Network Management Assignment Solution - [Course Code] - [Semester]
VerifiedAdded on 2020/04/13
|8
|1595
|44
Homework Assignment
AI Summary
This document provides a detailed solution to a network management assignment, addressing key concepts and practical scenarios. The solution begins by explaining how a switch learns and stores MAC addresses, followed by a comparison of Layer 2 and Layer 3 switches. It then covers topics such as how a host detects packet loss, considerations for IPv6 transition, subnetting a CIDR block, configuring a FastEthernet router interface, identifying DCE/DTE serial ports, interpreting BPDU data, and the suitability of Layer 2 switches in a campus network core. The assignment concludes with an analysis of the impact of different media types on a 1Gbps data link. The solution includes detailed explanations, configurations, and justifications, along with relevant references and a bibliography. This assignment is designed to test and enhance understanding of core networking principles and practical implementation.

Running head: NETWORK MANAGEMENT
Network Management
[Name of the Student]
[Name of the University]
[Author note]
Network Management
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK MANAGEMENT
1. Explain how a switch learns MAC addresses, and where a switch stores the address.
Ans: Broadcast of frame is never done by a switch neither it is an action which can be taken by a
switch. Flooding of the frame is only possible by the use of a switch. A broadcast is nothing but
a frame which has a destination MAC address that is nnn.nnn.nnn. When a frame is received by a
switch the MAC address table is updated with that of the MAC address and the port where the
frame is received (Tootoonchian et al., 2012). In case if the MAC address at the destination is not
the MAC address at the table, then the frame is flooded to all the ports excluding the port that has
received the frame.
2. How does a layer 3 switch differ from a layer 2 switch?
Ans: The tradition method of switching operates at layer 2 of the OSI model in which the switch
port receives the packets that are generally based on the destination of the MAC address.
Whereas the routing process is operated on the layer 3 switch in which the packets are sent to the
hop IP that present next to it and this is based upon the IP address of the destination (Decusatis,
Carranza & DeCusatis, 2012).
3. Explain how a host knows whether a data packet was not received.
Ans: During the transfer of the packet data from one end to another a dialogue goes on between
the TCP/IP software of the host computer and the receiver computer so as to ensure that the
transfer of files is successful. In cases if the receiver computer dose not receives the whole
packet then the TCP/IP of the receiver sends the message to the TCP/IP of the host asking it to
resend the particular packet that is missing. The receiving of the dialogue continues until the
packets are received by the receiver (Afanasyev et al., 2014).
1. Explain how a switch learns MAC addresses, and where a switch stores the address.
Ans: Broadcast of frame is never done by a switch neither it is an action which can be taken by a
switch. Flooding of the frame is only possible by the use of a switch. A broadcast is nothing but
a frame which has a destination MAC address that is nnn.nnn.nnn. When a frame is received by a
switch the MAC address table is updated with that of the MAC address and the port where the
frame is received (Tootoonchian et al., 2012). In case if the MAC address at the destination is not
the MAC address at the table, then the frame is flooded to all the ports excluding the port that has
received the frame.
2. How does a layer 3 switch differ from a layer 2 switch?
Ans: The tradition method of switching operates at layer 2 of the OSI model in which the switch
port receives the packets that are generally based on the destination of the MAC address.
Whereas the routing process is operated on the layer 3 switch in which the packets are sent to the
hop IP that present next to it and this is based upon the IP address of the destination (Decusatis,
Carranza & DeCusatis, 2012).
3. Explain how a host knows whether a data packet was not received.
Ans: During the transfer of the packet data from one end to another a dialogue goes on between
the TCP/IP software of the host computer and the receiver computer so as to ensure that the
transfer of files is successful. In cases if the receiver computer dose not receives the whole
packet then the TCP/IP of the receiver sends the message to the TCP/IP of the host asking it to
resend the particular packet that is missing. The receiving of the dialogue continues until the
packets are received by the receiver (Afanasyev et al., 2014).

2NETWORK MANAGEMENT
4. Your boss has read about IPv6 and wants to know whether the network you oversee is
ready for the transition. Prepare a response based on the networking and computer
operating systems used in your facility.
Ans: The use of IPv6 will make the elimination of the NAT as the use of IPv6 will make each
device have their own unique IP addresses. All the devices will be able to access the public
network which will help in easy management of the file sharing, peer-to-peer programs and other
applications by avoiding the complex settings in the routers. The security also increases by the
use of IPv6 (Davies, 2012).
5. Your company is assigned a 206.206.155.0/24 CIDR block by your ISP. Your company
consists of 5 different networks.
Network A: 50 users
Network B: 26 users
Network C: 12 users
Network D: 10 users
Your job is to create four subnets and allocate enough IP addresses for the users within the
network. Document how you will do this.
Ans:
4. Your boss has read about IPv6 and wants to know whether the network you oversee is
ready for the transition. Prepare a response based on the networking and computer
operating systems used in your facility.
Ans: The use of IPv6 will make the elimination of the NAT as the use of IPv6 will make each
device have their own unique IP addresses. All the devices will be able to access the public
network which will help in easy management of the file sharing, peer-to-peer programs and other
applications by avoiding the complex settings in the routers. The security also increases by the
use of IPv6 (Davies, 2012).
5. Your company is assigned a 206.206.155.0/24 CIDR block by your ISP. Your company
consists of 5 different networks.
Network A: 50 users
Network B: 26 users
Network C: 12 users
Network D: 10 users
Your job is to create four subnets and allocate enough IP addresses for the users within the
network. Document how you will do this.
Ans:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
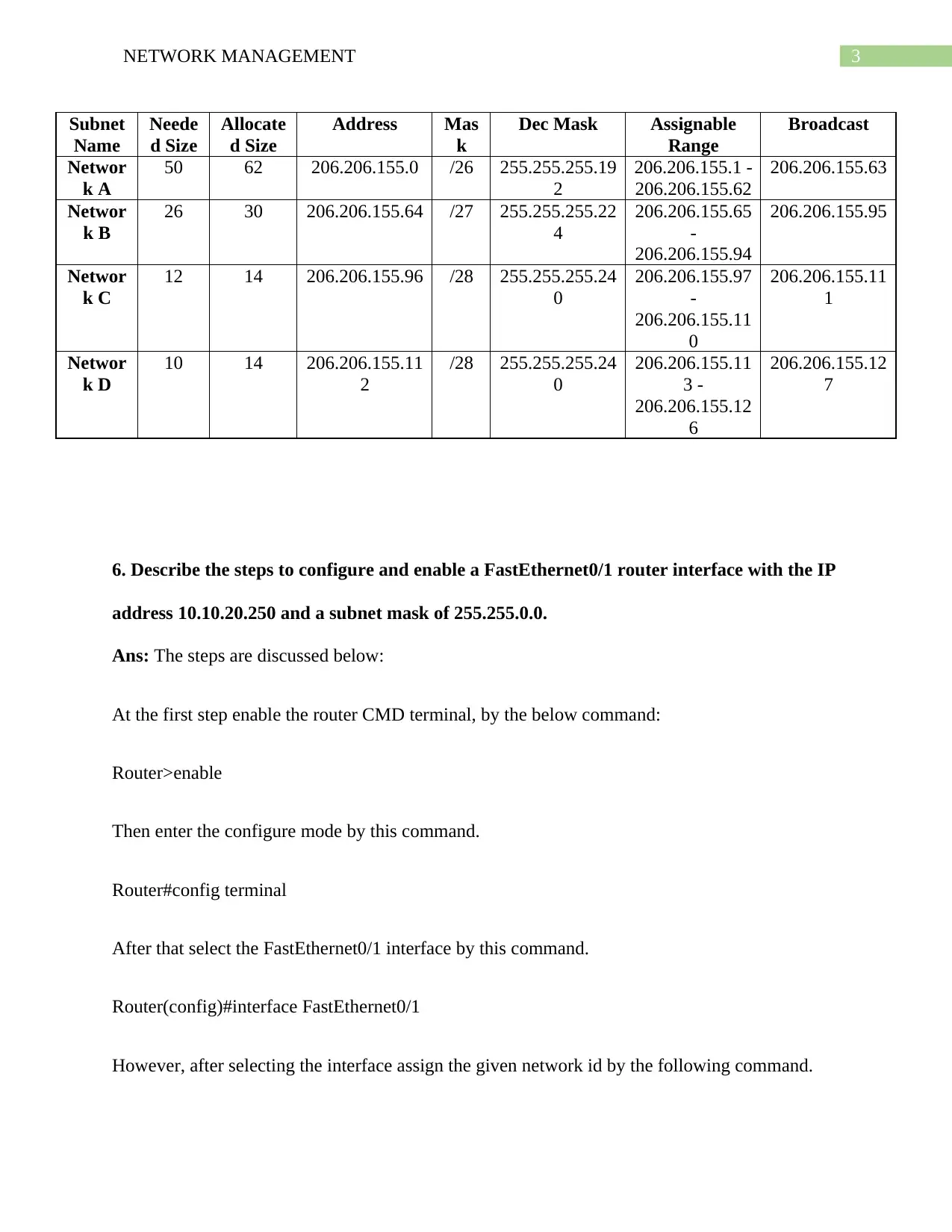
3NETWORK MANAGEMENT
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Networ
k A
50 62 206.206.155.0 /26 255.255.255.19
2
206.206.155.1 -
206.206.155.62
206.206.155.63
Networ
k B
26 30 206.206.155.64 /27 255.255.255.22
4
206.206.155.65
-
206.206.155.94
206.206.155.95
Networ
k C
12 14 206.206.155.96 /28 255.255.255.24
0
206.206.155.97
-
206.206.155.11
0
206.206.155.11
1
Networ
k D
10 14 206.206.155.11
2
/28 255.255.255.24
0
206.206.155.11
3 -
206.206.155.12
6
206.206.155.12
7
6. Describe the steps to configure and enable a FastEthernet0/1 router interface with the IP
address 10.10.20.250 and a subnet mask of 255.255.0.0.
Ans: The steps are discussed below:
At the first step enable the router CMD terminal, by the below command:
Router>enable
Then enter the configure mode by this command.
Router#config terminal
After that select the FastEthernet0/1 interface by this command.
Router(config)#interface FastEthernet0/1
However, after selecting the interface assign the given network id by the following command.
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Networ
k A
50 62 206.206.155.0 /26 255.255.255.19
2
206.206.155.1 -
206.206.155.62
206.206.155.63
Networ
k B
26 30 206.206.155.64 /27 255.255.255.22
4
206.206.155.65
-
206.206.155.94
206.206.155.95
Networ
k C
12 14 206.206.155.96 /28 255.255.255.24
0
206.206.155.97
-
206.206.155.11
0
206.206.155.11
1
Networ
k D
10 14 206.206.155.11
2
/28 255.255.255.24
0
206.206.155.11
3 -
206.206.155.12
6
206.206.155.12
7
6. Describe the steps to configure and enable a FastEthernet0/1 router interface with the IP
address 10.10.20.250 and a subnet mask of 255.255.0.0.
Ans: The steps are discussed below:
At the first step enable the router CMD terminal, by the below command:
Router>enable
Then enter the configure mode by this command.
Router#config terminal
After that select the FastEthernet0/1 interface by this command.
Router(config)#interface FastEthernet0/1
However, after selecting the interface assign the given network id by the following command.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK MANAGEMENT
Router(config-if)#ip address 10.10.20.250 255.255.0.0
Then exit the configure mode using the following command.
Router(config-if)#exit
Then exit the configure mode.
Router(config)#exit
7. What are the three ways to see if your router’s serial port is a DCE or DTE end?
Ans: The most important way of finding the difference is that DCE supplies the clock signal
which helps in pacing up of the communication in the bus. The instructions provided in the
device also helps in determining whether it is a DTE or DCE. The device can also be identified
by looking into the connecter of the device. The DTE has a male connector that is the pins
protrude from the base of the connecter whereas the DCE has a female connector that is the
connector has holes so as receive the pins. The devices like the terminals, data service
unit/channel service unit (DSU/CSU) and the devices included in the DCE are modems (Yankov
& Ilieva, 2015).
8. A BPDU data packet lists the “Forward Delay” as 15 seconds. What information does
this provide?
Ans: The 15seconds time listed as Forward delay in the BPDU data packet is the time which is
spent for the purpose of listening and learning the states. This means that a change will occur in
the active STP topology making the port move from blocking to forwarding stage (Marchese &
Mongelli, 2012).
Router(config-if)#ip address 10.10.20.250 255.255.0.0
Then exit the configure mode using the following command.
Router(config-if)#exit
Then exit the configure mode.
Router(config)#exit
7. What are the three ways to see if your router’s serial port is a DCE or DTE end?
Ans: The most important way of finding the difference is that DCE supplies the clock signal
which helps in pacing up of the communication in the bus. The instructions provided in the
device also helps in determining whether it is a DTE or DCE. The device can also be identified
by looking into the connecter of the device. The DTE has a male connector that is the pins
protrude from the base of the connecter whereas the DCE has a female connector that is the
connector has holes so as receive the pins. The devices like the terminals, data service
unit/channel service unit (DSU/CSU) and the devices included in the DCE are modems (Yankov
& Ilieva, 2015).
8. A BPDU data packet lists the “Forward Delay” as 15 seconds. What information does
this provide?
Ans: The 15seconds time listed as Forward delay in the BPDU data packet is the time which is
spent for the purpose of listening and learning the states. This means that a change will occur in
the active STP topology making the port move from blocking to forwarding stage (Marchese &
Mongelli, 2012).

5NETWORK MANAGEMENT
9. Your supervisor asks you if a layer 2 switch could be used in the core of the campus
network. Prepare a response to your supervisor. Be sure to justify your recommendation.
Ans: The use of layer 2 switch will terminate the VLANs at the layer of distribution making the
access layer switches to run in the form of pure bridges. Due the limitations in the spanning tree
most of the uplinks or half of the uplinks will be blocked unless and until aggregation is done for
them with a multi-chassis link aggregation (Decusatis, Carranza & DeCusatis, 2012). The layer 2
switch just requires VSS on Cat6500 which makes it a major showstopper along due to the fact
of requirement for multiple security zones.
10. A 1Gbps data link is to be set up between building A and building B in a campus
network. Does it matter if the link is fibre or microwave or some other media? Explain
your answer.
Ans: The speed in fibre is much slower in the fibre as the speed in the fibre depends on the
distance between the buildings whereas the distance dose not plays any role in the transmission
of data between the two ends (Jung & Kim, 2015).
9. Your supervisor asks you if a layer 2 switch could be used in the core of the campus
network. Prepare a response to your supervisor. Be sure to justify your recommendation.
Ans: The use of layer 2 switch will terminate the VLANs at the layer of distribution making the
access layer switches to run in the form of pure bridges. Due the limitations in the spanning tree
most of the uplinks or half of the uplinks will be blocked unless and until aggregation is done for
them with a multi-chassis link aggregation (Decusatis, Carranza & DeCusatis, 2012). The layer 2
switch just requires VSS on Cat6500 which makes it a major showstopper along due to the fact
of requirement for multiple security zones.
10. A 1Gbps data link is to be set up between building A and building B in a campus
network. Does it matter if the link is fibre or microwave or some other media? Explain
your answer.
Ans: The speed in fibre is much slower in the fibre as the speed in the fibre depends on the
distance between the buildings whereas the distance dose not plays any role in the transmission
of data between the two ends (Jung & Kim, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK MANAGEMENT
References:
Afanasyev, A., Burke, J., Zhang, L., Claffy, K., Wang, L., Jacobson, V., ... & Zhang, B. (2014).
Named data networking. ACM SIGCOMM Computer Communication Review, 44(3), 66-
73.
Davies, J. (2012). Understanding ipv6. Pearson Education.
Decusatis, C. J. S., Carranza, A., & DeCusatis, C. M. (2012). Communication within clouds:
open standards and proprietary protocols for data center networking. IEEE
Communications Magazine, 50(9).
Decusatis, C. J. S., Carranza, A., & DeCusatis, C. M. (2012). Communication within clouds:
open standards and proprietary protocols for data center networking. IEEE
Communications Magazine, 50(9).
Jung, K., & Kim, J. (2015). All-fibre photonic signal generator for attosecond timing and
ultralow-noise microwave. Scientific reports, 5, 16250.
Marchese, M., & Mongelli, M. (2012). Simple protocol enhancements of Rapid Spanning Tree
Protocol over ring topologies. Computer Networks, 56(4), 1131-1151.
Tootoonchian, A., Gorbunov, S., Ganjali, Y., Casado, M., & Sherwood, R. (2012). On Controller
Performance in Software-Defined Networks. Hot-ICE, 12, 1-6.
Yankov, K., & Ilieva, D. (2015). User Interface for Analysis of Experimental Data. Trakia
Journal of Sciences, 13(1), 420-425.
References:
Afanasyev, A., Burke, J., Zhang, L., Claffy, K., Wang, L., Jacobson, V., ... & Zhang, B. (2014).
Named data networking. ACM SIGCOMM Computer Communication Review, 44(3), 66-
73.
Davies, J. (2012). Understanding ipv6. Pearson Education.
Decusatis, C. J. S., Carranza, A., & DeCusatis, C. M. (2012). Communication within clouds:
open standards and proprietary protocols for data center networking. IEEE
Communications Magazine, 50(9).
Decusatis, C. J. S., Carranza, A., & DeCusatis, C. M. (2012). Communication within clouds:
open standards and proprietary protocols for data center networking. IEEE
Communications Magazine, 50(9).
Jung, K., & Kim, J. (2015). All-fibre photonic signal generator for attosecond timing and
ultralow-noise microwave. Scientific reports, 5, 16250.
Marchese, M., & Mongelli, M. (2012). Simple protocol enhancements of Rapid Spanning Tree
Protocol over ring topologies. Computer Networks, 56(4), 1131-1151.
Tootoonchian, A., Gorbunov, S., Ganjali, Y., Casado, M., & Sherwood, R. (2012). On Controller
Performance in Software-Defined Networks. Hot-ICE, 12, 1-6.
Yankov, K., & Ilieva, D. (2015). User Interface for Analysis of Experimental Data. Trakia
Journal of Sciences, 13(1), 420-425.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK MANAGEMENT
Bibliography:
Domzal, J., Dudek, J., Jurkiewicz, P., & Wójcik, R. (2014). The cross-protect router:
implementation tests and opportunities. IEEE Communications Magazine, 52(9), 115-
123.
Sampigethaya, K. (2015, April). Software-defined networking in aviation: Opportunities and
challenges. In Integrated Communication, Navigation, and Surveillance Conference
(ICNS), 2015 (pp. 1-21). IEEE.
Bibliography:
Domzal, J., Dudek, J., Jurkiewicz, P., & Wójcik, R. (2014). The cross-protect router:
implementation tests and opportunities. IEEE Communications Magazine, 52(9), 115-
123.
Sampigethaya, K. (2015, April). Software-defined networking in aviation: Opportunities and
challenges. In Integrated Communication, Navigation, and Surveillance Conference
(ICNS), 2015 (pp. 1-21). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





