Networking Assignment: Analysis of Fundamentals (Weeks 1-9)
VerifiedAdded on 2023/01/19
|14
|3329
|65
Homework Assignment
AI Summary
This assignment addresses various aspects of networking fundamentals, covering topics from multiprogramming and multitasking to network topologies, including star topology and the choice of network cables like UTP and fiber optic. It explores the OSI model layers, IPv6 advantages, and the role of firewalls. Additionally, the assignment delves into switching tables, cloud computing concepts, and the differences between viruses and worms, providing a comprehensive overview of key networking concepts. The assignment includes detailed answers to questions about network protocols, security, and the practical implications of different network technologies and configurations. It also provides a clear understanding of how these concepts relate to real-world scenarios and challenges in network design and management.

ASSIGNMENT SUBMISSION
Due date: Friday Week 11 (11:45 PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
While it should not be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using the
Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
ASSESSMENT On Fundamentals of Networking - PAGE 1
Due date: Friday Week 11 (11:45 PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
While it should not be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using the
Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
ASSESSMENT On Fundamentals of Networking - PAGE 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week One
Assignment Question:
It is common to be running several programs at once on your PC or laptop, for
example, listening to music while you are browsing webs. How is this possible?
Describe two ways that your PC or laptop can do, or appear to do, two or more things
at once.
Your answer:
Multiprogramming is the method of running multiple programs at any given
time. In multiprogramming systems, a number of programs get loaded into main
memory when batch processing is done (Lamichhane, Moreno and Fischmeister
2018). The first program starts to run and when it gets instructions to wait for
peripheral devices, the second program is given the chance to run. This process
follows for the n number of programs.
In multitasking, programs do not necessarily run for their entire duration unless
they are too short or poorly designed. The common resource shared by multiple
applications is shared among each other periodically. Thus it becomes possible to
browse the web and listen to music at the same time.
Your question:
How do programs accessing the same resource run concurrently in multitasking?
Your sample answer:
Every program is assigned a CPU time slice to ensure that all programs in the
queue get to run. A time slice is access to CPU for limited time. When this time slice
expires, the current program is suspended and the next program in the queue gets
CPU time.
ASSESSMENT On Fundamentals of Networking - PAGE 2
Assignment Question:
It is common to be running several programs at once on your PC or laptop, for
example, listening to music while you are browsing webs. How is this possible?
Describe two ways that your PC or laptop can do, or appear to do, two or more things
at once.
Your answer:
Multiprogramming is the method of running multiple programs at any given
time. In multiprogramming systems, a number of programs get loaded into main
memory when batch processing is done (Lamichhane, Moreno and Fischmeister
2018). The first program starts to run and when it gets instructions to wait for
peripheral devices, the second program is given the chance to run. This process
follows for the n number of programs.
In multitasking, programs do not necessarily run for their entire duration unless
they are too short or poorly designed. The common resource shared by multiple
applications is shared among each other periodically. Thus it becomes possible to
browse the web and listen to music at the same time.
Your question:
How do programs accessing the same resource run concurrently in multitasking?
Your sample answer:
Every program is assigned a CPU time slice to ensure that all programs in the
queue get to run. A time slice is access to CPU for limited time. When this time slice
expires, the current program is suspended and the next program in the queue gets
CPU time.
ASSESSMENT On Fundamentals of Networking - PAGE 2

Week Two
Assignment Question:
The company Things-Connected has 8 workstations in a wired LAN with a 100 Mbps
switch. It was suggested to the admin officer to replace the switch with a wireless
Access Point (AP) that uses the 802.11ac standard and operates at 1 Gbps.
Assuming all workstations were simultaneously using the LAN, would the AP deliver
faster or slower speeds to the users? Explain your reasoning by including estimates
of effective bandwidth for each case.
Your answer:
In the case of replacing a switch with wireless access points that use ac
standard. The DHCP protocol needs to be configured in wireless access points.
The 8 workstations of the LAN network, now WLAN network should have DHCP
configuration enabled (Qin and WANG 2017). When the 8 workstations were
connected directly by wires from the switch, the network connection would be shared.
The same situation occurs when these workstations are connected through wireless
networks. However when directly connected through Ethernet wires, the latency of
the connection is usually low facilitating smoother internet access. In wireless
connections, the signal strength varies upon the distance between the workstation
and the access point as well as thee obstacles in between and hence internet access
can get choppy.
Your question:
Is wireless network access ideal for workstations in offie premises?
Your sample answer:
Wireless network (WLAN) connections is not ideal for workstations since these
are not portable devices and are supposed to occupy fixed spaces and hence fixed
wired connections are more appropriate for these systems. Wireless becomes rather
useful for laptops, MacBook, VoIP and other portable devices.
ASSESSMENT On Fundamentals of Networking - PAGE 3
Assignment Question:
The company Things-Connected has 8 workstations in a wired LAN with a 100 Mbps
switch. It was suggested to the admin officer to replace the switch with a wireless
Access Point (AP) that uses the 802.11ac standard and operates at 1 Gbps.
Assuming all workstations were simultaneously using the LAN, would the AP deliver
faster or slower speeds to the users? Explain your reasoning by including estimates
of effective bandwidth for each case.
Your answer:
In the case of replacing a switch with wireless access points that use ac
standard. The DHCP protocol needs to be configured in wireless access points.
The 8 workstations of the LAN network, now WLAN network should have DHCP
configuration enabled (Qin and WANG 2017). When the 8 workstations were
connected directly by wires from the switch, the network connection would be shared.
The same situation occurs when these workstations are connected through wireless
networks. However when directly connected through Ethernet wires, the latency of
the connection is usually low facilitating smoother internet access. In wireless
connections, the signal strength varies upon the distance between the workstation
and the access point as well as thee obstacles in between and hence internet access
can get choppy.
Your question:
Is wireless network access ideal for workstations in offie premises?
Your sample answer:
Wireless network (WLAN) connections is not ideal for workstations since these
are not portable devices and are supposed to occupy fixed spaces and hence fixed
wired connections are more appropriate for these systems. Wireless becomes rather
useful for laptops, MacBook, VoIP and other portable devices.
ASSESSMENT On Fundamentals of Networking - PAGE 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week Three
Assignment Question:
Describe the difference between a network’s physical topology and its logical
topology; explain the advantages and disadvantages of a physical star topology.
Your answer:
Logical topology of networks concerns with showing how users are connected
to the network and how they utilize the services (Quinn, Elzur and Pignataro 2018).
In contrast Physical topology deals with elaborating the physical positioning and
arrangements of network components as well as the cables, wires used and their
specifications.
Advantages of Physical Star Topology
1. Computers and peripheral devices can be easily installed and wired.
2. Connecting or removing devices do not cause any disruptions.
3. Faults in the network are easily detectable.
Disadvantages
1. More cabling required compared to linear bus.
2. Failure in the hub results in disconnection of all connected nodes.
3. Costlier than the bus topology.
Your question:
Why are more cables required in bus topology? Is this the only reason for higher
costs?
Your sample answer:
Star topology requires more cabling since every device is individually connected to
the hub or switch with different cables. Apart from the cables cost of installing the
hubs, switches or connectors significantly increase of implementing star topology.
ASSESSMENT On Fundamentals of Networking - PAGE 4
Assignment Question:
Describe the difference between a network’s physical topology and its logical
topology; explain the advantages and disadvantages of a physical star topology.
Your answer:
Logical topology of networks concerns with showing how users are connected
to the network and how they utilize the services (Quinn, Elzur and Pignataro 2018).
In contrast Physical topology deals with elaborating the physical positioning and
arrangements of network components as well as the cables, wires used and their
specifications.
Advantages of Physical Star Topology
1. Computers and peripheral devices can be easily installed and wired.
2. Connecting or removing devices do not cause any disruptions.
3. Faults in the network are easily detectable.
Disadvantages
1. More cabling required compared to linear bus.
2. Failure in the hub results in disconnection of all connected nodes.
3. Costlier than the bus topology.
Your question:
Why are more cables required in bus topology? Is this the only reason for higher
costs?
Your sample answer:
Star topology requires more cabling since every device is individually connected to
the hub or switch with different cables. Apart from the cables cost of installing the
hubs, switches or connectors significantly increase of implementing star topology.
ASSESSMENT On Fundamentals of Networking - PAGE 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week Four
Assignment Question:
Things-Connected facilities in West end, Queensland (Townsville), are two office
buildings 180 meters apart, each with its own LAN. To connect the two networks, the
budget-conscious facilities manager suggests using Category 6 of Unshielded
Twisted-Pair Cable.
Is this a suitable advice?
Give two other media connectivity options, outline their advantages and
disadvantages
Your answer:
The maximum allowed length for a Category 6 Unshielded Twisted Pair (UTP)
Cable is 100 meters including 10 meters of stranded cabling near the jack and
attached device (Tuenge, Kelly and Poplawski 2017). Therefore, maximum range is
90 meters.
Two office buildings of Things-Connected are 180 meters which is twice the
coverage of UTP and hence more suitable cable or transmission media is required
otherwise the network performance will suffer massively.
An alternative to Category 6 UTP and STP cables can be fibre optic cables
which can provide a network bandwidth of 1GB/s up to a range of 550 meters (Hecht
2016). However, these cables are costly to acquire. A cheaper alternative can be
10base5 coaxial cable. Since no additional connections are required between the two
buildings, the coaxial cable is both suitable and cheap despite not being as flexible
as fibre optic cables.
Your question:
What is the primary advantage to be gained by opting for fibre optic cables instead of
10base5 coaxial cable?
Your sample answer:
10base5 stands for 10 Mbps 500meters meaning it can only deliver maximum of 10
Mbps speeds up to 500 meters. In comparison fibre optic cables can deliver speeds
up to 1 GB/s.
ASSESSMENT On Fundamentals of Networking - PAGE 5
Assignment Question:
Things-Connected facilities in West end, Queensland (Townsville), are two office
buildings 180 meters apart, each with its own LAN. To connect the two networks, the
budget-conscious facilities manager suggests using Category 6 of Unshielded
Twisted-Pair Cable.
Is this a suitable advice?
Give two other media connectivity options, outline their advantages and
disadvantages
Your answer:
The maximum allowed length for a Category 6 Unshielded Twisted Pair (UTP)
Cable is 100 meters including 10 meters of stranded cabling near the jack and
attached device (Tuenge, Kelly and Poplawski 2017). Therefore, maximum range is
90 meters.
Two office buildings of Things-Connected are 180 meters which is twice the
coverage of UTP and hence more suitable cable or transmission media is required
otherwise the network performance will suffer massively.
An alternative to Category 6 UTP and STP cables can be fibre optic cables
which can provide a network bandwidth of 1GB/s up to a range of 550 meters (Hecht
2016). However, these cables are costly to acquire. A cheaper alternative can be
10base5 coaxial cable. Since no additional connections are required between the two
buildings, the coaxial cable is both suitable and cheap despite not being as flexible
as fibre optic cables.
Your question:
What is the primary advantage to be gained by opting for fibre optic cables instead of
10base5 coaxial cable?
Your sample answer:
10base5 stands for 10 Mbps 500meters meaning it can only deliver maximum of 10
Mbps speeds up to 500 meters. In comparison fibre optic cables can deliver speeds
up to 1 GB/s.
ASSESSMENT On Fundamentals of Networking - PAGE 5
Week Five
Assignment Question:
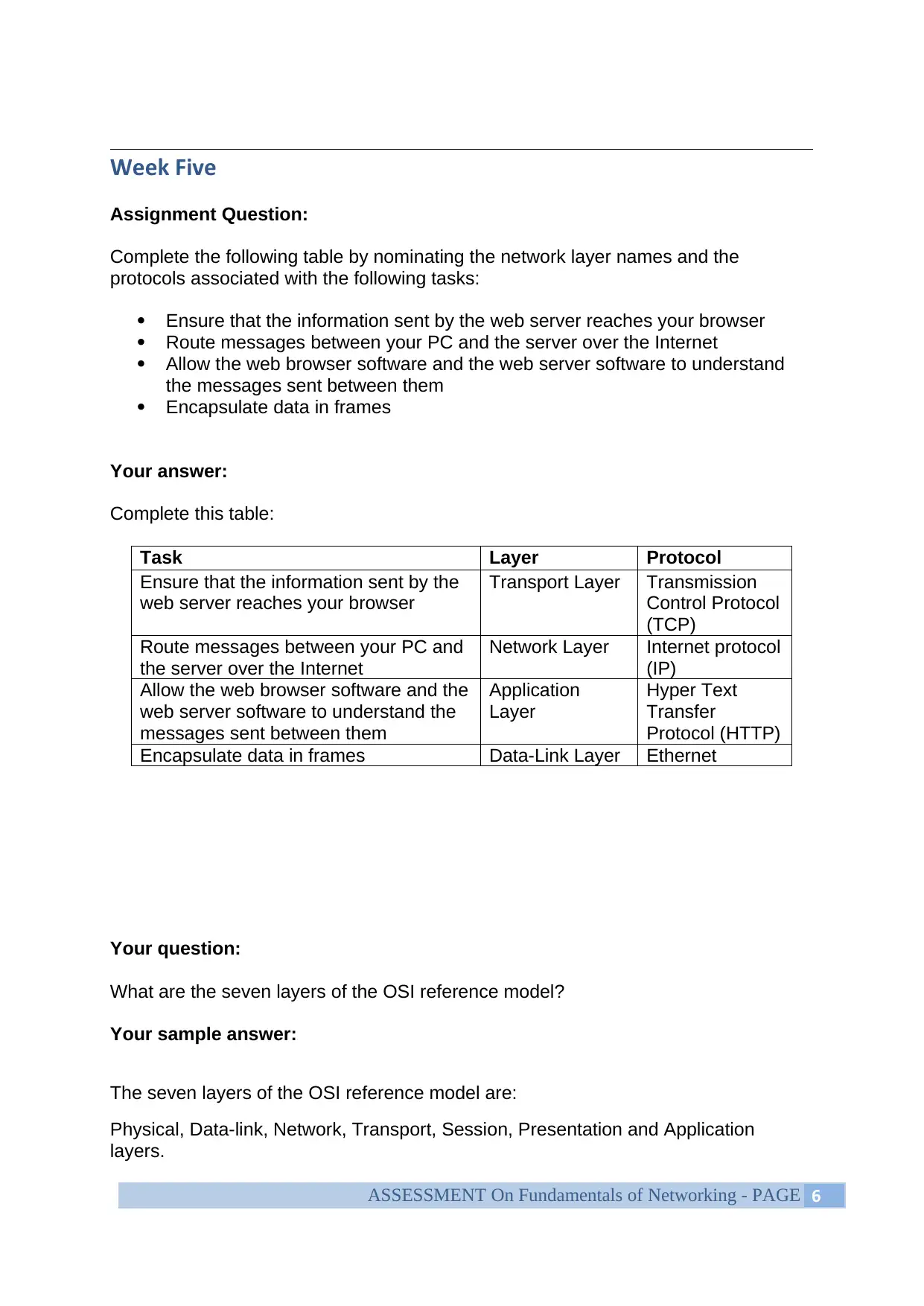
Complete the following table by nominating the network layer names and the
protocols associated with the following tasks:
Ensure that the information sent by the web server reaches your browser
Route messages between your PC and the server over the Internet
Allow the web browser software and the web server software to understand
the messages sent between them
Encapsulate data in frames
Your answer:
Complete this table:
Task Layer Protocol
Ensure that the information sent by the
web server reaches your browser
Transport Layer Transmission
Control Protocol
(TCP)
Route messages between your PC and
the server over the Internet
Network Layer Internet protocol
(IP)
Allow the web browser software and the
web server software to understand the
messages sent between them
Application
Layer
Hyper Text
Transfer
Protocol (HTTP)
Encapsulate data in frames Data-Link Layer Ethernet
Your question:
What are the seven layers of the OSI reference model?
Your sample answer:
The seven layers of the OSI reference model are:
Physical, Data-link, Network, Transport, Session, Presentation and Application
layers.
ASSESSMENT On Fundamentals of Networking - PAGE 6
Assignment Question:
Complete the following table by nominating the network layer names and the
protocols associated with the following tasks:
Ensure that the information sent by the web server reaches your browser
Route messages between your PC and the server over the Internet
Allow the web browser software and the web server software to understand
the messages sent between them
Encapsulate data in frames
Your answer:
Complete this table:
Task Layer Protocol
Ensure that the information sent by the
web server reaches your browser
Transport Layer Transmission
Control Protocol
(TCP)
Route messages between your PC and
the server over the Internet
Network Layer Internet protocol
(IP)
Allow the web browser software and the
web server software to understand the
messages sent between them
Application
Layer
Hyper Text
Transfer
Protocol (HTTP)
Encapsulate data in frames Data-Link Layer Ethernet
Your question:
What are the seven layers of the OSI reference model?
Your sample answer:
The seven layers of the OSI reference model are:
Physical, Data-link, Network, Transport, Session, Presentation and Application
layers.
ASSESSMENT On Fundamentals of Networking - PAGE 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week Six
Assignment Question:
Internet Protocol version 6 (IPv6), the most recent version of the Internet Protocol
(IP), is the communications protocol that provides an identification and location
system for computers on networks and routes traffic across the Internet. As of 31
December 2017, the percentage of users reaching Google services with IPv6
reached 22.6% for the first time in regular measurements, growing at about 5.8% per
year, although varying widely by region. As of December 2017, about 33% of Alexa
Top 500 web servers support IPv6.
List 3 advantages of IPv6 and briefly comment on how IPv6 improves or enhances
security. Explain how it is that IPv4 and IPv6 can co-exist in the same network.
Your answer:
Three advantages of IPv6 are:
1. Efficient hierarchical routing through reduction of routing table sizes. Here the
source device is responsible for fragmentation instead of the router.
2. Better compatibility for newer services like VoIP and QoS. Here the Network
Address Translation or NAT is eliminated restoring end to end connectivity in
IP layer thus peer to peer connections are easier to implement.
3. Simplified networking from Address auto configuration which is an inbuilt
feature in IPv6. Here the hosts are able to generate their own IPs by adding
their link layer MAC address.
Another built in feature of IPv6 is IPSec (Amutha, Rabara and Sundaram 2016).
IPSec provides authentication, data integrity and confidentiality thus making IPv6 far
secure compared to IPv4 ICMP packets which can get easily affected by malwares.
Your question:
How are data flows conducted by IPv6? How it differs from IPv4?
Your sample answer:
Compared to broadcast dataflows of IPv4, IPv6 does multicast. In this method the
high bandwidth intensive packets are sent to multiple destinations at the same time
thus the bandwidth of the network is saved from getting choked.
ASSESSMENT On Fundamentals of Networking - PAGE 7
Assignment Question:
Internet Protocol version 6 (IPv6), the most recent version of the Internet Protocol
(IP), is the communications protocol that provides an identification and location
system for computers on networks and routes traffic across the Internet. As of 31
December 2017, the percentage of users reaching Google services with IPv6
reached 22.6% for the first time in regular measurements, growing at about 5.8% per
year, although varying widely by region. As of December 2017, about 33% of Alexa
Top 500 web servers support IPv6.
List 3 advantages of IPv6 and briefly comment on how IPv6 improves or enhances
security. Explain how it is that IPv4 and IPv6 can co-exist in the same network.
Your answer:
Three advantages of IPv6 are:
1. Efficient hierarchical routing through reduction of routing table sizes. Here the
source device is responsible for fragmentation instead of the router.
2. Better compatibility for newer services like VoIP and QoS. Here the Network
Address Translation or NAT is eliminated restoring end to end connectivity in
IP layer thus peer to peer connections are easier to implement.
3. Simplified networking from Address auto configuration which is an inbuilt
feature in IPv6. Here the hosts are able to generate their own IPs by adding
their link layer MAC address.
Another built in feature of IPv6 is IPSec (Amutha, Rabara and Sundaram 2016).
IPSec provides authentication, data integrity and confidentiality thus making IPv6 far
secure compared to IPv4 ICMP packets which can get easily affected by malwares.
Your question:
How are data flows conducted by IPv6? How it differs from IPv4?
Your sample answer:
Compared to broadcast dataflows of IPv4, IPv6 does multicast. In this method the
high bandwidth intensive packets are sent to multiple destinations at the same time
thus the bandwidth of the network is saved from getting choked.
ASSESSMENT On Fundamentals of Networking - PAGE 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Week Seven
Assignment Question:
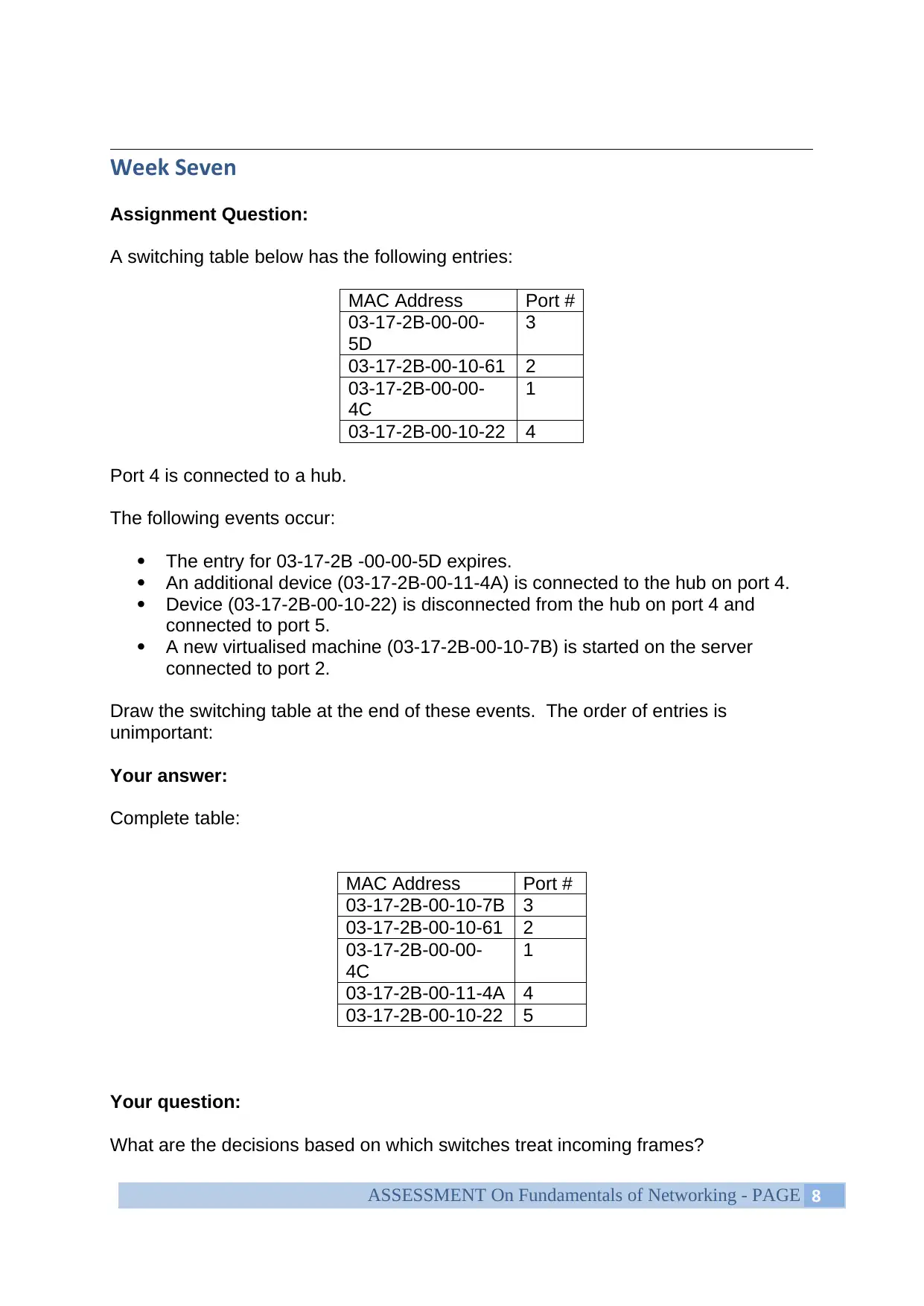
A switching table below has the following entries:
MAC Address Port #
03-17-2B-00-00-
5D
3
03-17-2B-00-10-61 2
03-17-2B-00-00-
4C
1
03-17-2B-00-10-22 4
Port 4 is connected to a hub.
The following events occur:
The entry for 03-17-2B -00-00-5D expires.
An additional device (03-17-2B-00-11-4A) is connected to the hub on port 4.
Device (03-17-2B-00-10-22) is disconnected from the hub on port 4 and
connected to port 5.
A new virtualised machine (03-17-2B-00-10-7B) is started on the server
connected to port 2.
Draw the switching table at the end of these events. The order of entries is
unimportant:
Your answer:
Complete table:
MAC Address Port #
03-17-2B-00-10-7B 3
03-17-2B-00-10-61 2
03-17-2B-00-00-
4C
1
03-17-2B-00-11-4A 4
03-17-2B-00-10-22 5
Your question:
What are the decisions based on which switches treat incoming frames?
ASSESSMENT On Fundamentals of Networking - PAGE 8
Assignment Question:
A switching table below has the following entries:
MAC Address Port #
03-17-2B-00-00-
5D
3
03-17-2B-00-10-61 2
03-17-2B-00-00-
4C
1
03-17-2B-00-10-22 4
Port 4 is connected to a hub.
The following events occur:
The entry for 03-17-2B -00-00-5D expires.
An additional device (03-17-2B-00-11-4A) is connected to the hub on port 4.
Device (03-17-2B-00-10-22) is disconnected from the hub on port 4 and
connected to port 5.
A new virtualised machine (03-17-2B-00-10-7B) is started on the server
connected to port 2.
Draw the switching table at the end of these events. The order of entries is
unimportant:
Your answer:
Complete table:
MAC Address Port #
03-17-2B-00-10-7B 3
03-17-2B-00-10-61 2
03-17-2B-00-00-
4C
1
03-17-2B-00-11-4A 4
03-17-2B-00-10-22 5
Your question:
What are the decisions based on which switches treat incoming frames?
ASSESSMENT On Fundamentals of Networking - PAGE 8

Your sample answer:
The decisions based on which switches treat incoming frames are forwarding,
flooding and filtering (Li 2017).
ASSESSMENT On Fundamentals of Networking - PAGE 9
The decisions based on which switches treat incoming frames are forwarding,
flooding and filtering (Li 2017).
ASSESSMENT On Fundamentals of Networking - PAGE 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week Eight
Assignment Question:
Firewalls can be effective against worms but are generally of no use against viruses.
Why is this?
Your answer:
A firewall concerns with filtering of packets (Kokko 2017). They monitor the
traffic of the network along with the attempts to connect to or outside the network and
based on the rules and policies configured decides if the attempts will be allowed or
not.
Viruses are programs that aims to compromise computers by means of
executing malicious codes or by exploiting vulnerabilities and can cause denial of
service (Chen 2016). Generally, these inputs from the system users are required for
an infection to occur such as downloading infected files. This way viruses can
override the firewall of the particular system.
Your question:
Can firewalls protect against Denial of Service (DoS) Attacks?
Your sample answer:
There exists many forms of Denial of Service (DoS) attacks. Some can target the
network of the system through the DNS while other DoS attacks can also target
system resources. Firewalls generally provide adequate protection from all
DoS attacks except protocol attack which drains firewall resources.
ASSESSMENT On Fundamentals of Networking - PAGE 10
Assignment Question:
Firewalls can be effective against worms but are generally of no use against viruses.
Why is this?
Your answer:
A firewall concerns with filtering of packets (Kokko 2017). They monitor the
traffic of the network along with the attempts to connect to or outside the network and
based on the rules and policies configured decides if the attempts will be allowed or
not.
Viruses are programs that aims to compromise computers by means of
executing malicious codes or by exploiting vulnerabilities and can cause denial of
service (Chen 2016). Generally, these inputs from the system users are required for
an infection to occur such as downloading infected files. This way viruses can
override the firewall of the particular system.
Your question:
Can firewalls protect against Denial of Service (DoS) Attacks?
Your sample answer:
There exists many forms of Denial of Service (DoS) attacks. Some can target the
network of the system through the DNS while other DoS attacks can also target
system resources. Firewalls generally provide adequate protection from all
DoS attacks except protocol attack which drains firewall resources.
ASSESSMENT On Fundamentals of Networking - PAGE 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week Nine
Assignment Question:
Cloud computing is an information technology (IT) paradigm that enables ubiquitous
access to shared pools of configurable system resources and higher-level services
that can be rapidly provisioned with minimal management effort, often over the
Internet. Cloud computing relies on sharing of resources to achieve coherence and
economies of scale, similar to a public utility.
Cloud-computing providers offer their services according to different models. Explain
the three basic service models including one example for each.
Your answer:
The three basic service models of cloud computing are:
IaaS (Infrastructure-as-a-Service): Here consumers are not required to operate or
manage the infrastructure components of that cloud service and yet gets control of
storage space, operating system, applications as also partial control over the network
resources. A popular example can be Amazon Web Services or AWS.
PaaS (Platform-as-a-Service): In this model consumers never get to operate or
manage the infrastructure components of that cloud service but gets control of
applications and respective configurations regarding hosting of the application and
associated environment. A popular example can be Microsoft Azure.
SaaS (Software-as-a-Service): Here The consumers do not have to operate or
manage infrastructure components of that cloud service although can control
configuration of applications for particular users. A popular example can be Dropbox.
Your question:
What are the main differences between IaaS, PaaS and SaaS?
Your sample answer:
The primary difference between the three basic service models (IaaS, PaaS and
SaaS) are that through IaaS almost all cloud-based services are obtained (Gonzales
et al. 2017). With PaaS, hardware as well as software-based resources can be
accessible. From SaaS, only third-party software resources are accessible.
ASSESSMENT On Fundamentals of Networking - PAGE 11
Assignment Question:
Cloud computing is an information technology (IT) paradigm that enables ubiquitous
access to shared pools of configurable system resources and higher-level services
that can be rapidly provisioned with minimal management effort, often over the
Internet. Cloud computing relies on sharing of resources to achieve coherence and
economies of scale, similar to a public utility.
Cloud-computing providers offer their services according to different models. Explain
the three basic service models including one example for each.
Your answer:
The three basic service models of cloud computing are:
IaaS (Infrastructure-as-a-Service): Here consumers are not required to operate or
manage the infrastructure components of that cloud service and yet gets control of
storage space, operating system, applications as also partial control over the network
resources. A popular example can be Amazon Web Services or AWS.
PaaS (Platform-as-a-Service): In this model consumers never get to operate or
manage the infrastructure components of that cloud service but gets control of
applications and respective configurations regarding hosting of the application and
associated environment. A popular example can be Microsoft Azure.
SaaS (Software-as-a-Service): Here The consumers do not have to operate or
manage infrastructure components of that cloud service although can control
configuration of applications for particular users. A popular example can be Dropbox.
Your question:
What are the main differences between IaaS, PaaS and SaaS?
Your sample answer:
The primary difference between the three basic service models (IaaS, PaaS and
SaaS) are that through IaaS almost all cloud-based services are obtained (Gonzales
et al. 2017). With PaaS, hardware as well as software-based resources can be
accessible. From SaaS, only third-party software resources are accessible.
ASSESSMENT On Fundamentals of Networking - PAGE 11
Week Ten
Assignment Question:
Things-Connected has special management software that only runs on Windows.
The admin officer has a problem that his desktop was replaced by a MacBook Pro
running macOS. How could virtualisation help to solve this problem? What type of
virtualisation would be used? Give an example of the name of a product that could
be used.
Your answer:
The special management software of Things-Connected which only runs on Windows
can be accessed from a MacBook Pro by running a virtual machine (VM) setup with
windows installed in that VM. This type of virtualisation is called system virtualisation
or Full virtualisation (Obasuyi and Sari 2015). A popular example of virtual machine
application can be VMware.
Your question:
Does virtualisation require hardware assistance?
Your sample answer:
Yes, some virtualisation techniques like system virtualisation or full virtualisation
requires hardware assisted virtualisation and makes use of the host hardware
especially the CPU (Brengel, Backes and Rossow 2016). Supported CPUs should
have VT or virtualisation technology enabled.
ASSESSMENT On Fundamentals of Networking - PAGE 12
Assignment Question:
Things-Connected has special management software that only runs on Windows.
The admin officer has a problem that his desktop was replaced by a MacBook Pro
running macOS. How could virtualisation help to solve this problem? What type of
virtualisation would be used? Give an example of the name of a product that could
be used.
Your answer:
The special management software of Things-Connected which only runs on Windows
can be accessed from a MacBook Pro by running a virtual machine (VM) setup with
windows installed in that VM. This type of virtualisation is called system virtualisation
or Full virtualisation (Obasuyi and Sari 2015). A popular example of virtual machine
application can be VMware.
Your question:
Does virtualisation require hardware assistance?
Your sample answer:
Yes, some virtualisation techniques like system virtualisation or full virtualisation
requires hardware assisted virtualisation and makes use of the host hardware
especially the CPU (Brengel, Backes and Rossow 2016). Supported CPUs should
have VT or virtualisation technology enabled.
ASSESSMENT On Fundamentals of Networking - PAGE 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



