IT Write Up Report 2022
VerifiedAdded on 2022/10/17
|12
|2753
|23
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: IT Write Up
0
IT Write Up
IT for business
(Student Details: )
9/25/2019
0
IT Write Up
IT for business
(Student Details: )
9/25/2019
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Write Up
1
Contents
IT for Tourism Industry: Intercontinental Hotel Group.............................................................2
Introduction................................................................................................................................2
Overview of Business................................................................................................................3
Background on information security breach in business...........................................................4
Need of IT in business................................................................................................................4
Importance of IT for business survival......................................................................................4
Required resources to apply IT in business................................................................................5
How chosen business use IT......................................................................................................6
Benefits and advantages of IT....................................................................................................6
Risk of IT...................................................................................................................................7
How selected business can maintain and monitor IT.................................................................8
Conclusion..................................................................................................................................8
References................................................................................................................................10
1
Contents
IT for Tourism Industry: Intercontinental Hotel Group.............................................................2
Introduction................................................................................................................................2
Overview of Business................................................................................................................3
Background on information security breach in business...........................................................4
Need of IT in business................................................................................................................4
Importance of IT for business survival......................................................................................4
Required resources to apply IT in business................................................................................5
How chosen business use IT......................................................................................................6
Benefits and advantages of IT....................................................................................................6
Risk of IT...................................................................................................................................7
How selected business can maintain and monitor IT.................................................................8
Conclusion..................................................................................................................................8
References................................................................................................................................10

IT Write Up
2
IT for Tourism Industry: Intercontinental Hotel Group
Introduction
This report is based on identifying IT role in tourism industry while exploring its significance
for the hospitality sector of tourism industry. To do so, a well-known hotel group has been
chosen as ‘Intercontinental Hotels Group’ (IHG) so that recent information security (IS)
breaches can be explored and studied for addressing those issues effectively. Based on
(Sharp, 2017), this report will discuss IT role for IHG’s business in the context of present and
future as well. The purpose of the report is to analyse IS breach while covering cyber security
as well as suggested IS practices of their information and network systems. This report will
help readers include IT, directors, CIOs (Chief information officers) to advance IS policy of
electronic info in hotels. While discussing benefits of IT for IHG business, this report will
also suggest security tools and techniques in order to ensure enhanced information security
for the group’s computer networks (Bhavani, 2013). In addition, need for IT for IHG business
along with importance of IT for their business survival will be discussed in detail. In this
way, risks of IT, monitoring as well as maintenance need of chosen business will also be
covered in this report.
2
IT for Tourism Industry: Intercontinental Hotel Group
Introduction
This report is based on identifying IT role in tourism industry while exploring its significance
for the hospitality sector of tourism industry. To do so, a well-known hotel group has been
chosen as ‘Intercontinental Hotels Group’ (IHG) so that recent information security (IS)
breaches can be explored and studied for addressing those issues effectively. Based on
(Sharp, 2017), this report will discuss IT role for IHG’s business in the context of present and
future as well. The purpose of the report is to analyse IS breach while covering cyber security
as well as suggested IS practices of their information and network systems. This report will
help readers include IT, directors, CIOs (Chief information officers) to advance IS policy of
electronic info in hotels. While discussing benefits of IT for IHG business, this report will
also suggest security tools and techniques in order to ensure enhanced information security
for the group’s computer networks (Bhavani, 2013). In addition, need for IT for IHG business
along with importance of IT for their business survival will be discussed in detail. In this
way, risks of IT, monitoring as well as maintenance need of chosen business will also be
covered in this report.
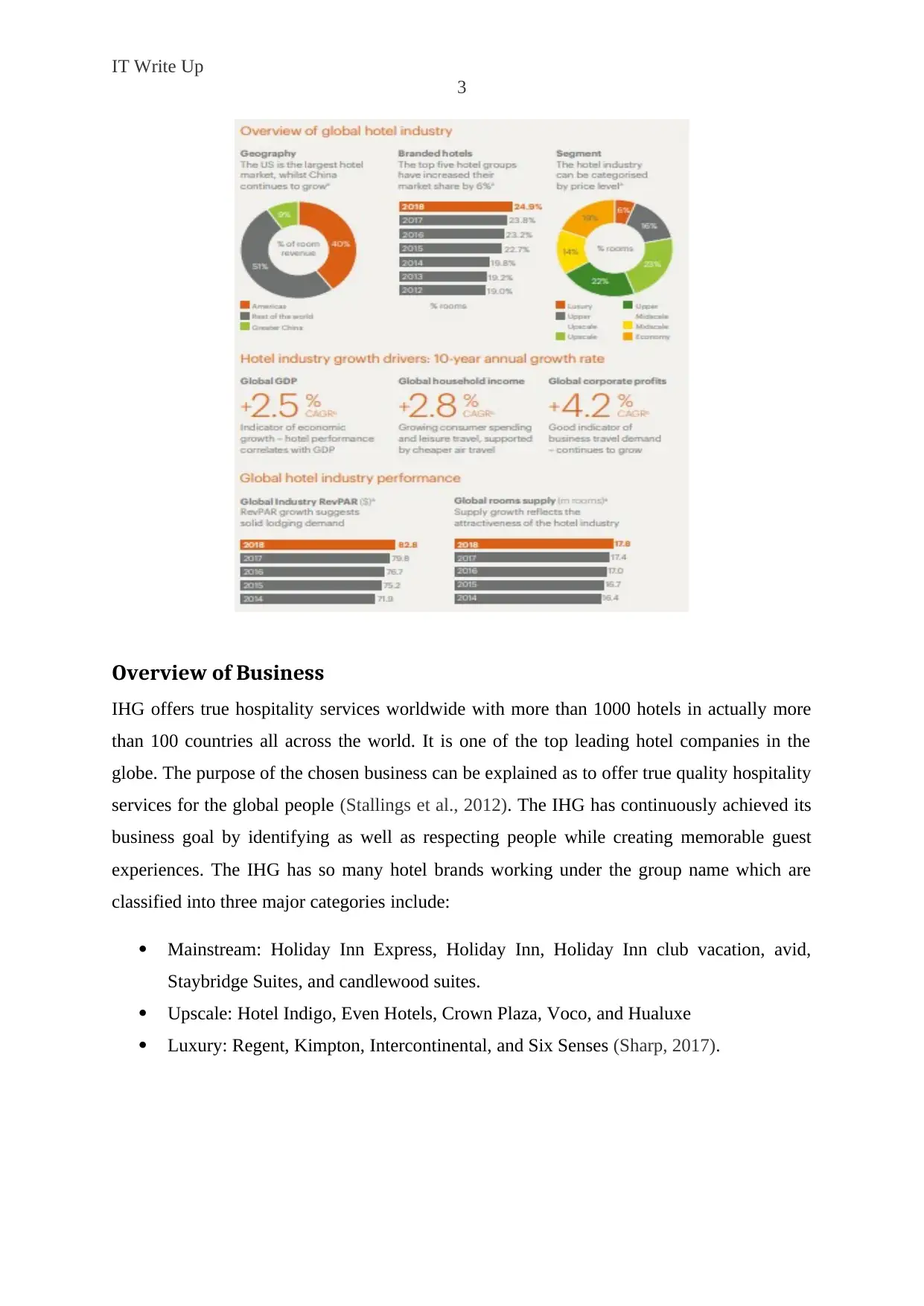
IT Write Up
3
Overview of Business
IHG offers true hospitality services worldwide with more than 1000 hotels in actually more
than 100 countries all across the world. It is one of the top leading hotel companies in the
globe. The purpose of the chosen business can be explained as to offer true quality hospitality
services for the global people (Stallings et al., 2012). The IHG has continuously achieved its
business goal by identifying as well as respecting people while creating memorable guest
experiences. The IHG has so many hotel brands working under the group name which are
classified into three major categories include:
Mainstream: Holiday Inn Express, Holiday Inn, Holiday Inn club vacation, avid,
Staybridge Suites, and candlewood suites.
Upscale: Hotel Indigo, Even Hotels, Crown Plaza, Voco, and Hualuxe
Luxury: Regent, Kimpton, Intercontinental, and Six Senses (Sharp, 2017).
3
Overview of Business
IHG offers true hospitality services worldwide with more than 1000 hotels in actually more
than 100 countries all across the world. It is one of the top leading hotel companies in the
globe. The purpose of the chosen business can be explained as to offer true quality hospitality
services for the global people (Stallings et al., 2012). The IHG has continuously achieved its
business goal by identifying as well as respecting people while creating memorable guest
experiences. The IHG has so many hotel brands working under the group name which are
classified into three major categories include:
Mainstream: Holiday Inn Express, Holiday Inn, Holiday Inn club vacation, avid,
Staybridge Suites, and candlewood suites.
Upscale: Hotel Indigo, Even Hotels, Crown Plaza, Voco, and Hualuxe
Luxury: Regent, Kimpton, Intercontinental, and Six Senses (Sharp, 2017).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Write Up
4
Background on information security breach in the business
Based on (Sharp, 2017), cyber-attack or information security breach has hit around 1200
InterContinental hotels in the United States (US). As reported by the business traveler, during
2016 a severe data breach occurred when hackers stole data from more than 1,200 IHG
hotels. The data security violation incident occurred in the US. Besides, the specific
information about this data breach incident suggests that incidents happened between
September and December of 2016. It has been found that information such as cardholder
names, expiration dates, numbers, as well as internal verification codes of the IHG guests was
stolen by the hackers while using credit-card burglary malware. It is worth knowing that
aforementioned malware was not eliminated till March 2017 (Sharp, 2017). After facing this
IS breach, IHG has learned a lot about information security breaches. As the guest credit
cards were extensively used without authorization post their stays at the group’s hotels hence
IHG business learned a great lesson for future business development (Shabani, 2017).
Need for IT in business
After knowing and analysing chosen data security breach, it is clear that IHG business needs
IT largely. It is because at each level of hotel management computer networks are involved
for example, at both user-level and property level, IT is needed for providing desired security.
In this context, at property level, local area networks typically include front office,
reservation, restaurant management, accounting, and human resources, all of which require
IT for their smooth and safe execution. On the other hand, at user level, website which is
usually browsed by the users for making reservations as well as accessing the hotelier
information is considered. In this way, for controlling and reducing vulnerabilities of
computer systems IT is needed largely (The Economic Times, 2018).
Apart from this, IT solves so many problems such as communication, smooth functioning,
competitor analysis, business survival solving IT security. In this way, it is evident that IT
needs for the chosen business of IHG is huge which requires to be addressed effectively
(Australian Government, 2018).
Importance of IT for business survival
Many researchers have found that the world is widely using IT which is the science as well as
technology of utilising computer systems and networks while saving and transmitting
4
Background on information security breach in the business
Based on (Sharp, 2017), cyber-attack or information security breach has hit around 1200
InterContinental hotels in the United States (US). As reported by the business traveler, during
2016 a severe data breach occurred when hackers stole data from more than 1,200 IHG
hotels. The data security violation incident occurred in the US. Besides, the specific
information about this data breach incident suggests that incidents happened between
September and December of 2016. It has been found that information such as cardholder
names, expiration dates, numbers, as well as internal verification codes of the IHG guests was
stolen by the hackers while using credit-card burglary malware. It is worth knowing that
aforementioned malware was not eliminated till March 2017 (Sharp, 2017). After facing this
IS breach, IHG has learned a lot about information security breaches. As the guest credit
cards were extensively used without authorization post their stays at the group’s hotels hence
IHG business learned a great lesson for future business development (Shabani, 2017).
Need for IT in business
After knowing and analysing chosen data security breach, it is clear that IHG business needs
IT largely. It is because at each level of hotel management computer networks are involved
for example, at both user-level and property level, IT is needed for providing desired security.
In this context, at property level, local area networks typically include front office,
reservation, restaurant management, accounting, and human resources, all of which require
IT for their smooth and safe execution. On the other hand, at user level, website which is
usually browsed by the users for making reservations as well as accessing the hotelier
information is considered. In this way, for controlling and reducing vulnerabilities of
computer systems IT is needed largely (The Economic Times, 2018).
Apart from this, IT solves so many problems such as communication, smooth functioning,
competitor analysis, business survival solving IT security. In this way, it is evident that IT
needs for the chosen business of IHG is huge which requires to be addressed effectively
(Australian Government, 2018).
Importance of IT for business survival
Many researchers have found that the world is widely using IT which is the science as well as
technology of utilising computer systems and networks while saving and transmitting

IT Write Up
5
information all across the world and organization. Now, hotels are using IT for managing
variety of data like market, sales, customers, accounts, stocks and shares, booking and
airplane tickets (Bhavani, 2013). In this way, chosen IHG business need IT majorly for
various business functions include
Managing and administrating electronic info safely
Managing and administrating electronic info securely
In this way, IHG need IT for business survival among their competitors while protecting
hospitality firms’ information and assets (Gatzlaff & McCullough, 2010).
Required resources to apply IT in business
In this context, there can be a number of resources that need to be applied in IHG’s business
for the betterment of the business. IHG’s IT systems in hotels need both software and
hardware resources. They are as follows:
Possible software resources
Point of sale system (POS)
Property management system (PMS)
Accounting system (Vacca, 2012).
Call accounting system (CAS)
Possible hardware resources
POS terminals
Front desk computers
Printers
Routers
Switches
Back office computers
Network cables
Firewalls (The AME group, 2018).
5
information all across the world and organization. Now, hotels are using IT for managing
variety of data like market, sales, customers, accounts, stocks and shares, booking and
airplane tickets (Bhavani, 2013). In this way, chosen IHG business need IT majorly for
various business functions include
Managing and administrating electronic info safely
Managing and administrating electronic info securely
In this way, IHG need IT for business survival among their competitors while protecting
hospitality firms’ information and assets (Gatzlaff & McCullough, 2010).
Required resources to apply IT in business
In this context, there can be a number of resources that need to be applied in IHG’s business
for the betterment of the business. IHG’s IT systems in hotels need both software and
hardware resources. They are as follows:
Possible software resources
Point of sale system (POS)
Property management system (PMS)
Accounting system (Vacca, 2012).
Call accounting system (CAS)
Possible hardware resources
POS terminals
Front desk computers
Printers
Routers
Switches
Back office computers
Network cables
Firewalls (The AME group, 2018).

IT Write Up
6
How chosen business use IT
The chosen business as IHG uses IT for both internal and external communication. For
instance, internally IHG uses IT networking apps for effective communication among their
in-house employees. On the other hand, shareholders, stakeholders, suppliers, and customers
at IHG’s hotel brands get connected to each other with the help of advanced IT platforms
(Popescul & Genete, 2016).
Based on (Sharp, 2017), IHG is using IT in the form of various applications, for instance, the
group is using a cloud-based technology platform that contains hospitality industry-leading
Guest Reservation System (GRS). It has been found that with the use of IT, IHG could bring
their core hotel systems altogether, whole offering the correct mix of technology,
functionality, and data, which is required for improving user stay experiences. Currently, IT
use at IHG is helping the firm’s owners to drive performance and revenue in best possible
way. In addition to that, IHG is looking forward to developing the second phase of IT
emphasized on improving the guest reservation experience (Buhalis & Crotts, 2013).
Furthermore, in order to find more ways for enriching ever business process from guests
booking to marketing and stays, IT is getting utilised by the IHG hospitality firm (Gollmann,
2010). IHG has also understood the importance of data security and privacy after facing the
IS or data breach during 2016 (Sharp, 2017).
Benefits and advantages of IT
In general, Information Technology is beneficial for following favours in the tourism
industry:
For reducing the overall costs of various business functions
For enhancing operational efficiency
For improving services as well as customer experiences (Picanso, 2010).
In this way, in the tourism industry, both the customers as well as business can leverage
benefits from improved communication, reservations, along with guest service systems with
IT.
The IT use in IHG business is having below-listed advantages:
1. The hotelier firm can assess post-purchasing behaviour with the help of IT
6
How chosen business use IT
The chosen business as IHG uses IT for both internal and external communication. For
instance, internally IHG uses IT networking apps for effective communication among their
in-house employees. On the other hand, shareholders, stakeholders, suppliers, and customers
at IHG’s hotel brands get connected to each other with the help of advanced IT platforms
(Popescul & Genete, 2016).
Based on (Sharp, 2017), IHG is using IT in the form of various applications, for instance, the
group is using a cloud-based technology platform that contains hospitality industry-leading
Guest Reservation System (GRS). It has been found that with the use of IT, IHG could bring
their core hotel systems altogether, whole offering the correct mix of technology,
functionality, and data, which is required for improving user stay experiences. Currently, IT
use at IHG is helping the firm’s owners to drive performance and revenue in best possible
way. In addition to that, IHG is looking forward to developing the second phase of IT
emphasized on improving the guest reservation experience (Buhalis & Crotts, 2013).
Furthermore, in order to find more ways for enriching ever business process from guests
booking to marketing and stays, IT is getting utilised by the IHG hospitality firm (Gollmann,
2010). IHG has also understood the importance of data security and privacy after facing the
IS or data breach during 2016 (Sharp, 2017).
Benefits and advantages of IT
In general, Information Technology is beneficial for following favours in the tourism
industry:
For reducing the overall costs of various business functions
For enhancing operational efficiency
For improving services as well as customer experiences (Picanso, 2010).
In this way, in the tourism industry, both the customers as well as business can leverage
benefits from improved communication, reservations, along with guest service systems with
IT.
The IT use in IHG business is having below-listed advantages:
1. The hotelier firm can assess post-purchasing behaviour with the help of IT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Write Up
7
2. The hotelier firm can effectively use IT for offering better purchase decision to its
users
3. The hotelier firm can evaluate more alternatives for taking business decisions while
providing quality products and services to global users
4. The hotelier firm uses IT for enhanced and customized information searches in
relation to their business growth for sustainable business model.
5. The hotelier firm can use IT for customer need recognition, which ultimately helps
IHG to grow its customer value and reputation worldwide (Ismail, 2017).
Risk of IT
In the context of IT for the hotel group’s business, when IT can provide so many advantages
and benefits to the firm, simultaneously IT poses so many risks and challenges to the chosen
business (Kizza, 2009). These identified IT risks are as follows:
There are risks such as silent invasions and cyber-crime attacks. Such risks are those
powerful tactics that are generally posed by the next generation of criminals.
For example, in 2015, so many cybercriminals have targeted as well as attacked the
famous hotels’ Wi-Fi to acquire the hotel guests’ personal info along with their
passwords.
Another IT risk can be seen in terms of identity theft which may further lead to credit
card fraud (Mullins & Dossor, 2013).
IT may cause a lot of data breaches as well as information stealing from the hotel’s
network systems, which is ultimately responsible for several identity frauds all across
the world.
Although global hotelier firms are using IT for their business growth yet they are
having no security audit cycles. The aforementioned issue can raise the difficult
situation for the investors as well as the guests of high risk.
IT may pose the risks of loss of competitive advantage as well as a firm image with
negative mouth publicity. This is because data breach events occurred at hotel servers
spread quickly like a viral with internet facility hence it may cause reputation damage.
IT may pose the risks of physical crimes such as terrorism which put the modern
hotels in the challenge. Subsequently, it harms hotelier firms’ image and reputation
(Liu et al., 2018).
7
2. The hotelier firm can effectively use IT for offering better purchase decision to its
users
3. The hotelier firm can evaluate more alternatives for taking business decisions while
providing quality products and services to global users
4. The hotelier firm uses IT for enhanced and customized information searches in
relation to their business growth for sustainable business model.
5. The hotelier firm can use IT for customer need recognition, which ultimately helps
IHG to grow its customer value and reputation worldwide (Ismail, 2017).
Risk of IT
In the context of IT for the hotel group’s business, when IT can provide so many advantages
and benefits to the firm, simultaneously IT poses so many risks and challenges to the chosen
business (Kizza, 2009). These identified IT risks are as follows:
There are risks such as silent invasions and cyber-crime attacks. Such risks are those
powerful tactics that are generally posed by the next generation of criminals.
For example, in 2015, so many cybercriminals have targeted as well as attacked the
famous hotels’ Wi-Fi to acquire the hotel guests’ personal info along with their
passwords.
Another IT risk can be seen in terms of identity theft which may further lead to credit
card fraud (Mullins & Dossor, 2013).
IT may cause a lot of data breaches as well as information stealing from the hotel’s
network systems, which is ultimately responsible for several identity frauds all across
the world.
Although global hotelier firms are using IT for their business growth yet they are
having no security audit cycles. The aforementioned issue can raise the difficult
situation for the investors as well as the guests of high risk.
IT may pose the risks of loss of competitive advantage as well as a firm image with
negative mouth publicity. This is because data breach events occurred at hotel servers
spread quickly like a viral with internet facility hence it may cause reputation damage.
IT may pose the risks of physical crimes such as terrorism which put the modern
hotels in the challenge. Subsequently, it harms hotelier firms’ image and reputation
(Liu et al., 2018).

IT Write Up
8
How selected business can maintain and monitor IT
The chosen IHG business can effectively monitor and maintain their IT systems as follows:
By monitoring available security vulnerabilities on hotel servers, IT network systems
can be monitored effectively
Safety monitoring features on their website and hotel booking applications
Computer server monitoring systems can be used.
With the help of conducting information security investigations, IHG can monitor and
maintain their IT-driven systems
IHG can further maintain correct and efficient IS measures for monitoring
unauthorized hotels’ computer access
IT infrastructure monitoring and tracking systems can be used
With technical monitoring of all software and hardware of the hotel management
systems, whole computer systems can be monitored easily
Network monitoring can also help in IT maintenance and monitoring by the IHG
Through hiring best IT experts and CIOs, IHG can use the best possible techniques
and tactics for monitoring IT systems (Vacca, 2012).
Conclusion
In whole, this report has successfully researched the different roles of IT in tourism and
hospitality industry. While discussing the significance of IT for IHG business, the report has
discussed IT importance for business survival in this modern era. In addition, different
resources required for applying IT into IHG business while covering several hotelier
operations have been discussed in detail. Apart from this, the reasons why IHG use IT have
been identified, explained and explored effectively. It has been found that IHG uses IT for
having effective communication throughout its business activities while highlighting IT use
internally and externally. On the other hand, so many benefits and advantages have been
discussed which IT brings to IHG business worldwide. Moreover, while discussing IT for
tourism business, this research has identified all possible type of risks which IT brings to the
8
How selected business can maintain and monitor IT
The chosen IHG business can effectively monitor and maintain their IT systems as follows:
By monitoring available security vulnerabilities on hotel servers, IT network systems
can be monitored effectively
Safety monitoring features on their website and hotel booking applications
Computer server monitoring systems can be used.
With the help of conducting information security investigations, IHG can monitor and
maintain their IT-driven systems
IHG can further maintain correct and efficient IS measures for monitoring
unauthorized hotels’ computer access
IT infrastructure monitoring and tracking systems can be used
With technical monitoring of all software and hardware of the hotel management
systems, whole computer systems can be monitored easily
Network monitoring can also help in IT maintenance and monitoring by the IHG
Through hiring best IT experts and CIOs, IHG can use the best possible techniques
and tactics for monitoring IT systems (Vacca, 2012).
Conclusion
In whole, this report has successfully researched the different roles of IT in tourism and
hospitality industry. While discussing the significance of IT for IHG business, the report has
discussed IT importance for business survival in this modern era. In addition, different
resources required for applying IT into IHG business while covering several hotelier
operations have been discussed in detail. Apart from this, the reasons why IHG use IT have
been identified, explained and explored effectively. It has been found that IHG uses IT for
having effective communication throughout its business activities while highlighting IT use
internally and externally. On the other hand, so many benefits and advantages have been
discussed which IT brings to IHG business worldwide. Moreover, while discussing IT for
tourism business, this research has identified all possible type of risks which IT brings to the

IT Write Up
9
chosen business. In this context, IT risks like privacy, security, and confidentiality have been
narrated and highlighted in an efficient way. Furthermore, the findings of this research report
are suggesting that IHG can effectively utilise several kinds of monitoring systems for
effective IT maintenance and monitoring.
9
chosen business. In this context, IT risks like privacy, security, and confidentiality have been
narrated and highlighted in an efficient way. Furthermore, the findings of this research report
are suggesting that IHG can effectively utilise several kinds of monitoring systems for
effective IT maintenance and monitoring.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Write Up
10
References
Australian Government, 2018. Notifiable Data Breaches scheme. [Online] Available at:
https://www.oaic.gov.au/privacy-law/privacy-act/notifiable-data-breaches-scheme [Accessed
16 October 2018].
Bhavani, M.G., 2013. Customer’s expectations of hospitality services–a study on five star
hotels in Hyderabad city. Journal of Management and Science, 3(4), pp.16-22.
Buhalis, D. & Crotts, J., 2013. Global alliances in tourism and hospitality management.
LOndon : Routledge.
Gatzlaff, K. & McCullough, K., 2010. The effect of data breaches on shareholder wealth.
Risk management and Insurance Review, 13(1), pp.61-83.
Gollmann, D., 2010. Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), pp.544-54.
Ismail, N., 2017. 7 nightmare cyber security threats to SMEs and how to secure against them.
[Online] Available at: https://www.information-age.com/7-nightmare-cyber-security-threats-
smes-secure-123466495/ [Accessed 12 October 2018].
Kizza, J., 2009. Guide to computer network security. London: Springer.
Liu, L., Han, M., Wang, Y. & Zhou, Y., 2018. Understanding data breach: a visualization
aspect. International Conference on Wireless Algorithms systems and applications, pp.883-
92.
Mullins, L. & Dossor, P., 2013. Hospitality Management and Organisational Behaviour. 5th
ed. UK: Pearson.
Picanso, K.E., 2010. Protecting information security under a uniform data breach notification
law. Fordham L., (Rev.), p.355.
Popescul, D. & Genete, L., 2016. Data security in smart cities: challenges and solutions.
Informatica Ecomonica, 20(1).
Shabani, N., 2017. A study of cyber security in hospitality industry-threats and
countermeasures: case study in Reno, Nevada. ArXiv.
10
References
Australian Government, 2018. Notifiable Data Breaches scheme. [Online] Available at:
https://www.oaic.gov.au/privacy-law/privacy-act/notifiable-data-breaches-scheme [Accessed
16 October 2018].
Bhavani, M.G., 2013. Customer’s expectations of hospitality services–a study on five star
hotels in Hyderabad city. Journal of Management and Science, 3(4), pp.16-22.
Buhalis, D. & Crotts, J., 2013. Global alliances in tourism and hospitality management.
LOndon : Routledge.
Gatzlaff, K. & McCullough, K., 2010. The effect of data breaches on shareholder wealth.
Risk management and Insurance Review, 13(1), pp.61-83.
Gollmann, D., 2010. Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), pp.544-54.
Ismail, N., 2017. 7 nightmare cyber security threats to SMEs and how to secure against them.
[Online] Available at: https://www.information-age.com/7-nightmare-cyber-security-threats-
smes-secure-123466495/ [Accessed 12 October 2018].
Kizza, J., 2009. Guide to computer network security. London: Springer.
Liu, L., Han, M., Wang, Y. & Zhou, Y., 2018. Understanding data breach: a visualization
aspect. International Conference on Wireless Algorithms systems and applications, pp.883-
92.
Mullins, L. & Dossor, P., 2013. Hospitality Management and Organisational Behaviour. 5th
ed. UK: Pearson.
Picanso, K.E., 2010. Protecting information security under a uniform data breach notification
law. Fordham L., (Rev.), p.355.
Popescul, D. & Genete, L., 2016. Data security in smart cities: challenges and solutions.
Informatica Ecomonica, 20(1).
Shabani, N., 2017. A study of cyber security in hospitality industry-threats and
countermeasures: case study in Reno, Nevada. ArXiv.

IT Write Up
11
Sharp, A., 2017. Cyber attack hits 1,200 InterContinental hotels in United States. [Online]
Available at: https://www.reuters.com/article/us-intercontinental-cyber/cyber-attack-hits-
1200-intercontinental-hotels-in-united-states-idUSKBN17L1TA [Accessed 25 September
2019].
Stallings, W., Brown, L., Bauer, M. & Bhattacharjee, A., 2012. Computer security: principles
and practice. NJ: Pearson Education.
The AME group, 2018. Data Security Breach: 5 Consequences for Your Business. [Online]
Available at: https://www.theamegroup.com/security-breach/ [Accessed 16 October 2018].
The Economic Times, 2018. 5 simple tips to keep your business secure from cyberattacks.
[Online] Available at:
https://economictimes.indiatimes.com/small-biz/security-tech/security/5-simple-tips-to-keep-
your-business-secure-from-cyberattacks/articleshow/64568063.cms [Accessed 12 October
2018].
Vacca, J., 2012. Computer and information security handbook. London: Newnes.
11
Sharp, A., 2017. Cyber attack hits 1,200 InterContinental hotels in United States. [Online]
Available at: https://www.reuters.com/article/us-intercontinental-cyber/cyber-attack-hits-
1200-intercontinental-hotels-in-united-states-idUSKBN17L1TA [Accessed 25 September
2019].
Stallings, W., Brown, L., Bauer, M. & Bhattacharjee, A., 2012. Computer security: principles
and practice. NJ: Pearson Education.
The AME group, 2018. Data Security Breach: 5 Consequences for Your Business. [Online]
Available at: https://www.theamegroup.com/security-breach/ [Accessed 16 October 2018].
The Economic Times, 2018. 5 simple tips to keep your business secure from cyberattacks.
[Online] Available at:
https://economictimes.indiatimes.com/small-biz/security-tech/security/5-simple-tips-to-keep-
your-business-secure-from-cyberattacks/articleshow/64568063.cms [Accessed 12 October
2018].
Vacca, J., 2012. Computer and information security handbook. London: Newnes.
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





