Cloud Privacy and Security: Analysis of Employee Data for DAS
VerifiedAdded on 2020/02/24
|18
|2193
|34
Report
AI Summary
This report, a student's assignment, delves into the critical aspects of cloud privacy and security, specifically focusing on the protection of employee data within a governmental context. The document meticulously analyzes various threats and risks, including insider threats, cyber attacks, digital identity issues, and the implications of using different cloud service models like PaaS and hybrid cloud architectures. It evaluates the security of employee data, digital identity issues, and provider solution issues, including the sensitivity of data across different jurisdictions. The report proposes a hybrid cloud solution to mitigate risks and enhance security, providing a detailed risk assessment of traditional versus cloud-based data centers. The analysis covers topics such as data sensitivity, PaaS risks, and the benefits of distributed data centers, concluding that a hybrid cloud platform significantly reduces the risk profile for both employee data security and privacy. The report also includes appendices showing communication and meeting details.

Running head; CLOUD PRIVACY AND SECURITY 1
Cloud Privacy and Security
Student 1 Student ID
Student 2 Student ID
Student 3 Student ID
Date
Cloud Privacy and Security
Student 1 Student ID
Student 2 Student ID
Student 3 Student ID
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head; CLOUD PRIVACY AND SECURITY 2
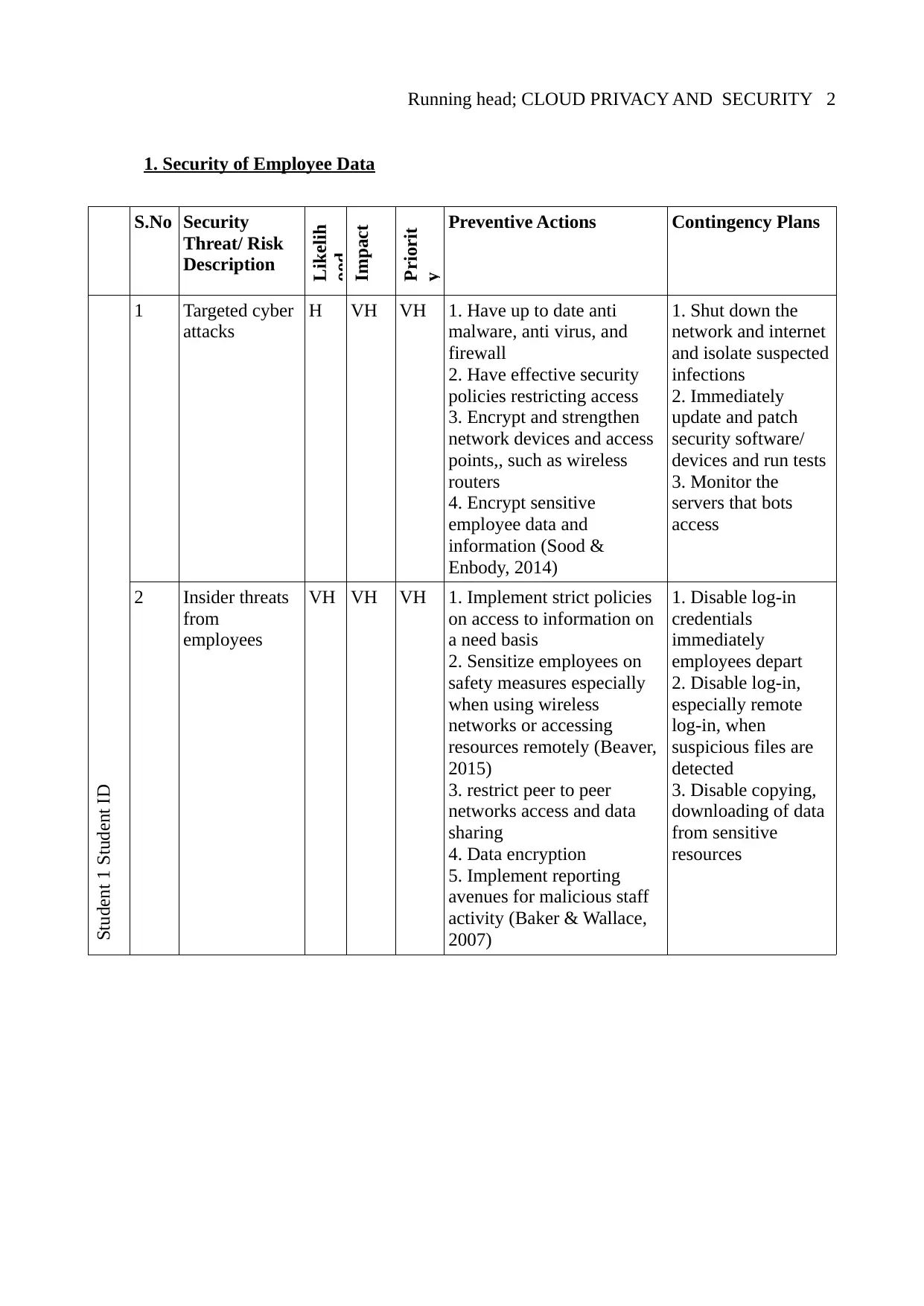
1. Security of Employee Data
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
Student 1 Student ID
1 Targeted cyber
attacks
H VH VH 1. Have up to date anti
malware, anti virus, and
firewall
2. Have effective security
policies restricting access
3. Encrypt and strengthen
network devices and access
points,, such as wireless
routers
4. Encrypt sensitive
employee data and
information (Sood &
Enbody, 2014)
1. Shut down the
network and internet
and isolate suspected
infections
2. Immediately
update and patch
security software/
devices and run tests
3. Monitor the
servers that bots
access
2 Insider threats
from
employees
VH VH VH 1. Implement strict policies
on access to information on
a need basis
2. Sensitize employees on
safety measures especially
when using wireless
networks or accessing
resources remotely (Beaver,
2015)
3. restrict peer to peer
networks access and data
sharing
4. Data encryption
5. Implement reporting
avenues for malicious staff
activity (Baker & Wallace,
2007)
1. Disable log-in
credentials
immediately
employees depart
2. Disable log-in,
especially remote
log-in, when
suspicious files are
detected
3. Disable copying,
downloading of data
from sensitive
resources
1. Security of Employee Data
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
Student 1 Student ID
1 Targeted cyber
attacks
H VH VH 1. Have up to date anti
malware, anti virus, and
firewall
2. Have effective security
policies restricting access
3. Encrypt and strengthen
network devices and access
points,, such as wireless
routers
4. Encrypt sensitive
employee data and
information (Sood &
Enbody, 2014)
1. Shut down the
network and internet
and isolate suspected
infections
2. Immediately
update and patch
security software/
devices and run tests
3. Monitor the
servers that bots
access
2 Insider threats
from
employees
VH VH VH 1. Implement strict policies
on access to information on
a need basis
2. Sensitize employees on
safety measures especially
when using wireless
networks or accessing
resources remotely (Beaver,
2015)
3. restrict peer to peer
networks access and data
sharing
4. Data encryption
5. Implement reporting
avenues for malicious staff
activity (Baker & Wallace,
2007)
1. Disable log-in
credentials
immediately
employees depart
2. Disable log-in,
especially remote
log-in, when
suspicious files are
detected
3. Disable copying,
downloading of data
from sensitive
resources
Running head; CLOUD PRIVACY AND SECURITY 3
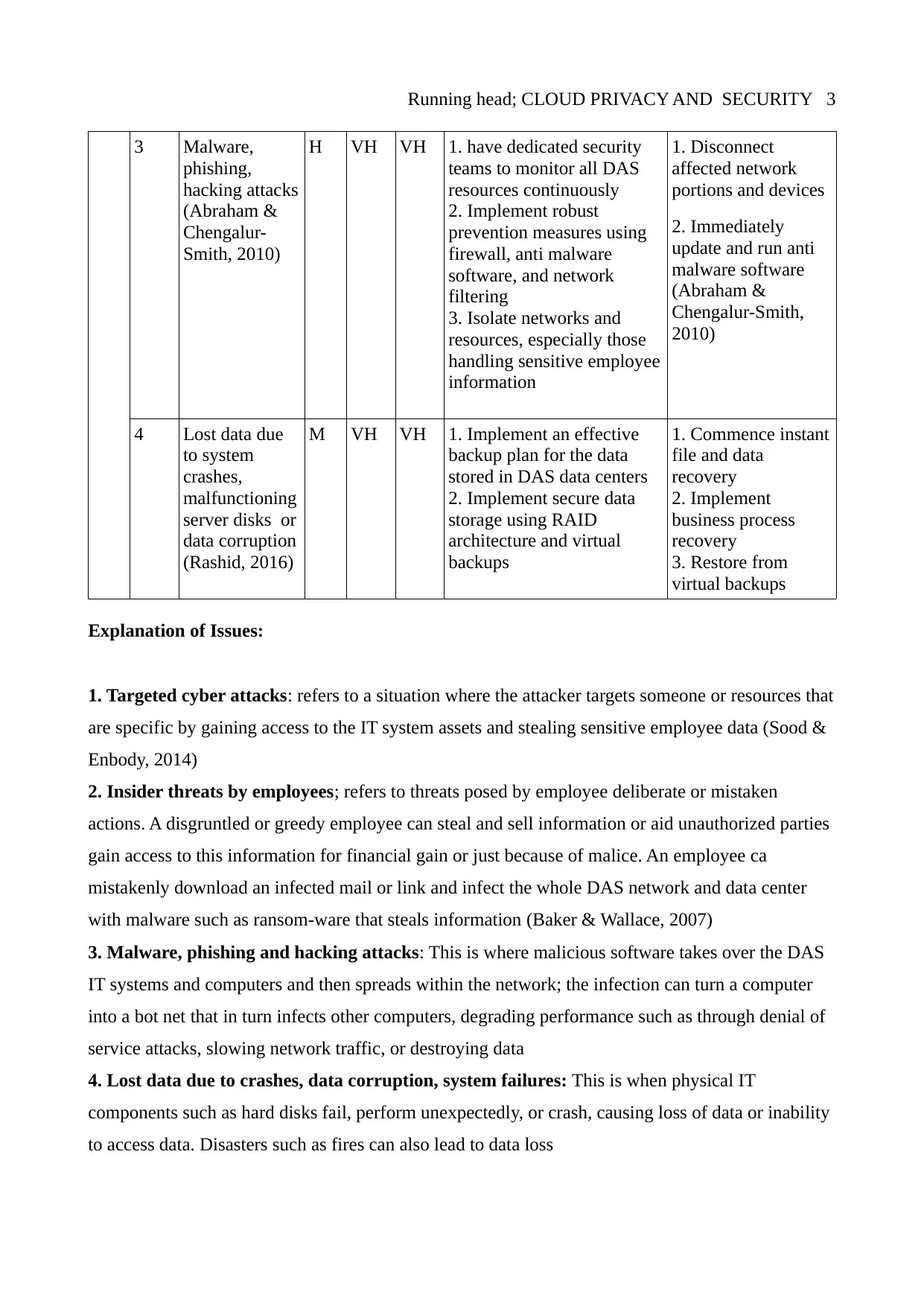
3 Malware,
phishing,
hacking attacks
(Abraham &
Chengalur-
Smith, 2010)
H VH VH 1. have dedicated security
teams to monitor all DAS
resources continuously
2. Implement robust
prevention measures using
firewall, anti malware
software, and network
filtering
3. Isolate networks and
resources, especially those
handling sensitive employee
information
1. Disconnect
affected network
portions and devices
2. Immediately
update and run anti
malware software
(Abraham &
Chengalur-Smith,
2010)
4 Lost data due
to system
crashes,
malfunctioning
server disks or
data corruption
(Rashid, 2016)
M VH VH 1. Implement an effective
backup plan for the data
stored in DAS data centers
2. Implement secure data
storage using RAID
architecture and virtual
backups
1. Commence instant
file and data
recovery
2. Implement
business process
recovery
3. Restore from
virtual backups
Explanation of Issues:
1. Targeted cyber attacks: refers to a situation where the attacker targets someone or resources that
are specific by gaining access to the IT system assets and stealing sensitive employee data (Sood &
Enbody, 2014)
2. Insider threats by employees; refers to threats posed by employee deliberate or mistaken
actions. A disgruntled or greedy employee can steal and sell information or aid unauthorized parties
gain access to this information for financial gain or just because of malice. An employee ca
mistakenly download an infected mail or link and infect the whole DAS network and data center
with malware such as ransom-ware that steals information (Baker & Wallace, 2007)
3. Malware, phishing and hacking attacks: This is where malicious software takes over the DAS
IT systems and computers and then spreads within the network; the infection can turn a computer
into a bot net that in turn infects other computers, degrading performance such as through denial of
service attacks, slowing network traffic, or destroying data
4. Lost data due to crashes, data corruption, system failures: This is when physical IT
components such as hard disks fail, perform unexpectedly, or crash, causing loss of data or inability
to access data. Disasters such as fires can also lead to data loss
3 Malware,
phishing,
hacking attacks
(Abraham &
Chengalur-
Smith, 2010)
H VH VH 1. have dedicated security
teams to monitor all DAS
resources continuously
2. Implement robust
prevention measures using
firewall, anti malware
software, and network
filtering
3. Isolate networks and
resources, especially those
handling sensitive employee
information
1. Disconnect
affected network
portions and devices
2. Immediately
update and run anti
malware software
(Abraham &
Chengalur-Smith,
2010)
4 Lost data due
to system
crashes,
malfunctioning
server disks or
data corruption
(Rashid, 2016)
M VH VH 1. Implement an effective
backup plan for the data
stored in DAS data centers
2. Implement secure data
storage using RAID
architecture and virtual
backups
1. Commence instant
file and data
recovery
2. Implement
business process
recovery
3. Restore from
virtual backups
Explanation of Issues:
1. Targeted cyber attacks: refers to a situation where the attacker targets someone or resources that
are specific by gaining access to the IT system assets and stealing sensitive employee data (Sood &
Enbody, 2014)
2. Insider threats by employees; refers to threats posed by employee deliberate or mistaken
actions. A disgruntled or greedy employee can steal and sell information or aid unauthorized parties
gain access to this information for financial gain or just because of malice. An employee ca
mistakenly download an infected mail or link and infect the whole DAS network and data center
with malware such as ransom-ware that steals information (Baker & Wallace, 2007)
3. Malware, phishing and hacking attacks: This is where malicious software takes over the DAS
IT systems and computers and then spreads within the network; the infection can turn a computer
into a bot net that in turn infects other computers, degrading performance such as through denial of
service attacks, slowing network traffic, or destroying data
4. Lost data due to crashes, data corruption, system failures: This is when physical IT
components such as hard disks fail, perform unexpectedly, or crash, causing loss of data or inability
to access data. Disasters such as fires can also lead to data loss
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head; CLOUD PRIVACY AND SECURITY 4
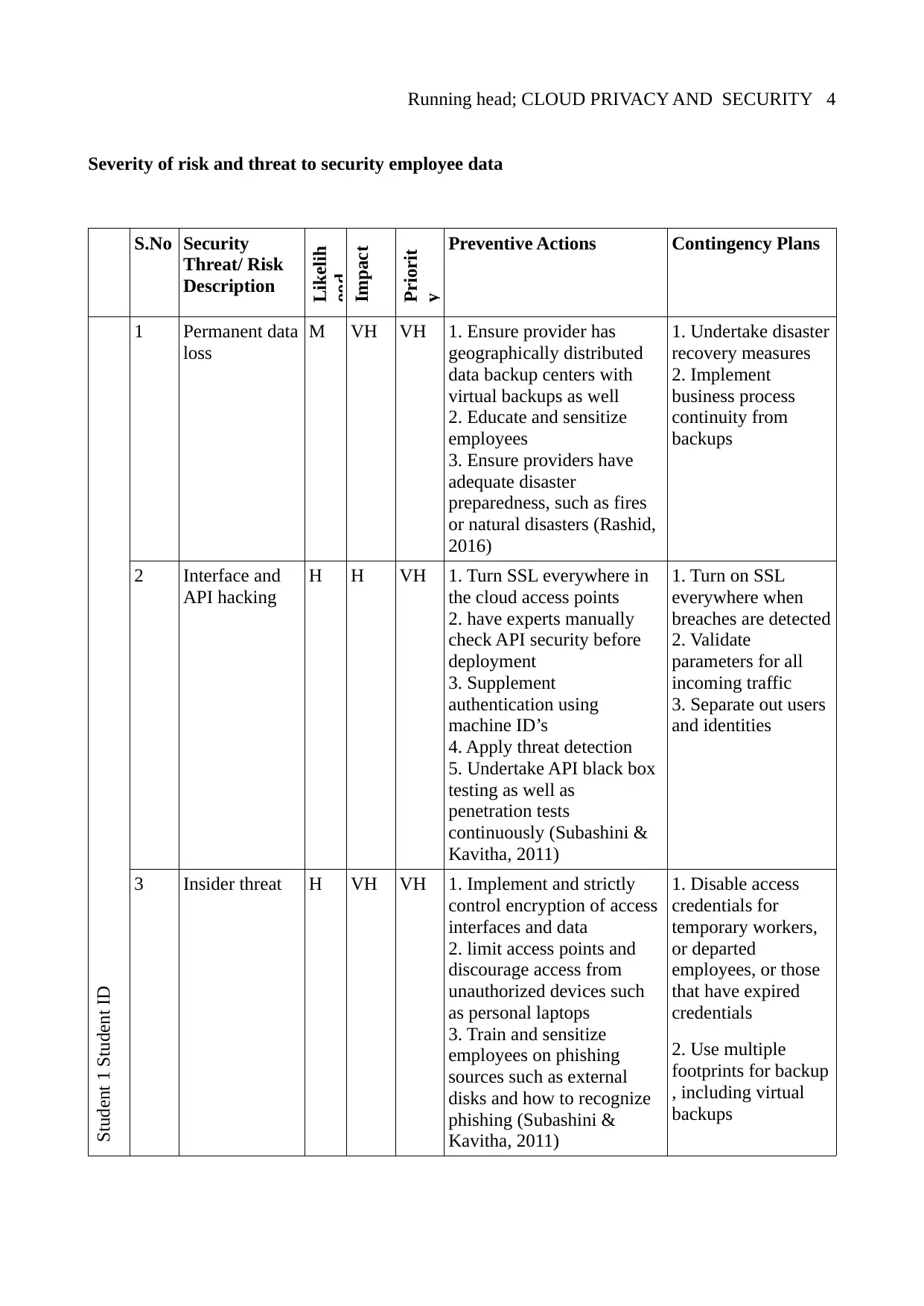
Severity of risk and threat to security employee data
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
Student 1 Student ID
1 Permanent data
loss
M VH VH 1. Ensure provider has
geographically distributed
data backup centers with
virtual backups as well
2. Educate and sensitize
employees
3. Ensure providers have
adequate disaster
preparedness, such as fires
or natural disasters (Rashid,
2016)
1. Undertake disaster
recovery measures
2. Implement
business process
continuity from
backups
2 Interface and
API hacking
H H VH 1. Turn SSL everywhere in
the cloud access points
2. have experts manually
check API security before
deployment
3. Supplement
authentication using
machine ID’s
4. Apply threat detection
5. Undertake API black box
testing as well as
penetration tests
continuously (Subashini &
Kavitha, 2011)
1. Turn on SSL
everywhere when
breaches are detected
2. Validate
parameters for all
incoming traffic
3. Separate out users
and identities
3 Insider threat H VH VH 1. Implement and strictly
control encryption of access
interfaces and data
2. limit access points and
discourage access from
unauthorized devices such
as personal laptops
3. Train and sensitize
employees on phishing
sources such as external
disks and how to recognize
phishing (Subashini &
Kavitha, 2011)
1. Disable access
credentials for
temporary workers,
or departed
employees, or those
that have expired
credentials
2. Use multiple
footprints for backup
, including virtual
backups
Severity of risk and threat to security employee data
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
Student 1 Student ID
1 Permanent data
loss
M VH VH 1. Ensure provider has
geographically distributed
data backup centers with
virtual backups as well
2. Educate and sensitize
employees
3. Ensure providers have
adequate disaster
preparedness, such as fires
or natural disasters (Rashid,
2016)
1. Undertake disaster
recovery measures
2. Implement
business process
continuity from
backups
2 Interface and
API hacking
H H VH 1. Turn SSL everywhere in
the cloud access points
2. have experts manually
check API security before
deployment
3. Supplement
authentication using
machine ID’s
4. Apply threat detection
5. Undertake API black box
testing as well as
penetration tests
continuously (Subashini &
Kavitha, 2011)
1. Turn on SSL
everywhere when
breaches are detected
2. Validate
parameters for all
incoming traffic
3. Separate out users
and identities
3 Insider threat H VH VH 1. Implement and strictly
control encryption of access
interfaces and data
2. limit access points and
discourage access from
unauthorized devices such
as personal laptops
3. Train and sensitize
employees on phishing
sources such as external
disks and how to recognize
phishing (Subashini &
Kavitha, 2011)
1. Disable access
credentials for
temporary workers,
or departed
employees, or those
that have expired
credentials
2. Use multiple
footprints for backup
, including virtual
backups
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head; CLOUD PRIVACY AND SECURITY 5
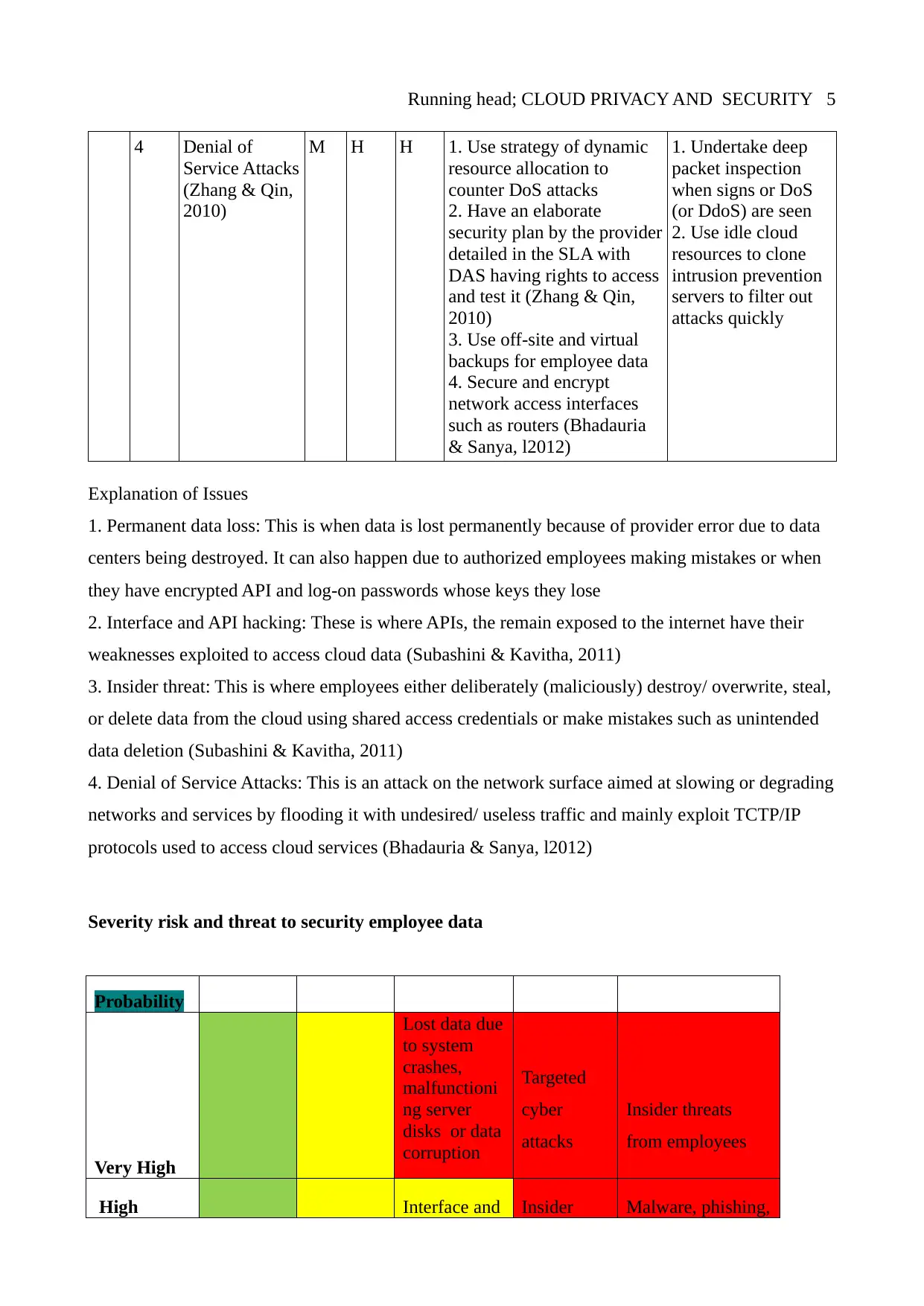
4 Denial of
Service Attacks
(Zhang & Qin,
2010)
M H H 1. Use strategy of dynamic
resource allocation to
counter DoS attacks
2. Have an elaborate
security plan by the provider
detailed in the SLA with
DAS having rights to access
and test it (Zhang & Qin,
2010)
3. Use off-site and virtual
backups for employee data
4. Secure and encrypt
network access interfaces
such as routers (Bhadauria
& Sanya, l2012)
1. Undertake deep
packet inspection
when signs or DoS
(or DdoS) are seen
2. Use idle cloud
resources to clone
intrusion prevention
servers to filter out
attacks quickly
Explanation of Issues
1. Permanent data loss: This is when data is lost permanently because of provider error due to data
centers being destroyed. It can also happen due to authorized employees making mistakes or when
they have encrypted API and log-on passwords whose keys they lose
2. Interface and API hacking: These is where APIs, the remain exposed to the internet have their
weaknesses exploited to access cloud data (Subashini & Kavitha, 2011)
3. Insider threat: This is where employees either deliberately (maliciously) destroy/ overwrite, steal,
or delete data from the cloud using shared access credentials or make mistakes such as unintended
data deletion (Subashini & Kavitha, 2011)
4. Denial of Service Attacks: This is an attack on the network surface aimed at slowing or degrading
networks and services by flooding it with undesired/ useless traffic and mainly exploit TCTP/IP
protocols used to access cloud services (Bhadauria & Sanya, l2012)
Severity risk and threat to security employee data
Probability
Very High
Lost data due
to system
crashes,
malfunctioni
ng server
disks or data
corruption
Targeted
cyber
attacks
Insider threats
from employees
High Interface and Insider Malware, phishing,
4 Denial of
Service Attacks
(Zhang & Qin,
2010)
M H H 1. Use strategy of dynamic
resource allocation to
counter DoS attacks
2. Have an elaborate
security plan by the provider
detailed in the SLA with
DAS having rights to access
and test it (Zhang & Qin,
2010)
3. Use off-site and virtual
backups for employee data
4. Secure and encrypt
network access interfaces
such as routers (Bhadauria
& Sanya, l2012)
1. Undertake deep
packet inspection
when signs or DoS
(or DdoS) are seen
2. Use idle cloud
resources to clone
intrusion prevention
servers to filter out
attacks quickly
Explanation of Issues
1. Permanent data loss: This is when data is lost permanently because of provider error due to data
centers being destroyed. It can also happen due to authorized employees making mistakes or when
they have encrypted API and log-on passwords whose keys they lose
2. Interface and API hacking: These is where APIs, the remain exposed to the internet have their
weaknesses exploited to access cloud data (Subashini & Kavitha, 2011)
3. Insider threat: This is where employees either deliberately (maliciously) destroy/ overwrite, steal,
or delete data from the cloud using shared access credentials or make mistakes such as unintended
data deletion (Subashini & Kavitha, 2011)
4. Denial of Service Attacks: This is an attack on the network surface aimed at slowing or degrading
networks and services by flooding it with undesired/ useless traffic and mainly exploit TCTP/IP
protocols used to access cloud services (Bhadauria & Sanya, l2012)
Severity risk and threat to security employee data
Probability
Very High
Lost data due
to system
crashes,
malfunctioni
ng server
disks or data
corruption
Targeted
cyber
attacks
Insider threats
from employees
High Interface and Insider Malware, phishing,
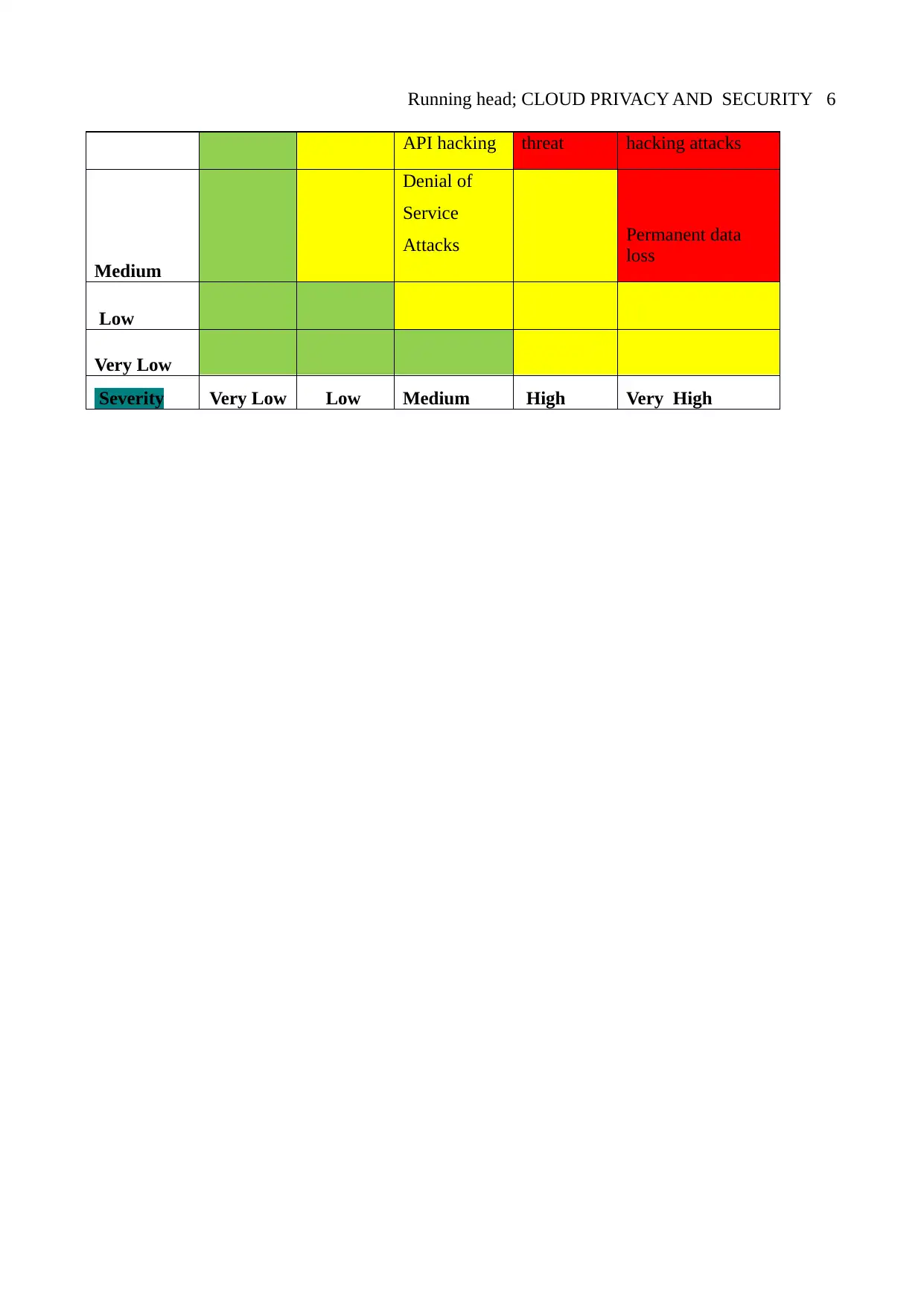
Running head; CLOUD PRIVACY AND SECURITY 6
API hacking threat hacking attacks
Medium
Denial of
Service
Attacks Permanent data
loss
Low
Very Low
Severity Very Low Low Medium High Very High
API hacking threat hacking attacks
Medium
Denial of
Service
Attacks Permanent data
loss
Low
Very Low
Severity Very Low Low Medium High Very High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
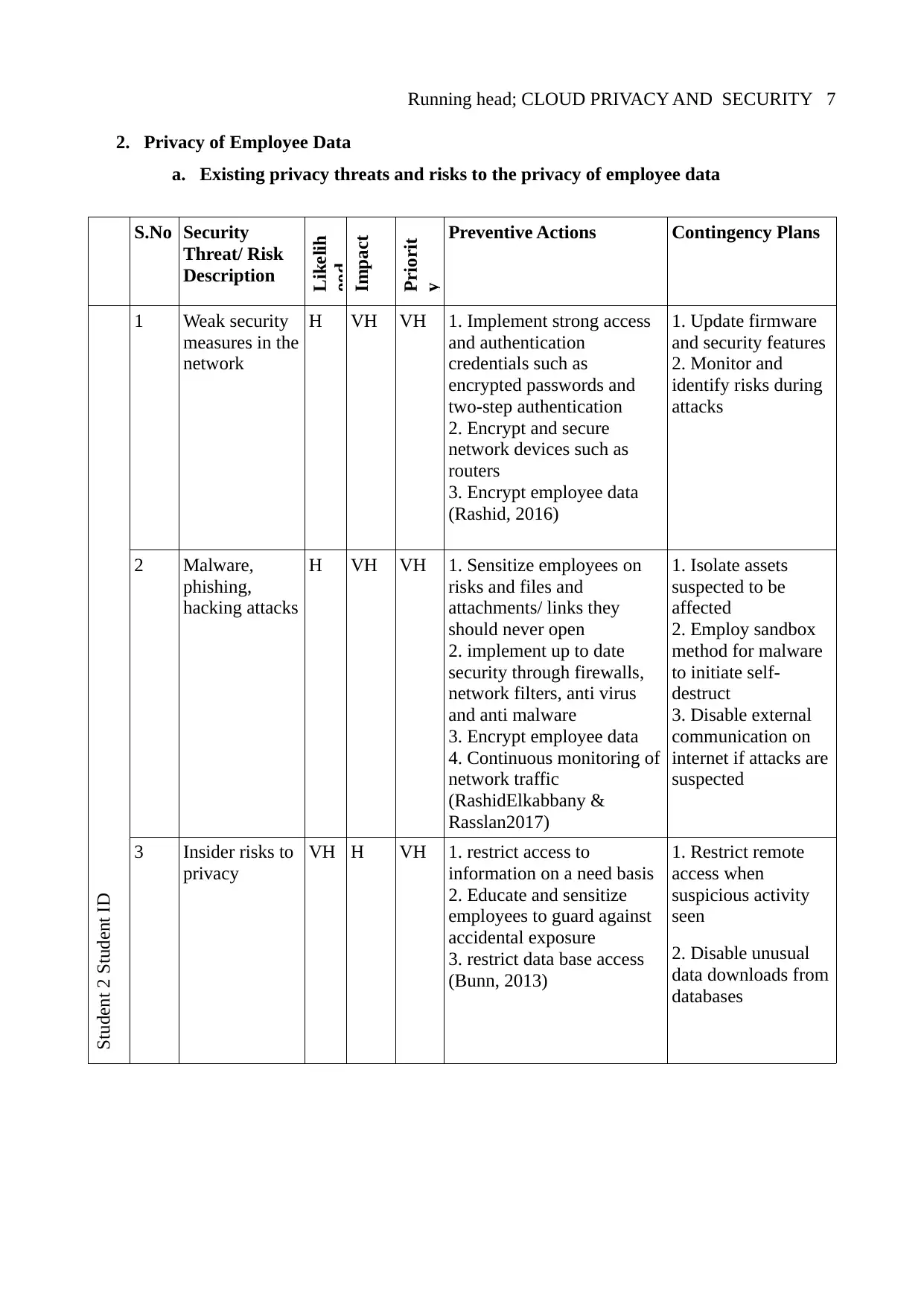
Running head; CLOUD PRIVACY AND SECURITY 7
2. Privacy of Employee Data
a. Existing privacy threats and risks to the privacy of employee data
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
Student 2 Student ID
1 Weak security
measures in the
network
H VH VH 1. Implement strong access
and authentication
credentials such as
encrypted passwords and
two-step authentication
2. Encrypt and secure
network devices such as
routers
3. Encrypt employee data
(Rashid, 2016)
1. Update firmware
and security features
2. Monitor and
identify risks during
attacks
2 Malware,
phishing,
hacking attacks
H VH VH 1. Sensitize employees on
risks and files and
attachments/ links they
should never open
2. implement up to date
security through firewalls,
network filters, anti virus
and anti malware
3. Encrypt employee data
4. Continuous monitoring of
network traffic
(RashidElkabbany &
Rasslan2017)
1. Isolate assets
suspected to be
affected
2. Employ sandbox
method for malware
to initiate self-
destruct
3. Disable external
communication on
internet if attacks are
suspected
3 Insider risks to
privacy
VH H VH 1. restrict access to
information on a need basis
2. Educate and sensitize
employees to guard against
accidental exposure
3. restrict data base access
(Bunn, 2013)
1. Restrict remote
access when
suspicious activity
seen
2. Disable unusual
data downloads from
databases
2. Privacy of Employee Data
a. Existing privacy threats and risks to the privacy of employee data
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
Student 2 Student ID
1 Weak security
measures in the
network
H VH VH 1. Implement strong access
and authentication
credentials such as
encrypted passwords and
two-step authentication
2. Encrypt and secure
network devices such as
routers
3. Encrypt employee data
(Rashid, 2016)
1. Update firmware
and security features
2. Monitor and
identify risks during
attacks
2 Malware,
phishing,
hacking attacks
H VH VH 1. Sensitize employees on
risks and files and
attachments/ links they
should never open
2. implement up to date
security through firewalls,
network filters, anti virus
and anti malware
3. Encrypt employee data
4. Continuous monitoring of
network traffic
(RashidElkabbany &
Rasslan2017)
1. Isolate assets
suspected to be
affected
2. Employ sandbox
method for malware
to initiate self-
destruct
3. Disable external
communication on
internet if attacks are
suspected
3 Insider risks to
privacy
VH H VH 1. restrict access to
information on a need basis
2. Educate and sensitize
employees to guard against
accidental exposure
3. restrict data base access
(Bunn, 2013)
1. Restrict remote
access when
suspicious activity
seen
2. Disable unusual
data downloads from
databases
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
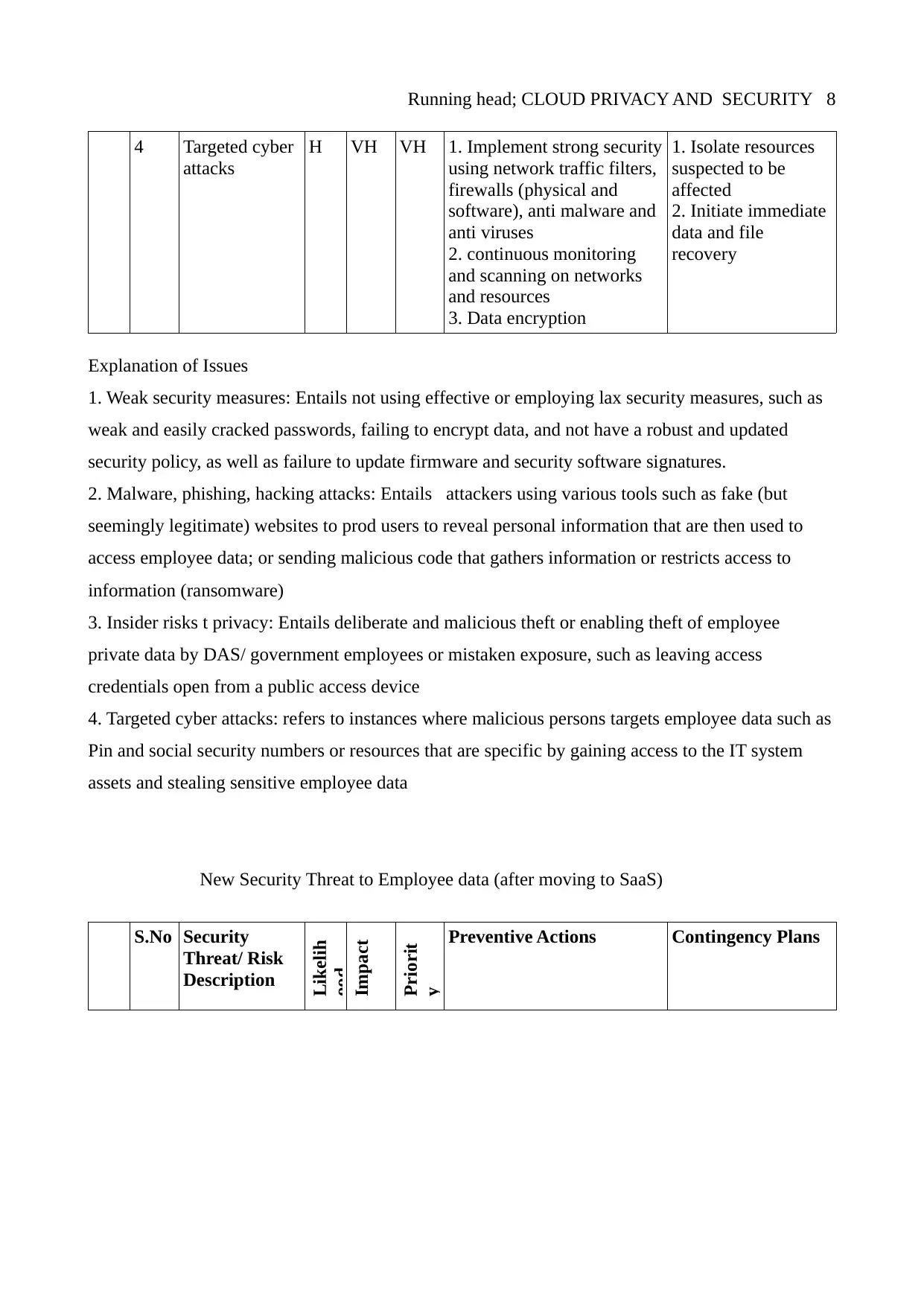
Running head; CLOUD PRIVACY AND SECURITY 8
4 Targeted cyber
attacks
H VH VH 1. Implement strong security
using network traffic filters,
firewalls (physical and
software), anti malware and
anti viruses
2. continuous monitoring
and scanning on networks
and resources
3. Data encryption
1. Isolate resources
suspected to be
affected
2. Initiate immediate
data and file
recovery
Explanation of Issues
1. Weak security measures: Entails not using effective or employing lax security measures, such as
weak and easily cracked passwords, failing to encrypt data, and not have a robust and updated
security policy, as well as failure to update firmware and security software signatures.
2. Malware, phishing, hacking attacks: Entails attackers using various tools such as fake (but
seemingly legitimate) websites to prod users to reveal personal information that are then used to
access employee data; or sending malicious code that gathers information or restricts access to
information (ransomware)
3. Insider risks t privacy: Entails deliberate and malicious theft or enabling theft of employee
private data by DAS/ government employees or mistaken exposure, such as leaving access
credentials open from a public access device
4. Targeted cyber attacks: refers to instances where malicious persons targets employee data such as
Pin and social security numbers or resources that are specific by gaining access to the IT system
assets and stealing sensitive employee data
New Security Threat to Employee data (after moving to SaaS)
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
4 Targeted cyber
attacks
H VH VH 1. Implement strong security
using network traffic filters,
firewalls (physical and
software), anti malware and
anti viruses
2. continuous monitoring
and scanning on networks
and resources
3. Data encryption
1. Isolate resources
suspected to be
affected
2. Initiate immediate
data and file
recovery
Explanation of Issues
1. Weak security measures: Entails not using effective or employing lax security measures, such as
weak and easily cracked passwords, failing to encrypt data, and not have a robust and updated
security policy, as well as failure to update firmware and security software signatures.
2. Malware, phishing, hacking attacks: Entails attackers using various tools such as fake (but
seemingly legitimate) websites to prod users to reveal personal information that are then used to
access employee data; or sending malicious code that gathers information or restricts access to
information (ransomware)
3. Insider risks t privacy: Entails deliberate and malicious theft or enabling theft of employee
private data by DAS/ government employees or mistaken exposure, such as leaving access
credentials open from a public access device
4. Targeted cyber attacks: refers to instances where malicious persons targets employee data such as
Pin and social security numbers or resources that are specific by gaining access to the IT system
assets and stealing sensitive employee data
New Security Threat to Employee data (after moving to SaaS)
S.No Security
Threat/ Risk
Description
Likelih
ood
Impact
Priorit
y
Preventive Actions Contingency Plans
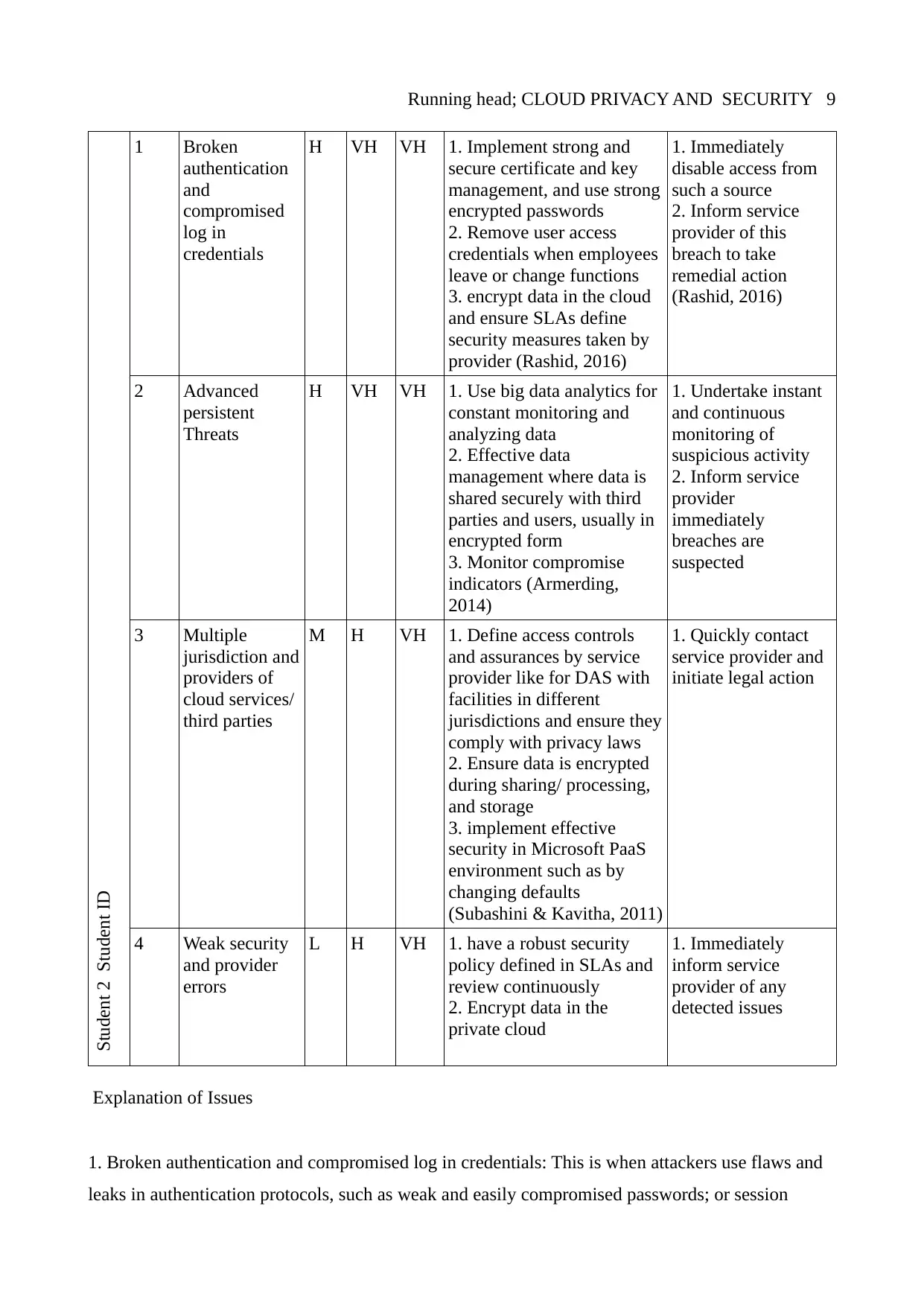
Running head; CLOUD PRIVACY AND SECURITY 9
Student 2 Student ID
1 Broken
authentication
and
compromised
log in
credentials
H VH VH 1. Implement strong and
secure certificate and key
management, and use strong
encrypted passwords
2. Remove user access
credentials when employees
leave or change functions
3. encrypt data in the cloud
and ensure SLAs define
security measures taken by
provider (Rashid, 2016)
1. Immediately
disable access from
such a source
2. Inform service
provider of this
breach to take
remedial action
(Rashid, 2016)
2 Advanced
persistent
Threats
H VH VH 1. Use big data analytics for
constant monitoring and
analyzing data
2. Effective data
management where data is
shared securely with third
parties and users, usually in
encrypted form
3. Monitor compromise
indicators (Armerding,
2014)
1. Undertake instant
and continuous
monitoring of
suspicious activity
2. Inform service
provider
immediately
breaches are
suspected
3 Multiple
jurisdiction and
providers of
cloud services/
third parties
M H VH 1. Define access controls
and assurances by service
provider like for DAS with
facilities in different
jurisdictions and ensure they
comply with privacy laws
2. Ensure data is encrypted
during sharing/ processing,
and storage
3. implement effective
security in Microsoft PaaS
environment such as by
changing defaults
(Subashini & Kavitha, 2011)
1. Quickly contact
service provider and
initiate legal action
4 Weak security
and provider
errors
L H VH 1. have a robust security
policy defined in SLAs and
review continuously
2. Encrypt data in the
private cloud
1. Immediately
inform service
provider of any
detected issues
Explanation of Issues
1. Broken authentication and compromised log in credentials: This is when attackers use flaws and
leaks in authentication protocols, such as weak and easily compromised passwords; or session
Student 2 Student ID
1 Broken
authentication
and
compromised
log in
credentials
H VH VH 1. Implement strong and
secure certificate and key
management, and use strong
encrypted passwords
2. Remove user access
credentials when employees
leave or change functions
3. encrypt data in the cloud
and ensure SLAs define
security measures taken by
provider (Rashid, 2016)
1. Immediately
disable access from
such a source
2. Inform service
provider of this
breach to take
remedial action
(Rashid, 2016)
2 Advanced
persistent
Threats
H VH VH 1. Use big data analytics for
constant monitoring and
analyzing data
2. Effective data
management where data is
shared securely with third
parties and users, usually in
encrypted form
3. Monitor compromise
indicators (Armerding,
2014)
1. Undertake instant
and continuous
monitoring of
suspicious activity
2. Inform service
provider
immediately
breaches are
suspected
3 Multiple
jurisdiction and
providers of
cloud services/
third parties
M H VH 1. Define access controls
and assurances by service
provider like for DAS with
facilities in different
jurisdictions and ensure they
comply with privacy laws
2. Ensure data is encrypted
during sharing/ processing,
and storage
3. implement effective
security in Microsoft PaaS
environment such as by
changing defaults
(Subashini & Kavitha, 2011)
1. Quickly contact
service provider and
initiate legal action
4 Weak security
and provider
errors
L H VH 1. have a robust security
policy defined in SLAs and
review continuously
2. Encrypt data in the
private cloud
1. Immediately
inform service
provider of any
detected issues
Explanation of Issues
1. Broken authentication and compromised log in credentials: This is when attackers use flaws and
leaks in authentication protocols, such as weak and easily compromised passwords; or session
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
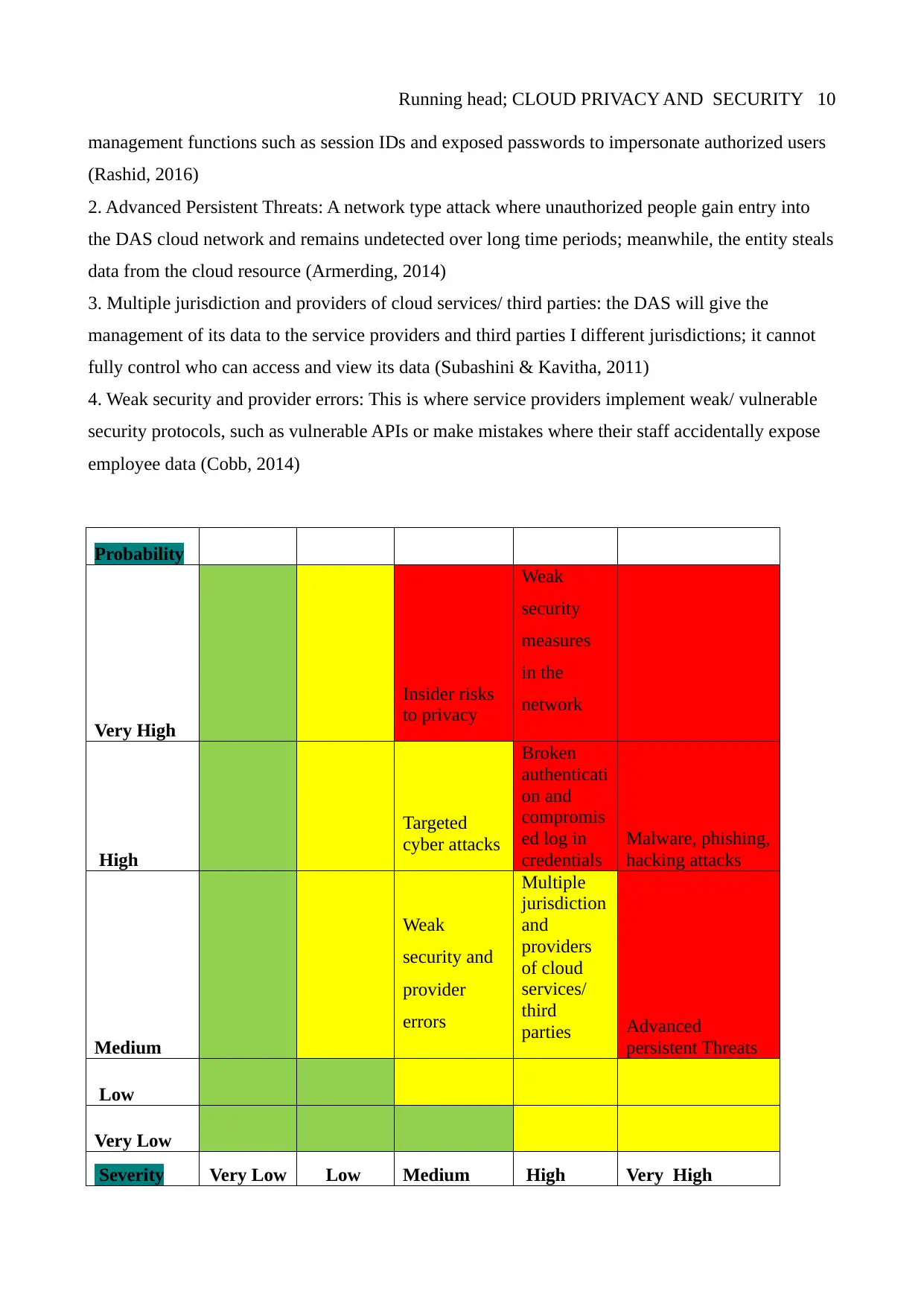
Running head; CLOUD PRIVACY AND SECURITY 10
management functions such as session IDs and exposed passwords to impersonate authorized users
(Rashid, 2016)
2. Advanced Persistent Threats: A network type attack where unauthorized people gain entry into
the DAS cloud network and remains undetected over long time periods; meanwhile, the entity steals
data from the cloud resource (Armerding, 2014)
3. Multiple jurisdiction and providers of cloud services/ third parties: the DAS will give the
management of its data to the service providers and third parties I different jurisdictions; it cannot
fully control who can access and view its data (Subashini & Kavitha, 2011)
4. Weak security and provider errors: This is where service providers implement weak/ vulnerable
security protocols, such as vulnerable APIs or make mistakes where their staff accidentally expose
employee data (Cobb, 2014)
Probability
Very High
Insider risks
to privacy
Weak
security
measures
in the
network
High
Targeted
cyber attacks
Broken
authenticati
on and
compromis
ed log in
credentials
Malware, phishing,
hacking attacks
Medium
Weak
security and
provider
errors
Multiple
jurisdiction
and
providers
of cloud
services/
third
parties Advanced
persistent Threats
Low
Very Low
Severity Very Low Low Medium High Very High
management functions such as session IDs and exposed passwords to impersonate authorized users
(Rashid, 2016)
2. Advanced Persistent Threats: A network type attack where unauthorized people gain entry into
the DAS cloud network and remains undetected over long time periods; meanwhile, the entity steals
data from the cloud resource (Armerding, 2014)
3. Multiple jurisdiction and providers of cloud services/ third parties: the DAS will give the
management of its data to the service providers and third parties I different jurisdictions; it cannot
fully control who can access and view its data (Subashini & Kavitha, 2011)
4. Weak security and provider errors: This is where service providers implement weak/ vulnerable
security protocols, such as vulnerable APIs or make mistakes where their staff accidentally expose
employee data (Cobb, 2014)
Probability
Very High
Insider risks
to privacy
Weak
security
measures
in the
network
High
Targeted
cyber attacks
Broken
authenticati
on and
compromis
ed log in
credentials
Malware, phishing,
hacking attacks
Medium
Weak
security and
provider
errors
Multiple
jurisdiction
and
providers
of cloud
services/
third
parties Advanced
persistent Threats
Low
Very Low
Severity Very Low Low Medium High Very High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head; CLOUD PRIVACY AND SECURITY 11
3. Digital Identity Issues (threats and risks to the digital identities of Government
employees from the move to SaaS applications) (some issues from Q3 Assignment1)
Student 3 Student ID
1. Poor security policies: This is when employee IDs are posted in online portals where hackers
and malicious persons can access them and use tools such as phishing and social engineering
attacks to gain their identity and use them maliciously
2. Exposed access points: Because the cloud is based on the internet; government employees can
access the resources from any location, including at home using their personal devices. These
devices may have resident malware that then gain access to the cloud through employee IDs and
devices, hence gaining access to other employee IDs (Decman & Vintar, 2013)
3. Identity sprawl weakness: The employees may need to access different resources at different
levels using a single password or log-on credential; this means that should their ID be stolen, then
malicious users can access the IDs of other government employees at different levels and locations.
For instance, having a single access credential to access the HR information as well as payroll
means an attacker can access both resources using a single log in credential.
4. Central management of user IDs: Likely, an administrator will manage all user IDs from a
single location/ console; breaching this console, either accidentally or through cooperation implies
hackers and other malicious entities can have access to all user IDs and use them to access other
restricted resources (Decman & Vintar, 2013) .
Student 3 Student ID
4. Provider Solution Issues and why?
1. Threat from using Microsoft Share Point : using the Share point (Microsoft) implies that the
cloud will be set up in a PaaS configuration, which also comes with its own set of challenges.
Usually, a PaaS architecture passes the responsibility for managing security and sessions to the
client, (in this case) (Zissis & Lekkas, 2011).
2. Multiple Cloud Architecture with Hybrid; DAS will use the services of different service
providers; one American, and the other German for different critical tasks; further, the service
providers have multiple locations which spreads, and ultimately, minimizes risks to its data security
and privacy. The approach mitigates risks and threats to data security and privacy as different
portions are handled by different providers, meaning all applications cannot be compromised as
happens with a single provider. Further, DAS has its own data center which creates a hybrid cloud
3. Digital Identity Issues (threats and risks to the digital identities of Government
employees from the move to SaaS applications) (some issues from Q3 Assignment1)
Student 3 Student ID
1. Poor security policies: This is when employee IDs are posted in online portals where hackers
and malicious persons can access them and use tools such as phishing and social engineering
attacks to gain their identity and use them maliciously
2. Exposed access points: Because the cloud is based on the internet; government employees can
access the resources from any location, including at home using their personal devices. These
devices may have resident malware that then gain access to the cloud through employee IDs and
devices, hence gaining access to other employee IDs (Decman & Vintar, 2013)
3. Identity sprawl weakness: The employees may need to access different resources at different
levels using a single password or log-on credential; this means that should their ID be stolen, then
malicious users can access the IDs of other government employees at different levels and locations.
For instance, having a single access credential to access the HR information as well as payroll
means an attacker can access both resources using a single log in credential.
4. Central management of user IDs: Likely, an administrator will manage all user IDs from a
single location/ console; breaching this console, either accidentally or through cooperation implies
hackers and other malicious entities can have access to all user IDs and use them to access other
restricted resources (Decman & Vintar, 2013) .
Student 3 Student ID
4. Provider Solution Issues and why?
1. Threat from using Microsoft Share Point : using the Share point (Microsoft) implies that the
cloud will be set up in a PaaS configuration, which also comes with its own set of challenges.
Usually, a PaaS architecture passes the responsibility for managing security and sessions to the
client, (in this case) (Zissis & Lekkas, 2011).
2. Multiple Cloud Architecture with Hybrid; DAS will use the services of different service
providers; one American, and the other German for different critical tasks; further, the service
providers have multiple locations which spreads, and ultimately, minimizes risks to its data security
and privacy. The approach mitigates risks and threats to data security and privacy as different
portions are handled by different providers, meaning all applications cannot be compromised as
happens with a single provider. Further, DAS has its own data center which creates a hybrid cloud

Running head; CLOUD PRIVACY AND SECURITY 12
that has increased security benefits since sensitive information can be encrypted and stored in its
private cloud; which also offers an additional layer of security (Zissis & Lekkas, 2011).
3. Using PaaS poses security risks: PaaS (Microsoft Share Point) is a third party software;
although it provides an platform for DAS to run applications, it also transfers security and
management to DAS, rather than have a specialist do it as happens with a SaaS setup. This is
because the SSL feature and default configurations are some of the biggest risks and weakest points
vulnerable for exploitation from malicious users.
4. Enhanced data security: using the hybrid cloud setup gives DAS enhanced security as
compared to the in-house IT setup. For one, the cloud setup provides additional backups, which are
further distributed geographically. Employing features such as virtualization will ensure continuity
on demand, in case of any exploits. It also minimizes the level of threats and their severity
compared to the in-house setup. Using protocols such as RAID will ensure fail-safe setup as data
integrity will be retained even in the event of a disaster. The setup also allows DAS to enjoy quality
services on demand at a cost effective rate a it removes the need for expensive hardware and staff to
manage a full fledged in-house data center with its demands for power, space and bandwidth.
Drawing of Solution Architecture including security and Privacy
DAS Private cloud
US Cloud provider
Distributed data centers
German cloud provider
Distributed data centers
Firewall
IndiaIndia USA
Ireland
Germany Ireland
Bridge
INTERNET
Unified administration
that has increased security benefits since sensitive information can be encrypted and stored in its
private cloud; which also offers an additional layer of security (Zissis & Lekkas, 2011).
3. Using PaaS poses security risks: PaaS (Microsoft Share Point) is a third party software;
although it provides an platform for DAS to run applications, it also transfers security and
management to DAS, rather than have a specialist do it as happens with a SaaS setup. This is
because the SSL feature and default configurations are some of the biggest risks and weakest points
vulnerable for exploitation from malicious users.
4. Enhanced data security: using the hybrid cloud setup gives DAS enhanced security as
compared to the in-house IT setup. For one, the cloud setup provides additional backups, which are
further distributed geographically. Employing features such as virtualization will ensure continuity
on demand, in case of any exploits. It also minimizes the level of threats and their severity
compared to the in-house setup. Using protocols such as RAID will ensure fail-safe setup as data
integrity will be retained even in the event of a disaster. The setup also allows DAS to enjoy quality
services on demand at a cost effective rate a it removes the need for expensive hardware and staff to
manage a full fledged in-house data center with its demands for power, space and bandwidth.
Drawing of Solution Architecture including security and Privacy
DAS Private cloud
US Cloud provider
Distributed data centers
German cloud provider
Distributed data centers
Firewall
IndiaIndia USA
Ireland
Germany Ireland
Bridge
INTERNET
Unified administration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





