COIT20246 IT Assignment: Week 1-5 Tech Resource Review & Summary
VerifiedAdded on 2023/04/25
|13
|4628
|232
Homework Assignment
AI Summary
This assignment for COIT20246 involves summarizing various IT resources covering topics from weeks 1 to 5. Week 1 focuses on Very Large Scale Integration (VLSI) technology and its applications in wireless mobile communication. Week 2 explores the future use of blockchain operating systems, particularly Hyperledger Fabric. Week 3 discusses on-demand computing, using Google as a specific example of a company providing such services. Week 4 examines the features and uses of Virtual Local Area Networks (VLANs) as a Layer 2 protocol. Finally, Week 5 delves into the application of the Internet of Things (IoT) in the medical and health sectors, focusing on the Internet of Health Things. Each summary provides insights into the chosen resources and their relevance to the respective topics.
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see unit website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see unit website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There
is a table to complete for each task. Please fill in the information required. An
example of a completed task is below. Note the first response is good – so aim
for something like this. The second response is not acceptable, so if you submit
anything like it, you won’t pass the assignment! The reasons? Poor resource
selection (Wikipedia), no Harvard reference and a block cut and paste from the
site (no citation, no original content).
Example
Task Find two resources that explain aspects of IT Service
Management.
(Good
Respons
e)
Title and Reference:
COBIT versus ITIL
Ibaraki, S 2014, online, COBIT versus ITIL, viewed 29/01/2015,
<http://blogs.technet.com/b/cdnitmanagers/archive/2014/04/06/cobit-
versus-itil.aspx>.
Summary:
This resource is a blog entry discussing the differences between
CoBIT and ITIL. I chose this resource as there is a lot of confusion
about the way in which ITSM is applied and the distinction between
the CoBIT and ITIL implementations is frequently unclear. Ibaraki
explains that CoBIT provides the governance and metric structures
while ITIL delivers on the actual mechanics and “how-to” processes.
The author makes an interesting observation that it is wrong to
simplify COBIT as providing the ‘why’ and ITIL providing the ‘how’
because both ITSM mechanisms have considerable overlap and
both need to be used at the same time. I found this article very
useful in explaining the differences and similarities between these
two aspects of ITSM.
(Bad
Respons
e)
Title and Reference:
http://en.wikipedia.org/wiki/IT_service_management
Summary:
This pages talks about ITSM. It says that IT service
management (ITSM) refers to the entirety of activities – directed
by policies, organized and structured in processes and
supporting procedures – that are performed by an organization or
part of an organization to plan, deliver, operate and control IT
services offered to customers. It is thus concerned with the
implementation of quality IT services that meet the needs of
customers, and is performed by the IT service provider through an
appropriate mix of people, process and information technology.
There are ten (10) tasks, one for each week: the tasks are detailed below. There
is a table to complete for each task. Please fill in the information required. An
example of a completed task is below. Note the first response is good – so aim
for something like this. The second response is not acceptable, so if you submit
anything like it, you won’t pass the assignment! The reasons? Poor resource
selection (Wikipedia), no Harvard reference and a block cut and paste from the
site (no citation, no original content).
Example
Task Find two resources that explain aspects of IT Service
Management.
(Good
Respons
e)
Title and Reference:
COBIT versus ITIL
Ibaraki, S 2014, online, COBIT versus ITIL, viewed 29/01/2015,
<http://blogs.technet.com/b/cdnitmanagers/archive/2014/04/06/cobit-
versus-itil.aspx>.
Summary:
This resource is a blog entry discussing the differences between
CoBIT and ITIL. I chose this resource as there is a lot of confusion
about the way in which ITSM is applied and the distinction between
the CoBIT and ITIL implementations is frequently unclear. Ibaraki
explains that CoBIT provides the governance and metric structures
while ITIL delivers on the actual mechanics and “how-to” processes.
The author makes an interesting observation that it is wrong to
simplify COBIT as providing the ‘why’ and ITIL providing the ‘how’
because both ITSM mechanisms have considerable overlap and
both need to be used at the same time. I found this article very
useful in explaining the differences and similarities between these
two aspects of ITSM.
(Bad
Respons
e)
Title and Reference:
http://en.wikipedia.org/wiki/IT_service_management
Summary:
This pages talks about ITSM. It says that IT service
management (ITSM) refers to the entirety of activities – directed
by policies, organized and structured in processes and
supporting procedures – that are performed by an organization or
part of an organization to plan, deliver, operate and control IT
services offered to customers. It is thus concerned with the
implementation of quality IT services that meet the needs of
customers, and is performed by the IT service provider through an
appropriate mix of people, process and information technology.
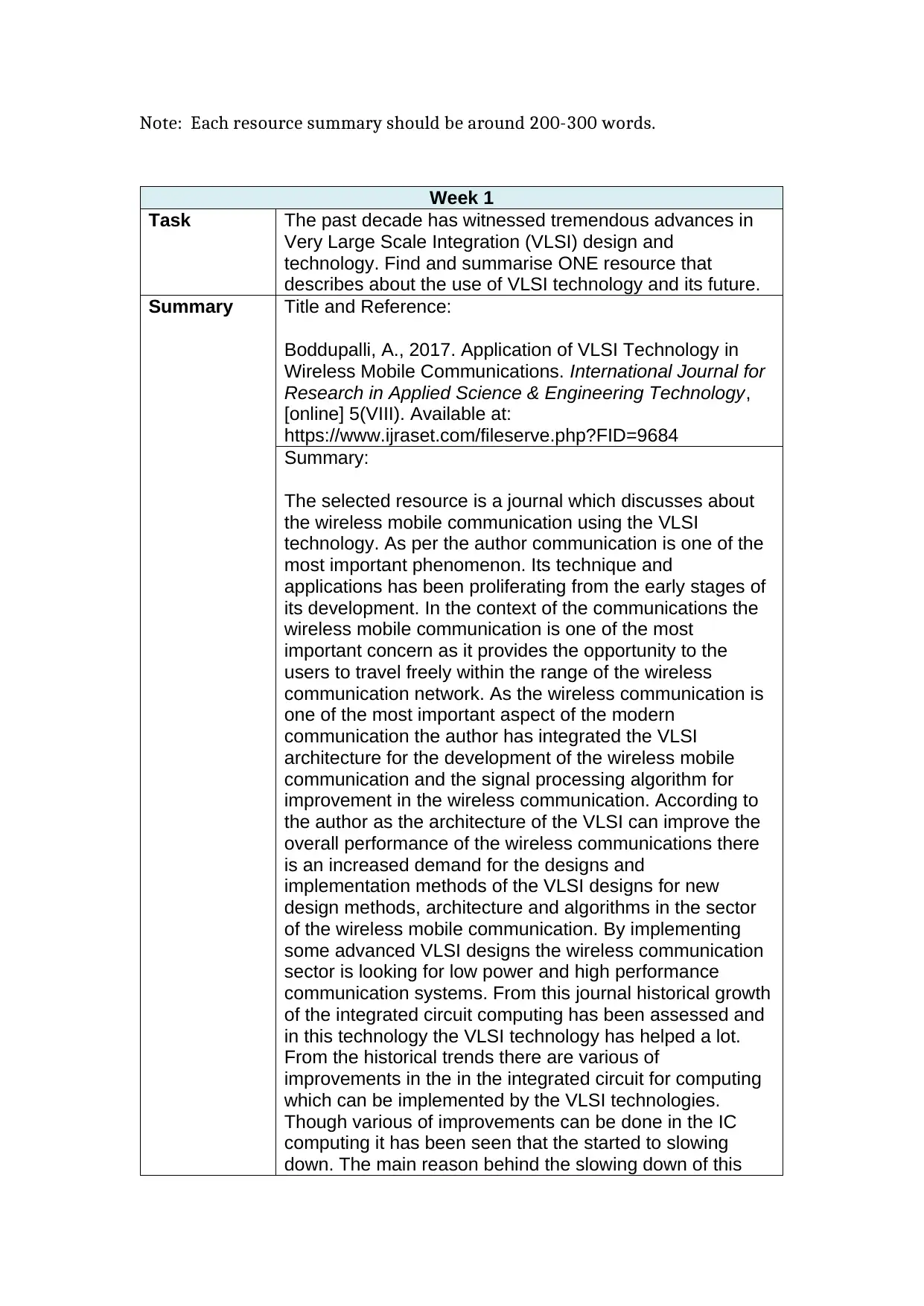
Note: Each resource summary should be around 200-300 words.
Week 1
Task The past decade has witnessed tremendous advances in
Very Large Scale Integration (VLSI) design and
technology. Find and summarise ONE resource that
describes about the use of VLSI technology and its future.
Summary Title and Reference:
Boddupalli, A., 2017. Application of VLSI Technology in
Wireless Mobile Communications. International Journal for
Research in Applied Science & Engineering Technology,
[online] 5(VIII). Available at:
https://www.ijraset.com/fileserve.php?FID=9684
Summary:
The selected resource is a journal which discusses about
the wireless mobile communication using the VLSI
technology. As per the author communication is one of the
most important phenomenon. Its technique and
applications has been proliferating from the early stages of
its development. In the context of the communications the
wireless mobile communication is one of the most
important concern as it provides the opportunity to the
users to travel freely within the range of the wireless
communication network. As the wireless communication is
one of the most important aspect of the modern
communication the author has integrated the VLSI
architecture for the development of the wireless mobile
communication and the signal processing algorithm for
improvement in the wireless communication. According to
the author as the architecture of the VLSI can improve the
overall performance of the wireless communications there
is an increased demand for the designs and
implementation methods of the VLSI designs for new
design methods, architecture and algorithms in the sector
of the wireless mobile communication. By implementing
some advanced VLSI designs the wireless communication
sector is looking for low power and high performance
communication systems. From this journal historical growth
of the integrated circuit computing has been assessed and
in this technology the VLSI technology has helped a lot.
From the historical trends there are various of
improvements in the in the integrated circuit for computing
which can be implemented by the VLSI technologies.
Though various of improvements can be done in the IC
computing it has been seen that the started to slowing
down. The main reason behind the slowing down of this
Week 1
Task The past decade has witnessed tremendous advances in
Very Large Scale Integration (VLSI) design and
technology. Find and summarise ONE resource that
describes about the use of VLSI technology and its future.
Summary Title and Reference:
Boddupalli, A., 2017. Application of VLSI Technology in
Wireless Mobile Communications. International Journal for
Research in Applied Science & Engineering Technology,
[online] 5(VIII). Available at:
https://www.ijraset.com/fileserve.php?FID=9684
Summary:
The selected resource is a journal which discusses about
the wireless mobile communication using the VLSI
technology. As per the author communication is one of the
most important phenomenon. Its technique and
applications has been proliferating from the early stages of
its development. In the context of the communications the
wireless mobile communication is one of the most
important concern as it provides the opportunity to the
users to travel freely within the range of the wireless
communication network. As the wireless communication is
one of the most important aspect of the modern
communication the author has integrated the VLSI
architecture for the development of the wireless mobile
communication and the signal processing algorithm for
improvement in the wireless communication. According to
the author as the architecture of the VLSI can improve the
overall performance of the wireless communications there
is an increased demand for the designs and
implementation methods of the VLSI designs for new
design methods, architecture and algorithms in the sector
of the wireless mobile communication. By implementing
some advanced VLSI designs the wireless communication
sector is looking for low power and high performance
communication systems. From this journal historical growth
of the integrated circuit computing has been assessed and
in this technology the VLSI technology has helped a lot.
From the historical trends there are various of
improvements in the in the integrated circuit for computing
which can be implemented by the VLSI technologies.
Though various of improvements can be done in the IC
computing it has been seen that the started to slowing
down. The main reason behind the slowing down of this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
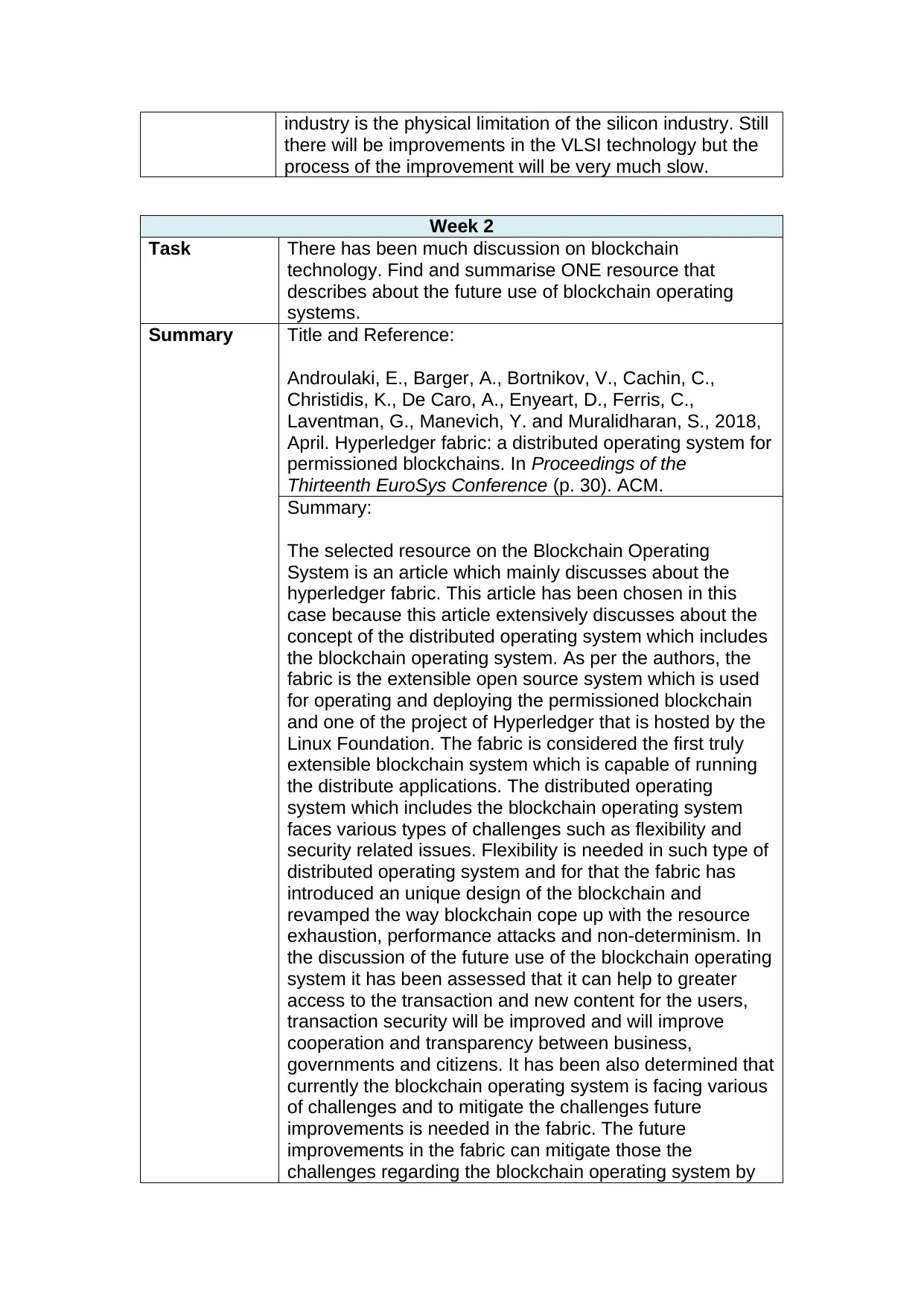
industry is the physical limitation of the silicon industry. Still
there will be improvements in the VLSI technology but the
process of the improvement will be very much slow.
Week 2
Task There has been much discussion on blockchain
technology. Find and summarise ONE resource that
describes about the future use of blockchain operating
systems.
Summary Title and Reference:
Androulaki, E., Barger, A., Bortnikov, V., Cachin, C.,
Christidis, K., De Caro, A., Enyeart, D., Ferris, C.,
Laventman, G., Manevich, Y. and Muralidharan, S., 2018,
April. Hyperledger fabric: a distributed operating system for
permissioned blockchains. In Proceedings of the
Thirteenth EuroSys Conference (p. 30). ACM.
Summary:
The selected resource on the Blockchain Operating
System is an article which mainly discusses about the
hyperledger fabric. This article has been chosen in this
case because this article extensively discusses about the
concept of the distributed operating system which includes
the blockchain operating system. As per the authors, the
fabric is the extensible open source system which is used
for operating and deploying the permissioned blockchain
and one of the project of Hyperledger that is hosted by the
Linux Foundation. The fabric is considered the first truly
extensible blockchain system which is capable of running
the distribute applications. The distributed operating
system which includes the blockchain operating system
faces various types of challenges such as flexibility and
security related issues. Flexibility is needed in such type of
distributed operating system and for that the fabric has
introduced an unique design of the blockchain and
revamped the way blockchain cope up with the resource
exhaustion, performance attacks and non-determinism. In
the discussion of the future use of the blockchain operating
system it has been assessed that it can help to greater
access to the transaction and new content for the users,
transaction security will be improved and will improve
cooperation and transparency between business,
governments and citizens. It has been also determined that
currently the blockchain operating system is facing various
of challenges and to mitigate the challenges future
improvements is needed in the fabric. The future
improvements in the fabric can mitigate those the
challenges regarding the blockchain operating system by
there will be improvements in the VLSI technology but the
process of the improvement will be very much slow.
Week 2
Task There has been much discussion on blockchain
technology. Find and summarise ONE resource that
describes about the future use of blockchain operating
systems.
Summary Title and Reference:
Androulaki, E., Barger, A., Bortnikov, V., Cachin, C.,
Christidis, K., De Caro, A., Enyeart, D., Ferris, C.,
Laventman, G., Manevich, Y. and Muralidharan, S., 2018,
April. Hyperledger fabric: a distributed operating system for
permissioned blockchains. In Proceedings of the
Thirteenth EuroSys Conference (p. 30). ACM.
Summary:
The selected resource on the Blockchain Operating
System is an article which mainly discusses about the
hyperledger fabric. This article has been chosen in this
case because this article extensively discusses about the
concept of the distributed operating system which includes
the blockchain operating system. As per the authors, the
fabric is the extensible open source system which is used
for operating and deploying the permissioned blockchain
and one of the project of Hyperledger that is hosted by the
Linux Foundation. The fabric is considered the first truly
extensible blockchain system which is capable of running
the distribute applications. The distributed operating
system which includes the blockchain operating system
faces various types of challenges such as flexibility and
security related issues. Flexibility is needed in such type of
distributed operating system and for that the fabric has
introduced an unique design of the blockchain and
revamped the way blockchain cope up with the resource
exhaustion, performance attacks and non-determinism. In
the discussion of the future use of the blockchain operating
system it has been assessed that it can help to greater
access to the transaction and new content for the users,
transaction security will be improved and will improve
cooperation and transparency between business,
governments and citizens. It has been also determined that
currently the blockchain operating system is facing various
of challenges and to mitigate the challenges future
improvements is needed in the fabric. The future
improvements in the fabric can mitigate those the
challenges regarding the blockchain operating system by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
pipelining the validation stages.
Week 3
Task On-demand computing is a business computing model
whereby computing resources and technology are made
available to the user at anytime. Find and summarise ONE
resource that describes about a specific company which
provides on-demand computing. Explain in detail about the
types of services that the company provides.
Summary Title and Reference:
Google.com, 2019. Our Products | Google. [online]
Available at: https://www.google.com/about/products/
Summary:
The selected resource is an online resource and official
website of the Google LLC itself. In this case this resource
has been selected because Google is one of the major
organizations that provides on demand computing model
for both the business and personal use by its cloud
platform. In this cloud platform the Google uses the online
servers which serves the customers when they demand
some online services or some files which are stored in the
online database or online storage. The Google LLC is an
American Multinational organization which is specialized in
the internet related products and services. With the on
demand computing services which often known as the
cloud computing services the Google LLC also provides
services like the online advertising, search engine,
hardware and software. The Google LLC is famous
worldwide for its search engine which is considered one of
the best search engine in the world. In the search engine
services Google LLC also provides search engine
optimization and the search engine marketing. Also, in this
section of the services Google also provides promotion of
the websites and optimization services of the websites.
Online advertising services is one of the major services
which is provided by the Google LLC. Google gains most
of the profit of them from this online advertising services. In
the sector of the software division Google provides
services regarding one of the most popular operating
system which is Android operating system. Beside that
Google also provides services regarding the Chrome OS
which is developed by Google itself. Google LLC also
provides services in the artificial intelligence sector which is
smart assistance services. This smart assistance is known
as the Google Assistance. The other services provided by
the Google LLC are the navigational services and
education related services.
Week 3
Task On-demand computing is a business computing model
whereby computing resources and technology are made
available to the user at anytime. Find and summarise ONE
resource that describes about a specific company which
provides on-demand computing. Explain in detail about the
types of services that the company provides.
Summary Title and Reference:
Google.com, 2019. Our Products | Google. [online]
Available at: https://www.google.com/about/products/
Summary:
The selected resource is an online resource and official
website of the Google LLC itself. In this case this resource
has been selected because Google is one of the major
organizations that provides on demand computing model
for both the business and personal use by its cloud
platform. In this cloud platform the Google uses the online
servers which serves the customers when they demand
some online services or some files which are stored in the
online database or online storage. The Google LLC is an
American Multinational organization which is specialized in
the internet related products and services. With the on
demand computing services which often known as the
cloud computing services the Google LLC also provides
services like the online advertising, search engine,
hardware and software. The Google LLC is famous
worldwide for its search engine which is considered one of
the best search engine in the world. In the search engine
services Google LLC also provides search engine
optimization and the search engine marketing. Also, in this
section of the services Google also provides promotion of
the websites and optimization services of the websites.
Online advertising services is one of the major services
which is provided by the Google LLC. Google gains most
of the profit of them from this online advertising services. In
the sector of the software division Google provides
services regarding one of the most popular operating
system which is Android operating system. Beside that
Google also provides services regarding the Chrome OS
which is developed by Google itself. Google LLC also
provides services in the artificial intelligence sector which is
smart assistance services. This smart assistance is known
as the Google Assistance. The other services provided by
the Google LLC are the navigational services and
education related services.
Week 4
Task Ethernet is a layer 2 protocol that defines wiring and
signaling standards for the physical layer of TCP/IP. Find
and summarise ONE resource that describes the features
and uses of ONE other layer 2 protocol that is not
discussed in the textbook.
Summary Title and Reference:
Bassey, D.E., Okon, B.E. and Umunnah, R., 2016. „The
Security Implications of Virtual Local Area Network
(VLAN), Niger Mills, Calabar, Nigeria‟. International
Journal of Scientific & Engineering Research (IJSER), 7(3),
pp.1187-1194.
Summary:
The selected article is a journal article and this article has
an intensive discussion on the Virtual Local Area Network
or the VLAN. Form the article it has been assessed that
the Virtual Local Area Network is a typical type of logical
grouping of the users of the network and resources which
are connected for administratively defining various of
operations done by the activated ports on a switch. It has
been assessed that by the creation of the VLAN is saddled
with the ability of developing small broadcasting domain
within a switching router 2. In the current selected article,
the application was a redesigned project and this project
executed on the Niger-Mills network for improvement in the
operational short falls which are identified by the operators
itself. In this article the LAN connection of the Niger Mills
also discussed and it has been assessed that it has
covered a total number of five departments in the LAN
which includes marketing, finance, sales, management and
engineering. In this project five user randomly sampled
from each of the department for constituting their individual
LAN which formed total 25 of computers. The project
initially run successfully but in the further cases the project
was troubleshooted and from this process it was obvious
that the switches of the layer 2 only read the frames for the
filtering process. Though this does not access the network
layer protocol but the introduction of the VLAN effectively
added smaller type of broadcasting domain at the layer of
2. The main design was based on this framework and it
was modified further by six core layer switches with 24 port
Task Ethernet is a layer 2 protocol that defines wiring and
signaling standards for the physical layer of TCP/IP. Find
and summarise ONE resource that describes the features
and uses of ONE other layer 2 protocol that is not
discussed in the textbook.
Summary Title and Reference:
Bassey, D.E., Okon, B.E. and Umunnah, R., 2016. „The
Security Implications of Virtual Local Area Network
(VLAN), Niger Mills, Calabar, Nigeria‟. International
Journal of Scientific & Engineering Research (IJSER), 7(3),
pp.1187-1194.
Summary:
The selected article is a journal article and this article has
an intensive discussion on the Virtual Local Area Network
or the VLAN. Form the article it has been assessed that
the Virtual Local Area Network is a typical type of logical
grouping of the users of the network and resources which
are connected for administratively defining various of
operations done by the activated ports on a switch. It has
been assessed that by the creation of the VLAN is saddled
with the ability of developing small broadcasting domain
within a switching router 2. In the current selected article,
the application was a redesigned project and this project
executed on the Niger-Mills network for improvement in the
operational short falls which are identified by the operators
itself. In this article the LAN connection of the Niger Mills
also discussed and it has been assessed that it has
covered a total number of five departments in the LAN
which includes marketing, finance, sales, management and
engineering. In this project five user randomly sampled
from each of the department for constituting their individual
LAN which formed total 25 of computers. The project
initially run successfully but in the further cases the project
was troubleshooted and from this process it was obvious
that the switches of the layer 2 only read the frames for the
filtering process. Though this does not access the network
layer protocol but the introduction of the VLAN effectively
added smaller type of broadcasting domain at the layer of
2. The main design was based on this framework and it
was modified further by six core layer switches with 24 port
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cisco catalyst 2950 switch.
Week 5
Task There has been much discussion on the application of the
Internet of Things (IoT) for medical and health related
purposes. Find and summarise ONE resource that
describes the application of the Internet of Health Things in
the health sector.
Summary Title and Reference:
Gope, P. and Hwang, T., 2016. BSN-Care: A secure IoT-based
modern healthcare system using body sensor network. IEEE
Sensors Journal, 16(5), pp.1368-1376.
Summary:
The recent advancement in the Information and the
communication technologies has led to the innovation
regarding the implementation of the Internet of Things
devices in almost every sector including the health care
sector also. In the current environment of the modern
health care systems the implementation of the Internet of
Things technologies has helped the doctors and the
patients in various of sectors regarding the health care.
This technology has helped the health care sector in the
aspect of the information management system of the
patients, health care management and real time monitoring
of the patient’s health condition. In this article the authors
has widely discussed about the particular implementation
of the Internet of Things in the health care sector which is
the body sensor network or the BSN technology. This BSN
technology or the body sensor network technology is one
of the core technologies which has been developed
through the IoT developments in the sector of the health
care administration. In this case the patient is monitored
efficiently by the collection of the very small and some light
weight wireless sensors. As per the author though this is
one of the great inventions in the sector of the health care
industry this technology has some of the major flaws. In
such of the cases the smart devices can create a
vulnerability point in the privacy of the patient if the security
of the devices are not accounted properly. Thus in paper
the authors has mainly focused on the major security
requirements for the BSN based modern devices in the
health care sector. The authors has also proposed a new
secure type of IoT based health care system which are
using the mechanism of the BSN and called BSN care.
Both of them are capable to accomplish the required
security related tasks very easily.
Week 5
Task There has been much discussion on the application of the
Internet of Things (IoT) for medical and health related
purposes. Find and summarise ONE resource that
describes the application of the Internet of Health Things in
the health sector.
Summary Title and Reference:
Gope, P. and Hwang, T., 2016. BSN-Care: A secure IoT-based
modern healthcare system using body sensor network. IEEE
Sensors Journal, 16(5), pp.1368-1376.
Summary:
The recent advancement in the Information and the
communication technologies has led to the innovation
regarding the implementation of the Internet of Things
devices in almost every sector including the health care
sector also. In the current environment of the modern
health care systems the implementation of the Internet of
Things technologies has helped the doctors and the
patients in various of sectors regarding the health care.
This technology has helped the health care sector in the
aspect of the information management system of the
patients, health care management and real time monitoring
of the patient’s health condition. In this article the authors
has widely discussed about the particular implementation
of the Internet of Things in the health care sector which is
the body sensor network or the BSN technology. This BSN
technology or the body sensor network technology is one
of the core technologies which has been developed
through the IoT developments in the sector of the health
care administration. In this case the patient is monitored
efficiently by the collection of the very small and some light
weight wireless sensors. As per the author though this is
one of the great inventions in the sector of the health care
industry this technology has some of the major flaws. In
such of the cases the smart devices can create a
vulnerability point in the privacy of the patient if the security
of the devices are not accounted properly. Thus in paper
the authors has mainly focused on the major security
requirements for the BSN based modern devices in the
health care sector. The authors has also proposed a new
secure type of IoT based health care system which are
using the mechanism of the BSN and called BSN care.
Both of them are capable to accomplish the required
security related tasks very easily.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Week 6
Task Cloud computing technologies have gained popularity due
to the number of advantages they provide to organisations
and individuals such as reduced cost, better storage, and
improved performance. In recent years, there has been a
lot of discussion on the development and implementation
of fog computing. Find and summarise ONE resource that
describes the fog computing. The resource and your
summary should describe how fog computing differs from
cloud computing.
Summary Title and Reference:
Yannuzzi, M., Milito, R., Serral-Gracià, R., Montero, D. and
Nemirovsky, M., 2014, December. Key ingredients in an IoT
recipe: Fog Computing, Cloud computing, and more Fog
Computing. In 2014 IEEE 19th International Workshop on
Computer Aided Modeling and Design of Communication Links
and Networks (CAMAD) (pp. 325-329). IEEE.
Summary:
The selected resource is a journal article and it has
examined some of the most challenging and most
promising scenarios in the Internet of Things and has
elaborated why the present storage and the compute
models confined with the data sectors is not able to fulfil
requirements of many of the applications foreseen in this
scenario. The main discussion of the authors was on the
three interrelated requirements which are the reliable
control, mobility and the scalability. As the IoT technologies
are spanned over a large geographical area and it also
requires the real time decisions solely based on the data
analytics methods. Thus from the analysis the authors has
found that the why the Fog Computing creates the natural
environment or the platform for the IoT technologies. The
authors in this article has also identified the unavoidable
interplay between the cloud and the fog computing. In such
of the process some of the technologies has been
reviewed in this article which are very much important in
the case of remarkable advancement in the market of the
IoT. In this article the differences between the fog
computing and the cloud computing also has been
assessed and it is identified that both of the cloud and the
fog computing has low latency but the fog computing has
very much low latency compared to the cloud computing in
the terms of network. Also, in the concern of the capacity
the cloud computing does not perform any reduction while
sending the data but for the fog computing data is reduced
while sent over a network. In the respect of the bandwidth
the fog computer conserves a very high amount of
Task Cloud computing technologies have gained popularity due
to the number of advantages they provide to organisations
and individuals such as reduced cost, better storage, and
improved performance. In recent years, there has been a
lot of discussion on the development and implementation
of fog computing. Find and summarise ONE resource that
describes the fog computing. The resource and your
summary should describe how fog computing differs from
cloud computing.
Summary Title and Reference:
Yannuzzi, M., Milito, R., Serral-Gracià, R., Montero, D. and
Nemirovsky, M., 2014, December. Key ingredients in an IoT
recipe: Fog Computing, Cloud computing, and more Fog
Computing. In 2014 IEEE 19th International Workshop on
Computer Aided Modeling and Design of Communication Links
and Networks (CAMAD) (pp. 325-329). IEEE.
Summary:
The selected resource is a journal article and it has
examined some of the most challenging and most
promising scenarios in the Internet of Things and has
elaborated why the present storage and the compute
models confined with the data sectors is not able to fulfil
requirements of many of the applications foreseen in this
scenario. The main discussion of the authors was on the
three interrelated requirements which are the reliable
control, mobility and the scalability. As the IoT technologies
are spanned over a large geographical area and it also
requires the real time decisions solely based on the data
analytics methods. Thus from the analysis the authors has
found that the why the Fog Computing creates the natural
environment or the platform for the IoT technologies. The
authors in this article has also identified the unavoidable
interplay between the cloud and the fog computing. In such
of the process some of the technologies has been
reviewed in this article which are very much important in
the case of remarkable advancement in the market of the
IoT. In this article the differences between the fog
computing and the cloud computing also has been
assessed and it is identified that both of the cloud and the
fog computing has low latency but the fog computing has
very much low latency compared to the cloud computing in
the terms of network. Also, in the concern of the capacity
the cloud computing does not perform any reduction while
sending the data but for the fog computing data is reduced
while sent over a network. In the respect of the bandwidth
the fog computer conserves a very high amount of
bandwidth when compared with the cloud computing.
Week 7
Task Business intelligence and analytics has emerged as an
important tool that provide insight and fuel innovation,
enabling organizations to leverage the intrinsic value of
their data. Find and summarise ONE resource that
describes the effective use of business intelligence and
analytics in the finance sector.
Summary Title and Reference:
Van Belle, J.P. and Dawson, L., 2013. Critical success factors
for business intelligence in the South African financial services
sector. South African Journal of Information Management,
15(1), pp.1-12.
Summary:
The selected article for this topic is a journal article and this
article describes the critical success factors for the process
of the business intelligence in the financial service sector
of South Africa. In the article the authors have described
the effective usage of the business intelligence and why it
has become an important part of the business solutions.
The business intelligence is efficiently providing vital
decision-making information which build the shareholder
value and ensures the sustainability. The critical success
factors is providing insight to those factors which are
needed by the organizations for addressing and improving
the business intelligence projects. On this article the
authors has performed a research and the main aim of this
research is determining the critical success factors which
are one of the most important in the financial sector of the
nation South Africa. For evaluating the critical success
factors the authors in this case used the Delphi-technique
of approach which with the collaboration of the key
stakeholders of the project in total three different types of
business intelligence projects in the region of the South
African financial services. From the research the authors
has found the critical success factors for the business
intelligence are the business vision, committed
management support and champion, data quality and user
involvement. As per the authors the effective usage of the
business intelligence in the financial sector enables the
organizations to analyze the vast amount of the customer
data and helps to gain insight about the data of the
customer’s needs for improvements in the services and the
products.
Week 7
Task Business intelligence and analytics has emerged as an
important tool that provide insight and fuel innovation,
enabling organizations to leverage the intrinsic value of
their data. Find and summarise ONE resource that
describes the effective use of business intelligence and
analytics in the finance sector.
Summary Title and Reference:
Van Belle, J.P. and Dawson, L., 2013. Critical success factors
for business intelligence in the South African financial services
sector. South African Journal of Information Management,
15(1), pp.1-12.
Summary:
The selected article for this topic is a journal article and this
article describes the critical success factors for the process
of the business intelligence in the financial service sector
of South Africa. In the article the authors have described
the effective usage of the business intelligence and why it
has become an important part of the business solutions.
The business intelligence is efficiently providing vital
decision-making information which build the shareholder
value and ensures the sustainability. The critical success
factors is providing insight to those factors which are
needed by the organizations for addressing and improving
the business intelligence projects. On this article the
authors has performed a research and the main aim of this
research is determining the critical success factors which
are one of the most important in the financial sector of the
nation South Africa. For evaluating the critical success
factors the authors in this case used the Delphi-technique
of approach which with the collaboration of the key
stakeholders of the project in total three different types of
business intelligence projects in the region of the South
African financial services. From the research the authors
has found the critical success factors for the business
intelligence are the business vision, committed
management support and champion, data quality and user
involvement. As per the authors the effective usage of the
business intelligence in the financial sector enables the
organizations to analyze the vast amount of the customer
data and helps to gain insight about the data of the
customer’s needs for improvements in the services and the
products.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Week 8
Task The term “translytical” is a recent addition to the database
industry jargon. Find and summarise ONE resource that
describes the main functions of a translytical data platform.
The resource and your summary should describe how
translytical data platform differs from transactional data
platform.
Summary Title and Reference:
Datanami. 2019. Translytical Databases Hit the Ground
Running. [online] Available at:
https://www.datanami.com/2017/12/06/translytical-databases-
hit-ground-running
Summary:
The selected article is an online article which describe the
main functions of the translytical data platform. As per the
author of this article the main functions or work loads of the
translytical data platform are the some real time
applications which includes the connected data apps,
continuous learning and the operational data of the Internet
of Things. As per the author the translytical data platform
market is expanding in a huge rate because of the pros of
more enterprise architectures. The enterprise architectures
are considering the translytical data platform is very much
critical for their enterprise related data strategy. The
translytical data platform also helps in the case of the
operational analytics which helps to discard the
requirement of the constantly moving data between the
database and the storage for supporting the analytical and
transactional workloads and this is the main reason that the
growth of the translytical data platform is very much huge.
This entire framework uses only a single data tier which
serves both of the analytical and transactional workloads.
This online article has also described the difference
between the translytical data platform and the transactional
data platform. As per this article the transactional data is
the information from the transaction. In this case the
transaction is some sequence of the information exchange
that is used for satisfaction of a request. This type of data
mainly are the logistical, financial or something work
related where the translytical data platform is a typical type
of technology which is able to combine the analytics and
the transaction on a single platform. This type of platforms
can support several of different of use cases.
Task The term “translytical” is a recent addition to the database
industry jargon. Find and summarise ONE resource that
describes the main functions of a translytical data platform.
The resource and your summary should describe how
translytical data platform differs from transactional data
platform.
Summary Title and Reference:
Datanami. 2019. Translytical Databases Hit the Ground
Running. [online] Available at:
https://www.datanami.com/2017/12/06/translytical-databases-
hit-ground-running
Summary:
The selected article is an online article which describe the
main functions of the translytical data platform. As per the
author of this article the main functions or work loads of the
translytical data platform are the some real time
applications which includes the connected data apps,
continuous learning and the operational data of the Internet
of Things. As per the author the translytical data platform
market is expanding in a huge rate because of the pros of
more enterprise architectures. The enterprise architectures
are considering the translytical data platform is very much
critical for their enterprise related data strategy. The
translytical data platform also helps in the case of the
operational analytics which helps to discard the
requirement of the constantly moving data between the
database and the storage for supporting the analytical and
transactional workloads and this is the main reason that the
growth of the translytical data platform is very much huge.
This entire framework uses only a single data tier which
serves both of the analytical and transactional workloads.
This online article has also described the difference
between the translytical data platform and the transactional
data platform. As per this article the transactional data is
the information from the transaction. In this case the
transaction is some sequence of the information exchange
that is used for satisfaction of a request. This type of data
mainly are the logistical, financial or something work
related where the translytical data platform is a typical type
of technology which is able to combine the analytics and
the transaction on a single platform. This type of platforms
can support several of different of use cases.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 9
Task The term sustainability has gained significant popularity in
IS project management. Find and summarise ONE
resource that discusses the importance of sustainability in
IS project management.
Summary Title and Reference:
Silvius, A.J. and Schipper, R.P., 2014. Sustainability in project
management: A literature review and impact analysis. Social
Business, 4(1), pp.63-96.
Summary:
The selected article is a journal article and it efficiently
describes the importance of the sustainability in the case of
the information system project management. As per the
authors sustainability is one of the utmost important
challenges in the present situation. Without the
sustainability features the life of the future generations is
going to be heavily compromised. Thus most of the
organizations and the projects are adding sustainability
related ideas in their projects including the IS related
projects also. The projects are very much important as it
plays an important role for realizing more sustainable
practice of the business. The concept of the sustainability
is lined with the project management procedures. In this
article the authors has provided a structured review of total
number of 164 publications which are related to mainly
with the sustainability to the project management covering
the information system related projects also. This article
has answered the research question of ‘How does
considering sustainability impact project management?’
and ‘How is sustainability defined or considered in
the context of project management?’ Based on the vast
amount of the literature review the authors of this article
has identified the areas of impact of the sustainability of
the feature on the project management. The authors has
identified that the impact of sustainability on the project
management on the different levels. As per the authors this
sustainability for the information system project
management includes the management of the project time,
quality and the budget and managing the social quality.
Week 10
Task The term sustainability has gained significant popularity in
IS project management. Find and summarise ONE
resource that discusses the importance of sustainability in
IS project management.
Summary Title and Reference:
Silvius, A.J. and Schipper, R.P., 2014. Sustainability in project
management: A literature review and impact analysis. Social
Business, 4(1), pp.63-96.
Summary:
The selected article is a journal article and it efficiently
describes the importance of the sustainability in the case of
the information system project management. As per the
authors sustainability is one of the utmost important
challenges in the present situation. Without the
sustainability features the life of the future generations is
going to be heavily compromised. Thus most of the
organizations and the projects are adding sustainability
related ideas in their projects including the IS related
projects also. The projects are very much important as it
plays an important role for realizing more sustainable
practice of the business. The concept of the sustainability
is lined with the project management procedures. In this
article the authors has provided a structured review of total
number of 164 publications which are related to mainly
with the sustainability to the project management covering
the information system related projects also. This article
has answered the research question of ‘How does
considering sustainability impact project management?’
and ‘How is sustainability defined or considered in
the context of project management?’ Based on the vast
amount of the literature review the authors of this article
has identified the areas of impact of the sustainability of
the feature on the project management. The authors has
identified that the impact of sustainability on the project
management on the different levels. As per the authors this
sustainability for the information system project
management includes the management of the project time,
quality and the budget and managing the social quality.
Week 10

Task The development of information systems (IS) has been
actively pursued by organisations in a globalized market to
maintain their competitive advantages However, these
IS/IT implementation project failures often result in
substantial financial losses. Find and summarise ONE
resource that describes ONE example of a failed IT/IS
project in the government sector.
Summary Title and Reference:
Service, S., 2019. Biggest UK Government Project Failures.
[online] Softwareadvisoryservice.com. Available at:
https://www.softwareadvisoryservice.com/blog/biggest-uk-
government-project-failures/
Summary:
In this case the selected article is an online article which
describes about an IT failure project by the UK
Government. The failure of the project occurred in the
Department for Transport Shared Services Centre of UK. In
this project a typical type of IT scheme was designed for
the Department for Transport’s human resources and
financial services. The main aim of this project was saving
the money of the taxpayers but far from this true the whole
project costed around £81 million which was no where from
the estimated costs. This initiated project overrun the
budget of the project due to the management ineptitude
and it has been assessed by the Public Accounts
Committee. The Public Accounts Committee also described
this as a “stupendous incompetence”. The main plan of this
project was cutting the administration expenses by basing
the personal, financial services and the payroll in a single
site of Swansea. In this case the Common Public Accounts
Committee determined that the whole project was done
with a rush and due to that the project is going to make
losses. The management team of the project rushed over
the project to adhere to overly optimistic deadlines and due
to that the project was completed with major defects. This
major defects raised within the project because the
computer systems of the project tested insufficiently, and
this has led to some dubious set up when it was turned on.
The workers of the DLVA were also greeted through the
message generated by the computer systems in German.
After eight months of the final deadline to the project only
two of the total seven agencies were able to use the new
systems and this was a true loss to the project.
actively pursued by organisations in a globalized market to
maintain their competitive advantages However, these
IS/IT implementation project failures often result in
substantial financial losses. Find and summarise ONE
resource that describes ONE example of a failed IT/IS
project in the government sector.
Summary Title and Reference:
Service, S., 2019. Biggest UK Government Project Failures.
[online] Softwareadvisoryservice.com. Available at:
https://www.softwareadvisoryservice.com/blog/biggest-uk-
government-project-failures/
Summary:
In this case the selected article is an online article which
describes about an IT failure project by the UK
Government. The failure of the project occurred in the
Department for Transport Shared Services Centre of UK. In
this project a typical type of IT scheme was designed for
the Department for Transport’s human resources and
financial services. The main aim of this project was saving
the money of the taxpayers but far from this true the whole
project costed around £81 million which was no where from
the estimated costs. This initiated project overrun the
budget of the project due to the management ineptitude
and it has been assessed by the Public Accounts
Committee. The Public Accounts Committee also described
this as a “stupendous incompetence”. The main plan of this
project was cutting the administration expenses by basing
the personal, financial services and the payroll in a single
site of Swansea. In this case the Common Public Accounts
Committee determined that the whole project was done
with a rush and due to that the project is going to make
losses. The management team of the project rushed over
the project to adhere to overly optimistic deadlines and due
to that the project was completed with major defects. This
major defects raised within the project because the
computer systems of the project tested insufficiently, and
this has led to some dubious set up when it was turned on.
The workers of the DLVA were also greeted through the
message generated by the computer systems in German.
After eight months of the final deadline to the project only
two of the total seven agencies were able to use the new
systems and this was a true loss to the project.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




