Network Design Proposal for XYZ Retails
VerifiedAdded on 2023/04/20
|15
|873
|395
Presentation
AI Summary
This proposal of network design will provide security to the XYZ retails from different types of the cyber-attacks. It will provide flexibility in areas such as security, data backup, and network scalability.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Computer-
Networks
A connected group of
computer systems.
Networks
A connected group of
computer systems.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Content
Introduction
XYZ retails current network
Network planning
Inventory of network devices
Necessary Software Required
Security implementation
Disaster recovery & cost analysis
Proposed Network design
Implementing new network
Training and education
Introduction
XYZ retails current network
Network planning
Inventory of network devices
Necessary Software Required
Security implementation
Disaster recovery & cost analysis
Proposed Network design
Implementing new network
Training and education
Introduction
This proposal of network design will
provide security to the XYZ retails from
different types of the cyber-attacks
This will provide flexibility in these
areas
Security
Data backup
Network scalability
This proposal of network design will
provide security to the XYZ retails from
different types of the cyber-attacks
This will provide flexibility in these
areas
Security
Data backup
Network scalability

Present network of XYZ Retails
Present network is not having a proper
connectivity. All the departments are
based on the Local Area Network s(LAN)
There is no proper security in the their
network from the public network
Basic network devices are used to
connect system using LAN’s and internet
They have three store in a same city but
not connected separately
Present network is not having a proper
connectivity. All the departments are
based on the Local Area Network s(LAN)
There is no proper security in the their
network from the public network
Basic network devices are used to
connect system using LAN’s and internet
They have three store in a same city but
not connected separately
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Network Planning
Milestone #1 : Find basic requirements
Milestone #2 : Inventory equipment, such as
servers, and networking device
Milestone #3: find required software to solve
security issues
Milestone #4 : Networking and configuration of
servers as well as configuration of network
devices
Milestone #5: user’s permissions and
performance check
Milestone #1 : Find basic requirements
Milestone #2 : Inventory equipment, such as
servers, and networking device
Milestone #3: find required software to solve
security issues
Milestone #4 : Networking and configuration of
servers as well as configuration of network
devices
Milestone #5: user’s permissions and
performance check

Hardware requirements
Audit for network devices
Usages of current network devices
New network devices
Calculate basic things, such as number
of systems, servers, cables, connectors
and many more (Dye, McDonald, & Rufi,
2007).
Audit for network devices
Usages of current network devices
New network devices
Calculate basic things, such as number
of systems, servers, cables, connectors
and many more (Dye, McDonald, & Rufi,
2007).
Network devices inventory
Servers
• 10 print servers
• 1 web servers
• 1 application server
• 1 servers (Linus
based)
• 1 directory server for
the Windows server
2016
• 1 database server
Workstation
• 94 workstations
• 25 print
Need of network
devices
• 20 switches
• 10 routers
• 10 DSU/ CSU
(Certiology, 2018).
Servers
• 10 print servers
• 1 web servers
• 1 application server
• 1 servers (Linus
based)
• 1 directory server for
the Windows server
2016
• 1 database server
Workstation
• 94 workstations
• 25 print
Need of network
devices
• 20 switches
• 10 routers
• 10 DSU/ CSU
(Certiology, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Software Requirements
All nodes will be configured in same
manner (Dosal, 2018).
Antivirus, Microsoft office 2016, backup
utility installed in each node
Basic applications will installed in all the
nodes, such as retail software, SQL, and
Fedora 8 and connect all the location via
VPN
All nodes will be configured in same
manner (Dosal, 2018).
Antivirus, Microsoft office 2016, backup
utility installed in each node
Basic applications will installed in all the
nodes, such as retail software, SQL, and
Fedora 8 and connect all the location via
VPN
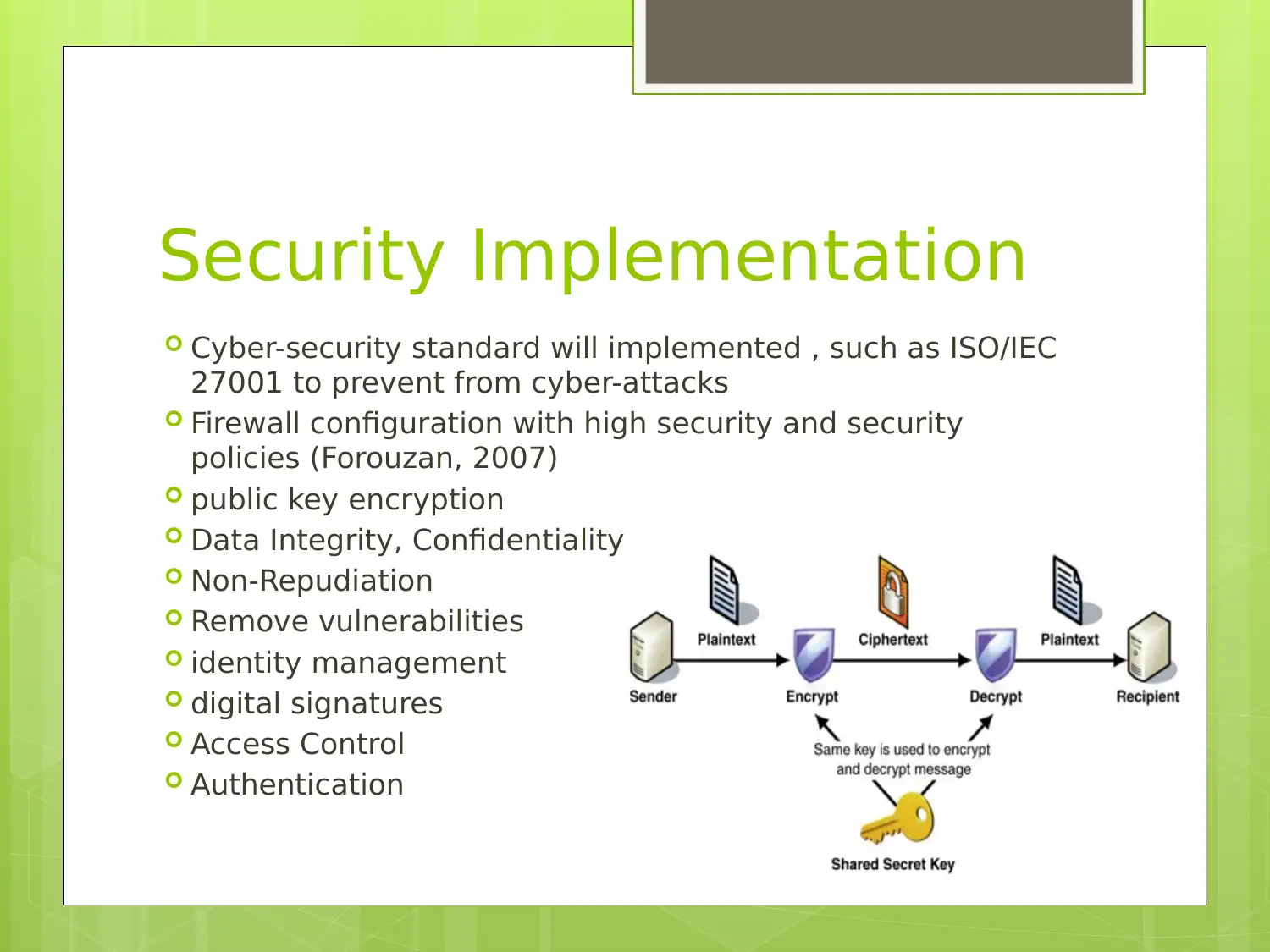
Security Implementation
Cyber-security standard will implemented , such as ISO/IEC
27001 to prevent from cyber-attacks
Firewall configuration with high security and security
policies (Forouzan, 2007)
public key encryption
Data Integrity, Confidentiality
Non-Repudiation
Remove vulnerabilities
identity management
digital signatures
Access Control
Authentication
Cyber-security standard will implemented , such as ISO/IEC
27001 to prevent from cyber-attacks
Firewall configuration with high security and security
policies (Forouzan, 2007)
public key encryption
Data Integrity, Confidentiality
Non-Repudiation
Remove vulnerabilities
identity management
digital signatures
Access Control
Authentication

Firewall and IDS/IPS
Firewall: it is used for the network security from
suspicious packets from outside of network. it filter
all the packets, which are coming from outside of
network.
IDS: it is a system that have special instruction to
detect suspicious activities in the network and
inform about it to the network administrator
IPS: Instruction protection system is used to secure
network from internal and external threats. It find
out suspicious things in the network and make them
in a list, which are trying for unauthorized access.
Firewall: it is used for the network security from
suspicious packets from outside of network. it filter
all the packets, which are coming from outside of
network.
IDS: it is a system that have special instruction to
detect suspicious activities in the network and
inform about it to the network administrator
IPS: Instruction protection system is used to secure
network from internal and external threats. It find
out suspicious things in the network and make them
in a list, which are trying for unauthorized access.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Disaster Recovery
Business continuity: data and information
are so important for business continuity
(Cowley, 2012).
Installed new hardware
Backup of all the data in data centers and
backup servers
Software patches
Implement legal things
Disaster recovery benefits
Business continuity: data and information
are so important for business continuity
(Cowley, 2012).
Installed new hardware
Backup of all the data in data centers and
backup servers
Software patches
Implement legal things
Disaster recovery benefits
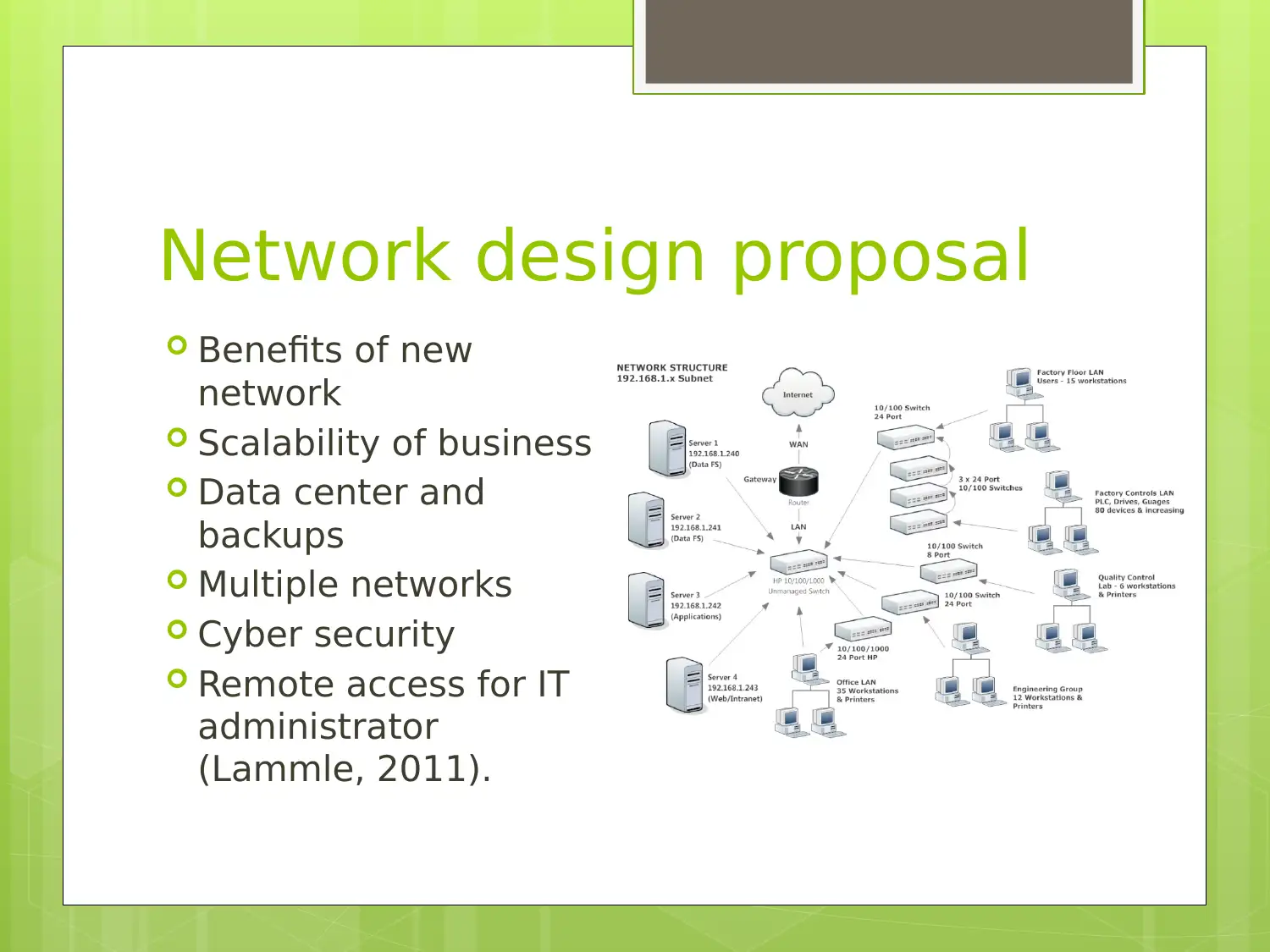
Network design proposal
Benefits of new
network
Scalability of business
Data center and
backups
Multiple networks
Cyber security
Remote access for IT
administrator
(Lammle, 2011).
Benefits of new
network
Scalability of business
Data center and
backups
Multiple networks
Cyber security
Remote access for IT
administrator
(Lammle, 2011).
Testing performance of Network
Network testing
Hardware testing
Security testing
Retails software testing
Database testing
All servers access testing using scripts
(Jacobs, 2016).
Network testing
Hardware testing
Security testing
Retails software testing
Database testing
All servers access testing using scripts
(Jacobs, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Dosal, E., 2018. 5 Common Network Security Problems and Solutions. [Online]
Available at: https://www.compuquip.com/blog/5-common-network-security-problems-and-
solutions
[Accessed 12 March 2019].
Schilling , J., 2017. Building A Strong Foundation: How Network Architecture Dictates IT
Security. [Online]
Available at: https://www.forbes.com/sites/forbestechcouncil/2017/09/21/building-a-strong-
foundation-how-network-architecture-dictates-it-security/#4201e0c23d5b
Certiology, 2018. Network Devices:. [Online]
Available at: http://www.certiology.com/computing/computer-networking/network-devices.html
[Accessed 29 08 2018].
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Dye, M., McDonald, R. & Rufi, A., 2007. Network Fundamentals, CCNA Exploration Companion
Guide. Indianapolis: Cisco press..
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata McGraw-
Hill Education.
Jacobs, D., 2016. Network fault management in today's complex data centers. [Online]
Available at: https://searchnetworking.techtarget.com/tip/Network-fault-management-in-
todays-complex-data-centers
Lammle, T., 2011. CCNA Cisco Certified Network Associate Deluxe Study Guide. indiana: John
Wiley & Sons.
Dosal, E., 2018. 5 Common Network Security Problems and Solutions. [Online]
Available at: https://www.compuquip.com/blog/5-common-network-security-problems-and-
solutions
[Accessed 12 March 2019].
Schilling , J., 2017. Building A Strong Foundation: How Network Architecture Dictates IT
Security. [Online]
Available at: https://www.forbes.com/sites/forbestechcouncil/2017/09/21/building-a-strong-
foundation-how-network-architecture-dictates-it-security/#4201e0c23d5b
Certiology, 2018. Network Devices:. [Online]
Available at: http://www.certiology.com/computing/computer-networking/network-devices.html
[Accessed 29 08 2018].
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Dye, M., McDonald, R. & Rufi, A., 2007. Network Fundamentals, CCNA Exploration Companion
Guide. Indianapolis: Cisco press..
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata McGraw-
Hill Education.
Jacobs, D., 2016. Network fault management in today's complex data centers. [Online]
Available at: https://searchnetworking.techtarget.com/tip/Network-fault-management-in-
todays-complex-data-centers
Lammle, T., 2011. CCNA Cisco Certified Network Associate Deluxe Study Guide. indiana: John
Wiley & Sons.

Any Questions ?
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




