Comprehensive Cybersecurity Report: Principles, Risks, and Ethics
VerifiedAdded on 2023/06/17
|6
|1800
|106
Report
AI Summary
This cybersecurity report provides a detailed analysis of key principles such as confidentiality, integrity, and availability, and their limitations in combating fake news. It discusses the 'run as administrator' option in Windows and its role-based access control model, emphasizing the impossibility of absolute security and the importance of user education in detecting malware. The report addresses the WannaCry ransomware attack, highlighting mitigation measures like regular OS updates and cautious online behavior. Furthermore, it evaluates the NIST cybersecurity framework for SCU, detailing risk assessment and management strategies for online systems, including identifying and prioritizing threats like online transaction theft, phishing attacks, ransomware, and DDoS attacks. The report also covers legal obligations such as the Spam Act 2003 and the Criminal Code Act 1995, emphasizing ethical behavior in cybersecurity to protect users and maintain data confidentiality. Desklib offers more solved assignments and resources for students.

CYBERSECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECTION A
A 1
Three main principles of information security cannot battle against fake news: this is
because information security is based upon its three principles that are confidentiality, integrity
and availability. Confidentiality can prevent unauthorized disclosure of information but cannot
prevent unauthorized publishing of information. Integrity can protect information against
unauthorised changes but cannot protect but cannot prevent uploading of fake news. Whereas
availability can help in making news fully available to its users but cannot prevent fake news
getting delivered or made available to users. Due to this reason main principles of information
cannot fails to battle against fake news. Not only this, these principles cannot prevent junk news
or fake news being uploaded and delivered to its users.
A 2
Option to run a program as administrator in windows is an available option in windows that can
be used when access rights to an object or a program are different for different users. All kinds of
administrative control and administrative rights of that object or program are given to owner only
and other users have restricted control over the program or object. So, situation in run a program
as administrator option is used when there is a need of requirement of accessing the program as
owner of the program such that any kind of changes can be done and other users can be
prevented from doing those changes. So it can be said that when users with different access to a
program are assigned then run a program as administrator option is used. Role-based access
control model is being implemented in windows for this purpose. It is a kind of non-discretionary
access control model that control access to any document.
A 3
Yes, I do agree with this statement that there no such thing like absolute security. Security
attacks do happen and it is extremely difficult to keep every computer safe from malware. It is
difficult to troubleshot and recover from an attack but it is even more difficult to prevent any
attack from happening. Due to this it is extremely important to educate each and every user about
some typical symptoms of presence of any kind of virus, malware, spyware present within their
computer system. It directly affects one’s decision as a security practitioner. As it is difficult to
achieve absolute security so as a security practitioner it is important to educate users of computer
symptoms about coon type of malware or attack that can happen and follow general but specific
1
A 1
Three main principles of information security cannot battle against fake news: this is
because information security is based upon its three principles that are confidentiality, integrity
and availability. Confidentiality can prevent unauthorized disclosure of information but cannot
prevent unauthorized publishing of information. Integrity can protect information against
unauthorised changes but cannot protect but cannot prevent uploading of fake news. Whereas
availability can help in making news fully available to its users but cannot prevent fake news
getting delivered or made available to users. Due to this reason main principles of information
cannot fails to battle against fake news. Not only this, these principles cannot prevent junk news
or fake news being uploaded and delivered to its users.
A 2
Option to run a program as administrator in windows is an available option in windows that can
be used when access rights to an object or a program are different for different users. All kinds of
administrative control and administrative rights of that object or program are given to owner only
and other users have restricted control over the program or object. So, situation in run a program
as administrator option is used when there is a need of requirement of accessing the program as
owner of the program such that any kind of changes can be done and other users can be
prevented from doing those changes. So it can be said that when users with different access to a
program are assigned then run a program as administrator option is used. Role-based access
control model is being implemented in windows for this purpose. It is a kind of non-discretionary
access control model that control access to any document.
A 3
Yes, I do agree with this statement that there no such thing like absolute security. Security
attacks do happen and it is extremely difficult to keep every computer safe from malware. It is
difficult to troubleshot and recover from an attack but it is even more difficult to prevent any
attack from happening. Due to this it is extremely important to educate each and every user about
some typical symptoms of presence of any kind of virus, malware, spyware present within their
computer system. It directly affects one’s decision as a security practitioner. As it is difficult to
achieve absolute security so as a security practitioner it is important to educate users of computer
symptoms about coon type of malware or attack that can happen and follow general but specific
1

steps of detecting and removing malware infection like identifying symptom, quarantine
infection, update anti-malware software, use scan and remove technique, restore windows and
educate use about the same.
A 4
WannaCry targeted Windows OS only because before this attack there were some security
patches in old OS of Windows that were removed in updated OS. These security patches were
created because an year before WannaCry attack, EternalBlue of NSA was stolen an year before
this attach that directly propagated through security of Windows OS.
In Ransomware attack files in the system are encrypted and ransom is demanded in exchange of
decryption key.
In order to protect organization from ransomware attack in future it is extremely important for
organization to update their operating system from time to time as this attach occurred only
because of non-updated operating systems. Mitigation measures useful for ransomware attach
are: they should update their software and operating system regularly, they should not click on
suspicious links, untrusted email attachments should not be opened, download from untrusted
websites should not be done, connection of unknown USB should not be done, installation of
security software should be done, backup of data should be taken regularly.
SECTION B
B 1
(a)
There are many different kinds of frameworks that can be used or adopted by SCU. One of
the most appropriate frameworks that can be adopted by SCU is NIST cybersecurity framework.
This framework is appropriate for SCU as it helps in providing guidance to both internal and
external stakeholders of origination for managing and reducing cybersecurity risk. This
framework further helps in providing guidance for conducting risk assessment as well. On the
basis of scenario, it has been identified that SCU requires a system that can protect organization
from cycler security threats. System of SCU would be used by different stakeholders including
visitors, employees and communication between all the campuses around Australia will also be
done.
As this system would be used by different internal and external stakeholders, usage of this
framework is more appropriate because adoption of this framework would eventually helps in
2
infection, update anti-malware software, use scan and remove technique, restore windows and
educate use about the same.
A 4
WannaCry targeted Windows OS only because before this attack there were some security
patches in old OS of Windows that were removed in updated OS. These security patches were
created because an year before WannaCry attack, EternalBlue of NSA was stolen an year before
this attach that directly propagated through security of Windows OS.
In Ransomware attack files in the system are encrypted and ransom is demanded in exchange of
decryption key.
In order to protect organization from ransomware attack in future it is extremely important for
organization to update their operating system from time to time as this attach occurred only
because of non-updated operating systems. Mitigation measures useful for ransomware attach
are: they should update their software and operating system regularly, they should not click on
suspicious links, untrusted email attachments should not be opened, download from untrusted
websites should not be done, connection of unknown USB should not be done, installation of
security software should be done, backup of data should be taken regularly.
SECTION B
B 1
(a)
There are many different kinds of frameworks that can be used or adopted by SCU. One of
the most appropriate frameworks that can be adopted by SCU is NIST cybersecurity framework.
This framework is appropriate for SCU as it helps in providing guidance to both internal and
external stakeholders of origination for managing and reducing cybersecurity risk. This
framework further helps in providing guidance for conducting risk assessment as well. On the
basis of scenario, it has been identified that SCU requires a system that can protect organization
from cycler security threats. System of SCU would be used by different stakeholders including
visitors, employees and communication between all the campuses around Australia will also be
done.
As this system would be used by different internal and external stakeholders, usage of this
framework is more appropriate because adoption of this framework would eventually helps in
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
providing cyber security to organization and would eventually help in protecting system from all
the stakeholders. Adoption of this framework would eventually help in providing protection to
the organization and their online system from threats that have been faced by organization such
as DDoS, ransomware attack, phasing attach etc. and would eventually help in making system
safe to b used by both employees and visitors. These requirements make it important to adopt
NIST cybersecurity framework so that network can be made safe to be used by internal
stakeholders (employees) and external stakeholders (visitors) so that all kinds of risk associated
with the network can be managed with existing guidelines, standards and practices defined by
this framework.
(b)
In order to initiate use of new online system it is extremely important to conduct a brief
risk assessment and management so that main types of risk associated with the new system and
ways in which it would be managed can be identified in an appropriate manner.
Risk identification
On the basis of previous history of attacks faced by SCU and new requirements of the
system, some of the main and common type of risk identified are:
Threat associated with online traction (financial damages)
Theft of online data of students, employees etc.
Phishing attack
Ransomware attack
Distributed DDoS attack
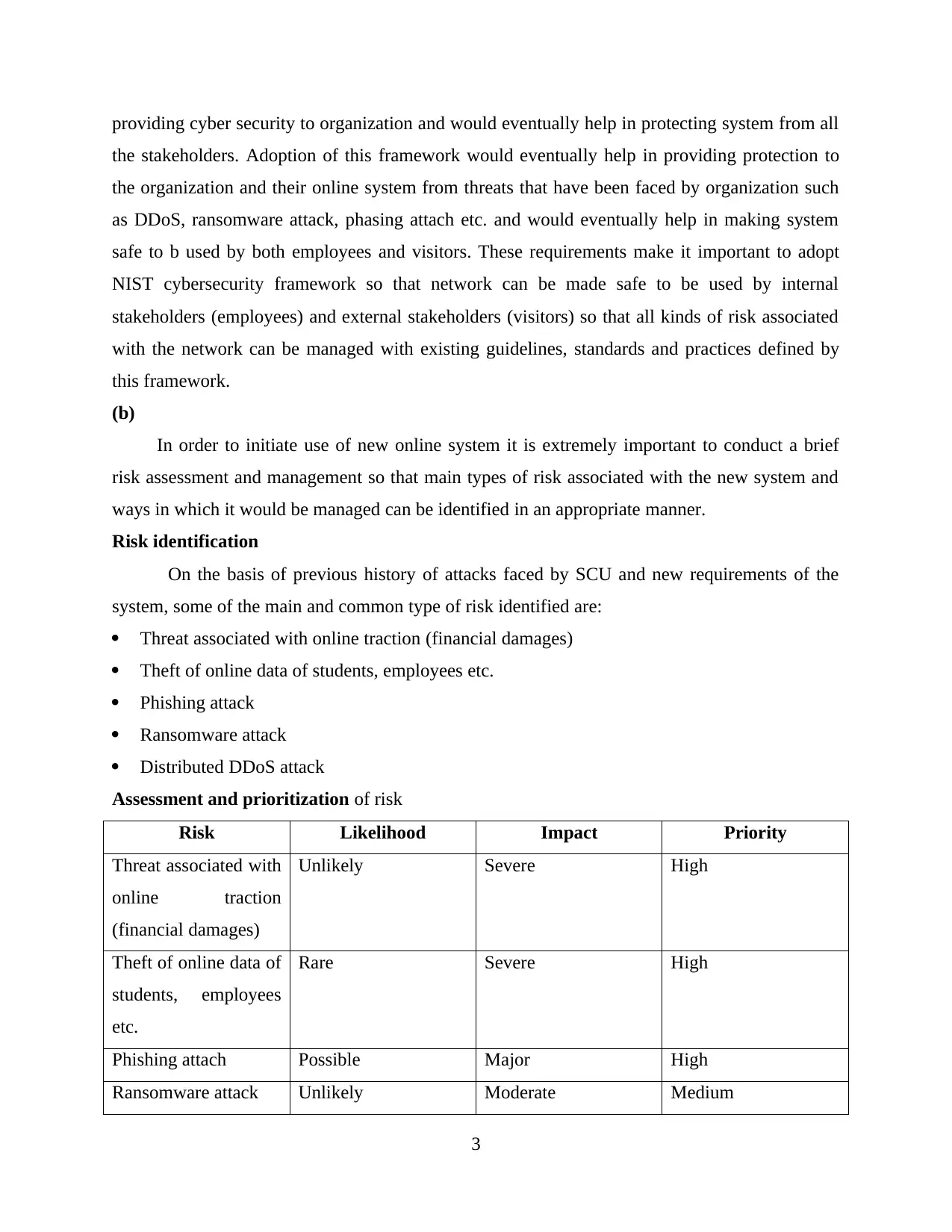
Assessment and prioritization of risk
Risk Likelihood Impact Priority
Threat associated with
online traction
(financial damages)
Unlikely Severe High
Theft of online data of
students, employees
etc.
Rare Severe High
Phishing attach Possible Major High
Ransomware attack Unlikely Moderate Medium
3
the stakeholders. Adoption of this framework would eventually help in providing protection to
the organization and their online system from threats that have been faced by organization such
as DDoS, ransomware attack, phasing attach etc. and would eventually help in making system
safe to b used by both employees and visitors. These requirements make it important to adopt
NIST cybersecurity framework so that network can be made safe to be used by internal
stakeholders (employees) and external stakeholders (visitors) so that all kinds of risk associated
with the network can be managed with existing guidelines, standards and practices defined by
this framework.
(b)
In order to initiate use of new online system it is extremely important to conduct a brief
risk assessment and management so that main types of risk associated with the new system and
ways in which it would be managed can be identified in an appropriate manner.
Risk identification
On the basis of previous history of attacks faced by SCU and new requirements of the
system, some of the main and common type of risk identified are:
Threat associated with online traction (financial damages)
Theft of online data of students, employees etc.
Phishing attack
Ransomware attack
Distributed DDoS attack
Assessment and prioritization of risk
Risk Likelihood Impact Priority
Threat associated with
online traction
(financial damages)
Unlikely Severe High
Theft of online data of
students, employees
etc.
Rare Severe High
Phishing attach Possible Major High
Ransomware attack Unlikely Moderate Medium
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Distributed DDoS
attack
Unlikely moderate Medium
Control risk
Following are some control measures that can be taken for resolving or managing
identified risk in an appropriate manner.
Défense: this control strategy can be used by organization for eliminating chances of
occurrence of Distributed DDoS stack, phishing attach, ransomware attack in an appropriate
manner. This can be done by adding additional defence, control and safeguarding method to
the online system such as: updating system regularly, using antivirus system or software,
developing a policy of not connecting any unknown device to the system. This control
measure is known as risk avoidance strategy.
Mitigation: this control measure can be used to mitigate chances of occurrence of
ransomware attack, online transaction theft and data security theft. This can be done with the
help of developing a contingency plan and preparing for the same. By keeping all the
software’s, operating system etc. updated and using third party security software for the
same.
B 3- Ethics, regulations, and laws
(a)
Some of the most important legal obligations that are important to be adhered and required to be
meet by SCU for cyber security are as follows:
Liability: organization is liable to pay or compensate their users for wrongful doing. It is
applicable even when no law to contract is applied. They are required to have strong ethical
code of conduct where organization is held liable for all kinds of wrongful doing.
Spam Act 2003: this legal obligation is required to be meet by SCU as under this act, SCU
need to meet all kinds of regulations associated with sending commercial emails and other
electronic message to their visitors vising their online website.
Telecommunications Act 1979: this act protects privacy of individuals who are using
telecommunication system. SCU need to meet this legal obligation and should ensure that
information of all the users of their online network (both visitors and employees) would be
kept confidential and their privacy would be respected.
4
attack
Unlikely moderate Medium
Control risk
Following are some control measures that can be taken for resolving or managing
identified risk in an appropriate manner.
Défense: this control strategy can be used by organization for eliminating chances of
occurrence of Distributed DDoS stack, phishing attach, ransomware attack in an appropriate
manner. This can be done by adding additional defence, control and safeguarding method to
the online system such as: updating system regularly, using antivirus system or software,
developing a policy of not connecting any unknown device to the system. This control
measure is known as risk avoidance strategy.
Mitigation: this control measure can be used to mitigate chances of occurrence of
ransomware attack, online transaction theft and data security theft. This can be done with the
help of developing a contingency plan and preparing for the same. By keeping all the
software’s, operating system etc. updated and using third party security software for the
same.
B 3- Ethics, regulations, and laws
(a)
Some of the most important legal obligations that are important to be adhered and required to be
meet by SCU for cyber security are as follows:
Liability: organization is liable to pay or compensate their users for wrongful doing. It is
applicable even when no law to contract is applied. They are required to have strong ethical
code of conduct where organization is held liable for all kinds of wrongful doing.
Spam Act 2003: this legal obligation is required to be meet by SCU as under this act, SCU
need to meet all kinds of regulations associated with sending commercial emails and other
electronic message to their visitors vising their online website.
Telecommunications Act 1979: this act protects privacy of individuals who are using
telecommunication system. SCU need to meet this legal obligation and should ensure that
information of all the users of their online network (both visitors and employees) would be
kept confidential and their privacy would be respected.
4

Criminal Code Act 1995: It is important for SCU to develop their online network in such a
manner that their users and organization themselves have access to safe online network
which is safe from DDoS stack, unauthorized modification of data, malicious hacking etc. as
all of these are criminal offences.
(b)
Ethical behaviour is related to cyber security in SCU because it can directly help in
providing protection to its users so that they can safely use their online network and in case of
any issue they can be compensated for the same. It further includes:
Ethical behaviours are moral principles that can help an organization in governing people’s
or employee’s behaviour. Ethics considerations that SCU should have are: data of its users
such as their financial information, personal information etc. should not be shared with
anyone and should be kept confidential. All the operational data which is required to be
shared should only be shared with respective department or person within organization and
with no one else.
Ethical behaviour is a kind of behaviour in which all kinds of social and cyber norms are
adopted by organizations and individuals and their actions are acceptable in public. Whereas
unethical behaviour is a kind of behaviour which is against social and cyber normal and this
kind of act is complete unacceptable by the society and public. This unethical behaviour can
further affect public or can harm them.
ethical behaviour is directly related to security positions within the SCU organisation because
ethical behaviour can directly help in setting some standard regulations and norms based
upon which organization and employees are required to behaviour. It would further help in
ensuring that none of the employee or top management of organization mishandle the
information and information of users is also protected.
5
manner that their users and organization themselves have access to safe online network
which is safe from DDoS stack, unauthorized modification of data, malicious hacking etc. as
all of these are criminal offences.
(b)
Ethical behaviour is related to cyber security in SCU because it can directly help in
providing protection to its users so that they can safely use their online network and in case of
any issue they can be compensated for the same. It further includes:
Ethical behaviours are moral principles that can help an organization in governing people’s
or employee’s behaviour. Ethics considerations that SCU should have are: data of its users
such as their financial information, personal information etc. should not be shared with
anyone and should be kept confidential. All the operational data which is required to be
shared should only be shared with respective department or person within organization and
with no one else.
Ethical behaviour is a kind of behaviour in which all kinds of social and cyber norms are
adopted by organizations and individuals and their actions are acceptable in public. Whereas
unethical behaviour is a kind of behaviour which is against social and cyber normal and this
kind of act is complete unacceptable by the society and public. This unethical behaviour can
further affect public or can harm them.
ethical behaviour is directly related to security positions within the SCU organisation because
ethical behaviour can directly help in setting some standard regulations and norms based
upon which organization and employees are required to behaviour. It would further help in
ensuring that none of the employee or top management of organization mishandle the
information and information of users is also protected.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





