Client Management System Report - Computer Networking Technology
VerifiedAdded on 2023/06/04
|16
|3454
|367
Report
AI Summary
This report provides an in-depth analysis of Client Management Systems (CMS) within computer networking technology. It explores the purpose and motivation behind CMS, highlighting its role in modernizing network infrastructures to emphasize performance, management, and security. The report details how CMS works through network virtualization and OpenFlow technology, covering aspects like software distribution, mobile device management, helpdesk integration, OS deployment, and remote administration. It also discusses the architecture and design of CMS, including collaborative, operational, and analytical components, and examines elements such as sales force automation, human resource management, lead management, customer service, and marketing. The report further presents the advantages and disadvantages of CMS, and it references several articles to support its findings. Desklib provides access to this and many other solved assignments for students.
COMPUTER NETWORKING TECHNOLOGY
NETWORK CLIENT MANAGEMENT SYSTEMS
NETWORK CLIENT MANAGEMENT SYSTEMS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
A new computer networking technology
Abstract
Most computing farms which are in a distributed form are progressing in figure assets provision.
Back then, exploration of the majority works specialized on Virtualization innovation through
the computational utilization and capacity assets. Nowadays, Cloud Computing, being the center
of frameworks foundation, registration assets, is strongly getting to be software defined.
Cybersecurity
A new computer networking technology
Abstract
Most computing farms which are in a distributed form are progressing in figure assets provision.
Back then, exploration of the majority works specialized on Virtualization innovation through
the computational utilization and capacity assets. Nowadays, Cloud Computing, being the center
of frameworks foundation, registration assets, is strongly getting to be software defined.
Cybersecurity

2
A new computer networking technology
Table of Contents
Abstract..........................................................................................................................................1
Introduction....................................................................................................................................3
Purpose of Client Management System.......................................................................................4
How CMS works............................................................................................................................5
The General Operation.................................................................................................................6
Architecture and Design................................................................................................................7
Advantages.....................................................................................................................................8
Disadvantages.................................................................................................................................9
Architecture and design features of two competing products.................................................10
Comparison of the two competing products.............................................................................12
Conclusion....................................................................................................................................13
References.....................................................................................................................................14
Cybersecurity
A new computer networking technology
Table of Contents
Abstract..........................................................................................................................................1
Introduction....................................................................................................................................3
Purpose of Client Management System.......................................................................................4
How CMS works............................................................................................................................5
The General Operation.................................................................................................................6
Architecture and Design................................................................................................................7
Advantages.....................................................................................................................................8
Disadvantages.................................................................................................................................9
Architecture and design features of two competing products.................................................10
Comparison of the two competing products.............................................................................12
Conclusion....................................................................................................................................13
References.....................................................................................................................................14
Cybersecurity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
A new computer networking technology
Introduction
Currently companies are ramping the existing network infrastructure with the rapidly evolving
network technologies. The new networking technologies are really emphasizing on network
performance, network management and network security. Connectivity to a network has become
so critical as demand for the skyrocketing mobile workplaces, proliferation of applications and
rise of Internet of things. Nonetheless, the overriding priority for each network infrastructure is
security. This report will explore client management system as one of the new networking
technologies in terms of its operations, components, architecture, pros and cons of the
technology.
Cybersecurity
A new computer networking technology
Introduction
Currently companies are ramping the existing network infrastructure with the rapidly evolving
network technologies. The new networking technologies are really emphasizing on network
performance, network management and network security. Connectivity to a network has become
so critical as demand for the skyrocketing mobile workplaces, proliferation of applications and
rise of Internet of things. Nonetheless, the overriding priority for each network infrastructure is
security. This report will explore client management system as one of the new networking
technologies in terms of its operations, components, architecture, pros and cons of the
technology.
Cybersecurity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
A new computer networking technology
Purpose of Client Management System
Motivation behind the innovation
According to latest technologies on mobile phones, virtualization of the server, approaching the
cloud based organizations is among the few examples driving most frameworks on organization
industry to realize standard frameworks modules (Ahmed, Imran, Zomaya, Rayes, Rodrigues,
Guibene, 2018). Different types of standard frameworks are leveled, combined with Ethernet
levels switches sorted in tree structure. This course of action seemed, by all possible means, be
well and awesome when servers for customers being ready for winning, but such static layout is
laid or connected to the changing figure and break points with need of present undertaking of
server farms, transportation conditions and also the grounds. A small percentage of the key
getting ready shows driving need for more structural view point includes;
Altering the design movements
On the inner side of the whole server cultivate, changes in development have occurred largely.
More than client server applications which use the primary piece of the correspondence
occurring between clients (Bakardjieva and Smith, 2011). With use of different database and
servers, making it like "east-west" thing or machine-machine improvement before returning data
to the end customer contraption in the great "north-south" development plan. Then, users
attached to the system are changing system development designs as they initiate more room for
access to corporate substance and applications from a contraption.
Getting into the Information Technology in depth
Most users nowadays are so much into the information Technology as the whole world is into the
same. For example, Phone gadgets, the tablets and the iPad are highly used to get into
technology sector not forgetting the laptops and the PCs.
Rise of cloud administrations
Cybersecurity
A new computer networking technology
Purpose of Client Management System
Motivation behind the innovation
According to latest technologies on mobile phones, virtualization of the server, approaching the
cloud based organizations is among the few examples driving most frameworks on organization
industry to realize standard frameworks modules (Ahmed, Imran, Zomaya, Rayes, Rodrigues,
Guibene, 2018). Different types of standard frameworks are leveled, combined with Ethernet
levels switches sorted in tree structure. This course of action seemed, by all possible means, be
well and awesome when servers for customers being ready for winning, but such static layout is
laid or connected to the changing figure and break points with need of present undertaking of
server farms, transportation conditions and also the grounds. A small percentage of the key
getting ready shows driving need for more structural view point includes;
Altering the design movements
On the inner side of the whole server cultivate, changes in development have occurred largely.
More than client server applications which use the primary piece of the correspondence
occurring between clients (Bakardjieva and Smith, 2011). With use of different database and
servers, making it like "east-west" thing or machine-machine improvement before returning data
to the end customer contraption in the great "north-south" development plan. Then, users
attached to the system are changing system development designs as they initiate more room for
access to corporate substance and applications from a contraption.
Getting into the Information Technology in depth
Most users nowadays are so much into the information Technology as the whole world is into the
same. For example, Phone gadgets, the tablets and the iPad are highly used to get into
technology sector not forgetting the laptops and the PCs.
Rise of cloud administrations
Cybersecurity

5
A new computer networking technology
Endeavors have enthusiastically gotten a handle on open and private (individual) cloud
organizations, realizing phenomenal advancement of these organizations. Adventure forte units
as of now require the spryness to get to applications, establishment, and other IT resources on
intrigue and exclusively. Giving self-advantage provisioning, paying little amounts to whether in
a private or public, calls for adaptable scaling of enrolling, accumulating and framework
resources, ideally from a run of the mill point of view and with a common suite of instruments.
Large amount of information, high capacity of transmission
In due connection to the large amounts of information, or large datasets needs consistent parallel
running on increased tally of servers, which of course all require coordinate association with
each other (Janik, 2016). The rise of huge data amounts is creating a smooth platform for the
server develop. High developers in hyper-scale, come up with structures that face the marvelous
errand of scaling the system to meet all the expectations, making it be open without deterring
anything.
How CMS works
Client Management System is designed with high technology that enables the owners (the ones
in control of the management) to be able manage their users in all cases experienced and also in
the way the want their business to be done. This is achievable by one system having control of
the whole system.
Network Virtualization
By automating the networking operations, Network Virtualization meats this by creating network
platforms which are not matched. The Network Virtualization gets rid of the problems and
eliminates the time wasted in some jobs which are concerned to network operations.
The OpenFlow Technology
Cybersecurity
A new computer networking technology
Endeavors have enthusiastically gotten a handle on open and private (individual) cloud
organizations, realizing phenomenal advancement of these organizations. Adventure forte units
as of now require the spryness to get to applications, establishment, and other IT resources on
intrigue and exclusively. Giving self-advantage provisioning, paying little amounts to whether in
a private or public, calls for adaptable scaling of enrolling, accumulating and framework
resources, ideally from a run of the mill point of view and with a common suite of instruments.
Large amount of information, high capacity of transmission
In due connection to the large amounts of information, or large datasets needs consistent parallel
running on increased tally of servers, which of course all require coordinate association with
each other (Janik, 2016). The rise of huge data amounts is creating a smooth platform for the
server develop. High developers in hyper-scale, come up with structures that face the marvelous
errand of scaling the system to meet all the expectations, making it be open without deterring
anything.
How CMS works
Client Management System is designed with high technology that enables the owners (the ones
in control of the management) to be able manage their users in all cases experienced and also in
the way the want their business to be done. This is achievable by one system having control of
the whole system.
Network Virtualization
By automating the networking operations, Network Virtualization meats this by creating network
platforms which are not matched. The Network Virtualization gets rid of the problems and
eliminates the time wasted in some jobs which are concerned to network operations.
The OpenFlow Technology
Cybersecurity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
A new computer networking technology
The Open Flow Technology provides the basic data plane gadgets transferring tables in a similar
way and reduces the elevation essence of legacy networking components using central controller
remotely.
The General Operation
Software distribution and software packaging
In a company network, installing updates on the devices in a timely manner and maintenance of
particular applications are everyday operations of administrators department. Time to time they
are required to often do it. However the client management system helps users to automate the
software distribution.
Client management system does not only assist in distribution of software via installation
program but also it assists with patch management and maintenance. In addition, users can keep
the overview of their used licenses and are often secure on the legal side this is due to direct link
to the license management. Hence, the distribution of the software contributes to the company
standard and simplified day to day operations of the Helpdesk and the administrator such as
supporting the clients fixing the errors and problems.
Manage mobile devices
Portable customer framework paying little mind to whether tablet-PCs or cell phones are difficult
to think away in many organizations these days. Numerous IT-chairmen screen the spreading of
these minicomputers rather incredulously. The stress is huge, that the new gadget classes convey
to high consumption with them with regards to administration and could likewise prompt
conceivable security dangers for the organization arrange. At first appearance the administration
of the gadgets is significantly more confounded and as opposed to seeing the points of interest
for the profitability of the representatives the doubt becomes much further with the "Bring your
very own Device" (BYOD)- rationality.
Helpdesk with ticket system
Cybersecurity
A new computer networking technology
The Open Flow Technology provides the basic data plane gadgets transferring tables in a similar
way and reduces the elevation essence of legacy networking components using central controller
remotely.
The General Operation
Software distribution and software packaging
In a company network, installing updates on the devices in a timely manner and maintenance of
particular applications are everyday operations of administrators department. Time to time they
are required to often do it. However the client management system helps users to automate the
software distribution.
Client management system does not only assist in distribution of software via installation
program but also it assists with patch management and maintenance. In addition, users can keep
the overview of their used licenses and are often secure on the legal side this is due to direct link
to the license management. Hence, the distribution of the software contributes to the company
standard and simplified day to day operations of the Helpdesk and the administrator such as
supporting the clients fixing the errors and problems.
Manage mobile devices
Portable customer framework paying little mind to whether tablet-PCs or cell phones are difficult
to think away in many organizations these days. Numerous IT-chairmen screen the spreading of
these minicomputers rather incredulously. The stress is huge, that the new gadget classes convey
to high consumption with them with regards to administration and could likewise prompt
conceivable security dangers for the organization arrange. At first appearance the administration
of the gadgets is significantly more confounded and as opposed to seeing the points of interest
for the profitability of the representatives the doubt becomes much further with the "Bring your
very own Device" (BYOD)- rationality.
Helpdesk with ticket system
Cybersecurity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
A new computer networking technology
Each IT-office sees itself went up against with a pretty much extensive number of inquiries,
mistake reports, tips and wishes that are gotten by the help.
All functionalities of the Client Lifecycle Management (CMS) are additionally available for the
helpdesk in reliance to the design. Programming circulation, changes of the arrangement by
means of customer directions or remote upkeep is finished by the help workers with a focal
programming: ACMP.
Indeed, even the less experienced client is progressively utilizing the choice to send reports to the
help through email. An email has numerous focal points for the customer. From one viewpoint
he is never again compelled to look out for the phone until the point when a help representative
is accessible and then again it is significantly less difficult to unequivocally plan the issue in
words without the time-weight of the phone.
On the opposite side, the help worker isn't hindered by phone calls amid work as regularly. A
decent helpdesk-framework like ACMP forms the approaching messages and incorporates them
into the helpdesk-process.
OS and Desktop Deployment
PCs these days are not supplanted as quickly as they were a few years prior. The execution of
present day PCs more often than not likewise gets the job done for the up and coming age of
working frameworks. The measure of customer frameworks is at the same time expanding
because of the way that an ever increasing number of clients currently likewise have a PC
available to them notwithstanding the stationary office-PC. Regardless of whether an
organization buys. The institutionalization of the working framework in the organization prompts
an improvement of the work process at the helpdesk in the most limited of times. The client now
just must be acquainted with one single working framework. The checking for patches and
updates is lessened to a solitary stage. Same goes for the essential driver condition, particularly
for peripherals, for example, printers or scanners.
Cybersecurity
A new computer networking technology
Each IT-office sees itself went up against with a pretty much extensive number of inquiries,
mistake reports, tips and wishes that are gotten by the help.
All functionalities of the Client Lifecycle Management (CMS) are additionally available for the
helpdesk in reliance to the design. Programming circulation, changes of the arrangement by
means of customer directions or remote upkeep is finished by the help workers with a focal
programming: ACMP.
Indeed, even the less experienced client is progressively utilizing the choice to send reports to the
help through email. An email has numerous focal points for the customer. From one viewpoint
he is never again compelled to look out for the phone until the point when a help representative
is accessible and then again it is significantly less difficult to unequivocally plan the issue in
words without the time-weight of the phone.
On the opposite side, the help worker isn't hindered by phone calls amid work as regularly. A
decent helpdesk-framework like ACMP forms the approaching messages and incorporates them
into the helpdesk-process.
OS and Desktop Deployment
PCs these days are not supplanted as quickly as they were a few years prior. The execution of
present day PCs more often than not likewise gets the job done for the up and coming age of
working frameworks. The measure of customer frameworks is at the same time expanding
because of the way that an ever increasing number of clients currently likewise have a PC
available to them notwithstanding the stationary office-PC. Regardless of whether an
organization buys. The institutionalization of the working framework in the organization prompts
an improvement of the work process at the helpdesk in the most limited of times. The client now
just must be acquainted with one single working framework. The checking for patches and
updates is lessened to a solitary stage. Same goes for the essential driver condition, particularly
for peripherals, for example, printers or scanners.
Cybersecurity

8
A new computer networking technology
Remote administration
Remote upkeep of PCs is winding up increasingly vital for the help of hard-and programming.
The potential outcomes for direct help by means of the help are expanded by the regularly
expanding association of PCs by means of the web, the setup of organization interior intranets
and ordinary media transmission techniques (ISDN, phone) (Batalla, Mastorakis,
Mavromoustakis, Zurek, 2016).
Items for remote support are utilized not minimum on account of the cost-sparing open doors
with regards to travel costs and better utilization of assets (staff and innovation).
Architecture and Design of the Client Management System
1. Collaborative.
All interchanges between a business and its clients are recorded, sorted out and handled in the
shared area of the product. This implies correspondence by phone, face to face, and by email.
2. Operational
This classification inside a CMS framework manages the automation of business forms including
client benefit, information on contenders, industry patterns, client account data and
administration.
3. Analytical
Analytical CMS may result in strategically pitching certain things to specific clients dependent
on their past purchasing propensities, or conferring data applicable just to specific fragments of a
client base (Park, &, 2014).
This piece of the CMS design is additionally important for distinguishing changes in the business
all in all, so organizations stay lithe and react rapidly to changing business sector requests.
Information can be investigated in various ways, and charts, reports and graphs created to all the
more likely outline the outcomes.
This is the essential design of a client administration framework, however the ascent of internet
based life and portable working has brought other, more characterized frameworks to the market.
Prominent 'additional items' to the essential structure of a CMS arrangement may incorporate
cloud based frameworks that are open from any gadget (Haag, Cummings, and Dawkins, 2008).
The catchphrase in CMS is coordination – combination of information with the goal that it very
well may be put to use in a way that advantages the business, as well as clients, providers and the
Cybersecurity
A new computer networking technology
Remote administration
Remote upkeep of PCs is winding up increasingly vital for the help of hard-and programming.
The potential outcomes for direct help by means of the help are expanded by the regularly
expanding association of PCs by means of the web, the setup of organization interior intranets
and ordinary media transmission techniques (ISDN, phone) (Batalla, Mastorakis,
Mavromoustakis, Zurek, 2016).
Items for remote support are utilized not minimum on account of the cost-sparing open doors
with regards to travel costs and better utilization of assets (staff and innovation).
Architecture and Design of the Client Management System
1. Collaborative.
All interchanges between a business and its clients are recorded, sorted out and handled in the
shared area of the product. This implies correspondence by phone, face to face, and by email.
2. Operational
This classification inside a CMS framework manages the automation of business forms including
client benefit, information on contenders, industry patterns, client account data and
administration.
3. Analytical
Analytical CMS may result in strategically pitching certain things to specific clients dependent
on their past purchasing propensities, or conferring data applicable just to specific fragments of a
client base (Park, &, 2014).
This piece of the CMS design is additionally important for distinguishing changes in the business
all in all, so organizations stay lithe and react rapidly to changing business sector requests.
Information can be investigated in various ways, and charts, reports and graphs created to all the
more likely outline the outcomes.
This is the essential design of a client administration framework, however the ascent of internet
based life and portable working has brought other, more characterized frameworks to the market.
Prominent 'additional items' to the essential structure of a CMS arrangement may incorporate
cloud based frameworks that are open from any gadget (Haag, Cummings, and Dawkins, 2008).
The catchphrase in CMS is coordination – combination of information with the goal that it very
well may be put to use in a way that advantages the business, as well as clients, providers and the
Cybersecurity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
A new computer networking technology
workforce. Utilizing versatile innovation and web based life was the conspicuous subsequent
stage in this procedure, and focuses on a radical new potential client base.
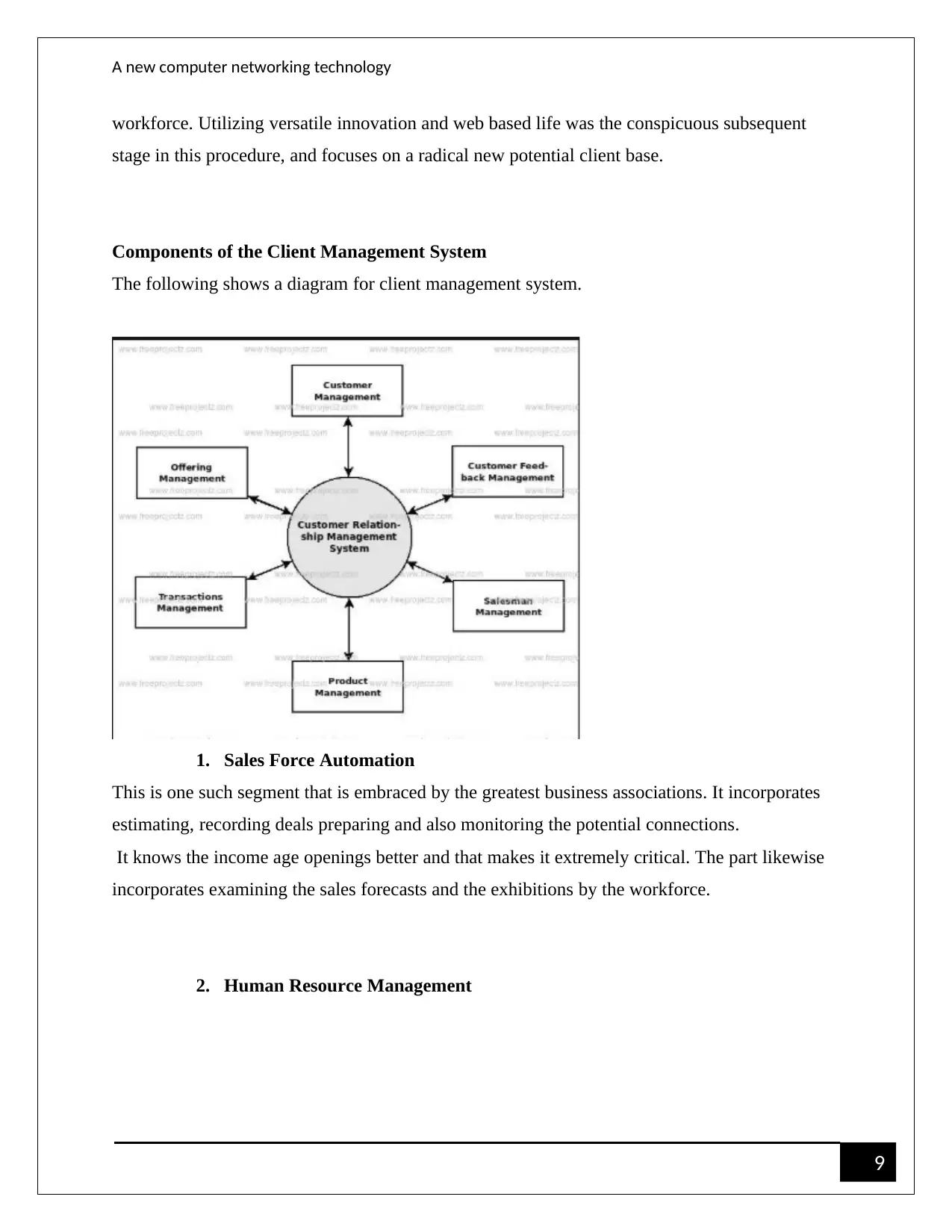
Components of the Client Management System
The following shows a diagram for client management system.
1. Sales Force Automation
This is one such segment that is embraced by the greatest business associations. It incorporates
estimating, recording deals preparing and also monitoring the potential connections.
It knows the income age openings better and that makes it extremely critical. The part likewise
incorporates examining the sales forecasts and the exhibitions by the workforce.
2. Human Resource Management
Cybersecurity
A new computer networking technology
workforce. Utilizing versatile innovation and web based life was the conspicuous subsequent
stage in this procedure, and focuses on a radical new potential client base.
Components of the Client Management System
The following shows a diagram for client management system.
1. Sales Force Automation
This is one such segment that is embraced by the greatest business associations. It incorporates
estimating, recording deals preparing and also monitoring the potential connections.
It knows the income age openings better and that makes it extremely critical. The part likewise
incorporates examining the sales forecasts and the exhibitions by the workforce.
2. Human Resource Management
Cybersecurity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
A new computer networking technology
It includes the suitable and right use of human resource and aptitudes at the specific moment and
situation. This requires to be guaranteed that the capacities and academic levels of the specialists
facilitate the endeavors endeavored by them according to their movement profiles.
It is an essential fragment for the broad scale endeavors and additionally the medium endeavors
moreover.
3. Lead Management
Lead Management as the name recommends, evades to checking the planned clients and
furthermore their dispersal.
The organizations that are benefitted by this portion of CRM the most are the business
undertakings, advancing firms and customer official core interests.
4. Customer Service
Client Management System complements on social event customer information and data, their
purchase data and precedents and incorporates giving the accumulated information to the critical
and concerned divisions.
5. Marketing
Advertising is a standout amongst the most critical segments of Customer Management System
and it alludes to the limited time exercises that are embraced by an organization with the end
goal to advance their items (Shornikov& Popov, 2018) .
6. Business Reporting
The customer care reports help the directors of an association to get a comprehension into their
step by step work organization and exercises.
7. Analytics
Examination is the route toward considering and addressing the data with the ultimate objective
to watch the examples in the market.
Cybersecurity
A new computer networking technology
It includes the suitable and right use of human resource and aptitudes at the specific moment and
situation. This requires to be guaranteed that the capacities and academic levels of the specialists
facilitate the endeavors endeavored by them according to their movement profiles.
It is an essential fragment for the broad scale endeavors and additionally the medium endeavors
moreover.
3. Lead Management
Lead Management as the name recommends, evades to checking the planned clients and
furthermore their dispersal.
The organizations that are benefitted by this portion of CRM the most are the business
undertakings, advancing firms and customer official core interests.
4. Customer Service
Client Management System complements on social event customer information and data, their
purchase data and precedents and incorporates giving the accumulated information to the critical
and concerned divisions.
5. Marketing
Advertising is a standout amongst the most critical segments of Customer Management System
and it alludes to the limited time exercises that are embraced by an organization with the end
goal to advance their items (Shornikov& Popov, 2018) .
6. Business Reporting
The customer care reports help the directors of an association to get a comprehension into their
step by step work organization and exercises.
7. Analytics
Examination is the route toward considering and addressing the data with the ultimate objective
to watch the examples in the market.
Cybersecurity

11
A new computer networking technology
Disadvantages of client management system
Customer Management System costs
How business is run affects the overall system.
Poor communication among the customers.
Lack of improper leadership
Advantages
Enhanced Informational Organization.
Customer Management System for Enhanced Communication
Improvement of ones Customer Service
Easing of daily activities.
More noteworthy proficiency for different groups.
Architecture and Design of two competing products
Systems Centre Configuration Manager (SCCM) and System Center Operations Manager
(SCOM)
Systems Centre Configuration Manager is a product issued by Microsoft which enables most of
its clients deal with many Personal Computers.
SCCM has features like remote control, settle organization, working system game plan, sort out
security and distinctive organizations.Clients of SCCM can incorporate with Microsoft InTune,
enabling them to oversee PCs associated with a business, or corporate, organize. SCCM enables
clients to oversee PCs running the Windows or macOS, servers utilizing the Linux or Unix, and
even cell phones running the Windows, iOS, and Android working frameworks (Ramallo et al.,
2015).
Cybersecurity
A new computer networking technology
Disadvantages of client management system
Customer Management System costs
How business is run affects the overall system.
Poor communication among the customers.
Lack of improper leadership
Advantages
Enhanced Informational Organization.
Customer Management System for Enhanced Communication
Improvement of ones Customer Service
Easing of daily activities.
More noteworthy proficiency for different groups.
Architecture and Design of two competing products
Systems Centre Configuration Manager (SCCM) and System Center Operations Manager
(SCOM)
Systems Centre Configuration Manager is a product issued by Microsoft which enables most of
its clients deal with many Personal Computers.
SCCM has features like remote control, settle organization, working system game plan, sort out
security and distinctive organizations.Clients of SCCM can incorporate with Microsoft InTune,
enabling them to oversee PCs associated with a business, or corporate, organize. SCCM enables
clients to oversee PCs running the Windows or macOS, servers utilizing the Linux or Unix, and
even cell phones running the Windows, iOS, and Android working frameworks (Ramallo et al.,
2015).
Cybersecurity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





