Computer System Architecture: A Comprehensive Guide
VerifiedAdded on 2024/07/01
|28
|4842
|497
AI Summary
This report delves into the fundamental concepts of computer system architecture, exploring the key subsystems that form the foundation of modern computing. It examines the Central Processing Unit (CPU), its purpose, and its intricate operation. The report also discusses the role of operating systems, their types, and the key features associated with their architecture. Furthermore, it explores the relationship between hardware and network addresses, including MAC and IP addresses, and their significance in networking devices. Finally, the report provides insights into essential computer maintenance activities, such as disk defragmentation, browser history clearing, and antivirus updates, to ensure optimal system performance and security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

COMPUTER SYSTEM
ARCHITECTURE
ARCHITECTURE
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
Introduction......................................................................................................................................1
Lo1................................................................................................................................................... 2
P1 identify the main subsystems of a computer and explain how they are organized and
connected..................................................................................................................................... 2
P2 Explain the purpose of the Central Processing Unit (CPU) and include details on its
operation...................................................................................................................................... 7
Lo2................................................................................................................................................... 8
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each....................................................................................................................8
P4 Discuss the key features associated with the architecture of an operating system...............11
Lo3................................................................................................................................................. 13
P5 Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components........................................................................13
P6 Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity....................................................................................... 16
Lo4................................................................................................................................................. 17
P7 Use information gathering methods to assess troubleshoot and document solutions to a
number of different technical hardware, software and networking issues................................17
P8 Conduct and document a range of maintenance activities with regards to computer
hardware and software............................................................................................................... 19
Conclusion..................................................................................................................................... 24
References......................................................................................................................................25
Introduction......................................................................................................................................1
Lo1................................................................................................................................................... 2
P1 identify the main subsystems of a computer and explain how they are organized and
connected..................................................................................................................................... 2
P2 Explain the purpose of the Central Processing Unit (CPU) and include details on its
operation...................................................................................................................................... 7
Lo2................................................................................................................................................... 8
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each....................................................................................................................8
P4 Discuss the key features associated with the architecture of an operating system...............11
Lo3................................................................................................................................................. 13
P5 Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components........................................................................13
P6 Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity....................................................................................... 16
Lo4................................................................................................................................................. 17
P7 Use information gathering methods to assess troubleshoot and document solutions to a
number of different technical hardware, software and networking issues................................17
P8 Conduct and document a range of maintenance activities with regards to computer
hardware and software............................................................................................................... 19
Conclusion..................................................................................................................................... 24
References......................................................................................................................................25

LIST OF FIGURES
Figure 1: Subsystems of a computer................................................................................................2
Figure 2: Von Neumann Architecture............................................................................................. 3
Figure 3: Memory hierarchy............................................................................................................ 5
Figure 4: System Bus;......................................................................................................................5
Figure 5: Screen shot of Screenlets of Ubuntu................................................................................9
Figure 6: Screenshot of window 10............................................................................................... 10
Figure 7: Operating Systems Architecture....................................................................................11
Figure 8: MAC address..................................................................................................................14
Figure 9: IP address (command prompt)....................................................................................... 15
Figure 10: Setting Up a Computer network...................................................................................16
Figure 11: File explorer in Start menu...........................................................................................19
Figure 12: Local Disk (C :)............................................................................................................20
Figure 13: Optimizing drive.......................................................................................................... 20
Figure 14: Selection of the drive for optimization.........................................................................21
Figure 15: fragmentation Percentage.............................................................................................21
Figure 16: Defragmentation process..............................................................................................22
Figure 17: Browser’s history clean-up..........................................................................................23
Figure 1: Subsystems of a computer................................................................................................2
Figure 2: Von Neumann Architecture............................................................................................. 3
Figure 3: Memory hierarchy............................................................................................................ 5
Figure 4: System Bus;......................................................................................................................5
Figure 5: Screen shot of Screenlets of Ubuntu................................................................................9
Figure 6: Screenshot of window 10............................................................................................... 10
Figure 7: Operating Systems Architecture....................................................................................11
Figure 8: MAC address..................................................................................................................14
Figure 9: IP address (command prompt)....................................................................................... 15
Figure 10: Setting Up a Computer network...................................................................................16
Figure 11: File explorer in Start menu...........................................................................................19
Figure 12: Local Disk (C :)............................................................................................................20
Figure 13: Optimizing drive.......................................................................................................... 20
Figure 14: Selection of the drive for optimization.........................................................................21
Figure 15: fragmentation Percentage.............................................................................................21
Figure 16: Defragmentation process..............................................................................................22
Figure 17: Browser’s history clean-up..........................................................................................23

Introduction
Computer architecture is the method and rules through which function, organization and
implementation of computer system is explained. This report discusses about computer
subsystems that forms the overall computer system. The report discusses about Central
Processing Unit and Operating System that are the major computer components. Every computer
or networking device has one logical and physical, address, this report discusses about their
relation and comparison. At last, the report discusses regarding the maintenance task that a user
must perform in regular basis for proper maintenance of the overall computer system and its
elements.
1
Computer architecture is the method and rules through which function, organization and
implementation of computer system is explained. This report discusses about computer
subsystems that forms the overall computer system. The report discusses about Central
Processing Unit and Operating System that are the major computer components. Every computer
or networking device has one logical and physical, address, this report discusses about their
relation and comparison. At last, the report discusses regarding the maintenance task that a user
must perform in regular basis for proper maintenance of the overall computer system and its
elements.
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Lo1
P1 identify the main subsystems of a computer and explain how they are organized and
connected
A computer system must effectively function considering it four main parts or subsystem.
Subsystem is referred to a device or unit which is a part of larger system like that of a computer.
In case any part malfunctions it may result in discontinuity of the services or hampering the
functionality of the other devices.
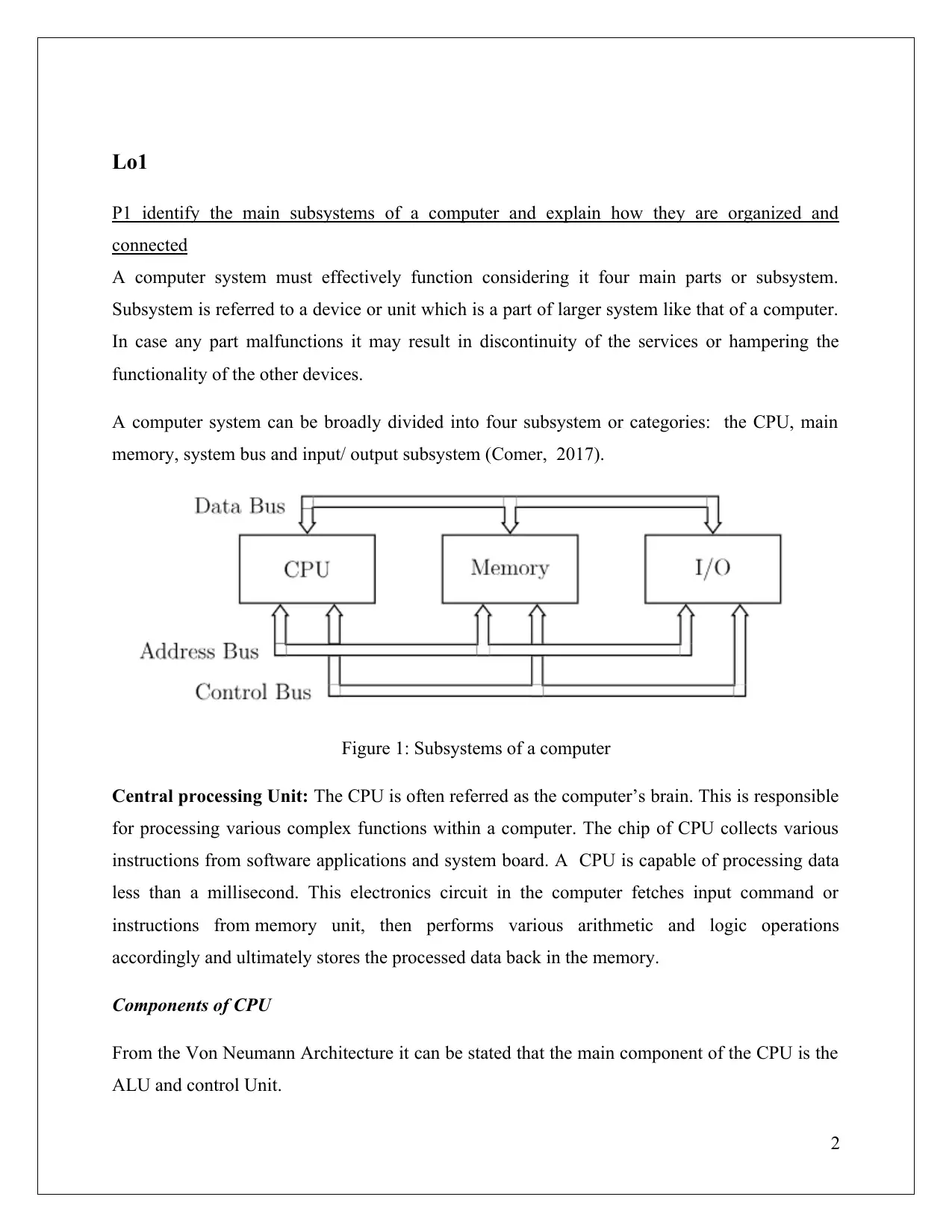
A computer system can be broadly divided into four subsystem or categories: the CPU, main
memory, system bus and input/ output subsystem (Comer, 2017).
Figure 1: Subsystems of a computer
Central processing Unit: The CPU is often referred as the computer’s brain. This is responsible
for processing various complex functions within a computer. The chip of CPU collects various
instructions from software applications and system board. A CPU is capable of processing data
less than a millisecond. This electronics circuit in the computer fetches input command or
instructions from memory unit, then performs various arithmetic and logic operations
accordingly and ultimately stores the processed data back in the memory.
Components of CPU
From the Von Neumann Architecture it can be stated that the main component of the CPU is the
ALU and control Unit.
2
P1 identify the main subsystems of a computer and explain how they are organized and
connected
A computer system must effectively function considering it four main parts or subsystem.
Subsystem is referred to a device or unit which is a part of larger system like that of a computer.
In case any part malfunctions it may result in discontinuity of the services or hampering the
functionality of the other devices.
A computer system can be broadly divided into four subsystem or categories: the CPU, main
memory, system bus and input/ output subsystem (Comer, 2017).
Figure 1: Subsystems of a computer
Central processing Unit: The CPU is often referred as the computer’s brain. This is responsible
for processing various complex functions within a computer. The chip of CPU collects various
instructions from software applications and system board. A CPU is capable of processing data
less than a millisecond. This electronics circuit in the computer fetches input command or
instructions from memory unit, then performs various arithmetic and logic operations
accordingly and ultimately stores the processed data back in the memory.
Components of CPU
From the Von Neumann Architecture it can be stated that the main component of the CPU is the
ALU and control Unit.
2
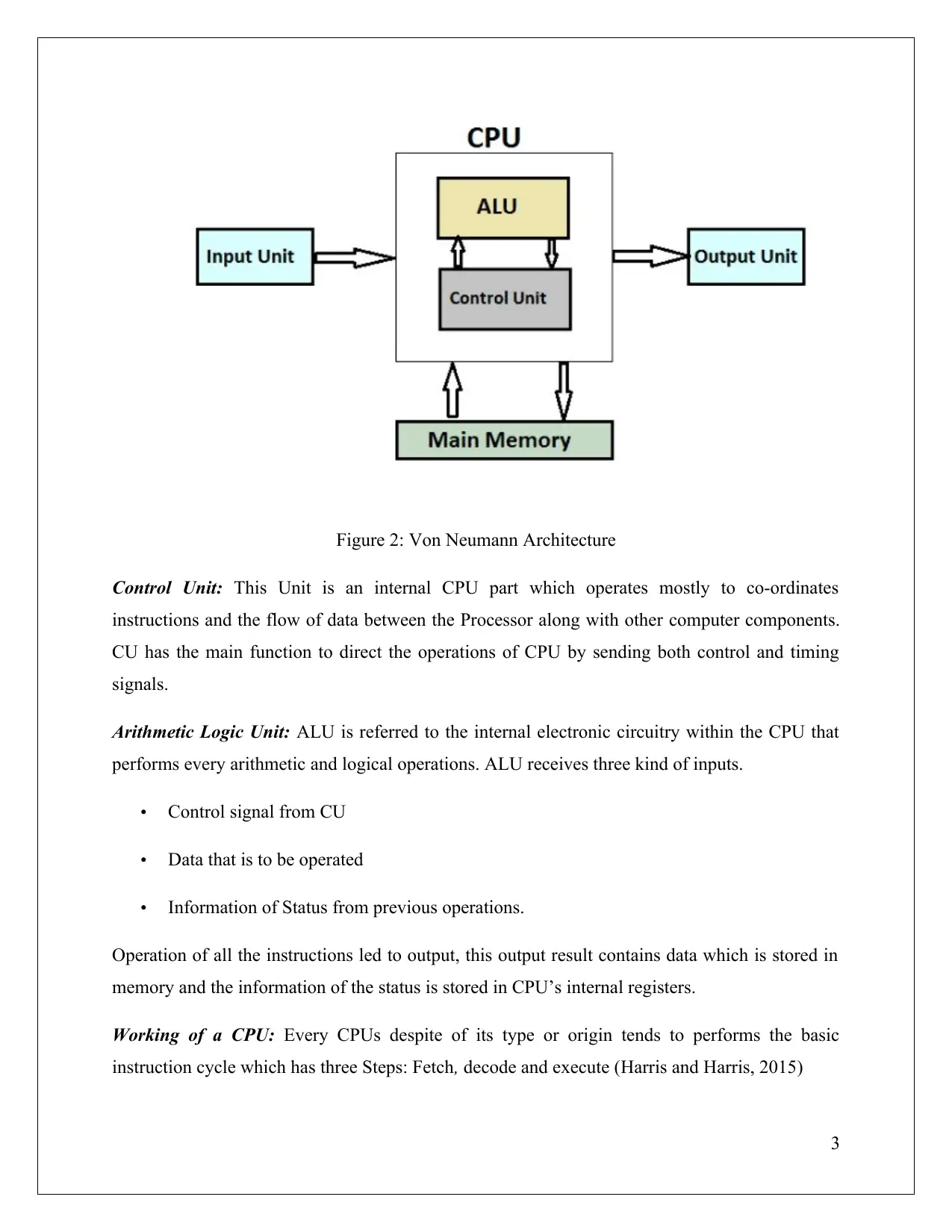
Figure 2: Von Neumann Architecture
Control Unit: This Unit is an internal CPU part which operates mostly to co-ordinates
instructions and the flow of data between the Processor along with other computer components.
CU has the main function to direct the operations of CPU by sending both control and timing
signals.
Arithmetic Logic Unit: ALU is referred to the internal electronic circuitry within the CPU that
performs every arithmetic and logical operations. ALU receives three kind of inputs.
Control signal from CU
Data that is to be operated
Information of Status from previous operations.
Operation of all the instructions led to output, this output result contains data which is stored in
memory and the information of the status is stored in CPU’s internal registers.
Working of a CPU: Every CPUs despite of its type or origin tends to performs the basic
instruction cycle which has three Steps: Fetch, decode and execute (Harris and Harris, 2015)
3
Control Unit: This Unit is an internal CPU part which operates mostly to co-ordinates
instructions and the flow of data between the Processor along with other computer components.
CU has the main function to direct the operations of CPU by sending both control and timing
signals.
Arithmetic Logic Unit: ALU is referred to the internal electronic circuitry within the CPU that
performs every arithmetic and logical operations. ALU receives three kind of inputs.
Control signal from CU
Data that is to be operated
Information of Status from previous operations.
Operation of all the instructions led to output, this output result contains data which is stored in
memory and the information of the status is stored in CPU’s internal registers.
Working of a CPU: Every CPUs despite of its type or origin tends to performs the basic
instruction cycle which has three Steps: Fetch, decode and execute (Harris and Harris, 2015)
3

Fetch: Number of instructions forms a program. And a memory stores various programs. During
fetch, CPU of a system reads that instruction which need to be operated of a specific memory
address. Program counter or PC keeps record of the address of particular instructions.
Decode: Instruction decoder is a circuitry that is responsible for decoding the instructions which
is fetched from memory. The decoded instructions form various signals which control other CPU
areas.
Execute: Lastly, CPU must executes those instruction.
Main Memory: The computer’s main memory includes collection of various storage locations
having unique identifier known as address. Data is transferred from or to memory in Bits groups
called words. Main memory is also referred as RAM or Random access memory. This part of the
computer is meant for storing, software applications, operating system software and information
related to CPU so that it access can be faster while performing a tasks.
Type of main memory
The main memory can be categories as RAM and ROM.
RAM: Random Access Memory is a computer memory that is base on semiconductor. RAM
basically is use for storing data and program code. The CPU can read, write access the data
stored in RAM. This memory is volatile in nature, thus it cannot be recovered in case of
discontinued power supply. The Ram can be further classified as Static Ram and Dynamic RAM.
ROM: Read Only Memory is also a semiconductor based memory that is responsible for storing
program code. This code can only be read not write by the CPU (Organick, 2014. ). Unlike
RAM, ROM is non-volatile thus even in case of power cut the data or program does not lose.
ROM can be classified as PROM or Programmable read-only memory, EPROM or Erasable
programmable read-only memory and EEPROM or Electrically erasable programmable read-
only memory.
Memory hierarchy
A Computer uses various types of memory, a user need memory which is fast as well s
inexpensive. Thus memory hierarchy is created.
4
fetch, CPU of a system reads that instruction which need to be operated of a specific memory
address. Program counter or PC keeps record of the address of particular instructions.
Decode: Instruction decoder is a circuitry that is responsible for decoding the instructions which
is fetched from memory. The decoded instructions form various signals which control other CPU
areas.
Execute: Lastly, CPU must executes those instruction.
Main Memory: The computer’s main memory includes collection of various storage locations
having unique identifier known as address. Data is transferred from or to memory in Bits groups
called words. Main memory is also referred as RAM or Random access memory. This part of the
computer is meant for storing, software applications, operating system software and information
related to CPU so that it access can be faster while performing a tasks.
Type of main memory
The main memory can be categories as RAM and ROM.
RAM: Random Access Memory is a computer memory that is base on semiconductor. RAM
basically is use for storing data and program code. The CPU can read, write access the data
stored in RAM. This memory is volatile in nature, thus it cannot be recovered in case of
discontinued power supply. The Ram can be further classified as Static Ram and Dynamic RAM.
ROM: Read Only Memory is also a semiconductor based memory that is responsible for storing
program code. This code can only be read not write by the CPU (Organick, 2014. ). Unlike
RAM, ROM is non-volatile thus even in case of power cut the data or program does not lose.
ROM can be classified as PROM or Programmable read-only memory, EPROM or Erasable
programmable read-only memory and EEPROM or Electrically erasable programmable read-
only memory.
Memory hierarchy
A Computer uses various types of memory, a user need memory which is fast as well s
inexpensive. Thus memory hierarchy is created.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
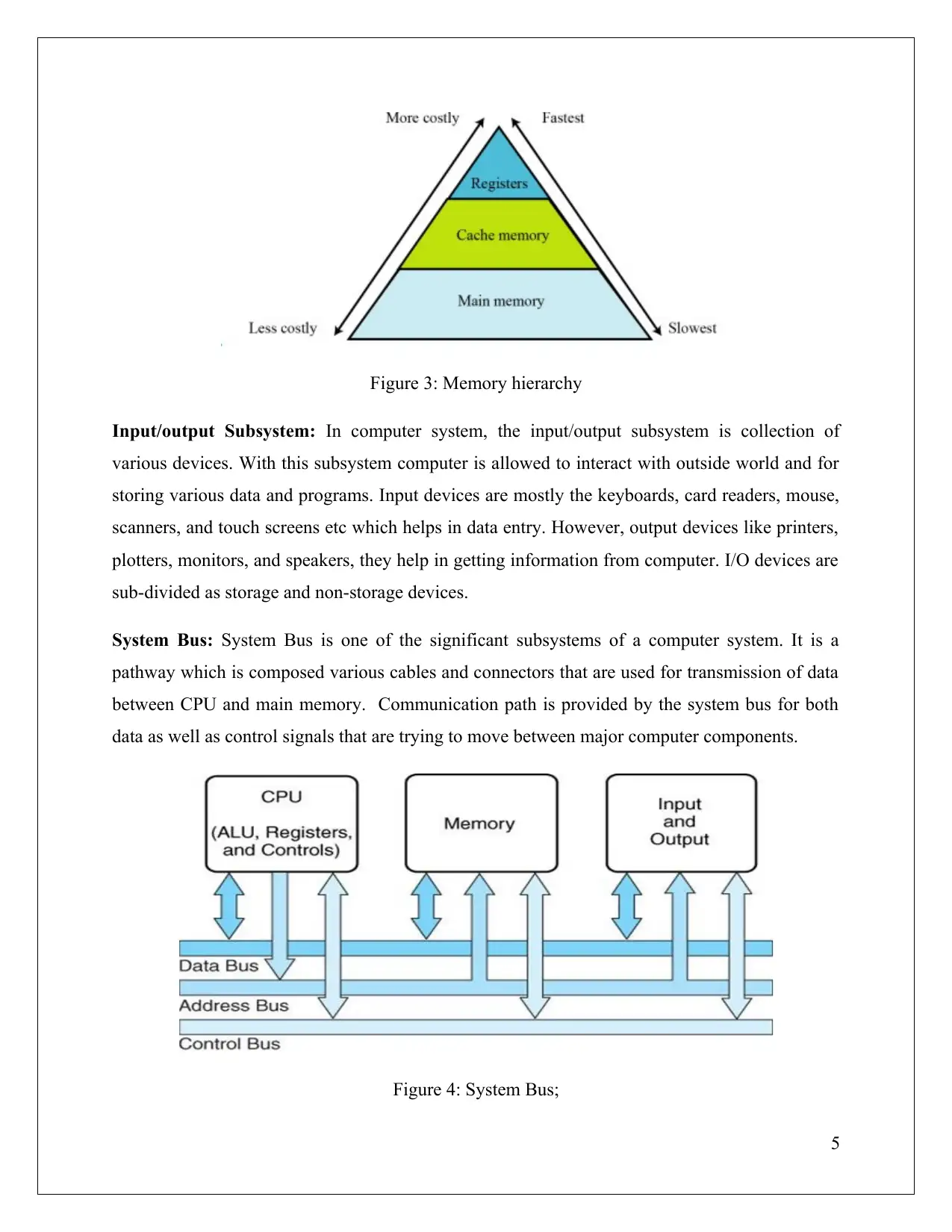
Figure 3: Memory hierarchy
Input/output Subsystem: In computer system, the input/output subsystem is collection of
various devices. With this subsystem computer is allowed to interact with outside world and for
storing various data and programs. Input devices are mostly the keyboards, card readers, mouse,
scanners, and touch screens etc which helps in data entry. However, output devices like printers,
plotters, monitors, and speakers, they help in getting information from computer. I/O devices are
sub-divided as storage and non-storage devices.
System Bus: System Bus is one of the significant subsystems of a computer system. It is a
pathway which is composed various cables and connectors that are used for transmission of data
between CPU and main memory. Communication path is provided by the system bus for both
data as well as control signals that are trying to move between major computer components.
Figure 4: System Bus;
5
Input/output Subsystem: In computer system, the input/output subsystem is collection of
various devices. With this subsystem computer is allowed to interact with outside world and for
storing various data and programs. Input devices are mostly the keyboards, card readers, mouse,
scanners, and touch screens etc which helps in data entry. However, output devices like printers,
plotters, monitors, and speakers, they help in getting information from computer. I/O devices are
sub-divided as storage and non-storage devices.
System Bus: System Bus is one of the significant subsystems of a computer system. It is a
pathway which is composed various cables and connectors that are used for transmission of data
between CPU and main memory. Communication path is provided by the system bus for both
data as well as control signals that are trying to move between major computer components.
Figure 4: System Bus;
5

Types of system bus and their function:
Control bus: This bus is meant for carrying signal of control, coordination and timing for
managing e different functions within the system.
Address bus: The main function of this bus is to specify the memory locations for data
transferred.
Data bus: This is a bidirectional path that carries data between processor, memory and
peripherals.
The dimension and design of system bus is on the basis of processor technology on which a
motherboard is designed.
6
Control bus: This bus is meant for carrying signal of control, coordination and timing for
managing e different functions within the system.
Address bus: The main function of this bus is to specify the memory locations for data
transferred.
Data bus: This is a bidirectional path that carries data between processor, memory and
peripherals.
The dimension and design of system bus is on the basis of processor technology on which a
motherboard is designed.
6

P2 Explain the purpose of the Central Processing Unit (CPU) and include details on its operation
The CPU or the Central Processing Unit is central component of a computer system. This
component is responsible for every single operation and function done by a computer or
computing devices. A CPU handles every instruction received by it from either
hardware or software. Purpose of the CPU installation in a computer system is that it acts as a
brain that performs different program instructions. Processor is mainly designed for carrying out
meticulous instruction set.
How CPU works?
CPU is located on the computer’s motherboard. Programs and Hardware components installed in
the computer need to transmit data via CPU before carrying out any functions. Whenever a
program, function, or a data is called, the CPU has the responsibility to pulls that from RAM and
supply it to relevant hardware for its processing. Instructions are read by the CPU related to any
task before transferring to RAM again. CPU receives instruction related to data transmission and
calculations. System bus trails the flow of data. CPU ensures guidance of data using the system
bus. CPU is responsible for making sure that correct order is followed for data transmission.
Operation of CPU
Fundamental operation CPU is execution of stored instructions in proper sequence. Instructions
which need to be executed are stored in the memory of the computer system. CPU operation
includes fetch, decode and execute stage, this are cooperatively called as instruction cycle.Once
the instruction is executed, the complete processes replicate itself, for the next instruction
through instruction cycle (White et al, 2017). Generally fetching is the next instruction in the
sequence due to PC’s or program counter incremented value. In case of execution of a jump
instruction, the PC modifies to hold the instruction address which was hoped to and execution of
the program continues. In complex CPUs, numerous instructions get concurrently fetched,
decoded or executed.
7
The CPU or the Central Processing Unit is central component of a computer system. This
component is responsible for every single operation and function done by a computer or
computing devices. A CPU handles every instruction received by it from either
hardware or software. Purpose of the CPU installation in a computer system is that it acts as a
brain that performs different program instructions. Processor is mainly designed for carrying out
meticulous instruction set.
How CPU works?
CPU is located on the computer’s motherboard. Programs and Hardware components installed in
the computer need to transmit data via CPU before carrying out any functions. Whenever a
program, function, or a data is called, the CPU has the responsibility to pulls that from RAM and
supply it to relevant hardware for its processing. Instructions are read by the CPU related to any
task before transferring to RAM again. CPU receives instruction related to data transmission and
calculations. System bus trails the flow of data. CPU ensures guidance of data using the system
bus. CPU is responsible for making sure that correct order is followed for data transmission.
Operation of CPU
Fundamental operation CPU is execution of stored instructions in proper sequence. Instructions
which need to be executed are stored in the memory of the computer system. CPU operation
includes fetch, decode and execute stage, this are cooperatively called as instruction cycle.Once
the instruction is executed, the complete processes replicate itself, for the next instruction
through instruction cycle (White et al, 2017). Generally fetching is the next instruction in the
sequence due to PC’s or program counter incremented value. In case of execution of a jump
instruction, the PC modifies to hold the instruction address which was hoped to and execution of
the program continues. In complex CPUs, numerous instructions get concurrently fetched,
decoded or executed.
7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Lo2
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each
Operating system
OS or operating system is referred to software present in computer’s hard drive. OS facilitate
communication of the computer hardware and work along with software. Without an operating
system, both computer and the software programs are worthless. OS perform different task
associated with computer system such as, controlling peripheral devices, memory management,
handling the input and output devices and also file management (Anderson and Roscoe, 2016).
Operating system types
Common desktop operating systems are OS X, Windows and Linux. However, all the OS are
different from each other but they offer graphical user interface, and folders/files of the computer
are managed. OS supports program installation and running which is written exclusively for OS.
Windows and Linux is installed in standard hardware of a computer, OS X is designed to run
exclusively for Apple’s system
Ubuntu: Ubuntu is open source and free kind of operating system. It has three variations:
Ubuntu Desktop that is compatibles for personal computers, Ubuntu Server is
for servers and for Internet of things devices Ubuntu Core. This OS is produced by Canonical and
Canonical offers guaranteed and free security updates.
Features: Default Ubuntu installation contain a very wide range of software
including Thunderbird, Firefox, and LibreOffice and along with lightweight games. Additional
packages of software are effectively accessible to the Ubuntu Software and even
with management tool that are APT-based. Ubuntu operate under GPL or GNU and application
software that are installed is by default free software. Ubuntu installs hardware drivers which are
only in binary format.
Use of Ubuntu: it is popular due to its being User-friendly, free, no-antivirus required, high
customization can be achieved, low system requirement, and open source.
8
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each
Operating system
OS or operating system is referred to software present in computer’s hard drive. OS facilitate
communication of the computer hardware and work along with software. Without an operating
system, both computer and the software programs are worthless. OS perform different task
associated with computer system such as, controlling peripheral devices, memory management,
handling the input and output devices and also file management (Anderson and Roscoe, 2016).
Operating system types
Common desktop operating systems are OS X, Windows and Linux. However, all the OS are
different from each other but they offer graphical user interface, and folders/files of the computer
are managed. OS supports program installation and running which is written exclusively for OS.
Windows and Linux is installed in standard hardware of a computer, OS X is designed to run
exclusively for Apple’s system
Ubuntu: Ubuntu is open source and free kind of operating system. It has three variations:
Ubuntu Desktop that is compatibles for personal computers, Ubuntu Server is
for servers and for Internet of things devices Ubuntu Core. This OS is produced by Canonical and
Canonical offers guaranteed and free security updates.
Features: Default Ubuntu installation contain a very wide range of software
including Thunderbird, Firefox, and LibreOffice and along with lightweight games. Additional
packages of software are effectively accessible to the Ubuntu Software and even
with management tool that are APT-based. Ubuntu operate under GPL or GNU and application
software that are installed is by default free software. Ubuntu installs hardware drivers which are
only in binary format.
Use of Ubuntu: it is popular due to its being User-friendly, free, no-antivirus required, high
customization can be achieved, low system requirement, and open source.
8
System requirement: 2 GHz dual core processor, 2 GB RAM, 25 GB of hard-drive space,
1024x768 VGA screen resolution, Internet access.
Figure 5: Screen shot of Screenlets of Ubuntu
Windows 10: It is the version of operating system that is released and developed by Microsoft.
Microsoft is responsible altering and modifying program code. It is considered as one of the most
commonly used OS. This OS harmonizes the experience of a user and functionality among
different device.
9
1024x768 VGA screen resolution, Internet access.
Figure 5: Screen shot of Screenlets of Ubuntu
Windows 10: It is the version of operating system that is released and developed by Microsoft.
Microsoft is responsible altering and modifying program code. It is considered as one of the most
commonly used OS. This OS harmonizes the experience of a user and functionality among
different device.
9
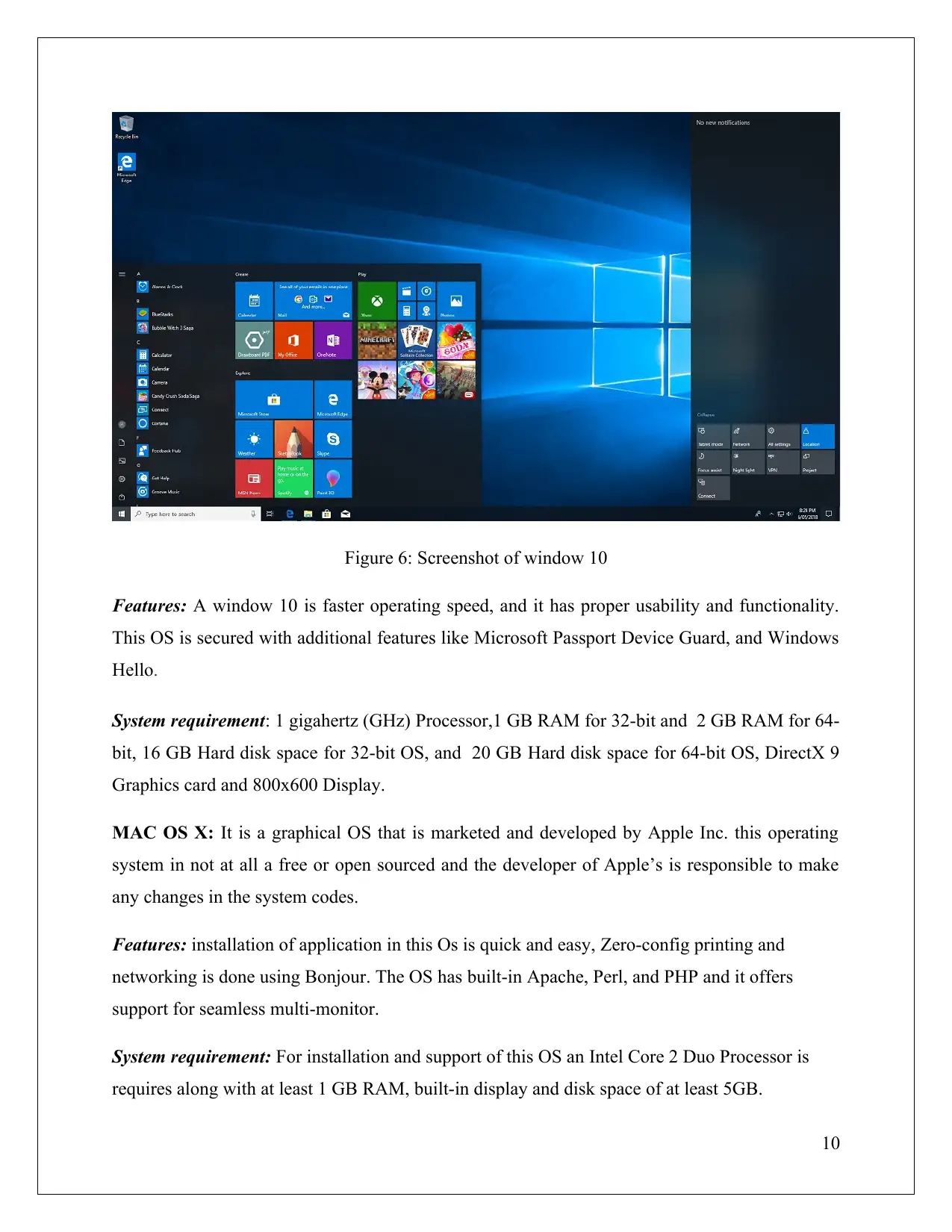
Figure 6: Screenshot of window 10
Features: A window 10 is faster operating speed, and it has proper usability and functionality.
This OS is secured with additional features like Microsoft Passport Device Guard, and Windows
Hello.
System requirement: 1 gigahertz (GHz) Processor,1 GB RAM for 32-bit and 2 GB RAM for 64-
bit, 16 GB Hard disk space for 32-bit OS, and 20 GB Hard disk space for 64-bit OS, DirectX 9
Graphics card and 800x600 Display.
MAC OS X: It is a graphical OS that is marketed and developed by Apple Inc. this operating
system in not at all a free or open sourced and the developer of Apple’s is responsible to make
any changes in the system codes.
Features: installation of application in this Os is quick and easy, Zero-config printing and
networking is done using Bonjour. The OS has built-in Apache, Perl, and PHP and it offers
support for seamless multi-monitor.
System requirement: For installation and support of this OS an Intel Core 2 Duo Processor is
requires along with at least 1 GB RAM, built-in display and disk space of at least 5GB.
10
Features: A window 10 is faster operating speed, and it has proper usability and functionality.
This OS is secured with additional features like Microsoft Passport Device Guard, and Windows
Hello.
System requirement: 1 gigahertz (GHz) Processor,1 GB RAM for 32-bit and 2 GB RAM for 64-
bit, 16 GB Hard disk space for 32-bit OS, and 20 GB Hard disk space for 64-bit OS, DirectX 9
Graphics card and 800x600 Display.
MAC OS X: It is a graphical OS that is marketed and developed by Apple Inc. this operating
system in not at all a free or open sourced and the developer of Apple’s is responsible to make
any changes in the system codes.
Features: installation of application in this Os is quick and easy, Zero-config printing and
networking is done using Bonjour. The OS has built-in Apache, Perl, and PHP and it offers
support for seamless multi-monitor.
System requirement: For installation and support of this OS an Intel Core 2 Duo Processor is
requires along with at least 1 GB RAM, built-in display and disk space of at least 5GB.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
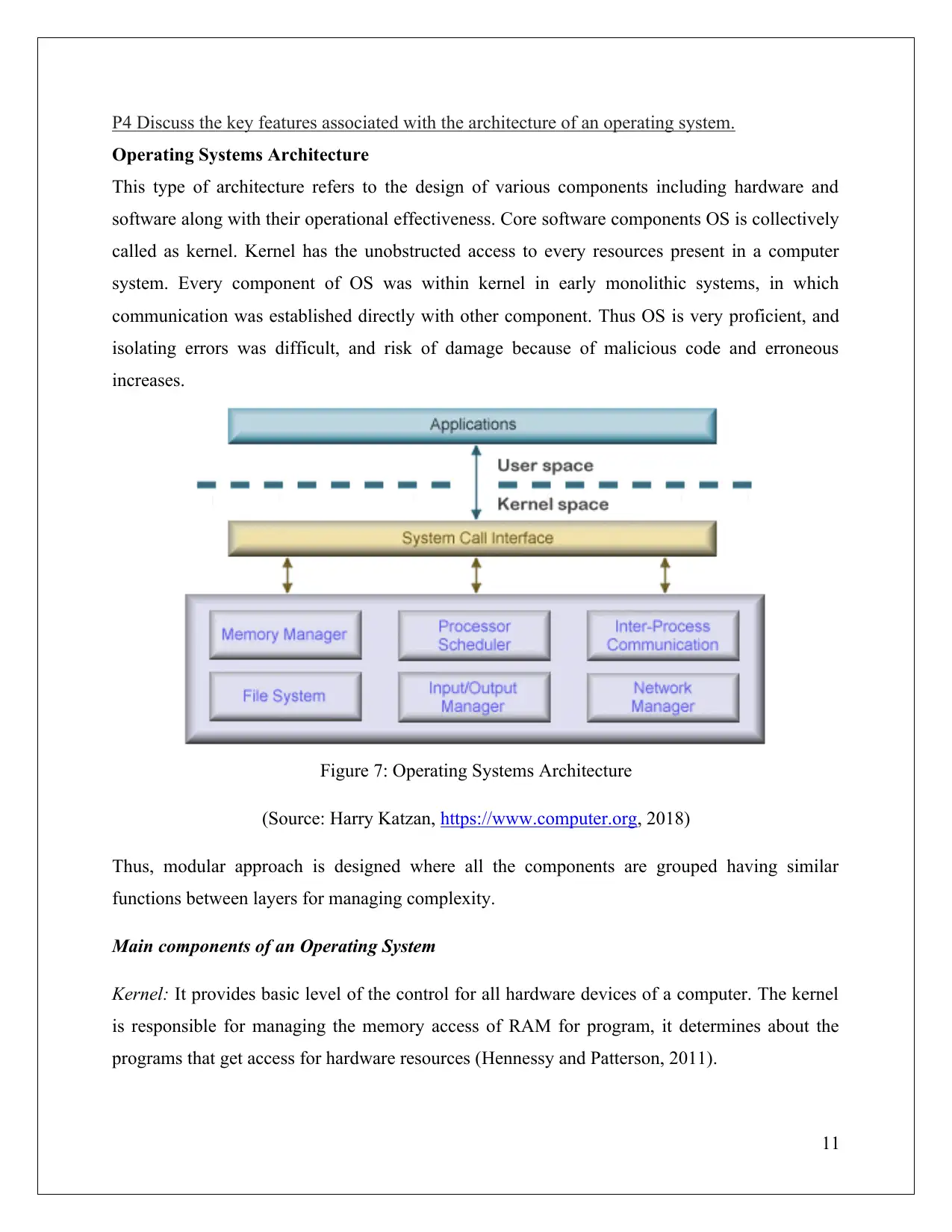
P4 Discuss the key features associated with the architecture of an operating system.
Operating Systems Architecture
This type of architecture refers to the design of various components including hardware and
software along with their operational effectiveness. Core software components OS is collectively
called as kernel. Kernel has the unobstructed access to every resources present in a computer
system. Every component of OS was within kernel in early monolithic systems, in which
communication was established directly with other component. Thus OS is very proficient, and
isolating errors was difficult, and risk of damage because of malicious code and erroneous
increases.
Figure 7: Operating Systems Architecture
(Source: Harry Katzan, https://www.computer.org, 2018)
Thus, modular approach is designed where all the components are grouped having similar
functions between layers for managing complexity.
Main components of an Operating System
Kernel: It provides basic level of the control for all hardware devices of a computer. The kernel
is responsible for managing the memory access of RAM for program, it determines about the
programs that get access for hardware resources (Hennessy and Patterson, 2011).
11
Operating Systems Architecture
This type of architecture refers to the design of various components including hardware and
software along with their operational effectiveness. Core software components OS is collectively
called as kernel. Kernel has the unobstructed access to every resources present in a computer
system. Every component of OS was within kernel in early monolithic systems, in which
communication was established directly with other component. Thus OS is very proficient, and
isolating errors was difficult, and risk of damage because of malicious code and erroneous
increases.
Figure 7: Operating Systems Architecture
(Source: Harry Katzan, https://www.computer.org, 2018)
Thus, modular approach is designed where all the components are grouped having similar
functions between layers for managing complexity.
Main components of an Operating System
Kernel: It provides basic level of the control for all hardware devices of a computer. The kernel
is responsible for managing the memory access of RAM for program, it determines about the
programs that get access for hardware resources (Hennessy and Patterson, 2011).
11

Program execution: Operating system offer interface between hardware and application program
of a computer, this supports application program to establish interaction with hardware devices.
Interrupts: They are the center of OS, through interrupts the operating system can effectively
interact and give reaction accordingly to environment. Interrupts in a computer offers the
methods of automatic saving of context of local register, and running of precise code for
responding to events.
File System: Here the control regarding the data is stored or retrieved in a computer. Deprived of
the file system in a computer the information storage will have large data body and will have no
appropriate method for creating information locations.
12
of a computer, this supports application program to establish interaction with hardware devices.
Interrupts: They are the center of OS, through interrupts the operating system can effectively
interact and give reaction accordingly to environment. Interrupts in a computer offers the
methods of automatic saving of context of local register, and running of precise code for
responding to events.
File System: Here the control regarding the data is stored or retrieved in a computer. Deprived of
the file system in a computer the information storage will have large data body and will have no
appropriate method for creating information locations.
12

Lo3
P5 Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components
Devices in the network have two types of addresses one is physical and the other is logical. The
IP address is considered as the logical address whereas the MAC is considered as physical
address of the networking device.
Mac Address: Mac addressing of a device is used for its unique hardware interface. In LAN
network, MAC address is not repeated for any devices. The manufacture provides the MAC
address for a system or device. While manufacturing a device, the manufacture assigns and burns
MAC address on the ROM of every NIC card.
The Mac address is a 12 digit hexadecimal address that means that the address is of 48-bit in
hexadecimal. For Mac address, MM:MM:MM:SS: SS: SS format is used. Here, MM:MM:MM is
the 3-byte manufacturer address, while the SS: SS: SS represent the NIC’s serial number present
in network. If the network replaces the NIC card for any computer, then the MAC address
automatically get changed (Husain, et al 2017). The MAC address of device is mostly applied for
OSI/TCP/IP model in its data link layer. MAC address can be achieved by ARP implementation
in the network.
For windows:
Steps to be followed for MAC address:
Start-Program-Accessories-Command prompt
Type ipconfig/all
13
P5 Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components
Devices in the network have two types of addresses one is physical and the other is logical. The
IP address is considered as the logical address whereas the MAC is considered as physical
address of the networking device.
Mac Address: Mac addressing of a device is used for its unique hardware interface. In LAN
network, MAC address is not repeated for any devices. The manufacture provides the MAC
address for a system or device. While manufacturing a device, the manufacture assigns and burns
MAC address on the ROM of every NIC card.
The Mac address is a 12 digit hexadecimal address that means that the address is of 48-bit in
hexadecimal. For Mac address, MM:MM:MM:SS: SS: SS format is used. Here, MM:MM:MM is
the 3-byte manufacturer address, while the SS: SS: SS represent the NIC’s serial number present
in network. If the network replaces the NIC card for any computer, then the MAC address
automatically get changed (Husain, et al 2017). The MAC address of device is mostly applied for
OSI/TCP/IP model in its data link layer. MAC address can be achieved by ARP implementation
in the network.
For windows:
Steps to be followed for MAC address:
Start-Program-Accessories-Command prompt
Type ipconfig/all
13
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
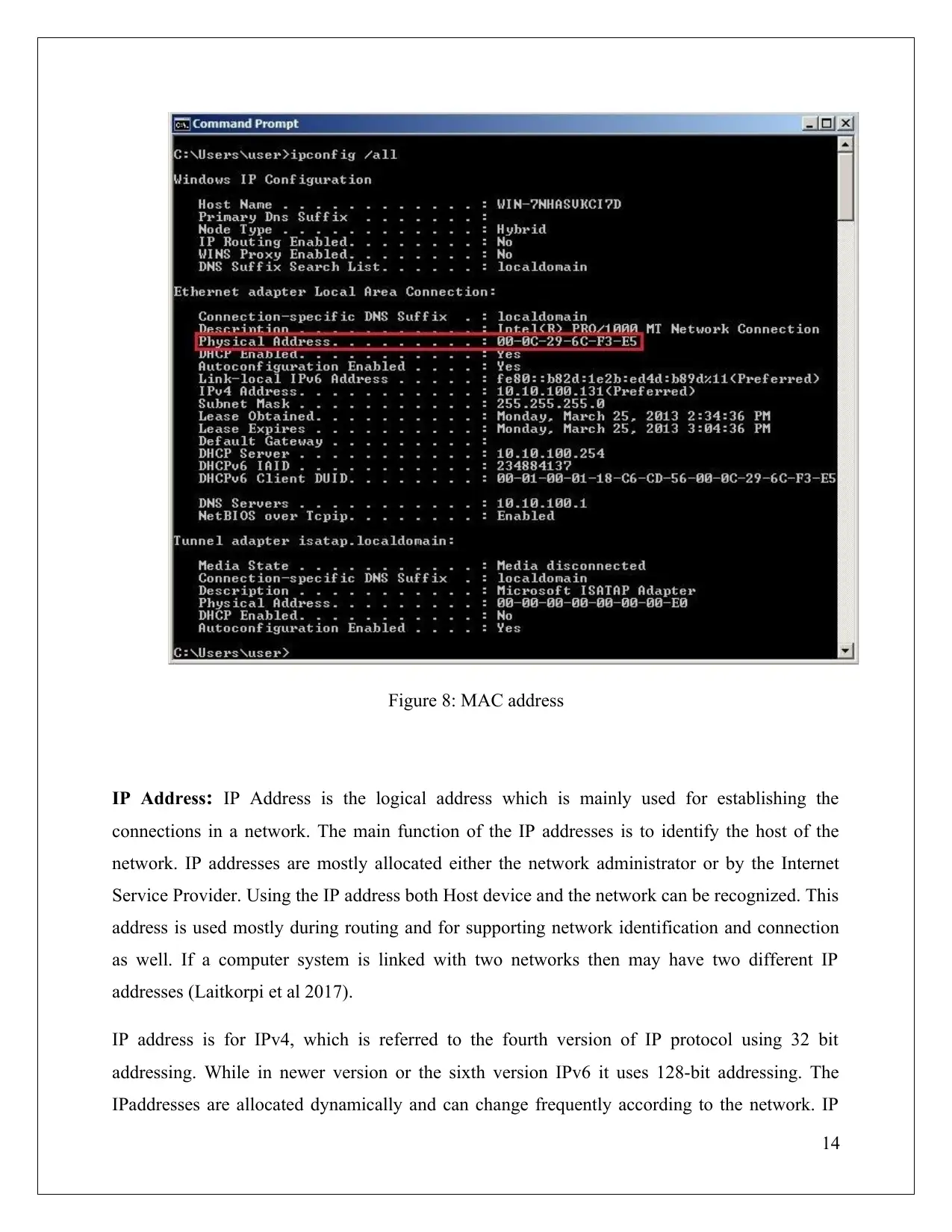
Figure 8: MAC address
IP Address: IP Address is the logical address which is mainly used for establishing the
connections in a network. The main function of the IP addresses is to identify the host of the
network. IP addresses are mostly allocated either the network administrator or by the Internet
Service Provider. Using the IP address both Host device and the network can be recognized. This
address is used mostly during routing and for supporting network identification and connection
as well. If a computer system is linked with two networks then may have two different IP
addresses (Laitkorpi et al 2017).
IP address is for IPv4, which is referred to the fourth version of IP protocol using 32 bit
addressing. While in newer version or the sixth version IPv6 it uses 128-bit addressing. The
IPaddresses are allocated dynamically and can change frequently according to the network. IP
14
IP Address: IP Address is the logical address which is mainly used for establishing the
connections in a network. The main function of the IP addresses is to identify the host of the
network. IP addresses are mostly allocated either the network administrator or by the Internet
Service Provider. Using the IP address both Host device and the network can be recognized. This
address is used mostly during routing and for supporting network identification and connection
as well. If a computer system is linked with two networks then may have two different IP
addresses (Laitkorpi et al 2017).
IP address is for IPv4, which is referred to the fourth version of IP protocol using 32 bit
addressing. While in newer version or the sixth version IPv6 it uses 128-bit addressing. The
IPaddresses are allocated dynamically and can change frequently according to the network. IP
14
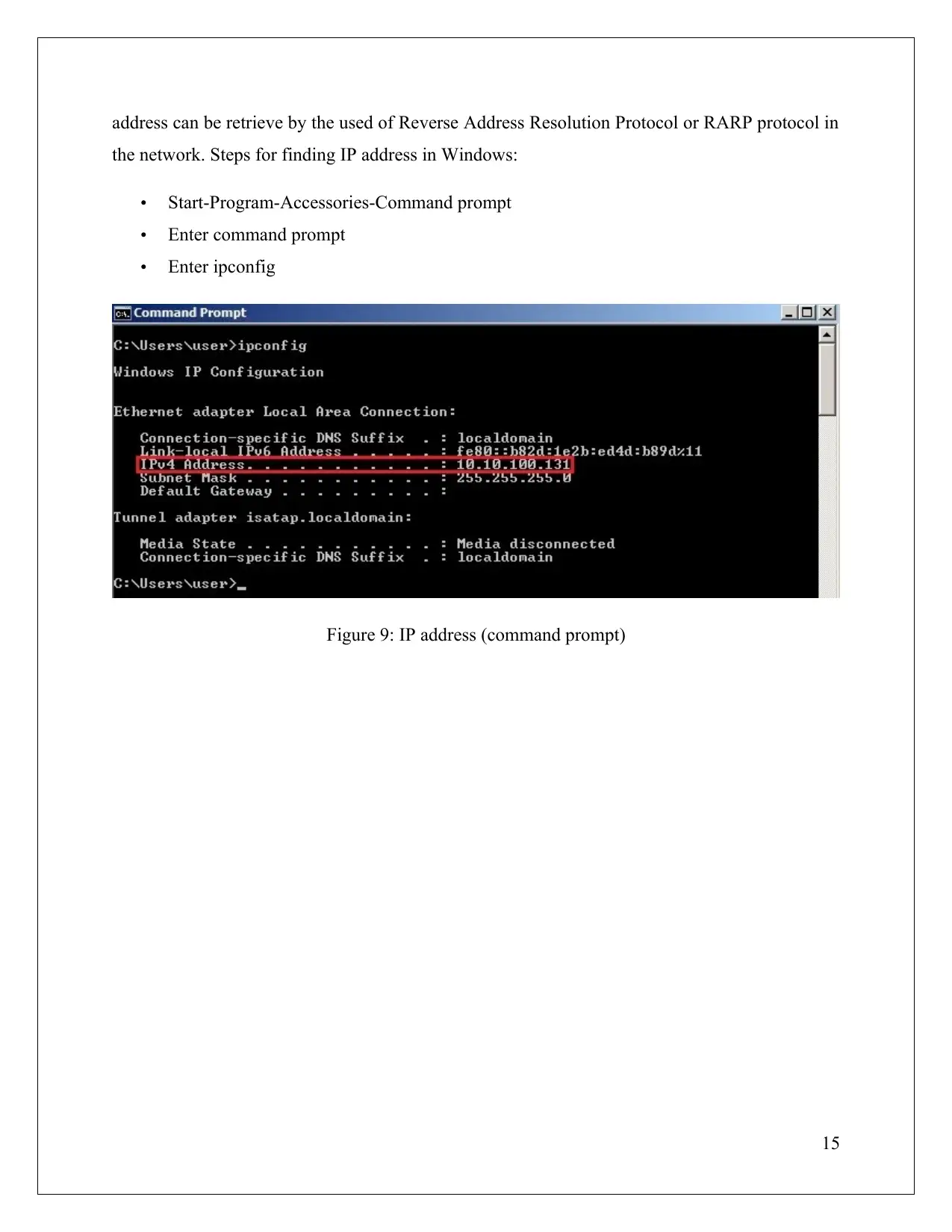
address can be retrieve by the used of Reverse Address Resolution Protocol or RARP protocol in
the network. Steps for finding IP address in Windows:
Start-Program-Accessories-Command prompt
Enter command prompt
Enter ipconfig
Figure 9: IP address (command prompt)
15
the network. Steps for finding IP address in Windows:
Start-Program-Accessories-Command prompt
Enter command prompt
Enter ipconfig
Figure 9: IP address (command prompt)
15
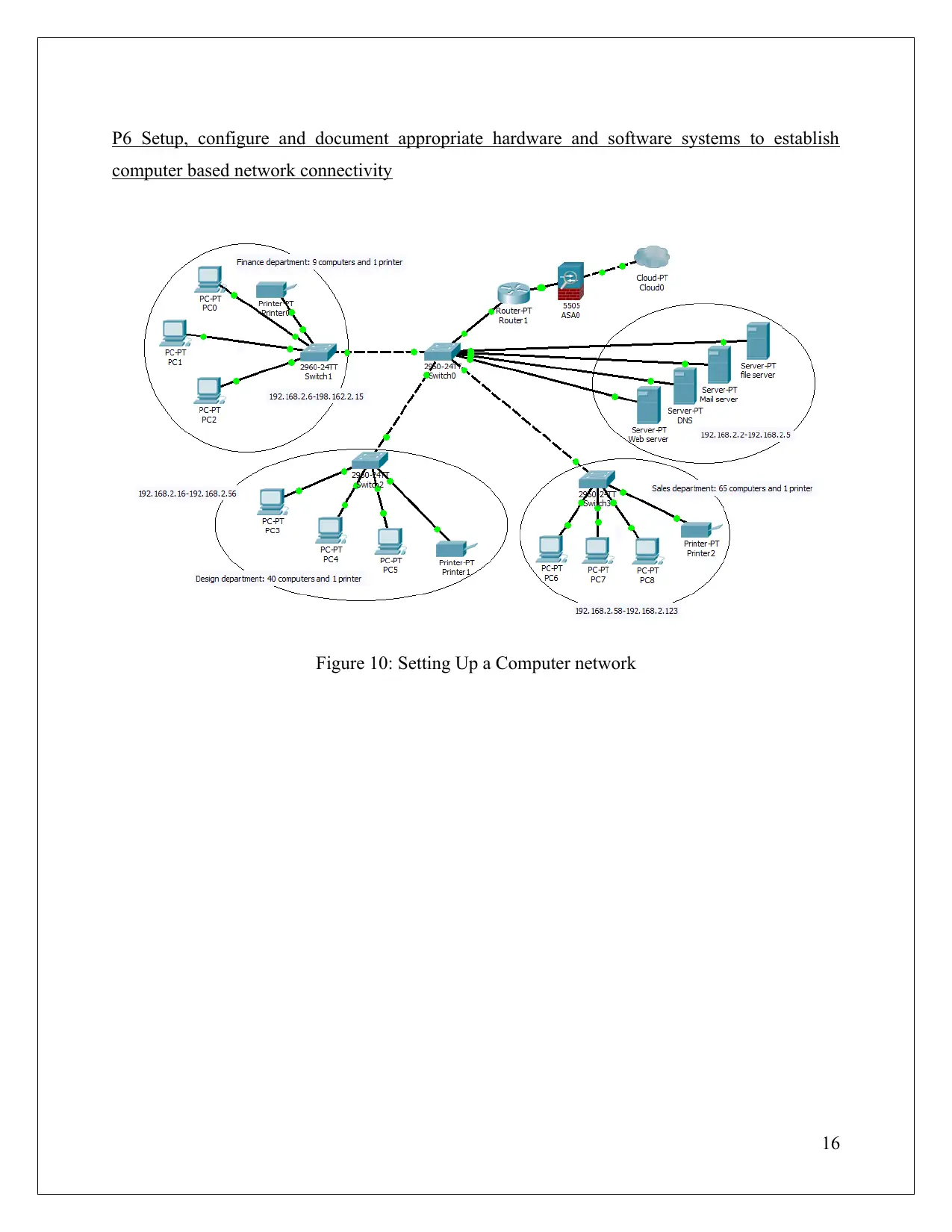
P6 Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity
Figure 10: Setting Up a Computer network
16
computer based network connectivity
Figure 10: Setting Up a Computer network
16
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Lo4
P7 Use information gathering methods to assess troubleshoot and document solutions to a
number of different technical hardware, software and networking issues.
The Network Administrator adopt various measures for trouble shooting by understanding the
answers received from the created questionnaire.
1. Are you facing issues related to hardware or software while using the computer system?
Yes
No
2. Name the common computer issue you are facing frequently?
Software
Hardware
Networking
All of the above
None of the above
3. Are you satisfied with the network connectivity offered in the organization?
Yes
No
4. What is the common hardware issue in the computer system?
Peripherals not working properly
Overheating
Slow computer
Unusual noises
5. What is the common software problem in the computer systems?
Google performing strangely
Attachments won’t open
Computer freezes
Pop-up ads
17
P7 Use information gathering methods to assess troubleshoot and document solutions to a
number of different technical hardware, software and networking issues.
The Network Administrator adopt various measures for trouble shooting by understanding the
answers received from the created questionnaire.
1. Are you facing issues related to hardware or software while using the computer system?
Yes
No
2. Name the common computer issue you are facing frequently?
Software
Hardware
Networking
All of the above
None of the above
3. Are you satisfied with the network connectivity offered in the organization?
Yes
No
4. What is the common hardware issue in the computer system?
Peripherals not working properly
Overheating
Slow computer
Unusual noises
5. What is the common software problem in the computer systems?
Google performing strangely
Attachments won’t open
Computer freezes
Pop-up ads
17

The common Issues the users are facing with the computer system regarding the hardware,
software and networking:
Overheating: Overheating of process or the overall computer system is one of the most
common issues the users are facing. Prolong overheating may shorten the life period of a
along with its performance. Main reason behind this issue is use of cheap cooling element
or incorrect device installation.
User errors: User may cause damages to the computer elements unknowingly or
unconsciously. This issue is due to incorrect driver installation, installation or un-
installation of software of device, file deletion etc.
Virus attack: Viruses are referred to irritation. Attack of virus in a computer system will
lead to its brake down by file damage, corruption and loss connectivity.
Measures taken:
Process of frequent data backup must be introduced, in which important data of the
computer system will be stored in cloud or hard drive.
Installation of the any hardware device must be done by removing the power sources.
Scan for virus and malware in the system using anti-virus software, this software must be
kept updated for protecting data as well as the computer system (Lederer, et al 2017).
The computer system must be placed in a ventilated area and the fan installed inside
should be check and cleansed so that overheating can be minimized.
18
software and networking:
Overheating: Overheating of process or the overall computer system is one of the most
common issues the users are facing. Prolong overheating may shorten the life period of a
along with its performance. Main reason behind this issue is use of cheap cooling element
or incorrect device installation.
User errors: User may cause damages to the computer elements unknowingly or
unconsciously. This issue is due to incorrect driver installation, installation or un-
installation of software of device, file deletion etc.
Virus attack: Viruses are referred to irritation. Attack of virus in a computer system will
lead to its brake down by file damage, corruption and loss connectivity.
Measures taken:
Process of frequent data backup must be introduced, in which important data of the
computer system will be stored in cloud or hard drive.
Installation of the any hardware device must be done by removing the power sources.
Scan for virus and malware in the system using anti-virus software, this software must be
kept updated for protecting data as well as the computer system (Lederer, et al 2017).
The computer system must be placed in a ventilated area and the fan installed inside
should be check and cleansed so that overheating can be minimized.
18
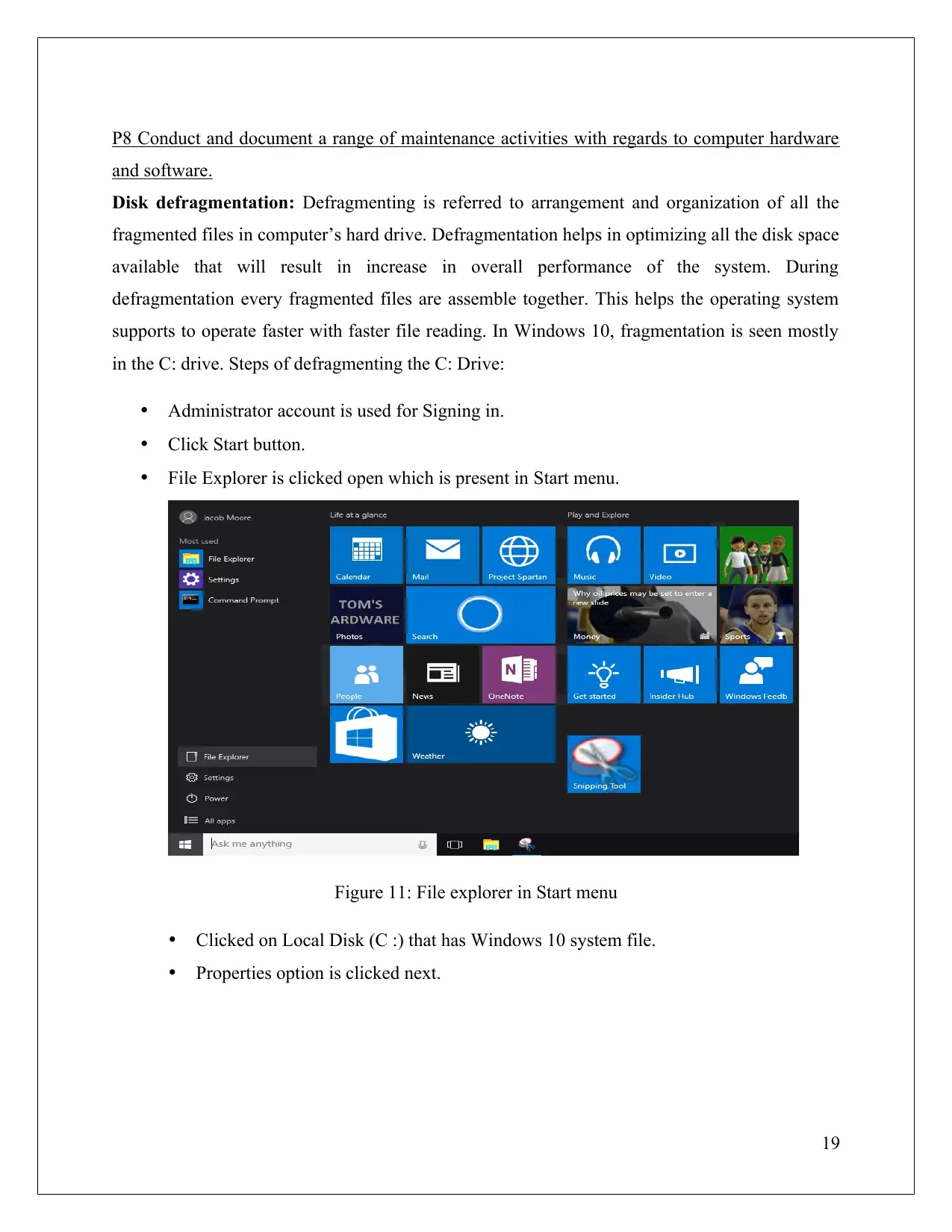
P8 Conduct and document a range of maintenance activities with regards to computer hardware
and software.
Disk defragmentation: Defragmenting is referred to arrangement and organization of all the
fragmented files in computer’s hard drive. Defragmentation helps in optimizing all the disk space
available that will result in increase in overall performance of the system. During
defragmentation every fragmented files are assemble together. This helps the operating system
supports to operate faster with faster file reading. In Windows 10, fragmentation is seen mostly
in the C: drive. Steps of defragmenting the C: Drive:
Administrator account is used for Signing in.
Click Start button.
File Explorer is clicked open which is present in Start menu.
Figure 11: File explorer in Start menu
Clicked on Local Disk (C :) that has Windows 10 system file.
Properties option is clicked next.
19
and software.
Disk defragmentation: Defragmenting is referred to arrangement and organization of all the
fragmented files in computer’s hard drive. Defragmentation helps in optimizing all the disk space
available that will result in increase in overall performance of the system. During
defragmentation every fragmented files are assemble together. This helps the operating system
supports to operate faster with faster file reading. In Windows 10, fragmentation is seen mostly
in the C: drive. Steps of defragmenting the C: Drive:
Administrator account is used for Signing in.
Click Start button.
File Explorer is clicked open which is present in Start menu.
Figure 11: File explorer in Start menu
Clicked on Local Disk (C :) that has Windows 10 system file.
Properties option is clicked next.
19
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
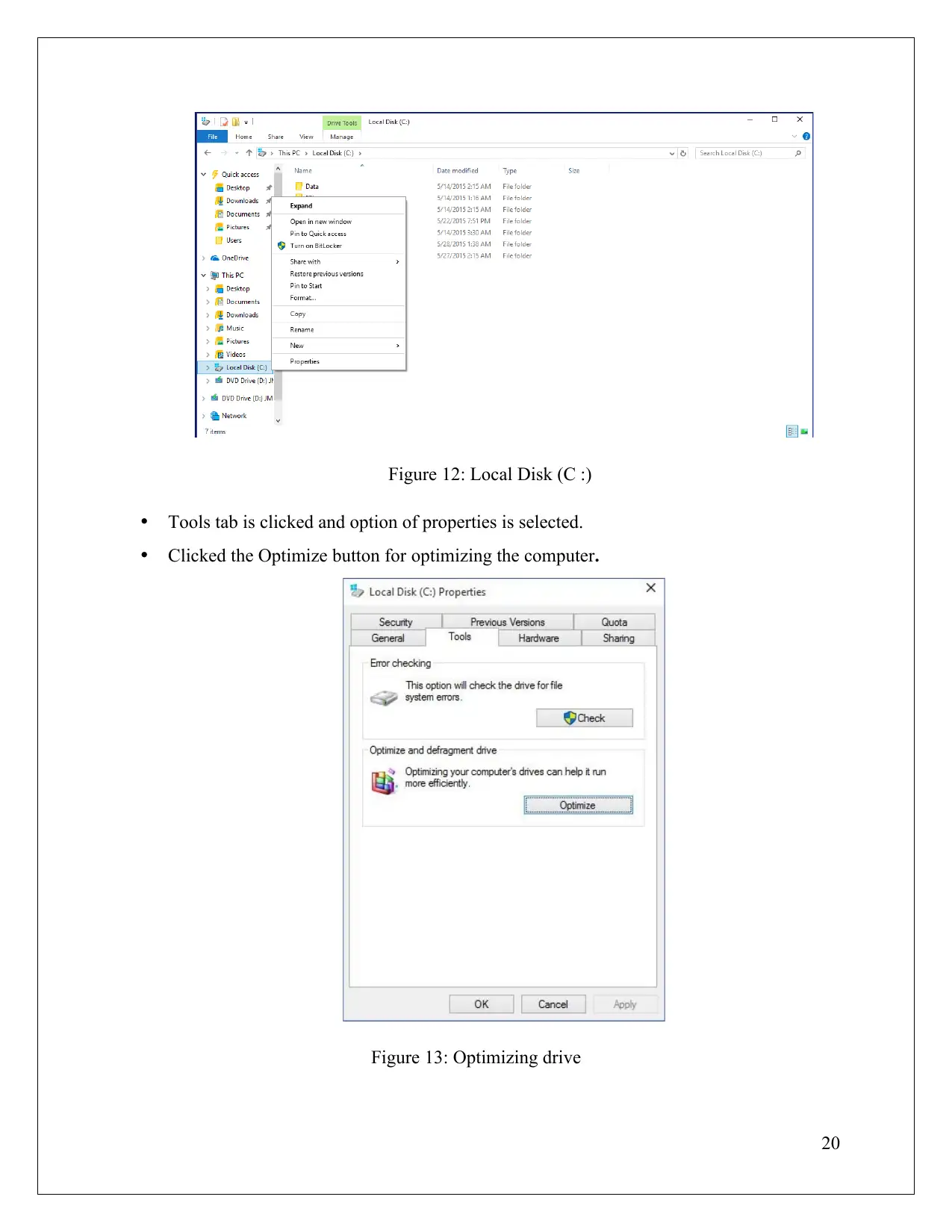
Figure 12: Local Disk (C :)
Tools tab is clicked and option of properties is selected.
Clicked the Optimize button for optimizing the computer.
Figure 13: Optimizing drive
20
Tools tab is clicked and option of properties is selected.
Clicked the Optimize button for optimizing the computer.
Figure 13: Optimizing drive
20
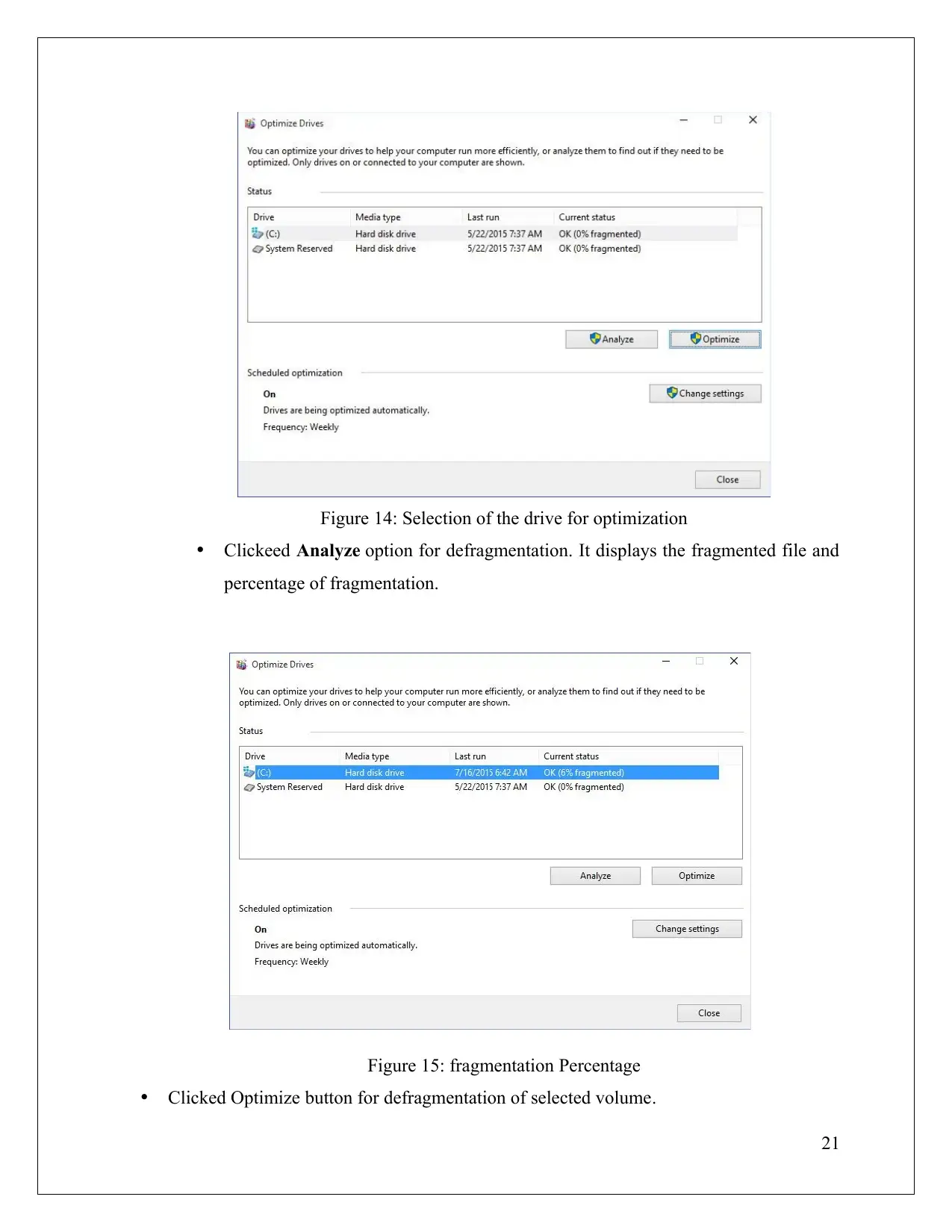
Figure 14: Selection of the drive for optimization
Clickeed Analyze option for defragmentation. It displays the fragmented file and
percentage of fragmentation.
Figure 15: fragmentation Percentage
Clicked Optimize button for defragmentation of selected volume.
21
Clickeed Analyze option for defragmentation. It displays the fragmented file and
percentage of fragmentation.
Figure 15: fragmentation Percentage
Clicked Optimize button for defragmentation of selected volume.
21
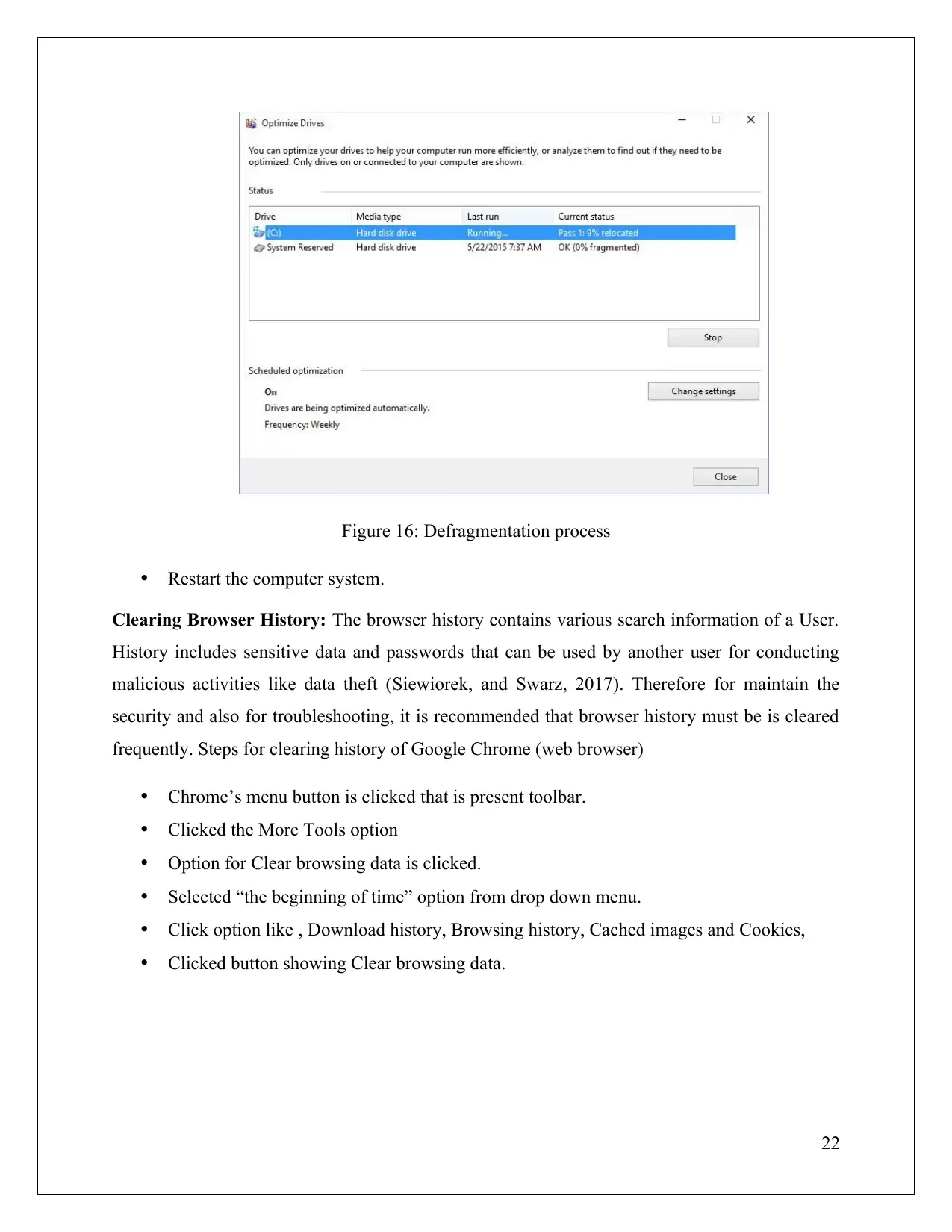
Figure 16: Defragmentation process
Restart the computer system.
Clearing Browser History: The browser history contains various search information of a User.
History includes sensitive data and passwords that can be used by another user for conducting
malicious activities like data theft (Siewiorek, and Swarz, 2017). Therefore for maintain the
security and also for troubleshooting, it is recommended that browser history must be is cleared
frequently. Steps for clearing history of Google Chrome (web browser)
Chrome’s menu button is clicked that is present toolbar.
Clicked the More Tools option
Option for Clear browsing data is clicked.
Selected “the beginning of time” option from drop down menu.
Click option like , Download history, Browsing history, Cached images and Cookies,
Clicked button showing Clear browsing data.
22
Restart the computer system.
Clearing Browser History: The browser history contains various search information of a User.
History includes sensitive data and passwords that can be used by another user for conducting
malicious activities like data theft (Siewiorek, and Swarz, 2017). Therefore for maintain the
security and also for troubleshooting, it is recommended that browser history must be is cleared
frequently. Steps for clearing history of Google Chrome (web browser)
Chrome’s menu button is clicked that is present toolbar.
Clicked the More Tools option
Option for Clear browsing data is clicked.
Selected “the beginning of time” option from drop down menu.
Click option like , Download history, Browsing history, Cached images and Cookies,
Clicked button showing Clear browsing data.
22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
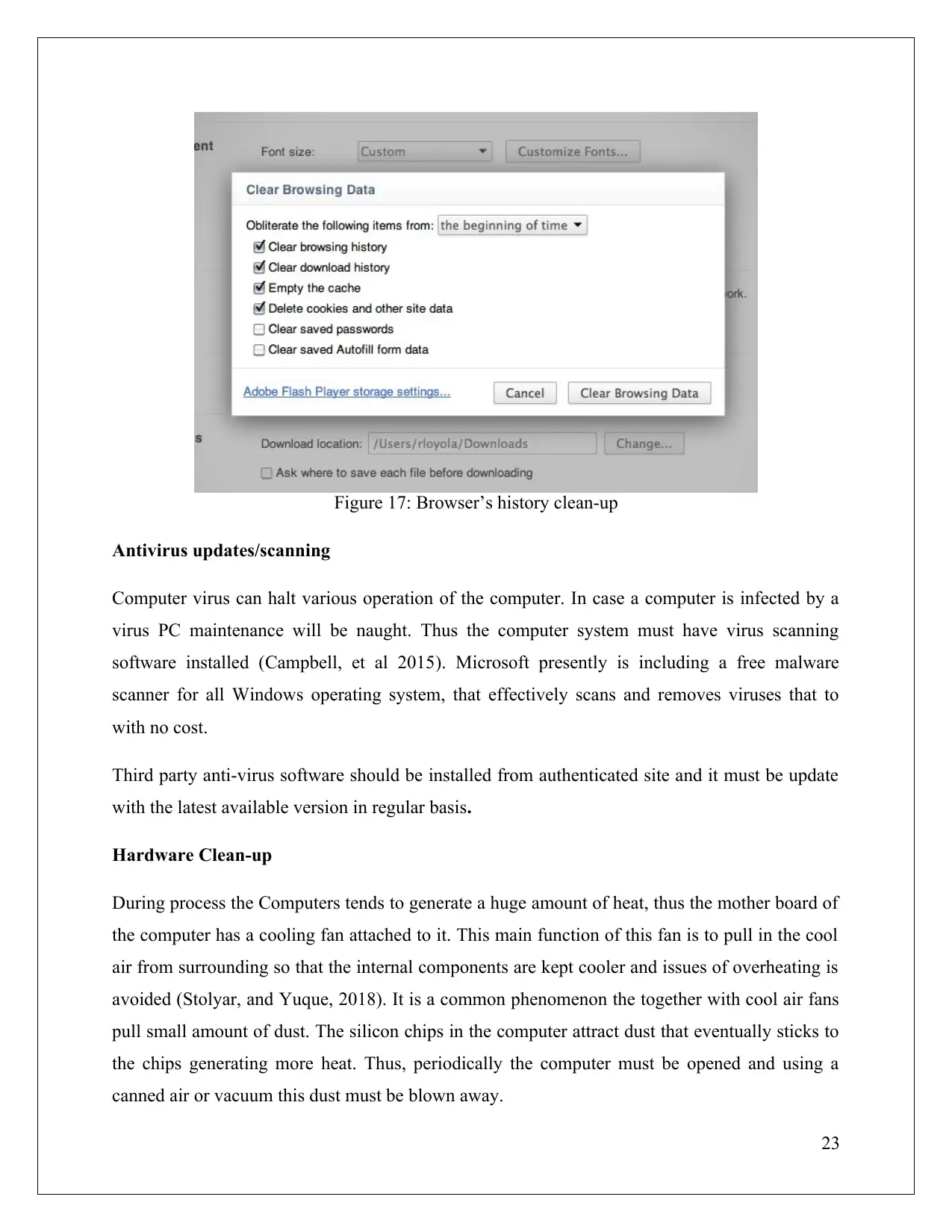
Figure 17: Browser’s history clean-up
Antivirus updates/scanning
Computer virus can halt various operation of the computer. In case a computer is infected by a
virus PC maintenance will be naught. Thus the computer system must have virus scanning
software installed (Campbell, et al 2015). Microsoft presently is including a free malware
scanner for all Windows operating system, that effectively scans and removes viruses that to
with no cost.
Third party anti-virus software should be installed from authenticated site and it must be update
with the latest available version in regular basis.
Hardware Clean-up
During process the Computers tends to generate a huge amount of heat, thus the mother board of
the computer has a cooling fan attached to it. This main function of this fan is to pull in the cool
air from surrounding so that the internal components are kept cooler and issues of overheating is
avoided (Stolyar, and Yuque, 2018). It is a common phenomenon the together with cool air fans
pull small amount of dust. The silicon chips in the computer attract dust that eventually sticks to
the chips generating more heat. Thus, periodically the computer must be opened and using a
canned air or vacuum this dust must be blown away.
23
Antivirus updates/scanning
Computer virus can halt various operation of the computer. In case a computer is infected by a
virus PC maintenance will be naught. Thus the computer system must have virus scanning
software installed (Campbell, et al 2015). Microsoft presently is including a free malware
scanner for all Windows operating system, that effectively scans and removes viruses that to
with no cost.
Third party anti-virus software should be installed from authenticated site and it must be update
with the latest available version in regular basis.
Hardware Clean-up
During process the Computers tends to generate a huge amount of heat, thus the mother board of
the computer has a cooling fan attached to it. This main function of this fan is to pull in the cool
air from surrounding so that the internal components are kept cooler and issues of overheating is
avoided (Stolyar, and Yuque, 2018). It is a common phenomenon the together with cool air fans
pull small amount of dust. The silicon chips in the computer attract dust that eventually sticks to
the chips generating more heat. Thus, periodically the computer must be opened and using a
canned air or vacuum this dust must be blown away.
23

Conclusion
From this above report conclusion can be made that Computer system comprises of various
hardware and software devices for performing different operations. The main computer
component is the processor or the CPU. In this above report, purpose, importance, and elements
CPU unit has been discussed. Next important element is the operating system that controls and
manages the overall computer system. This Report has discussed the importance of OS and types
of operating system. The report has illustrated different addresses the networking devices have.
Report has also discussed about various issues the user faces while using a computer system
using a questionnaire and lastly the report also have mentioned steps involved in computer
maintenance activities through which overall performance of the computer can be maintained.
24
From this above report conclusion can be made that Computer system comprises of various
hardware and software devices for performing different operations. The main computer
component is the processor or the CPU. In this above report, purpose, importance, and elements
CPU unit has been discussed. Next important element is the operating system that controls and
manages the overall computer system. This Report has discussed the importance of OS and types
of operating system. The report has illustrated different addresses the networking devices have.
Report has also discussed about various issues the user faces while using a computer system
using a questionnaire and lastly the report also have mentioned steps involved in computer
maintenance activities through which overall performance of the computer can be maintained.
24

References
Books and journals
Comer, D., 2017. Essentials of computer architecture. Chapman and Hall/CRC.
Harris, S. and Harris, D., 2015. Digital design and computer architecture: arm edition.
Morgan Kaufmann. Peter, S., Li, J., Zhang, I., Ports, D.R., Woos, D., Krishnamurthy, A.,
Anderson, T. and Roscoe, T., 2016. Arrakis: The operating system is the control
plane. ACM Transactions on Computer Systems (TOCS), 33(4), p.11.
Hennessy, J.L. and Patterson, D.A., 2011. Computer architecture: a quantitative
approach. Elsevier
Laitkorpi, M., Nivala, A., Lepola, J., Metsapelto, A. and Partanen, T., M-FILES OY,
2017. Method, an apparatus, a computer system, a security component and a computer
readable medium for defining access rights in metadata-based file arrangement. U.S.
Patent 9,576,148.
Lederer, F., Köhn, I. and Frank, W., Fujitsu Technology Solutions Intellectual Property
GmbH, 2017. Computer system, arrangement for remote maintenance and remote
maintenance method. U.S. Patent 9,606,560.
Organick, E.I., 2014. Computer system organization: the B5700/B6700 series. Academic
Press.
Organick, E.I., 2014. Computer system organization: the B5700/B6700 series. Academic
Press.
Siewiorek, D. and Swarz, R., 2017. Reliable Computer Systems: Design and Evaluatuion.
Digital Press.
Campbell, J.D. and Reyes-Picknell, J.V., 2015. Uptime: Strategies for excellence in
maintenance management. CRC Press.
Husain, S.M.A. and Printz, R.P., ClearCube Tech Inc, 2017. Computer system image
clustering architecture and use. U.S. Patent 9,537,949.
White, G.B., Fisch, E.A. and Pooch, U.W., 2017. Computer system and network security.
CRC press.
25
Books and journals
Comer, D., 2017. Essentials of computer architecture. Chapman and Hall/CRC.
Harris, S. and Harris, D., 2015. Digital design and computer architecture: arm edition.
Morgan Kaufmann. Peter, S., Li, J., Zhang, I., Ports, D.R., Woos, D., Krishnamurthy, A.,
Anderson, T. and Roscoe, T., 2016. Arrakis: The operating system is the control
plane. ACM Transactions on Computer Systems (TOCS), 33(4), p.11.
Hennessy, J.L. and Patterson, D.A., 2011. Computer architecture: a quantitative
approach. Elsevier
Laitkorpi, M., Nivala, A., Lepola, J., Metsapelto, A. and Partanen, T., M-FILES OY,
2017. Method, an apparatus, a computer system, a security component and a computer
readable medium for defining access rights in metadata-based file arrangement. U.S.
Patent 9,576,148.
Lederer, F., Köhn, I. and Frank, W., Fujitsu Technology Solutions Intellectual Property
GmbH, 2017. Computer system, arrangement for remote maintenance and remote
maintenance method. U.S. Patent 9,606,560.
Organick, E.I., 2014. Computer system organization: the B5700/B6700 series. Academic
Press.
Organick, E.I., 2014. Computer system organization: the B5700/B6700 series. Academic
Press.
Siewiorek, D. and Swarz, R., 2017. Reliable Computer Systems: Design and Evaluatuion.
Digital Press.
Campbell, J.D. and Reyes-Picknell, J.V., 2015. Uptime: Strategies for excellence in
maintenance management. CRC Press.
Husain, S.M.A. and Printz, R.P., ClearCube Tech Inc, 2017. Computer system image
clustering architecture and use. U.S. Patent 9,537,949.
White, G.B., Fisch, E.A. and Pooch, U.W., 2017. Computer system and network security.
CRC press.
25
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





