Software Failure Mode and Effects Analysis
VerifiedAdded on 2020/03/13
|26
|5150
|464
AI Summary
This assignment focuses on conducting a Failure Mode and Effects Analysis (FMEA) for a software development project. It identifies potential failure modes within the software, such as faulty functionality, data issues, synchronization problems, algorithm limitations, error recovery failures, and security vulnerabilities. For each failure mode, the analysis considers its effect, severity, cause, probability of occurrence, detectability, and proposes control measures to mitigate risks. The assignment also calculates the Risk Priority Number (RPN) for each failure mode and recommends actions to prioritize and address them effectively.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Risk Management in Engineering
Name of the Student
Name of the University
Author Note
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
RISK MANAGEMENT IN ENGINEERING
Executive Summary
The report aims at establishing the risk management procedure for the implementation of a new
in-patient data storing system for hospital. The project chosen for this topic is named ‘My Health
Record System’ undertaken by an Australian hospital for storing the patients’ record over
electronic means, specifically internet. Both the patients and the professionals can access the
information stored. However, there are certain risks associated with the storing of patients’ data
over electronic means. This report elaborates the risk management procedure of this project
according to the AS/NZS ISO 31000:2009.
RISK MANAGEMENT IN ENGINEERING
Executive Summary
The report aims at establishing the risk management procedure for the implementation of a new
in-patient data storing system for hospital. The project chosen for this topic is named ‘My Health
Record System’ undertaken by an Australian hospital for storing the patients’ record over
electronic means, specifically internet. Both the patients and the professionals can access the
information stored. However, there are certain risks associated with the storing of patients’ data
over electronic means. This report elaborates the risk management procedure of this project
according to the AS/NZS ISO 31000:2009.

2
RISK MANAGEMENT IN ENGINEERING
Table of Contents
1. Introduction......................................................................................................................4
2. Project Overview and boundaries of the Project.............................................................4
3. Establishing the Context..................................................................................................5
3.1. Internal Context........................................................................................................5
3.2. External Context.......................................................................................................7
3.3. Risk management Context........................................................................................7
3.4. Risk Criteria..............................................................................................................7
4. Stakeholders.....................................................................................................................9
4.1. Stakeholder Identification.........................................................................................9
4.2. Stakeholder Analysis................................................................................................9
5. Communication and Consultation.................................................................................10
6. Four Risk assessment Methods......................................................................................11
6.1. Risk Identification......................................................................................................11
6.2. Risk Analysis..............................................................................................................13
6.2.1. The risk Associated with the Project...................................................................13
6.2.2. Existing Controls and Their Effectiveness..........................................................14
6.3. Risk Evaluation...........................................................................................................15
6.4. Risk Treatment............................................................................................................16
6.4.1. Identification of the appropriate risk treatment...................................................17
RISK MANAGEMENT IN ENGINEERING
Table of Contents
1. Introduction......................................................................................................................4
2. Project Overview and boundaries of the Project.............................................................4
3. Establishing the Context..................................................................................................5
3.1. Internal Context........................................................................................................5
3.2. External Context.......................................................................................................7
3.3. Risk management Context........................................................................................7
3.4. Risk Criteria..............................................................................................................7
4. Stakeholders.....................................................................................................................9
4.1. Stakeholder Identification.........................................................................................9
4.2. Stakeholder Analysis................................................................................................9
5. Communication and Consultation.................................................................................10
6. Four Risk assessment Methods......................................................................................11
6.1. Risk Identification......................................................................................................11
6.2. Risk Analysis..............................................................................................................13
6.2.1. The risk Associated with the Project...................................................................13
6.2.2. Existing Controls and Their Effectiveness..........................................................14
6.3. Risk Evaluation...........................................................................................................15
6.4. Risk Treatment............................................................................................................16
6.4.1. Identification of the appropriate risk treatment...................................................17

3
RISK MANAGEMENT IN ENGINEERING
6.4.2. Risk Recovery......................................................................................................17
7. Risk tolerability.............................................................................................................18
7. Monitoring and Review.................................................................................................19
8. Societal benefits of risk exposure..................................................................................20
9. Risk Closure...................................................................................................................20
10. Conclusion...................................................................................................................20
11. References....................................................................................................................22
12. Appendix......................................................................................................................25
12.1. Risk Identification Checklist................................................................................25
12.2. FMEA Analysis....................................................................................................26
RISK MANAGEMENT IN ENGINEERING
6.4.2. Risk Recovery......................................................................................................17
7. Risk tolerability.............................................................................................................18
7. Monitoring and Review.................................................................................................19
8. Societal benefits of risk exposure..................................................................................20
9. Risk Closure...................................................................................................................20
10. Conclusion...................................................................................................................20
11. References....................................................................................................................22
12. Appendix......................................................................................................................25
12.1. Risk Identification Checklist................................................................................25
12.2. FMEA Analysis....................................................................................................26
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
RISK MANAGEMENT IN ENGINEERING
1. Introduction
The proposed project ‘Implementation of new in patient data storing system’ aims at
automating the process of storing patients’ data , who are admitted in the hospital and monitor it
electronically. The proposed system aims at eliminating the hassle of manually storing the
patients’ records and monitoring it. Both the hospital and the patients will access this health
record system. The records are uploaded and transferred to and from the system electronically
and the patients’ data is stored over a common database of the hospital with the application of
cloud storage. This proposed system will make the process of data keeping simpler, easier and
less time consuming. This will be beneficial for the patients as well since they would not have to
carry the manual records of their previous medication in case they see a new professional.
However, there are certain risks associated with the implementation of the project. These risks
are needed to be eliminated or acknowledged in order to implement the system successfully. The
risk management strategy financial and security risks of the project is elaborated in the following
paragraphs.
2. Project Overview and boundaries of the Project
The in patient data storing system for hospitals, named as ‘My Health record System’ is
to be implemented to automate the system of manual recordings. This system is designed with an
objective of storing and accessing patients’ record electronically. The records and patients details
are stored are at first uploaded into the system. The patients and the doctors have to register into
the system in order to access the data thus ensuring the privacy of data (Woods et al. 2013). The
data is stored in the cloud thus offering unlimited data entries and storage.
RISK MANAGEMENT IN ENGINEERING
1. Introduction
The proposed project ‘Implementation of new in patient data storing system’ aims at
automating the process of storing patients’ data , who are admitted in the hospital and monitor it
electronically. The proposed system aims at eliminating the hassle of manually storing the
patients’ records and monitoring it. Both the hospital and the patients will access this health
record system. The records are uploaded and transferred to and from the system electronically
and the patients’ data is stored over a common database of the hospital with the application of
cloud storage. This proposed system will make the process of data keeping simpler, easier and
less time consuming. This will be beneficial for the patients as well since they would not have to
carry the manual records of their previous medication in case they see a new professional.
However, there are certain risks associated with the implementation of the project. These risks
are needed to be eliminated or acknowledged in order to implement the system successfully. The
risk management strategy financial and security risks of the project is elaborated in the following
paragraphs.
2. Project Overview and boundaries of the Project
The in patient data storing system for hospitals, named as ‘My Health record System’ is
to be implemented to automate the system of manual recordings. This system is designed with an
objective of storing and accessing patients’ record electronically. The records and patients details
are stored are at first uploaded into the system. The patients and the doctors have to register into
the system in order to access the data thus ensuring the privacy of data (Woods et al. 2013). The
data is stored in the cloud thus offering unlimited data entries and storage.

5
RISK MANAGEMENT IN ENGINEERING
However, there are certain limitations in this system. The data is to be stored in cloud,
thus certain security issues arises with the data security (Kulkarni et al. 2012). Moreover, there is
a risk of data loss in case of system failure and that would result in a huge problem. The
uploading of the data is needed to be done very carefully as that would be the only copy of the
patients’ record in the hospital.
3. Establishing the Context
For implementing the risk management strategy using AS/NZS ISO 31000:2009, the
context of the risk are necessary to be defined (Ernawati and Nugroho 2012). The contexts are to
be identified carefully in order to ensure an effective risk management plan. This includes
establishment of internal, external, stakeholders and risk management context of the plan. These
contexts are established in the following paragraphs (McNeil, Frey and Embrechts 2015).
3.1. Internal Context
With the emergence of digital world, people are keener on using internet to make their
work easier. This idea has been implemented by the project “My Health Record System” for
automating the storage and transfer of the patients’ data admit7ted in the hospital. This record
will include every detail such as the name, address, medical details and prescribed medication of
the patients. Both the professionals and the patients can access this record.
The financial context of the business covers the responsibilities of designing the system,
Initial investment for the up gradation process, uploading and archiving the previous records into
the new system, and re investment strategy. Fluctuation in the finances of the hospital will
resonate into every part of the business, which is needed to be tracked by the project manager
and the project sponsors (Hopkin 2017).
RISK MANAGEMENT IN ENGINEERING
However, there are certain limitations in this system. The data is to be stored in cloud,
thus certain security issues arises with the data security (Kulkarni et al. 2012). Moreover, there is
a risk of data loss in case of system failure and that would result in a huge problem. The
uploading of the data is needed to be done very carefully as that would be the only copy of the
patients’ record in the hospital.
3. Establishing the Context
For implementing the risk management strategy using AS/NZS ISO 31000:2009, the
context of the risk are necessary to be defined (Ernawati and Nugroho 2012). The contexts are to
be identified carefully in order to ensure an effective risk management plan. This includes
establishment of internal, external, stakeholders and risk management context of the plan. These
contexts are established in the following paragraphs (McNeil, Frey and Embrechts 2015).
3.1. Internal Context
With the emergence of digital world, people are keener on using internet to make their
work easier. This idea has been implemented by the project “My Health Record System” for
automating the storage and transfer of the patients’ data admit7ted in the hospital. This record
will include every detail such as the name, address, medical details and prescribed medication of
the patients. Both the professionals and the patients can access this record.
The financial context of the business covers the responsibilities of designing the system,
Initial investment for the up gradation process, uploading and archiving the previous records into
the new system, and re investment strategy. Fluctuation in the finances of the hospital will
resonate into every part of the business, which is needed to be tracked by the project manager
and the project sponsors (Hopkin 2017).

6
RISK MANAGEMENT IN ENGINEERING
Designing a secure system is another internal context of this project. Maintaining the
confidentiality of the information is necessary for the hospital in order to earn the patients’ trust,
which is essential for business perspective.
The various department of the hospital that are involved with the designing and
development of this project are as follows-
1) Operations Department
2) Clinical department
3) Billing Department
4) Patients’ discharge department
Information from all these departments is necessary for manual input of the previous
patients’ data into the new system.
The project teams involved in developing this system are listed below-
1) Designing team
2) Coding team (for database designing and coding)
3) Testing team
4) Project management team (which includes the project manager and the business nalyst
of the project)
Lastly the patients whose information is to be stored within the health record system are
also part of the internal context of the project under consideration.
RISK MANAGEMENT IN ENGINEERING
Designing a secure system is another internal context of this project. Maintaining the
confidentiality of the information is necessary for the hospital in order to earn the patients’ trust,
which is essential for business perspective.
The various department of the hospital that are involved with the designing and
development of this project are as follows-
1) Operations Department
2) Clinical department
3) Billing Department
4) Patients’ discharge department
Information from all these departments is necessary for manual input of the previous
patients’ data into the new system.
The project teams involved in developing this system are listed below-
1) Designing team
2) Coding team (for database designing and coding)
3) Testing team
4) Project management team (which includes the project manager and the business nalyst
of the project)
Lastly the patients whose information is to be stored within the health record system are
also part of the internal context of the project under consideration.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
RISK MANAGEMENT IN ENGINEERING
3.2. External Context
The external context of this project has a direct influence on the internal environment of
the hospital. By implementing this project successfully and developing the “My Health Record
System”, the hospital will have a positive impact on the other hospitals for implementing this
idea and adopting the change. This will provide fresh business to the hospital by gaining more
patients as everyone would love to have an electronic version of data storage instead of the
traditional and manual way of data storing (Sadgrove 2016). However, with the implementation
of this project, the other hospitals might be negatively affected by the competition resulting from
the implementation of “My Health Record System”
3.3. Risk management Context
For this particular project, the risk management context focuses on managing only the
financial and security risks associated with the implementation of the project. The primary goal
of this study is to access and analyze relevant risks associated with the project and treat them
accordingly (Lam 2014). The goals of the risk management plan are listed below-
1) Reduce the risk of project failure in its first year of implementation.
2) Establishing and building a system that fits the purpose of providing a better service to
the patients of the hospital.
3) Ensuring that the business perspective of the project and its performance is aligned
with the primary objective of the system.
4) Evaluate the risk involved in storing of patients’ information in cloud.
3.4. Risk Criteria
RISK MANAGEMENT IN ENGINEERING
3.2. External Context
The external context of this project has a direct influence on the internal environment of
the hospital. By implementing this project successfully and developing the “My Health Record
System”, the hospital will have a positive impact on the other hospitals for implementing this
idea and adopting the change. This will provide fresh business to the hospital by gaining more
patients as everyone would love to have an electronic version of data storage instead of the
traditional and manual way of data storing (Sadgrove 2016). However, with the implementation
of this project, the other hospitals might be negatively affected by the competition resulting from
the implementation of “My Health Record System”
3.3. Risk management Context
For this particular project, the risk management context focuses on managing only the
financial and security risks associated with the implementation of the project. The primary goal
of this study is to access and analyze relevant risks associated with the project and treat them
accordingly (Lam 2014). The goals of the risk management plan are listed below-
1) Reduce the risk of project failure in its first year of implementation.
2) Establishing and building a system that fits the purpose of providing a better service to
the patients of the hospital.
3) Ensuring that the business perspective of the project and its performance is aligned
with the primary objective of the system.
4) Evaluate the risk involved in storing of patients’ information in cloud.
3.4. Risk Criteria

8
RISK MANAGEMENT IN ENGINEERING
As this report mainly focuses on the financial and security risk of developing a new
system in hospitals, the risk criteria will also be addressed only on basis of financial and security
issues in the system (Christoffersen 2012).
The following points are needed to be considered in establishing the risk criteria.
1) A method of determining the degree of threat in storage of patients’ personal
information in cloud and prioritizing those threats
2) The amount of available resources in treating the risk if faced
3) Setting up a tolerability benchmark
3) The probable impact of immediate and delayed risks in the system
These points aim at:
1) Helping the project manager in effective decision making
2) Considering various scenarios and their impact on achieving the objective of the
project
3) Allocating resources at the initial stage of development in order to bypass high-level
risks
4) Providing a clear and simple tool for clear and essential communication
The internal goals of the hospital in developing the in patient data storing system are as
follows-
1) The project must comply with the government regulations and laws
RISK MANAGEMENT IN ENGINEERING
As this report mainly focuses on the financial and security risk of developing a new
system in hospitals, the risk criteria will also be addressed only on basis of financial and security
issues in the system (Christoffersen 2012).
The following points are needed to be considered in establishing the risk criteria.
1) A method of determining the degree of threat in storage of patients’ personal
information in cloud and prioritizing those threats
2) The amount of available resources in treating the risk if faced
3) Setting up a tolerability benchmark
3) The probable impact of immediate and delayed risks in the system
These points aim at:
1) Helping the project manager in effective decision making
2) Considering various scenarios and their impact on achieving the objective of the
project
3) Allocating resources at the initial stage of development in order to bypass high-level
risks
4) Providing a clear and simple tool for clear and essential communication
The internal goals of the hospital in developing the in patient data storing system are as
follows-
1) The project must comply with the government regulations and laws

9
RISK MANAGEMENT IN ENGINEERING
2) Profit must not be less than 6%
3) The system implementation should not lead to the over budget of the project
4) The system should be developed in such a way that it will be opened for further
advancements if required
5) Zero turnover rates in order to avoid unnecessary costs rising from training the staffs
in using the new system.
4. Stakeholders
The detailed analysis of the stakeholders involved in this project are elaborated in the
following paragraph (Harrison and Wicks 2013)-
4.1. Stakeholder Identification
The following are the identified stakeholders of the project under consideration (Pacheco
and Garcia 2012) -
The Hospital Owner
The Project manger ( the project deals with designing the health record system)
Project Team
Sponsors
The Billing department of the Hospital
The patients
Table 1: The list of stakeholders involved in the project
4.2. Stakeholder Analysis
RISK MANAGEMENT IN ENGINEERING
2) Profit must not be less than 6%
3) The system implementation should not lead to the over budget of the project
4) The system should be developed in such a way that it will be opened for further
advancements if required
5) Zero turnover rates in order to avoid unnecessary costs rising from training the staffs
in using the new system.
4. Stakeholders
The detailed analysis of the stakeholders involved in this project are elaborated in the
following paragraph (Harrison and Wicks 2013)-
4.1. Stakeholder Identification
The following are the identified stakeholders of the project under consideration (Pacheco
and Garcia 2012) -
The Hospital Owner
The Project manger ( the project deals with designing the health record system)
Project Team
Sponsors
The Billing department of the Hospital
The patients
Table 1: The list of stakeholders involved in the project
4.2. Stakeholder Analysis
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
RISK MANAGEMENT IN ENGINEERING
Detailed analysis of the identified stakeholders are elaborated in the following table
(Lienert, Schnetzer and Ingold, 2013)-
Stakeholder Influence/Interest
The Hospital Owner Responsible for setting up the objectives of the
project
The Project manger ( the project deals with designing
the health record system)
Responsible for planning and executing the
project according to the specified objectives
Project Team Responsible for the implementation of the
project within the specified time
Sponsors Responsible for managing the economical
aspects of the project and is the source of
funding for the project
The Billing department of the Hospital Responsible for providing necessary details of
the patients to be uploaded into the new system
The patients Responsible for supporting the project by
agreeing to store their personal information and
health records into a common database of the
hospital.
Table 2: Representing the Stakeholders’ Analysis
5. Communication and Consultation
Engaging the stakeholders through an appropriate communication and consultation plan
is necessary to address the stakeholders’ interest and concerns. This project is a medium sized
RISK MANAGEMENT IN ENGINEERING
Detailed analysis of the identified stakeholders are elaborated in the following table
(Lienert, Schnetzer and Ingold, 2013)-
Stakeholder Influence/Interest
The Hospital Owner Responsible for setting up the objectives of the
project
The Project manger ( the project deals with designing
the health record system)
Responsible for planning and executing the
project according to the specified objectives
Project Team Responsible for the implementation of the
project within the specified time
Sponsors Responsible for managing the economical
aspects of the project and is the source of
funding for the project
The Billing department of the Hospital Responsible for providing necessary details of
the patients to be uploaded into the new system
The patients Responsible for supporting the project by
agreeing to store their personal information and
health records into a common database of the
hospital.
Table 2: Representing the Stakeholders’ Analysis
5. Communication and Consultation
Engaging the stakeholders through an appropriate communication and consultation plan
is necessary to address the stakeholders’ interest and concerns. This project is a medium sized

11
RISK MANAGEMENT IN ENGINEERING
project and hence it is essential to recognize the potential risks associated with the opening up of
a new system and build awareness in regard to the significance of the ‘My health Record
System’ (Lundgren and McMakin 2013).
An effective Communication plan eliminates the conflict of interest and decision among
the project stakeholders and therefore it is very essential for a smooth implementation of the
project (Lando 2014).
In order to develop an effective communication and consultation plan, a proper analysis
of the power and the interest of the stakeholders in necessary to consider (Fassin 2012). The
group of stakeholders who have less power or interest on this project would be least pronounced
in the communication and the consultation plan. While the group of stakeholders who have high
power and interest over this project should be specifically and formally addressed and included
in the communication and consultation plan through proper email. Mass communication should
be made with this group as this group of stakeholder has higher interest in the project. They
should be informed about the project progress in daily basis. The stakeholders included into this
group are the hospital authority and the owner. Stakeholders that have low interest over the
project can be notified about the project progress less often.
6. Four Risk assessment Methods
The four relevant risk assessment methods are elaborated in the following paragraphs-
6.1. Risk Identification
For the purpose of risk identification in developing this system, two methods were
primarily undertaken, brainstorming and checklist (Kerzner 2013).
RISK MANAGEMENT IN ENGINEERING
project and hence it is essential to recognize the potential risks associated with the opening up of
a new system and build awareness in regard to the significance of the ‘My health Record
System’ (Lundgren and McMakin 2013).
An effective Communication plan eliminates the conflict of interest and decision among
the project stakeholders and therefore it is very essential for a smooth implementation of the
project (Lando 2014).
In order to develop an effective communication and consultation plan, a proper analysis
of the power and the interest of the stakeholders in necessary to consider (Fassin 2012). The
group of stakeholders who have less power or interest on this project would be least pronounced
in the communication and the consultation plan. While the group of stakeholders who have high
power and interest over this project should be specifically and formally addressed and included
in the communication and consultation plan through proper email. Mass communication should
be made with this group as this group of stakeholder has higher interest in the project. They
should be informed about the project progress in daily basis. The stakeholders included into this
group are the hospital authority and the owner. Stakeholders that have low interest over the
project can be notified about the project progress less often.
6. Four Risk assessment Methods
The four relevant risk assessment methods are elaborated in the following paragraphs-
6.1. Risk Identification
For the purpose of risk identification in developing this system, two methods were
primarily undertaken, brainstorming and checklist (Kerzner 2013).
12
RISK MANAGEMENT IN ENGINEERING
The Brainstorming session was proposed for evaluating the risk that might creep in while
the project is implemented (Keeney 2012). The brainstorming session was performed with the
investing partners and general manager of the hospital along with the project manager in a
number of face-to-face meetings. The results of these meetings and discussions are to be
analyzed in order to indentify the risk associated with the project (refer to appendix 12.1. for risk
identification checklist).
The different areas of risks associated with the project are elaborated in the following
table-
Risk Type Risk Description Risk Class
Finance The project might not be
completed within the assigned
budget
High
Legal Complaints from patients about
data privacy and security may
stop the project leading to huge
financial loss
Low
Technology Malfunctioning of the system,
security and equipments
Medium
Security Failure of securing the
confidentiality of the patients
information
High
Future Competition Competition from other leading
hospital may affect the business
High
RISK MANAGEMENT IN ENGINEERING
The Brainstorming session was proposed for evaluating the risk that might creep in while
the project is implemented (Keeney 2012). The brainstorming session was performed with the
investing partners and general manager of the hospital along with the project manager in a
number of face-to-face meetings. The results of these meetings and discussions are to be
analyzed in order to indentify the risk associated with the project (refer to appendix 12.1. for risk
identification checklist).
The different areas of risks associated with the project are elaborated in the following
table-
Risk Type Risk Description Risk Class
Finance The project might not be
completed within the assigned
budget
High
Legal Complaints from patients about
data privacy and security may
stop the project leading to huge
financial loss
Low
Technology Malfunctioning of the system,
security and equipments
Medium
Security Failure of securing the
confidentiality of the patients
information
High
Future Competition Competition from other leading
hospital may affect the business
High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13
RISK MANAGEMENT IN ENGINEERING
Table 3: Representing the risk areas involved in the project
6.2. Risk Analysis
Risk analysis is a process of reviewing the risks associated with a particular project.
Risks are analyzed on both qualitative and quantitative basis (McNeil, Frey and Embrechts
2015). Risk analysis is an important component of risk management. A proper risk analysis is
essential to estimate the damage that might be a cause of the risk. The analysis demonstrates the
relationship between the probability of the risk in occurring and the amount of damage it might
cause. The risk level is determined by the combination of probability and consequence of the
risk. The hospital authority adopts a proper risk analysis tool and the project manager to evaluate
the risk related to the project (Cox 2012).
6.2.1. The risk Associated with the Project
The risk associated with the project are elaborated in the following table-
SL No. Description of the Risk Likelihood Impact Priority
1. The Project is not
completed within the
estimated schedule
Medium The whole
procedure of
upgrading the
system might be
delayed.
High
2. An error has occurred in
manual uploading of the
previous records
High The whole
procedure of
record uploading
might have to be
High
RISK MANAGEMENT IN ENGINEERING
Table 3: Representing the risk areas involved in the project
6.2. Risk Analysis
Risk analysis is a process of reviewing the risks associated with a particular project.
Risks are analyzed on both qualitative and quantitative basis (McNeil, Frey and Embrechts
2015). Risk analysis is an important component of risk management. A proper risk analysis is
essential to estimate the damage that might be a cause of the risk. The analysis demonstrates the
relationship between the probability of the risk in occurring and the amount of damage it might
cause. The risk level is determined by the combination of probability and consequence of the
risk. The hospital authority adopts a proper risk analysis tool and the project manager to evaluate
the risk related to the project (Cox 2012).
6.2.1. The risk Associated with the Project
The risk associated with the project are elaborated in the following table-
SL No. Description of the Risk Likelihood Impact Priority
1. The Project is not
completed within the
estimated schedule
Medium The whole
procedure of
upgrading the
system might be
delayed.
High
2. An error has occurred in
manual uploading of the
previous records
High The whole
procedure of
record uploading
might have to be
High
14
RISK MANAGEMENT IN ENGINEERING
repeated leading to
a considerable loss
of time.
3. The confidentiality in
patients’ information is not
maintained (Chen and
Zhao 2012).
Low The project may
fail completely as
it is essential to
protect the data
stored in the
system, as it is a
matter of
maintaining the
privacy of the
patients’ details.
High
4. The price of developing
the system is found to be
more than the advantages it
offers
Low This would lead to
considerable
economic loss of
the hospital.
Medium
Table 4: Representing the risks Involved with the project
6.2.2. Existing Controls and Their Effectiveness
RISK MANAGEMENT IN ENGINEERING
repeated leading to
a considerable loss
of time.
3. The confidentiality in
patients’ information is not
maintained (Chen and
Zhao 2012).
Low The project may
fail completely as
it is essential to
protect the data
stored in the
system, as it is a
matter of
maintaining the
privacy of the
patients’ details.
High
4. The price of developing
the system is found to be
more than the advantages it
offers
Low This would lead to
considerable
economic loss of
the hospital.
Medium
Table 4: Representing the risks Involved with the project
6.2.2. Existing Controls and Their Effectiveness

15
RISK MANAGEMENT IN ENGINEERING
Controls are necessarily established to eliminate the probability of risks occurring. The
controls are implemented after discussing its effectiveness with the management and the project
manager.
In any project, human error is a large possibility and hence it is significantly considered
in any risk management process. Therefore, controls are to be carefully written and reviewed
before finalizing. These guidelines are to be handed to the every members of project team at the
beginning of project initiation. The effectiveness of these controls cannot be quantitatively
measured.
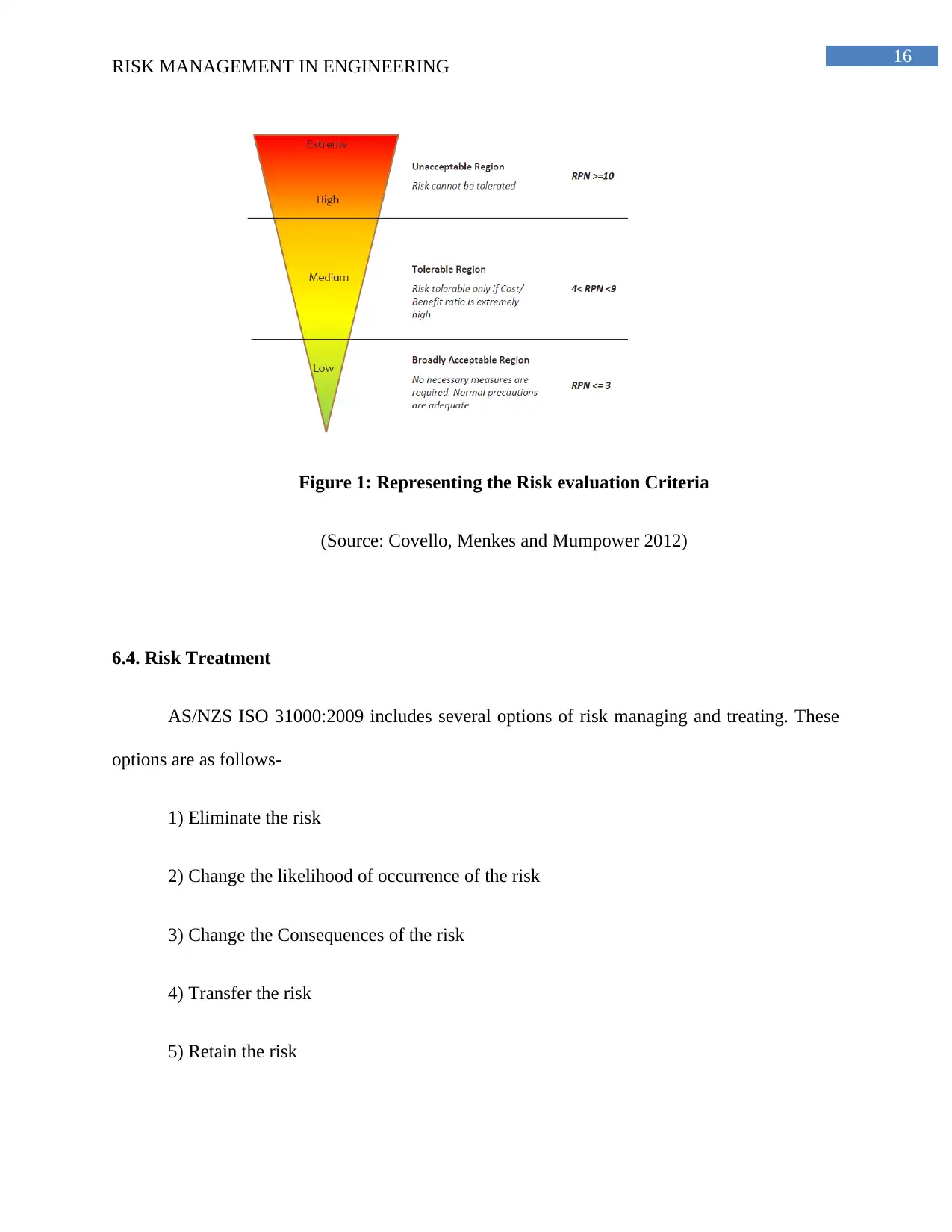
6.3. Risk Evaluation
After analyzing the risks in terms of their probability and consequence, every risk is
segregated into a unique risk rating according to their severity. Every risk is classified into three
categories-> High, Medium and Low. The risks that fall in the ‘High’ region needs immediate
attention and cannot be tolerated, the risks that fall into ‘medium’ category can be tolerated only
if the cost benefit analysis is extremely high, the risk that fall under ‘low’ category can be
ignored (Covello, Menkes and Mumpower 2012). The FMEA Analysis (refer to appendix 12.2.)
is done to identify the possible risk and the damage they would create in the project.
RISK MANAGEMENT IN ENGINEERING
Controls are necessarily established to eliminate the probability of risks occurring. The
controls are implemented after discussing its effectiveness with the management and the project
manager.
In any project, human error is a large possibility and hence it is significantly considered
in any risk management process. Therefore, controls are to be carefully written and reviewed
before finalizing. These guidelines are to be handed to the every members of project team at the
beginning of project initiation. The effectiveness of these controls cannot be quantitatively
measured.
6.3. Risk Evaluation
After analyzing the risks in terms of their probability and consequence, every risk is
segregated into a unique risk rating according to their severity. Every risk is classified into three
categories-> High, Medium and Low. The risks that fall in the ‘High’ region needs immediate
attention and cannot be tolerated, the risks that fall into ‘medium’ category can be tolerated only
if the cost benefit analysis is extremely high, the risk that fall under ‘low’ category can be
ignored (Covello, Menkes and Mumpower 2012). The FMEA Analysis (refer to appendix 12.2.)
is done to identify the possible risk and the damage they would create in the project.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
16
RISK MANAGEMENT IN ENGINEERING
Figure 1: Representing the Risk evaluation Criteria
(Source: Covello, Menkes and Mumpower 2012)
6.4. Risk Treatment
AS/NZS ISO 31000:2009 includes several options of risk managing and treating. These
options are as follows-
1) Eliminate the risk
2) Change the likelihood of occurrence of the risk
3) Change the Consequences of the risk
4) Transfer the risk
5) Retain the risk
RISK MANAGEMENT IN ENGINEERING
Figure 1: Representing the Risk evaluation Criteria
(Source: Covello, Menkes and Mumpower 2012)
6.4. Risk Treatment
AS/NZS ISO 31000:2009 includes several options of risk managing and treating. These
options are as follows-
1) Eliminate the risk
2) Change the likelihood of occurrence of the risk
3) Change the Consequences of the risk
4) Transfer the risk
5) Retain the risk

17
RISK MANAGEMENT IN ENGINEERING
6.4.1. Identification of the appropriate risk treatment
There are several methods present for treating the identified risk. For this particular
project the risk treatment methods were chosen on basis of (Bojanc and Jerman-Blažič 2013)-
1) Suitability and usefulness of the treatment
2) Cost of the treatment
3) Choosing the best alternatives among the existing alternatives
5) Acceptability of the residual risks
Appropriate risk treatment were identified keeping in mind the criteria stated above. The
best risk treatment was so design the project plan in such a way that would eliminate all the
possible financial and security risks (Feng, Wang and Li 2014).
6.4.2. Risk Recovery
Implementation of the project ‘My Health Record System’ is very important and
therefore it is important to have a risk recovery strategy to handle the unexpected and extreme
impacts. A flawless project plan is essential to eliminate the major risks associate with the
project. The most prominent risk associated with this project is storing of the patients’ data in a
secure manner. Elimination of this risk is possible by ensuring that the project plan includes the
development of the system with proper cryptographic methods (Fernandes et al 2014). The
storing of the patients’ information is carried over internet and hence additional security of the
data should be ascertained. However, if any discrepancy occurs in the course of project
implementation, risk recovery techniques and strategies helps in overcoming the adverse effect.
The risk recovery technique applied in this project is crisis management planning that establishes
RISK MANAGEMENT IN ENGINEERING
6.4.1. Identification of the appropriate risk treatment
There are several methods present for treating the identified risk. For this particular
project the risk treatment methods were chosen on basis of (Bojanc and Jerman-Blažič 2013)-
1) Suitability and usefulness of the treatment
2) Cost of the treatment
3) Choosing the best alternatives among the existing alternatives
5) Acceptability of the residual risks
Appropriate risk treatment were identified keeping in mind the criteria stated above. The
best risk treatment was so design the project plan in such a way that would eliminate all the
possible financial and security risks (Feng, Wang and Li 2014).
6.4.2. Risk Recovery
Implementation of the project ‘My Health Record System’ is very important and
therefore it is important to have a risk recovery strategy to handle the unexpected and extreme
impacts. A flawless project plan is essential to eliminate the major risks associate with the
project. The most prominent risk associated with this project is storing of the patients’ data in a
secure manner. Elimination of this risk is possible by ensuring that the project plan includes the
development of the system with proper cryptographic methods (Fernandes et al 2014). The
storing of the patients’ information is carried over internet and hence additional security of the
data should be ascertained. However, if any discrepancy occurs in the course of project
implementation, risk recovery techniques and strategies helps in overcoming the adverse effect.
The risk recovery technique applied in this project is crisis management planning that establishes
18
RISK MANAGEMENT IN ENGINEERING
a backup plan for a financial and security threat. This includes changing the whole projects plan
unless necessary (Carr and Yu 2012).
7. Risk tolerability
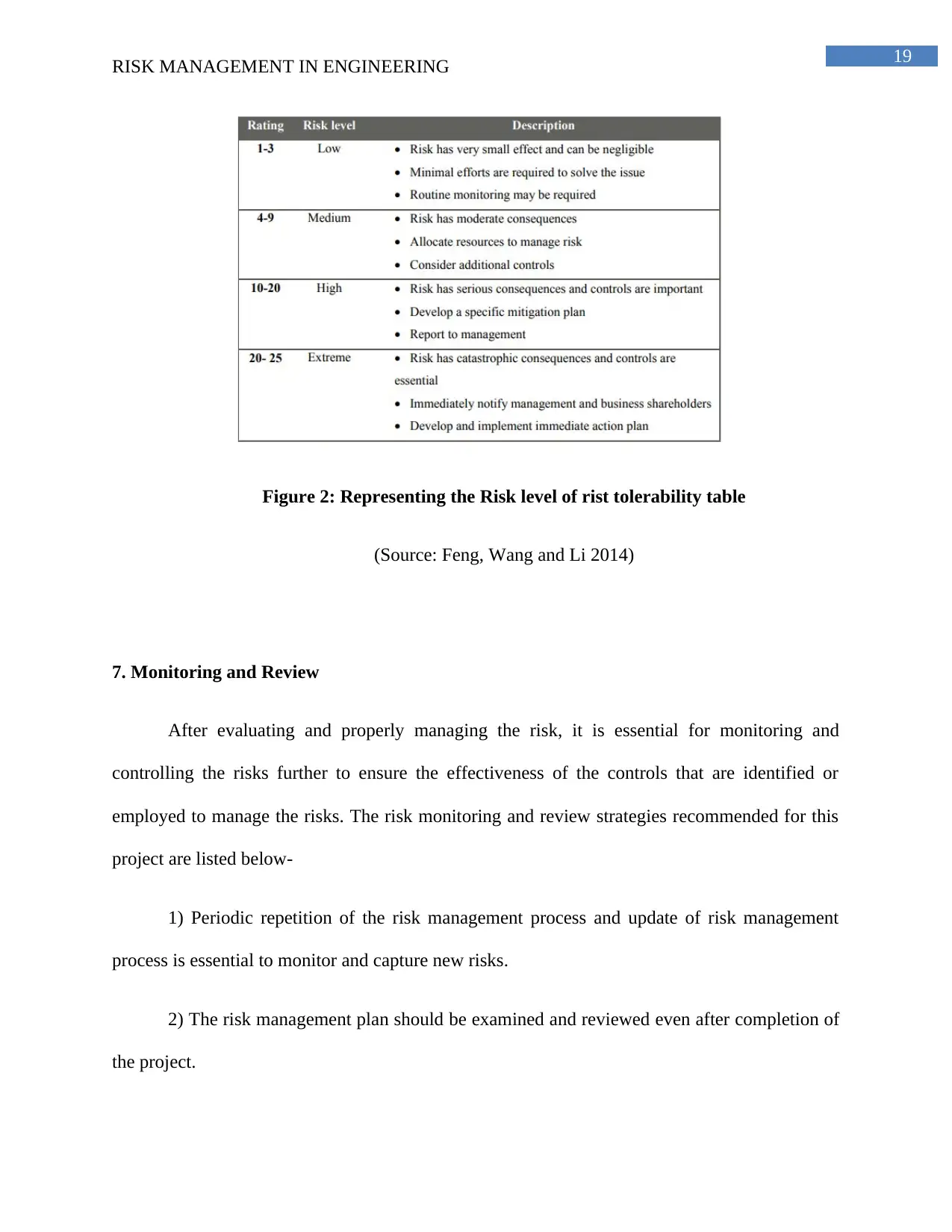
Tolerability of risk identifies the tolerability of risks associated with the system. It is
generally measured in a scale of 1 to 25 with 1 being the lowest risk level and 25 being the
extreme level of risk.
The risk tolerability table matrix is elaborated below-
Almost Certain Medium
5
High
10
High
15
Extreme
20
Extreme
25
Likely Medium
4
Medium
8
High
12
High
16
Extreme
20
Moderate Low
3
Medium
6
Medium
9
High
12
High
15
Unlikely Low
2
Medium
4
Medium
6
Medium
8
High
10
Rare Low
1
Low
2
Low
3
Medium
4
Medium
5
Likelihood
Impact
Insignificant Minor Moderate Major Catastrophic
RISK MANAGEMENT IN ENGINEERING
a backup plan for a financial and security threat. This includes changing the whole projects plan
unless necessary (Carr and Yu 2012).
7. Risk tolerability
Tolerability of risk identifies the tolerability of risks associated with the system. It is
generally measured in a scale of 1 to 25 with 1 being the lowest risk level and 25 being the
extreme level of risk.
The risk tolerability table matrix is elaborated below-
Almost Certain Medium
5
High
10
High
15
Extreme
20
Extreme
25
Likely Medium
4
Medium
8
High
12
High
16
Extreme
20
Moderate Low
3
Medium
6
Medium
9
High
12
High
15
Unlikely Low
2
Medium
4
Medium
6
Medium
8
High
10
Rare Low
1
Low
2
Low
3
Medium
4
Medium
5
Likelihood
Impact
Insignificant Minor Moderate Major Catastrophic
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19
RISK MANAGEMENT IN ENGINEERING
Figure 2: Representing the Risk level of rist tolerability table
(Source: Feng, Wang and Li 2014)
7. Monitoring and Review
After evaluating and properly managing the risk, it is essential for monitoring and
controlling the risks further to ensure the effectiveness of the controls that are identified or
employed to manage the risks. The risk monitoring and review strategies recommended for this
project are listed below-
1) Periodic repetition of the risk management process and update of risk management
process is essential to monitor and capture new risks.
2) The risk management plan should be examined and reviewed even after completion of
the project.
RISK MANAGEMENT IN ENGINEERING
Figure 2: Representing the Risk level of rist tolerability table
(Source: Feng, Wang and Li 2014)
7. Monitoring and Review
After evaluating and properly managing the risk, it is essential for monitoring and
controlling the risks further to ensure the effectiveness of the controls that are identified or
employed to manage the risks. The risk monitoring and review strategies recommended for this
project are listed below-
1) Periodic repetition of the risk management process and update of risk management
process is essential to monitor and capture new risks.
2) The risk management plan should be examined and reviewed even after completion of
the project.

20
RISK MANAGEMENT IN ENGINEERING
3) Observed risk should be properly recorded in the risk register.
8. Societal benefits of risk exposure
The societal benefits of risk exposure are listed below-
1) The patients will have a clear idea about the security policies of the new system
2) The system will be beneficial not only for the inpatient but for the casualties as well
3) The system will give financial benefit to the hospital
4) It prevents further creeping up of the risk into the system
5) Exposes the vulnerability of the project under development
9. Risk Closure
The responsibility of the risk assemenet manger is to close a risk once it has been treted.
The conmdition of risk closing are as follows-
1) Ensuring that the treatment actions are properly implemented
2) Positive feedback has been received after the risk treatment
3) No additional risk has been encountered while treating an existing risk.
10. Conclusion
Therefore, from the above discussion it can be concluded that risk management is very
essential for successful implementation of the project. Certain steps are undertaken for proper
risk management. These include, establishing the context of the risk, evaluating the risk criteria,
RISK MANAGEMENT IN ENGINEERING
3) Observed risk should be properly recorded in the risk register.
8. Societal benefits of risk exposure
The societal benefits of risk exposure are listed below-
1) The patients will have a clear idea about the security policies of the new system
2) The system will be beneficial not only for the inpatient but for the casualties as well
3) The system will give financial benefit to the hospital
4) It prevents further creeping up of the risk into the system
5) Exposes the vulnerability of the project under development
9. Risk Closure
The responsibility of the risk assemenet manger is to close a risk once it has been treted.
The conmdition of risk closing are as follows-
1) Ensuring that the treatment actions are properly implemented
2) Positive feedback has been received after the risk treatment
3) No additional risk has been encountered while treating an existing risk.
10. Conclusion
Therefore, from the above discussion it can be concluded that risk management is very
essential for successful implementation of the project. Certain steps are undertaken for proper
risk management. These include, establishing the context of the risk, evaluating the risk criteria,

21
RISK MANAGEMENT IN ENGINEERING
analyzing the relevant stakeholders, establishing a proper communication and consultation plan,
identification of the risk, risk analysis and risk evaluation followed by the proper treatment of the
risk and monitoring the risk. A risk manager is to be appointed for properly managing all the
aspects of a risk management process. After analyzing evaluating and eliminating the risk from a
project, it is essential to monitor the risk even after its elimination. This is essential to prevent the
any type of further risk creeping into the system or project. Since this project deals with the
storing of patients’ data over electronic means, maintaining the security of the data is very
essential. This is ensured by involving proper cryptographic methods and encryption as various
means of data security. After proper risk treatment and getting a satisfied result, the risk can be
subsequently closed after evaluating certain criteria and ensuring that the risk would not creep
into the system once again.
RISK MANAGEMENT IN ENGINEERING
analyzing the relevant stakeholders, establishing a proper communication and consultation plan,
identification of the risk, risk analysis and risk evaluation followed by the proper treatment of the
risk and monitoring the risk. A risk manager is to be appointed for properly managing all the
aspects of a risk management process. After analyzing evaluating and eliminating the risk from a
project, it is essential to monitor the risk even after its elimination. This is essential to prevent the
any type of further risk creeping into the system or project. Since this project deals with the
storing of patients’ data over electronic means, maintaining the security of the data is very
essential. This is ensured by involving proper cryptographic methods and encryption as various
means of data security. After proper risk treatment and getting a satisfied result, the risk can be
subsequently closed after evaluating certain criteria and ensuring that the risk would not creep
into the system once again.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22
RISK MANAGEMENT IN ENGINEERING
11. References
Bojanc, R. and Jerman-Blažič, B., 2013. A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), pp.25-37.
Carr, P. and Yu, J., 2012. Risk, return, and Ross recovery. The Journal of Derivatives, 20(1),
pp.38-59.
Chen, D. and Zhao, H., 2012, March. Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012 International
Conference on (Vol. 1, pp. 647-651). IEEE.
Christoffersen, P.F., 2012. Elements of financial risk management. Academic Press.
Covello, V.T., Menkes, J. and Mumpower, J.L. eds., 2012. Risk evaluation and management
(Vol. 1). Springer Science & Business Media.
Cox, L.A.T., 2012. Confronting deep uncertainties in risk analysis. Risk Analysis, 32(10),
pp.1607-1629.
Ernawati, T. and Nugroho, D.R., 2012, September. IT risk management framework based on ISO
31000: 2009. In System Engineering and Technology (ICSET), 2012 International Conference
on (pp. 1-8). IEEE.
Fassin, Y., 2012. Stakeholder management, reciprocity and stakeholder responsibility. Journal of
Business Ethics, 109(1), pp.83-96.
RISK MANAGEMENT IN ENGINEERING
11. References
Bojanc, R. and Jerman-Blažič, B., 2013. A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), pp.25-37.
Carr, P. and Yu, J., 2012. Risk, return, and Ross recovery. The Journal of Derivatives, 20(1),
pp.38-59.
Chen, D. and Zhao, H., 2012, March. Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012 International
Conference on (Vol. 1, pp. 647-651). IEEE.
Christoffersen, P.F., 2012. Elements of financial risk management. Academic Press.
Covello, V.T., Menkes, J. and Mumpower, J.L. eds., 2012. Risk evaluation and management
(Vol. 1). Springer Science & Business Media.
Cox, L.A.T., 2012. Confronting deep uncertainties in risk analysis. Risk Analysis, 32(10),
pp.1607-1629.
Ernawati, T. and Nugroho, D.R., 2012, September. IT risk management framework based on ISO
31000: 2009. In System Engineering and Technology (ICSET), 2012 International Conference
on (pp. 1-8). IEEE.
Fassin, Y., 2012. Stakeholder management, reciprocity and stakeholder responsibility. Journal of
Business Ethics, 109(1), pp.83-96.

23
RISK MANAGEMENT IN ENGINEERING
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information sciences,
256, pp.57-73.
Fernandes, D.A., Soares, L.F., Gomes, J.V., Freire, M.M. and Inácio, P.R., 2014. Security issues
in cloud environments: a survey. International Journal of Information Security, 13(2), pp.113-
170.
Harrison, J.S. and Wicks, A.C., 2013. Stakeholder theory, value, and firm performance. Business
ethics quarterly, 23(1), pp.97-124.
Hopkin, P., 2017. Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Keeney, R.L., 2012. Value-focused brainstorming. Decision Analysis, 9(4), pp.303-313.
Kerzner, H., 2013. Project management: a systems approach to planning, scheduling, and
controlling. John Wiley & Sons.
Kulkarni, G., Chavan, N., Chandorkar, R., Waghmare, R. and Palwe, R., 2012, October. Cloud
security challenges. In Telecommunication Systems, Services, and Applications (TSSA), 2012
7th International Conference on (pp. 88-91). IEEE.
Lam, J., 2014. Enterprise risk management: from incentives to controls. John Wiley & Sons.
Lando, A.L., 2014. The critical role of crisis communication plan in corporations' crises
preparedness and management. Global Media Journal, 7(1), p.5.
RISK MANAGEMENT IN ENGINEERING
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information sciences,
256, pp.57-73.
Fernandes, D.A., Soares, L.F., Gomes, J.V., Freire, M.M. and Inácio, P.R., 2014. Security issues
in cloud environments: a survey. International Journal of Information Security, 13(2), pp.113-
170.
Harrison, J.S. and Wicks, A.C., 2013. Stakeholder theory, value, and firm performance. Business
ethics quarterly, 23(1), pp.97-124.
Hopkin, P., 2017. Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Keeney, R.L., 2012. Value-focused brainstorming. Decision Analysis, 9(4), pp.303-313.
Kerzner, H., 2013. Project management: a systems approach to planning, scheduling, and
controlling. John Wiley & Sons.
Kulkarni, G., Chavan, N., Chandorkar, R., Waghmare, R. and Palwe, R., 2012, October. Cloud
security challenges. In Telecommunication Systems, Services, and Applications (TSSA), 2012
7th International Conference on (pp. 88-91). IEEE.
Lam, J., 2014. Enterprise risk management: from incentives to controls. John Wiley & Sons.
Lando, A.L., 2014. The critical role of crisis communication plan in corporations' crises
preparedness and management. Global Media Journal, 7(1), p.5.

24
RISK MANAGEMENT IN ENGINEERING
Lienert, J., Schnetzer, F. and Ingold, K., 2013. Stakeholder analysis combined with social
network analysis provides fine-grained insights into water infrastructure planning processes.
Journal of environmental management, 125, pp.134-148.
Lundgren, R.E. and McMakin, A.H., 2013. Risk communication: A handbook for
communicating environmental, safety, and health risks. John Wiley & Sons.
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Pacheco, C. and Garcia, I., 2012. A systematic literature review of stakeholder identification
methods in requirements elicitation. Journal of Systems and Software, 85(9), pp.2171-2181.
Sadgrove, K., 2016. The complete guide to business risk management. Routledge.
Woods, S.S., Schwartz, E., Tuepker, A., Press, N.A., Nazi, K.M., Turvey, C.L. and Nichol, W.P.,
2013. Patient experiences with full electronic access to health records and clinical notes through
the My HealtheVet Personal Health Record Pilot: qualitative study. Journal of medical Internet
research, 15(3).
RISK MANAGEMENT IN ENGINEERING
Lienert, J., Schnetzer, F. and Ingold, K., 2013. Stakeholder analysis combined with social
network analysis provides fine-grained insights into water infrastructure planning processes.
Journal of environmental management, 125, pp.134-148.
Lundgren, R.E. and McMakin, A.H., 2013. Risk communication: A handbook for
communicating environmental, safety, and health risks. John Wiley & Sons.
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Pacheco, C. and Garcia, I., 2012. A systematic literature review of stakeholder identification
methods in requirements elicitation. Journal of Systems and Software, 85(9), pp.2171-2181.
Sadgrove, K., 2016. The complete guide to business risk management. Routledge.
Woods, S.S., Schwartz, E., Tuepker, A., Press, N.A., Nazi, K.M., Turvey, C.L. and Nichol, W.P.,
2013. Patient experiences with full electronic access to health records and clinical notes through
the My HealtheVet Personal Health Record Pilot: qualitative study. Journal of medical Internet
research, 15(3).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
25
RISK MANAGEMENT IN ENGINEERING
12. Appendix
12.1. Risk Identification Checklist
Sl no Description Yes/No
1. Is the planning of the system development abide by the
objective
2. Are the objectives clear to the project manager?
3. Is the system development following Agile methodology?
4. Is proper schedule being allocated for the system
development?
5. Is proper cryptographic method ensured in coding?
6. Has proper feasibility study of the project been performed?
7. Is the budget allocated sufficient for the system
development?
8. Have the user been properly trained to use the new system?
9. Has the recovery plan included in the system
implementation?
10. Has the tools of software development properly planned?
RISK MANAGEMENT IN ENGINEERING
12. Appendix
12.1. Risk Identification Checklist
Sl no Description Yes/No
1. Is the planning of the system development abide by the
objective
2. Are the objectives clear to the project manager?
3. Is the system development following Agile methodology?
4. Is proper schedule being allocated for the system
development?
5. Is proper cryptographic method ensured in coding?
6. Has proper feasibility study of the project been performed?
7. Is the budget allocated sufficient for the system
development?
8. Have the user been properly trained to use the new system?
9. Has the recovery plan included in the system
implementation?
10. Has the tools of software development properly planned?
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




