Detailed Security Evaluation and Investigation of WidgetsInc System
VerifiedAdded on 2021/06/17
|25
|4292
|26
Report
AI Summary
This report presents a security evaluation of the WidgetsInc system, conducted using a VMware virtual machine. The investigation utilized various tools and techniques, including Linux commands, to identify vulnerabilities. The report details the security investigation process, including authorization, privacy, authenticity, and integrity checks. It covers the use of tools such as VMware Workstation Player, Nikto, Httrack, Nmap, Traceroute, and John the Ripper. The findings highlight easily identifiable usernames and passwords, and the presence of unwanted processes. The report suggests steps to secure the system, such as strengthening passwords, minimizing software, and checking for open ports and non-root accounts. Additionally, the report discusses the use of Fail2ban as an Intrusion Detection System (IDS) to mitigate brute-force attacks and protect against potential security breaches. The conclusion emphasizes the importance of robust security measures to protect sensitive data and ensure system efficiency.

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
1. Introduction.......................................................................................................................................2
2. Security Investigation........................................................................................................................3
3. Tools and Techniques........................................................................................................................8
4. Results obtained...............................................................................................................................14
5. Steps to Secure the System..............................................................................................................19
6. Security Issues found in the designed system................................................................................15
7. Conclusion........................................................................................................................................22
8. References........................................................................................................................................23
1
1. Introduction.......................................................................................................................................2
2. Security Investigation........................................................................................................................3
3. Tools and Techniques........................................................................................................................8
4. Results obtained...............................................................................................................................14
5. Steps to Secure the System..............................................................................................................19
6. Security Issues found in the designed system................................................................................15
7. Conclusion........................................................................................................................................22
8. References........................................................................................................................................23
1

1. Introduction
This project is going to evaluate the security of the system which is provided by the WidgetsInc.
The Benny VandergastInc provided the VMware virtual machine for testing the security of the
software. The evaluation process of security of the system will be performed on the virtual
machine image which was given. In this project, various types of tools and techniques will be
used to investigate the security of the system. After investigating the security of the system, the
security issues encountered in the given system will be removed and explained. The
resultobtained from the investigation of the security of the system will be explained. Then, how
to enhance the system security and its efficiency will be proposed.
2
This project is going to evaluate the security of the system which is provided by the WidgetsInc.
The Benny VandergastInc provided the VMware virtual machine for testing the security of the
software. The evaluation process of security of the system will be performed on the virtual
machine image which was given. In this project, various types of tools and techniques will be
used to investigate the security of the system. After investigating the security of the system, the
security issues encountered in the given system will be removed and explained. The
resultobtained from the investigation of the security of the system will be explained. Then, how
to enhance the system security and its efficiency will be proposed.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
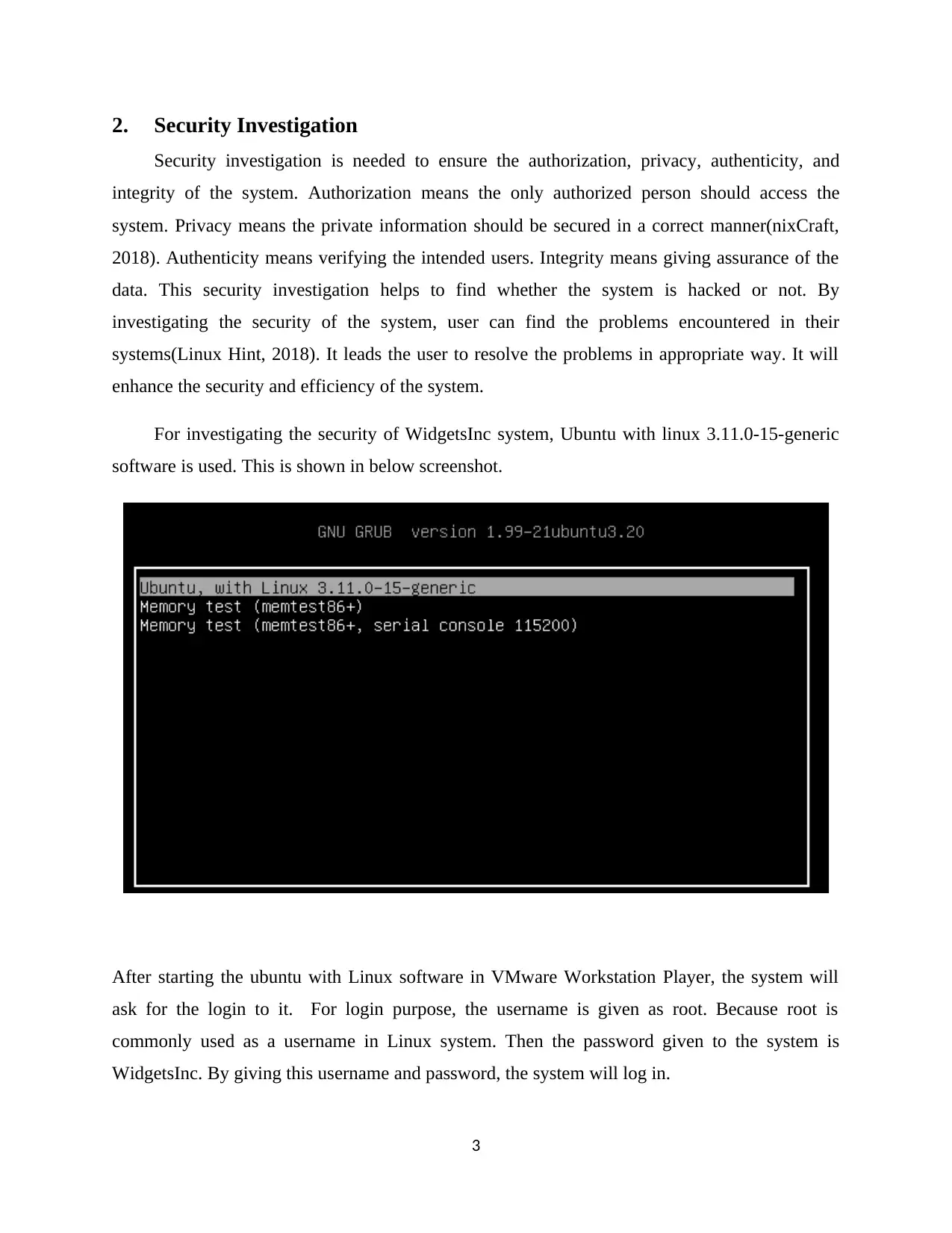
2. Security Investigation
Security investigation is needed to ensure the authorization, privacy, authenticity, and
integrity of the system. Authorization means the only authorized person should access the
system. Privacy means the private information should be secured in a correct manner(nixCraft,
2018). Authenticity means verifying the intended users. Integrity means giving assurance of the
data. This security investigation helps to find whether the system is hacked or not. By
investigating the security of the system, user can find the problems encountered in their
systems(Linux Hint, 2018). It leads the user to resolve the problems in appropriate way. It will
enhance the security and efficiency of the system.
For investigating the security of WidgetsInc system, Ubuntu with linux 3.11.0-15-generic
software is used. This is shown in below screenshot.
After starting the ubuntu with Linux software in VMware Workstation Player, the system will
ask for the login to it. For login purpose, the username is given as root. Because root is
commonly used as a username in Linux system. Then the password given to the system is
WidgetsInc. By giving this username and password, the system will log in.
3
Security investigation is needed to ensure the authorization, privacy, authenticity, and
integrity of the system. Authorization means the only authorized person should access the
system. Privacy means the private information should be secured in a correct manner(nixCraft,
2018). Authenticity means verifying the intended users. Integrity means giving assurance of the
data. This security investigation helps to find whether the system is hacked or not. By
investigating the security of the system, user can find the problems encountered in their
systems(Linux Hint, 2018). It leads the user to resolve the problems in appropriate way. It will
enhance the security and efficiency of the system.
For investigating the security of WidgetsInc system, Ubuntu with linux 3.11.0-15-generic
software is used. This is shown in below screenshot.
After starting the ubuntu with Linux software in VMware Workstation Player, the system will
ask for the login to it. For login purpose, the username is given as root. Because root is
commonly used as a username in Linux system. Then the password given to the system is
WidgetsInc. By giving this username and password, the system will log in.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
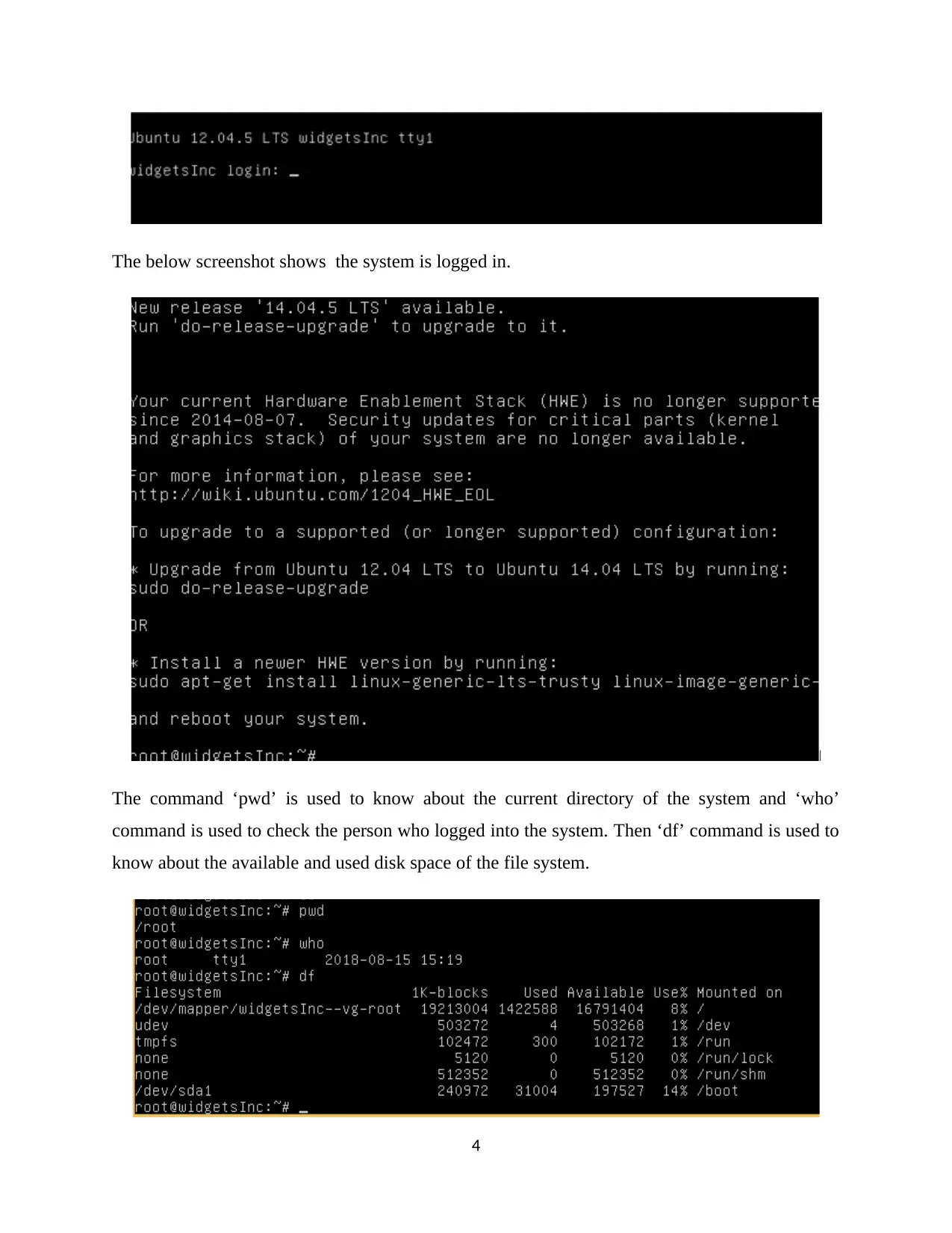
The below screenshot shows the system is logged in.
The command ‘pwd’ is used to know about the current directory of the system and ‘who’
command is used to check the person who logged into the system. Then ‘df’ command is used to
know about the available and used disk space of the file system.
4
The command ‘pwd’ is used to know about the current directory of the system and ‘who’
command is used to check the person who logged into the system. Then ‘df’ command is used to
know about the available and used disk space of the file system.
4
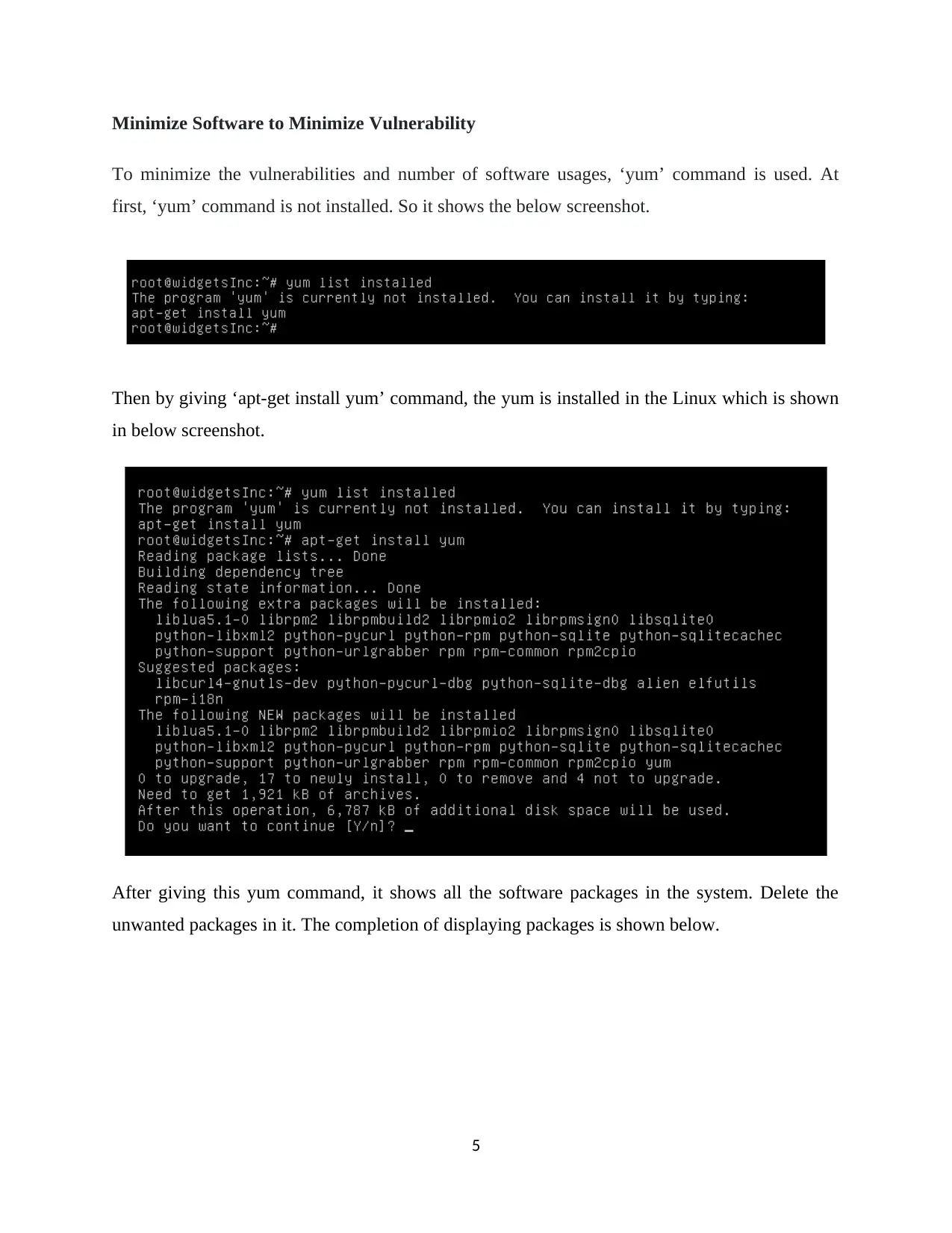
Minimize Software to Minimize Vulnerability
To minimize the vulnerabilities and number of software usages, ‘yum’ command is used. At
first, ‘yum’ command is not installed. So it shows the below screenshot.
Then by giving ‘apt-get install yum’ command, the yum is installed in the Linux which is shown
in below screenshot.
After giving this yum command, it shows all the software packages in the system. Delete the
unwanted packages in it. The completion of displaying packages is shown below.
5
To minimize the vulnerabilities and number of software usages, ‘yum’ command is used. At
first, ‘yum’ command is not installed. So it shows the below screenshot.
Then by giving ‘apt-get install yum’ command, the yum is installed in the Linux which is shown
in below screenshot.
After giving this yum command, it shows all the software packages in the system. Delete the
unwanted packages in it. The completion of displaying packages is shown below.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
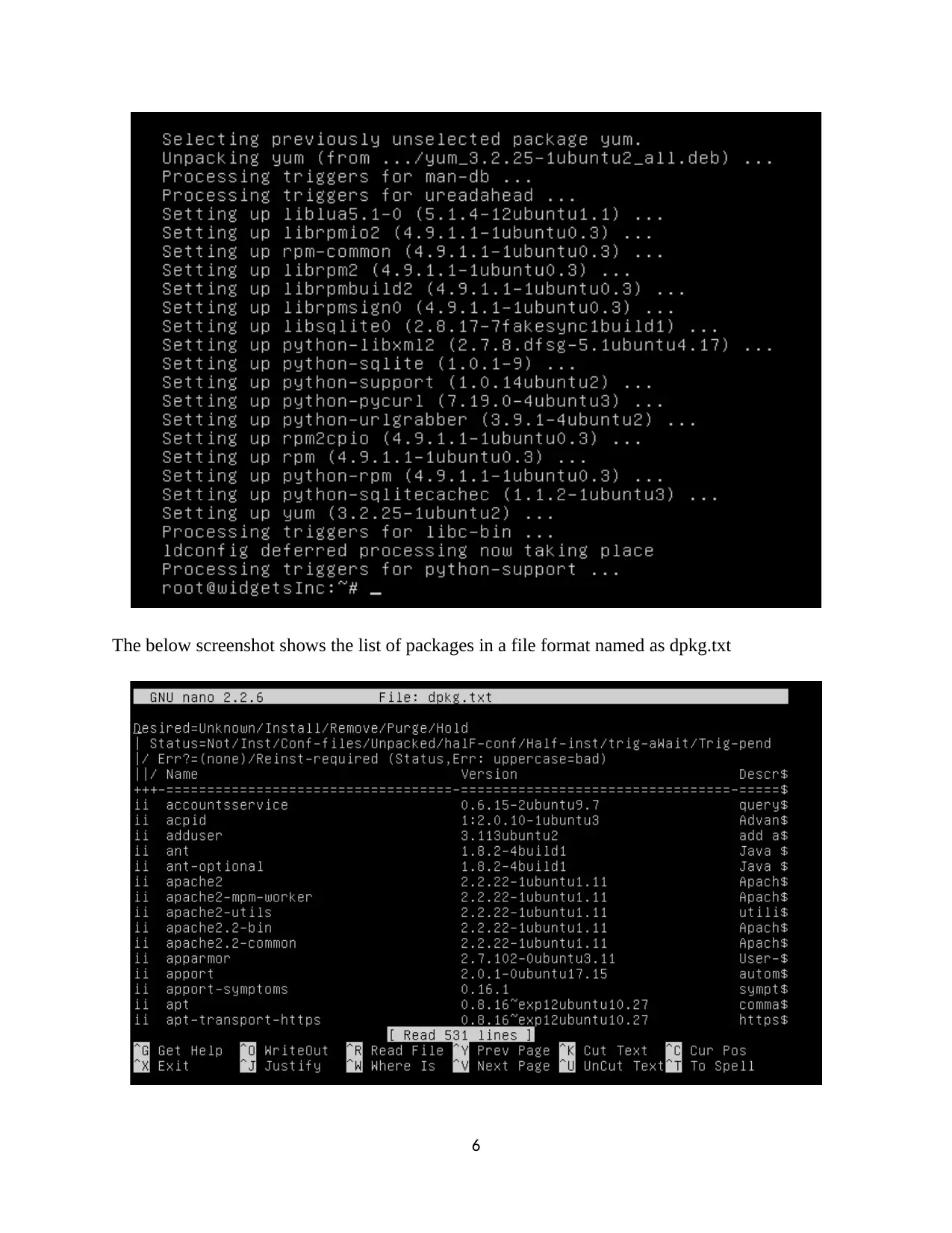
The below screenshot shows the list of packages in a file format named as dpkg.txt
6
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Unwanted Processors on the machine
By using ‘ps aux’ command, all running processes in the WidgetsInc machine are displayed with
their Process ID (PID). It is shown in the below screenshot. If the user wants to remove the
unwanted processes in the system, then ‘kill’ command is used to remove it along with its PID.
From below screenshot, if the user wants to remove the process named ‘whoopsie’ from the
system, then the following command is used. ‘# kill 1418’. It results in the removal of the
whoopsie process from the system.
3. Tools and Techniques
Security Tool
The encryption, firewalls, authentication, detection, and filters are the security tools for Linux.
Encryption used for encoding the hidden files in the form of IP security and it also analyzes the
sender and the communications between sender and receiver and nowadays more technologies
are developed as encrypted file sharing systems (Uprit, 2018). And then firewalls work as a filter
used to block the traffic and it also worked against worms and crackers. While traffic occurs, the
filters are used for blocking and the intruders’ detection is used when the attacker hack the
7
By using ‘ps aux’ command, all running processes in the WidgetsInc machine are displayed with
their Process ID (PID). It is shown in the below screenshot. If the user wants to remove the
unwanted processes in the system, then ‘kill’ command is used to remove it along with its PID.
From below screenshot, if the user wants to remove the process named ‘whoopsie’ from the
system, then the following command is used. ‘# kill 1418’. It results in the removal of the
whoopsie process from the system.
3. Tools and Techniques
Security Tool
The encryption, firewalls, authentication, detection, and filters are the security tools for Linux.
Encryption used for encoding the hidden files in the form of IP security and it also analyzes the
sender and the communications between sender and receiver and nowadays more technologies
are developed as encrypted file sharing systems (Uprit, 2018). And then firewalls work as a filter
used to block the traffic and it also worked against worms and crackers. While traffic occurs, the
filters are used for blocking and the intruders’ detection is used when the attacker hack the
7

system and honeypots are used to protect from the attacker (Anon, 2018). And the virtual
machine is used for running multiple computers on the same system.
VMware Workstation Player
VM ware player is a tool which runs multiple software and products for virtualization. It allows
running the second OS in a single system. It allows the user to create a virtual machine and it can
able to work without disturbing the normal system simultaneously. It is useful for testing client-
server environments.
Virtual machine performs all the operations in a logical manner. The virtual machine can be
affected by underlying programs in computers (nixCraft, 2018). Using this type of computer
system we can easily degrade the performance of the virtual machine. The one processor can do
the complete control of all virtual machines. (Ieeexplore.ieee.org, 2018). The two steps are
followed to build the security system. One is the antivirus detection system and the other is the
intrusion detection system. All the hackers are vulnerable to the system of security. The special
type of operating system now we are using is the modern operating system.
In the modern operating system, it has a various number of processor. The User can make the
impact of the isolation process between two different processes. In the virtual machine, the
underlying software’s is used (Linux capability vulnerability, 2000). The virtual machines have
an ability to control computers.
Nikto
Nikto is a web server testing tool and it is also an open source web server scanner. NIKTO is a
web server testing tool which is used for finding all sorts of hidden issues in a web application. It
also is known as ‘web vulnerability scanner’(Kali Linux – Assuring Security by Penetration
Testing, 2014). NIKTO web server scanning is a straightforward process which means that from
a single command user can get whether there are vulnerabilities or not in the server. This
command is given with the IP address of the machine. This is given in below screenshot.
8
machine is used for running multiple computers on the same system.
VMware Workstation Player
VM ware player is a tool which runs multiple software and products for virtualization. It allows
running the second OS in a single system. It allows the user to create a virtual machine and it can
able to work without disturbing the normal system simultaneously. It is useful for testing client-
server environments.
Virtual machine performs all the operations in a logical manner. The virtual machine can be
affected by underlying programs in computers (nixCraft, 2018). Using this type of computer
system we can easily degrade the performance of the virtual machine. The one processor can do
the complete control of all virtual machines. (Ieeexplore.ieee.org, 2018). The two steps are
followed to build the security system. One is the antivirus detection system and the other is the
intrusion detection system. All the hackers are vulnerable to the system of security. The special
type of operating system now we are using is the modern operating system.
In the modern operating system, it has a various number of processor. The User can make the
impact of the isolation process between two different processes. In the virtual machine, the
underlying software’s is used (Linux capability vulnerability, 2000). The virtual machines have
an ability to control computers.
Nikto
Nikto is a web server testing tool and it is also an open source web server scanner. NIKTO is a
web server testing tool which is used for finding all sorts of hidden issues in a web application. It
also is known as ‘web vulnerability scanner’(Kali Linux – Assuring Security by Penetration
Testing, 2014). NIKTO web server scanning is a straightforward process which means that from
a single command user can get whether there are vulnerabilities or not in the server. This
command is given with the IP address of the machine. This is given in below screenshot.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
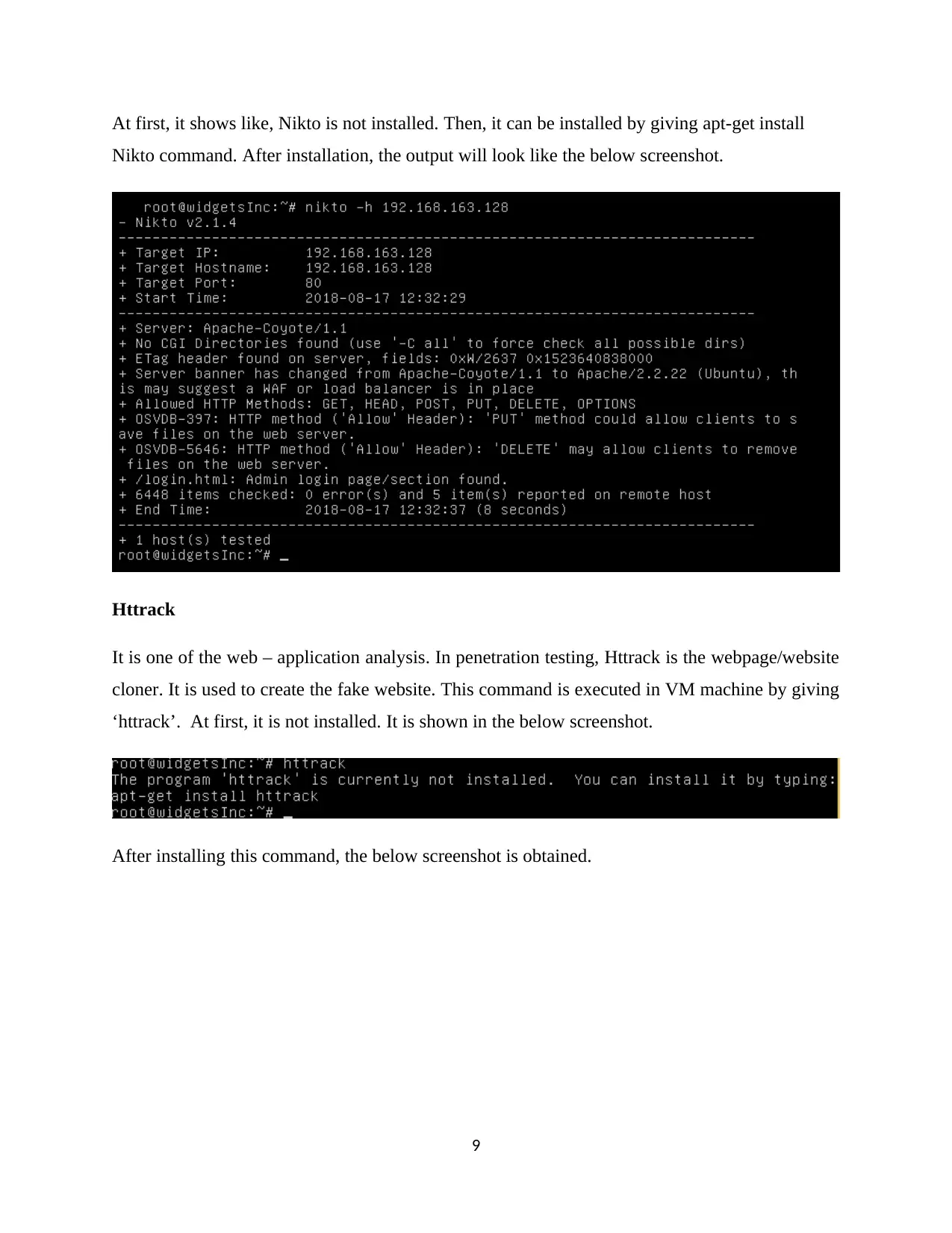
At first, it shows like, Nikto is not installed. Then, it can be installed by giving apt-get install
Nikto command. After installation, the output will look like the below screenshot.
Httrack
It is one of the web – application analysis. In penetration testing, Httrack is the webpage/website
cloner. It is used to create the fake website. This command is executed in VM machine by giving
‘httrack’. At first, it is not installed. It is shown in the below screenshot.
After installing this command, the below screenshot is obtained.
9
Nikto command. After installation, the output will look like the below screenshot.
Httrack
It is one of the web – application analysis. In penetration testing, Httrack is the webpage/website
cloner. It is used to create the fake website. This command is executed in VM machine by giving
‘httrack’. At first, it is not installed. It is shown in the below screenshot.
After installing this command, the below screenshot is obtained.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
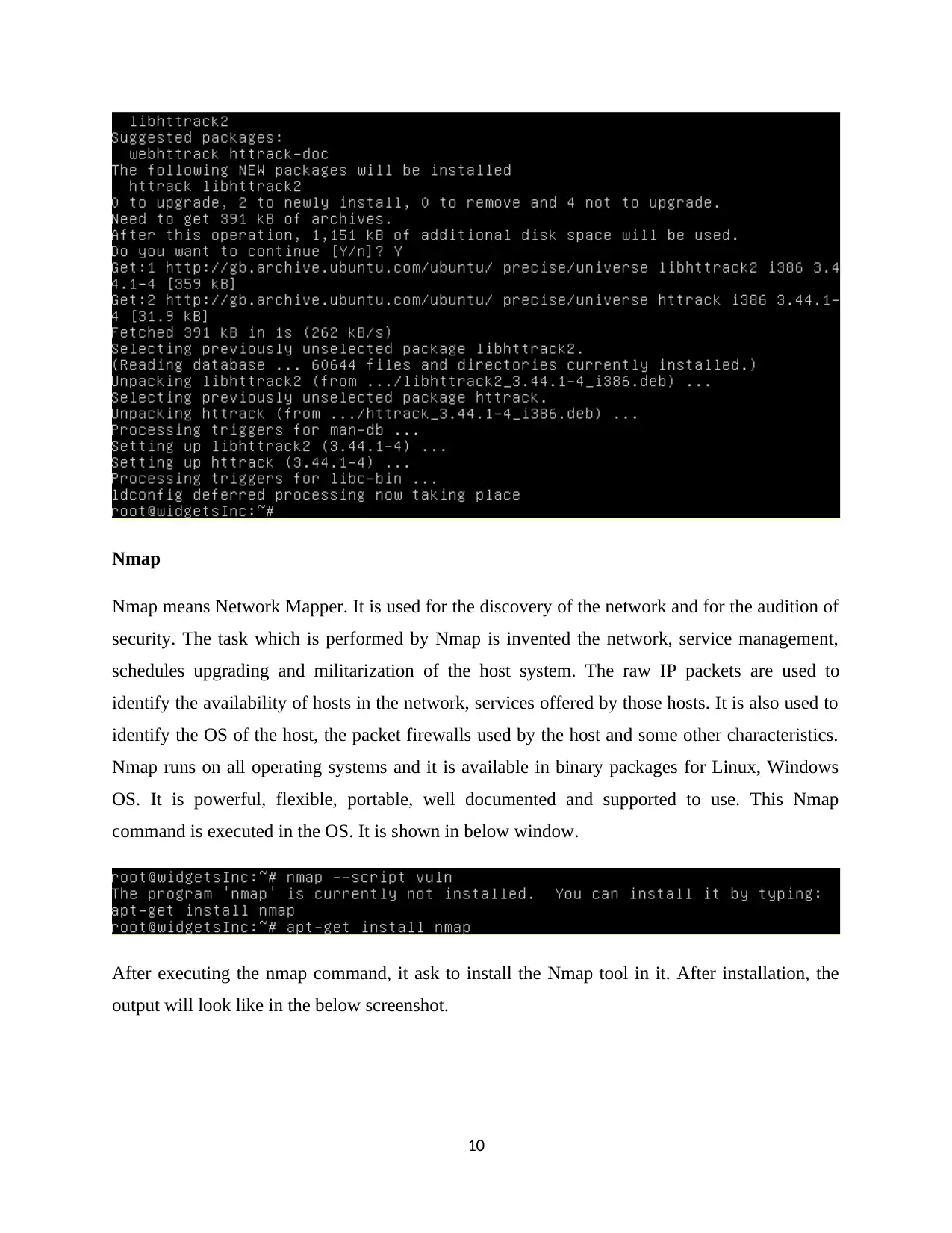
Nmap
Nmap means Network Mapper. It is used for the discovery of the network and for the audition of
security. The task which is performed by Nmap is invented the network, service management,
schedules upgrading and militarization of the host system. The raw IP packets are used to
identify the availability of hosts in the network, services offered by those hosts. It is also used to
identify the OS of the host, the packet firewalls used by the host and some other characteristics.
Nmap runs on all operating systems and it is available in binary packages for Linux, Windows
OS. It is powerful, flexible, portable, well documented and supported to use. This Nmap
command is executed in the OS. It is shown in below window.
After executing the nmap command, it ask to install the Nmap tool in it. After installation, the
output will look like in the below screenshot.
10
Nmap means Network Mapper. It is used for the discovery of the network and for the audition of
security. The task which is performed by Nmap is invented the network, service management,
schedules upgrading and militarization of the host system. The raw IP packets are used to
identify the availability of hosts in the network, services offered by those hosts. It is also used to
identify the OS of the host, the packet firewalls used by the host and some other characteristics.
Nmap runs on all operating systems and it is available in binary packages for Linux, Windows
OS. It is powerful, flexible, portable, well documented and supported to use. This Nmap
command is executed in the OS. It is shown in below window.
After executing the nmap command, it ask to install the Nmap tool in it. After installation, the
output will look like in the below screenshot.
10
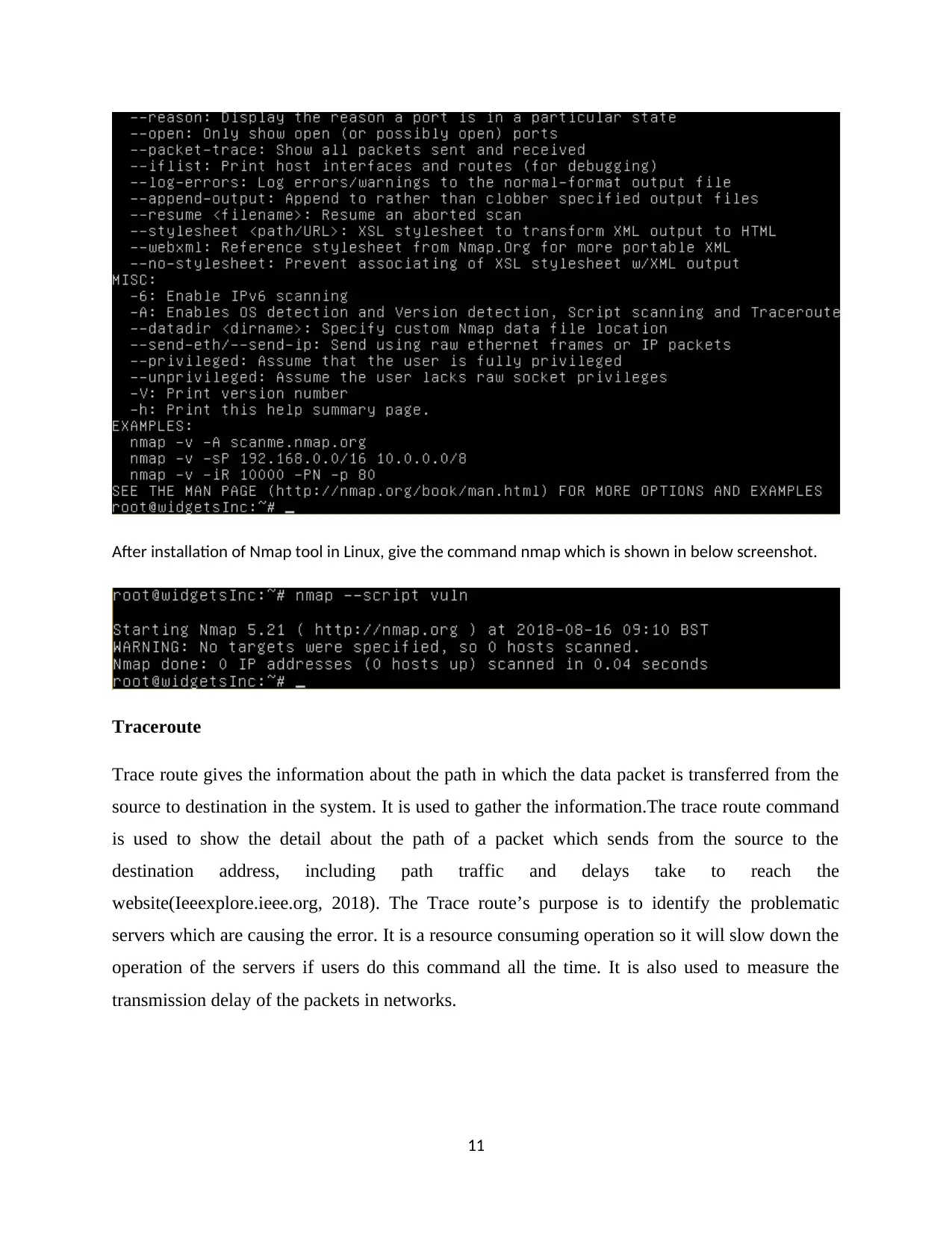
After installation of Nmap tool in Linux, give the command nmap which is shown in below screenshot.
Traceroute
Trace route gives the information about the path in which the data packet is transferred from the
source to destination in the system. It is used to gather the information.The trace route command
is used to show the detail about the path of a packet which sends from the source to the
destination address, including path traffic and delays take to reach the
website(Ieeexplore.ieee.org, 2018). The Trace route’s purpose is to identify the problematic
servers which are causing the error. It is a resource consuming operation so it will slow down the
operation of the servers if users do this command all the time. It is also used to measure the
transmission delay of the packets in networks.
11
Traceroute
Trace route gives the information about the path in which the data packet is transferred from the
source to destination in the system. It is used to gather the information.The trace route command
is used to show the detail about the path of a packet which sends from the source to the
destination address, including path traffic and delays take to reach the
website(Ieeexplore.ieee.org, 2018). The Trace route’s purpose is to identify the problematic
servers which are causing the error. It is a resource consuming operation so it will slow down the
operation of the servers if users do this command all the time. It is also used to measure the
transmission delay of the packets in networks.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





