Managing Cyber Security Threats and Challenges Report
VerifiedAdded on 2020/02/24
|12
|2039
|43
Report
AI Summary
This report comprehensively addresses the multifaceted challenges of cyber security in the face of rapidly advancing technological developments. It begins with an executive summary that highlights the increasing interconnectedness of computer networks and the rise of cybercrime, emphasizing the importance of cyber security measures. The report delves into the problem statement, focusing on the escalating rate of cybercrime and the need for innovative solutions. It provides justification for the study, underscoring the risks associated with technology and the necessity for organizations to mitigate cyber threats. The report then explores cybercrime through four levels of thinking, analyzes recent cybercrime trends, and examines underlying cybercrime structures and mental models. It defines cyber security and outlines its benefits to businesses, including data protection, improved security, and business stability. The report further discusses factors influencing cyber security policies, such as the lack of security procedures, employee training, and user security. It then addresses the impacts of ineffective cyber security and proposes solutions such as employee sensitization, skilled staff, and budget allocation. The report concludes by emphasizing the continuous evolution of the technology industry and the importance of proactive cyber security measures to protect against data breaches and ensure business sustainability. The report is well-researched and provides an overview of the current state of cyber security.

Cyber Security Report 1
MANAGING CYBER SECURITY CHALLENGES
By: Student name:
Subject code:
Tutor:
School:
City:
Date:
MANAGING CYBER SECURITY CHALLENGES
By: Student name:
Subject code:
Tutor:
School:
City:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security Report 2
Executive Summary
Technology advances are rapidly developing, and so are the prospects and challenges that
come along with this developments. The society today is filled with interconnected computer
networks with the growth of the Internet including techniques such as the Internet of Things
(IoT) and big data automation. Because of the challenges brought about by technology
advances, it is important to ensure we defend and implement measures to stop them through
the practice of cyber security.
This report states the problem brought about by cyber-attacks by discussing cybercrime using
four steps of thinking. It also discusses cyber security an outlines the benefits of cyber
security to business organizations. In addition, the paper expounds on factors that influence
cyber security policies and procedures and provides solutions that can be implemented in
business organizations to enhance cyber security and minimize the impact of cybercrime and
finally, a conclusion on enhancing cyber security.
Executive Summary
Technology advances are rapidly developing, and so are the prospects and challenges that
come along with this developments. The society today is filled with interconnected computer
networks with the growth of the Internet including techniques such as the Internet of Things
(IoT) and big data automation. Because of the challenges brought about by technology
advances, it is important to ensure we defend and implement measures to stop them through
the practice of cyber security.
This report states the problem brought about by cyber-attacks by discussing cybercrime using
four steps of thinking. It also discusses cyber security an outlines the benefits of cyber
security to business organizations. In addition, the paper expounds on factors that influence
cyber security policies and procedures and provides solutions that can be implemented in
business organizations to enhance cyber security and minimize the impact of cybercrime and
finally, a conclusion on enhancing cyber security.

Cyber Security Report 3
Table of Contents
Introduction................................................................................................................................4
Problem statement......................................................................................................................4
Justification................................................................................................................................4
Cybercrime: four levels of thinking..........................................................................................5
Recent cybercrime trends and events.....................................................................................5
Underlying cybercrime structures..........................................................................................6
Mental mode...........................................................................................................................7
Cyber security............................................................................................................................7
Benefits of embracing cyber security.....................................................................................7
Factors that influence cyber security......................................................................................8
Impacts of ineffective cyber security procedures...................................................................9
Solutions to traditional cyber security measures....................................................................9
Conclusion................................................................................................................................10
References................................................................................................................................11
Table of Contents
Introduction................................................................................................................................4
Problem statement......................................................................................................................4
Justification................................................................................................................................4
Cybercrime: four levels of thinking..........................................................................................5
Recent cybercrime trends and events.....................................................................................5
Underlying cybercrime structures..........................................................................................6
Mental mode...........................................................................................................................7
Cyber security............................................................................................................................7
Benefits of embracing cyber security.....................................................................................7
Factors that influence cyber security......................................................................................8
Impacts of ineffective cyber security procedures...................................................................9
Solutions to traditional cyber security measures....................................................................9
Conclusion................................................................................................................................10
References................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security Report 4
Introduction
Technological advances have, and continues to positively affect our societies and everyday
lives. However, they also have led to cybercrime, which comprises criminal actions done on
the World Wide Web. Cybercrime has made a lot of effects in our communities including
our individual lives, businesses, and governmental systems. Progressively our lives are
strongly tied to the Internet through the growing web technology. Our personal details
comprising monetary, medical, spending activities, photographs, and emails are stored on the
web. We have adopted cloud computing which involves storing sensitive data and
information on the Internet. Yet we can’t really tell whether such technologies are completely
safe. Emerging technologies are constantly developing as the world remains and becomes
more and more coupled every single day, which leads to increasing complexity with
hardware and software systems. As a result, this has presented more chances for hackers to
exploit new vulnerabilities. Companies are nowadays forced to adopt cyber security
procedures, and continue to spend a lot resources in order to defend themselves against
cyber-attacks. This report investigates cyber security by understanding current existing cyber
security procedures, factors that influence it, effects of not implementing it and initiatives that
can be taken to minimize and manage cyber-security risks more effectively.
Problem statement
The rate at which cyber-crime is occurring keeps increasing. Cyber security policies and
procedures are also increasingly being set up. However, even with cyber security processes in
place, cyber-attacks are on the rise. The problem this report solves are the challenges in cyber
security procedures and the reasons they are yet to yield the anticipated results, as well as
propose innovative processes of handling cyber security threats.
Introduction
Technological advances have, and continues to positively affect our societies and everyday
lives. However, they also have led to cybercrime, which comprises criminal actions done on
the World Wide Web. Cybercrime has made a lot of effects in our communities including
our individual lives, businesses, and governmental systems. Progressively our lives are
strongly tied to the Internet through the growing web technology. Our personal details
comprising monetary, medical, spending activities, photographs, and emails are stored on the
web. We have adopted cloud computing which involves storing sensitive data and
information on the Internet. Yet we can’t really tell whether such technologies are completely
safe. Emerging technologies are constantly developing as the world remains and becomes
more and more coupled every single day, which leads to increasing complexity with
hardware and software systems. As a result, this has presented more chances for hackers to
exploit new vulnerabilities. Companies are nowadays forced to adopt cyber security
procedures, and continue to spend a lot resources in order to defend themselves against
cyber-attacks. This report investigates cyber security by understanding current existing cyber
security procedures, factors that influence it, effects of not implementing it and initiatives that
can be taken to minimize and manage cyber-security risks more effectively.
Problem statement
The rate at which cyber-crime is occurring keeps increasing. Cyber security policies and
procedures are also increasingly being set up. However, even with cyber security processes in
place, cyber-attacks are on the rise. The problem this report solves are the challenges in cyber
security procedures and the reasons they are yet to yield the anticipated results, as well as
propose innovative processes of handling cyber security threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security Report 5
Justification
Technology is developing increasingly and keeps changing how we live, communicate and
do business through disruptive technologies. With the growth of the Internet, business
systems are more improved and more connected to each other and holds confidential data and
information. However, amidst the benefits that technology offers come great risks and
challenges including cyber threats. It is imperative for organizations to realize the risks
brought about by cybercrime, as well as minimize and defend against them.
Cybercrime: Four levels of thinking
Cybercrime involves threats and attacks against computer systems via the Internet (Salim,
2014). Statistics demonstrates that cyber-attacks are developing at an alarming rate. With the
formation of emerging technologies, it has become hard to ensure that computer systems
including hardware, software, networks, and web transmissions are secured (Salim &
Madnick, 2014). Almost all modern organizations have adopted technology and are now
holding important customer information and equally important business intelligence
information on their Internet accessed web systems which have increases cyber-attacks.
Recent cybercrime trends and events
Cybercrime rates have doubled all over the globe. A recent study in Australia showed that,
more than 60 percent of organizations surveyed in 2016 had detected a security incident.
(Osman, 2017). According to the Australian Cybercrime Online Reporting
Network (ACORN), online fraud makes up 49 percent of all reported incidents (Johnston,
2016). Cybercrime continues to increase with time and advancing technology. The recent and
largest ransom ware cyber-attack, WannaCry, saw 150 countries suffer the attack effects
(Liptak, 2017). The world is said to be a global village because of the Interconnection
through the Internet. Technology adoption will continue to expand and develop. If there are
Justification
Technology is developing increasingly and keeps changing how we live, communicate and
do business through disruptive technologies. With the growth of the Internet, business
systems are more improved and more connected to each other and holds confidential data and
information. However, amidst the benefits that technology offers come great risks and
challenges including cyber threats. It is imperative for organizations to realize the risks
brought about by cybercrime, as well as minimize and defend against them.
Cybercrime: Four levels of thinking
Cybercrime involves threats and attacks against computer systems via the Internet (Salim,
2014). Statistics demonstrates that cyber-attacks are developing at an alarming rate. With the
formation of emerging technologies, it has become hard to ensure that computer systems
including hardware, software, networks, and web transmissions are secured (Salim &
Madnick, 2014). Almost all modern organizations have adopted technology and are now
holding important customer information and equally important business intelligence
information on their Internet accessed web systems which have increases cyber-attacks.
Recent cybercrime trends and events
Cybercrime rates have doubled all over the globe. A recent study in Australia showed that,
more than 60 percent of organizations surveyed in 2016 had detected a security incident.
(Osman, 2017). According to the Australian Cybercrime Online Reporting
Network (ACORN), online fraud makes up 49 percent of all reported incidents (Johnston,
2016). Cybercrime continues to increase with time and advancing technology. The recent and
largest ransom ware cyber-attack, WannaCry, saw 150 countries suffer the attack effects
(Liptak, 2017). The world is said to be a global village because of the Interconnection
through the Internet. Technology adoption will continue to expand and develop. If there are

Cyber Security Report 6
no necessary policies put in place to prevent cybercrime, it will continually be a great risk for
both individuals and organizations. Figure 1 below shows that cybercrime is the leading
cause of data breach attack (Passeri, 2016).
Figure 1: Cyber Attacks 2016.Source: (Passeri, 2016)
Underlying cybercrime structures
Internationally, different countries continue to face the challenge of effectively addressing the
problem of illegal cyber activity and cybercrime victimization. Cybercrime is encouraged by
the fact that IT hardware and software is now closely interlinked in the Internet of Things as
shown in Figure 2. Another underlying structure is that hackers are making use of advancing
technology to attack network systems.
Figure 2: Internet of Things (IoT) Source: (Salim, 2014)
Mental mode
no necessary policies put in place to prevent cybercrime, it will continually be a great risk for
both individuals and organizations. Figure 1 below shows that cybercrime is the leading
cause of data breach attack (Passeri, 2016).
Figure 1: Cyber Attacks 2016.Source: (Passeri, 2016)
Underlying cybercrime structures
Internationally, different countries continue to face the challenge of effectively addressing the
problem of illegal cyber activity and cybercrime victimization. Cybercrime is encouraged by
the fact that IT hardware and software is now closely interlinked in the Internet of Things as
shown in Figure 2. Another underlying structure is that hackers are making use of advancing
technology to attack network systems.
Figure 2: Internet of Things (IoT) Source: (Salim, 2014)
Mental mode
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber Security Report 7
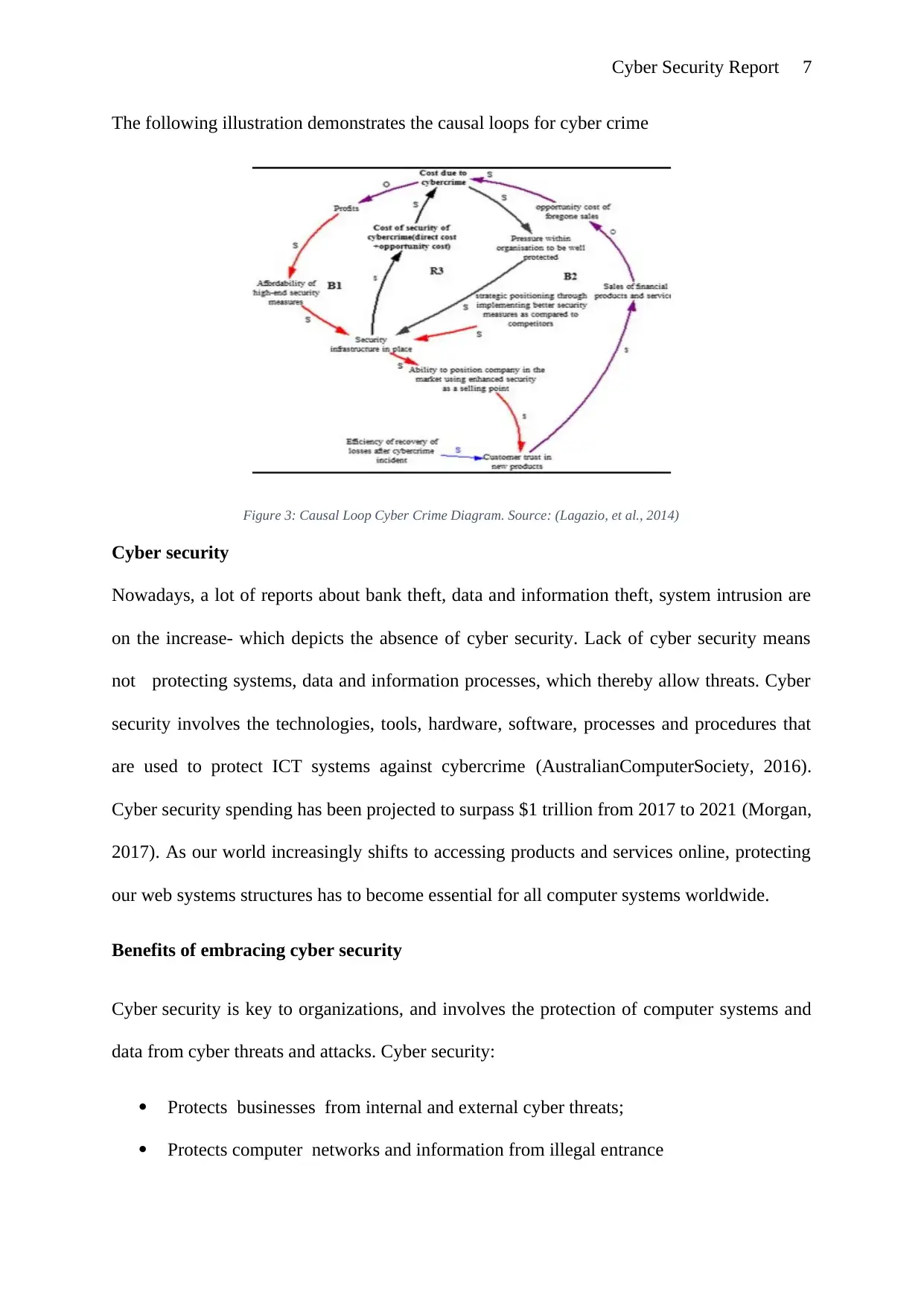
The following illustration demonstrates the causal loops for cyber crime
Figure 3: Causal Loop Cyber Crime Diagram. Source: (Lagazio, et al., 2014)
Cyber security
Nowadays, a lot of reports about bank theft, data and information theft, system intrusion are
on the increase- which depicts the absence of cyber security. Lack of cyber security means
not protecting systems, data and information processes, which thereby allow threats. Cyber
security involves the technologies, tools, hardware, software, processes and procedures that
are used to protect ICT systems against cybercrime (AustralianComputerSociety, 2016).
Cyber security spending has been projected to surpass $1 trillion from 2017 to 2021 (Morgan,
2017). As our world increasingly shifts to accessing products and services online, protecting
our web systems structures has to become essential for all computer systems worldwide.
Benefits of embracing cyber security
Cyber security is key to organizations, and involves the protection of computer systems and
data from cyber threats and attacks. Cyber security:
Protects businesses from internal and external cyber threats;
Protects computer networks and information from illegal entrance
The following illustration demonstrates the causal loops for cyber crime
Figure 3: Causal Loop Cyber Crime Diagram. Source: (Lagazio, et al., 2014)
Cyber security
Nowadays, a lot of reports about bank theft, data and information theft, system intrusion are
on the increase- which depicts the absence of cyber security. Lack of cyber security means
not protecting systems, data and information processes, which thereby allow threats. Cyber
security involves the technologies, tools, hardware, software, processes and procedures that
are used to protect ICT systems against cybercrime (AustralianComputerSociety, 2016).
Cyber security spending has been projected to surpass $1 trillion from 2017 to 2021 (Morgan,
2017). As our world increasingly shifts to accessing products and services online, protecting
our web systems structures has to become essential for all computer systems worldwide.
Benefits of embracing cyber security
Cyber security is key to organizations, and involves the protection of computer systems and
data from cyber threats and attacks. Cyber security:
Protects businesses from internal and external cyber threats;
Protects computer networks and information from illegal entrance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security Report 8
Improves data and information security and enhances business stability management
Develops stakeholder assurance in your information security arrangement
Increases company authorizations through the use of the right security controls
Provides quick recovery times in the event of data breach
Factors that influence cyber security
There are many factors influencing the success of cyber security procedures according to
(Miliefsky, 2017) including the following:
Lack of installing security procedures – much as business have continued to suffer computer
breaches, they do not install mechanisms to secure their systems against attackers which
increases cybercrime.
Attack detection - It takes long to discover a security threat - The average time between when
an attack happens and when it is discovered is 280 days.
Employee training – if company staff are not continuously trained on cyber security, they
continue to be the weakest link against securing computer systems.
Cyber Insurance – businesses are now able to pay for cyber security policy cover so that
incase an attack hits, there’s business continuity
Intranets security – organization are not implementing intranet security which largely affects
whether an attack will work or not.
User Security – system users including employees and clients should make strong passwords
and constantly change them. This may stop the possibility of a data breach.
Impacts of ineffective cyber security procedures
i) Lack of cyber security is a great risk for both small, medium sized and large
organizations. Cyber-attacks result to huge financial losses for businesses which can
Improves data and information security and enhances business stability management
Develops stakeholder assurance in your information security arrangement
Increases company authorizations through the use of the right security controls
Provides quick recovery times in the event of data breach
Factors that influence cyber security
There are many factors influencing the success of cyber security procedures according to
(Miliefsky, 2017) including the following:
Lack of installing security procedures – much as business have continued to suffer computer
breaches, they do not install mechanisms to secure their systems against attackers which
increases cybercrime.
Attack detection - It takes long to discover a security threat - The average time between when
an attack happens and when it is discovered is 280 days.
Employee training – if company staff are not continuously trained on cyber security, they
continue to be the weakest link against securing computer systems.
Cyber Insurance – businesses are now able to pay for cyber security policy cover so that
incase an attack hits, there’s business continuity
Intranets security – organization are not implementing intranet security which largely affects
whether an attack will work or not.
User Security – system users including employees and clients should make strong passwords
and constantly change them. This may stop the possibility of a data breach.
Impacts of ineffective cyber security procedures
i) Lack of cyber security is a great risk for both small, medium sized and large
organizations. Cyber-attacks result to huge financial losses for businesses which can

Cyber Security Report 9
arise from information theft and financial theft, inability to carry perform online
transactions, loss of contract deals and expenses connected with repairing affected
computer systems
ii) Reputation damage for organization leading to loss of sales, clients and reduction in
profits
iii) Legal consequences leading to fines and regulatory sanctions since organizations are
required to protect customer data and information
Solutions to ineffective cyber security measures
Organizations can adopt the following measures to minimize cyber-attacks and enhance
cyber security policies and techniques:
Sensitize employees on security awareness
Employ skilled staff on cyber security
Create and maintain cyber security budgets
Ensure system and department collaboration
Implement software patch updates
Perform penetration testing to test system vulnerabilities
Secure organization intranets
Conclusion
Today, the technology industry is constantly evolving. ICT components are getting more
connected than ever with the advent of advances as the Internet of Things. There have been
an emphasis on mechanisms for protecting ICT systems from threats by policy makers.
Some effective instruments for defending the privacy and the prevention of unlawful
scrutiny, and sharing of information and tools used to intelligently gather data can be
valuable cyber security tools. Business organizations need to implement cyber security
arise from information theft and financial theft, inability to carry perform online
transactions, loss of contract deals and expenses connected with repairing affected
computer systems
ii) Reputation damage for organization leading to loss of sales, clients and reduction in
profits
iii) Legal consequences leading to fines and regulatory sanctions since organizations are
required to protect customer data and information
Solutions to ineffective cyber security measures
Organizations can adopt the following measures to minimize cyber-attacks and enhance
cyber security policies and techniques:
Sensitize employees on security awareness
Employ skilled staff on cyber security
Create and maintain cyber security budgets
Ensure system and department collaboration
Implement software patch updates
Perform penetration testing to test system vulnerabilities
Secure organization intranets
Conclusion
Today, the technology industry is constantly evolving. ICT components are getting more
connected than ever with the advent of advances as the Internet of Things. There have been
an emphasis on mechanisms for protecting ICT systems from threats by policy makers.
Some effective instruments for defending the privacy and the prevention of unlawful
scrutiny, and sharing of information and tools used to intelligently gather data can be
valuable cyber security tools. Business organizations need to implement cyber security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security Report 10
processes continuously to be able to stand against data breaches and enhance business
sustainability.
processes continuously to be able to stand against data breaches and enhance business
sustainability.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security Report 11
References
AustralianComputerSociety, 2016. Cybersecurity: Threats, Challenges, Opportunities.
[Online]
Available at:
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
[Accessed 28 Augsut 2017].
Johnston, R., 2016. Gizmodo: Over 39,000 Cases Of Cybercrime Reported In Australia Last
Year. [Online]
Available at: https://www.gizmodo.com.au/2016/01/over-39000-cases-of-cybercrime-
reported-in-australia-last-year/
[Accessed 28 August 2017].
Lagazio, M., Sherif, N. & Cushman, M., 2014. A multi-level approach to understanding the
impact of cyber crime on the financial sector. Science Direct, Volume 45, pp. Pages 58- 74 .
Liptak, A., 2017. The Verge: The WannaCry ransomware attack has spread to 150 countries.
[Online]
Available at: https://www.theverge.com/2017/5/14/15637888/authorities-wannacry-
ransomware-attack-spread-150-countries
[Accessed 28 August 2017].
Miliefsky, G., 2017. Trends and factors that continue to impact cybersecurity in 2017.
[Online]
Available at: http://www.propertycasualty360.com/2017/03/03/5-trends-and-factors-that-
continue-to-impact-cyber?page=2&slreturn=1503945108
[Accessed 28 August 2017].
Morgan, S., 2017. Top 5 cybersecurity facts, figures and statistics for 2017. [Online]
Available at: http://www.csoonline.com/article/3153707/security/top-5-cybersecurity-facts-
figures-and-statistics-for-2017.html
[Accessed 28 August 2017].
Osman, H., 2017. ARN: Cybercrime in Australia doubled in 2016. [Online]
Available at: https://www.arnnet.com.au/article/616804/cybercrime-australia-doubled-2016/
[Accessed 28 August 2017].
Passeri, P., 2016. January 2016 Cyber Attacks Statistics. [Online]
Available at: http://www.hackmageddon.com/2016/02/16/january-2016-cyber-attacks-
statistics/
[Accessed 26 August 2017].
Salim, H., 2014. Cyber Safety:A Systems Thinking and Systems Theory Approach. [Online]
Available at: http://web.mit.edu/smadnick/www/wp/2014-07.pdf
[Accessed 27 August 2017].
Salim, H. & Madnick, S., 2014. Cyber Safety: A Systems Thinking and Systems Theory
Approach. [Online]
References
AustralianComputerSociety, 2016. Cybersecurity: Threats, Challenges, Opportunities.
[Online]
Available at:
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
[Accessed 28 Augsut 2017].
Johnston, R., 2016. Gizmodo: Over 39,000 Cases Of Cybercrime Reported In Australia Last
Year. [Online]
Available at: https://www.gizmodo.com.au/2016/01/over-39000-cases-of-cybercrime-
reported-in-australia-last-year/
[Accessed 28 August 2017].
Lagazio, M., Sherif, N. & Cushman, M., 2014. A multi-level approach to understanding the
impact of cyber crime on the financial sector. Science Direct, Volume 45, pp. Pages 58- 74 .
Liptak, A., 2017. The Verge: The WannaCry ransomware attack has spread to 150 countries.
[Online]
Available at: https://www.theverge.com/2017/5/14/15637888/authorities-wannacry-
ransomware-attack-spread-150-countries
[Accessed 28 August 2017].
Miliefsky, G., 2017. Trends and factors that continue to impact cybersecurity in 2017.
[Online]
Available at: http://www.propertycasualty360.com/2017/03/03/5-trends-and-factors-that-
continue-to-impact-cyber?page=2&slreturn=1503945108
[Accessed 28 August 2017].
Morgan, S., 2017. Top 5 cybersecurity facts, figures and statistics for 2017. [Online]
Available at: http://www.csoonline.com/article/3153707/security/top-5-cybersecurity-facts-
figures-and-statistics-for-2017.html
[Accessed 28 August 2017].
Osman, H., 2017. ARN: Cybercrime in Australia doubled in 2016. [Online]
Available at: https://www.arnnet.com.au/article/616804/cybercrime-australia-doubled-2016/
[Accessed 28 August 2017].
Passeri, P., 2016. January 2016 Cyber Attacks Statistics. [Online]
Available at: http://www.hackmageddon.com/2016/02/16/january-2016-cyber-attacks-
statistics/
[Accessed 26 August 2017].
Salim, H., 2014. Cyber Safety:A Systems Thinking and Systems Theory Approach. [Online]
Available at: http://web.mit.edu/smadnick/www/wp/2014-07.pdf
[Accessed 27 August 2017].
Salim, H. & Madnick, S., 2014. Cyber Safety: A Systems Thinking and Systems Theory
Approach. [Online]

Cyber Security Report 12
Available at: https://ic3.mit.edu/sites/default/files/documents/2014-12.pdf
[Accessed 26 August 2017].
Available at: https://ic3.mit.edu/sites/default/files/documents/2014-12.pdf
[Accessed 26 August 2017].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





