Analysis of Host Discovery Assignment 2022
VerifiedAdded on 2022/09/28
|22
|1377
|21
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
PART A.........................................................................................................................................................3
Project summary.....................................................................................................................................3
summarize...............................................................................................................................................5
Tasks (four tasks) of Nmap.....................................................................................................................5
Feature........................................................................................................................................................6
a).............................................................................................................................................................6
b).............................................................................................................................................................6
C).............................................................................................................................................................6
d).............................................................................................................................................................6
Mitigation plan............................................................................................................................................6
Analysis of host discovery............................................................................................................................7
PART B.......................................................................................................................................................12
Setup of Firewall...................................................................................................................................12
Practical.................................................................................................................................................13
firewall Status........................................................................................................................................15
Enable firewall or disable firewall..........................................................................................................15
3. Add a firewall rule and Allow services TCP, SSH and samba..............................................................16
4. Check firewall rules............................................................................................................................17
5 . Allow HTTP port, deny the port........................................................................................................17
6. Allow and deny protocol from any to any port..............................................................................18
7. Check firewall rules........................................................................................................................19
8. Allow HTTP for access specific service............................................................................................20
Conclusion.................................................................................................................................................22
Page | 2
PART A.........................................................................................................................................................3
Project summary.....................................................................................................................................3
summarize...............................................................................................................................................5
Tasks (four tasks) of Nmap.....................................................................................................................5
Feature........................................................................................................................................................6
a).............................................................................................................................................................6
b).............................................................................................................................................................6
C).............................................................................................................................................................6
d).............................................................................................................................................................6
Mitigation plan............................................................................................................................................6
Analysis of host discovery............................................................................................................................7
PART B.......................................................................................................................................................12
Setup of Firewall...................................................................................................................................12
Practical.................................................................................................................................................13
firewall Status........................................................................................................................................15
Enable firewall or disable firewall..........................................................................................................15
3. Add a firewall rule and Allow services TCP, SSH and samba..............................................................16
4. Check firewall rules............................................................................................................................17
5 . Allow HTTP port, deny the port........................................................................................................17
6. Allow and deny protocol from any to any port..............................................................................18
7. Check firewall rules........................................................................................................................19
8. Allow HTTP for access specific service............................................................................................20
Conclusion.................................................................................................................................................22
Page | 2

PART A
Project summary
The network is very significant for the business process. Without a network, we cannot increase the
efficiency of the business process. The network helps us to generate information and increase
communication. Information will be broken down into packets and information packets send on the
network from source to destination. Day by day network communication is increasing but there is also
increasing the possibility of the hacking. Security issues also increasing due to the cracker. They are
stealing information on the network and they are responsible for the loss of information. network
security is a primary objective for any company. Without security, we cannot provide the quality of the
service. Weak security will increase the gap of the network (G. S. Rao. 2014). There are various network
security tool is available on the network. Here, we are going to use the Nmap tool. This tool helps to
check and monitoring the network. Nmap helps to map and protect the network. We can also scan the
port of the network and check the vulnerability. This tool helps to configure the network server and also
scan the insecure network.
Page | 3
Project summary
The network is very significant for the business process. Without a network, we cannot increase the
efficiency of the business process. The network helps us to generate information and increase
communication. Information will be broken down into packets and information packets send on the
network from source to destination. Day by day network communication is increasing but there is also
increasing the possibility of the hacking. Security issues also increasing due to the cracker. They are
stealing information on the network and they are responsible for the loss of information. network
security is a primary objective for any company. Without security, we cannot provide the quality of the
service. Weak security will increase the gap of the network (G. S. Rao. 2014). There are various network
security tool is available on the network. Here, we are going to use the Nmap tool. This tool helps to
check and monitoring the network. Nmap helps to map and protect the network. We can also scan the
port of the network and check the vulnerability. This tool helps to configure the network server and also
scan the insecure network.
Page | 3

summarize
The network security tool helps to protect network data. Nmap is helped to scan the port of the network
and check the port is secure or not. the map can check the open port of the system. Nmap does not
allow to illegally. This tool helps to explorer device and helps to protect the network. map ensure the
valid configuration of the network and also check the firewall configuration. It can scan and filter the
ports of the network. Nmap has a smart default network setting and you can run the Nmap without any
specific setting. It is a better choice to a user the Nmap tool for network security. We can choose the
tool which helps to identify the network IP address. It also helps to identify the IP address of the
network (S. Shin. 2013). Nmap is an open-source tool and we can use it without any license. Nmap
provides the program which is capable the manage the network services and host control. It also helps
to filter the packets. This tool able to scan the network with high speed.
Tasks (four tasks) of Nmap
we can easily scan the vulnerabilities of TCP protocol. As per the study of RCF. No one packet has SYN
and RSS, AC. It does not get any response and no return of the package. It can scan and pass through
the router and firewall filter.
It helps to scan and helps to filter. It is an IDS system that helps to identify the zombies. The remote
device will be an explorer by NIPP.
An Nmap scan covers the filter in some cases like an IPID scan. The NIPP manager exports to a remote
device using another device. (Often referred to as zombies) without collecting information each (Gordon
Lyon.2002).
It helps to protect the system and networks from the attacks.
It helps to set up a firewall and identifies the open port.
We can use -SA and set up the firewall by TCP ACK.
It helps to network mapping and also helps to host detection.
It helps to detect the operating system.
Page | 4
The network security tool helps to protect network data. Nmap is helped to scan the port of the network
and check the port is secure or not. the map can check the open port of the system. Nmap does not
allow to illegally. This tool helps to explorer device and helps to protect the network. map ensure the
valid configuration of the network and also check the firewall configuration. It can scan and filter the
ports of the network. Nmap has a smart default network setting and you can run the Nmap without any
specific setting. It is a better choice to a user the Nmap tool for network security. We can choose the
tool which helps to identify the network IP address. It also helps to identify the IP address of the
network (S. Shin. 2013). Nmap is an open-source tool and we can use it without any license. Nmap
provides the program which is capable the manage the network services and host control. It also helps
to filter the packets. This tool able to scan the network with high speed.
Tasks (four tasks) of Nmap
we can easily scan the vulnerabilities of TCP protocol. As per the study of RCF. No one packet has SYN
and RSS, AC. It does not get any response and no return of the package. It can scan and pass through
the router and firewall filter.
It helps to scan and helps to filter. It is an IDS system that helps to identify the zombies. The remote
device will be an explorer by NIPP.
An Nmap scan covers the filter in some cases like an IPID scan. The NIPP manager exports to a remote
device using another device. (Often referred to as zombies) without collecting information each (Gordon
Lyon.2002).
It helps to protect the system and networks from the attacks.
It helps to set up a firewall and identifies the open port.
We can use -SA and set up the firewall by TCP ACK.
It helps to network mapping and also helps to host detection.
It helps to detect the operating system.
Page | 4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

It helps to scan and detect the service directory like the name of the server.
It helps to monitor and control the network traffic (Gordon Lyon.2002). It also helps to identify the
network error.
Feature
a)
It improves and provides the functionality of NSE.
It provides support for IPv6
Provide faster network scanning
Provide service for TLS/SSL scanning.
b)
It is taking more time for UDP scanning.
C)
It improves network discovery performance and makes it faster.
d)
Mitigation plan
Identify all the risks and determine participation and support services.
Manage the limitation and requirement of the program which helps to reduce the risk and also helps to
schedule.
Take decision and action for minimizing loss and risk.
Change the environment which helps to reduce the risk (Unknown Author.2015).
Page | 5
It helps to monitor and control the network traffic (Gordon Lyon.2002). It also helps to identify the
network error.
Feature
a)
It improves and provides the functionality of NSE.
It provides support for IPv6
Provide faster network scanning
Provide service for TLS/SSL scanning.
b)
It is taking more time for UDP scanning.
C)
It improves network discovery performance and makes it faster.
d)
Mitigation plan
Identify all the risks and determine participation and support services.
Manage the limitation and requirement of the program which helps to reduce the risk and also helps to
schedule.
Take decision and action for minimizing loss and risk.
Change the environment which helps to reduce the risk (Unknown Author.2015).
Page | 5
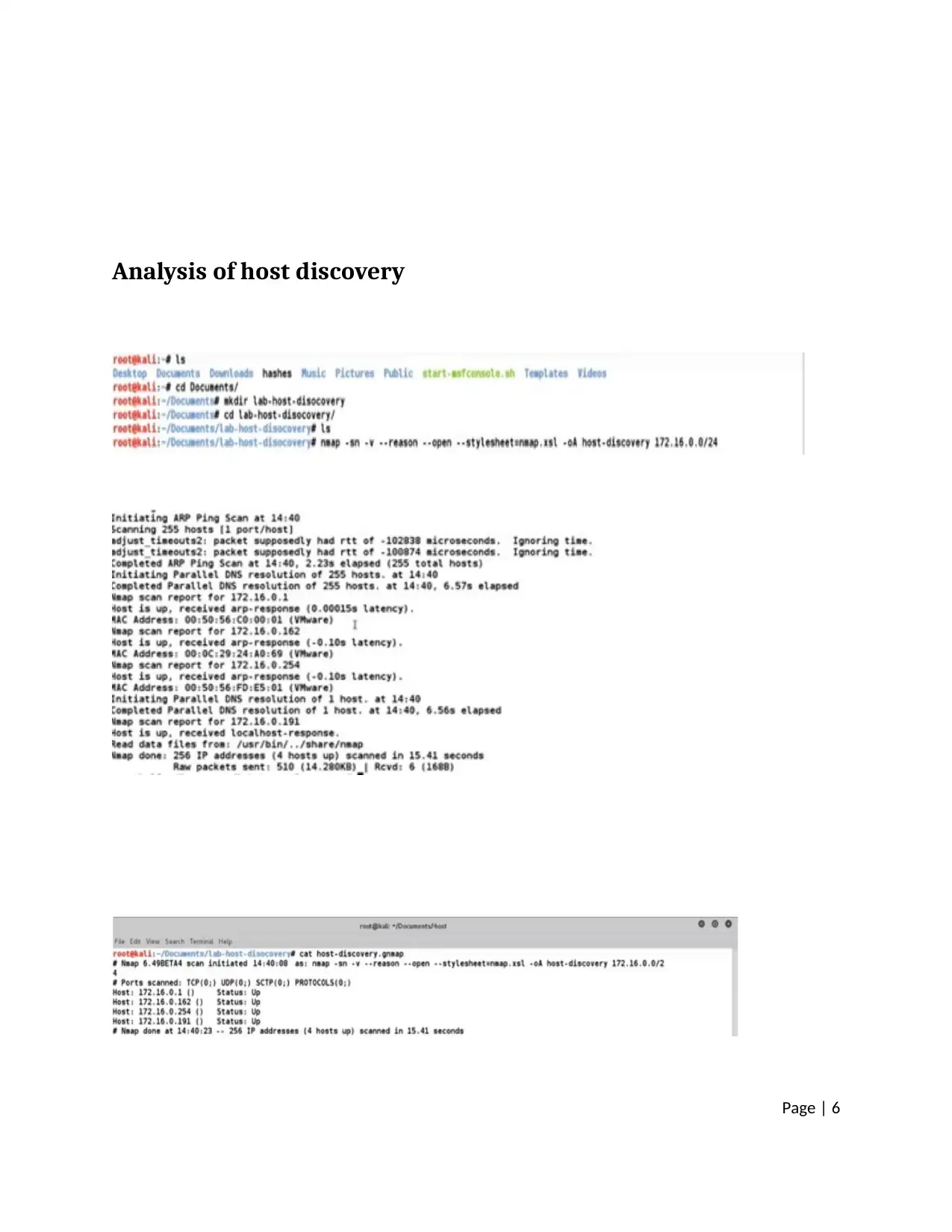
Analysis of host discovery
Page | 6
Page | 6
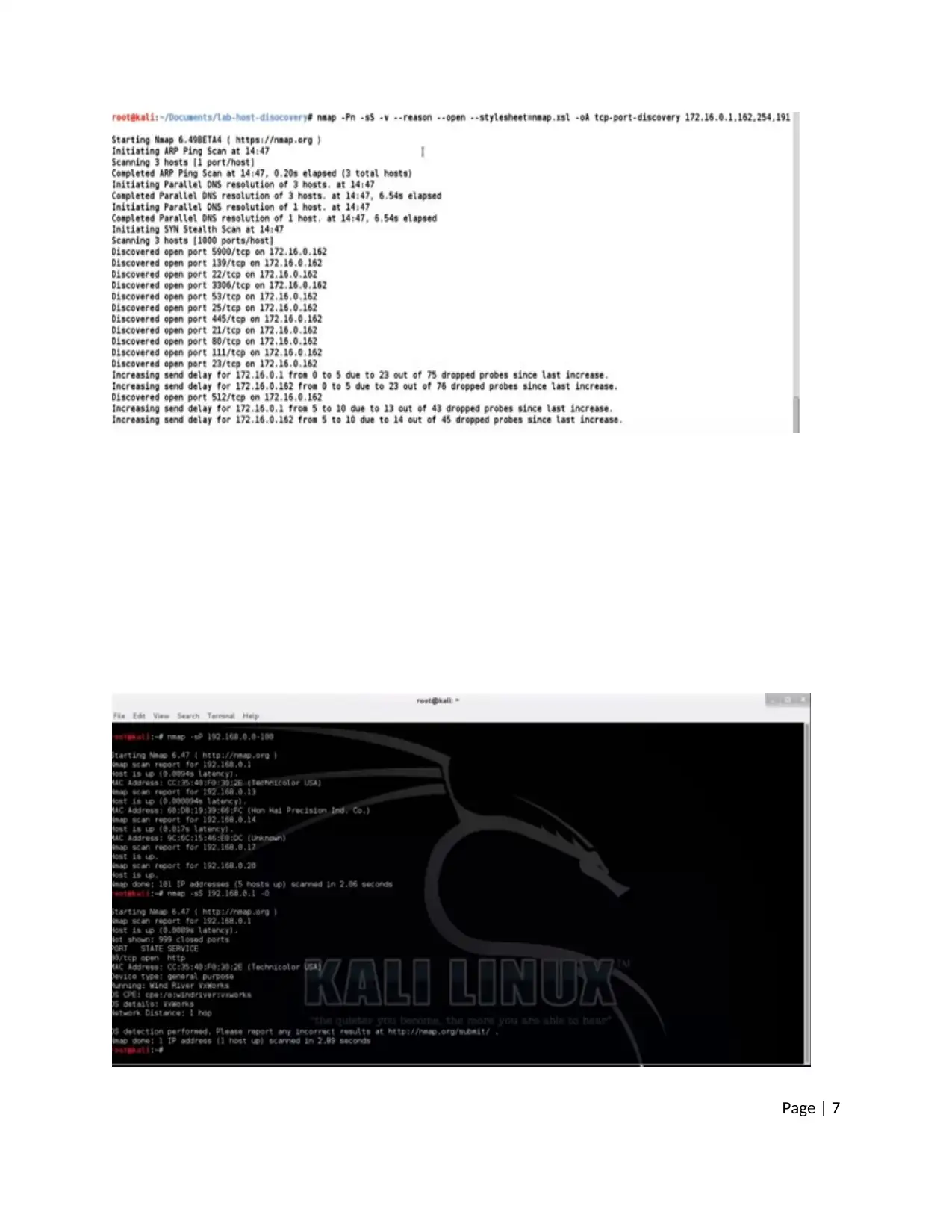
Page | 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
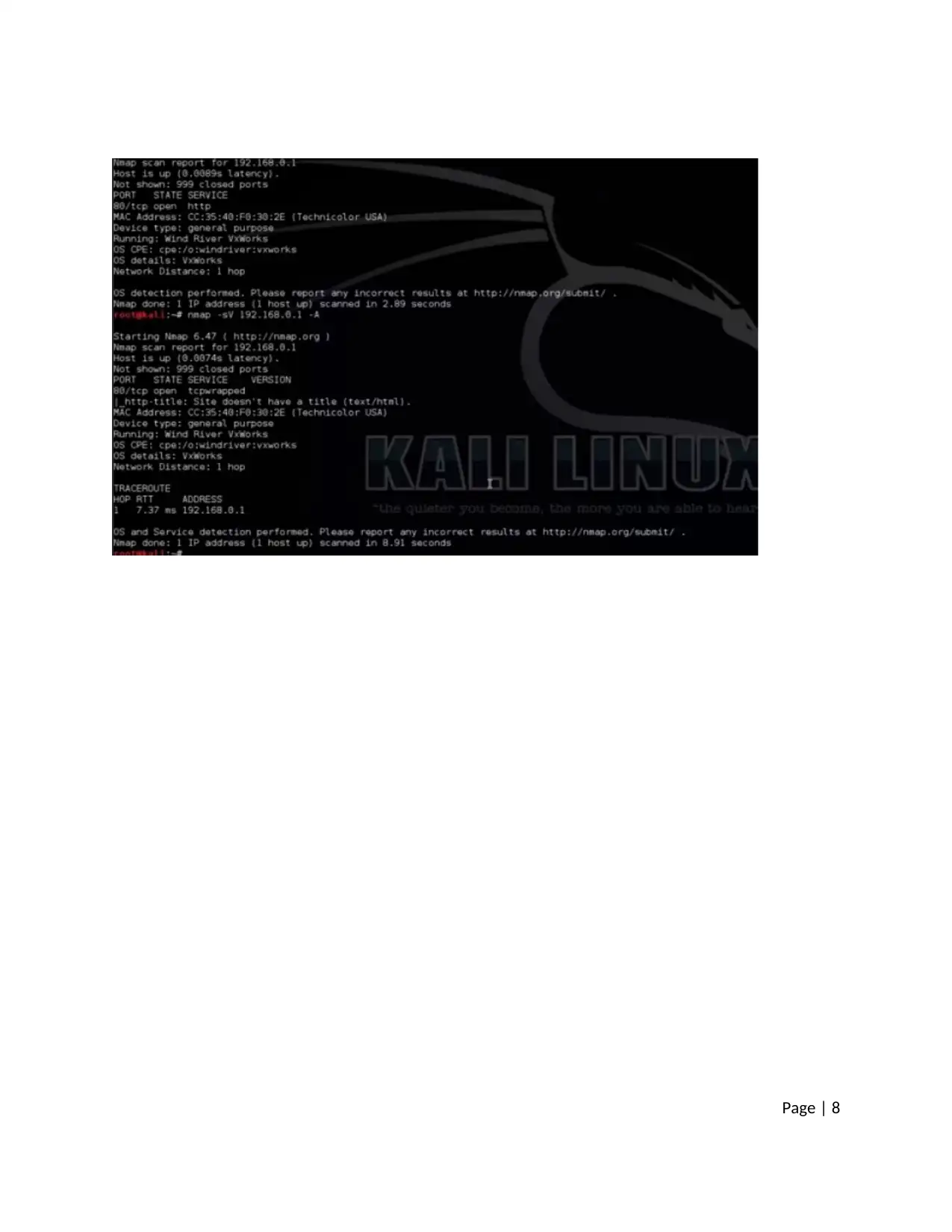
Page | 8
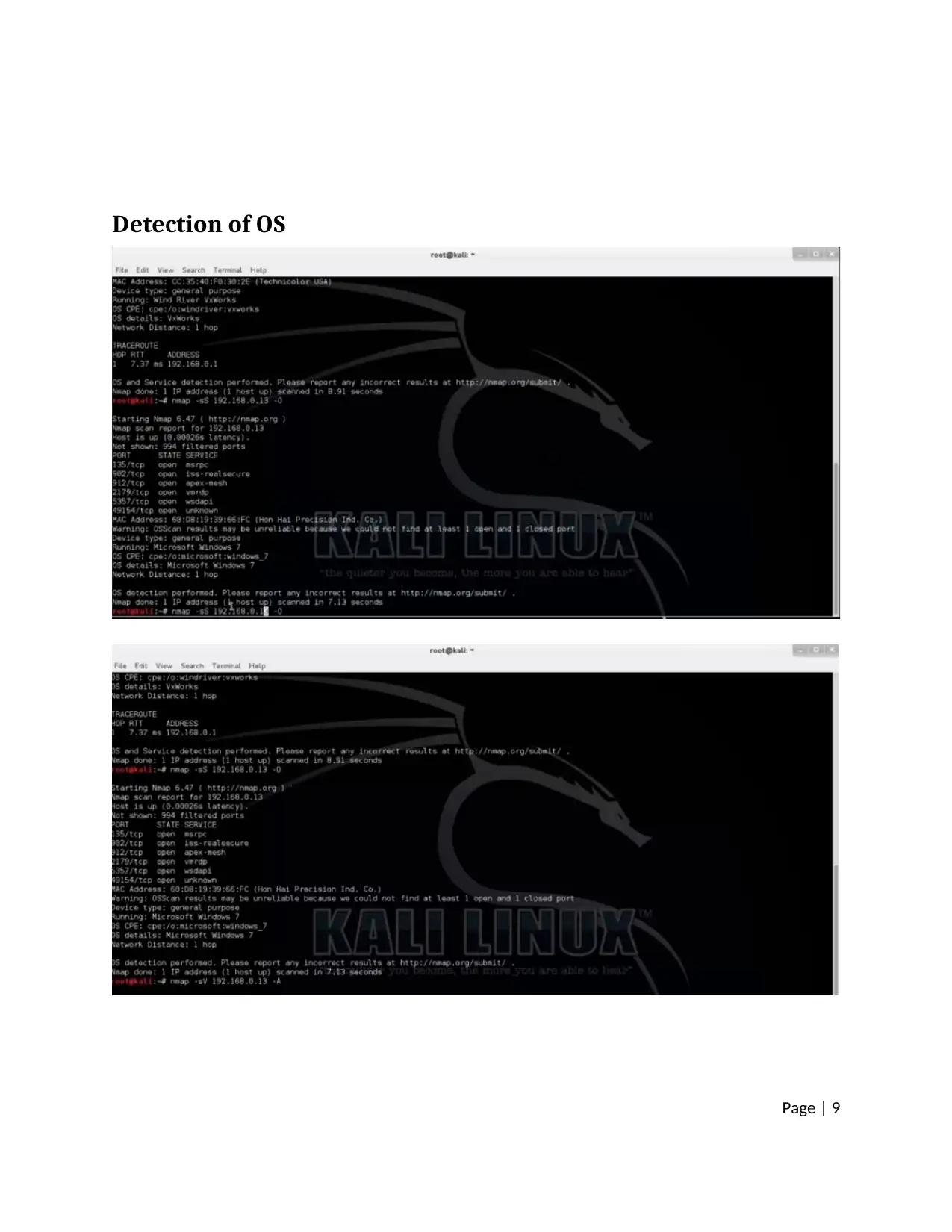
Detection of OS
Page | 9
Page | 9

PART B
Setup of Firewall
Here, the Nmap is valuable tool and very powerful tool that used for discovering the data about network
over the internet. It is used to allows the machine send the packets that are used to detect a whole
things from the running services. Also help to detect the open ports to the software versions and the
operating system (Gordon Lyon.2002). Here, the firewall is used for filter packets. We can scan the
system with the help of Nmap.
NSE
Page | 10
Setup of Firewall
Here, the Nmap is valuable tool and very powerful tool that used for discovering the data about network
over the internet. It is used to allows the machine send the packets that are used to detect a whole
things from the running services. Also help to detect the open ports to the software versions and the
operating system (Gordon Lyon.2002). Here, the firewall is used for filter packets. We can scan the
system with the help of Nmap.
NSE
Page | 10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
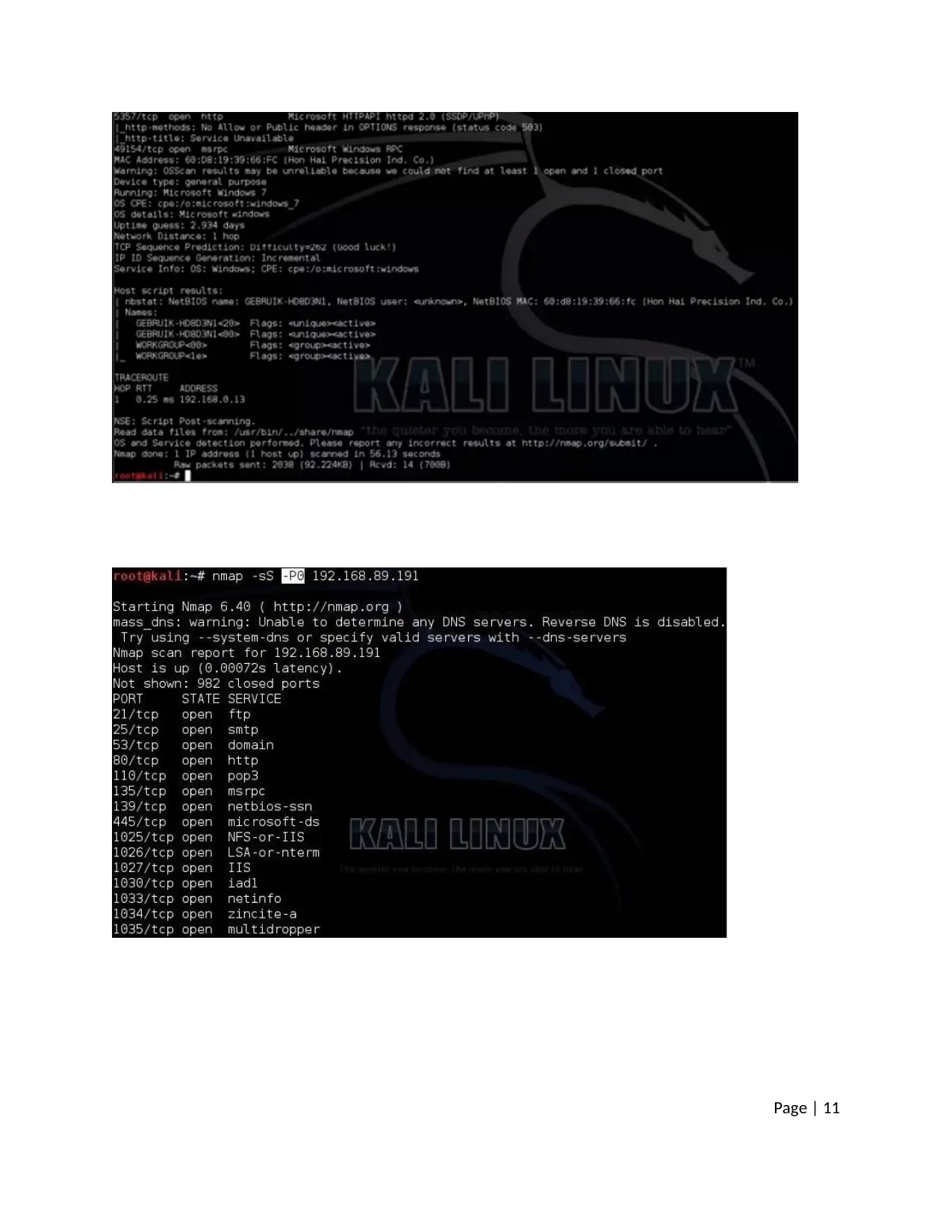
Page | 11
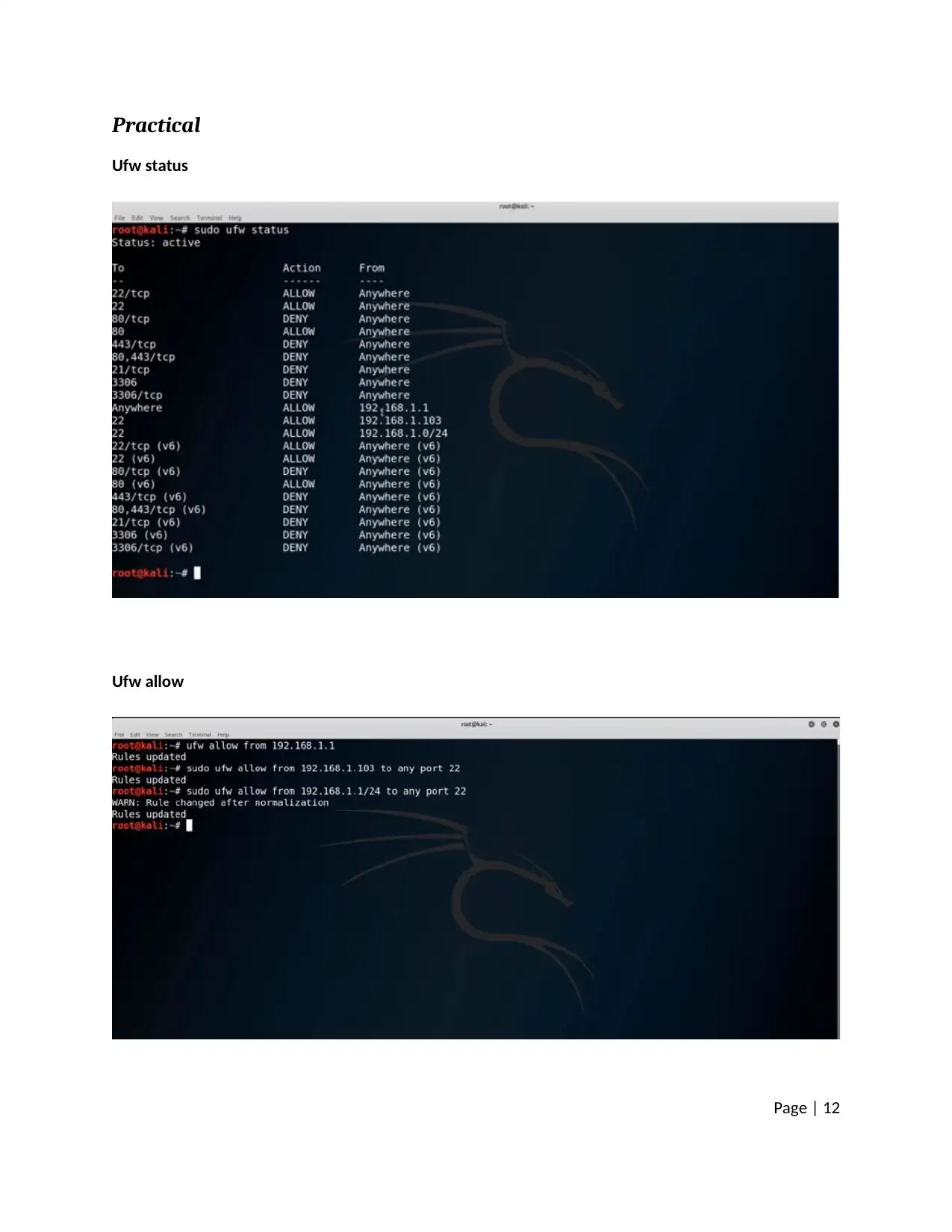
Practical
Ufw status
Ufw allow
Page | 12
Ufw status
Ufw allow
Page | 12
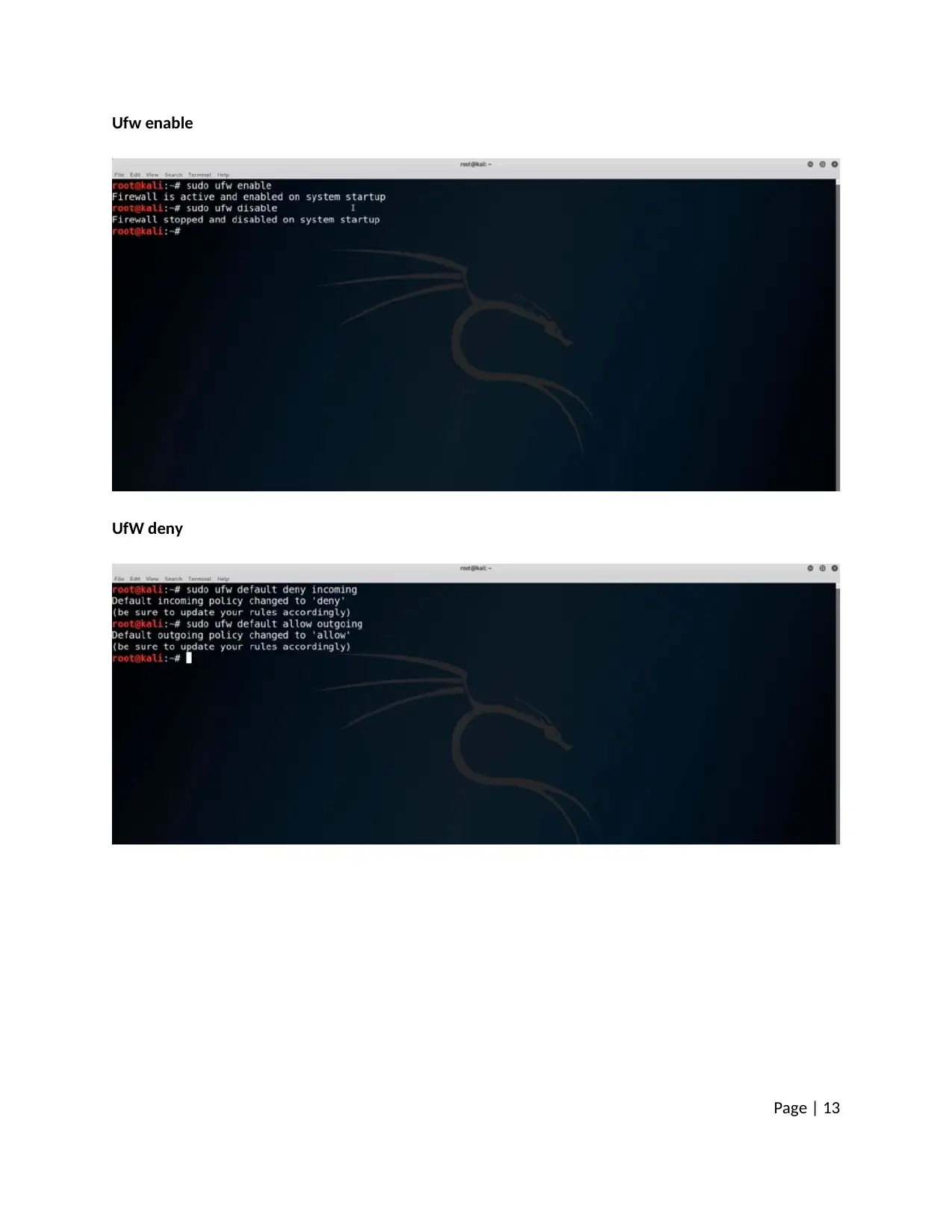
Ufw enable
UfW deny
Page | 13
UfW deny
Page | 13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
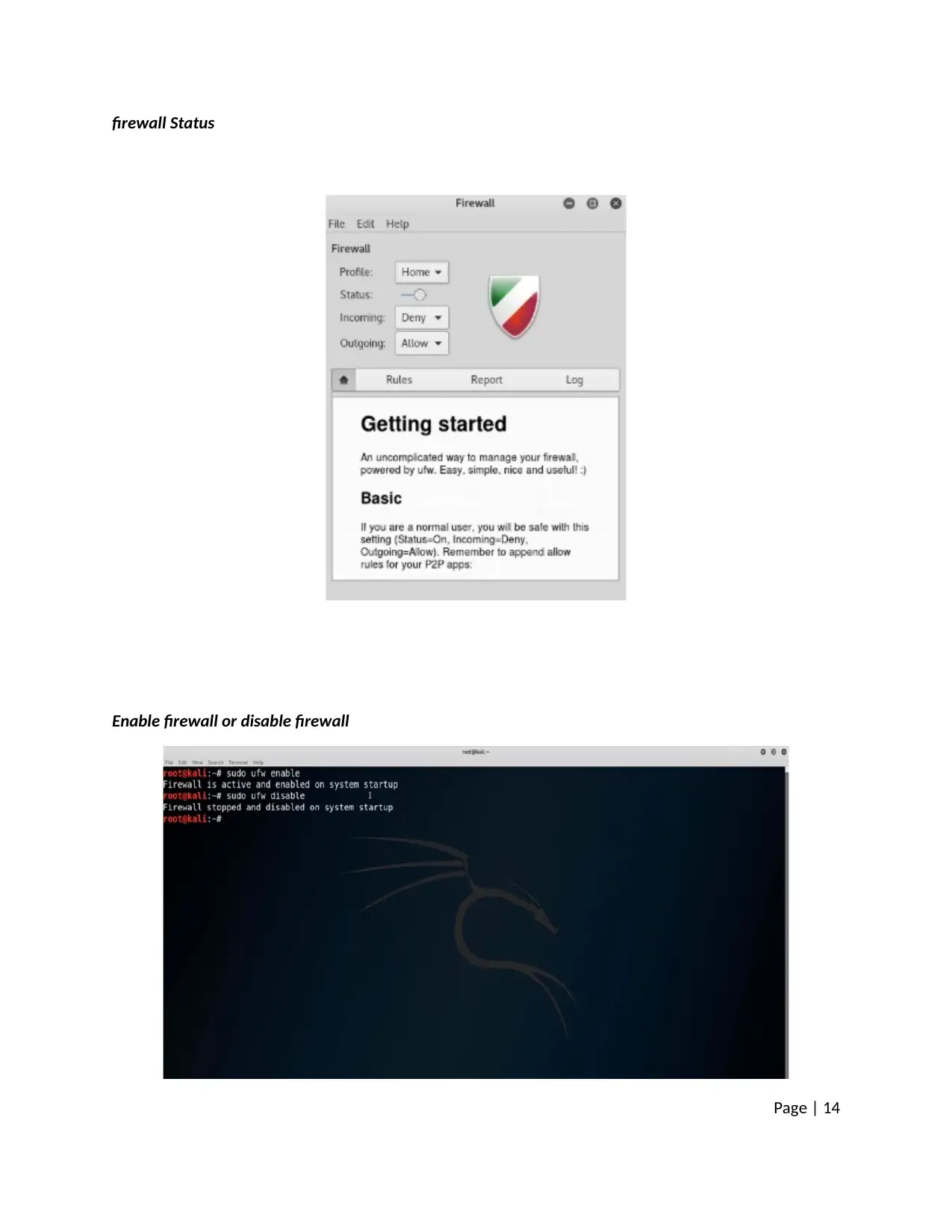
firewall Status
Enable firewall or disable firewall
Page | 14
Enable firewall or disable firewall
Page | 14
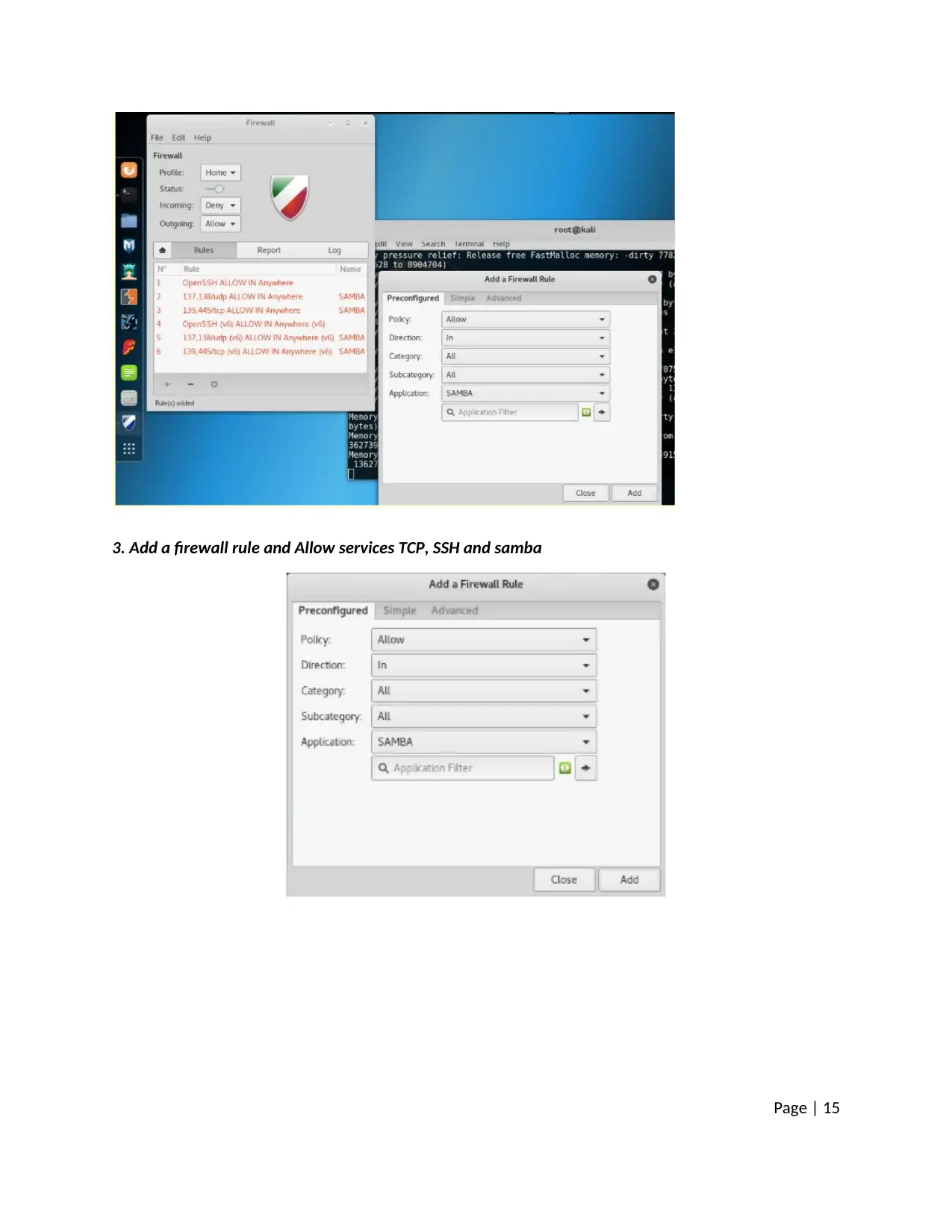
3. Add a firewall rule and Allow services TCP, SSH and samba
Page | 15
Page | 15
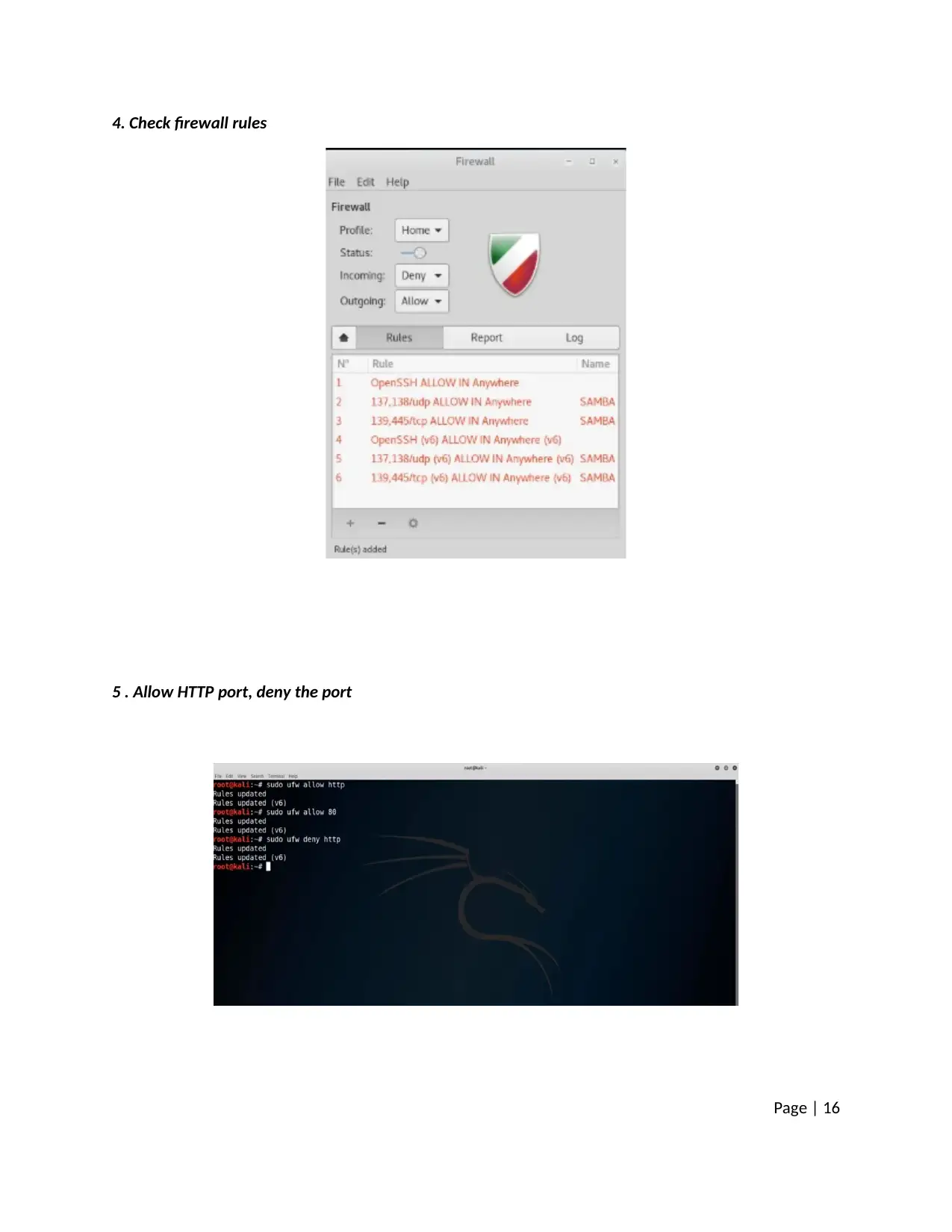
4. Check firewall rules
5 . Allow HTTP port, deny the port
Page | 16
5 . Allow HTTP port, deny the port
Page | 16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
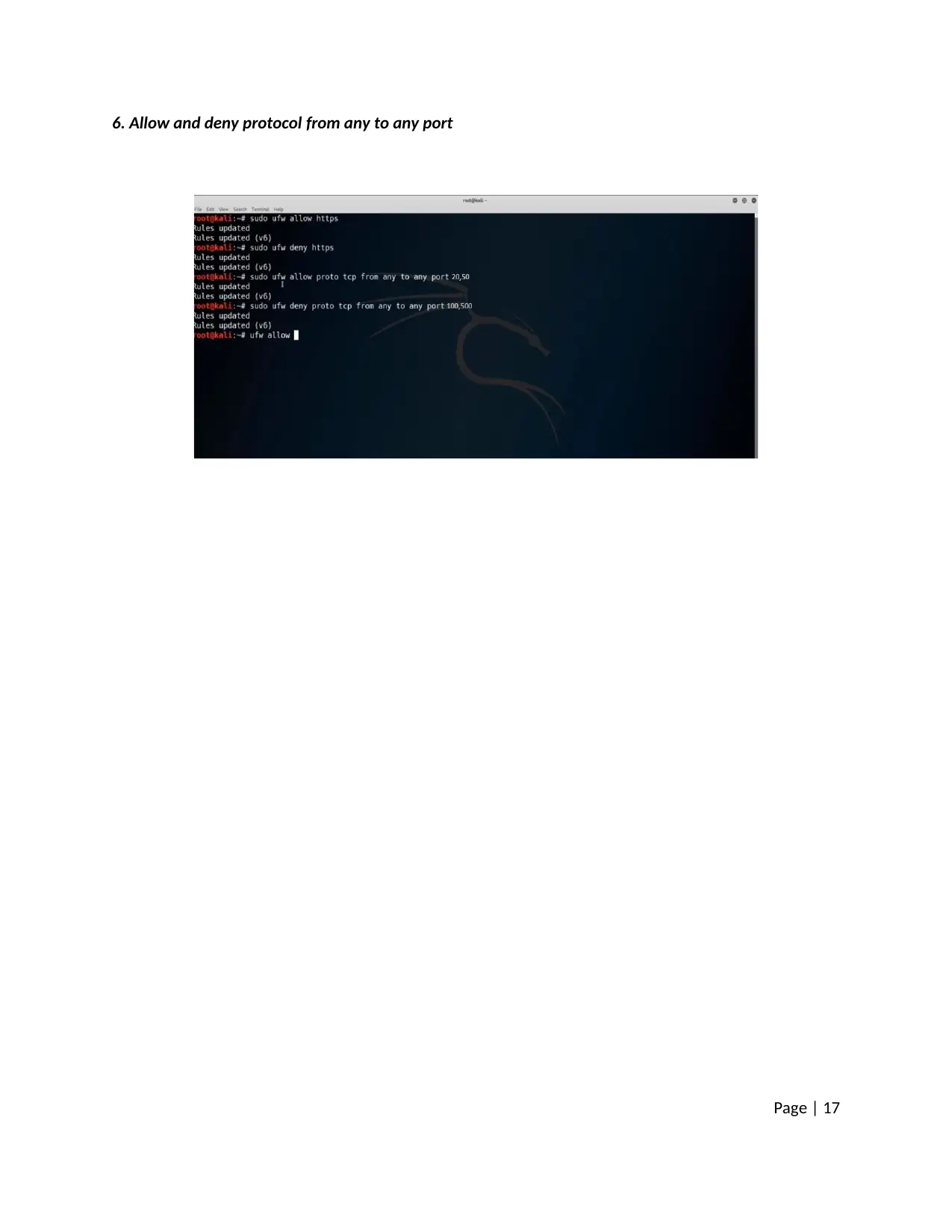
6. Allow and deny protocol from any to any port
Page | 17
Page | 17
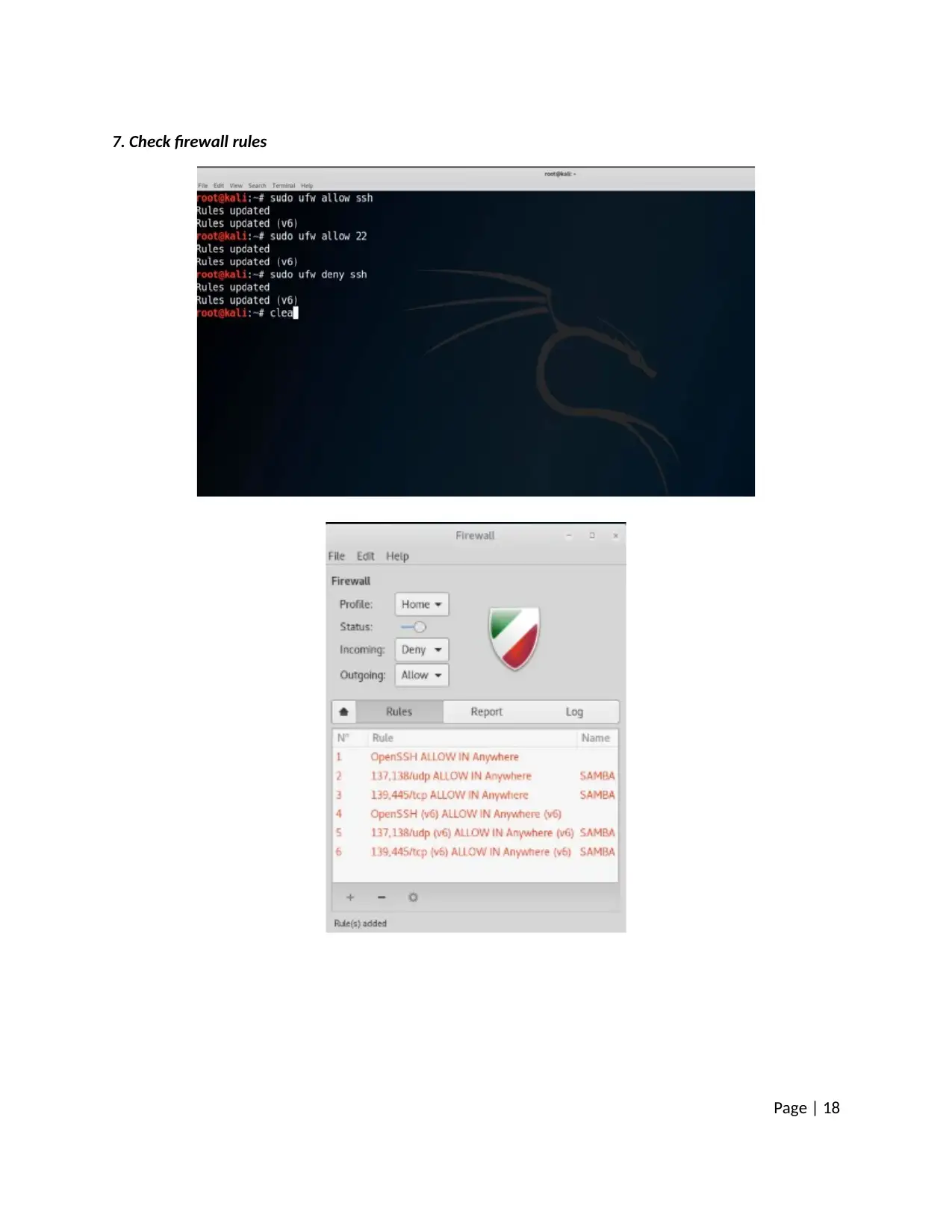
7. Check firewall rules
Page | 18
Page | 18
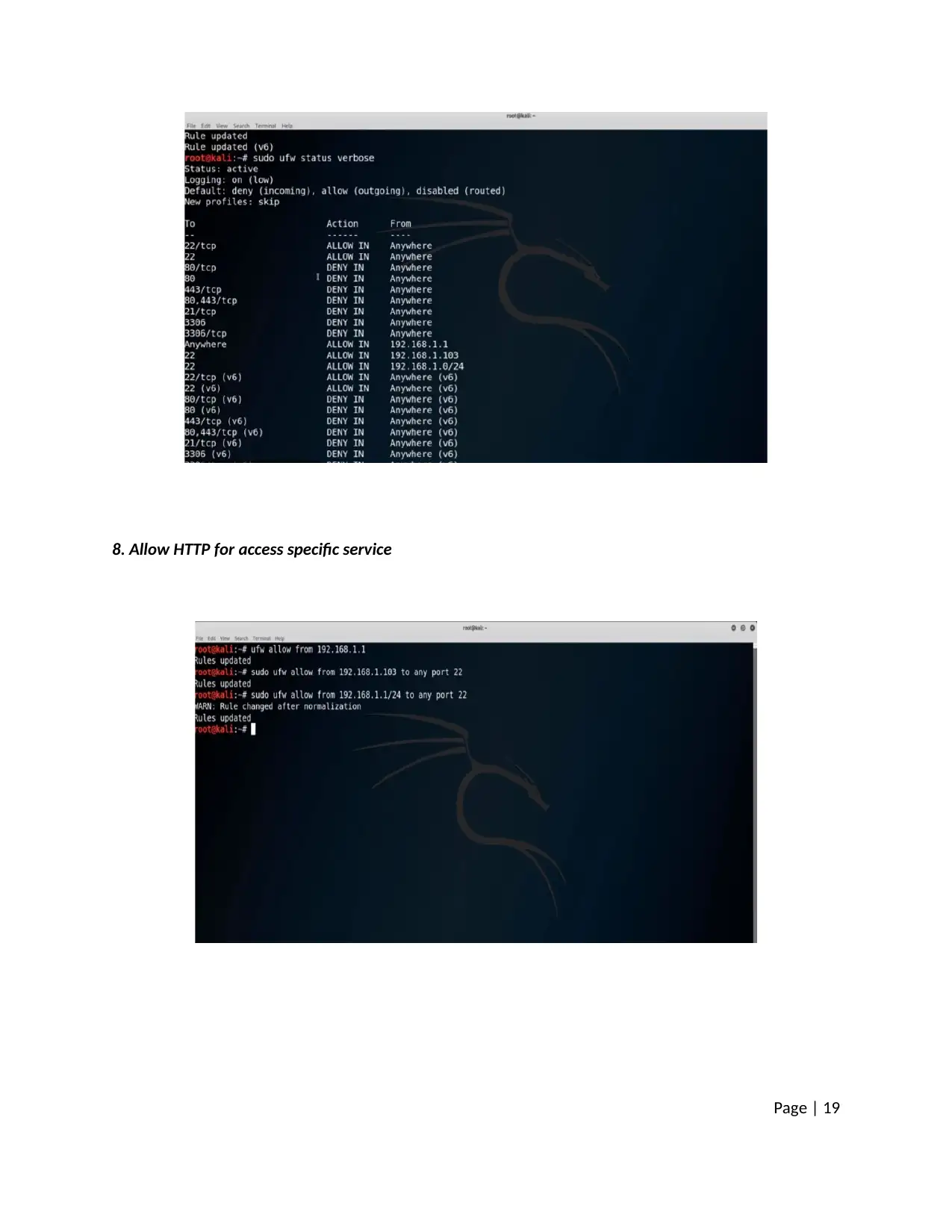
8. Allow HTTP for access specific service
Page | 19
Page | 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
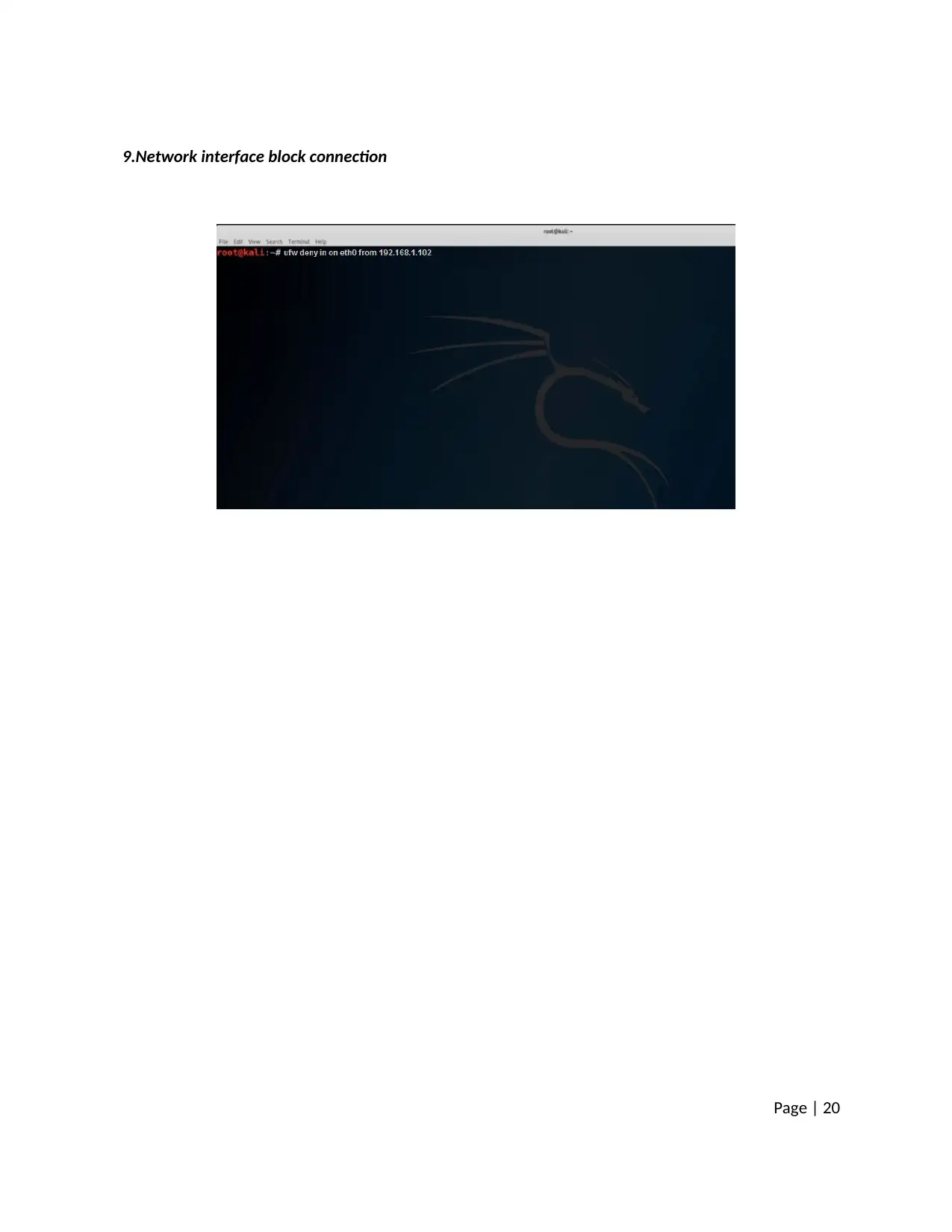
9.Network interface block connection
Page | 20
Page | 20

Conclusion
Here, we have used the Nmap tool for testing the network vulnerability. This tool is very important and
powerful which is helps to collect network data. It is helps to access the data, including the gathering
network information and firewall setting. In this assignment, we have discuss about the security of the
data over the internet with the help of Nmap tool. We have seen, how Nmap tests the TCP and UDD
protocol. This tool is to help identify open ports on the target system. We tested the targeted service
and operating system by more effective scanning.
Page | 21
Here, we have used the Nmap tool for testing the network vulnerability. This tool is very important and
powerful which is helps to collect network data. It is helps to access the data, including the gathering
network information and firewall setting. In this assignment, we have discuss about the security of the
data over the internet with the help of Nmap tool. We have seen, how Nmap tests the TCP and UDD
protocol. This tool is to help identify open ports on the target system. We tested the targeted service
and operating system by more effective scanning.
Page | 21

References
Durumeric . 2013. "ZMap: Fast Internet-Wide Scanning and its Security Applications", proceedings of the
22nd USENIX Security Symposium.
Durumeric Zakir, .2013, "ZMap: Fast Internet-wide scanning and its security applications", Proceedings
of the 22nd USENIX Security Symposium.
G. S. Rao. 2014. "Security assessment of computer networks-an ethical hacker's
perspective", Proceedings of IEEE ICCC.
John Strand.2011. Pen Testing through the Tor Network [online] Available:
http://securitystreetknowledge.com/?p=283.
Gordon Lyon.2002. "Nmap Network Scanning" in , Sunnyvale, CA:Insecure.com, LLC, pp. 129
Medeiros, João Paulo S.2009. Computational Intelligence in Security for Information Systems. Advances
in Intelligent and Soft Computing. 63. pp. 1–8. doi:10.1007/978-3-642-04091-7_1. ISBN 978-3-642-
04090-
S. Shin. 2013. "Attacking software-defined networks: A first feasibility study", Proceedings of the second
ACM SIGCOMM workshop on Hot topics in software defined networking..
Unknown Author.2015. Kali Linux Tutorial: Setting Up ProxyChains + Tor For Anonymity And Security,
[online] Available: http://www.picateshackz.com/2015/05/kali-linux-tutorial-setting-up.html.
Page | 22
Durumeric . 2013. "ZMap: Fast Internet-Wide Scanning and its Security Applications", proceedings of the
22nd USENIX Security Symposium.
Durumeric Zakir, .2013, "ZMap: Fast Internet-wide scanning and its security applications", Proceedings
of the 22nd USENIX Security Symposium.
G. S. Rao. 2014. "Security assessment of computer networks-an ethical hacker's
perspective", Proceedings of IEEE ICCC.
John Strand.2011. Pen Testing through the Tor Network [online] Available:
http://securitystreetknowledge.com/?p=283.
Gordon Lyon.2002. "Nmap Network Scanning" in , Sunnyvale, CA:Insecure.com, LLC, pp. 129
Medeiros, João Paulo S.2009. Computational Intelligence in Security for Information Systems. Advances
in Intelligent and Soft Computing. 63. pp. 1–8. doi:10.1007/978-3-642-04091-7_1. ISBN 978-3-642-
04090-
S. Shin. 2013. "Attacking software-defined networks: A first feasibility study", Proceedings of the second
ACM SIGCOMM workshop on Hot topics in software defined networking..
Unknown Author.2015. Kali Linux Tutorial: Setting Up ProxyChains + Tor For Anonymity And Security,
[online] Available: http://www.picateshackz.com/2015/05/kali-linux-tutorial-setting-up.html.
Page | 22
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



