Computer Systems Architecture Report: Network Connectivity Analysis
VerifiedAdded on 2023/01/07
|15
|4443
|2
Report
AI Summary
This report delves into computer systems architecture, exploring the relationship between hardware and network addresses, including their use in networking devices and components. It covers the setup, configuration, and documentation of hardware and software systems to establish computer-based network connectivity, discussing various network topologies such as bus, star, ring, and mesh. The report also examines information-gathering methods for assessing, troubleshooting, and documenting solutions to technical hardware, software, and networking issues. Furthermore, it includes a discussion on conducting and documenting maintenance activities related to computer hardware and software, with an overview of operating system features like memory, processor, device, and file management, along with network protocols such as TCP/IP, UDP, OSI, and ICMP. The report emphasizes the importance of network security, including audit, mapping, and software updates, along with setting up a LAN network. The report aims to provide a comprehensive understanding of computer systems architecture, networking, and maintenance, offering insights into both hardware and software aspects.

Computer Systems
Architecture
Architecture
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION ..........................................................................................................................1
TASK 3............................................................................................................................................1
P5. Explain the relationships between hardware and network addresses including their use
with regards to networking devices and components.................................................................1
P6. Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity.........................................................................................3
TASK 4............................................................................................................................................4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues..................................4
P8. Conduct and document a range of maintenance activities with regards to computer
hardware and software................................................................................................................4
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5
INTRODUCTION ..........................................................................................................................1
TASK 3............................................................................................................................................1
P5. Explain the relationships between hardware and network addresses including their use
with regards to networking devices and components.................................................................1
P6. Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity.........................................................................................3
TASK 4............................................................................................................................................4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues..................................4
P8. Conduct and document a range of maintenance activities with regards to computer
hardware and software................................................................................................................4
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5

INTRODUCTION
A computer system is considered as the nutshell as it include looking back to the timeline
of the computer evolution over the decades. A computer is a machine which is instructed in
terms of carrying out the significant sequence of logical operations automatically through
computer programming. These programmes include computers in terms of performing wide
range of task as it include hardware, operating system, software and other concerning
equipments that are used for the further operations and referred as the computer system (Lao and
et. al., 2020). It is a programmable device which automatically perform prominent sequence of
calculations and other operations as it can store, process, retrieve and process data as per the
internal instructions. The report is going to cover the relationship among hardware and network
address including their usage concerning the networking devices and also setup, configure and
document hardware and software system for the effectively developing computer based network.
Furthermore, it also use the prominent information of collecting various methods to assess and
document solutions to the number of various technical hardware and other networking issues.
Lastly, it conduct a range of care activities for computer.
P3 Explicate different features of operating system.
The interface in between users and computer hardware is referred to as operating system.
It is a software that is liable for performing basic tasks such as memory, process and file
management. The different functions can be carried out by making use of OS are specified
below: Memory Management: This denotes managing main or primary memory. This provides
fast storage which can be directly accessed by CPU. This is responsible for keeping track
and allocation of memory. In case of multiprogramming, the operating system is liable
for deciding which process will be provided with memory and for how long this will
occur. Processor Management: In this case, OS is responsible for deciding which process will
be provided with processor and for how long (Ahmadi and et. al., 2018). This function is
referred to as process scheduling. Track processor along with status of process will be
maintained. The program is liable for carrying out this task, and this is known as traffic
controller.
1
A computer system is considered as the nutshell as it include looking back to the timeline
of the computer evolution over the decades. A computer is a machine which is instructed in
terms of carrying out the significant sequence of logical operations automatically through
computer programming. These programmes include computers in terms of performing wide
range of task as it include hardware, operating system, software and other concerning
equipments that are used for the further operations and referred as the computer system (Lao and
et. al., 2020). It is a programmable device which automatically perform prominent sequence of
calculations and other operations as it can store, process, retrieve and process data as per the
internal instructions. The report is going to cover the relationship among hardware and network
address including their usage concerning the networking devices and also setup, configure and
document hardware and software system for the effectively developing computer based network.
Furthermore, it also use the prominent information of collecting various methods to assess and
document solutions to the number of various technical hardware and other networking issues.
Lastly, it conduct a range of care activities for computer.
P3 Explicate different features of operating system.
The interface in between users and computer hardware is referred to as operating system.
It is a software that is liable for performing basic tasks such as memory, process and file
management. The different functions can be carried out by making use of OS are specified
below: Memory Management: This denotes managing main or primary memory. This provides
fast storage which can be directly accessed by CPU. This is responsible for keeping track
and allocation of memory. In case of multiprogramming, the operating system is liable
for deciding which process will be provided with memory and for how long this will
occur. Processor Management: In this case, OS is responsible for deciding which process will
be provided with processor and for how long (Ahmadi and et. al., 2018). This function is
referred to as process scheduling. Track processor along with status of process will be
maintained. The program is liable for carrying out this task, and this is known as traffic
controller.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Device Management: OS manage the communication through respective drivers by
keeping track of all the devices. This will also ensure that devices are allocated in an
effective manner. The program is liable for tracking all devices which is known as input
output controller.
File management: This will make sure that all the directories are organised in an
adequate manner for easy usage and navigation for tracking information, status, use and
many other aspects. The collective facilities are referred to as file system. This also
manage allocation as well as deallocation of resources.
The other essential activities carried out by OS are to make sure security, control over
performance of system, error detection, job detection and coordination among other software's
and users.
TASK 3
P5. Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components
Network communication technology include ICT network which consider explanation of
various technologies like intranet, internet and extranet. For this, it leads to include various
network protocols that deliver reliable and fast communication over large distances. As computer
system relies on the networks on the repeatable operations in terms of maintaining network
integrity for executing transfer protocol models that forces information to adhere to primary
rules. Few network protocols are mentioned below:
TCP/IP Protocol: This protocol represents the significant activities that are used as the
protocol stack as by resembling the OSI, TCP/IP work on its own particular manner. In terms of
this, IP refers to the internet protocol of data transmission in which data is separated into units of
data and also sent over the routing information that direct to the destination (Dickerson and
Mavris, 2016). Along with this, TCP depicts the transmission control protocol that develop
significant connections and send data concerning the receipt of information and the receiver
notifies the sender regarding the information that remain intact.
UDP: It refers to the User Datagram protocol which is used as the transport layer and the
application developers use UDP at the place of TCP. It is the scaled down economy model and it
does not offer prominent bells and signal of TCP as it does a very good job for transporting
2
keeping track of all the devices. This will also ensure that devices are allocated in an
effective manner. The program is liable for tracking all devices which is known as input
output controller.
File management: This will make sure that all the directories are organised in an
adequate manner for easy usage and navigation for tracking information, status, use and
many other aspects. The collective facilities are referred to as file system. This also
manage allocation as well as deallocation of resources.
The other essential activities carried out by OS are to make sure security, control over
performance of system, error detection, job detection and coordination among other software's
and users.
TASK 3
P5. Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components
Network communication technology include ICT network which consider explanation of
various technologies like intranet, internet and extranet. For this, it leads to include various
network protocols that deliver reliable and fast communication over large distances. As computer
system relies on the networks on the repeatable operations in terms of maintaining network
integrity for executing transfer protocol models that forces information to adhere to primary
rules. Few network protocols are mentioned below:
TCP/IP Protocol: This protocol represents the significant activities that are used as the
protocol stack as by resembling the OSI, TCP/IP work on its own particular manner. In terms of
this, IP refers to the internet protocol of data transmission in which data is separated into units of
data and also sent over the routing information that direct to the destination (Dickerson and
Mavris, 2016). Along with this, TCP depicts the transmission control protocol that develop
significant connections and send data concerning the receipt of information and the receiver
notifies the sender regarding the information that remain intact.
UDP: It refers to the User Datagram protocol which is used as the transport layer and the
application developers use UDP at the place of TCP. It is the scaled down economy model and it
does not offer prominent bells and signal of TCP as it does a very good job for transporting
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information which does not need reliable delivery and also use far fewer network resources. It is
also undertaken as the unreliable transport protocol that sends segments over the network and
also forget about other networks and also permit for the acknowledgement of safe arrival.
OSI Protocol task: This model of network data moves from one computer to another in
terms of succeeding the layers of computer software. Moreover, this model set up the prominent
system of layers including physical layer of wires and electricity at the lowermost section. In
terms of this, when an individual send data over the network, it moves down to the heap by each
layer acquiring several data headers, address the information and security checking devices at
every level before reaching over the physical medium (Hwang and Jotwani, 2016).
ICMP: It refers to the Internet Control Message Protocol that leads to support protocol
for the internet suite and also used by network devices considering routers to send fault messages
and other operational information that indicate towards the success and failure in terms of
communicating with another IP address. It differs from the transport protocols including TCP
and UDP which is not used to exchange information and data among systems and also regularly
employed by end user network applications.
Relationship between Hardware and network address
An IP address is the unique set of numbers that leads to examine the device which is
connected to the internet in order to understand that from where the address come and also
understand that how it works. It is a bunch of various networks that are connected together and
also work together in terms of purchasing a services from an ISP as it connect ISP network from
all other networks (Firouzi and et. al., 2018). On the other hand, MAC address examines the
unique network interface within the device as the IP addresses are delegated by the ISPs that can
be re-assigned to other devices that connect and disconnect to its addresses and tied to the
physical adapter. Moreover, both of these work together and interlinked with each other for the
effective use of transport data from one to another network by using prominent TCP/IP protocol
and MAC deliver data to the significant devices on the network.
Network devices and components
Router: It is undertaken as the hardware device which is useful in terms of connecting to
LAN with the internet connection and also used to receive, identify and forward the incoming
packets to other networks. It works as the network layer which include 3 layers of the OSI model
and also forward on the basis of information which is available in routing table. It also determine
3
also undertaken as the unreliable transport protocol that sends segments over the network and
also forget about other networks and also permit for the acknowledgement of safe arrival.
OSI Protocol task: This model of network data moves from one computer to another in
terms of succeeding the layers of computer software. Moreover, this model set up the prominent
system of layers including physical layer of wires and electricity at the lowermost section. In
terms of this, when an individual send data over the network, it moves down to the heap by each
layer acquiring several data headers, address the information and security checking devices at
every level before reaching over the physical medium (Hwang and Jotwani, 2016).
ICMP: It refers to the Internet Control Message Protocol that leads to support protocol
for the internet suite and also used by network devices considering routers to send fault messages
and other operational information that indicate towards the success and failure in terms of
communicating with another IP address. It differs from the transport protocols including TCP
and UDP which is not used to exchange information and data among systems and also regularly
employed by end user network applications.
Relationship between Hardware and network address
An IP address is the unique set of numbers that leads to examine the device which is
connected to the internet in order to understand that from where the address come and also
understand that how it works. It is a bunch of various networks that are connected together and
also work together in terms of purchasing a services from an ISP as it connect ISP network from
all other networks (Firouzi and et. al., 2018). On the other hand, MAC address examines the
unique network interface within the device as the IP addresses are delegated by the ISPs that can
be re-assigned to other devices that connect and disconnect to its addresses and tied to the
physical adapter. Moreover, both of these work together and interlinked with each other for the
effective use of transport data from one to another network by using prominent TCP/IP protocol
and MAC deliver data to the significant devices on the network.
Network devices and components
Router: It is undertaken as the hardware device which is useful in terms of connecting to
LAN with the internet connection and also used to receive, identify and forward the incoming
packets to other networks. It works as the network layer which include 3 layers of the OSI model
and also forward on the basis of information which is available in routing table. It also determine
3

the best suited path from the available paths for the effective transmission of bundle. Router is
more secure, reliable, enhances the overall performance for the network and also has effective
network range.
Switch: It is the hardware devices that connects with various devices and contain
advanced features instead of Hub. It contain the updated table the leads to decide about the data
is transmitted or not (Sharma and Park, 2018). It delivers about the message for the correct
destination which is based on physical address that present at the incoming message. It does not
broadcast the message to the entire network just like Hub. Switch leads to determine the device
regarding the message which is to be transmitted.
P6. Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity
Computer network is the group of computer that leads to use the set of common
communication protocol over digital interconnections for the purpose of sharing resources that
are offered by the network nodes. Moreover, topology refers to the structure of network
regarding its components that are interconnected with each other. Various topologies are
mentioned below:
Bus: It is designed by considering all the stations that are connected by the single cable
which is known as the backbone cable as its each node is directly connected to the backbone
cable. As each node wants to send message over the network and put message over the network
that leads to receive the message (Wells and Wells, 2017). It is prominently used in 802.3
standard networks and the configuration for the bus topology is quite simple as compared to
other topologies. It is also undertaken as the single lane in which the message is broadcast to all
its stations.
4
more secure, reliable, enhances the overall performance for the network and also has effective
network range.
Switch: It is the hardware devices that connects with various devices and contain
advanced features instead of Hub. It contain the updated table the leads to decide about the data
is transmitted or not (Sharma and Park, 2018). It delivers about the message for the correct
destination which is based on physical address that present at the incoming message. It does not
broadcast the message to the entire network just like Hub. Switch leads to determine the device
regarding the message which is to be transmitted.
P6. Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity
Computer network is the group of computer that leads to use the set of common
communication protocol over digital interconnections for the purpose of sharing resources that
are offered by the network nodes. Moreover, topology refers to the structure of network
regarding its components that are interconnected with each other. Various topologies are
mentioned below:
Bus: It is designed by considering all the stations that are connected by the single cable
which is known as the backbone cable as its each node is directly connected to the backbone
cable. As each node wants to send message over the network and put message over the network
that leads to receive the message (Wells and Wells, 2017). It is prominently used in 802.3
standard networks and the configuration for the bus topology is quite simple as compared to
other topologies. It is also undertaken as the single lane in which the message is broadcast to all
its stations.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
(Source: What is Topology?, 2018)
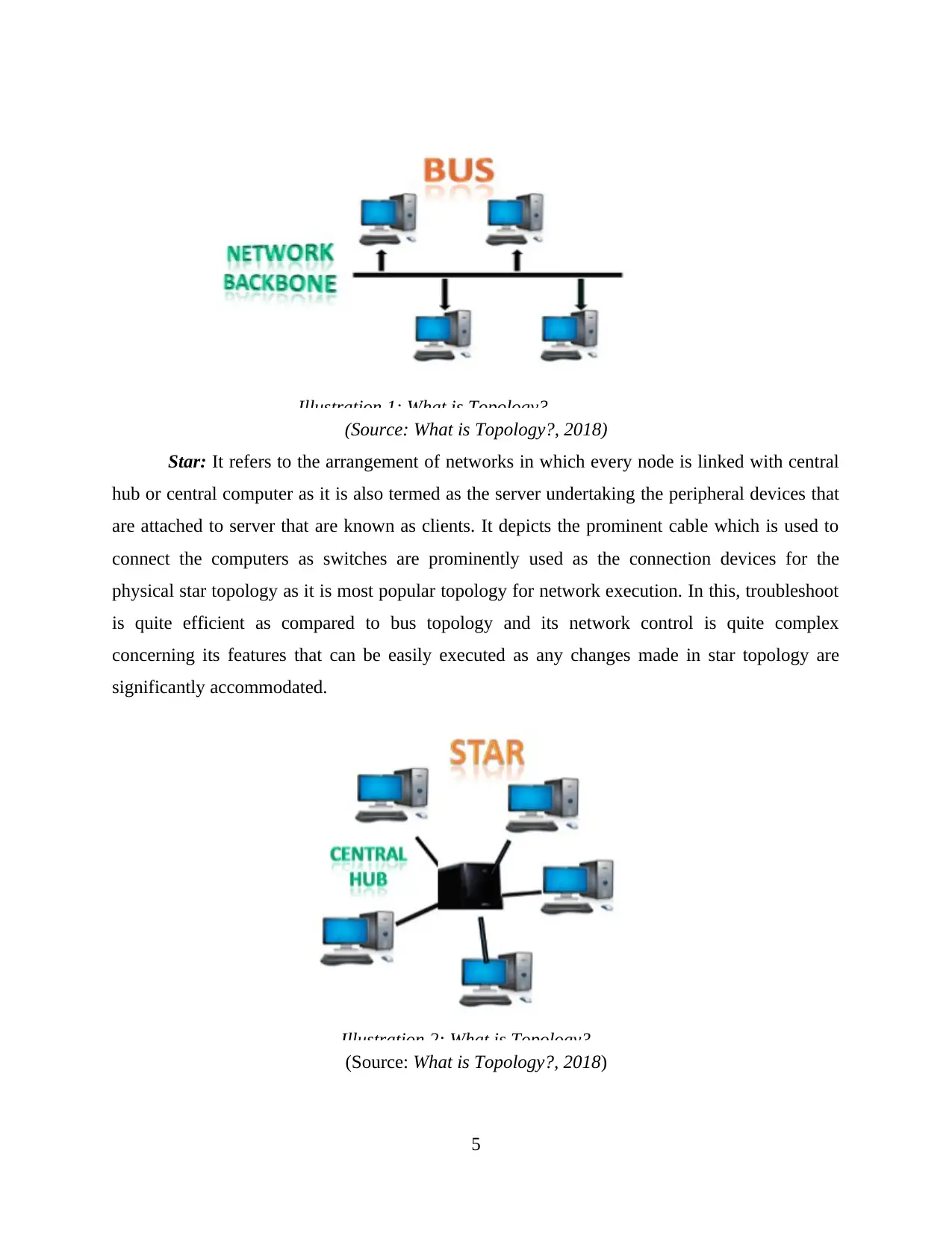
Star: It refers to the arrangement of networks in which every node is linked with central
hub or central computer as it is also termed as the server undertaking the peripheral devices that
are attached to server that are known as clients. It depicts the prominent cable which is used to
connect the computers as switches are prominently used as the connection devices for the
physical star topology as it is most popular topology for network execution. In this, troubleshoot
is quite efficient as compared to bus topology and its network control is quite complex
concerning its features that can be easily executed as any changes made in star topology are
significantly accommodated.
(Source: What is Topology?, 2018)
5
Illustration 1: What is Topology?
Illustration 2: What is Topology?
Star: It refers to the arrangement of networks in which every node is linked with central
hub or central computer as it is also termed as the server undertaking the peripheral devices that
are attached to server that are known as clients. It depicts the prominent cable which is used to
connect the computers as switches are prominently used as the connection devices for the
physical star topology as it is most popular topology for network execution. In this, troubleshoot
is quite efficient as compared to bus topology and its network control is quite complex
concerning its features that can be easily executed as any changes made in star topology are
significantly accommodated.
(Source: What is Topology?, 2018)
5
Illustration 1: What is Topology?
Illustration 2: What is Topology?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
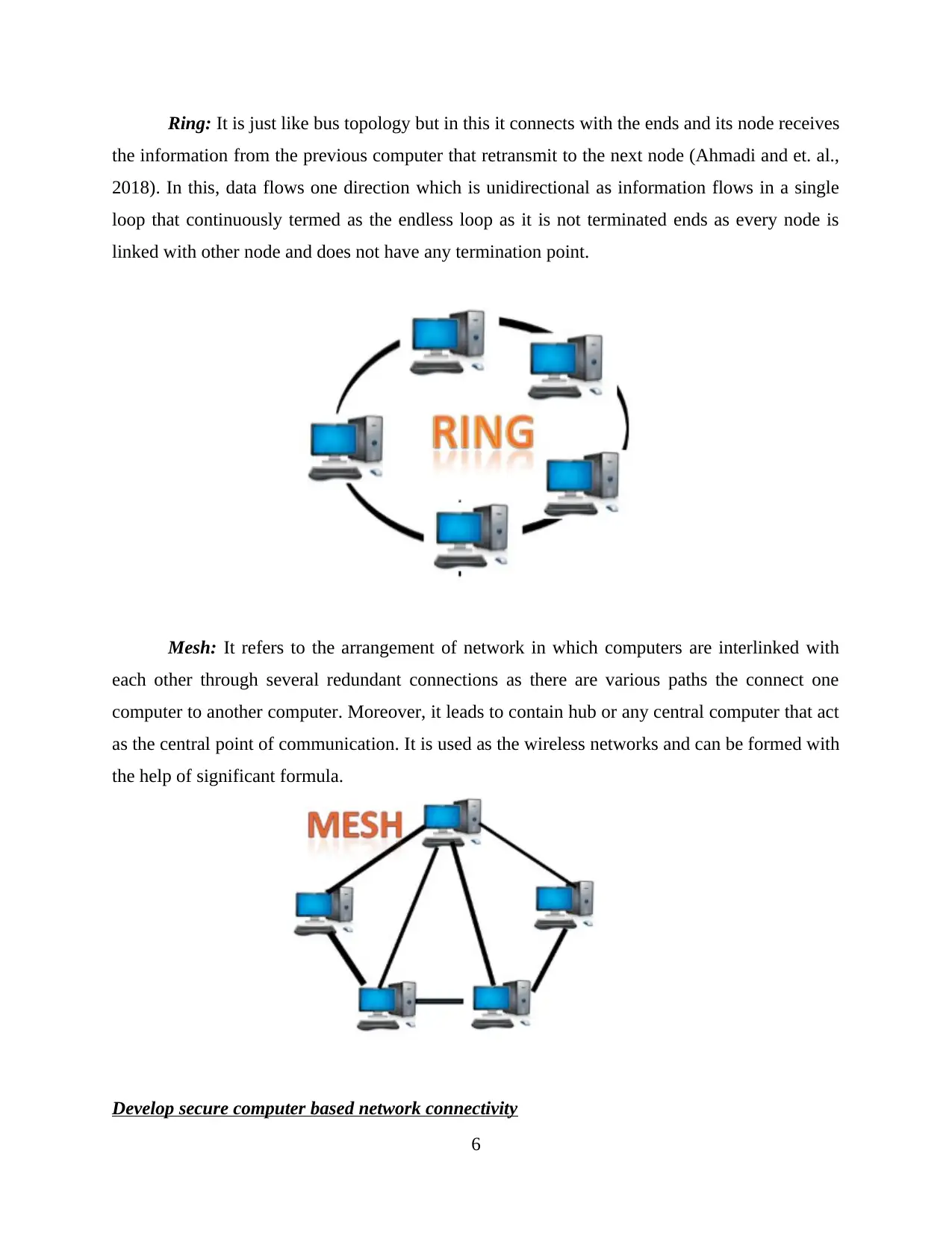
Ring: It is just like bus topology but in this it connects with the ends and its node receives
the information from the previous computer that retransmit to the next node (Ahmadi and et. al.,
2018). In this, data flows one direction which is unidirectional as information flows in a single
loop that continuously termed as the endless loop as it is not terminated ends as every node is
linked with other node and does not have any termination point.
Mesh: It refers to the arrangement of network in which computers are interlinked with
each other through several redundant connections as there are various paths the connect one
computer to another computer. Moreover, it leads to contain hub or any central computer that act
as the central point of communication. It is used as the wireless networks and can be formed with
the help of significant formula.
Develop secure computer based network connectivity
6
the information from the previous computer that retransmit to the next node (Ahmadi and et. al.,
2018). In this, data flows one direction which is unidirectional as information flows in a single
loop that continuously termed as the endless loop as it is not terminated ends as every node is
linked with other node and does not have any termination point.
Mesh: It refers to the arrangement of network in which computers are interlinked with
each other through several redundant connections as there are various paths the connect one
computer to another computer. Moreover, it leads to contain hub or any central computer that act
as the central point of communication. It is used as the wireless networks and can be formed with
the help of significant formula.
Develop secure computer based network connectivity
6

In relation with developing secure computer based network connectivity, effective audit
and mapping for the network should be performed for the prominent understanding of entire
network infrastructure which is basic configuration of firewall. After the audit, network should
be keep up to date and check software updates for the network infrastructure components. At that
time, they also need to make sure about effective developing security plan and also try to prevent
from the outsiders. In terms of this, the whole network should be encrypt undertaking the
capability of client which natively supported by windows as well.
Steps to set up LAN network
Equipment: In order to develop LAN network, firstly significant equipments are required
which include router, Ethernet cables for every devices in which an individual want to connect, a
computer system, devices and the broadband connection which include modem and router.
Connect the first computer: If the router is new then it is important to set up the
computer first and connect it to the router with the help of Ethernet cable. For this, windows PC
need to be prominently prompt in terms of developing wizard for the first connection and also
find it in the network and sharing centre in the control panel.
Set up Wi-Fi: The automatic setup wizard tends to take step by step development by the
effective process as by this people can have the prominent internet speed. It also tends to depict
the working of Wi-Fi and the devices that are connected to the Ethernet cables.
Connect to the internet: It depicts that every single devices tends to connect with the
LAN requirements and also set up with effective passcode in terms of connecting successfully to
7
and mapping for the network should be performed for the prominent understanding of entire
network infrastructure which is basic configuration of firewall. After the audit, network should
be keep up to date and check software updates for the network infrastructure components. At that
time, they also need to make sure about effective developing security plan and also try to prevent
from the outsiders. In terms of this, the whole network should be encrypt undertaking the
capability of client which natively supported by windows as well.
Steps to set up LAN network
Equipment: In order to develop LAN network, firstly significant equipments are required
which include router, Ethernet cables for every devices in which an individual want to connect, a
computer system, devices and the broadband connection which include modem and router.
Connect the first computer: If the router is new then it is important to set up the
computer first and connect it to the router with the help of Ethernet cable. For this, windows PC
need to be prominently prompt in terms of developing wizard for the first connection and also
find it in the network and sharing centre in the control panel.
Set up Wi-Fi: The automatic setup wizard tends to take step by step development by the
effective process as by this people can have the prominent internet speed. It also tends to depict
the working of Wi-Fi and the devices that are connected to the Ethernet cables.
Connect to the internet: It depicts that every single devices tends to connect with the
LAN requirements and also set up with effective passcode in terms of connecting successfully to
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the internet. For this, it should be make sure that the password should be protected and must have
the right firewalls that run for the safety.
Connect the remaining devices: It represent that it tends to connect with the remaining
devices such as printers and mobile devices that need significant internet connection in terms of
connecting with LAN and also able to use it more effectively. Therefore, it bring additional help
and also tends to make sure that this procedure run on smooth basis.
TASK 4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues
Troubleshooting is the network which is quite difficult at the best time but also try to do
this with limited data as it makes it more hard. A try to troubleshoot the network without
prominent information leads to cause the wrong problem. It also depicts various components in
terms of considering to be the part of problem (Siewiorek and Swarz, 2017). For instance,
understand about the hardware, software or connectivity problem as most of the times computer
users have patience in order to resolve technical problems, prominently undertaking the tight
scheduling and lack of downtime. In terms of this, following steps are mentioned as under:
Identify the issues: It include the prominent identification of problem as it is not possible
to find a prominent solution without considering the exact issue which is occurred in network. In
terms of this, there are various ways to analyse the issue including information gathering with the
help of questionnaires, survey and also identify the symptoms (Jiang, 2018).
Develop a theory of probable cause: For effectively solving issues it is important to
undertake prominent changes regarding effective development and try to solve prominent issues
that leads to cause suitable improvement. In this, it is important to effectively identify the
problem considering the various circumstances. Furthermore, more and more details are gathered
with the aim of eliminating variables and also consider error messages, event logs, diagnostic
outcome and effective monitoring (Bondar and et. al., 2017).
Attempt a fix based on findings: For this, effective focused experimentation is important
as to fix the problem root cause is essential. For this, individual can try tweaking changes
settings that are concerned with the problem and swapping out of the faulty parts, update drivers
and software and so on until the problem gets solve.
8
the right firewalls that run for the safety.
Connect the remaining devices: It represent that it tends to connect with the remaining
devices such as printers and mobile devices that need significant internet connection in terms of
connecting with LAN and also able to use it more effectively. Therefore, it bring additional help
and also tends to make sure that this procedure run on smooth basis.
TASK 4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues
Troubleshooting is the network which is quite difficult at the best time but also try to do
this with limited data as it makes it more hard. A try to troubleshoot the network without
prominent information leads to cause the wrong problem. It also depicts various components in
terms of considering to be the part of problem (Siewiorek and Swarz, 2017). For instance,
understand about the hardware, software or connectivity problem as most of the times computer
users have patience in order to resolve technical problems, prominently undertaking the tight
scheduling and lack of downtime. In terms of this, following steps are mentioned as under:
Identify the issues: It include the prominent identification of problem as it is not possible
to find a prominent solution without considering the exact issue which is occurred in network. In
terms of this, there are various ways to analyse the issue including information gathering with the
help of questionnaires, survey and also identify the symptoms (Jiang, 2018).
Develop a theory of probable cause: For effectively solving issues it is important to
undertake prominent changes regarding effective development and try to solve prominent issues
that leads to cause suitable improvement. In this, it is important to effectively identify the
problem considering the various circumstances. Furthermore, more and more details are gathered
with the aim of eliminating variables and also consider error messages, event logs, diagnostic
outcome and effective monitoring (Bondar and et. al., 2017).
Attempt a fix based on findings: For this, effective focused experimentation is important
as to fix the problem root cause is essential. For this, individual can try tweaking changes
settings that are concerned with the problem and swapping out of the faulty parts, update drivers
and software and so on until the problem gets solve.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Identify troubleshooting guide that include hardware, software and networking
Check hardware: It represent that check all the hardware connections in order to make
sure the connection properly and turn it on for effective working. It could become the prominent
problem behind the networking issues as there is no point to go through with the process of
troubleshooting network issues and also make sure the prominent switches that are at correct
position.
Use ipconfig: It is undertaken as the terminal and the default gateway for the IP address
of the next number as for this, computer is not receiving the valid IP address and it starts with
other things that is 169 and the computer is being allocated with valid IP address from the router.
Use ping and tracert: This stage depicts that the router is working fine and must have an
effective IP address that start with something like 169 and the problem is significantly located
among the router and the internet itself.
Perform a DNS check: In regard of this, company need to use tools and other command
which is “nslookup” in order to determine that the problem with the server is trying to connect or
not and also depict the response from the server.
Contact the ISP: From all the problems, it is effective to try and contact with the internet
service provider and see with the concerning issues. In terms of this, it is important to look up for
the outage maps and concerning information on the smartphones undertaking the same issues.
Check on malware and virus protection: It is also important to make sure about the virus
and malware techniques that run and also have flagged that tends to affect the prominent part of
network and also stop functioning.
9
Check hardware: It represent that check all the hardware connections in order to make
sure the connection properly and turn it on for effective working. It could become the prominent
problem behind the networking issues as there is no point to go through with the process of
troubleshooting network issues and also make sure the prominent switches that are at correct
position.
Use ipconfig: It is undertaken as the terminal and the default gateway for the IP address
of the next number as for this, computer is not receiving the valid IP address and it starts with
other things that is 169 and the computer is being allocated with valid IP address from the router.
Use ping and tracert: This stage depicts that the router is working fine and must have an
effective IP address that start with something like 169 and the problem is significantly located
among the router and the internet itself.
Perform a DNS check: In regard of this, company need to use tools and other command
which is “nslookup” in order to determine that the problem with the server is trying to connect or
not and also depict the response from the server.
Contact the ISP: From all the problems, it is effective to try and contact with the internet
service provider and see with the concerning issues. In terms of this, it is important to look up for
the outage maps and concerning information on the smartphones undertaking the same issues.
Check on malware and virus protection: It is also important to make sure about the virus
and malware techniques that run and also have flagged that tends to affect the prominent part of
network and also stop functioning.
9

Review database logs: Lastly, it is important to review the database logs to ensure the
effective functioning of data to match its expectations and consider the network performance.
P8. Conduct and document a range of maintenance activities with regards to computer hardware
and software
The effective management of hardware and software become more complex for the
corporate running for small number of applications. It depicts the complexity which leads to
increase the number of corporate users working on the road and remote areas for effective
management system. Moreover, it include the effective diagnostic and troubleshooting skills that
describe various ways for improvement like availability of heuristic which contains thinking for
the actual cause, confirmation bias that cause response for time metric for the evidence of
problem and so on. In terms of improving the troubleshooting skills, it is important to aware, get
feedback, practice, consider data and also identify what is happening. For this, an individual need
to consider data, identify and aware about the biases and other challenges for troubleshooting in
order to get problem solve much faster with better accuracy. Moreover, the future of IT
troubleshooting is based on analytical approaches.
Information gathering methods and techniques
System document: It depicts the system which is used in terms of receiving, tracking,
managing and storing documents for the elimination of paper. In terms of this, it is quite capable
in terms of keeping record for several versions that are created and modified by various users.
For this, the digital documents of management is based on computer programs (Benhlima, 2018).
As this term has some overlap with the prominent concept of content management system. It is
also viewed as the component of enterprise content management which is related with digital
asset management, document imagining, effective workflow system and recording management
systems.
User information: It include significant user related information which is duplication of
IP addresses for quickly fixing the issues and taking preventive measures. Exhaustion of IP
address as it use ipconfig command for the troubleshoot problem and other factors (Madhavan
and et. al., 2018). For this, at the time of network troubleshooting it is important to undertake
various informations for effective networking field which is important for the number of tools as
it is used for troubleshoot for the variety of several network conditions. In terms of this, specific
10
effective functioning of data to match its expectations and consider the network performance.
P8. Conduct and document a range of maintenance activities with regards to computer hardware
and software
The effective management of hardware and software become more complex for the
corporate running for small number of applications. It depicts the complexity which leads to
increase the number of corporate users working on the road and remote areas for effective
management system. Moreover, it include the effective diagnostic and troubleshooting skills that
describe various ways for improvement like availability of heuristic which contains thinking for
the actual cause, confirmation bias that cause response for time metric for the evidence of
problem and so on. In terms of improving the troubleshooting skills, it is important to aware, get
feedback, practice, consider data and also identify what is happening. For this, an individual need
to consider data, identify and aware about the biases and other challenges for troubleshooting in
order to get problem solve much faster with better accuracy. Moreover, the future of IT
troubleshooting is based on analytical approaches.
Information gathering methods and techniques
System document: It depicts the system which is used in terms of receiving, tracking,
managing and storing documents for the elimination of paper. In terms of this, it is quite capable
in terms of keeping record for several versions that are created and modified by various users.
For this, the digital documents of management is based on computer programs (Benhlima, 2018).
As this term has some overlap with the prominent concept of content management system. It is
also viewed as the component of enterprise content management which is related with digital
asset management, document imagining, effective workflow system and recording management
systems.
User information: It include significant user related information which is duplication of
IP addresses for quickly fixing the issues and taking preventive measures. Exhaustion of IP
address as it use ipconfig command for the troubleshoot problem and other factors (Madhavan
and et. al., 2018). For this, at the time of network troubleshooting it is important to undertake
various informations for effective networking field which is important for the number of tools as
it is used for troubleshoot for the variety of several network conditions. In terms of this, specific
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





