Password Cracking Tools: THC Hydra, John the Ripper, RainbowCrack, and Ophcrack
VerifiedAdded on 2023/01/03
|16
|2242
|86
AI Summary
This document provides an overview of different password cracking tools such as THC Hydra, John the Ripper, RainbowCrack, and Ophcrack. It explains their features, advantages, and how to use them. The document also discusses the best tool for cracking passwords and provides insights into computer security and network administration.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Computer Security 1
CO4509-COMPUTER SECURITY
(Student’s Name)
(Course Title)
(Tutor’s Name)
(Date)
CO4509-COMPUTER SECURITY
(Student’s Name)
(Course Title)
(Tutor’s Name)
(Date)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Computer Security 2
Table of Contents
Introduction......................................................................................................................................2
Overview of THC Hydra password.............................................................................................3
How to crack passwords using THC-Hydra................................................................................4
John the ripper Password Cracking tool..........................................................................................6
How to use John Ripper...............................................................................................................7
RainbowCrack Password Cracking tool..........................................................................................9
Overview of RainbowCrack tool.................................................................................................9
Using rainbowCrack tool...........................................................................................................11
Ophcrack........................................................................................................................................13
Overview of OphCrack..............................................................................................................13
How one can use Ophcrack LiveCD..........................................................................................14
Justification of the best tool...........................................................................................................15
References......................................................................................................................................16
Table of Contents
Introduction......................................................................................................................................2
Overview of THC Hydra password.............................................................................................3
How to crack passwords using THC-Hydra................................................................................4
John the ripper Password Cracking tool..........................................................................................6
How to use John Ripper...............................................................................................................7
RainbowCrack Password Cracking tool..........................................................................................9
Overview of RainbowCrack tool.................................................................................................9
Using rainbowCrack tool...........................................................................................................11
Ophcrack........................................................................................................................................13
Overview of OphCrack..............................................................................................................13
How one can use Ophcrack LiveCD..........................................................................................14
Justification of the best tool...........................................................................................................15
References......................................................................................................................................16

Computer Security 3
Introduction
Network security can be an overwhelming; the world of network security can be
complicated. Network administrators opt to use network security tools to assists in monitoring
Information Technology (IT) environment. One of the most popular form of attack is password
cracking. Password hacking software has evolved tremendously in the current 21st century.
Password hacking software usually involves a cracker brute forcing their way into a certain
website admin panel or a login page. There are several password cracking tools. Every tool has
its own advantages and disadvantages.
Passwords are cracked using three major forms which are brute force, dictionary, and
hybrid. Dictionary form of attack uses a list of worlds when they are encrypted at a time and
then checks if hashes are equal. Hybrid is done through mutation filters. This paper will be
covering four major password cracking tools which are; THC hydra, John the ripper,
RainbowCrack, and ophCrack.
THC Hydra password cracking tool
Overview of THC Hydra password
THC Hydra is a tool used by hackers to crack passwords by enforcing both brute force
attack and dictionary type of attack. Brute force implies that the software launches a number of
passwords at a login until the correct password is achieved. Since people want to use password
that they will not forget, they tend to use words that are common in their lives like their name,
football team, and place of birth. These information is easy to fetch in the social media and so
when the hacker has analyzed this data it be compiled into a password list, which is later used by
hydra to execute brute force attack. The password list combined with the easily known
passwords, will be taken by hydra which will execute the brute force attack. With time,
Introduction
Network security can be an overwhelming; the world of network security can be
complicated. Network administrators opt to use network security tools to assists in monitoring
Information Technology (IT) environment. One of the most popular form of attack is password
cracking. Password hacking software has evolved tremendously in the current 21st century.
Password hacking software usually involves a cracker brute forcing their way into a certain
website admin panel or a login page. There are several password cracking tools. Every tool has
its own advantages and disadvantages.
Passwords are cracked using three major forms which are brute force, dictionary, and
hybrid. Dictionary form of attack uses a list of worlds when they are encrypted at a time and
then checks if hashes are equal. Hybrid is done through mutation filters. This paper will be
covering four major password cracking tools which are; THC hydra, John the ripper,
RainbowCrack, and ophCrack.
THC Hydra password cracking tool
Overview of THC Hydra password
THC Hydra is a tool used by hackers to crack passwords by enforcing both brute force
attack and dictionary type of attack. Brute force implies that the software launches a number of
passwords at a login until the correct password is achieved. Since people want to use password
that they will not forget, they tend to use words that are common in their lives like their name,
football team, and place of birth. These information is easy to fetch in the social media and so
when the hacker has analyzed this data it be compiled into a password list, which is later used by
hydra to execute brute force attack. The password list combined with the easily known
passwords, will be taken by hydra which will execute the brute force attack. With time,

Computer Security 4
depending on the processor’s and internet’s speed, hydra will systematically execute each
password until the correct one is gotten. Incorporated in the Hydra package is the password-
inspector that reads passwords and output those that meet the requirements. If the cracking
session is successful, hydra outputs the log in name plus the password (Shema, 2014, p. 34).
The advantage of this tool is that it provides the hacker with various protocols to attack
and it is easy to add new modules to it. Hydra supports various modules like HTTP-
Proxy,Rlogin,MS-SQL,SMTP Enum, Cisco enable,Cisco auth,Cisco AAA, NNTP, PC-
Anywhere,PC-NTFS,LDAP among others. These modules make it efficient and easy to use. Also
the tool has the ability to perform what network administrators refer to as dictionary attacks
which is against over fifty protocols which includes ftp, smb, and telnet
How to crack passwords using THC-Hydra
One needs to first download the very recent version of THC hydra
Change the THC-hydra directory
Type ./configure and then make
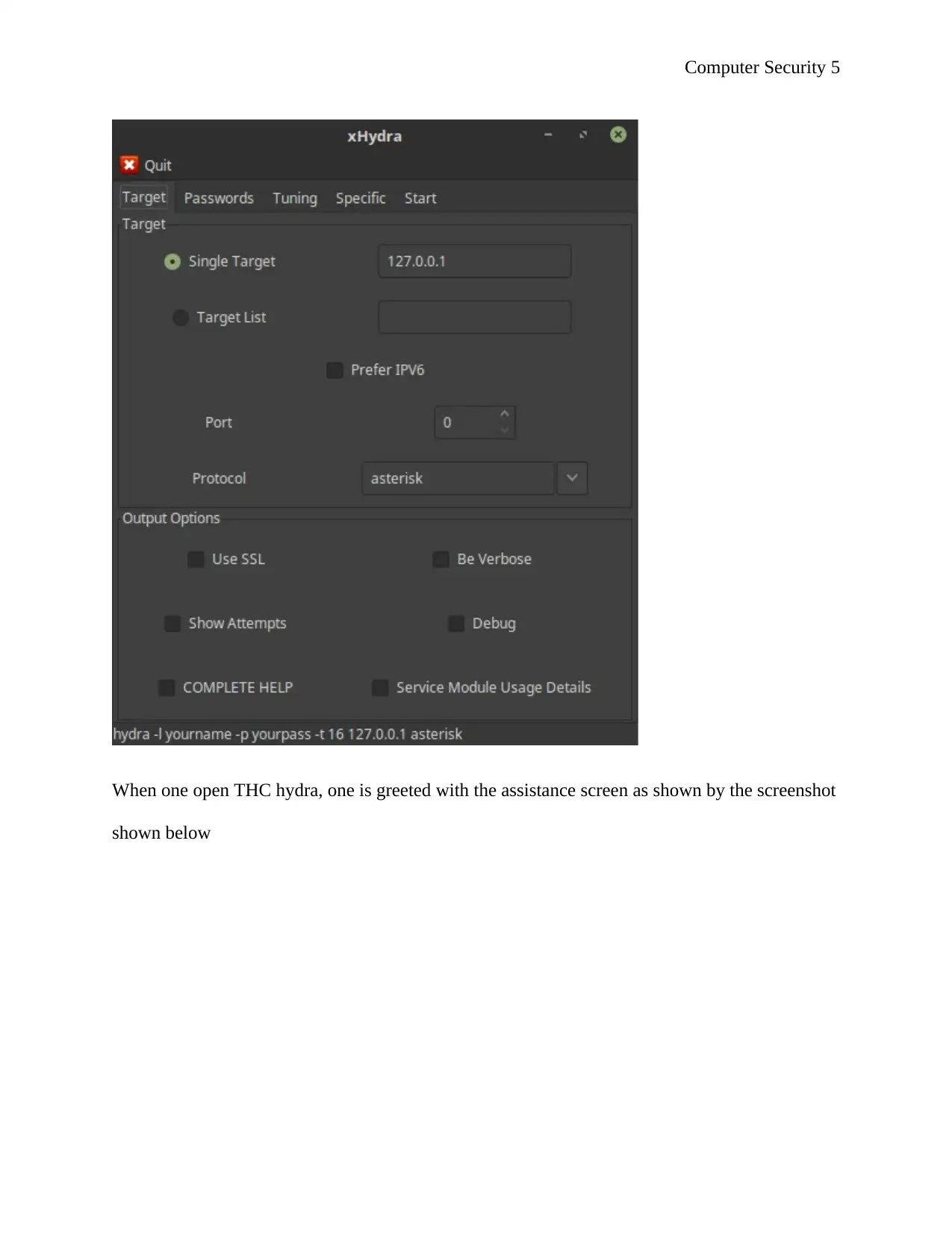
Once installed one has a new application which is reffered to as xHyra as shown by the
screenshot below
depending on the processor’s and internet’s speed, hydra will systematically execute each
password until the correct one is gotten. Incorporated in the Hydra package is the password-
inspector that reads passwords and output those that meet the requirements. If the cracking
session is successful, hydra outputs the log in name plus the password (Shema, 2014, p. 34).
The advantage of this tool is that it provides the hacker with various protocols to attack
and it is easy to add new modules to it. Hydra supports various modules like HTTP-
Proxy,Rlogin,MS-SQL,SMTP Enum, Cisco enable,Cisco auth,Cisco AAA, NNTP, PC-
Anywhere,PC-NTFS,LDAP among others. These modules make it efficient and easy to use. Also
the tool has the ability to perform what network administrators refer to as dictionary attacks
which is against over fifty protocols which includes ftp, smb, and telnet
How to crack passwords using THC-Hydra
One needs to first download the very recent version of THC hydra
Change the THC-hydra directory
Type ./configure and then make
Once installed one has a new application which is reffered to as xHyra as shown by the
screenshot below
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Computer Security 5
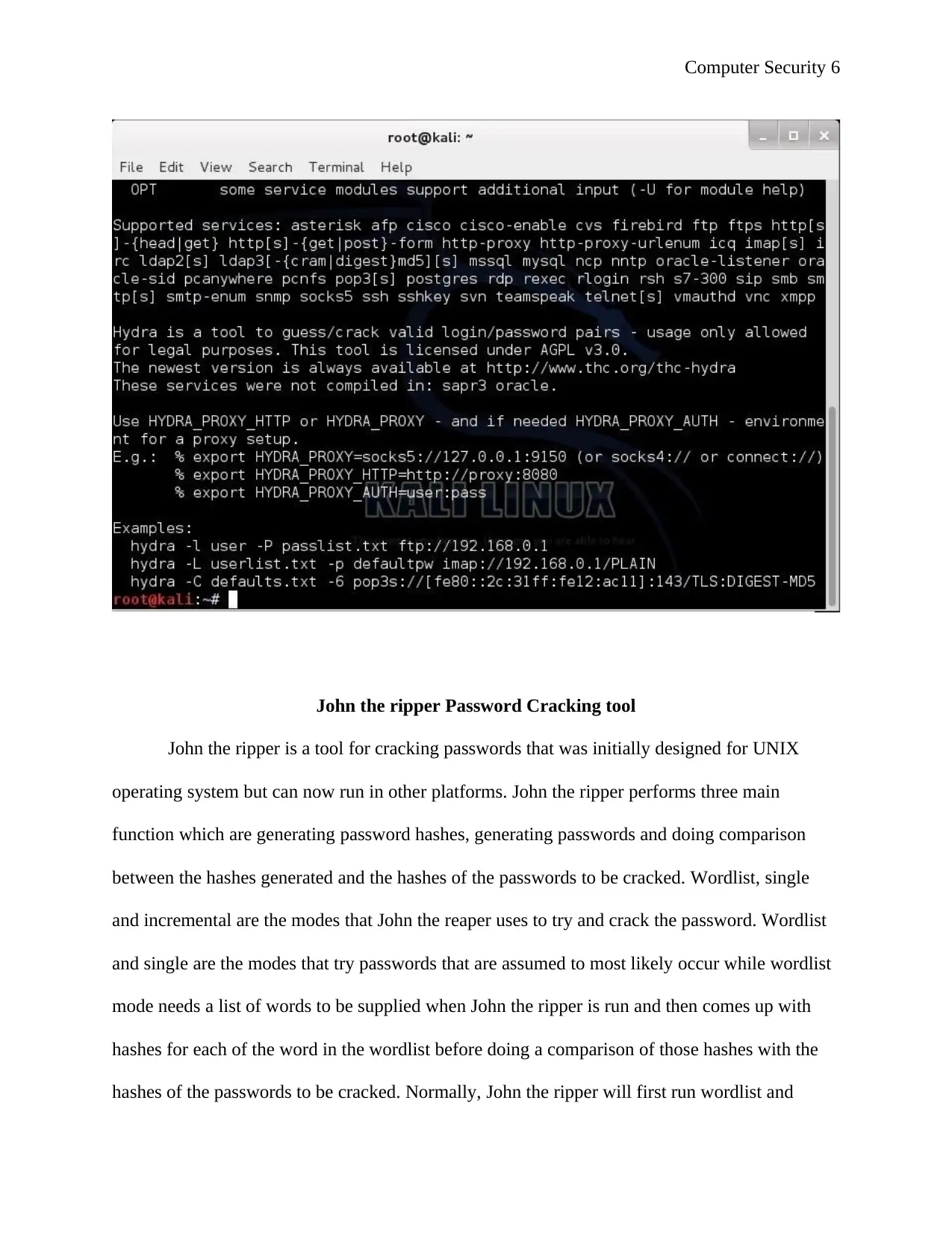
When one open THC hydra, one is greeted with the assistance screen as shown by the screenshot
shown below
When one open THC hydra, one is greeted with the assistance screen as shown by the screenshot
shown below
Computer Security 6
John the ripper Password Cracking tool
John the ripper is a tool for cracking passwords that was initially designed for UNIX
operating system but can now run in other platforms. John the ripper performs three main
function which are generating password hashes, generating passwords and doing comparison
between the hashes generated and the hashes of the passwords to be cracked. Wordlist, single
and incremental are the modes that John the reaper uses to try and crack the password. Wordlist
and single are the modes that try passwords that are assumed to most likely occur while wordlist
mode needs a list of words to be supplied when John the ripper is run and then comes up with
hashes for each of the word in the wordlist before doing a comparison of those hashes with the
hashes of the passwords to be cracked. Normally, John the ripper will first run wordlist and
John the ripper Password Cracking tool
John the ripper is a tool for cracking passwords that was initially designed for UNIX
operating system but can now run in other platforms. John the ripper performs three main
function which are generating password hashes, generating passwords and doing comparison
between the hashes generated and the hashes of the passwords to be cracked. Wordlist, single
and incremental are the modes that John the reaper uses to try and crack the password. Wordlist
and single are the modes that try passwords that are assumed to most likely occur while wordlist
mode needs a list of words to be supplied when John the ripper is run and then comes up with
hashes for each of the word in the wordlist before doing a comparison of those hashes with the
hashes of the passwords to be cracked. Normally, John the ripper will first run wordlist and
Computer Security 7
single mode before the incremental mode. The mode that needs processing power and time is the
incremental mode that come up with random passwords, creates hashes for them and then does
the comparison between those hashes and the hashes of the passwords to be cracked (Najera-
Gutierrez, 2016, p. 64).
Once the password is cracked it is printed at the terminal and saved in a file named
$JOHN/john.pot. This file is again used to not load password hashes that are already cracked the
next time you run John the ripper. If you wish to retrieve the passwords that have been cracked,
you only need to run ‘john - -show passwd’ command.
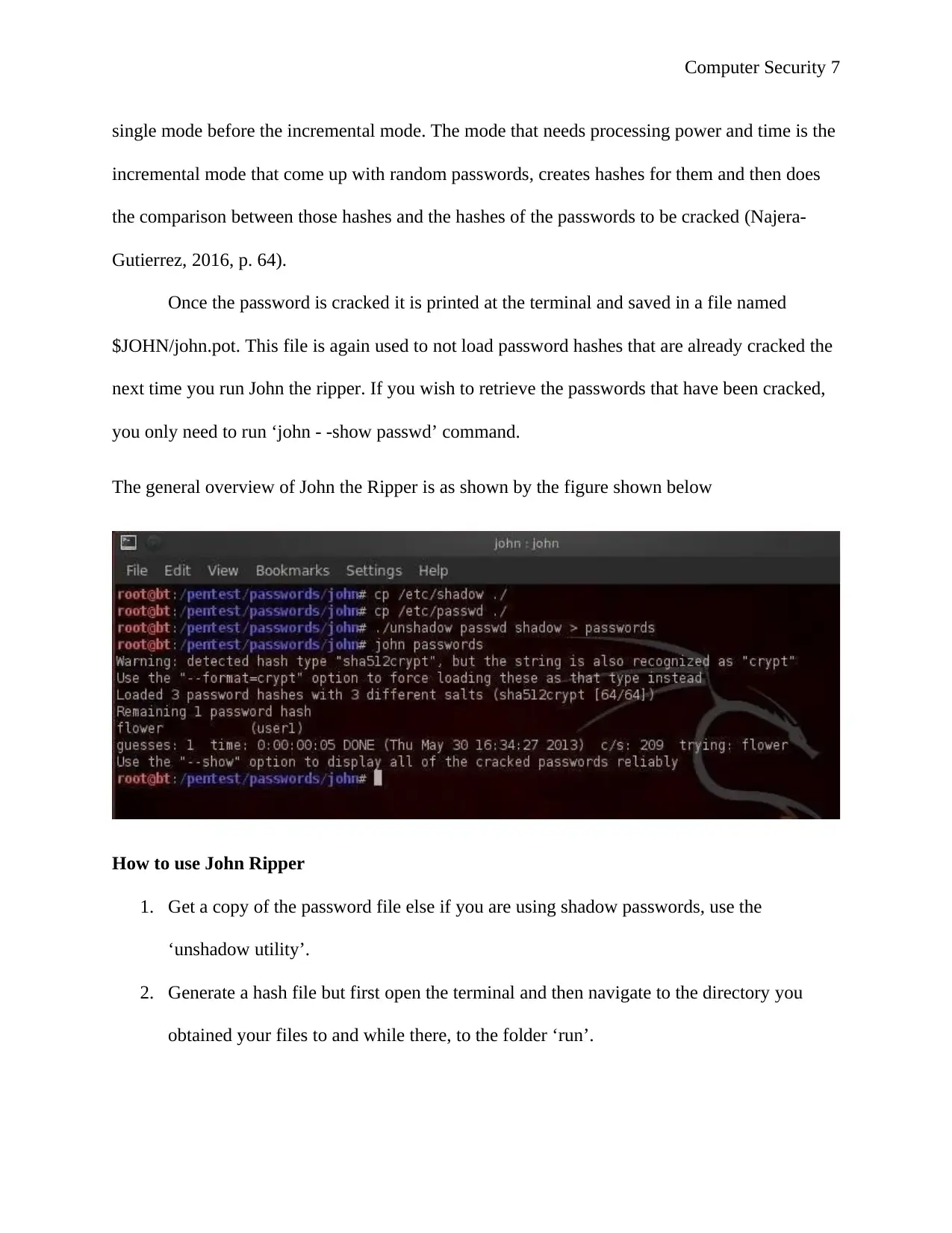
The general overview of John the Ripper is as shown by the figure shown below
How to use John Ripper
1. Get a copy of the password file else if you are using shadow passwords, use the
‘unshadow utility’.
2. Generate a hash file but first open the terminal and then navigate to the directory you
obtained your files to and while there, to the folder ‘run’.
single mode before the incremental mode. The mode that needs processing power and time is the
incremental mode that come up with random passwords, creates hashes for them and then does
the comparison between those hashes and the hashes of the passwords to be cracked (Najera-
Gutierrez, 2016, p. 64).
Once the password is cracked it is printed at the terminal and saved in a file named
$JOHN/john.pot. This file is again used to not load password hashes that are already cracked the
next time you run John the ripper. If you wish to retrieve the passwords that have been cracked,
you only need to run ‘john - -show passwd’ command.
The general overview of John the Ripper is as shown by the figure shown below
How to use John Ripper
1. Get a copy of the password file else if you are using shadow passwords, use the
‘unshadow utility’.
2. Generate a hash file but first open the terminal and then navigate to the directory you
obtained your files to and while there, to the folder ‘run’.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Computer Security 8
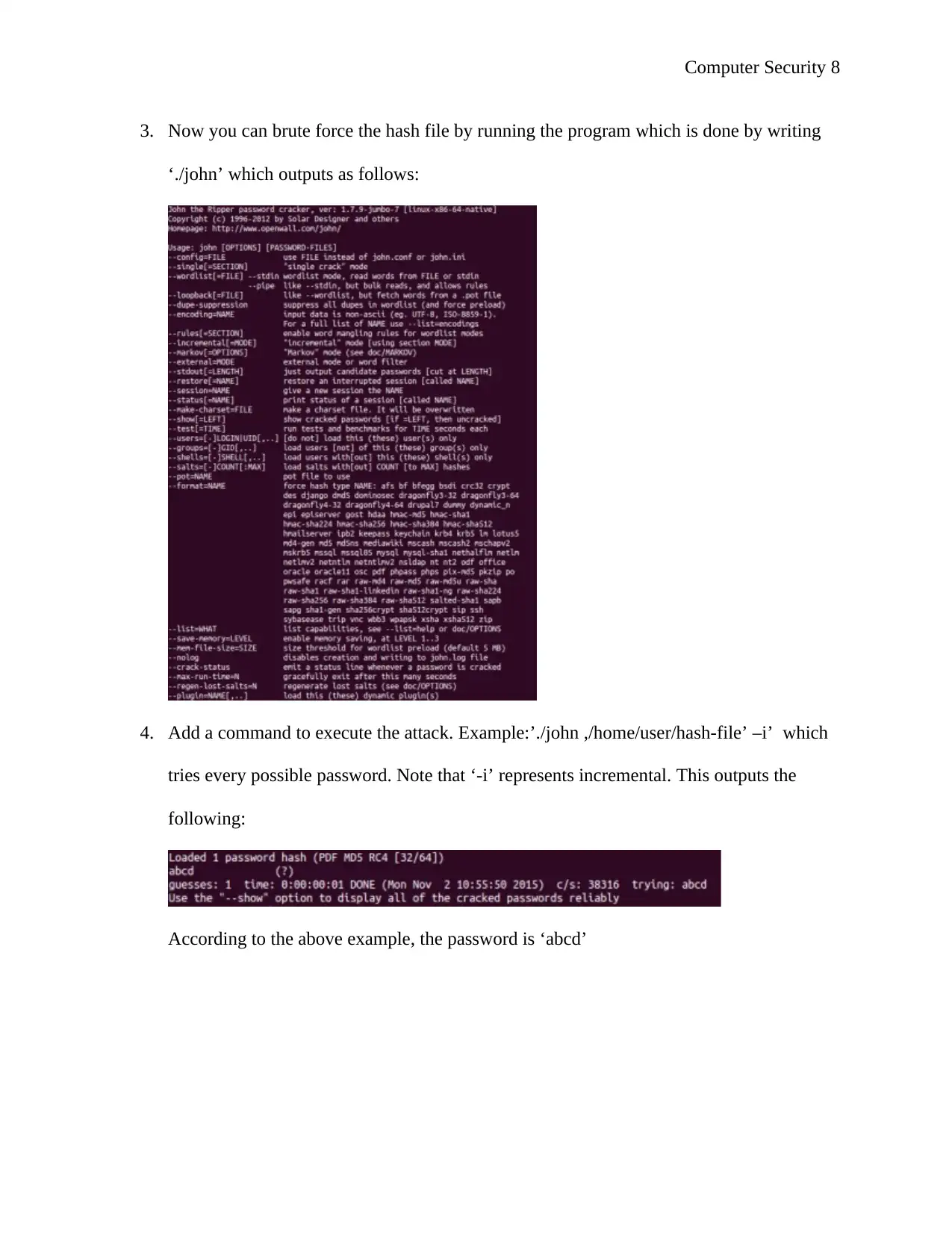
3. Now you can brute force the hash file by running the program which is done by writing
‘./john’ which outputs as follows:
4. Add a command to execute the attack. Example:’./john ,/home/user/hash-file’ –i’ which
tries every possible password. Note that ‘-i’ represents incremental. This outputs the
following:
According to the above example, the password is ‘abcd’
3. Now you can brute force the hash file by running the program which is done by writing
‘./john’ which outputs as follows:
4. Add a command to execute the attack. Example:’./john ,/home/user/hash-file’ –i’ which
tries every possible password. Note that ‘-i’ represents incremental. This outputs the
following:
According to the above example, the password is ‘abcd’

Computer Security 9
RainbowCrack Password Cracking tool
Overview of RainbowCrack tool
RainbowCrack is one of password cracking tools. It is one of the hash cracker tool which
uses a large-scale time-memory trade off process. Large-scale trade off process is employed for
faster password cracking than traditional brute force tools. In addition, time-memory trade-off is
a computational process where all hash pairs and plain text are calculated using a selected has
algorithm (Infosec, n.d).
RainbowCrack password cracker works by generating rainbow tables which are used by
password cracking. This type of tool differs from conventional brute force cracker in that the tool
uses large pre-computed tables so as to reduce the time needed for cracking password. The tool
was developed by Zhu Shuanglei but was originated in Phillippe Oechslin.
RainbowCrack tool has over ten features which are;
Support rainbow table for any charset
Runs of Linux OS
Runs of Windows OS platform
It is command line user based
It has GOU acceleration with several GPUs
Computation on multi-core processor support
Support rainbow table which are based on hash algorithm
Unified rainbow table file format which are supported operating systems
The look of rainbowCrack is as shown by the figure shown below
RainbowCrack Password Cracking tool
Overview of RainbowCrack tool
RainbowCrack is one of password cracking tools. It is one of the hash cracker tool which
uses a large-scale time-memory trade off process. Large-scale trade off process is employed for
faster password cracking than traditional brute force tools. In addition, time-memory trade-off is
a computational process where all hash pairs and plain text are calculated using a selected has
algorithm (Infosec, n.d).
RainbowCrack password cracker works by generating rainbow tables which are used by
password cracking. This type of tool differs from conventional brute force cracker in that the tool
uses large pre-computed tables so as to reduce the time needed for cracking password. The tool
was developed by Zhu Shuanglei but was originated in Phillippe Oechslin.
RainbowCrack tool has over ten features which are;
Support rainbow table for any charset
Runs of Linux OS
Runs of Windows OS platform
It is command line user based
It has GOU acceleration with several GPUs
Computation on multi-core processor support
Support rainbow table which are based on hash algorithm
Unified rainbow table file format which are supported operating systems
The look of rainbowCrack is as shown by the figure shown below

Computer Security 10
Figure 1: RainbowCrack tool
As shown by the figure shown above, there is a tab for Rainbow tables. Usually this tab is
used to reduce the difficulty in brute force by cracking a single password. This tab creates a pre-
Figure 1: RainbowCrack tool
As shown by the figure shown above, there is a tab for Rainbow tables. Usually this tab is
used to reduce the difficulty in brute force by cracking a single password. This tab creates a pre-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Computer Security 11
generated data set of hashes from every possible password. Rainbow Tables takes much more
time to create than the actual cracking a single hash.
Some of rainbow table configurations is as shown by table 1 below
Table 1: LM configuration
Charset [ABCDEFGHIJKLMNOPQRSTUVWXYZ]
Success probability 0.9990
Keyspace 8353082582
Table size 610 MB
The above type of configuration has a success probability of about 99.90 percent and it only
takes about 610 MB. RainbowCrack tool has several configurations; the first command is to start
table generation using the command (Gregg, 2015, p. 45)
Rtgeb md5 loweralpha-numeric 1 7 0 3899 33554432 o
Using rainbowCrack tool
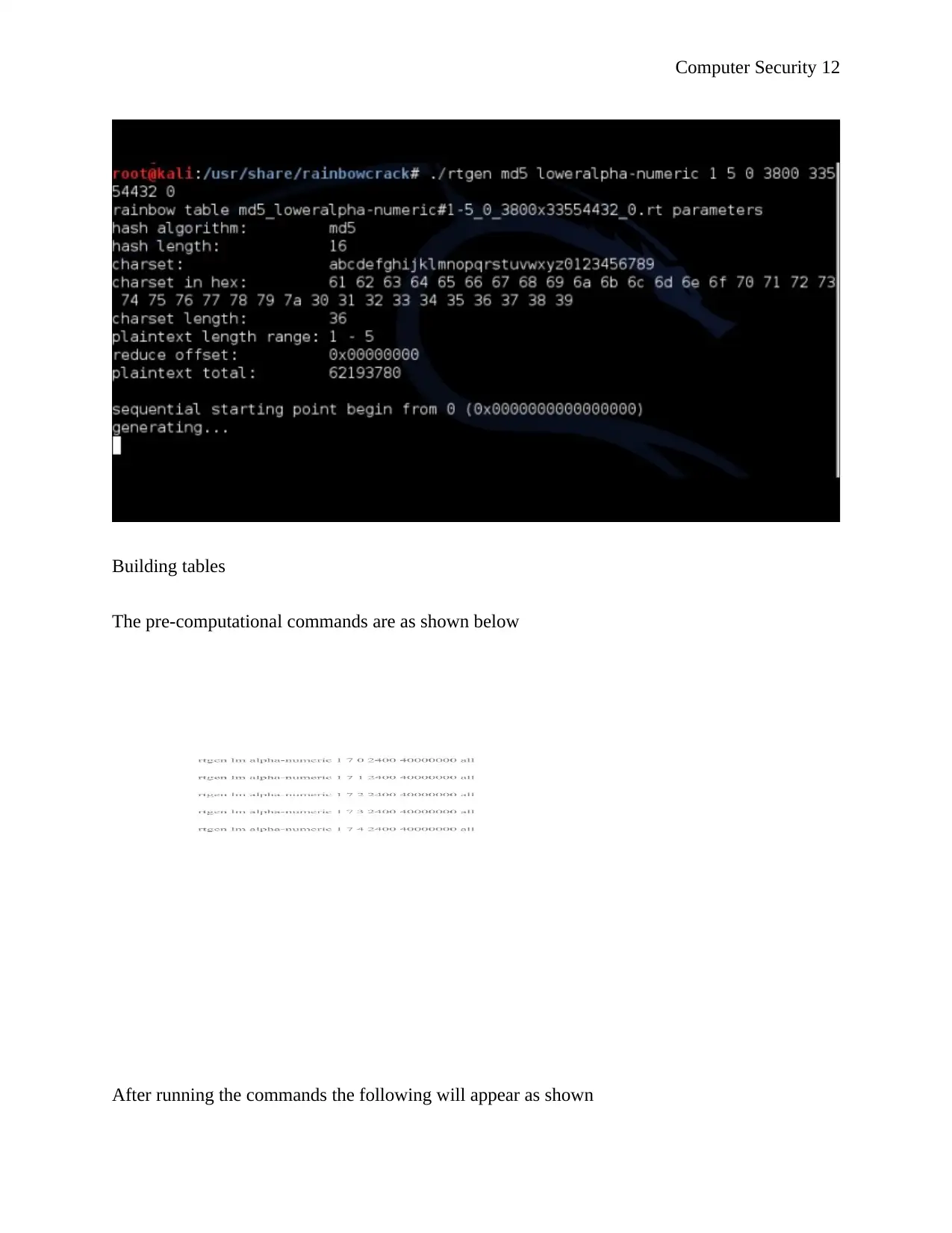
The tool that is used to generate Rainbow Tables usually comes along with RainbowCrack
download, the tool is rtgen on windows platform as shown by figure 2 shown below
Figure 2: Rainbow table generator
generated data set of hashes from every possible password. Rainbow Tables takes much more
time to create than the actual cracking a single hash.
Some of rainbow table configurations is as shown by table 1 below
Table 1: LM configuration
Charset [ABCDEFGHIJKLMNOPQRSTUVWXYZ]
Success probability 0.9990
Keyspace 8353082582
Table size 610 MB
The above type of configuration has a success probability of about 99.90 percent and it only
takes about 610 MB. RainbowCrack tool has several configurations; the first command is to start
table generation using the command (Gregg, 2015, p. 45)
Rtgeb md5 loweralpha-numeric 1 7 0 3899 33554432 o
Using rainbowCrack tool
The tool that is used to generate Rainbow Tables usually comes along with RainbowCrack
download, the tool is rtgen on windows platform as shown by figure 2 shown below
Figure 2: Rainbow table generator
Computer Security 12
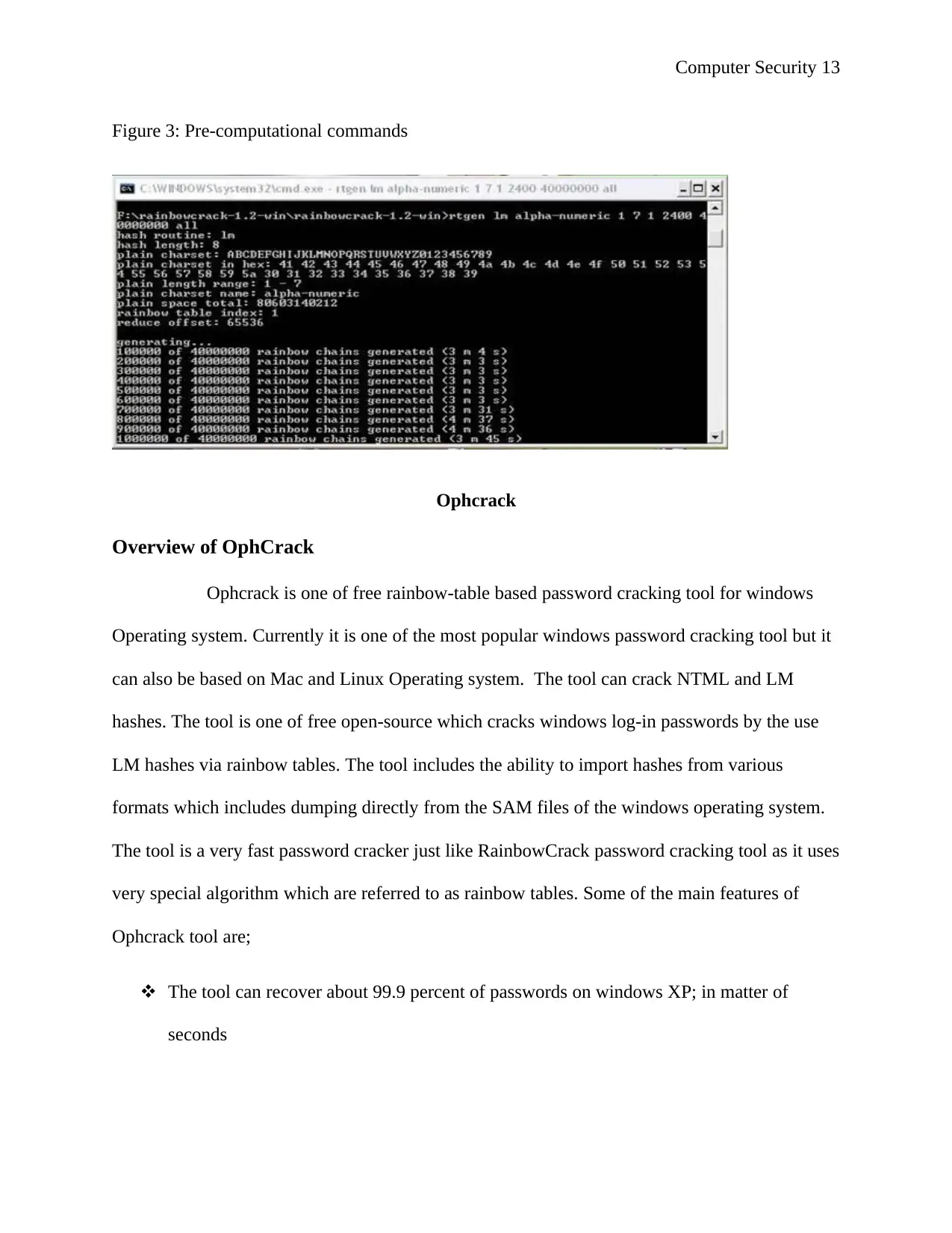
Building tables
The pre-computational commands are as shown below
After running the commands the following will appear as shown
Building tables
The pre-computational commands are as shown below
After running the commands the following will appear as shown
Computer Security 13
Figure 3: Pre-computational commands
Ophcrack
Overview of OphCrack
Ophcrack is one of free rainbow-table based password cracking tool for windows
Operating system. Currently it is one of the most popular windows password cracking tool but it
can also be based on Mac and Linux Operating system. The tool can crack NTML and LM
hashes. The tool is one of free open-source which cracks windows log-in passwords by the use
LM hashes via rainbow tables. The tool includes the ability to import hashes from various
formats which includes dumping directly from the SAM files of the windows operating system.
The tool is a very fast password cracker just like RainbowCrack password cracking tool as it uses
very special algorithm which are referred to as rainbow tables. Some of the main features of
Ophcrack tool are;
The tool can recover about 99.9 percent of passwords on windows XP; in matter of
seconds
Figure 3: Pre-computational commands
Ophcrack
Overview of OphCrack
Ophcrack is one of free rainbow-table based password cracking tool for windows
Operating system. Currently it is one of the most popular windows password cracking tool but it
can also be based on Mac and Linux Operating system. The tool can crack NTML and LM
hashes. The tool is one of free open-source which cracks windows log-in passwords by the use
LM hashes via rainbow tables. The tool includes the ability to import hashes from various
formats which includes dumping directly from the SAM files of the windows operating system.
The tool is a very fast password cracker just like RainbowCrack password cracking tool as it uses
very special algorithm which are referred to as rainbow tables. Some of the main features of
Ophcrack tool are;
The tool can recover about 99.9 percent of passwords on windows XP; in matter of
seconds
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Security 14
The tool can recover 99 percent of passwords from windows vista, windows 7, or
windows 8 which in this can case it slower than dictionary attack
The liveCD method usually requires no installation in windows thus making it safe
alternative to lots of other password recovery tools
As indicated by computer security analysis there is no windows which needs to be known
to use the Ophcrack live CD to crack windows passwords
Audit mode and CSV export
In here one uses real-time graphs to analyze the system passwords
How one can use Ophcrack LiveCD
One first need ti download the ISO file which contains image files
One can then burn the files on a USB flash disk or a DVD
One then needs to boot the computer system of the device which contains the password
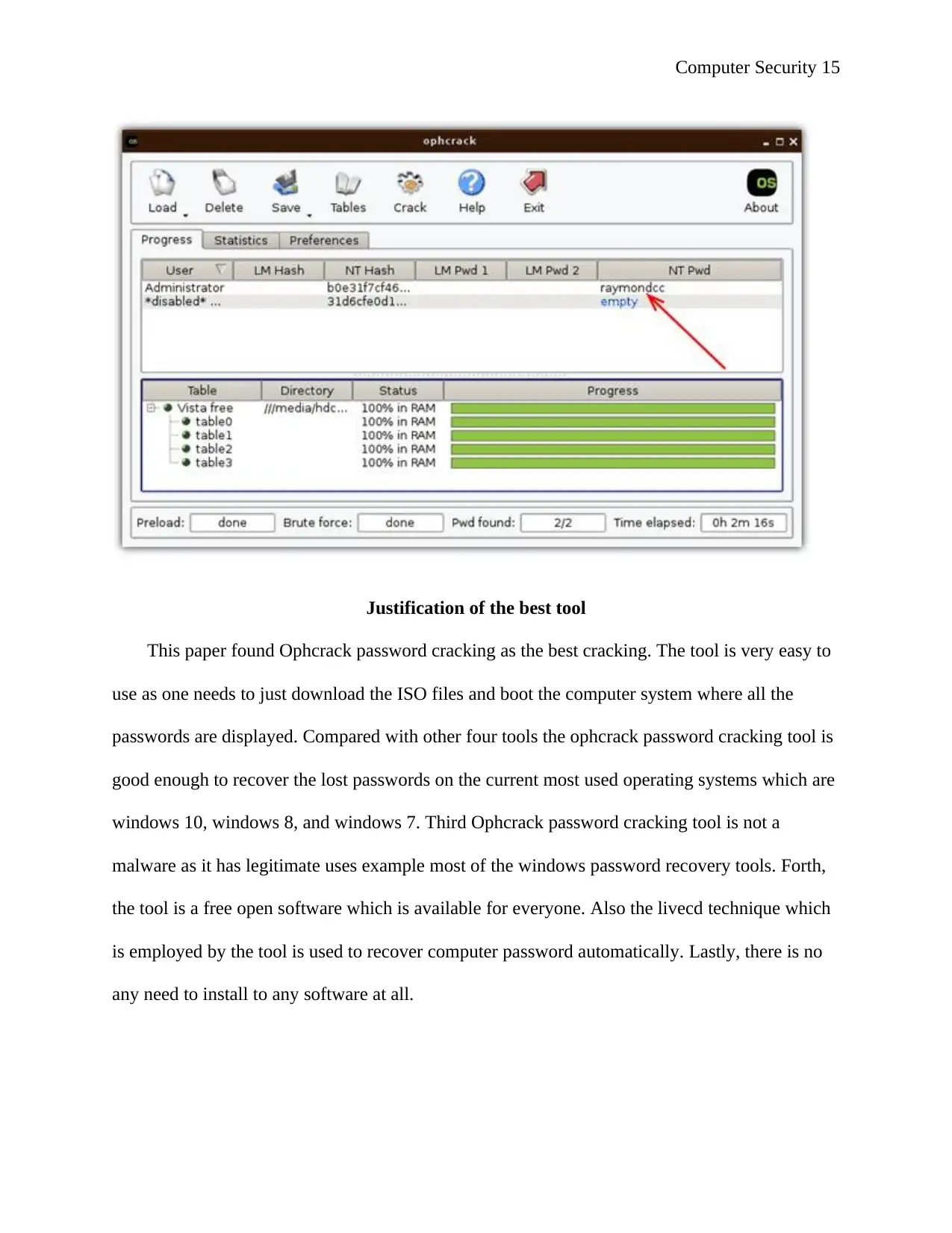
from the bootable flash drive or the CD. It will appear as shown by the figure below
The software will then locate the users on the windows system and here is where one
begins to crack the password
The process is usually automatic as one needs not to type anything or even click
anything; the passwords are displayed on the screen one only needs to write them down.
In this case it appeared as shown by the figure shown below
The tool can recover 99 percent of passwords from windows vista, windows 7, or
windows 8 which in this can case it slower than dictionary attack
The liveCD method usually requires no installation in windows thus making it safe
alternative to lots of other password recovery tools
As indicated by computer security analysis there is no windows which needs to be known
to use the Ophcrack live CD to crack windows passwords
Audit mode and CSV export
In here one uses real-time graphs to analyze the system passwords
How one can use Ophcrack LiveCD
One first need ti download the ISO file which contains image files
One can then burn the files on a USB flash disk or a DVD
One then needs to boot the computer system of the device which contains the password
from the bootable flash drive or the CD. It will appear as shown by the figure below
The software will then locate the users on the windows system and here is where one
begins to crack the password
The process is usually automatic as one needs not to type anything or even click
anything; the passwords are displayed on the screen one only needs to write them down.
In this case it appeared as shown by the figure shown below
Computer Security 15
Justification of the best tool
This paper found Ophcrack password cracking as the best cracking. The tool is very easy to
use as one needs to just download the ISO files and boot the computer system where all the
passwords are displayed. Compared with other four tools the ophcrack password cracking tool is
good enough to recover the lost passwords on the current most used operating systems which are
windows 10, windows 8, and windows 7. Third Ophcrack password cracking tool is not a
malware as it has legitimate uses example most of the windows password recovery tools. Forth,
the tool is a free open software which is available for everyone. Also the livecd technique which
is employed by the tool is used to recover computer password automatically. Lastly, there is no
any need to install to any software at all.
Justification of the best tool
This paper found Ophcrack password cracking as the best cracking. The tool is very easy to
use as one needs to just download the ISO files and boot the computer system where all the
passwords are displayed. Compared with other four tools the ophcrack password cracking tool is
good enough to recover the lost passwords on the current most used operating systems which are
windows 10, windows 8, and windows 7. Third Ophcrack password cracking tool is not a
malware as it has legitimate uses example most of the windows password recovery tools. Forth,
the tool is a free open software which is available for everyone. Also the livecd technique which
is employed by the tool is used to recover computer password automatically. Lastly, there is no
any need to install to any software at all.

Computer Security 16
References
Bradley, T., 2016. Essential Computer Security : Everyone's Guide to Email, Internet, and
Wireless Security. Rockland: Elsevier Science.
Gregg, M., 2015. The network security test lab : a step-by-step guide. 2nd ed. Hoboken: John
Wiley & Sons.
Infosec, n.d. Introduction to the 10 Most Popular Password Cracking Tools. [Online]
Available at: https://resources.infosecinstitute.com/10-popular-password-cracking-tools/#gref
[Accessed 27th August 2019].
Najera-Gutierrez, G., 2016. Kali Linux web penetration tools. 1st ed. Birmingham: Packt
Publishing.
Shema, M., 2014. Anti-hacker tool kit.. 1st ed. NewYork: McGraw-Hill Education.
References
Bradley, T., 2016. Essential Computer Security : Everyone's Guide to Email, Internet, and
Wireless Security. Rockland: Elsevier Science.
Gregg, M., 2015. The network security test lab : a step-by-step guide. 2nd ed. Hoboken: John
Wiley & Sons.
Infosec, n.d. Introduction to the 10 Most Popular Password Cracking Tools. [Online]
Available at: https://resources.infosecinstitute.com/10-popular-password-cracking-tools/#gref
[Accessed 27th August 2019].
Najera-Gutierrez, G., 2016. Kali Linux web penetration tools. 1st ed. Birmingham: Packt
Publishing.
Shema, M., 2014. Anti-hacker tool kit.. 1st ed. NewYork: McGraw-Hill Education.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





