Impact of EHR Systems on Healthcare
VerifiedAdded on 2020/04/01
|17
|4040
|44
AI Summary
This assignment examines the influence of Electronic Health Records (EHR) systems on the healthcare industry. Students are tasked with analyzing both the positive and negative aspects of EHR implementation, particularly highlighting potential risks to patient privacy and data security. The focus is on understanding how these technological advancements can impact human roles and responsibilities within healthcare.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

1
COIT 20246
Name
Course
Professor
School
City
Date
COIT 20246
Name
Course
Professor
School
City
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number

3
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference: Quantum computing
Devitt, S.J., Munro, W.J. and Nemoto, K., 2008. High performance quantum computing. arXiv
preprint arXiv:0810.2444. Accessed At: https://arxiv.org/pdf/0810.2444.pdf
Summary:
Devitt and Nemoto they have written this resource about the high performance quantum
computing. This architecture scalability which has been afforded by the recent proposal for the large
scale quantum computers has allowed the movement of the discussion that is scale quantum formation
processing. The quantum computers have high performance where they are utilized by many of the
users in running of the algorithms as well as sharing of the quantum data. The quantum computers is
one of the discussed subject currently. The subject highlights how the computational process which the
quantum mechanical utilize apart from the usual digital computer.
I have selected on this resource article since it offers new insights when it
comes to the quantum computers along with the development its architecture and the
link to the other computing technologies.
The main key components which the resource highlights is on the quantum
computers. The resource highlights on the scaling structure to the optical architecture
which lead to attractive future served which has been based on the dedicated
mainframes. The aspect of the resource focus on the quantum computers and the
advancement in the computational models which have been formulated on this
subject.
The article is useful as it highlights on the concepts of the quantum computers.
Some of these which are clearly defined in the resource is on the topological clusters
and how to secure computing.
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference: Quantum computing
Devitt, S.J., Munro, W.J. and Nemoto, K., 2008. High performance quantum computing. arXiv
preprint arXiv:0810.2444. Accessed At: https://arxiv.org/pdf/0810.2444.pdf
Summary:
Devitt and Nemoto they have written this resource about the high performance quantum
computing. This architecture scalability which has been afforded by the recent proposal for the large
scale quantum computers has allowed the movement of the discussion that is scale quantum formation
processing. The quantum computers have high performance where they are utilized by many of the
users in running of the algorithms as well as sharing of the quantum data. The quantum computers is
one of the discussed subject currently. The subject highlights how the computational process which the
quantum mechanical utilize apart from the usual digital computer.
I have selected on this resource article since it offers new insights when it
comes to the quantum computers along with the development its architecture and the
link to the other computing technologies.
The main key components which the resource highlights is on the quantum
computers. The resource highlights on the scaling structure to the optical architecture
which lead to attractive future served which has been based on the dedicated
mainframes. The aspect of the resource focus on the quantum computers and the
advancement in the computational models which have been formulated on this
subject.
The article is useful as it highlights on the concepts of the quantum computers.
Some of these which are clearly defined in the resource is on the topological clusters
and how to secure computing.

4
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONE such individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference: High performance Linux clusters
Sloan, J.D., 2004. High Performance Linux Clusters with OSCAR, Rocks, OpenMosix, and MPI: A
Comprehensive Getting-Started Guide. " O'Reilly Media, Inc.".
.Accessed At: http://ai2-s2 pdfs.s3.amazonaws.com/1cfa/fc7e7949d542fc1b735ffba1d1e17a82f9ee.pdf
Summary:
Sloan has written on the resource in regards to the Linux operating system.
This resource is all about the Linux distribution. The resource highlights that the
decision of using of the operating system mostly depend on many consideration for
example is the cost of the system as well as the personal experiences with the various
systems. In this article it further highlights on both the features and the advantages of
the Linux distribution.
I have selected on this resource article since it concentrate on the usefulness of
this distribution. It shows where the distribution is utilized and for what purpose.
Additionally, being able to understand on the distribution becomes much easier as the
information which the resource has delivered would be very useful.
The major point to which have been discussed in the resource is on the
features as well as the advantages which are associated to the Linux distribution. The
advantage which is associated to the Linux operating distribution is much stable and
has capability of multitasking. The resource essential discuss on the advantage as well
as the features.
The resource has been very helpful as I will gains some insight when it comes
to the features and advantages of the Linux distribution.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONE such individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference: High performance Linux clusters
Sloan, J.D., 2004. High Performance Linux Clusters with OSCAR, Rocks, OpenMosix, and MPI: A
Comprehensive Getting-Started Guide. " O'Reilly Media, Inc.".
.Accessed At: http://ai2-s2 pdfs.s3.amazonaws.com/1cfa/fc7e7949d542fc1b735ffba1d1e17a82f9ee.pdf
Summary:
Sloan has written on the resource in regards to the Linux operating system.
This resource is all about the Linux distribution. The resource highlights that the
decision of using of the operating system mostly depend on many consideration for
example is the cost of the system as well as the personal experiences with the various
systems. In this article it further highlights on both the features and the advantages of
the Linux distribution.
I have selected on this resource article since it concentrate on the usefulness of
this distribution. It shows where the distribution is utilized and for what purpose.
Additionally, being able to understand on the distribution becomes much easier as the
information which the resource has delivered would be very useful.
The major point to which have been discussed in the resource is on the
features as well as the advantages which are associated to the Linux distribution. The
advantage which is associated to the Linux operating distribution is much stable and
has capability of multitasking. The resource essential discuss on the advantage as well
as the features.
The resource has been very helpful as I will gains some insight when it comes
to the features and advantages of the Linux distribution.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5

6
Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONE of the networks that led to the development of the
modern Internet.
Title and Reference: ARPANET Network
Theconversation.com. How the Internet was born: from the ARPANET to the Internet. Accessed At:
https://theconversation.com/how-the-internet-was-born-from-the-arpanet-to-the-internet-68072
Summary:
This resource article provides information on how the internet started. It
highlights on the ARPANET which was the earlier network that began in 1970. In the
article it articulate on how this network was used to be able to provide internet. The
internet concept has been clearly explained on this article on how it came to being. In
the 1970 it was when the four nodes of this network became functional things but at
the same time more complicated.
The resource has been choose since it provide information in regards to the
how the internet was born. The network which led to the development of the modern
internet was ARPANET. It was the first wide area packet switching kind of the
network and this evolved into what the internet we know as well as use today. The
article present the origin of the ARPANET and the transformation it has passed over
the years to become the internet that is known today.
The main aspect which has been discussed in the resource is on the evolution
of the network of the internet and the network which has been discussed to depth in
the resource is ARPANET.
This resource article has been significance as it has provided insight on the
other type of network that led to the development of the internet. Moreover, the
resource has proved to provide information on how the current internet we use came
in existence based on the development over the years. We are able to trace on the
Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONE of the networks that led to the development of the
modern Internet.
Title and Reference: ARPANET Network
Theconversation.com. How the Internet was born: from the ARPANET to the Internet. Accessed At:
https://theconversation.com/how-the-internet-was-born-from-the-arpanet-to-the-internet-68072
Summary:
This resource article provides information on how the internet started. It
highlights on the ARPANET which was the earlier network that began in 1970. In the
article it articulate on how this network was used to be able to provide internet. The
internet concept has been clearly explained on this article on how it came to being. In
the 1970 it was when the four nodes of this network became functional things but at
the same time more complicated.
The resource has been choose since it provide information in regards to the
how the internet was born. The network which led to the development of the modern
internet was ARPANET. It was the first wide area packet switching kind of the
network and this evolved into what the internet we know as well as use today. The
article present the origin of the ARPANET and the transformation it has passed over
the years to become the internet that is known today.
The main aspect which has been discussed in the resource is on the evolution
of the network of the internet and the network which has been discussed to depth in
the resource is ARPANET.
This resource article has been significance as it has provided insight on the
other type of network that led to the development of the internet. Moreover, the
resource has proved to provide information on how the current internet we use came
in existence based on the development over the years. We are able to trace on the

7
various network which were formed in the past.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title and Reference: MANETS
Larsen, E., 2012. TCP in MANETs–challenges and Solutions. FFI-Rapport-2012/01514. Accessed At:
http://www.ffi.no/no/Rapporter/12-01289.pdf
Summary:
This resource article is about the Mobile Ad hoc Networks also regarded as MANETs. These
have gained popularity over the last decade, due to the emergence of the cost of the technology which
is significantly low. The MANETs is aimed to offer support to the tactical domain communications
with the higher grade of the mobility. These network intends to interconnect with other kind of the
networks when it comes to the networking as well as the information infrastructure through use of the
IP which is the most common protocol which is used for connection.
This resource has been selected as it provides some insights to this protocol
which is useful to support the domain communication. Moreover, the article provides
advantages to the use of the MANET technology such as it is more suitable for the
tactical communication as many of the other based protocol are not directly usable in
this technology. Moreover, there is better control of the packet loss and the
interference which is not possible to control in the multi-hop networks. This protocol
has been found to be new congestion control technique. The resource has examined
on this protocol when it comes to static scenario that the TCP could display
efficiency. Moreover, the article has focused on how this transport protocol could be
customized on the MANET environment since it provided dependability as it can
various network which were formed in the past.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title and Reference: MANETS
Larsen, E., 2012. TCP in MANETs–challenges and Solutions. FFI-Rapport-2012/01514. Accessed At:
http://www.ffi.no/no/Rapporter/12-01289.pdf
Summary:
This resource article is about the Mobile Ad hoc Networks also regarded as MANETs. These
have gained popularity over the last decade, due to the emergence of the cost of the technology which
is significantly low. The MANETs is aimed to offer support to the tactical domain communications
with the higher grade of the mobility. These network intends to interconnect with other kind of the
networks when it comes to the networking as well as the information infrastructure through use of the
IP which is the most common protocol which is used for connection.
This resource has been selected as it provides some insights to this protocol
which is useful to support the domain communication. Moreover, the article provides
advantages to the use of the MANET technology such as it is more suitable for the
tactical communication as many of the other based protocol are not directly usable in
this technology. Moreover, there is better control of the packet loss and the
interference which is not possible to control in the multi-hop networks. This protocol
has been found to be new congestion control technique. The resource has examined
on this protocol when it comes to static scenario that the TCP could display
efficiency. Moreover, the article has focused on how this transport protocol could be
customized on the MANET environment since it provided dependability as it can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
anticipate on the causes of the packet loss which are caused by the queue tail drop. I
have learnt on how to solve on the issue of the poor performance, packet loss as well
as the interferences using MANETs particularly using the TCP protocol. This
research has provided alternative means in solving poor performance and how to
enhance on the protocol as compared to the dependability to TCP.
The major key information which has been examined from this resource is on
how the TCP protocol might help in solving of the problem for the poor performance
and interference especially in the networks. The research examines on the
performance of MANETs by the provisions of the connection as comparing to the
protocol layer. Moreover, the resource has been helpful as it provides insights on the
other additional protocol apart from the major one that are known that are UDP and
the TCP.
The resource has been useful since I have learnt various ways to which the
performance in the network could be enhanced, along with how to reduce interference
and in each case the type of protocol to use.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference: Russian Hacker who breached White House network
Paletta, D., Yadron, D. and Valentino-Devries, J., 2015. Cyberwar Ignites a New Arms Race. Wall
Street Journal, 12. Accessed At: http://activu.com/uploads/Cyberwar-Ignites-a-New-Arms-Race-
WSJ.pdf
Summary:
This resource article is about how the hackers had breaches on the networks of
the white house computer system. Back in 2014, there was a group of the hackers
were responsible for the breach in the white house computer system. These hackers
anticipate on the causes of the packet loss which are caused by the queue tail drop. I
have learnt on how to solve on the issue of the poor performance, packet loss as well
as the interferences using MANETs particularly using the TCP protocol. This
research has provided alternative means in solving poor performance and how to
enhance on the protocol as compared to the dependability to TCP.
The major key information which has been examined from this resource is on
how the TCP protocol might help in solving of the problem for the poor performance
and interference especially in the networks. The research examines on the
performance of MANETs by the provisions of the connection as comparing to the
protocol layer. Moreover, the resource has been helpful as it provides insights on the
other additional protocol apart from the major one that are known that are UDP and
the TCP.
The resource has been useful since I have learnt various ways to which the
performance in the network could be enhanced, along with how to reduce interference
and in each case the type of protocol to use.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference: Russian Hacker who breached White House network
Paletta, D., Yadron, D. and Valentino-Devries, J., 2015. Cyberwar Ignites a New Arms Race. Wall
Street Journal, 12. Accessed At: http://activu.com/uploads/Cyberwar-Ignites-a-New-Arms-Race-
WSJ.pdf
Summary:
This resource article is about how the hackers had breaches on the networks of
the white house computer system. Back in 2014, there was a group of the hackers
were responsible for the breach in the white house computer system. These hackers

9
were able to gain an access to the real time non-public information particularly that of
the schedule of the president. Based on the research, the hackers were believed to
have been the same individuals who were behind the cyber-attacks which were
experienced in the USA department the same year which had forced the department to
shut down their email system.
I have selected on this resources since it offers some insights in regards to the
issues of the cyber security threats particularly on the state department. These groups
of hackers were able to gain an access to any department there it is vital to keep the
system very secure.
The key major points which are provided in this resource is that the issues
related to the cyber security attack are real as this happened in the white house state
department. The hackers who were responsible were the Russian hackers who were
able to gain access to the system and gain information on the president schedule.
The resource article has been very helpful since one is able to learn various
situations to which the systems are breached by attackers and it offers approaches on
how to keep the system more secure by means of encrypting it as well as use of the
other security measures.
were able to gain an access to the real time non-public information particularly that of
the schedule of the president. Based on the research, the hackers were believed to
have been the same individuals who were behind the cyber-attacks which were
experienced in the USA department the same year which had forced the department to
shut down their email system.
I have selected on this resources since it offers some insights in regards to the
issues of the cyber security threats particularly on the state department. These groups
of hackers were able to gain an access to any department there it is vital to keep the
system very secure.
The key major points which are provided in this resource is that the issues
related to the cyber security attack are real as this happened in the white house state
department. The hackers who were responsible were the Russian hackers who were
able to gain access to the system and gain information on the president schedule.
The resource article has been very helpful since one is able to learn various
situations to which the systems are breached by attackers and it offers approaches on
how to keep the system more secure by means of encrypting it as well as use of the
other security measures.

10
Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference: Time clock
Kevin, F., Time cloak cloud revolutionize fiber networks. Accessed At:
https://www.computerworld.com/article/2853777/time-cloak-could-revolutionize-
fiber-networks.html
Summary:
This resource is about time clock which will be an emerging technology to be used in future.
The researcher at Purdue University have been able to create a way to communicate with absolute
secrecy through concealing of the messages in time by using tricks of the laser light as well as the fiber
optics. In this resource it highlights how this technique is able to conceal not only on the content of the
message as well as the fact which were sent through tucking on the message to the gap in that flow of
the photons which are sent by the laser down the single strand. This article highlights how this
technology would revolutionize on the way we communicate.
I have selected on this resource because it provide an insight on a new way of
communication where individual are able to communicate in secrecy by concealing
on the message sent in time by use of the laser lights. This is a new phenomenon and
the subject seems to be very interesting to understand new way of communication.
The key major point from the resource is that temporal cloaking is a new way
of communication of concealing the content of the message and tucking the message
into the gaps. This resource provide how the message would be sent particularly
through the laser lights and the fiber optics. Moreover, the resource explains on the
process of transfer of the message and the flow of the energy especially on the
photons and the strands of the lights. Moreover, the article explains on the new way of
packing of the 1.5 megabits of the data to the temporal cloak through use of the
superfast femtosecond laser as well as the off the shelf optical networking equipment.
The resource has been useful as I have learnt new way of communication
particularly when sending the message where I can send the message with absolute
Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference: Time clock
Kevin, F., Time cloak cloud revolutionize fiber networks. Accessed At:
https://www.computerworld.com/article/2853777/time-cloak-could-revolutionize-
fiber-networks.html
Summary:
This resource is about time clock which will be an emerging technology to be used in future.
The researcher at Purdue University have been able to create a way to communicate with absolute
secrecy through concealing of the messages in time by using tricks of the laser light as well as the fiber
optics. In this resource it highlights how this technique is able to conceal not only on the content of the
message as well as the fact which were sent through tucking on the message to the gap in that flow of
the photons which are sent by the laser down the single strand. This article highlights how this
technology would revolutionize on the way we communicate.
I have selected on this resource because it provide an insight on a new way of
communication where individual are able to communicate in secrecy by concealing
on the message sent in time by use of the laser lights. This is a new phenomenon and
the subject seems to be very interesting to understand new way of communication.
The key major point from the resource is that temporal cloaking is a new way
of communication of concealing the content of the message and tucking the message
into the gaps. This resource provide how the message would be sent particularly
through the laser lights and the fiber optics. Moreover, the resource explains on the
process of transfer of the message and the flow of the energy especially on the
photons and the strands of the lights. Moreover, the article explains on the new way of
packing of the 1.5 megabits of the data to the temporal cloak through use of the
superfast femtosecond laser as well as the off the shelf optical networking equipment.
The resource has been useful as I have learnt new way of communication
particularly when sending the message where I can send the message with absolute
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11
secrecy.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference: Real history of Twitter
Amanda, M., 2017. The real history of Twitter, in Brief. Accessed At:
https://www.lifewire.com/history-of-twitter-3288854
Summary:
The resource is about how the twitter social network company was developed.
The article highlights that twitter just began as an idea which the co-founder Jack
Dorsey had back in the year 2006. Further, this individual had just imaged twitter just
as a sms-based communication platform. There were groups of friends who could
keep the tabs on what each other was performing based on their status updates. The
resource further highlight that it was from this simple idea was there development of
this social media platform. The article highlights how the platform has grown over
time and the challenge they had to endure to reach to where they are currently.
I have selected on this article because it highlights one of the most visited
social media platform and understanding on its development would provide further
insights on how it was formed since I myself included uses it most of the time.
The major key point which the resource has focused on is how it started, the
experiences of the first twit by the co-founder Jack and the growth it has encountered
over the years. Moreover, the resource has focussed on the journey the company has
undergo and how they are still growing.
The resource has been useful as it provide some insight on how the twitter
secrecy.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference: Real history of Twitter
Amanda, M., 2017. The real history of Twitter, in Brief. Accessed At:
https://www.lifewire.com/history-of-twitter-3288854
Summary:
The resource is about how the twitter social network company was developed.
The article highlights that twitter just began as an idea which the co-founder Jack
Dorsey had back in the year 2006. Further, this individual had just imaged twitter just
as a sms-based communication platform. There were groups of friends who could
keep the tabs on what each other was performing based on their status updates. The
resource further highlight that it was from this simple idea was there development of
this social media platform. The article highlights how the platform has grown over
time and the challenge they had to endure to reach to where they are currently.
I have selected on this article because it highlights one of the most visited
social media platform and understanding on its development would provide further
insights on how it was formed since I myself included uses it most of the time.
The major key point which the resource has focused on is how it started, the
experiences of the first twit by the co-founder Jack and the growth it has encountered
over the years. Moreover, the resource has focussed on the journey the company has
undergo and how they are still growing.
The resource has been useful as it provide some insight on how the twitter

12
social media was developed and the growth they have undergo over the years to
achieve the success they are enjoying today.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference: Data mining
Bhowmik, R., 2008. Data mining techniques in fraud detection. The Journal of Digital Forensics,
Security and Law: JDFSL, 3(2), p.35. Accessed At: http://commons.erau.edu/cgi/viewcontent.cgi?
article=1040&context=jdfsl
Summary:
This resource examine on how data mining has been used in the fraud
detection. It offers various techniques to use to be able to know how to detect the
fraud cases. The article offers an example of the case in which the data mining
technique was used to detect on the fraud case. According to the article it highlight
that that there a number of the data based algorithms which are used to detect on the
fraud in the automobile insurance. Further the article has highlighted some of the
fraud cases such as credit card fraud, check forgery, as well as the insurance fraud.
The article further highlight some of the data mining techniques which are used for
the analysis of these frauds.
I have selected on this resource because it highlights a situation in which data
mining has been used successful in the business in order to determining the fraud
situation. The article has also highlighted on the Bayesian classification model for the
detection of the fraud when it comes to the automobile insurance.
The major key point which are highlighted in this resource is that it highlights
social media was developed and the growth they have undergo over the years to
achieve the success they are enjoying today.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference: Data mining
Bhowmik, R., 2008. Data mining techniques in fraud detection. The Journal of Digital Forensics,
Security and Law: JDFSL, 3(2), p.35. Accessed At: http://commons.erau.edu/cgi/viewcontent.cgi?
article=1040&context=jdfsl
Summary:
This resource examine on how data mining has been used in the fraud
detection. It offers various techniques to use to be able to know how to detect the
fraud cases. The article offers an example of the case in which the data mining
technique was used to detect on the fraud case. According to the article it highlight
that that there a number of the data based algorithms which are used to detect on the
fraud in the automobile insurance. Further the article has highlighted some of the
fraud cases such as credit card fraud, check forgery, as well as the insurance fraud.
The article further highlight some of the data mining techniques which are used for
the analysis of these frauds.
I have selected on this resource because it highlights a situation in which data
mining has been used successful in the business in order to determining the fraud
situation. The article has also highlighted on the Bayesian classification model for the
detection of the fraud when it comes to the automobile insurance.
The major key point which are highlighted in this resource is that it highlights

13
on how the data mining has been used to detect of the fraud case. The resource
provides some of the current techniques which are used in detecting of the fraud
situation.
The resource has been useful since it offers insights when it comes to the data
mining especially on how it has been used successfully in the business. This is an
important resource as one would be able to use a given technique to detect on
different kind of fraud cases.
on how the data mining has been used to detect of the fraud case. The resource
provides some of the current techniques which are used in detecting of the fraud
situation.
The resource has been useful since it offers insights when it comes to the data
mining especially on how it has been used successfully in the business. This is an
important resource as one would be able to use a given technique to detect on
different kind of fraud cases.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14
Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference: Successful App Redesign
Daniel, S., 2016. What it takes to have a successful App Redesign. Assessed At:
https://stories.appbot.co/what-it-takes-to-have-a-successful-app-redesign-461209b8fd83
Summary:
The resource highlights on the success story of the mobile app developer regarded as Stuart
Hall who is the CEO of Appbot. This resource focus on the successful App Redesign. This focusses on
how the odds had their redesign or perhaps the change in the logo to be able to yield on the immediate
positive response from the users as well as the outliers. According to the resource it has also
highlighted that the redesign of the app are met with the initial negative response particularly from the
users. The article has focussed on the way the app redesign could be used to change the perspective of
the users to certain products.
I have selected on this resource because this is an example of one of the
successful mobile app developer. This individual has been attributed to numerous app
development. This resource provides an insight when it comes to the development of
the apps as well as resigning on the application which could be utilized in the various
users.
The main key point focuses more on the individuals who have contributed to
the success of the information technology. In this case of the resource is the focus is
on Stuart Hall who has contributed significantly in the design and the development of
the mobile app. In the resource it has been based on how to redesign on the app to
make them have an instant hit.
The resource has been useful as it offers insights and motivation on some of
the work that has been done by the major app developer in the world and how their
work has contributed significantly in this era of technology.
Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference: Successful App Redesign
Daniel, S., 2016. What it takes to have a successful App Redesign. Assessed At:
https://stories.appbot.co/what-it-takes-to-have-a-successful-app-redesign-461209b8fd83
Summary:
The resource highlights on the success story of the mobile app developer regarded as Stuart
Hall who is the CEO of Appbot. This resource focus on the successful App Redesign. This focusses on
how the odds had their redesign or perhaps the change in the logo to be able to yield on the immediate
positive response from the users as well as the outliers. According to the resource it has also
highlighted that the redesign of the app are met with the initial negative response particularly from the
users. The article has focussed on the way the app redesign could be used to change the perspective of
the users to certain products.
I have selected on this resource because this is an example of one of the
successful mobile app developer. This individual has been attributed to numerous app
development. This resource provides an insight when it comes to the development of
the apps as well as resigning on the application which could be utilized in the various
users.
The main key point focuses more on the individuals who have contributed to
the success of the information technology. In this case of the resource is the focus is
on Stuart Hall who has contributed significantly in the design and the development of
the mobile app. In the resource it has been based on how to redesign on the app to
make them have an instant hit.
The resource has been useful as it offers insights and motivation on some of
the work that has been done by the major app developer in the world and how their
work has contributed significantly in this era of technology.

15
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference: Electronic health record technology
George, P., 2013. Electronic Health records: The good, the bad and the ugly.
Accessed At: http://www.beckershospitalreview.com/healthcare-information-
technology/electronic-health-records-the-good-the-bad-and-the-ugly.html
Summary:
This resources highlights that the electronic health records have been adopted widely all
across the healthcare business both large and the small. It highlights the benefits of the electronic
health record system. Nonetheless, it has also provided some inherent issues associated in the
adaptation of this technology. The resource outlines the ugly parts of the EHR system such as the
HIPAA violation in which there is the increased risk to the privacy solutions. There are instances when
the information of the patients have been stolen with the use of this system. As much as there are
advantage associated to the system there are devastation negative effect of the system.
I have selected on this resource because it highlights the ugly side of the EHR
system particularly on causing the negative effects and the outcomes to the human.
One such instant is when there is breach of the personal information which leads to
violation of privacy of people.
The main key aspects which have been highlighted by the resource is that it
shows negative effects and outcome of the information technology. These outcomes
could lead to impacting negatively on the aspects and duties of the humans.
The resource has been useful as it provide an insights on how the use
information technology could bring about the negative effects as well as the
outcomes. This is important in that individuals will have an idea on how to prevent
the drawbacks which are presented by the information technology.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference: Electronic health record technology
George, P., 2013. Electronic Health records: The good, the bad and the ugly.
Accessed At: http://www.beckershospitalreview.com/healthcare-information-
technology/electronic-health-records-the-good-the-bad-and-the-ugly.html
Summary:
This resources highlights that the electronic health records have been adopted widely all
across the healthcare business both large and the small. It highlights the benefits of the electronic
health record system. Nonetheless, it has also provided some inherent issues associated in the
adaptation of this technology. The resource outlines the ugly parts of the EHR system such as the
HIPAA violation in which there is the increased risk to the privacy solutions. There are instances when
the information of the patients have been stolen with the use of this system. As much as there are
advantage associated to the system there are devastation negative effect of the system.
I have selected on this resource because it highlights the ugly side of the EHR
system particularly on causing the negative effects and the outcomes to the human.
One such instant is when there is breach of the personal information which leads to
violation of privacy of people.
The main key aspects which have been highlighted by the resource is that it
shows negative effects and outcome of the information technology. These outcomes
could lead to impacting negatively on the aspects and duties of the humans.
The resource has been useful as it provide an insights on how the use
information technology could bring about the negative effects as well as the
outcomes. This is important in that individuals will have an idea on how to prevent
the drawbacks which are presented by the information technology.

16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
17
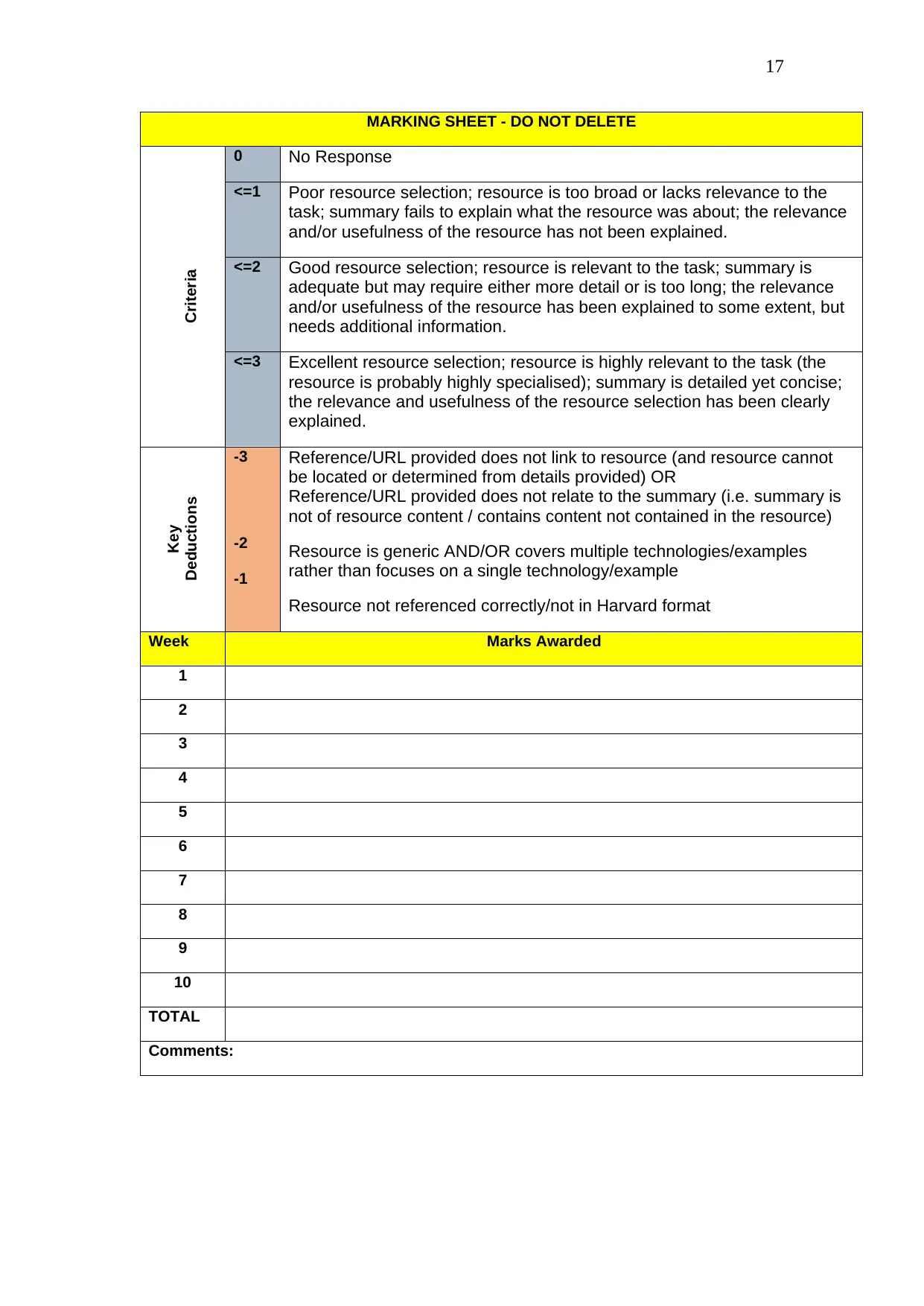
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





