Analyzing TCP/IP, IPv4, Network Structure and Identification
VerifiedAdded on 2022/09/09
|7
|1011
|35
Homework Assignment
AI Summary
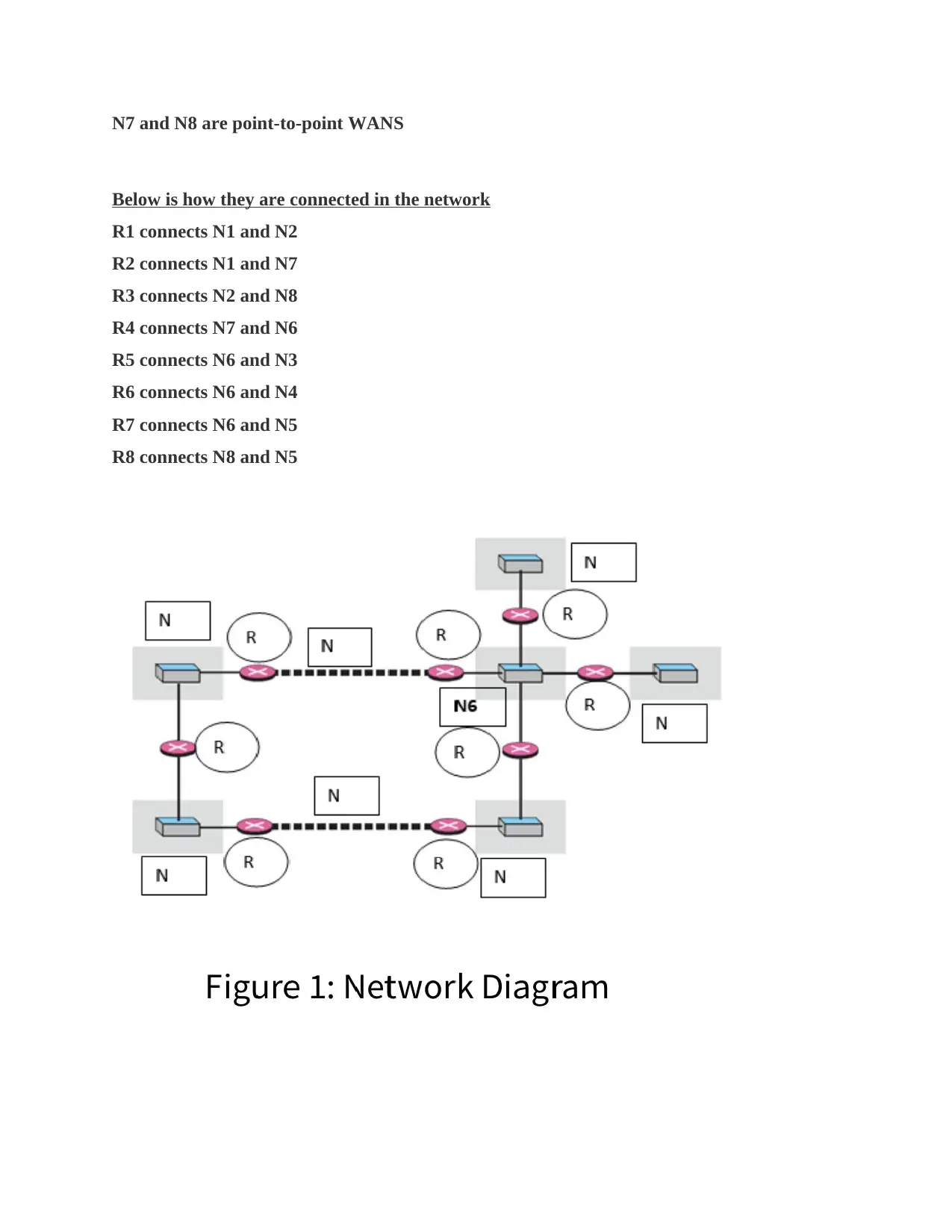
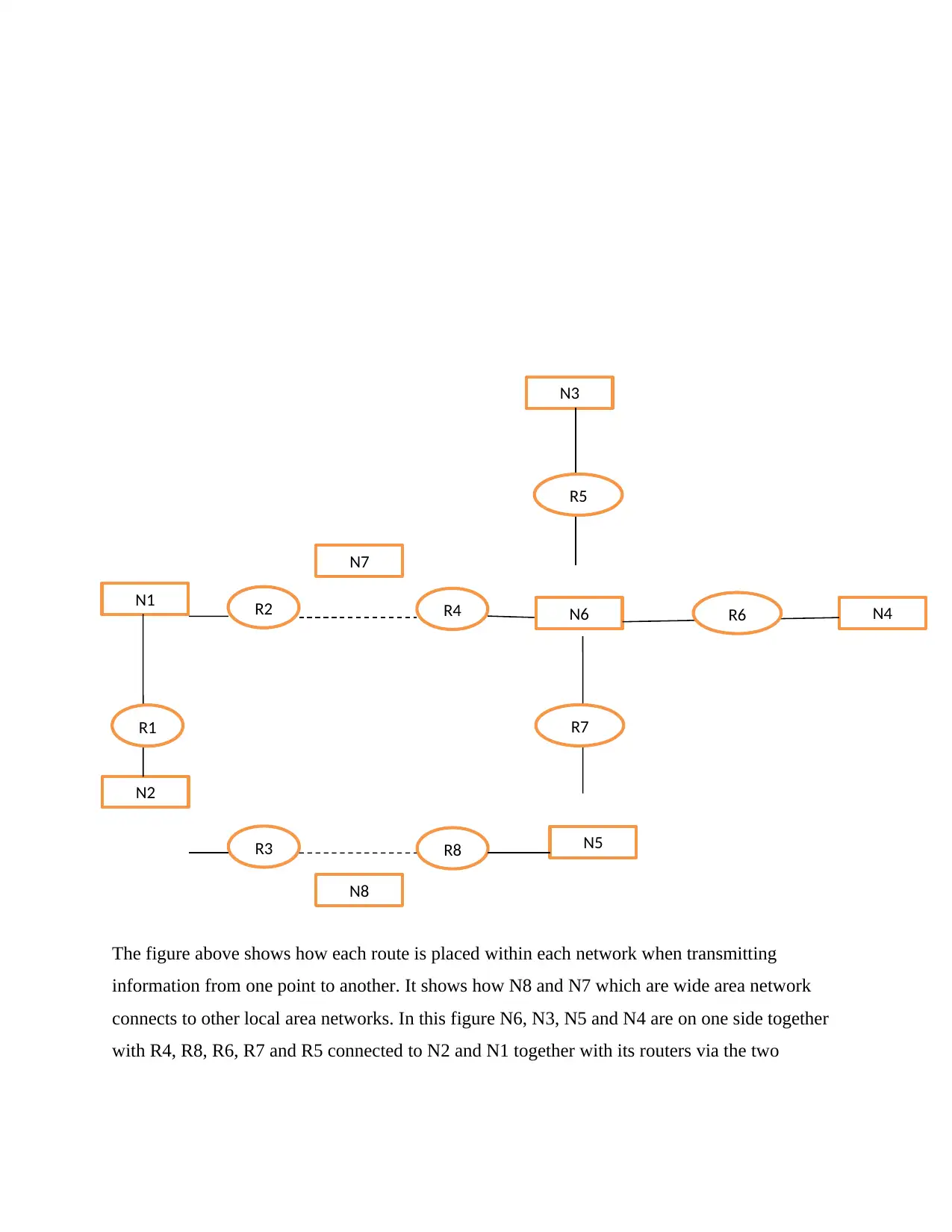
This assignment solution addresses key concepts in computer networks, focusing on the TCP/IP protocol suite and IPv4 addressing. The solution begins by outlining the three primary tasks handled by the internet layer, including data unit transmission, packet rearrangement, and error detection. It then describes the IPv4 header length field, explaining its variable nature and purpose in notifying the packet processor. The solution also details the IPv4 Identification field, explaining its role in detecting and removing duplicate datagrams, along with its use as a diagnostic tool. Furthermore, the assignment classifies given IP addresses (227.12.14.87 and 14.23.120.8), identifying them as Class D and Class A, respectively, and describing their typical uses. Finally, the solution identifies and describes the networks and routers in a provided network diagram, highlighting the connections between Ethernet LANs and point-to-point WANs. The solution references several sources to support the discussed concepts.
1 out of 7











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)