Applied Cryptography Assignment 2022
VerifiedAdded on 2022/08/26
|17
|2555
|21
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: APPLIED CRYPTOGRAPHY
APPLIED CRYPTOGRAPHY
Name of the Student
Name of the University
Author Note
APPLIED CRYPTOGRAPHY
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

APPLIED CRYPTOGRAPHY 1
Caesar Cipher:
The Caesar cipher technique is one of the simplest and earliest methods for encryption
and decryption. This is actually a kind of substitution cipher. Each of the letters of a provided
text is replaced by another letter with some fix number of positions. As example it can be said
that with the shift of 2, B will be replaced by D, and E will become G and So on. This
encryption can be presented utilizing the modular arithmetic by transforming the letters in to
number firstly. According to that A = 0, B = 1….. Z = 25.
1. Create a frequency analysis chart for your ciphertext (include a screenshot of this chart in
your report).
Cipher text:
fqjc j cdaw cqnv kjwmjpnb mrm pren vn cx kn bdan bqn ydc xw bxvn vxan lxju dwoxumnm
cqn luxcqnbqxabn
0 A
1 B
2 C
3 D
4 E
5 F
6 G
7 H
8 I
9 J
10 K
11 L
12 M
13 N
14 O
15 P
16 Q
17 R
18 S
19 T
20 U
Caesar Cipher:
The Caesar cipher technique is one of the simplest and earliest methods for encryption
and decryption. This is actually a kind of substitution cipher. Each of the letters of a provided
text is replaced by another letter with some fix number of positions. As example it can be said
that with the shift of 2, B will be replaced by D, and E will become G and So on. This
encryption can be presented utilizing the modular arithmetic by transforming the letters in to
number firstly. According to that A = 0, B = 1….. Z = 25.
1. Create a frequency analysis chart for your ciphertext (include a screenshot of this chart in
your report).
Cipher text:
fqjc j cdaw cqnv kjwmjpnb mrm pren vn cx kn bdan bqn ydc xw bxvn vxan lxju dwoxumnm
cqn luxcqnbqxabn
0 A
1 B
2 C
3 D
4 E
5 F
6 G
7 H
8 I
9 J
10 K
11 L
12 M
13 N
14 O
15 P
16 Q
17 R
18 S
19 T
20 U
2APPLIED CRYPTOGRAPHY
21 V
22 W
23 X
24 Y
25 Z
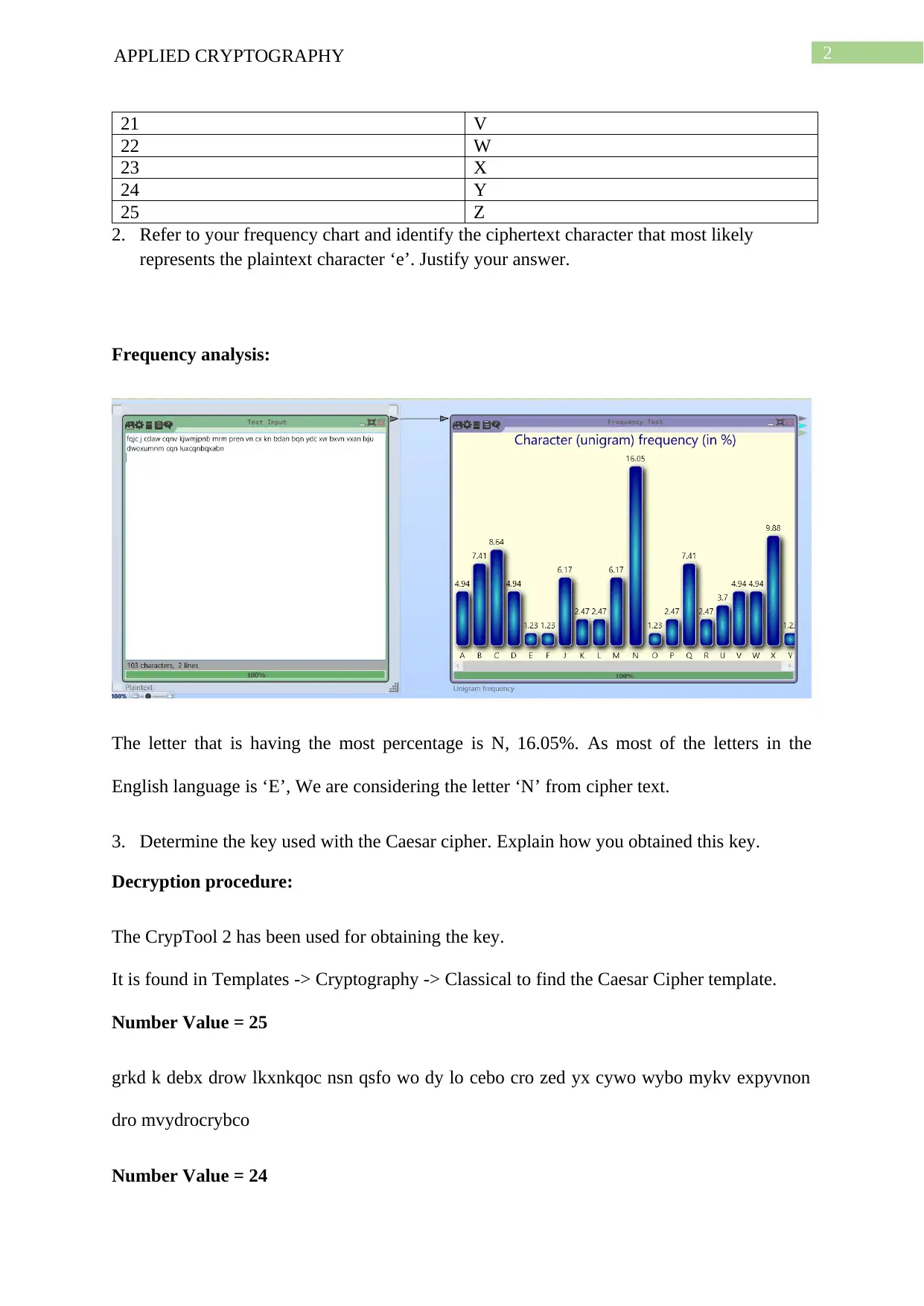
2. Refer to your frequency chart and identify the ciphertext character that most likely
represents the plaintext character ‘e’. Justify your answer.
Frequency analysis:
The letter that is having the most percentage is N, 16.05%. As most of the letters in the
English language is ‘E’, We are considering the letter ‘N’ from cipher text.
3. Determine the key used with the Caesar cipher. Explain how you obtained this key.
Decryption procedure:
The CrypTool 2 has been used for obtaining the key.
It is found in Templates -> Cryptography -> Classical to find the Caesar Cipher template.
Number Value = 25
grkd k debx drow lkxnkqoc nsn qsfo wo dy lo cebo cro zed yx cywo wybo mykv expyvnon
dro mvydrocrybco
Number Value = 24
21 V
22 W
23 X
24 Y
25 Z
2. Refer to your frequency chart and identify the ciphertext character that most likely
represents the plaintext character ‘e’. Justify your answer.
Frequency analysis:
The letter that is having the most percentage is N, 16.05%. As most of the letters in the
English language is ‘E’, We are considering the letter ‘N’ from cipher text.
3. Determine the key used with the Caesar cipher. Explain how you obtained this key.
Decryption procedure:
The CrypTool 2 has been used for obtaining the key.
It is found in Templates -> Cryptography -> Classical to find the Caesar Cipher template.
Number Value = 25
grkd k debx drow lkxnkqoc nsn qsfo wo dy lo cebo cro zed yx cywo wybo mykv expyvnon
dro mvydrocrybco
Number Value = 24
3APPLIED CRYPTOGRAPHY
hsle l efcy espx mlyolrpd oto rtgp xp ez mp dfcp dsp afe zy dzxp xzcp nzlw fyqzwopo esp
nwzespdszcdp
Number shift = 23
itmf m fgdz ftqy nmzpmsqe pup suhq yq fa nq egdq etq bgf az eayq yadq oamx gzraxpqp ftq
oxaftqetadeq
4. Provide the plaintext corresponding to the ciphertext you were given.
Starcenter > templates > Cipher analysis
Plain text:
Number value: 9
what a turn them bandages did give me to be sure she put on some more coal unfolded the
clotheshorse
Row/column Transposition Cipher:
The transposition cipher is basically a simple data encryption technique in that the
characters of plaintext are shifted in a regular pattern for getting ciphertext.
1. Create a frequency analysis chart for your ciphertext.
hsle l efcy espx mlyolrpd oto rtgp xp ez mp dfcp dsp afe zy dzxp xzcp nzlw fyqzwopo esp
nwzespdszcdp
Number shift = 23
itmf m fgdz ftqy nmzpmsqe pup suhq yq fa nq egdq etq bgf az eayq yadq oamx gzraxpqp ftq
oxaftqetadeq
4. Provide the plaintext corresponding to the ciphertext you were given.
Starcenter > templates > Cipher analysis
Plain text:
Number value: 9
what a turn them bandages did give me to be sure she put on some more coal unfolded the
clotheshorse
Row/column Transposition Cipher:
The transposition cipher is basically a simple data encryption technique in that the
characters of plaintext are shifted in a regular pattern for getting ciphertext.
1. Create a frequency analysis chart for your ciphertext.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4APPLIED CRYPTOGRAPHY
Cipher text:
*o*drior*e*c*Cnlertdfrt*Pr*tg*l*unnGtHowouss*ew*Etgeooe*t*ooPcenopNoeLsnt*iaze**
*safa*fh*uaarttaeekn
Frequency analysis:
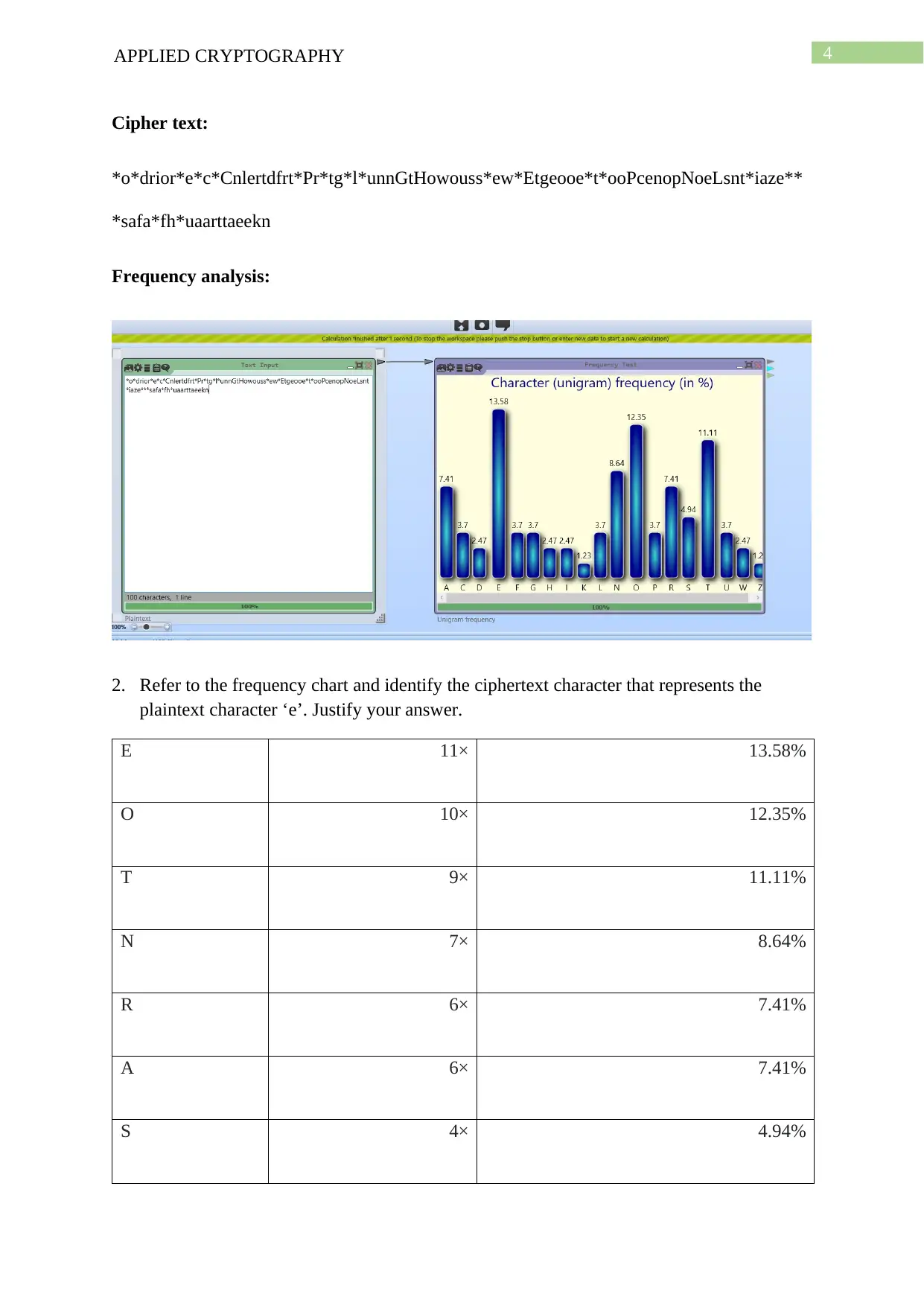
2. Refer to the frequency chart and identify the ciphertext character that represents the
plaintext character ‘e’. Justify your answer.
E 11× 13.58%
O 10× 12.35%
T 9× 11.11%
N 7× 8.64%
R 6× 7.41%
A 6× 7.41%
S 4× 4.94%
Cipher text:
*o*drior*e*c*Cnlertdfrt*Pr*tg*l*unnGtHowouss*ew*Etgeooe*t*ooPcenopNoeLsnt*iaze**
*safa*fh*uaarttaeekn
Frequency analysis:
2. Refer to the frequency chart and identify the ciphertext character that represents the
plaintext character ‘e’. Justify your answer.
E 11× 13.58%
O 10× 12.35%
T 9× 11.11%
N 7× 8.64%
R 6× 7.41%
A 6× 7.41%
S 4× 4.94%

5APPLIED CRYPTOGRAPHY
G 3× 3.7%
U 3× 3.7%
F 3× 3.7%
P 3× 3.7%
L 3× 3.7%
C 3× 3.7%
D 2× 2.47%
H 2× 2.47%
W 2× 2.47%
I 2× 2.47%
Z 1× 1.23%
K 1× 1.23
The letter that is having more percentage is E. The chart is presenting the frequent most
words that are occurring in the cipher text with higher percentage. The letter ‘E’ containing
13.58 % which is highest among all other letters.
3. Determine the key used with the transposition cipher. Explain how you obtained this key.
Table:
0 1 2 3 4
* o * d r
i o r * e
* c * C n
G 3× 3.7%
U 3× 3.7%
F 3× 3.7%
P 3× 3.7%
L 3× 3.7%
C 3× 3.7%
D 2× 2.47%
H 2× 2.47%
W 2× 2.47%
I 2× 2.47%
Z 1× 1.23%
K 1× 1.23
The letter that is having more percentage is E. The chart is presenting the frequent most
words that are occurring in the cipher text with higher percentage. The letter ‘E’ containing
13.58 % which is highest among all other letters.
3. Determine the key used with the transposition cipher. Explain how you obtained this key.
Table:
0 1 2 3 4
* o * d r
i o r * e
* c * C n

6APPLIED CRYPTOGRAPHY
l e r t d
f r t * P
r * t g *
l * u n n
G t H o w
o u s s *
e w * E t
g e o o e
* t * o o
P c e n o
p N o e L
s n t * i
a z e * *
* s a f a
* f h * u
a a r t t
a e e k n
The row/column transposition cipher is applied to get the plain text as output. Cipher text ->
*o*drior*e*c*Cnlertdfrt*Pr*tg*l*unnGtHowouss*ew*Etgeooe*t*ooPcenopNoeLsnt*iaze**
*safa*fh*uaarttaeekn
The cipher text is divided into number of columns step by step increasingly.
The cipher text is divided into 5 columns equally as well as the columns are shuffled to find
the plain text.
The Key is 4, 5, 3, 1, 2
4. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Plain text:
Course*stands*for*papier*now*for*the*eg*let*us*glance*at*our*continental*gazetteer*he*
took*down*fpo
l e r t d
f r t * P
r * t g *
l * u n n
G t H o w
o u s s *
e w * E t
g e o o e
* t * o o
P c e n o
p N o e L
s n t * i
a z e * *
* s a f a
* f h * u
a a r t t
a e e k n
The row/column transposition cipher is applied to get the plain text as output. Cipher text ->
*o*drior*e*c*Cnlertdfrt*Pr*tg*l*unnGtHowouss*ew*Etgeooe*t*ooPcenopNoeLsnt*iaze**
*safa*fh*uaarttaeekn
The cipher text is divided into number of columns step by step increasingly.
The cipher text is divided into 5 columns equally as well as the columns are shuffled to find
the plain text.
The Key is 4, 5, 3, 1, 2
4. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Plain text:
Course*stands*for*papier*now*for*the*eg*let*us*glance*at*our*continental*gazetteer*he*
took*down*fpo
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7APPLIED CRYPTOGRAPHY
Vigenere cipher:
The vigenere cipher is basically a technique for encrypting alphabetic text. A simple
form of the polyalphabetic substitution is used in this method.
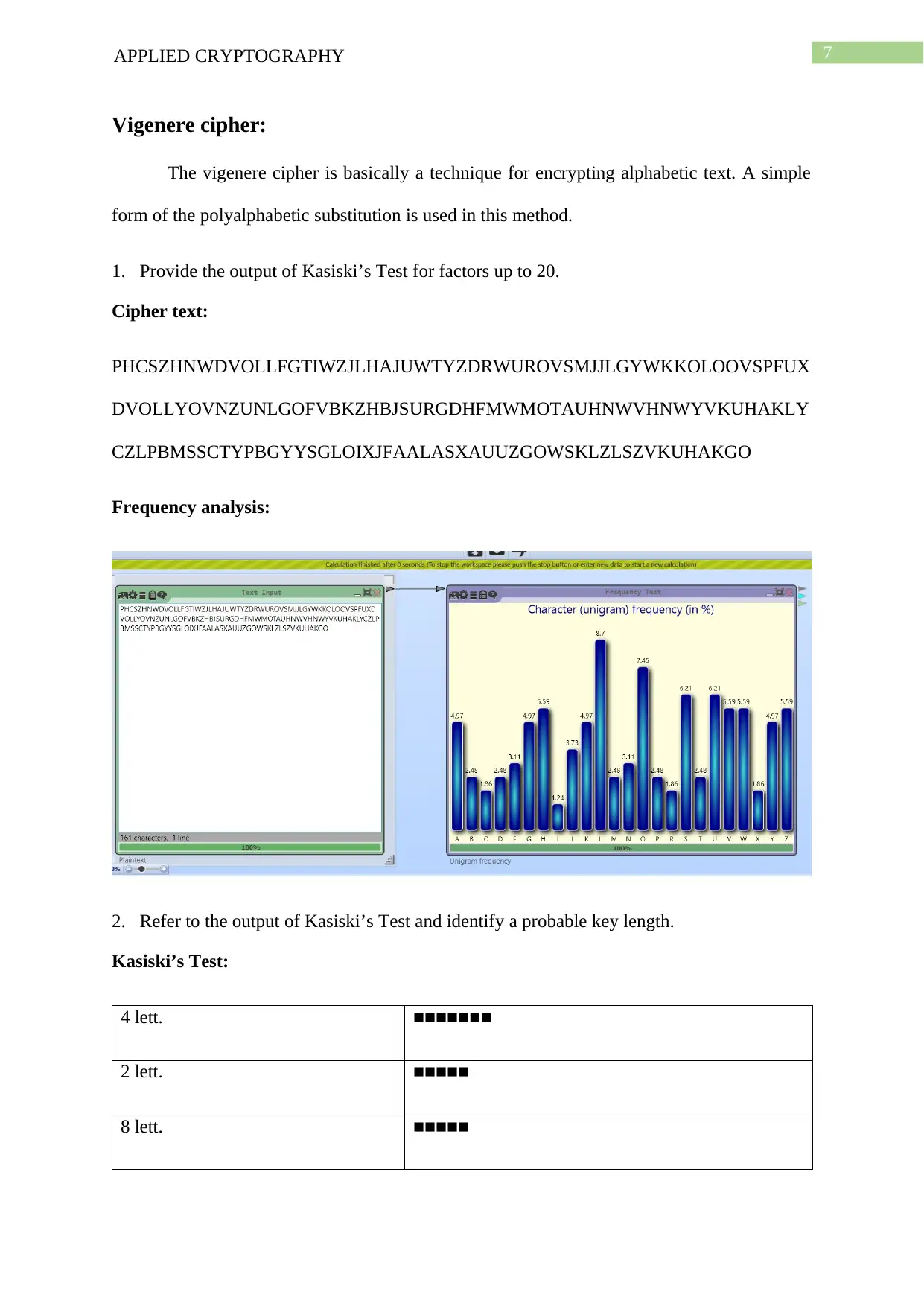
1. Provide the output of Kasiski’s Test for factors up to 20.
Cipher text:
PHCSZHNWDVOLLFGTIWZJLHAJUWTYZDRWUROVSMJJLGYWKKOLOOVSPFUX
DVOLLYOVNZUNLGOFVBKZHBJSURGDHFMWMOTAUHNWVHNWYVKUHAKLY
CZLPBMSSCTYPBGYYSGLOIXJFAALASXAUUZGOWSKLZLSZVKUHAKGO
Frequency analysis:
2. Refer to the output of Kasiski’s Test and identify a probable key length.
Kasiski’s Test:
4 lett. ■■■■■■■
2 lett. ■■■■■
8 lett. ■■■■■
Vigenere cipher:
The vigenere cipher is basically a technique for encrypting alphabetic text. A simple
form of the polyalphabetic substitution is used in this method.
1. Provide the output of Kasiski’s Test for factors up to 20.
Cipher text:
PHCSZHNWDVOLLFGTIWZJLHAJUWTYZDRWUROVSMJJLGYWKKOLOOVSPFUX
DVOLLYOVNZUNLGOFVBKZHBJSURGDHFMWMOTAUHNWVHNWYVKUHAKLY
CZLPBMSSCTYPBGYYSGLOIXJFAALASXAUUZGOWSKLZLSZVKUHAKGO
Frequency analysis:
2. Refer to the output of Kasiski’s Test and identify a probable key length.
Kasiski’s Test:
4 lett. ■■■■■■■
2 lett. ■■■■■
8 lett. ■■■■■

8APPLIED CRYPTOGRAPHY
12 lett. ■■■
6 lett. ■■■
13 lett. ■■■
3 lett. ■■
26 lett. ■■
16 lett. ■■
11 lett. ■■
24 lett. ■■
22 lett. ■
17 lett. ■
15 lett. ■
14 lett. ■
10 lett. ■
9 lett. ■
7 lett. ■
5 lett. ■
23 lett. ■
28 lett.
27 lett.
12 lett. ■■■
6 lett. ■■■
13 lett. ■■■
3 lett. ■■
26 lett. ■■
16 lett. ■■
11 lett. ■■
24 lett. ■■
22 lett. ■
17 lett. ■
15 lett. ■
14 lett. ■
10 lett. ■
9 lett. ■
7 lett. ■
5 lett. ■
23 lett. ■
28 lett.
27 lett.

9APPLIED CRYPTOGRAPHY
25 lett.
1 lett.
21 lett.
20 lett.
19 lett.
18 lett.
29 lett.
Kasiski’s test:
The size of the key is: 4
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
25 lett.
1 lett.
21 lett.
20 lett.
19 lett.
18 lett.
29 lett.
Kasiski’s test:
The size of the key is: 4
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10APPLIED CRYPTOGRAPHY
B B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
R R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
S S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
3. Describe the process involved in breaking the Vigenere cipher once the key length is
determined.
The procedure that is involved in breaking the vigenere cipher is as follows
CrypTool -> Templates -> Vigenere Analysis
4. Apply this process to determine the key used with the Vigenere cipher. Clearly explain
how you obtained the key
The process is used for determining the key.
The cipher text is given in the text input box and run by clicking on play button.
B B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
R R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
S S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
3. Describe the process involved in breaking the Vigenere cipher once the key length is
determined.
The procedure that is involved in breaking the vigenere cipher is as follows
CrypTool -> Templates -> Vigenere Analysis
4. Apply this process to determine the key used with the Vigenere cipher. Clearly explain
how you obtained the key
The process is used for determining the key.
The cipher text is given in the text input box and run by clicking on play button.

11APPLIED CRYPTOGRAPHY
The key length is 4.
The key is: hogs
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Plain text:
it was the white rabbit returning splendidly dressed with a pair of white kid gloves in one
hand and a large fan in the other he came trotting along in a great hurry muttering to himself
a she came oh
Hill Cipher:
1. The Hill cipher is polygraphic, with block size m. For m = 2, explain how a known-
plaintext attack is performed, and how much known plaintext is required for the attack to
succeed.
The hill cipher is basically a poly graphic substitution cipher which is based on the
linear algebra. Each of the letters are represented by the modulo number 26. Here A = 0, B =
1,…. Z = 25. For encrypting a message, each of the blocks of n letters will be multiplied by
n*n matrix against mod 26.
2. For a ciphertext-alone attack on a Hill cipher,some plaintext must be guessed.Assuming
the plaintext is in English,list some common digrams. Justify your choice of items.
The key length is 4.
The key is: hogs
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Plain text:
it was the white rabbit returning splendidly dressed with a pair of white kid gloves in one
hand and a large fan in the other he came trotting along in a great hurry muttering to himself
a she came oh
Hill Cipher:
1. The Hill cipher is polygraphic, with block size m. For m = 2, explain how a known-
plaintext attack is performed, and how much known plaintext is required for the attack to
succeed.
The hill cipher is basically a poly graphic substitution cipher which is based on the
linear algebra. Each of the letters are represented by the modulo number 26. Here A = 0, B =
1,…. Z = 25. For encrypting a message, each of the blocks of n letters will be multiplied by
n*n matrix against mod 26.
2. For a ciphertext-alone attack on a Hill cipher,some plaintext must be guessed.Assuming
the plaintext is in English,list some common digrams. Justify your choice of items.
12APPLIED CRYPTOGRAPHY
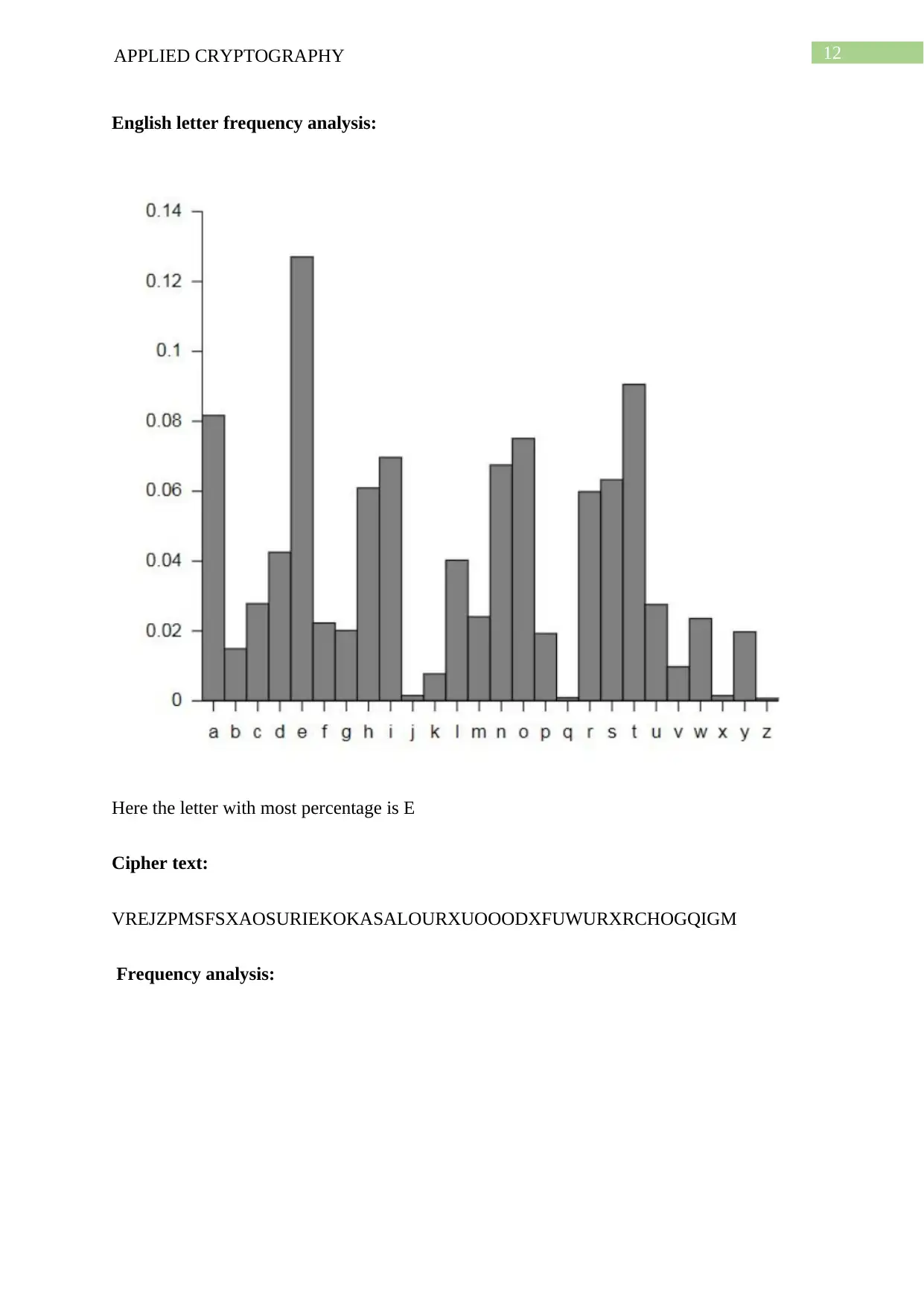
English letter frequency analysis:
Here the letter with most percentage is E
Cipher text:
VREJZPMSFSXAOSURIEKOKASALOURXUOOODXFUWURXRCHOGQIGM
Frequency analysis:
English letter frequency analysis:
Here the letter with most percentage is E
Cipher text:
VREJZPMSFSXAOSURIEKOKASALOURXUOOODXFUWURXRCHOGQIGM
Frequency analysis:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13APPLIED CRYPTOGRAPHY
Here the letter with most percentage is O
3. The position of a common plaintext word within a message may be unknown, so many
positions may be tested for a common word, in a process called ‘crib dragging’. Given the
knowledge that your plaintext contains the word about, apply crib dragging to obtain
the encryption key matrix 1.
Crib dragging:
Replacing O by E:
VREJZPMSFSXAESURIEKOKASALEURXUOOODXFUWURXRCHEGQIGM
A plain text is known that is ABOUT
Then
VREJ
ABOU
It is known that A-Z = 0-25
Cipher text:
21 17 = V R
4 9 E J
1
Here the letter with most percentage is O
3. The position of a common plaintext word within a message may be unknown, so many
positions may be tested for a common word, in a process called ‘crib dragging’. Given the
knowledge that your plaintext contains the word about, apply crib dragging to obtain
the encryption key matrix 1.
Crib dragging:
Replacing O by E:
VREJZPMSFSXAESURIEKOKASALEURXUOOODXFUWURXRCHEGQIGM
A plain text is known that is ABOUT
Then
VREJ
ABOU
It is known that A-Z = 0-25
Cipher text:
21 17 = V R
4 9 E J
1

14APPLIED CRYPTOGRAPHY
Plain text:
21 1 = A B
14 20 O U
key = ((ciphertext) * (plaintext)^(-1)) mod n
Inverse of plaintext is
8 0
8 8
KEY=
21 17 8 0
Mod 26
4 9 8 8
KEY =
8 17
9 13
4. Compute the corresponding decryption matrix.
21 17 = U Q
4 9 E J
KEY=
21 17 8 0
x
4 9 8 8
KEY =
8 17
9 13
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Cipher text:
VREJZPMSFSXAOSURIEKOKASALOURXUOOODXFUWURXRCHOGQIGM
KEY =
8 17
Plain text:
21 1 = A B
14 20 O U
key = ((ciphertext) * (plaintext)^(-1)) mod n
Inverse of plaintext is
8 0
8 8
KEY=
21 17 8 0
Mod 26
4 9 8 8
KEY =
8 17
9 13
4. Compute the corresponding decryption matrix.
21 17 = U Q
4 9 E J
KEY=
21 17 8 0
x
4 9 8 8
KEY =
8 17
9 13
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Cipher text:
VREJZPMSFSXAOSURIEKOKASALOURXUOOODXFUWURXRCHOGQIGM
KEY =
8 17
15APPLIED CRYPTOGRAPHY
9 13
Plain text:
This is about cryptography hill cipher.
9 13
Plain text:
This is about cryptography hill cipher.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16APPLIED CRYPTOGRAPHY
Bibliography:
Bennett, C. H., & Brassard, G. (2020). Quantum cryptography: Public key distribution and
coin tossing. arXiv preprint arXiv:2003.06557.
Goldreich, O. (2019). On the impact of cryptography on complexity theory. In Providing
Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio
Micali (pp. 497-526).
McKay, K., Bassham, L., Sönmez Turan, M., & Mouha, N. (2016). Report on lightweight
cryptography (No. NIST Internal or Interagency Report (NISTIR) 8114 (Draft)).
National Institute of Standards and Technology.
Stinson, D. R., & Paterson, M. (2018). Cryptography: theory and practice. CRC press.
Bibliography:
Bennett, C. H., & Brassard, G. (2020). Quantum cryptography: Public key distribution and
coin tossing. arXiv preprint arXiv:2003.06557.
Goldreich, O. (2019). On the impact of cryptography on complexity theory. In Providing
Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio
Micali (pp. 497-526).
McKay, K., Bassham, L., Sönmez Turan, M., & Mouha, N. (2016). Report on lightweight
cryptography (No. NIST Internal or Interagency Report (NISTIR) 8114 (Draft)).
National Institute of Standards and Technology.
Stinson, D. R., & Paterson, M. (2018). Cryptography: theory and practice. CRC press.
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





