-crime
is increasing day by day, so it is most important thing for small business. There is a big problem, which is
cost of all these security essentials. In Large size business, there are proper system is managed for
monitoring all the activities from outsides, such as Supervisory Control and Data Acquisition (SCADA).
SCADA provides risk assessment of an organization from cyber-attacks (Gordon & Loeb, 2006).
Cyber Security 5
Source: (Cherdantseva, Burnap, Blyth, Eden, & Jones, 2016)
In the diagram, security system is described with the help of different parts of an organization.
Basic security attacks are on the confidential data of the organization. Small business must follow few
concepts for cyber security, which are:
Password and authentication
Abstraction of Data and Controls
Secured Networks
Backup of all business data
Firewall security
The right fit for fictitious small business
Fictitious small business is required cyber security implementation for prevention of cyber-
attacks. First step is finding the best cyber security provider. Cyber security providers are providing best
security according to small businesses, which are beneficial for both parties. They provide latest tools for
prevention, monitoring and combat with cyber-attacks. It is just like part of small businesses. It is a
security division, which provides updates and bug reports.
Source: (Cherdantseva, Burnap, Blyth, Eden, & Jones, 2016)
In the diagram, security system is described with the help of different parts of an organization.
Basic security attacks are on the confidential data of the organization. Small business must follow few
concepts for cyber security, which are:
Password and authentication
Abstraction of Data and Controls
Secured Networks
Backup of all business data
Firewall security
The right fit for fictitious small business
Fictitious small business is required cyber security implementation for prevention of cyber-
attacks. First step is finding the best cyber security provider. Cyber security providers are providing best
security according to small businesses, which are beneficial for both parties. They provide latest tools for
prevention, monitoring and combat with cyber-attacks. It is just like part of small businesses. It is a
security division, which provides updates and bug reports.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 6
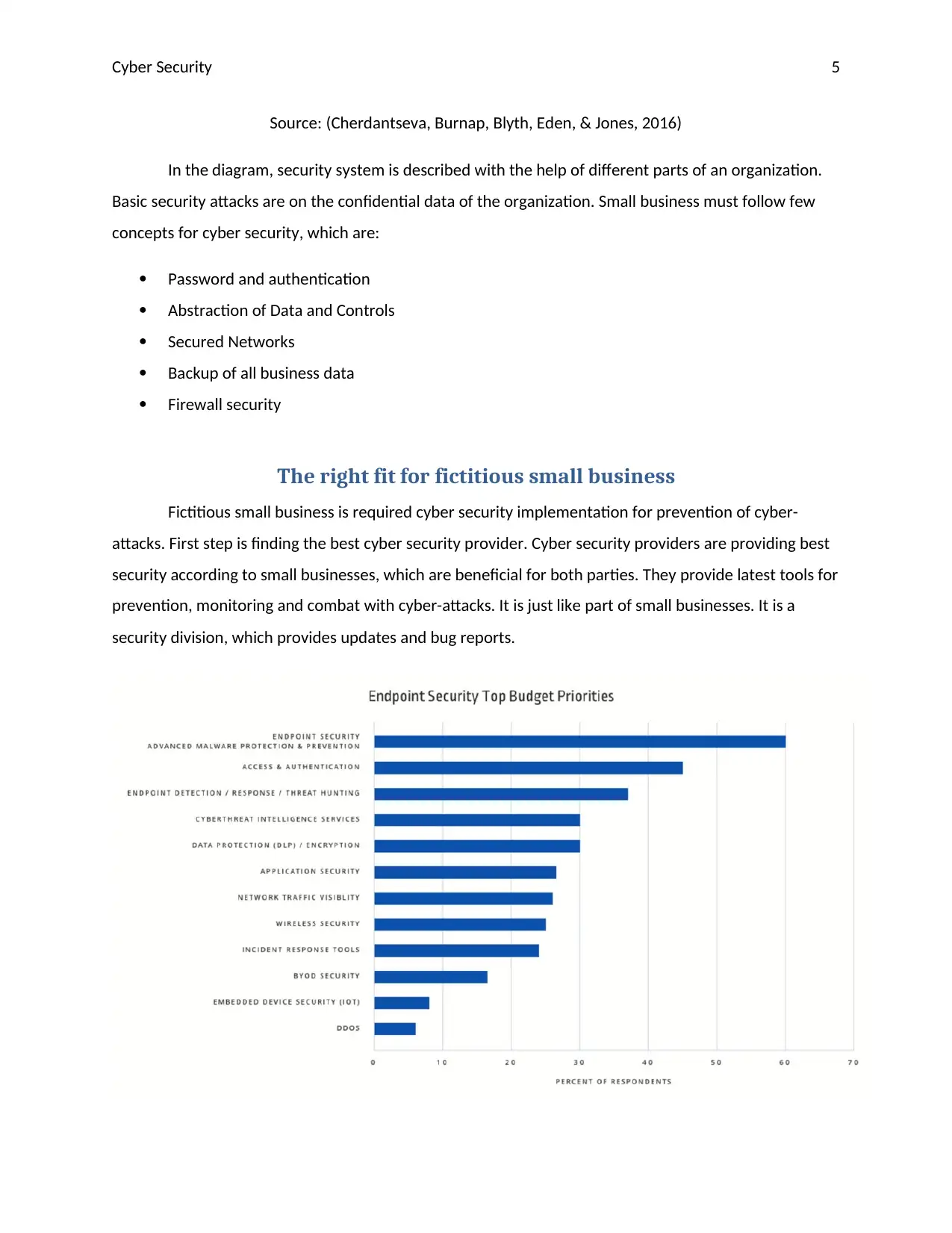
Source: (Barkly, 2018)
There are so many fields for acquiring security, such as Endpoint security, access and
authentication, data protection, application security, wireless security, and embedded device security.
All these fields are necessary to secure for securing business process.
There are basic concepts for security of computers and network of a company. It is also easy
process but it is cost effective for small businesses. Not all the small business has sufficient amount for
implantation of an information system but it was too expensive when they include customization cost
related to security of system and data (Von Solms & Van Niekerk, 2013).
Conclusion
It is concluded from the previous parts of this report that, Information technology is providing so
many advantages for small business, but it is costly and risky too. Lack of data integrity is increasing risk
of a small business. System is providing security but human activity is a high risk for the system.
SWOT analysis is providing indication about the risk of business, because of cyber-attacks. Cyber
security is most required thing for small business. Finally, it is concluded that SCADA is providing
different security solution from cybercrime.
Source: (Barkly, 2018)
There are so many fields for acquiring security, such as Endpoint security, access and
authentication, data protection, application security, wireless security, and embedded device security.
All these fields are necessary to secure for securing business process.
There are basic concepts for security of computers and network of a company. It is also easy
process but it is cost effective for small businesses. Not all the small business has sufficient amount for
implantation of an information system but it was too expensive when they include customization cost
related to security of system and data (Von Solms & Van Niekerk, 2013).
Conclusion
It is concluded from the previous parts of this report that, Information technology is providing so
many advantages for small business, but it is costly and risky too. Lack of data integrity is increasing risk
of a small business. System is providing security but human activity is a high risk for the system.
SWOT analysis is providing indication about the risk of business, because of cyber-attacks. Cyber
security is most required thing for small business. Finally, it is concluded that SCADA is providing
different security solution from cybercrime.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 7
References
Andrijcic, E., & Horowitz, B. (2016). A Macro Economic Framework for Evaluation of Cyber Security Risks‐
Related to Protection of Intellectual Property. Risk analysis, 26(4), 907-923.
Arlitsch, K., & Edelman, A. (2014). Staying safe: Cyber security for people and organizations. Journal of
Library Administration, 54(1), 46-56. Retrieved from
https://www.tandfonline.com/doi/abs/10.1080/01930826.2014.893116?journalCode=wjla20
Bhagat, B. (2012). Patent No. 13/016,999. U. S.
Chen, H., Chiang, R., & Storey, V. (2012). Business intelligence and analytics: from big data to big impact.
MIS quarterly, 1165-1188.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., & Jones, K. (2016). A review of cyber security risk
assessment methods for SCADA systems. Computers & security, 56, 1-27.
Gordon, L. A., & Loeb, M. (2006). Managing cybersecurity resources: a cost-benefit analysis (Vol. 1). New
York: McGraw-Hill.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security. computers &
security, 38, 97-102.
References
Andrijcic, E., & Horowitz, B. (2016). A Macro Economic Framework for Evaluation of Cyber Security Risks‐
Related to Protection of Intellectual Property. Risk analysis, 26(4), 907-923.
Arlitsch, K., & Edelman, A. (2014). Staying safe: Cyber security for people and organizations. Journal of
Library Administration, 54(1), 46-56. Retrieved from
https://www.tandfonline.com/doi/abs/10.1080/01930826.2014.893116?journalCode=wjla20
Bhagat, B. (2012). Patent No. 13/016,999. U. S.
Chen, H., Chiang, R., & Storey, V. (2012). Business intelligence and analytics: from big data to big impact.
MIS quarterly, 1165-1188.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., & Jones, K. (2016). A review of cyber security risk
assessment methods for SCADA systems. Computers & security, 56, 1-27.
Gordon, L. A., & Loeb, M. (2006). Managing cybersecurity resources: a cost-benefit analysis (Vol. 1). New
York: McGraw-Hill.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security. computers &
security, 38, 97-102.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





