Cloud Computing Architecture, Automation System for Regional Gardens
VerifiedAdded on 2023/06/14
|28
|3283
|419
Report
AI Summary
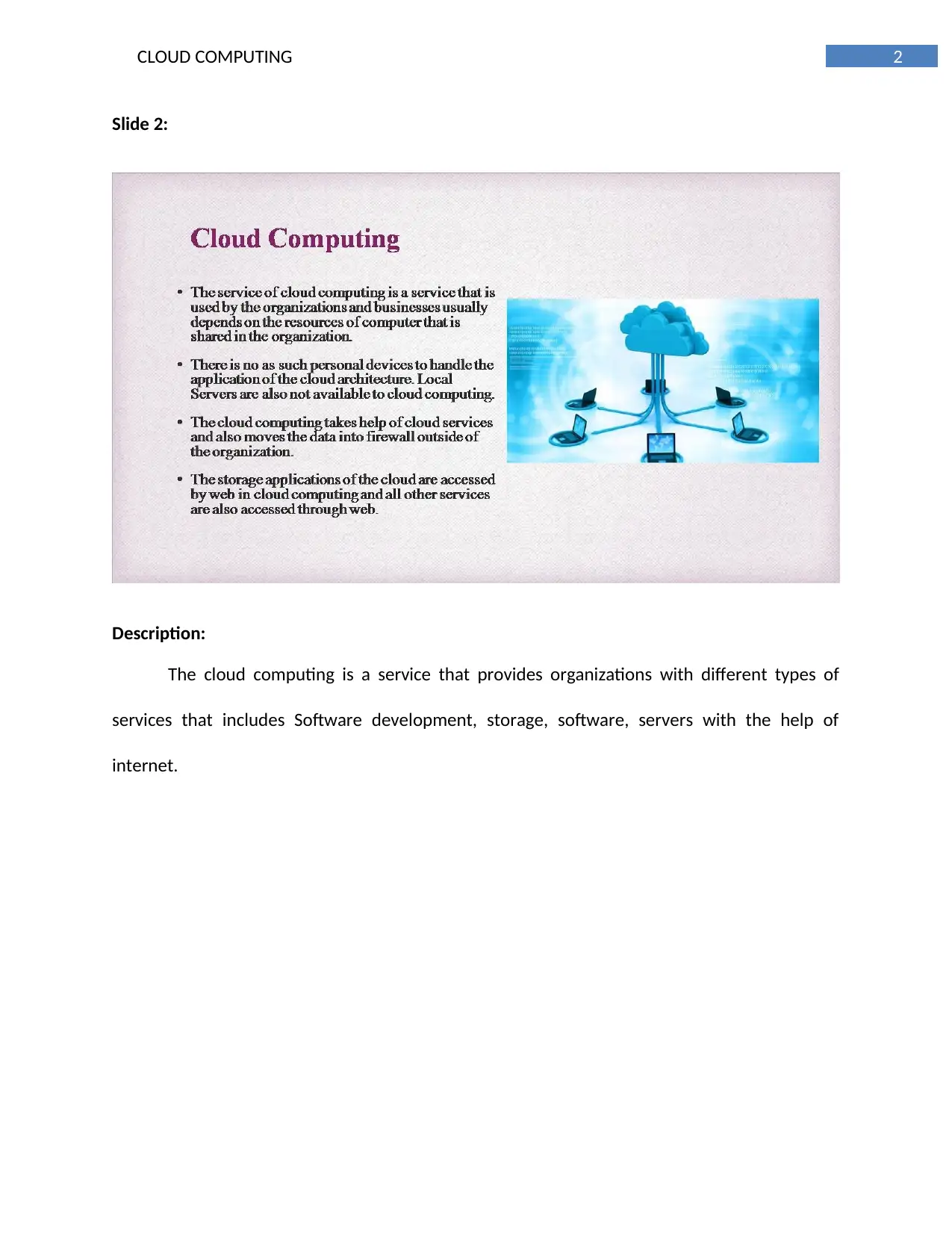
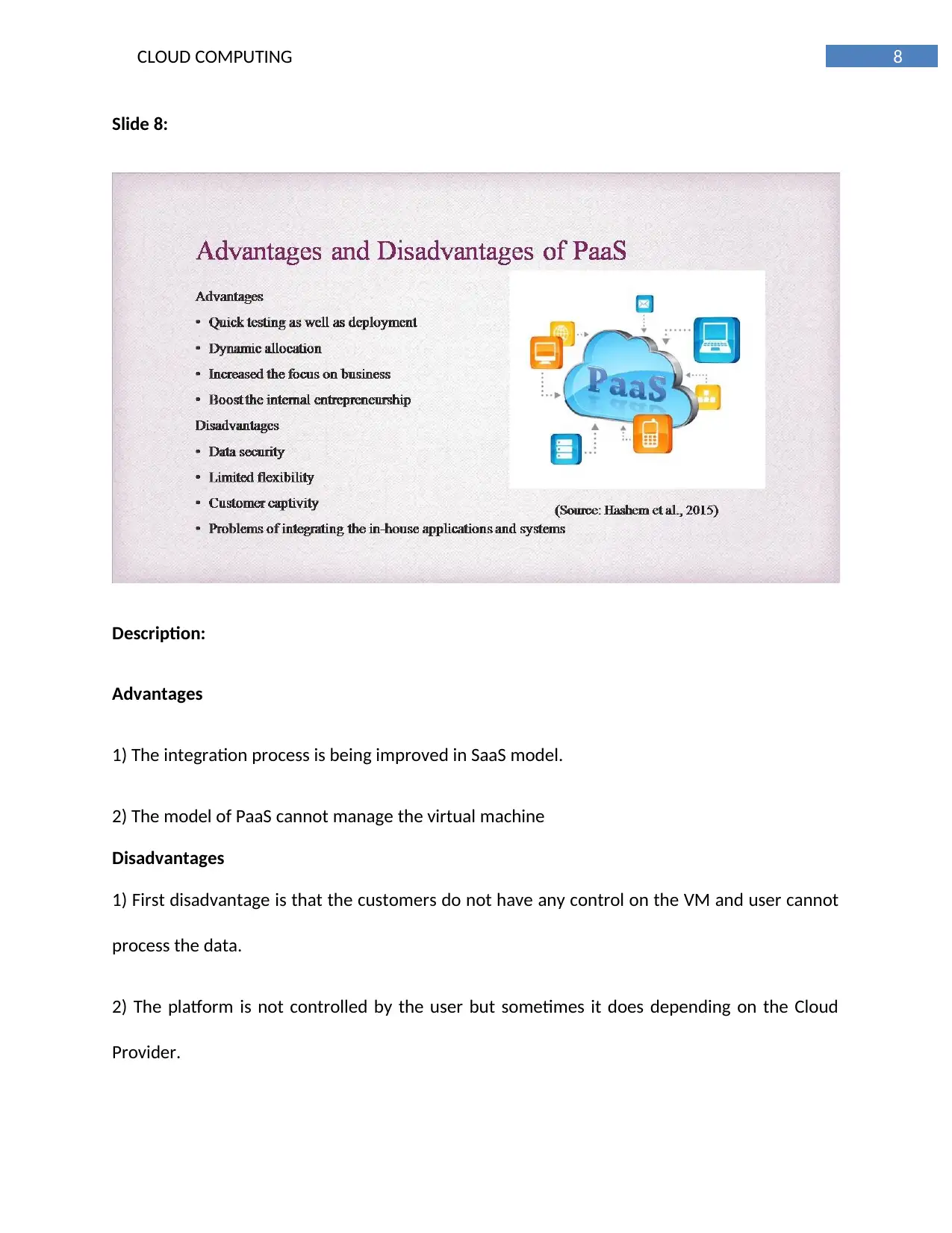
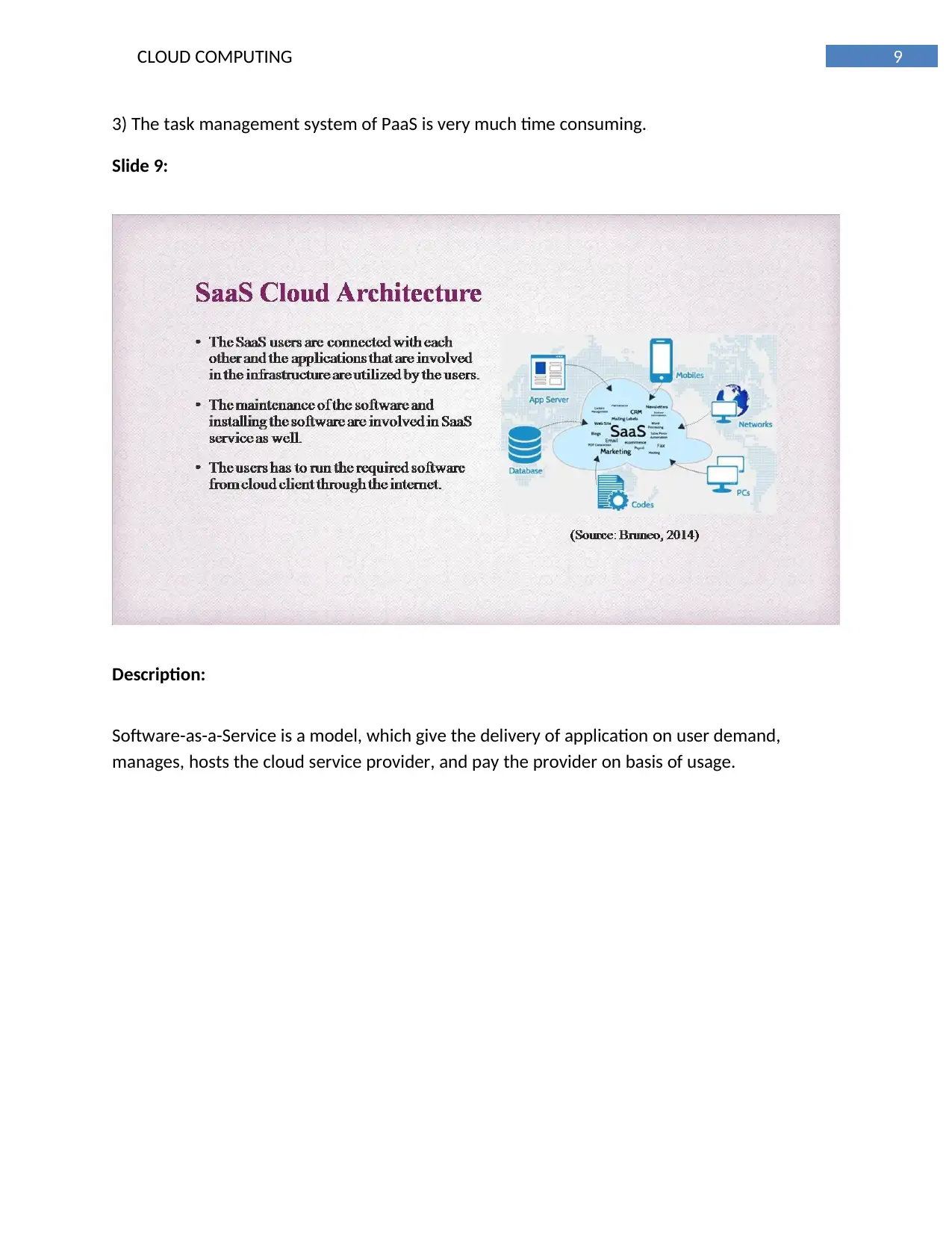
This report provides a comprehensive overview of cloud computing architectures, focusing on IaaS, PaaS, and SaaS models, and their application to Regional Gardens Ltd. It explores potential office automation systems, comparing integrated and traditional approaches, and recommends a hybrid model for optimal efficiency. The report also delves into web infrastructure differences between IaaS and PaaS, and evaluates the implementation of Microsoft SharePoint 2010, ultimately recommending the Infrastructure-as-a-Service model for its versatility and control. The document provides a detailed analysis of cloud computing solutions tailored for Regional Gardens Ltd, offering insights into system architecture, automation strategies, and infrastructure implementation. Desklib offers a wealth of resources, including past papers and solved assignments, to support students in their academic endeavors.
1 out of 28















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)