ITC571 Emerging Tech: Biometrics Security Project Plan & Proposal
VerifiedAdded on 2023/04/10
|11
|2031
|450
Project
AI Summary
This project plan outlines a comprehensive study on biometrics security, addressing its role in combating cybercrimes within both IT and non-IT organizations. The plan includes a project blog, weekly progress reports, and a detailed rationale highlighting the problem domain, purpose, and justification for the research. The research questions focus on biometrics security techniques, their application across different organizational types, associated benefits and challenges, and key attributes. The methodology involves qualitative research methods, including grounded theory and case studies, with data collection through interviews and observations. The project also considers ethical and compliance requirements, developing a work breakdown structure (WBS), risk analysis, and a Gantt chart for project management. Deliverables include an annotated bibliography, journal paper, and poster presentation, demonstrating the project's structured approach and expected outcomes. The plan covers various aspects of biometrics such as fingerprint, facial, and iris recognition.
Biometrics Security Project Plan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Biometrics Security
Table of Contents
Title.......................................................................................................................................................2
Project Blog.......................................................................................................................................2
Weekly Progress Reports Plan...........................................................................................................2
Rationale...............................................................................................................................................2
Problem domain................................................................................................................................2
Purpose and justification....................................................................................................................2
Supervisor Approval..............................................................................................................................2
Research Questions...............................................................................................................................2
Conceptual or Theoretical Framework..................................................................................................3
Methodology.........................................................................................................................................4
Analysis of sources of information (EndNote, APA Referencing Style)...........................................4
Research method(s)...........................................................................................................................4
Data collection or systems design methods.......................................................................................4
Ethical Issues.....................................................................................................................................5
Compliance Requirements (Workplace, Industry or Government regulations)..................................5
Project Plan...........................................................................................................................................5
Deliverables (Annotated Bibliography, Journal Paper and Poster Presentation.)...............................5
Work breakdown structure (WBS)....................................................................................................6
Risk Analysis.....................................................................................................................................7
Duration.............................................................................................................................................9
Gantt chart.........................................................................................................................................9
References...........................................................................................................................................10
Table of Contents
Title.......................................................................................................................................................2
Project Blog.......................................................................................................................................2
Weekly Progress Reports Plan...........................................................................................................2
Rationale...............................................................................................................................................2
Problem domain................................................................................................................................2
Purpose and justification....................................................................................................................2
Supervisor Approval..............................................................................................................................2
Research Questions...............................................................................................................................2
Conceptual or Theoretical Framework..................................................................................................3
Methodology.........................................................................................................................................4
Analysis of sources of information (EndNote, APA Referencing Style)...........................................4
Research method(s)...........................................................................................................................4
Data collection or systems design methods.......................................................................................4
Ethical Issues.....................................................................................................................................5
Compliance Requirements (Workplace, Industry or Government regulations)..................................5
Project Plan...........................................................................................................................................5
Deliverables (Annotated Bibliography, Journal Paper and Poster Presentation.)...............................5
Work breakdown structure (WBS)....................................................................................................6
Risk Analysis.....................................................................................................................................7
Duration.............................................................................................................................................9
Gantt chart.........................................................................................................................................9
References...........................................................................................................................................10
Biometrics Security
Title
Biometrics Security
Project Blog
https://thinkspace.csu.edu.au/sanketsalvi/?p=3&preview=true
Weekly Progress Reports Plan
There will be weekly blog entries done to share the progress updates and details with the
other members in the team along with the research guides and mentors.
Rationale
Problem domain
Cybercrimes have become a frequent occurrence in the business organizations. Also, the
individual users are impacted with such crimes resulting in adverse impacts. The digital
information is captured by the cyber criminals resulting in the violation of information
privacy and security. The organizations also suffer badly due to these incidents as there
negative implications, such as legal obligations, loss of customer trust, and poor market
reputation that arises.
Purpose and justification
The purpose of the plan is to include the research background and details and include the
project plan to carry out the research project.
The choice of the research topic is justified as the Biometrics Security is one of the
mechanisms that can control and put a check on the cybercrimes. The implementation of
biometrics measures will also reduce the attack surface and attack window.
Supervisor Approval
The research supervisor will provide the approval on the research title and the proposal so
that further research activities can be executed. The approval will be granted only if all of the
sections are included and there is a justified description present under every section.
Title
Biometrics Security
Project Blog
https://thinkspace.csu.edu.au/sanketsalvi/?p=3&preview=true
Weekly Progress Reports Plan
There will be weekly blog entries done to share the progress updates and details with the
other members in the team along with the research guides and mentors.
Rationale
Problem domain
Cybercrimes have become a frequent occurrence in the business organizations. Also, the
individual users are impacted with such crimes resulting in adverse impacts. The digital
information is captured by the cyber criminals resulting in the violation of information
privacy and security. The organizations also suffer badly due to these incidents as there
negative implications, such as legal obligations, loss of customer trust, and poor market
reputation that arises.
Purpose and justification
The purpose of the plan is to include the research background and details and include the
project plan to carry out the research project.
The choice of the research topic is justified as the Biometrics Security is one of the
mechanisms that can control and put a check on the cybercrimes. The implementation of
biometrics measures will also reduce the attack surface and attack window.
Supervisor Approval
The research supervisor will provide the approval on the research title and the proposal so
that further research activities can be executed. The approval will be granted only if all of the
sections are included and there is a justified description present under every section.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Biometrics Security
Research Questions
What are the biometrics security techniques that may be used to deal with
cybercrimes?
Can biometrics security be applied in the IT as well as non-IT organizations?
What are associated benefits and challenges of biometrics security?
What is the biometrics security attributes?
Conceptual or Theoretical Framework
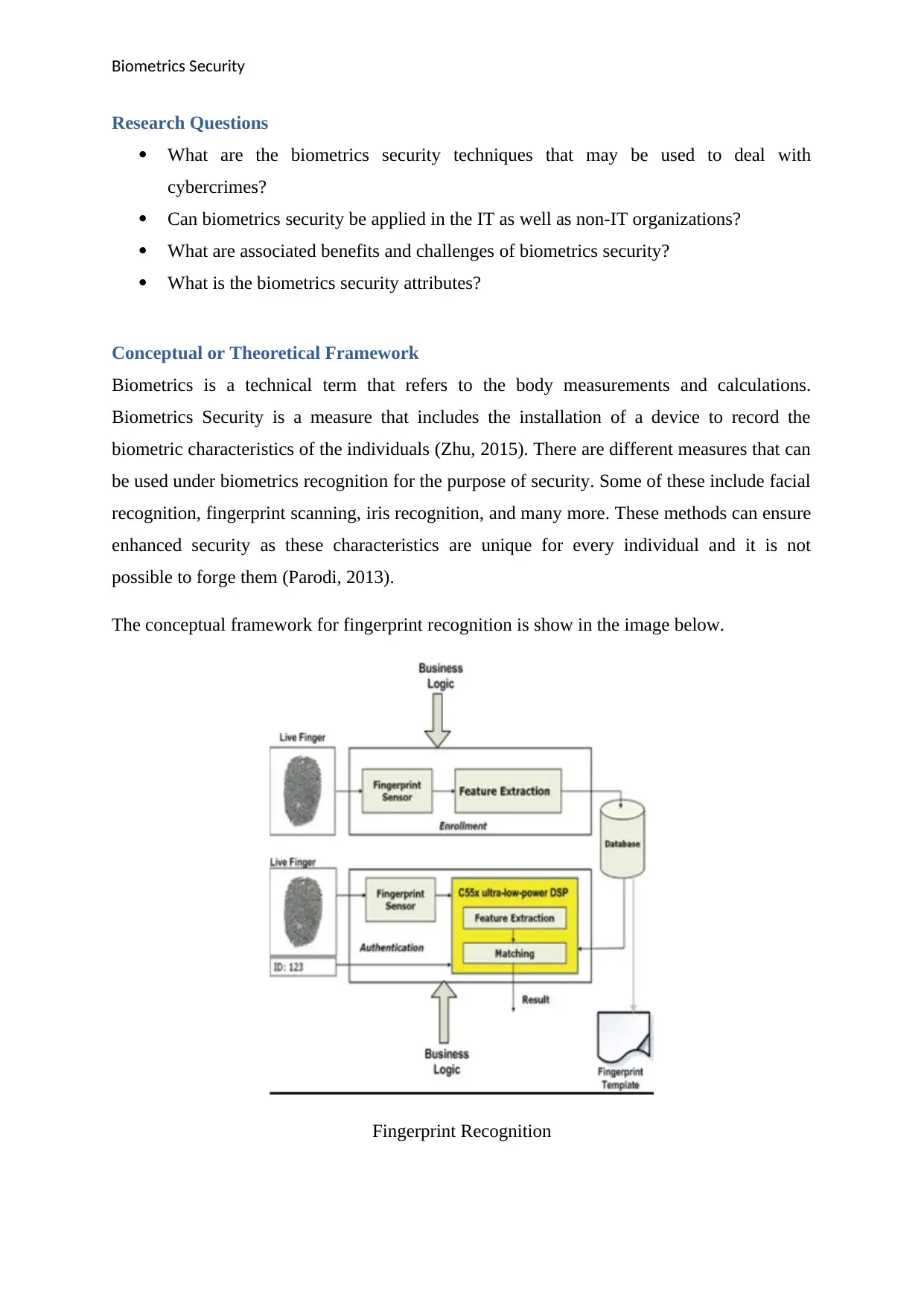
Biometrics is a technical term that refers to the body measurements and calculations.
Biometrics Security is a measure that includes the installation of a device to record the
biometric characteristics of the individuals (Zhu, 2015). There are different measures that can
be used under biometrics recognition for the purpose of security. Some of these include facial
recognition, fingerprint scanning, iris recognition, and many more. These methods can ensure
enhanced security as these characteristics are unique for every individual and it is not
possible to forge them (Parodi, 2013).
The conceptual framework for fingerprint recognition is show in the image below.
Fingerprint Recognition
Research Questions
What are the biometrics security techniques that may be used to deal with
cybercrimes?
Can biometrics security be applied in the IT as well as non-IT organizations?
What are associated benefits and challenges of biometrics security?
What is the biometrics security attributes?
Conceptual or Theoretical Framework
Biometrics is a technical term that refers to the body measurements and calculations.
Biometrics Security is a measure that includes the installation of a device to record the
biometric characteristics of the individuals (Zhu, 2015). There are different measures that can
be used under biometrics recognition for the purpose of security. Some of these include facial
recognition, fingerprint scanning, iris recognition, and many more. These methods can ensure
enhanced security as these characteristics are unique for every individual and it is not
possible to forge them (Parodi, 2013).
The conceptual framework for fingerprint recognition is show in the image below.
Fingerprint Recognition
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Biometrics Security
Methodology
Analysis of sources of information (EndNote, APA Referencing Style)
Biometrics Security is a subject area that has been developed and brought in use since past
few years. With the rise in the cases of cybercrimes, there are newer mechanisms that are
gradually being developed and researched upon. As a result, as soon as the technology was
brought in use, there is extensive research done in this area. The researchers have published
their research work and results in the form of journal papers. There are also various academic
sources that are available and accessible to study about the subject. These sources have been
referenced in the research work and the citations have been put. The Information Security and
Property rights have been secured while referring the information.
Research method(s)
The research method used to find out about the applications of Biometrics Security in the IT
and non-IT fields for treating cybercrimes will be done using qualitative research methods.
The exploration of the research subject will be done under this method to provide the answers
to the research questions. Grounded theory and case study will be used to carry out the
research. The theory will be used to determine the essence of the biometrics security
measures in the IT and non-IT companies (Evans & Kotchetkova, 2009). The use of
interviews, historical & legacy data, and axial coding techniques will be used under this
method to determine the results and findings. The case study method will also be followed to
understand the role of these measures in the organizations under varied domains. In this
research work, exploratory case studies will be used (Edwards & Brannelly, 2017).
Data collection or systems design methods
Data will have a lot of significance in the research process. The primary data collection
methods will be interviews and observations. The research for the use and application of
biometrics security is to be done for the IT as well as non-IT firms. The interviews will be
conducted for the employees of the organizations under both these categories. The technical
experts and Biometric specialists will also be interviewed to determine the possible use of the
measure. The cyber specialists will be interviewed to determine the forms of these attacks
and the threat agents that are used. The observation of the existing systems and tools will be
done to understand the attack patterns and mechanisms. The analysis of these information
sets will highlight the areas wherein biometrics security measures can be implemented.
Methodology
Analysis of sources of information (EndNote, APA Referencing Style)
Biometrics Security is a subject area that has been developed and brought in use since past
few years. With the rise in the cases of cybercrimes, there are newer mechanisms that are
gradually being developed and researched upon. As a result, as soon as the technology was
brought in use, there is extensive research done in this area. The researchers have published
their research work and results in the form of journal papers. There are also various academic
sources that are available and accessible to study about the subject. These sources have been
referenced in the research work and the citations have been put. The Information Security and
Property rights have been secured while referring the information.
Research method(s)
The research method used to find out about the applications of Biometrics Security in the IT
and non-IT fields for treating cybercrimes will be done using qualitative research methods.
The exploration of the research subject will be done under this method to provide the answers
to the research questions. Grounded theory and case study will be used to carry out the
research. The theory will be used to determine the essence of the biometrics security
measures in the IT and non-IT companies (Evans & Kotchetkova, 2009). The use of
interviews, historical & legacy data, and axial coding techniques will be used under this
method to determine the results and findings. The case study method will also be followed to
understand the role of these measures in the organizations under varied domains. In this
research work, exploratory case studies will be used (Edwards & Brannelly, 2017).
Data collection or systems design methods
Data will have a lot of significance in the research process. The primary data collection
methods will be interviews and observations. The research for the use and application of
biometrics security is to be done for the IT as well as non-IT firms. The interviews will be
conducted for the employees of the organizations under both these categories. The technical
experts and Biometric specialists will also be interviewed to determine the possible use of the
measure. The cyber specialists will be interviewed to determine the forms of these attacks
and the threat agents that are used. The observation of the existing systems and tools will be
done to understand the attack patterns and mechanisms. The analysis of these information
sets will highlight the areas wherein biometrics security measures can be implemented.

Biometrics Security
There will also be secondary data collection methods that will be used. Domain analysis will
be done for IT and non-IT organizations. The domain-specific attacks and patterns will be
determined. Group discussions and brainstorming sessions will also be organized to
determine the attack patterns and mechanisms along with the potential areas of application.
Ethical Issues
There may be certain ethical issues that may emerge in the research project. The research on
Biometrics Security will be done to understand the application areas of the technology to
control the cybercrimes. However, there may be violation of security norms and guidelines
during the research process. The members of the research team may also violate the ethical
codes and principles during the communication and information sharing processes (Dalal,
2014).
Compliance Requirements (Workplace, Industry or Government regulations)
The scope of Biometrics Security will be determined for the IT as well as for the non-IT
organizations. It will cover a wide range of industries, such as healthcare, finance, marketing,
real-estate, and many more. Every industry has its own set of policies and standards that need
to be complied with. For instance, healthcare industry must follow Health Insurance
Portability & Accountability Act (HIPAA) (Tyagi, Aggarwal, Dubey & Pilli, 2013). Such
standards and policies must be adhered to. There are also internal workplace policies of every
organization that must be ensured. The IT laws, Data Protection Act, ethical codes, and other
Government regulations must also be followed.
Project Plan
Deliverables (Annotated Bibliography, Journal Paper and Poster Presentation.)
Research Proposal and Research plan shall be delivered to share the research information and
details.
Annotated Bibliography on Biometrics security shall also be delivered so that the in-depth
understanding on the topic could be gained.
Journal Paper and poster Presentation must be provided so that the research findings and
outcomes are formally documented. The sharing of the research outcomes will be done using
these deliverables.
There will also be secondary data collection methods that will be used. Domain analysis will
be done for IT and non-IT organizations. The domain-specific attacks and patterns will be
determined. Group discussions and brainstorming sessions will also be organized to
determine the attack patterns and mechanisms along with the potential areas of application.
Ethical Issues
There may be certain ethical issues that may emerge in the research project. The research on
Biometrics Security will be done to understand the application areas of the technology to
control the cybercrimes. However, there may be violation of security norms and guidelines
during the research process. The members of the research team may also violate the ethical
codes and principles during the communication and information sharing processes (Dalal,
2014).
Compliance Requirements (Workplace, Industry or Government regulations)
The scope of Biometrics Security will be determined for the IT as well as for the non-IT
organizations. It will cover a wide range of industries, such as healthcare, finance, marketing,
real-estate, and many more. Every industry has its own set of policies and standards that need
to be complied with. For instance, healthcare industry must follow Health Insurance
Portability & Accountability Act (HIPAA) (Tyagi, Aggarwal, Dubey & Pilli, 2013). Such
standards and policies must be adhered to. There are also internal workplace policies of every
organization that must be ensured. The IT laws, Data Protection Act, ethical codes, and other
Government regulations must also be followed.
Project Plan
Deliverables (Annotated Bibliography, Journal Paper and Poster Presentation.)
Research Proposal and Research plan shall be delivered to share the research information and
details.
Annotated Bibliography on Biometrics security shall also be delivered so that the in-depth
understanding on the topic could be gained.
Journal Paper and poster Presentation must be provided so that the research findings and
outcomes are formally documented. The sharing of the research outcomes will be done using
these deliverables.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Biometrics Security
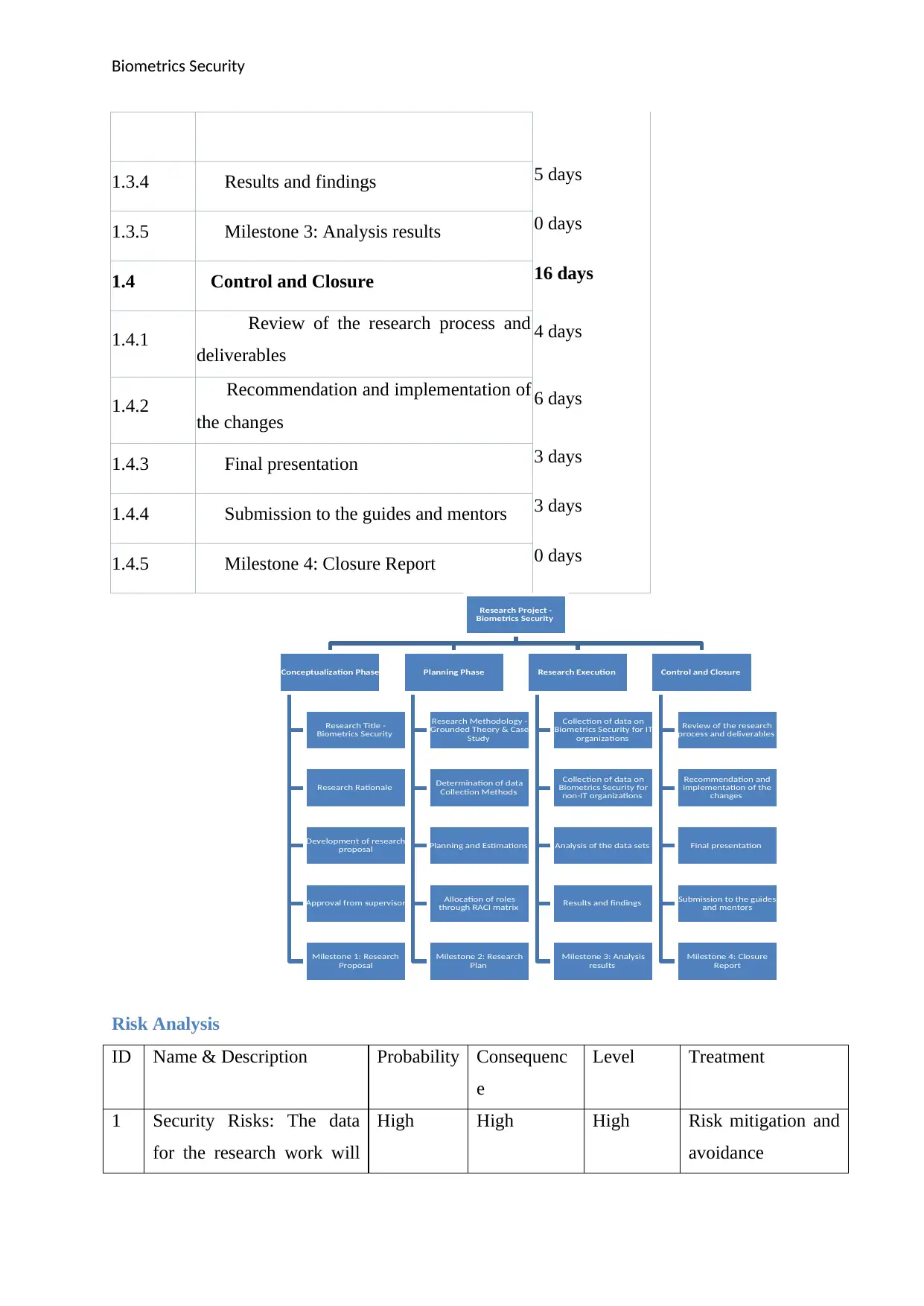
Work breakdown structure (WBS)
The research project will be conducted in four phases and there will be some activities
executed as a part of each phase. The work breakdown structure for the project is included in
the table and image below.
WBS Task Name Duration
1 Research Project - Biometrics Security 60 days
1.1 Conceptualization Phase 7 days
1.1.1 Research Title - Biometrics Security 1 day
1.1.2 Research Rationale 2 days
1.1.3 Development of research proposal 3 days
1.1.4 Approval from supervisor 1 day
1.1.5 Milestone 1: Research Proposal 0 days
1.2 Planning Phase 6 days
1.2.1 Research Methodology - Grounded
Theory & Case Study
2 days
1.2.2 Determination of data Collection
Methods
1 day
1.2.3 Planning and Estimations 2 days
1.2.4 Allocation of roles through RACI matrix 1 day
1.2.5 Milestone 2: Research Plan 0 days
1.3 Research Execution 31 days
1.3.1 Collection of data on Biometrics
Security for IT organizations
10 days
1.3.2 Collection of data on Biometrics
Security for non-IT organizations
10 days
1.3.3 Analysis of the data sets 16 days
Work breakdown structure (WBS)
The research project will be conducted in four phases and there will be some activities
executed as a part of each phase. The work breakdown structure for the project is included in
the table and image below.
WBS Task Name Duration
1 Research Project - Biometrics Security 60 days
1.1 Conceptualization Phase 7 days
1.1.1 Research Title - Biometrics Security 1 day
1.1.2 Research Rationale 2 days
1.1.3 Development of research proposal 3 days
1.1.4 Approval from supervisor 1 day
1.1.5 Milestone 1: Research Proposal 0 days
1.2 Planning Phase 6 days
1.2.1 Research Methodology - Grounded
Theory & Case Study
2 days
1.2.2 Determination of data Collection
Methods
1 day
1.2.3 Planning and Estimations 2 days
1.2.4 Allocation of roles through RACI matrix 1 day
1.2.5 Milestone 2: Research Plan 0 days
1.3 Research Execution 31 days
1.3.1 Collection of data on Biometrics
Security for IT organizations
10 days
1.3.2 Collection of data on Biometrics
Security for non-IT organizations
10 days
1.3.3 Analysis of the data sets 16 days
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Biometrics Security
1.3.4 Results and findings 5 days
1.3.5 Milestone 3: Analysis results 0 days
1.4 Control and Closure 16 days
1.4.1 Review of the research process and
deliverables
4 days
1.4.2 Recommendation and implementation of
the changes
6 days
1.4.3 Final presentation 3 days
1.4.4 Submission to the guides and mentors 3 days
1.4.5 Milestone 4: Closure Report 0 days
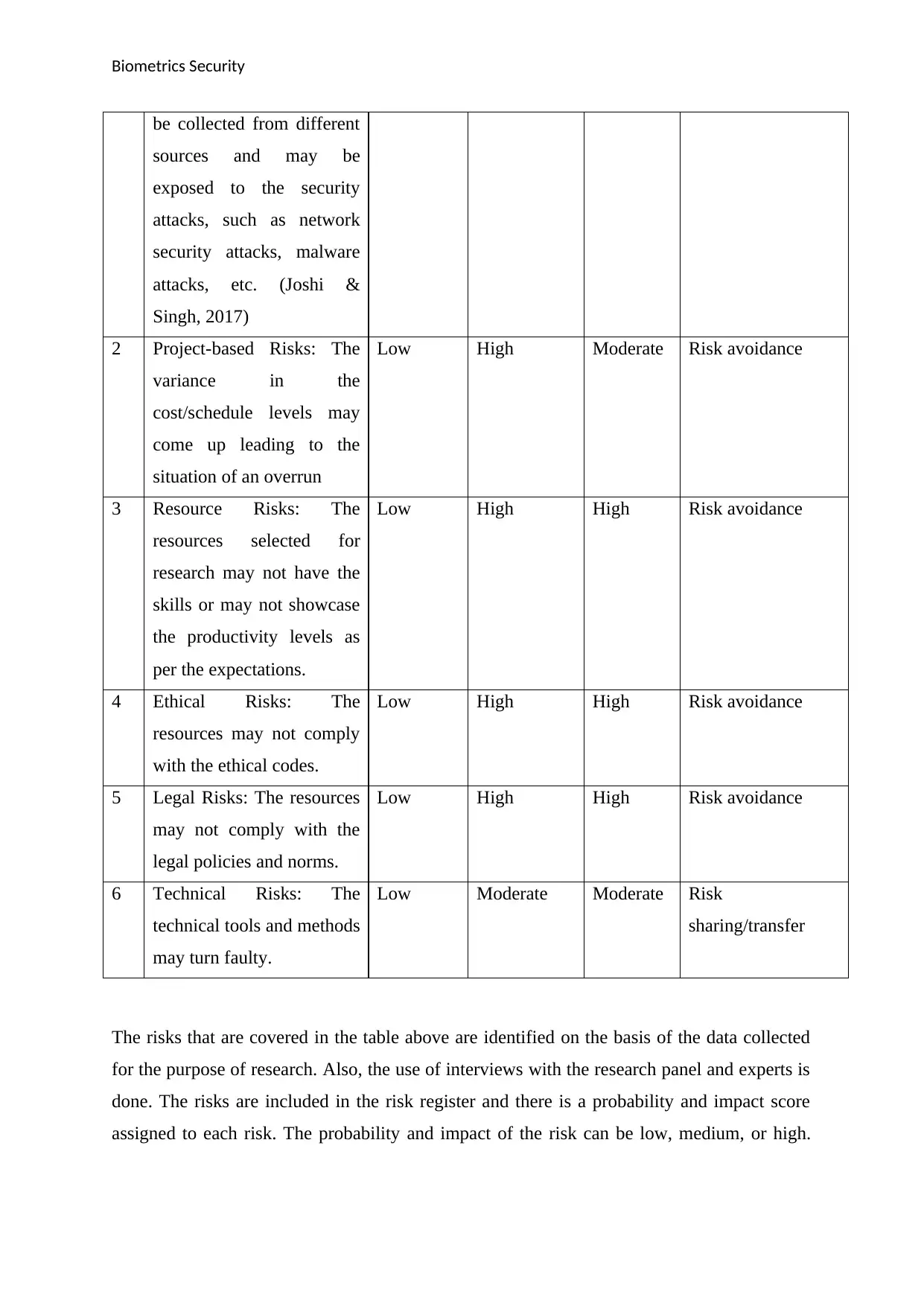
Risk Analysis
ID Name & Description Probability Consequenc
e
Level Treatment
1 Security Risks: The data
for the research work will
High High High Risk mitigation and
avoidance
Research Project -
Biometrics Security
Conceptualization Phase
Research Title -
Biometrics Security
Research Rationale
Development of research
proposal
Approval from supervisor
Milestone 1: Research
Proposal
Planning Phase
Research Methodology -
Grounded Theory & Case
Study
Determination of data
Collection Methods
Planning and Estimations
Allocation of roles
through RACI matrix
Milestone 2: Research
Plan
Research Execution
Collection of data on
Biometrics Security for IT
organizations
Collection of data on
Biometrics Security for
non-IT organizations
Analysis of the data sets
Results and findings
Milestone 3: Analysis
results
Control and Closure
Review of the research
process and deliverables
Recommendation and
implementation of the
changes
Final presentation
Submission to the guides
and mentors
Milestone 4: Closure
Report
1.3.4 Results and findings 5 days
1.3.5 Milestone 3: Analysis results 0 days
1.4 Control and Closure 16 days
1.4.1 Review of the research process and
deliverables
4 days
1.4.2 Recommendation and implementation of
the changes
6 days
1.4.3 Final presentation 3 days
1.4.4 Submission to the guides and mentors 3 days
1.4.5 Milestone 4: Closure Report 0 days
Risk Analysis
ID Name & Description Probability Consequenc
e
Level Treatment
1 Security Risks: The data
for the research work will
High High High Risk mitigation and
avoidance
Research Project -
Biometrics Security
Conceptualization Phase
Research Title -
Biometrics Security
Research Rationale
Development of research
proposal
Approval from supervisor
Milestone 1: Research
Proposal
Planning Phase
Research Methodology -
Grounded Theory & Case
Study
Determination of data
Collection Methods
Planning and Estimations
Allocation of roles
through RACI matrix
Milestone 2: Research
Plan
Research Execution
Collection of data on
Biometrics Security for IT
organizations
Collection of data on
Biometrics Security for
non-IT organizations
Analysis of the data sets
Results and findings
Milestone 3: Analysis
results
Control and Closure
Review of the research
process and deliverables
Recommendation and
implementation of the
changes
Final presentation
Submission to the guides
and mentors
Milestone 4: Closure
Report
Biometrics Security
be collected from different
sources and may be
exposed to the security
attacks, such as network
security attacks, malware
attacks, etc. (Joshi &
Singh, 2017)
2 Project-based Risks: The
variance in the
cost/schedule levels may
come up leading to the
situation of an overrun
Low High Moderate Risk avoidance
3 Resource Risks: The
resources selected for
research may not have the
skills or may not showcase
the productivity levels as
per the expectations.
Low High High Risk avoidance
4 Ethical Risks: The
resources may not comply
with the ethical codes.
Low High High Risk avoidance
5 Legal Risks: The resources
may not comply with the
legal policies and norms.
Low High High Risk avoidance
6 Technical Risks: The
technical tools and methods
may turn faulty.
Low Moderate Moderate Risk
sharing/transfer
The risks that are covered in the table above are identified on the basis of the data collected
for the purpose of research. Also, the use of interviews with the research panel and experts is
done. The risks are included in the risk register and there is a probability and impact score
assigned to each risk. The probability and impact of the risk can be low, medium, or high.
be collected from different
sources and may be
exposed to the security
attacks, such as network
security attacks, malware
attacks, etc. (Joshi &
Singh, 2017)
2 Project-based Risks: The
variance in the
cost/schedule levels may
come up leading to the
situation of an overrun
Low High Moderate Risk avoidance
3 Resource Risks: The
resources selected for
research may not have the
skills or may not showcase
the productivity levels as
per the expectations.
Low High High Risk avoidance
4 Ethical Risks: The
resources may not comply
with the ethical codes.
Low High High Risk avoidance
5 Legal Risks: The resources
may not comply with the
legal policies and norms.
Low High High Risk avoidance
6 Technical Risks: The
technical tools and methods
may turn faulty.
Low Moderate Moderate Risk
sharing/transfer
The risks that are covered in the table above are identified on the basis of the data collected
for the purpose of research. Also, the use of interviews with the research panel and experts is
done. The risks are included in the risk register and there is a probability and impact score
assigned to each risk. The probability and impact of the risk can be low, medium, or high.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Biometrics Security
There is a treatment strategy that is also mapped with each risk. The risk analysis is done
using qualitative methods of analysis (Zwikael & Ahn, 2010).
The mapping of the treatment strategy is done to bring down the probability and impact
scores. The risks will be treated and the implementation of the strategy will make sure that
the risks do not have any effect on the project progress or any of its areas.
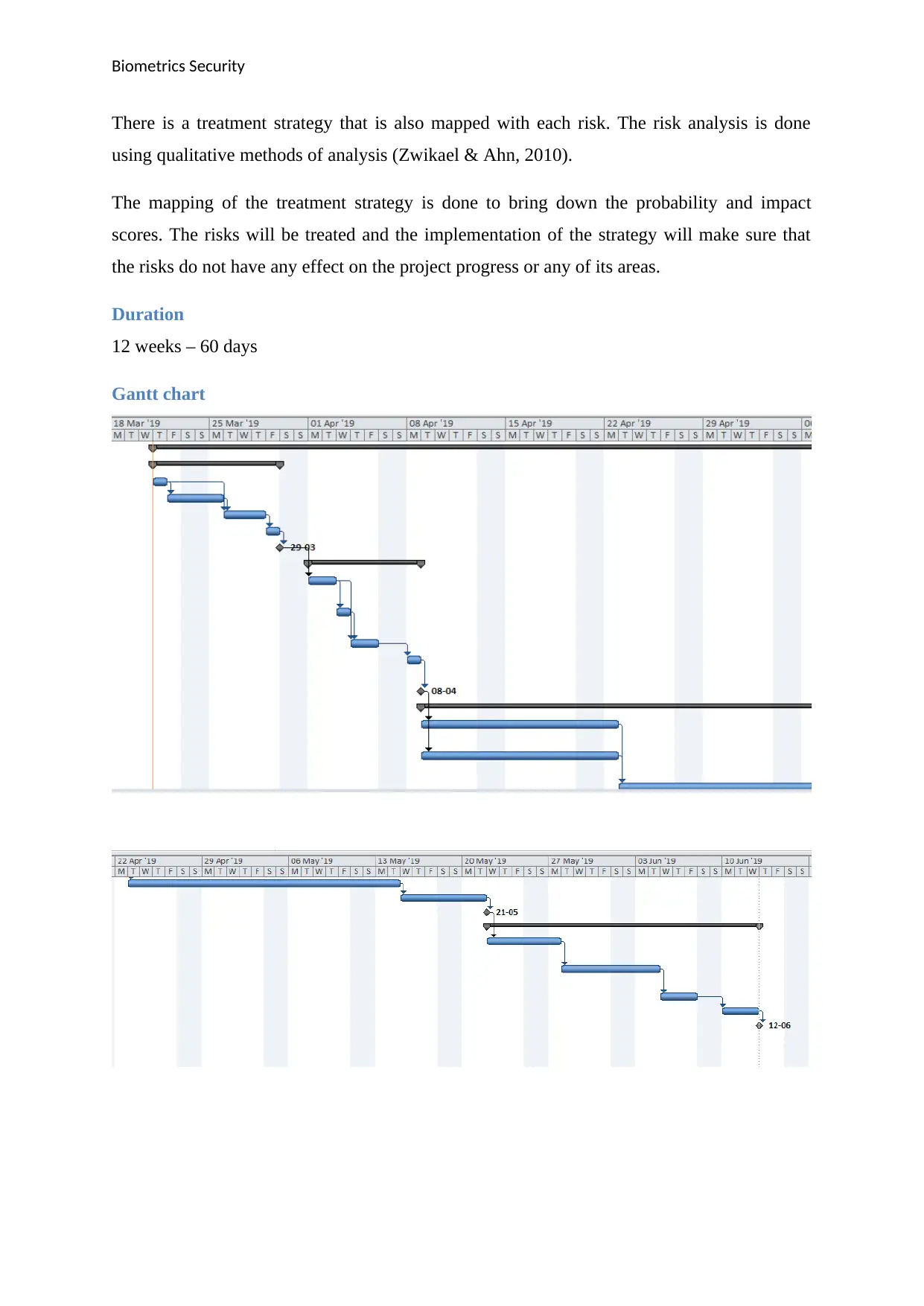
Duration
12 weeks – 60 days
Gantt chart
There is a treatment strategy that is also mapped with each risk. The risk analysis is done
using qualitative methods of analysis (Zwikael & Ahn, 2010).
The mapping of the treatment strategy is done to bring down the probability and impact
scores. The risks will be treated and the implementation of the strategy will make sure that
the risks do not have any effect on the project progress or any of its areas.
Duration
12 weeks – 60 days
Gantt chart
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Biometrics Security
References
Dalal, F. (2014). Ethics versus Compliance. The Institution, Ethical Psychotherapy Practice,
(and Me). Group Analysis, 47(1), 62-81. doi: 10.1177/0533316413520528
Edwards, R., & Brannelly, T. (2017). Approaches to democratising qualitative research
methods. Qualitative Research, 17(3), 271-277. doi: 10.1177/1468794117706869
Evans, R., & Kotchetkova, I. (2009). Qualitative research and deliberative methods: promise
or peril?. Qualitative Research, 9(5), 625-643. doi: 10.1177/1468794109343630
Joshi, C., & Singh, U. (2017). Information security risks management framework – A step
towards mitigating security risks in university network. Journal Of Information
Security And Applications, 35, 128-137. doi: 10.1016/j.jisa.2017.06.006
Parodi, F. (2013). The Concept of Cybercrime and Online Threats Analysis. International
Journal Of Information Security And Cybercrime, 2(1), 59-66. doi:
10.19107/ijisc.2013.01.07
Tyagi, P., Aggarwal, N., Dubey, B., & Pilli, E. (2013). HIPAA Compliance and Cloud
Computing. International Journal Of Computer Applications, 70(24), 29-32. doi:
10.5120/12215-8356
Zhu, H. (2015). One-time identity-password authenticated key agreement scheme based on
biometrics. Security And Communication Networks, 8(13), 2350-2360. doi:
10.1002/sec.1182
Zwikael, O., & Ahn, M. (2010). The Effectiveness of Risk Management: An Analysis of
Project Risk Planning Across Industries and Countries. Risk Analysis, 31(1), 25-37.
doi: 10.1111/j.1539-6924.2010.01470.x
References
Dalal, F. (2014). Ethics versus Compliance. The Institution, Ethical Psychotherapy Practice,
(and Me). Group Analysis, 47(1), 62-81. doi: 10.1177/0533316413520528
Edwards, R., & Brannelly, T. (2017). Approaches to democratising qualitative research
methods. Qualitative Research, 17(3), 271-277. doi: 10.1177/1468794117706869
Evans, R., & Kotchetkova, I. (2009). Qualitative research and deliberative methods: promise
or peril?. Qualitative Research, 9(5), 625-643. doi: 10.1177/1468794109343630
Joshi, C., & Singh, U. (2017). Information security risks management framework – A step
towards mitigating security risks in university network. Journal Of Information
Security And Applications, 35, 128-137. doi: 10.1016/j.jisa.2017.06.006
Parodi, F. (2013). The Concept of Cybercrime and Online Threats Analysis. International
Journal Of Information Security And Cybercrime, 2(1), 59-66. doi:
10.19107/ijisc.2013.01.07
Tyagi, P., Aggarwal, N., Dubey, B., & Pilli, E. (2013). HIPAA Compliance and Cloud
Computing. International Journal Of Computer Applications, 70(24), 29-32. doi:
10.5120/12215-8356
Zhu, H. (2015). One-time identity-password authenticated key agreement scheme based on
biometrics. Security And Communication Networks, 8(13), 2350-2360. doi:
10.1002/sec.1182
Zwikael, O., & Ahn, M. (2010). The Effectiveness of Risk Management: An Analysis of
Project Risk Planning Across Industries and Countries. Risk Analysis, 31(1), 25-37.
doi: 10.1111/j.1539-6924.2010.01470.x
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





