Comprehensive Risk Assessment: Cyber Security Management T1 2022
VerifiedAdded on 2023/06/10
|13
|3482
|205
Report
AI Summary
This report provides a comprehensive risk assessment for cyber security management, covering key areas such as confidentiality, integrity, and accountability of IT assets. It discusses the implications of biometric cryptography, cyclic redundancy checksums, and blockchain technology in securing data. The report also examines President Biden's National Security Memorandum (NSM) for cybersecurity, APP 8 guidelines for cross-border data disclosure, the Protective Security Policy Framework (PSPF), and ISO/IEC 27000:2018 standards. Furthermore, it delves into emerging technologies like the Metaverse and biometric psychography, highlighting associated risks to data privacy and human rights, and explores initiatives by the Australian government to mitigate these issues. Desklib offers a platform for students to access similar solved assignments and study tools.

ASSESSMENT 2 CRITICAL
THINKING TASK 2 T12022
RISK ASSESSMENT FOR
CYBER SECURITY
MANAGEMENT
1
THINKING TASK 2 T12022
RISK ASSESSMENT FOR
CYBER SECURITY
MANAGEMENT
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENT
INTRODUCTION...........................................................................................................................4
MAIN BODY..................................................................................................................................4
TASK 1............................................................................................................................................4
Confidentiality, integrity and accountability...............................................................................4
TASK 2............................................................................................................................................7
1. What is it:.................................................................................................................................7
Explaining Section 2 that allow removing barriers to share confidential and threat information
between government and private sectors:....................................................................................7
Giving reasons why IT service providers could refuse detailed threat incident information with
some cyberattack mitigation agencies such as CISA, FBI, and IC?............................................7
2. What does APP 8 say? Listing 2 steps that allow recipient to avoid violating APP guideline:
.....................................................................................................................................................8
3. The Protective Security Policy Framework (PSPF) and core requirement:............................8
4. What is ISO/IEC 27000:2018:.................................................................................................8
TASK 3............................................................................................................................................9
1. What is Metaverse:..................................................................................................................9
2. What is biometric psychography.............................................................................................9
3. Data protection law:...............................................................................................................10
4. current law for biometric:......................................................................................................10
5. Initiatives taken by the Australian government to mitigate data privacy issue:....................11
2
INTRODUCTION...........................................................................................................................4
MAIN BODY..................................................................................................................................4
TASK 1............................................................................................................................................4
Confidentiality, integrity and accountability...............................................................................4
TASK 2............................................................................................................................................7
1. What is it:.................................................................................................................................7
Explaining Section 2 that allow removing barriers to share confidential and threat information
between government and private sectors:....................................................................................7
Giving reasons why IT service providers could refuse detailed threat incident information with
some cyberattack mitigation agencies such as CISA, FBI, and IC?............................................7
2. What does APP 8 say? Listing 2 steps that allow recipient to avoid violating APP guideline:
.....................................................................................................................................................8
3. The Protective Security Policy Framework (PSPF) and core requirement:............................8
4. What is ISO/IEC 27000:2018:.................................................................................................8
TASK 3............................................................................................................................................9
1. What is Metaverse:..................................................................................................................9
2. What is biometric psychography.............................................................................................9
3. Data protection law:...............................................................................................................10
4. current law for biometric:......................................................................................................10
5. Initiatives taken by the Australian government to mitigate data privacy issue:....................11
2

CONCLUSION..............................................................................................................................11
REFERENCES..............................................................................................................................13
3
REFERENCES..............................................................................................................................13
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTRODUCTION
Cyber security management refer as the corporation strategic level ability that aims to
protect the information and other resources from being theft or from other malicious activities
(Nobles, 2018). Its management helps in preventing the sensitive data and other personal
information from being misuse by hackers or cyber attackers. Information technology asset refer
to the technologies and hardware, data communication lines etc. these can be utilised in making
the strategic decisions. Following report will cover the tasks that highlights the identification of
the asset that are related to confidentiality, integrity and accountability. Furthermore it will cover
the discussion over the biden’s cybersecurity executive and description of metaverse, biometric
psychography and so on.
MAIN BODY
TASK 1
Confidentiality, integrity and accountability
Confidentiality refer as the core concept in the cyber security, simply it ensures that the sensitive
or other data is protected and secured from any unauthorised disclosure. Protecting or securing
the confidentiality is the major responsibility of the technologist and others within the
organisation (Spremić and Šimunic, 2018). Violation of confidentiality can give the negative
impact over the business as well as it gives the advantage to other business rivalries. Integrity
define as the data in the system is managed and maintained, so that it cannot be upgraded and
modified by the attackers or unauthorised parties. It is the important aspect for maintaining the
reliability and accuracy in the data. Accountability gives the legitimacy to organisation, it helps
in preventing the corruption and to ensure the better governance. As in cyber security, security
aims that develops the needs for the actions about the entity to be track uniquely. It cooperates
with non-repudiation, isolation, intrusion identification (Aldawood and Skinner, 2018).
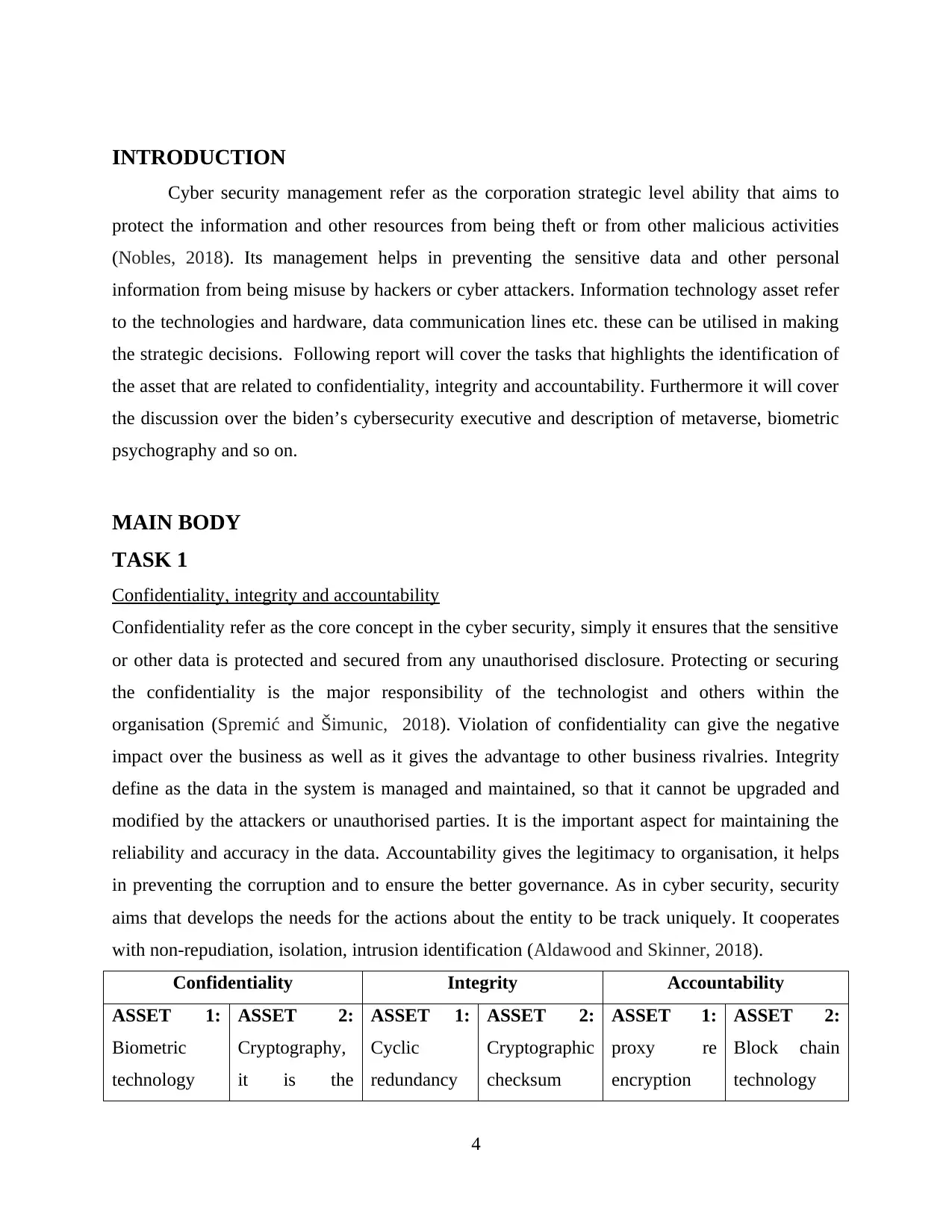
Confidentiality Integrity Accountability
ASSET 1:
Biometric
technology
ASSET 2:
Cryptography,
it is the
ASSET 1:
Cyclic
redundancy
ASSET 2:
Cryptographic
checksum
ASSET 1:
proxy re
encryption
ASSET 2:
Block chain
technology
4
Cyber security management refer as the corporation strategic level ability that aims to
protect the information and other resources from being theft or from other malicious activities
(Nobles, 2018). Its management helps in preventing the sensitive data and other personal
information from being misuse by hackers or cyber attackers. Information technology asset refer
to the technologies and hardware, data communication lines etc. these can be utilised in making
the strategic decisions. Following report will cover the tasks that highlights the identification of
the asset that are related to confidentiality, integrity and accountability. Furthermore it will cover
the discussion over the biden’s cybersecurity executive and description of metaverse, biometric
psychography and so on.
MAIN BODY
TASK 1
Confidentiality, integrity and accountability
Confidentiality refer as the core concept in the cyber security, simply it ensures that the sensitive
or other data is protected and secured from any unauthorised disclosure. Protecting or securing
the confidentiality is the major responsibility of the technologist and others within the
organisation (Spremić and Šimunic, 2018). Violation of confidentiality can give the negative
impact over the business as well as it gives the advantage to other business rivalries. Integrity
define as the data in the system is managed and maintained, so that it cannot be upgraded and
modified by the attackers or unauthorised parties. It is the important aspect for maintaining the
reliability and accuracy in the data. Accountability gives the legitimacy to organisation, it helps
in preventing the corruption and to ensure the better governance. As in cyber security, security
aims that develops the needs for the actions about the entity to be track uniquely. It cooperates
with non-repudiation, isolation, intrusion identification (Aldawood and Skinner, 2018).
Confidentiality Integrity Accountability
ASSET 1:
Biometric
technology
ASSET 2:
Cryptography,
it is the
ASSET 1:
Cyclic
redundancy
ASSET 2:
Cryptographic
checksum
ASSET 1:
proxy re
encryption
ASSET 2:
Block chain
technology
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
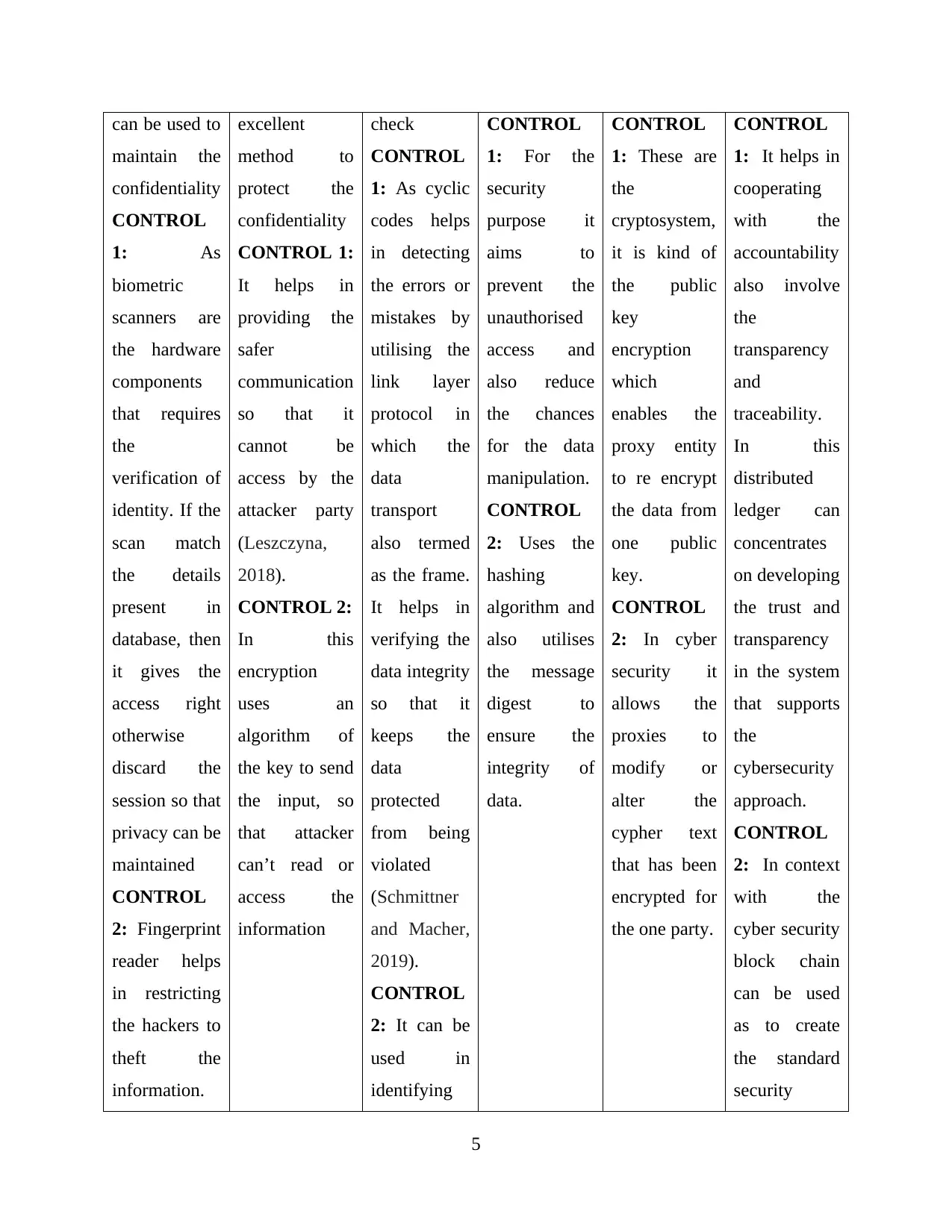
can be used to
maintain the
confidentiality
CONTROL
1: As
biometric
scanners are
the hardware
components
that requires
the
verification of
identity. If the
scan match
the details
present in
database, then
it gives the
access right
otherwise
discard the
session so that
privacy can be
maintained
CONTROL
2: Fingerprint
reader helps
in restricting
the hackers to
theft the
information.
excellent
method to
protect the
confidentiality
CONTROL 1:
It helps in
providing the
safer
communication
so that it
cannot be
access by the
attacker party
(Leszczyna,
2018).
CONTROL 2:
In this
encryption
uses an
algorithm of
the key to send
the input, so
that attacker
can’t read or
access the
information
check
CONTROL
1: As cyclic
codes helps
in detecting
the errors or
mistakes by
utilising the
link layer
protocol in
which the
data
transport
also termed
as the frame.
It helps in
verifying the
data integrity
so that it
keeps the
data
protected
from being
violated
(Schmittner
and Macher,
2019).
CONTROL
2: It can be
used in
identifying
CONTROL
1: For the
security
purpose it
aims to
prevent the
unauthorised
access and
also reduce
the chances
for the data
manipulation.
CONTROL
2: Uses the
hashing
algorithm and
also utilises
the message
digest to
ensure the
integrity of
data.
CONTROL
1: These are
the
cryptosystem,
it is kind of
the public
key
encryption
which
enables the
proxy entity
to re encrypt
the data from
one public
key.
CONTROL
2: In cyber
security it
allows the
proxies to
modify or
alter the
cypher text
that has been
encrypted for
the one party.
CONTROL
1: It helps in
cooperating
with the
accountability
also involve
the
transparency
and
traceability.
In this
distributed
ledger can
concentrates
on developing
the trust and
transparency
in the system
that supports
the
cybersecurity
approach.
CONTROL
2: In context
with the
cyber security
block chain
can be used
as to create
the standard
security
5
maintain the
confidentiality
CONTROL
1: As
biometric
scanners are
the hardware
components
that requires
the
verification of
identity. If the
scan match
the details
present in
database, then
it gives the
access right
otherwise
discard the
session so that
privacy can be
maintained
CONTROL
2: Fingerprint
reader helps
in restricting
the hackers to
theft the
information.
excellent
method to
protect the
confidentiality
CONTROL 1:
It helps in
providing the
safer
communication
so that it
cannot be
access by the
attacker party
(Leszczyna,
2018).
CONTROL 2:
In this
encryption
uses an
algorithm of
the key to send
the input, so
that attacker
can’t read or
access the
information
check
CONTROL
1: As cyclic
codes helps
in detecting
the errors or
mistakes by
utilising the
link layer
protocol in
which the
data
transport
also termed
as the frame.
It helps in
verifying the
data integrity
so that it
keeps the
data
protected
from being
violated
(Schmittner
and Macher,
2019).
CONTROL
2: It can be
used in
identifying
CONTROL
1: For the
security
purpose it
aims to
prevent the
unauthorised
access and
also reduce
the chances
for the data
manipulation.
CONTROL
2: Uses the
hashing
algorithm and
also utilises
the message
digest to
ensure the
integrity of
data.
CONTROL
1: These are
the
cryptosystem,
it is kind of
the public
key
encryption
which
enables the
proxy entity
to re encrypt
the data from
one public
key.
CONTROL
2: In cyber
security it
allows the
proxies to
modify or
alter the
cypher text
that has been
encrypted for
the one party.
CONTROL
1: It helps in
cooperating
with the
accountability
also involve
the
transparency
and
traceability.
In this
distributed
ledger can
concentrates
on developing
the trust and
transparency
in the system
that supports
the
cybersecurity
approach.
CONTROL
2: In context
with the
cyber security
block chain
can be used
as to create
the standard
security
5
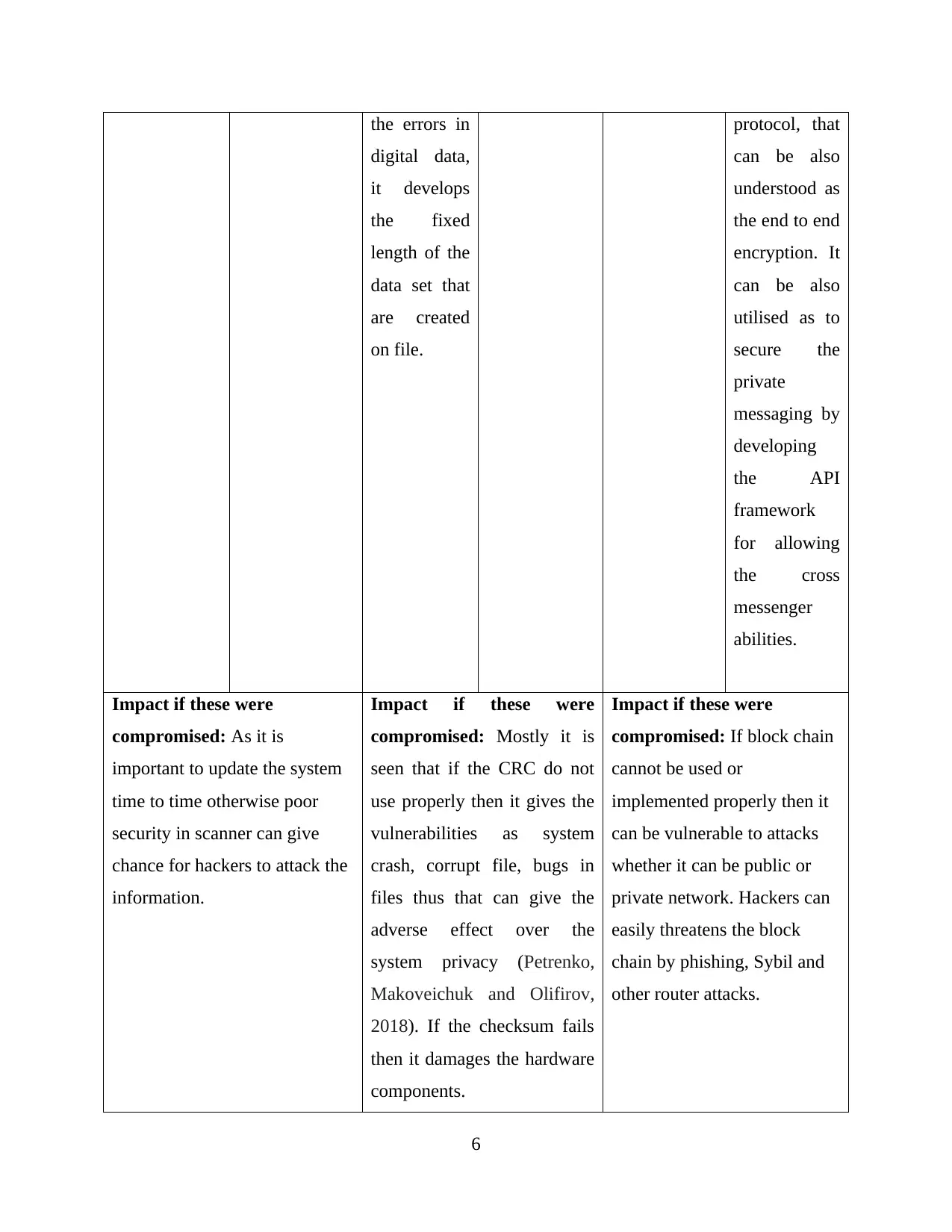
the errors in
digital data,
it develops
the fixed
length of the
data set that
are created
on file.
protocol, that
can be also
understood as
the end to end
encryption. It
can be also
utilised as to
secure the
private
messaging by
developing
the API
framework
for allowing
the cross
messenger
abilities.
Impact if these were
compromised: As it is
important to update the system
time to time otherwise poor
security in scanner can give
chance for hackers to attack the
information.
Impact if these were
compromised: Mostly it is
seen that if the CRC do not
use properly then it gives the
vulnerabilities as system
crash, corrupt file, bugs in
files thus that can give the
adverse effect over the
system privacy (Petrenko,
Makoveichuk and Olifirov,
2018). If the checksum fails
then it damages the hardware
components.
Impact if these were
compromised: If block chain
cannot be used or
implemented properly then it
can be vulnerable to attacks
whether it can be public or
private network. Hackers can
easily threatens the block
chain by phishing, Sybil and
other router attacks.
6
digital data,
it develops
the fixed
length of the
data set that
are created
on file.
protocol, that
can be also
understood as
the end to end
encryption. It
can be also
utilised as to
secure the
private
messaging by
developing
the API
framework
for allowing
the cross
messenger
abilities.
Impact if these were
compromised: As it is
important to update the system
time to time otherwise poor
security in scanner can give
chance for hackers to attack the
information.
Impact if these were
compromised: Mostly it is
seen that if the CRC do not
use properly then it gives the
vulnerabilities as system
crash, corrupt file, bugs in
files thus that can give the
adverse effect over the
system privacy (Petrenko,
Makoveichuk and Olifirov,
2018). If the checksum fails
then it damages the hardware
components.
Impact if these were
compromised: If block chain
cannot be used or
implemented properly then it
can be vulnerable to attacks
whether it can be public or
private network. Hackers can
easily threatens the block
chain by phishing, Sybil and
other router attacks.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
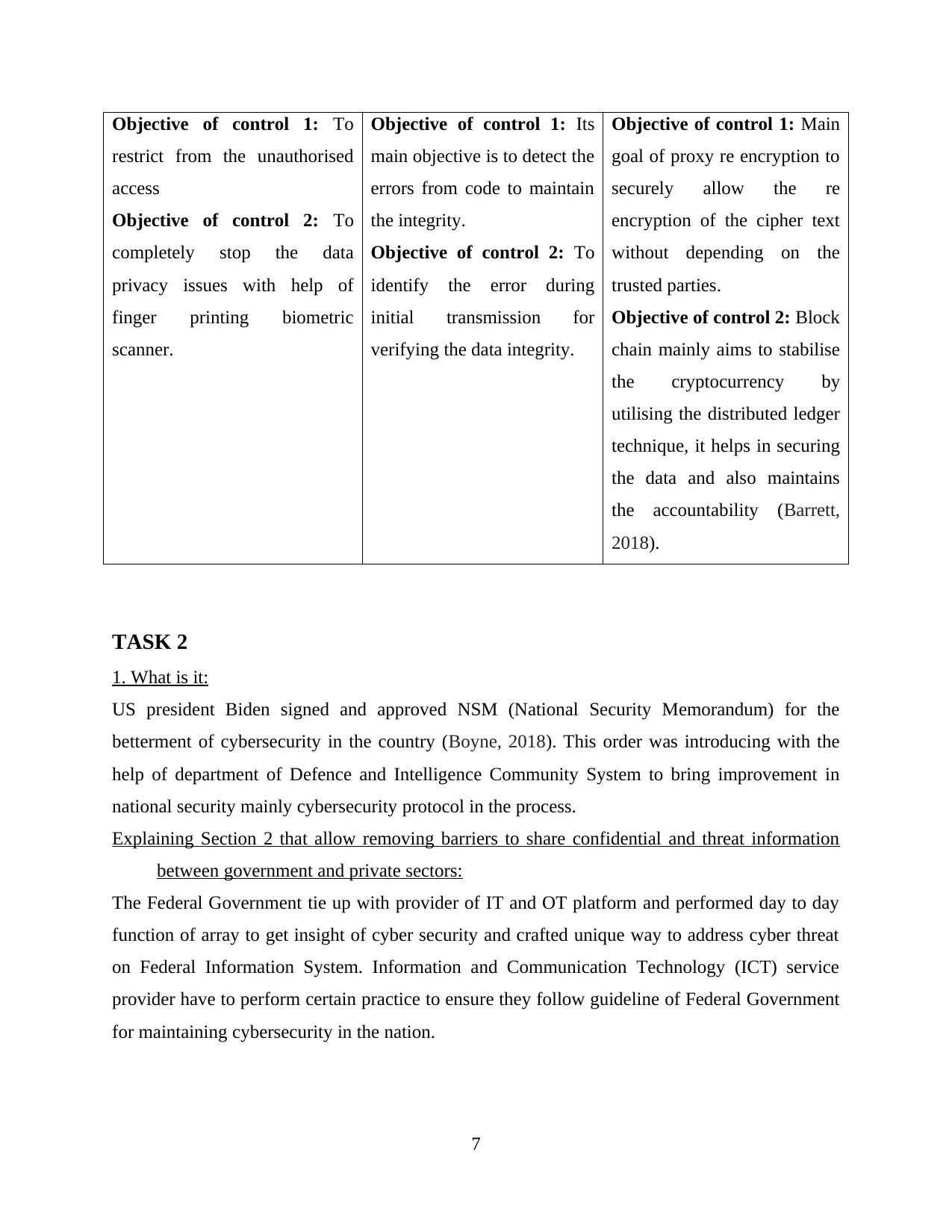
Objective of control 1: To
restrict from the unauthorised
access
Objective of control 2: To
completely stop the data
privacy issues with help of
finger printing biometric
scanner.
Objective of control 1: Its
main objective is to detect the
errors from code to maintain
the integrity.
Objective of control 2: To
identify the error during
initial transmission for
verifying the data integrity.
Objective of control 1: Main
goal of proxy re encryption to
securely allow the re
encryption of the cipher text
without depending on the
trusted parties.
Objective of control 2: Block
chain mainly aims to stabilise
the cryptocurrency by
utilising the distributed ledger
technique, it helps in securing
the data and also maintains
the accountability (Barrett,
2018).
TASK 2
1. What is it:
US president Biden signed and approved NSM (National Security Memorandum) for the
betterment of cybersecurity in the country (Boyne, 2018). This order was introducing with the
help of department of Defence and Intelligence Community System to bring improvement in
national security mainly cybersecurity protocol in the process.
Explaining Section 2 that allow removing barriers to share confidential and threat information
between government and private sectors:
The Federal Government tie up with provider of IT and OT platform and performed day to day
function of array to get insight of cyber security and crafted unique way to address cyber threat
on Federal Information System. Information and Communication Technology (ICT) service
provider have to perform certain practice to ensure they follow guideline of Federal Government
for maintaining cybersecurity in the nation.
7
restrict from the unauthorised
access
Objective of control 2: To
completely stop the data
privacy issues with help of
finger printing biometric
scanner.
Objective of control 1: Its
main objective is to detect the
errors from code to maintain
the integrity.
Objective of control 2: To
identify the error during
initial transmission for
verifying the data integrity.
Objective of control 1: Main
goal of proxy re encryption to
securely allow the re
encryption of the cipher text
without depending on the
trusted parties.
Objective of control 2: Block
chain mainly aims to stabilise
the cryptocurrency by
utilising the distributed ledger
technique, it helps in securing
the data and also maintains
the accountability (Barrett,
2018).
TASK 2
1. What is it:
US president Biden signed and approved NSM (National Security Memorandum) for the
betterment of cybersecurity in the country (Boyne, 2018). This order was introducing with the
help of department of Defence and Intelligence Community System to bring improvement in
national security mainly cybersecurity protocol in the process.
Explaining Section 2 that allow removing barriers to share confidential and threat information
between government and private sectors:
The Federal Government tie up with provider of IT and OT platform and performed day to day
function of array to get insight of cyber security and crafted unique way to address cyber threat
on Federal Information System. Information and Communication Technology (ICT) service
provider have to perform certain practice to ensure they follow guideline of Federal Government
for maintaining cybersecurity in the nation.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Giving reasons why IT service providers could refuse detailed threat incident information with
some cyberattack mitigation agencies such as CISA, FBI, and IC?
IT service provider can uphold detailed threat incident information with CISA, FBI and IC when
they have confidential information, these IT providers have to report to one of agency including
CISA, FBI and IC for further process. IT provider must directly report any threat incident
information to CISA for further investigation, IT service provider cannot deny to work with any
of agency for maintaining cybersecurity.
2. What does APP 8 say? Listing 2 steps that allow recipient to avoid violating APP guideline:
Under Privacy Act 1988, there are some principle guideline, APP 8, highlight cross border
disclosure of personal and confidential information (Walters, Trakman and Zeller, 2019). APP 8
simply provide framework that allow oversea recipient to avoid any kind of illegal activity and
ensure they carefully handle and manage personal information, APP 8.1 highlight APP entity to
take responsibility to ensure cross border recipient does not breach guideline of APP and perform
their work in legal manner, there are two steps;
Providing limited information to oversea recipient to ensure they avoid breaching APP
guideline.
Cross reference will be required for oversea disclosure of personal information in APP 8.
3. The Protective Security Policy Framework (PSPF) and core requirement:
Each entity need to have security plan that need to be approved by accountable authority to
handle security risk of the entity, this plan may include core requirement, these are:
Crafting security goals according to risk management intersect which help and support
wider business objectives.
Plan must highlight threat, risk and vulnerabilities that might impact people and their
information and assets.
Entity must have tolerance to manage security risk and capabilities to drive better result
even after risk impact.
Entity need to have positive risk culture and proper security risk management plan and
delivery against PSPF process.
4. What is ISO/IEC 27000:2018:
ISO/IEC 27000:2018 provide details of information security management system (ISMS),
this framework provides details of terms and condition that focus on ISMS family of standard.
8
some cyberattack mitigation agencies such as CISA, FBI, and IC?
IT service provider can uphold detailed threat incident information with CISA, FBI and IC when
they have confidential information, these IT providers have to report to one of agency including
CISA, FBI and IC for further process. IT provider must directly report any threat incident
information to CISA for further investigation, IT service provider cannot deny to work with any
of agency for maintaining cybersecurity.
2. What does APP 8 say? Listing 2 steps that allow recipient to avoid violating APP guideline:
Under Privacy Act 1988, there are some principle guideline, APP 8, highlight cross border
disclosure of personal and confidential information (Walters, Trakman and Zeller, 2019). APP 8
simply provide framework that allow oversea recipient to avoid any kind of illegal activity and
ensure they carefully handle and manage personal information, APP 8.1 highlight APP entity to
take responsibility to ensure cross border recipient does not breach guideline of APP and perform
their work in legal manner, there are two steps;
Providing limited information to oversea recipient to ensure they avoid breaching APP
guideline.
Cross reference will be required for oversea disclosure of personal information in APP 8.
3. The Protective Security Policy Framework (PSPF) and core requirement:
Each entity need to have security plan that need to be approved by accountable authority to
handle security risk of the entity, this plan may include core requirement, these are:
Crafting security goals according to risk management intersect which help and support
wider business objectives.
Plan must highlight threat, risk and vulnerabilities that might impact people and their
information and assets.
Entity must have tolerance to manage security risk and capabilities to drive better result
even after risk impact.
Entity need to have positive risk culture and proper security risk management plan and
delivery against PSPF process.
4. What is ISO/IEC 27000:2018:
ISO/IEC 27000:2018 provide details of information security management system (ISMS),
this framework provides details of terms and condition that focus on ISMS family of standard.
8

ISO/IEC 27000:2018 is applicable to every type of organization including commercial,
government and non-commercial enterprise, there are certain controls to measure data breach of
oversea recipient, these are:
Authentication: This will allow oversea recipient to avoid data breach, under ISO/IEC
27000:2018, authentication become important.
Encryption: According to ISO/IEC 27000:2018, entity need to provide encryption to
oversea breaching of personal information.
Update software: Entity need to have updated software to ensure oversea recipient do
not breach any information and maintain legal process.
TASK 3
1. What is Metaverse:
Metaverse is graphical rich virtual space, this is network of 3D world that allow people to
perform certain task including interacting with things or place, play certain virtual games, social
connection and even can perform business with the help of Metaverse. This is future of software
technology where people enjoy to connect themselves with unreal world with real world
activities (Ryz and Grest, 2016). Each user of Metaverse have to develop an avatar that allow
them to enter virtual world and practice certain thing, this can be seen in social media platform
where user gain those experience which is not been experienced before. However, Metaverse
create substantial risk to human right, this may be future of technology and social media but this
breach human right and at some point this
, these are:
Confidentiality and privacy: Every human have right to privacy where entity who
provide Metaverse need to ensure privacy of its user but major risk is associated when
entity focus on profit over privacy. Metaverse platform can leak data of user and sell it to
third party for surplus profit and violate right to confidentiality and privacy.
Online harassment: Human have right to be safe in the world and stand against
harassment, with the use of Metaverse, online harassment can be seen where user get
harassed by other virtual user while using these platforms.
2. What is biometric psychography
Biometric psychography is one of the new term in technological world, this simply means
biometric form of individual’s taste and preference, likes and interest and other psychological
9
government and non-commercial enterprise, there are certain controls to measure data breach of
oversea recipient, these are:
Authentication: This will allow oversea recipient to avoid data breach, under ISO/IEC
27000:2018, authentication become important.
Encryption: According to ISO/IEC 27000:2018, entity need to provide encryption to
oversea breaching of personal information.
Update software: Entity need to have updated software to ensure oversea recipient do
not breach any information and maintain legal process.
TASK 3
1. What is Metaverse:
Metaverse is graphical rich virtual space, this is network of 3D world that allow people to
perform certain task including interacting with things or place, play certain virtual games, social
connection and even can perform business with the help of Metaverse. This is future of software
technology where people enjoy to connect themselves with unreal world with real world
activities (Ryz and Grest, 2016). Each user of Metaverse have to develop an avatar that allow
them to enter virtual world and practice certain thing, this can be seen in social media platform
where user gain those experience which is not been experienced before. However, Metaverse
create substantial risk to human right, this may be future of technology and social media but this
breach human right and at some point this
, these are:
Confidentiality and privacy: Every human have right to privacy where entity who
provide Metaverse need to ensure privacy of its user but major risk is associated when
entity focus on profit over privacy. Metaverse platform can leak data of user and sell it to
third party for surplus profit and violate right to confidentiality and privacy.
Online harassment: Human have right to be safe in the world and stand against
harassment, with the use of Metaverse, online harassment can be seen where user get
harassed by other virtual user while using these platforms.
2. What is biometric psychography
Biometric psychography is one of the new term in technological world, this simply means
biometric form of individual’s taste and preference, likes and interest and other psychological
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

needs of individual. Biometric data may contain private thoughts and feeling, data is been
collected by XR devices to understand new form of biometric psychography that provide in
depth details of desire and inclination (Meurisch and Mühlhäuser, 2021). It is very clear that
Metaverse is unreal world where virtually element is being described, Metaverse impact
physiological response of human brain and allow them to become weak in body process,
biometric psychography impact real life response of human body to situation. Metaverse is
dangerous for human mind as this can impact their real life activity.
3. Data protection law:
The Data Protection Act 1988 is one of the most common but important law in Australia that
define protection of data and personal information, every sensitive and confidential data is been
protected under this law as organization have to protected personal information of their customer
including personal details like name, contact details and address. Office of the Australian
Information Commissioner (OAIC) play vital role in protecting data of individual, if any
personal information or data is breached then OAIC will act an agent to protect individual and
continue further investigation (Joyce, 2017). Under The Data Protection Act 1988, there are
certain Australian Privacy Principle (APP) that have great role in ensuring sensitive data is been
protected. Every individual has their own right to get protected against data breach, there is
another legislation process in the Australia. Privacy Regulation 2013 provide regulation to those
organizations that contain information of client for business purpose, with the help of OAIC any
these regulations as responsible to bring down breaches of data.
4. current law for biometric:
Biometric is one of the common technology that is been used in human verification process
where individual identify and personal data has been used to allow them access, biometric
psychography is new technology in Metaverse, this simply means collection of biometric data of
user. Under General Data Protection Regulation (GDPR) there are some regulation that drive use
of biometric data, GDPR took step forward to protect and prevent data breach occur due to
biometric psychography (Hoofnagle and et.al., 2019). However, there is no international law that
define biometric data and regulate them, apart from GDPR, Federal law of US define collection
and use of biometric data but do not regulate any law to control these data. Although, CISA take
certain measure to keep eye on biometric psychography, there are certain gaps, these are:
Leak of information.
10
collected by XR devices to understand new form of biometric psychography that provide in
depth details of desire and inclination (Meurisch and Mühlhäuser, 2021). It is very clear that
Metaverse is unreal world where virtually element is being described, Metaverse impact
physiological response of human brain and allow them to become weak in body process,
biometric psychography impact real life response of human body to situation. Metaverse is
dangerous for human mind as this can impact their real life activity.
3. Data protection law:
The Data Protection Act 1988 is one of the most common but important law in Australia that
define protection of data and personal information, every sensitive and confidential data is been
protected under this law as organization have to protected personal information of their customer
including personal details like name, contact details and address. Office of the Australian
Information Commissioner (OAIC) play vital role in protecting data of individual, if any
personal information or data is breached then OAIC will act an agent to protect individual and
continue further investigation (Joyce, 2017). Under The Data Protection Act 1988, there are
certain Australian Privacy Principle (APP) that have great role in ensuring sensitive data is been
protected. Every individual has their own right to get protected against data breach, there is
another legislation process in the Australia. Privacy Regulation 2013 provide regulation to those
organizations that contain information of client for business purpose, with the help of OAIC any
these regulations as responsible to bring down breaches of data.
4. current law for biometric:
Biometric is one of the common technology that is been used in human verification process
where individual identify and personal data has been used to allow them access, biometric
psychography is new technology in Metaverse, this simply means collection of biometric data of
user. Under General Data Protection Regulation (GDPR) there are some regulation that drive use
of biometric data, GDPR took step forward to protect and prevent data breach occur due to
biometric psychography (Hoofnagle and et.al., 2019). However, there is no international law that
define biometric data and regulate them, apart from GDPR, Federal law of US define collection
and use of biometric data but do not regulate any law to control these data. Although, CISA take
certain measure to keep eye on biometric psychography, there are certain gaps, these are:
Leak of information.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Misuse of personal information.
Selling of biometric data to third party.
Impact on human behaviour and mind.
Breaching of personal information.
5. Initiatives taken by the Australian government to mitigate data privacy issue:
The Privacy Act 1988 of Australia cover every important element to ensure data is protected
in every situation, this act define every crucial element for example; principles to secure personal
data of the individual and regulation to organization to ensure they compile with principle that
protect data of individual (Daly, 2018). The Australian government took certain initiatives to
bring down privacy issue as much as possible for example; government crafted principle
commonly known as APP apart from this, Australian government introduce data protection
officer strategy to control privacy issue for example if an individual meet with privacy issue of
data then they can appoint data protection officer to find best solution to manage this issue.
Australian government cover every essential area where privacy issue may arrive in the process.
Under Office of the Australian Information Commissioner (OAIC), Australian government take
initiative to manage data breach in the country, this regulation keep eye on oversea recipient for
data protection as most of case can be seen when information is shared with international
organization in the process.
CONCLUSION
From the above report it is concluded that cyber security threats majorly impact the
organisational performance, lately many businesses have faced the vulnerable situation because
of this. Above report have illustrated the discussion over the cyber security management as how
IT assets are beneficial in order to prevent from any threats. Above report have covered the
identification of asset related to confidentiality, integrity and accountability, it further discussed
about the Australian privacy principles, protective policies, metaverse, biometric psychography.
It also discussed about the technologies and other information technology asset that can be used
in cyber security. Report finally concluded with the description of the data protection laws and
also involves the initiatives that are taken by the Australian government to overcome the privacy
issues and challenges.
11
Selling of biometric data to third party.
Impact on human behaviour and mind.
Breaching of personal information.
5. Initiatives taken by the Australian government to mitigate data privacy issue:
The Privacy Act 1988 of Australia cover every important element to ensure data is protected
in every situation, this act define every crucial element for example; principles to secure personal
data of the individual and regulation to organization to ensure they compile with principle that
protect data of individual (Daly, 2018). The Australian government took certain initiatives to
bring down privacy issue as much as possible for example; government crafted principle
commonly known as APP apart from this, Australian government introduce data protection
officer strategy to control privacy issue for example if an individual meet with privacy issue of
data then they can appoint data protection officer to find best solution to manage this issue.
Australian government cover every essential area where privacy issue may arrive in the process.
Under Office of the Australian Information Commissioner (OAIC), Australian government take
initiative to manage data breach in the country, this regulation keep eye on oversea recipient for
data protection as most of case can be seen when information is shared with international
organization in the process.
CONCLUSION
From the above report it is concluded that cyber security threats majorly impact the
organisational performance, lately many businesses have faced the vulnerable situation because
of this. Above report have illustrated the discussion over the cyber security management as how
IT assets are beneficial in order to prevent from any threats. Above report have covered the
identification of asset related to confidentiality, integrity and accountability, it further discussed
about the Australian privacy principles, protective policies, metaverse, biometric psychography.
It also discussed about the technologies and other information technology asset that can be used
in cyber security. Report finally concluded with the description of the data protection laws and
also involves the initiatives that are taken by the Australian government to overcome the privacy
issues and challenges.
11

12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




