University Business Report: WholeWorldBand Information System Analysis
VerifiedAdded on 2020/02/24
|8
|967
|375
Report
AI Summary
This report analyzes the information system architecture of WholeWorldBand, an online platform for music and video enthusiasts. It identifies challenges such as DDoS attacks, system hijacking, and web application security vulnerabilities. The report recommends the adoption of SQL databases for business activities, emphasizing their role in data storage, customer data management, and transaction security. It also outlines measures to protect copyrighted materials, including access restrictions, strong password policies, and physical security measures. The report concludes with a summary of the challenges, SQL database benefits, and security measures discussed, offering a comprehensive overview of the information system's strengths and weaknesses and potential improvements.

Running head: INFORMATION OF THE BUSINESS SYSTEM
Information of the business system
Name of the Student
Name of the University
Author’s note
Information of the business system
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION OF THE BUSINESS SYSTEM
Table of Contents
1. Introduction............................................................................................................................2
2. The challenges associated with building information system architecture............................2
3. WholeWorldBand should employ SQL for their business activities.....................................3
4. The measures to protect the unauthorized access of the copyrighted materials....................3
5. Conclusion..............................................................................................................................4
6. References..............................................................................................................................5
Table of Contents
1. Introduction............................................................................................................................2
2. The challenges associated with building information system architecture............................2
3. WholeWorldBand should employ SQL for their business activities.....................................3
4. The measures to protect the unauthorized access of the copyrighted materials....................3
5. Conclusion..............................................................................................................................4
6. References..............................................................................................................................5

2INFORMATION OF THE BUSINESS SYSTEM
1. Introduction
WholeWorldBand (Refer to Appendix A) provides an online platform for video and
music enthusiasts. Anyone who is interested in creating personalized music videos and is
seeking to share the video with everyone all over the world must register with
WholeWorldBand. They have planned to enhance the information system architecture for
their business (Galliers and Leidner 2014). This report will highlight the various challenges
they can face and the probable measures that should be taken.
2. The challenges associated with building information system architecture
i. Vulnerable to DDoS attack: The users who are registered with WholeWorldBand
may be the targets. The intruders can hack the database and can the misuse the registered
users’ data (Buttyán 2016). The robots or the automation machine can infect the WholeWorld
Band’s system.
ii. System Hijacking: The WholeWorldBand database can be vulnerable to threats
and risks. The malware, virus attack can lead to a leak of personal information, the security
breach can affect the company’s reputation and the loss of data (Galliers and Leidner 2014).
iii. Securing web applications: The WholeWorldBand’s apps can also be the target of
a security breach. Thus security questions arise with the apps too. The users registered with
the email id, the password can get into trouble as there is a chance that information can be
hacked.
If WholeWorldBand adopts the cloud database architecture like Amazon AWS,
Microsoft Azure, that can be beneficial for both the companies (Wu 2014). Amazon or
Microsoft spends a lot of money on the security. WholeWorldBand by taking the IaaS
approach of cloud computing can enhance as well as secure their company.
1. Introduction
WholeWorldBand (Refer to Appendix A) provides an online platform for video and
music enthusiasts. Anyone who is interested in creating personalized music videos and is
seeking to share the video with everyone all over the world must register with
WholeWorldBand. They have planned to enhance the information system architecture for
their business (Galliers and Leidner 2014). This report will highlight the various challenges
they can face and the probable measures that should be taken.
2. The challenges associated with building information system architecture
i. Vulnerable to DDoS attack: The users who are registered with WholeWorldBand
may be the targets. The intruders can hack the database and can the misuse the registered
users’ data (Buttyán 2016). The robots or the automation machine can infect the WholeWorld
Band’s system.
ii. System Hijacking: The WholeWorldBand database can be vulnerable to threats
and risks. The malware, virus attack can lead to a leak of personal information, the security
breach can affect the company’s reputation and the loss of data (Galliers and Leidner 2014).
iii. Securing web applications: The WholeWorldBand’s apps can also be the target of
a security breach. Thus security questions arise with the apps too. The users registered with
the email id, the password can get into trouble as there is a chance that information can be
hacked.
If WholeWorldBand adopts the cloud database architecture like Amazon AWS,
Microsoft Azure, that can be beneficial for both the companies (Wu 2014). Amazon or
Microsoft spends a lot of money on the security. WholeWorldBand by taking the IaaS
approach of cloud computing can enhance as well as secure their company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION OF THE BUSINESS SYSTEM
Fig 1: The threats associated with building information system architecture
(Source: Wu 2014)
3. WholeWorldBand should employ SQL for their business activities
WholeWorldBand should choose the SQL database that does not require manual data
transmission, and secondly, they should integrate the SQL server with the cloud vendor’s
platform. SQL database has structured data which plays a vital role in business activities, it
assists to store the customer data and also the finance data (Sennewald and Baillie 2015).
WholeWorldBand websites, email portals can be maintained by scalable software and apps.
WholeWorldBand if planned for developing secured apps must go for the SQL
databases as SQL databases ensure data reliability, it also guarantees the safety of the
transactions (Wu 2014).
SQL database is used worldwide and facilitates eCommerce and WholeWorldBand
can be largely benefitted.
Fig 1: The threats associated with building information system architecture
(Source: Wu 2014)
3. WholeWorldBand should employ SQL for their business activities
WholeWorldBand should choose the SQL database that does not require manual data
transmission, and secondly, they should integrate the SQL server with the cloud vendor’s
platform. SQL database has structured data which plays a vital role in business activities, it
assists to store the customer data and also the finance data (Sennewald and Baillie 2015).
WholeWorldBand websites, email portals can be maintained by scalable software and apps.
WholeWorldBand if planned for developing secured apps must go for the SQL
databases as SQL databases ensure data reliability, it also guarantees the safety of the
transactions (Wu 2014).
SQL database is used worldwide and facilitates eCommerce and WholeWorldBand
can be largely benefitted.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
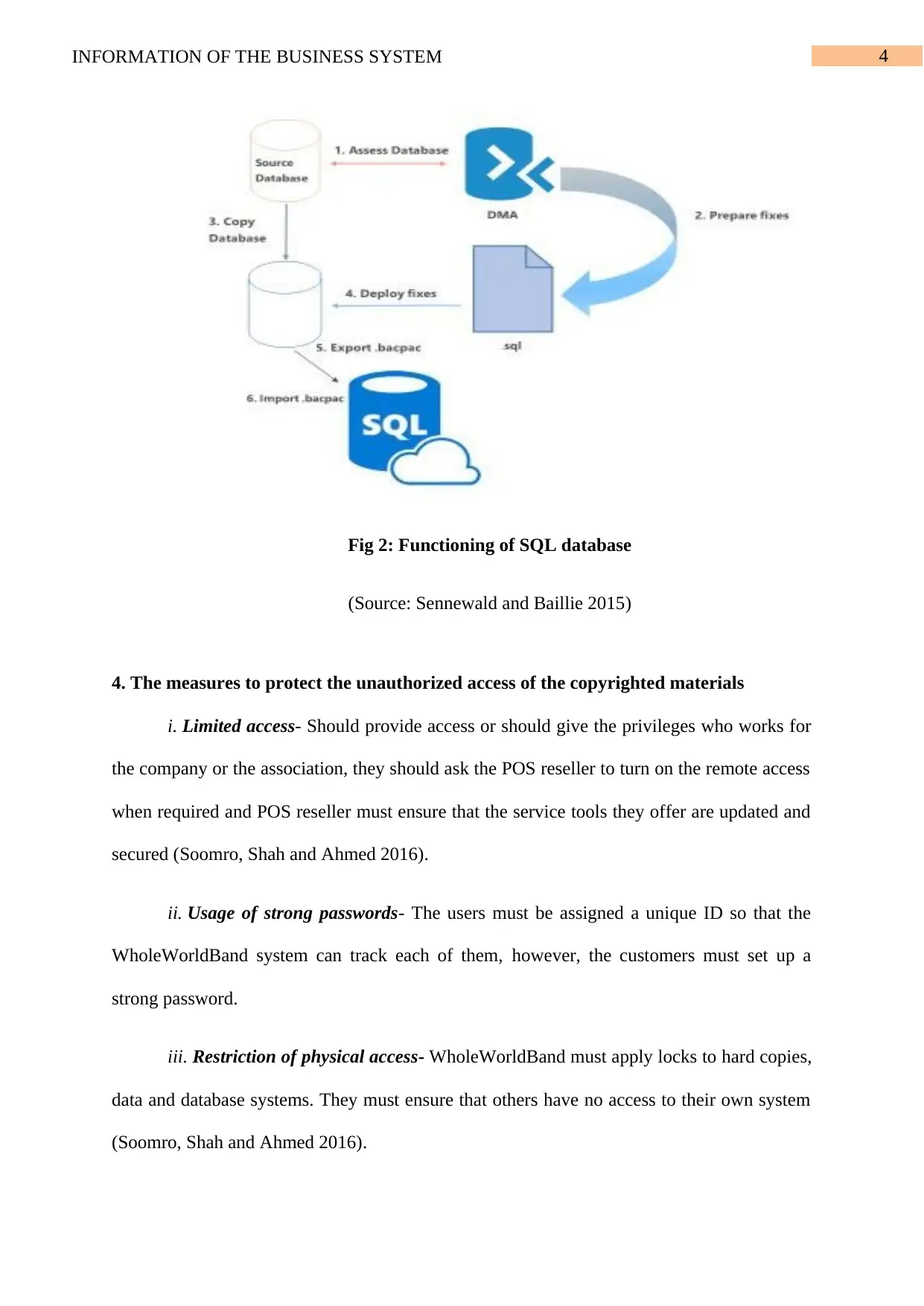
4INFORMATION OF THE BUSINESS SYSTEM
Fig 2: Functioning of SQL database
(Source: Sennewald and Baillie 2015)
4. The measures to protect the unauthorized access of the copyrighted materials
i. Limited access- Should provide access or should give the privileges who works for
the company or the association, they should ask the POS reseller to turn on the remote access
when required and POS reseller must ensure that the service tools they offer are updated and
secured (Soomro, Shah and Ahmed 2016).
ii. Usage of strong passwords- The users must be assigned a unique ID so that the
WholeWorldBand system can track each of them, however, the customers must set up a
strong password.
iii. Restriction of physical access- WholeWorldBand must apply locks to hard copies,
data and database systems. They must ensure that others have no access to their own system
(Soomro, Shah and Ahmed 2016).
Fig 2: Functioning of SQL database
(Source: Sennewald and Baillie 2015)
4. The measures to protect the unauthorized access of the copyrighted materials
i. Limited access- Should provide access or should give the privileges who works for
the company or the association, they should ask the POS reseller to turn on the remote access
when required and POS reseller must ensure that the service tools they offer are updated and
secured (Soomro, Shah and Ahmed 2016).
ii. Usage of strong passwords- The users must be assigned a unique ID so that the
WholeWorldBand system can track each of them, however, the customers must set up a
strong password.
iii. Restriction of physical access- WholeWorldBand must apply locks to hard copies,
data and database systems. They must ensure that others have no access to their own system
(Soomro, Shah and Ahmed 2016).

5INFORMATION OF THE BUSINESS SYSTEM
Fig 3: Security measures
(Source: Soomro, Shah and Ahmed 2016)
5. Conclusion
It can be concluded from the above discourse that WholeWorldBand has planned to
embellish their business activities by improving the database and the website. This report
highlighted the challenges correlated with the information system architecture, vulnerabilities
of DDoS attack, system hijacking, website security have been discussed, the benefits of
adopting SQL database have also been discussed and ultimately the measures to protect the
unauthorized access have been elaborated in this report.
Fig 3: Security measures
(Source: Soomro, Shah and Ahmed 2016)
5. Conclusion
It can be concluded from the above discourse that WholeWorldBand has planned to
embellish their business activities by improving the database and the website. This report
highlighted the challenges correlated with the information system architecture, vulnerabilities
of DDoS attack, system hijacking, website security have been discussed, the benefits of
adopting SQL database have also been discussed and ultimately the measures to protect the
unauthorized access have been elaborated in this report.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION OF THE BUSINESS SYSTEM
6. References
Buttyán, L., 2016. Introduction to IT Security.
Galliers, R.D. and Leidner, D.E. eds., 2014. Strategic information management: challenges
and strategies in managing information systems. Routledge.
Sennewald, C.A. and Baillie, C., 2015. Effective security management. Butterworth-
Heinemann.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Wu, A.J., 2014, May. Project development for ethical hacking practice in a website security
course. In Proceedings of the Western Canadian Conference on Computing Education (p.
18). ACM.
6. References
Buttyán, L., 2016. Introduction to IT Security.
Galliers, R.D. and Leidner, D.E. eds., 2014. Strategic information management: challenges
and strategies in managing information systems. Routledge.
Sennewald, C.A. and Baillie, C., 2015. Effective security management. Butterworth-
Heinemann.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Wu, A.J., 2014, May. Project development for ethical hacking practice in a website security
course. In Proceedings of the Western Canadian Conference on Computing Education (p.
18). ACM.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INFORMATION OF THE BUSINESS SYSTEM
Appendix A: About WholeWorldBand
Fig 4: About WholeWorldBand
Appendix A: About WholeWorldBand
Fig 4: About WholeWorldBand
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





