Implementation and Evaluation of Penetration Testing Tools Report
VerifiedAdded on 2022/09/14
|11
|836
|16
Report
AI Summary
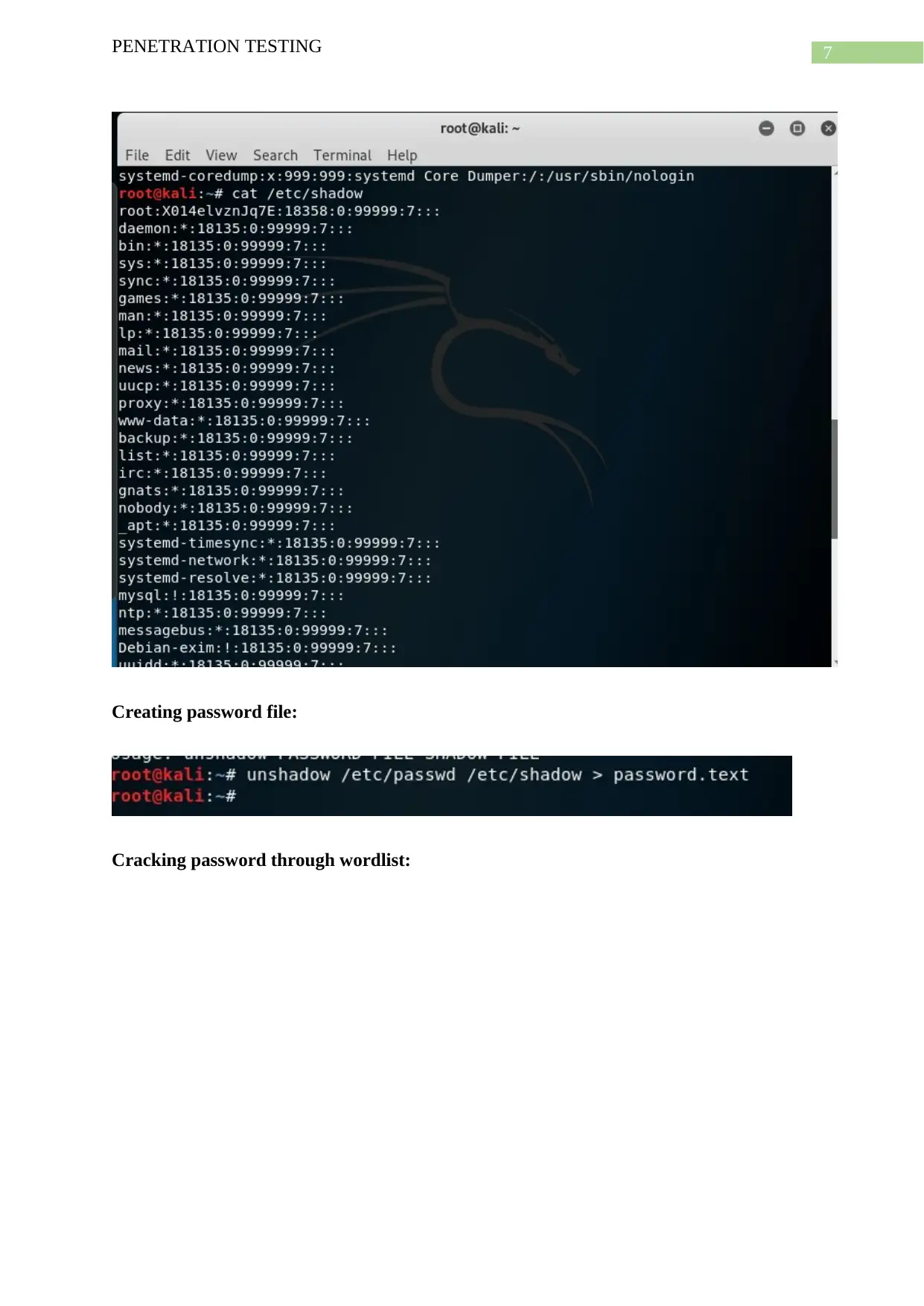
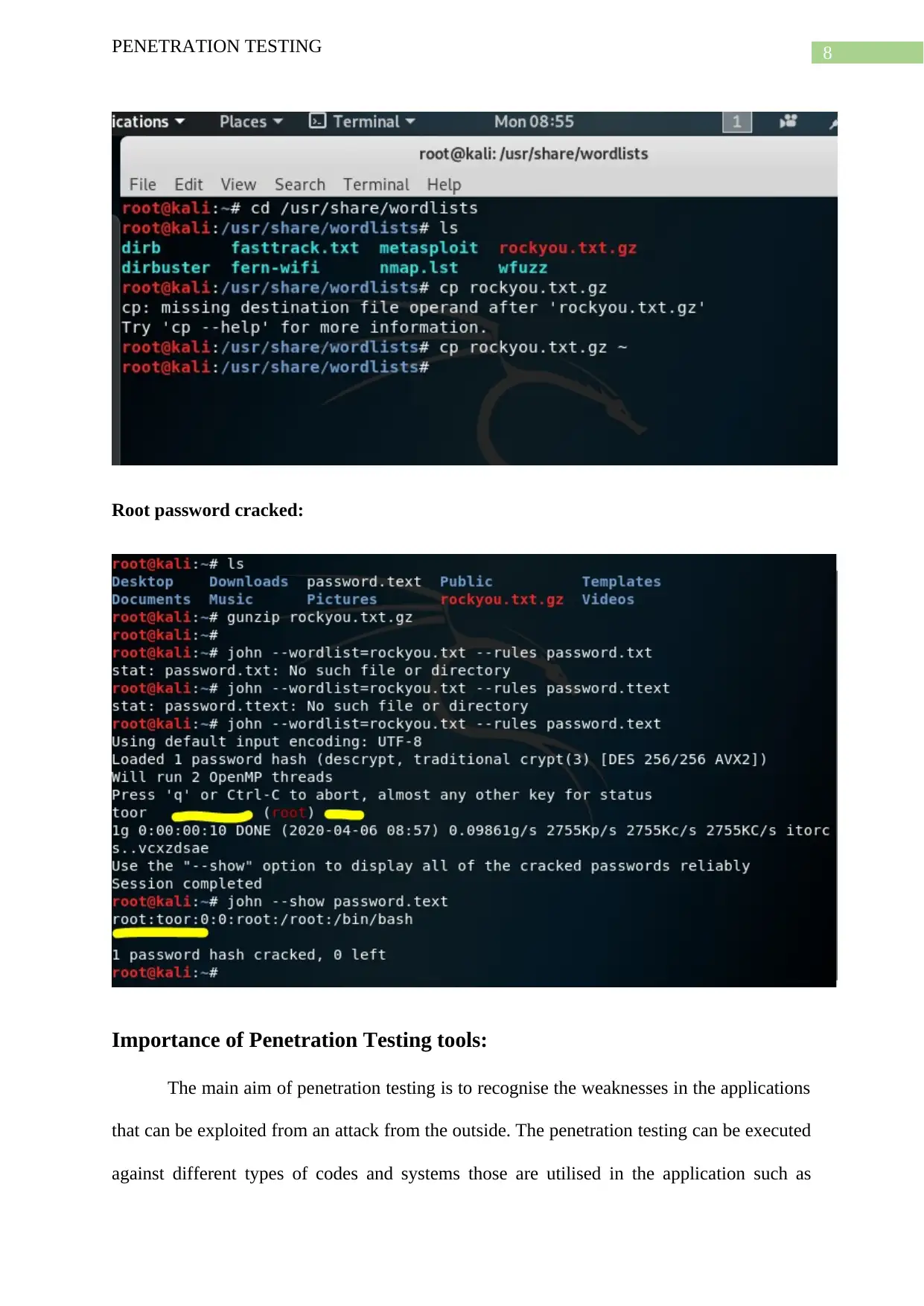
This report delves into the realm of penetration testing, focusing on the implementation and evaluation of security tools. It begins with an overview of password cracking, detailing its significance and methods, including the use of cryptographic hashes. The report then highlights Kali Linux, a Debian-based distribution designed for digital forensics and penetration testing, and its pre-installed tools such as Armitage, Nmap, Wireshark, and John the Ripper. It then provides a detailed examination of two specific password cracking tools: THC Hydra and John the Ripper, including their commands and functionalities. The report underscores the importance of penetration testing tools in identifying vulnerabilities and weaknesses in applications, emphasizing that these tools are crucial for preventing security breaches. Finally, it lists the attributes of penetration testing tools, such as result visualization, detailed reporting, scheduled scans, API access, and the ability to scan multiple targets simultaneously. The report concludes by referencing various sources related to penetration testing and related technologies.
1 out of 11











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)