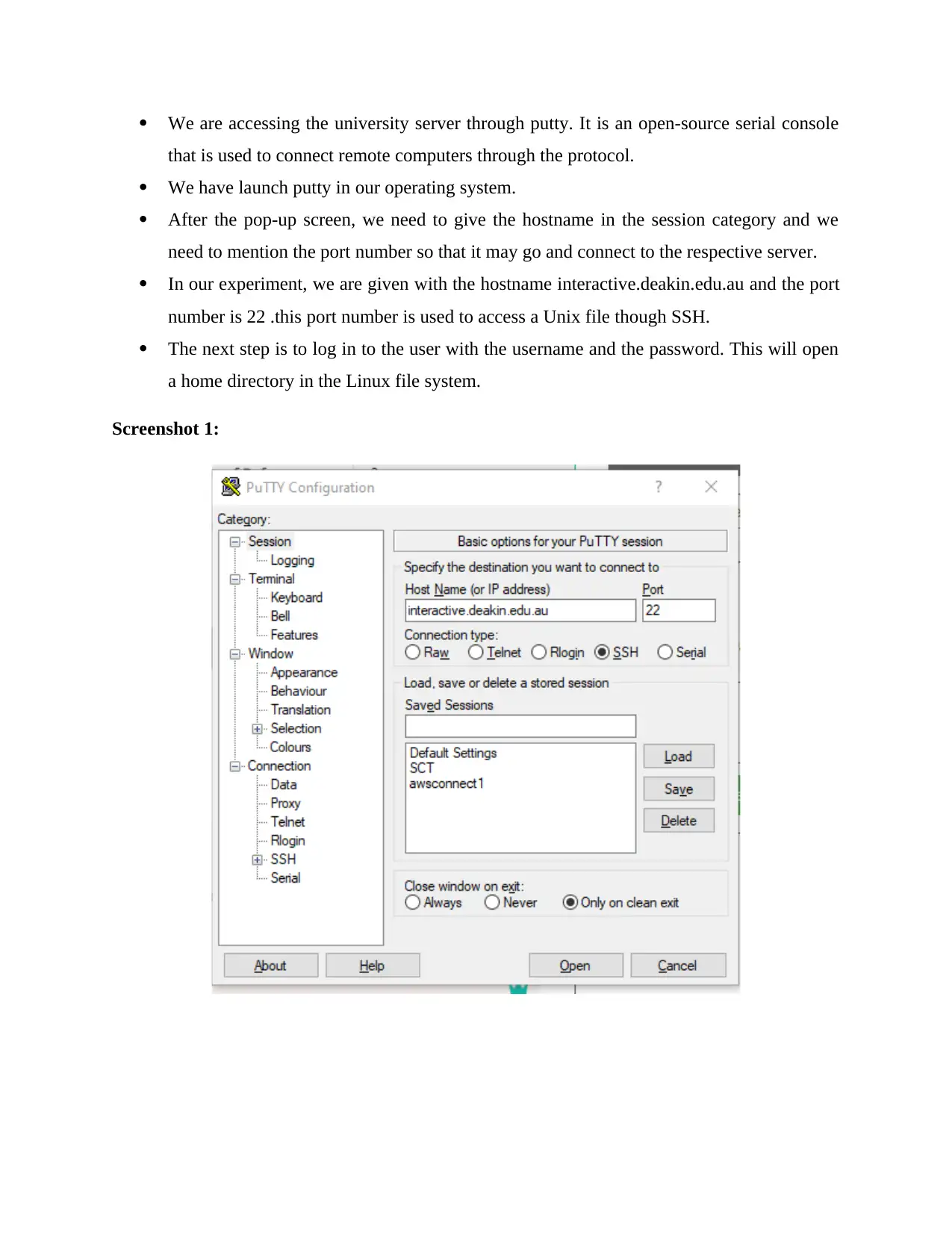
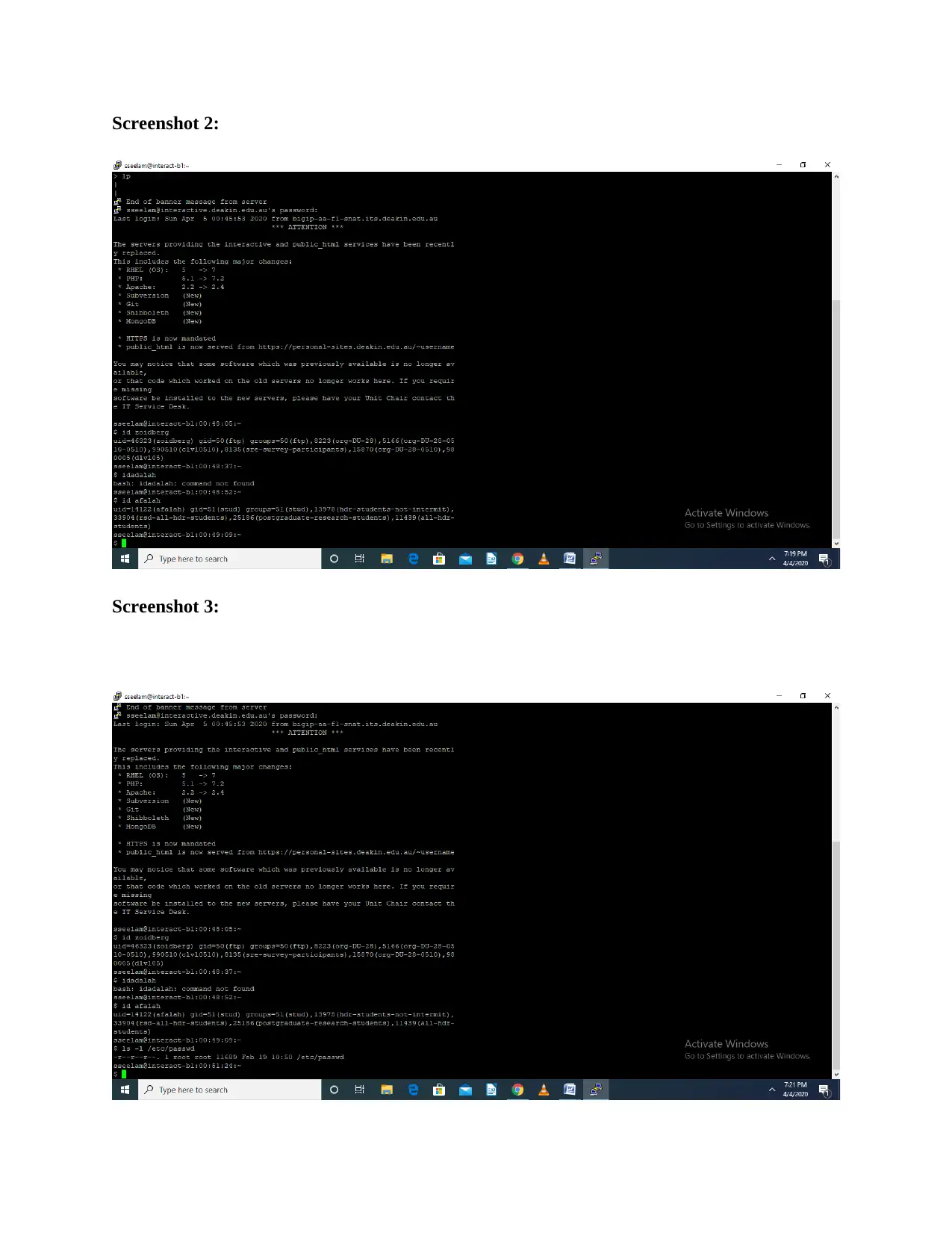
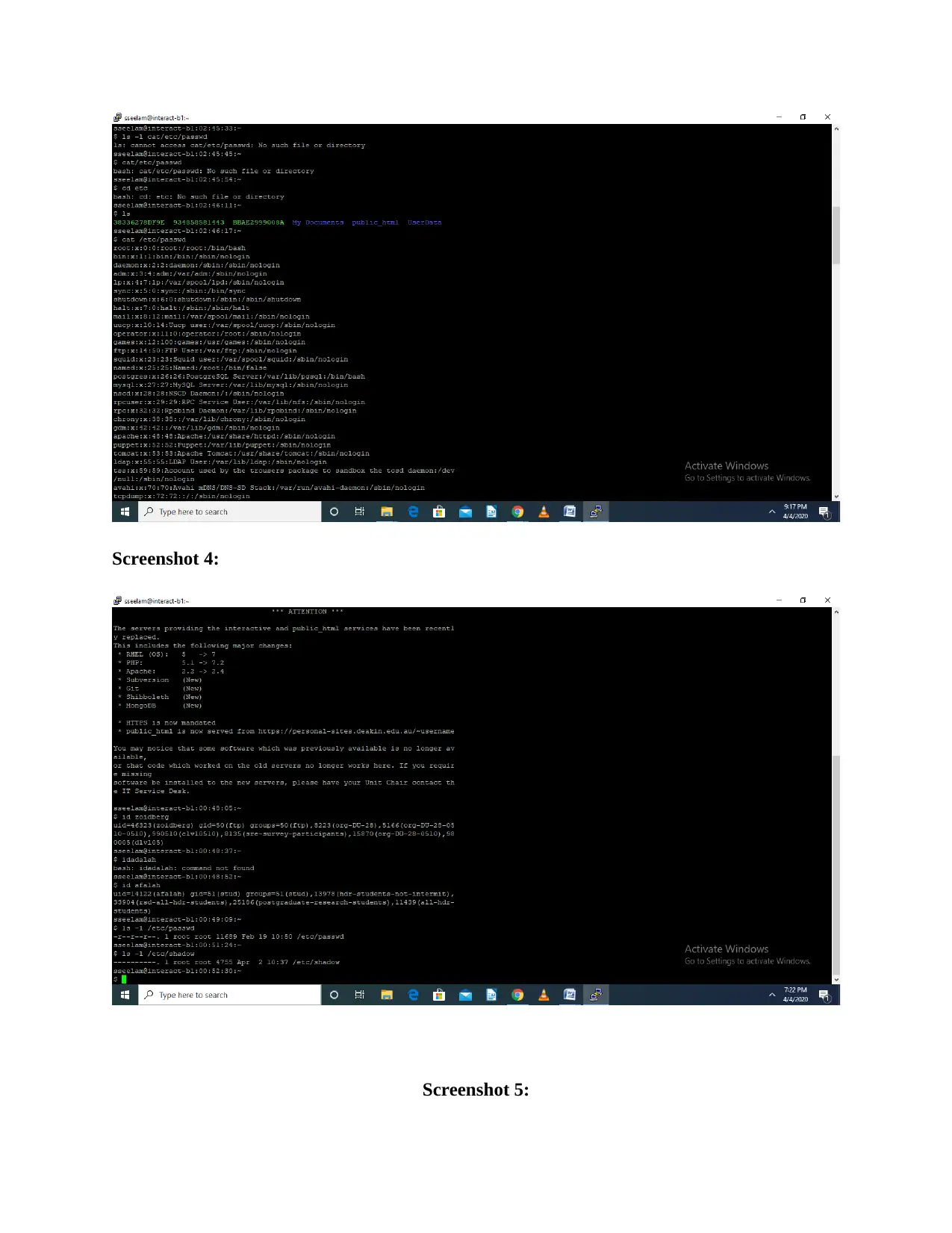
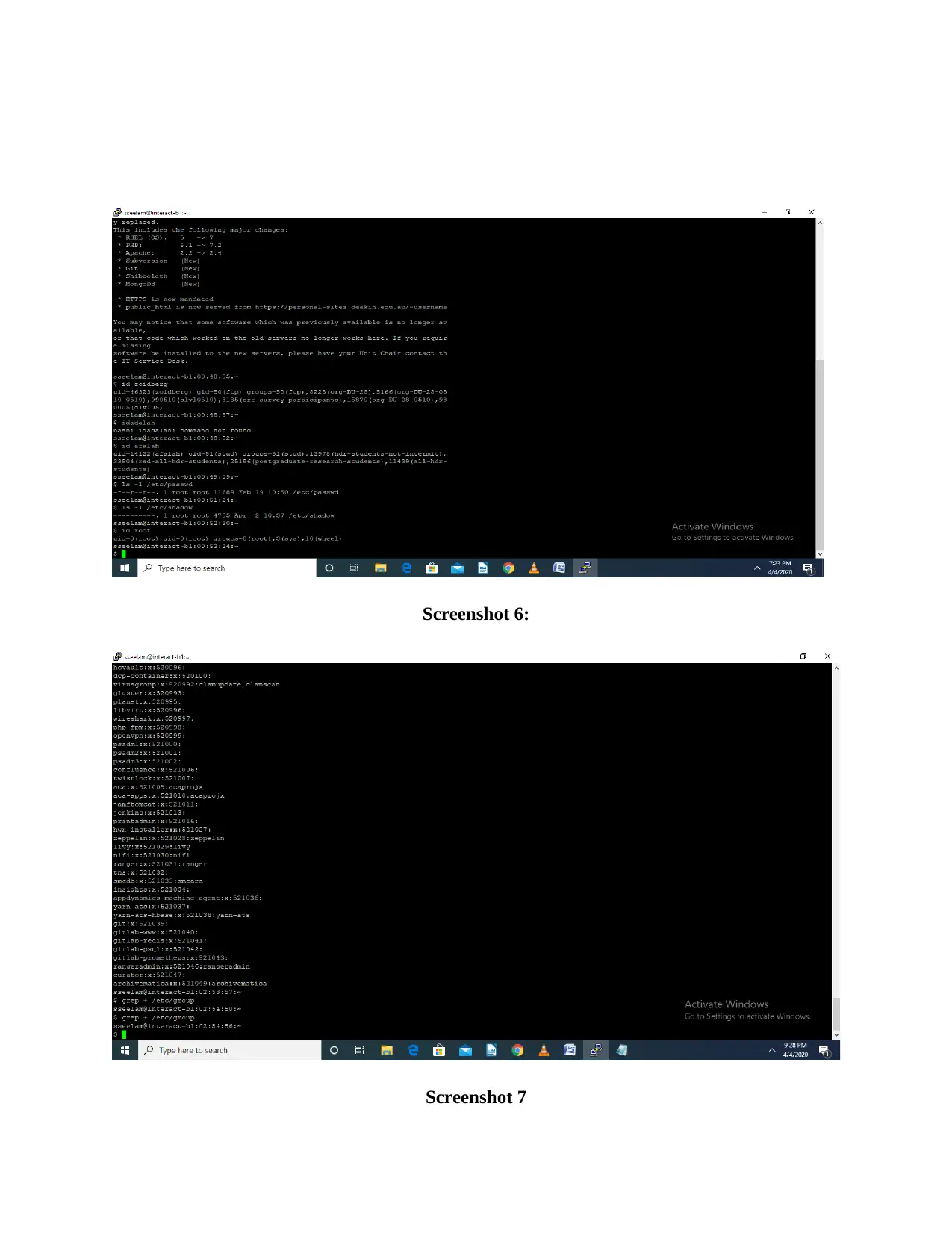
Deakin University SIT704: Basic Linux Security - Practical Assignment
VerifiedAdded on 2022/08/25
|7
|568
|19
Practical Assignment
AI Summary
This assignment solution details a practical exercise in basic Linux security using the Deakin University server and PuTTY. The task involves logging into the server via SSH, executing commands to check user and group permissions, and analyzing file access rights. The solution includes screenshots demonstrating the process of connecting to the server, running the 'id' command to view user information, and examining the contents of the /etc/passwd file. The assignment explores concepts like root access, group identifiers (GID), and the use of commands such as 'ls -l' and 'grep' to understand file permissions and user privileges within the Linux environment. The reflections highlight the practical application of Linux commands and the importance of understanding user and file permissions for system security.
1 out of 7










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)