Cyber Algorithms Assignment
VerifiedAdded on 2023/03/31
|10
|1383
|206
AI Summary
This report focuses on applying relevant error detection and correction algorithms on the MHR system, an Australia-based website for recording health conditions. It discusses activities such as login and adding a patient, as well as cryptography methods and role-based access control. Recommendations include implementing proper encryption methods and authentication measures for data security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER ALGORITHMS ASSIGNMENT
CYBER ALGORITHMS ASSIGNMENT –
Australian My Health Record - MHR system
Name of the Student
Name of the University
Author Note
CYBER ALGORITHMS ASSIGNMENT –
Australian My Health Record - MHR system
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER ALGORITHMS ASSIGNMENT
Table of Contents
Introduction......................................................................................................................................2
About the MHR system...................................................................................................................2
Activity 1:........................................................................................................................................2
Activity 2:........................................................................................................................................4
Activity 3.........................................................................................................................................4
Recommendation.............................................................................................................................5
Conclusion.......................................................................................................................................5
Bibliography....................................................................................................................................6
Table of Contents
Introduction......................................................................................................................................2
About the MHR system...................................................................................................................2
Activity 1:........................................................................................................................................2
Activity 2:........................................................................................................................................4
Activity 3.........................................................................................................................................4
Recommendation.............................................................................................................................5
Conclusion.......................................................................................................................................5
Bibliography....................................................................................................................................6

2CYBER ALGORITHMS ASSIGNMENT
Introduction
The main aim behind developing the report is to identify the major set of cyber security
algorithms that can be used for the purpose of detecting errors in an application. The report will
focus on applying relevant error detection and correction algorithms on the MHR system. MHR
system is an Australia based website that helps in recording the health condition of the users. this
is a new initiative that is started by Australia for the purpose of storing the patients data effective
at one place. MHR system will be allowing the main stakeholders to communicate effectively in
order to provide better services towards the patients. Thus it is expected that the MHR system
will ensure a better way of providing healthcare facility towards the patients.
About the MHR system
The MHR system is a new initiative that is started by Australia for providing better
services towards the patients. The system will store the necessary details associated with each
patient and will be able to provide better services towards them. Apart from the patient’s data,
MHR will also store details associated with nurses, specialists and doctors. The developed
system will be able to maintain data at one place securely. However the access is only provided
to authenticate persons. The MHR users are the one who has the authority to access the details
related to patient.
Introduction
The main aim behind developing the report is to identify the major set of cyber security
algorithms that can be used for the purpose of detecting errors in an application. The report will
focus on applying relevant error detection and correction algorithms on the MHR system. MHR
system is an Australia based website that helps in recording the health condition of the users. this
is a new initiative that is started by Australia for the purpose of storing the patients data effective
at one place. MHR system will be allowing the main stakeholders to communicate effectively in
order to provide better services towards the patients. Thus it is expected that the MHR system
will ensure a better way of providing healthcare facility towards the patients.
About the MHR system
The MHR system is a new initiative that is started by Australia for providing better
services towards the patients. The system will store the necessary details associated with each
patient and will be able to provide better services towards them. Apart from the patient’s data,
MHR will also store details associated with nurses, specialists and doctors. The developed
system will be able to maintain data at one place securely. However the access is only provided
to authenticate persons. The MHR users are the one who has the authority to access the details
related to patient.

3CYBER ALGORITHMS ASSIGNMENT
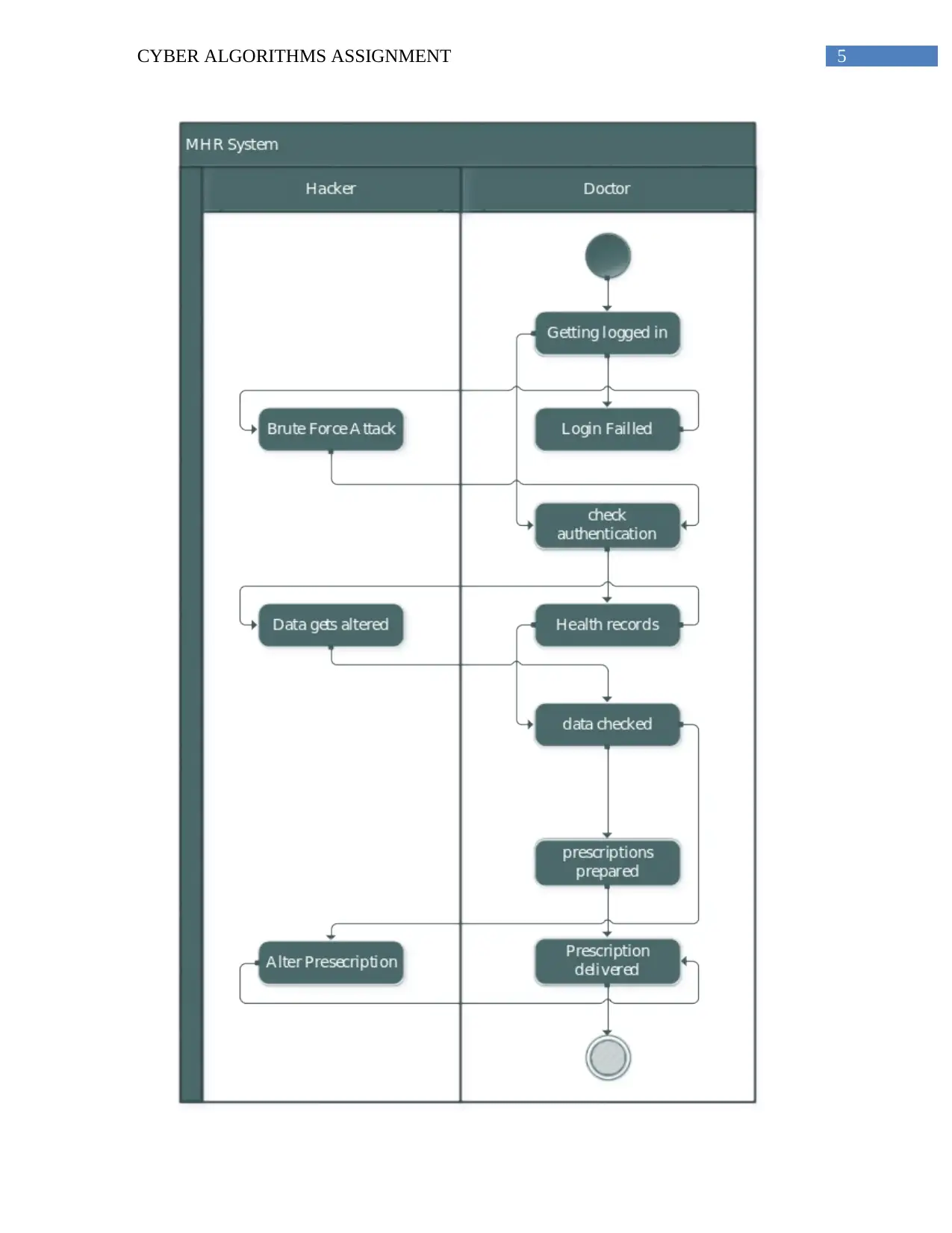
Activity 1:
The MHR system is responsible for performing several activities. However this part of
the report will focus on only two major activities. The activities are login to the system and
adding a patient within the system.
The login process is identified one of the important processes for the system. There is a
high need to ensure that proper person is given the access over the system. The main users
associated with MHR system are the users who will be allowed to access the health records
associated with a patient. The patient records can be accessed by the doctors, specialists, patients
and medical receptionist. In order to log in into the system the user must have proper credentials.
The user will be allowed to get into the system only when the credentials are verified by MHR.
The second process that is identified within the MHR system is adding a patient.
Whenever a new patients records are being provided towards the medical receptionist than they
will verify the data and will add the details within the system. As soon as the data of a patient is
added in the MHR system than the doctors and other users of system will be able to access it.
These actions are identified to be one of the important performances thus it is important
to ensure that proper control is maintained over these actions. In case login is provided to
unauthenticated person than it will become difficult to manage the activities. This will eventually
hamper the process and will impact the health records. Moreover they will get the power to
tamper the health records of patients. Thus proper login is needed to be provided towards the
users. This can harm the sensitive data that are stored within the system. The malicious attack
that can occur in response to adding patients within the MHR system is that if any patient data is
stored with inappropriate data than it can hamper the performance of the system. Moreover the if
Activity 1:
The MHR system is responsible for performing several activities. However this part of
the report will focus on only two major activities. The activities are login to the system and
adding a patient within the system.
The login process is identified one of the important processes for the system. There is a
high need to ensure that proper person is given the access over the system. The main users
associated with MHR system are the users who will be allowed to access the health records
associated with a patient. The patient records can be accessed by the doctors, specialists, patients
and medical receptionist. In order to log in into the system the user must have proper credentials.
The user will be allowed to get into the system only when the credentials are verified by MHR.
The second process that is identified within the MHR system is adding a patient.
Whenever a new patients records are being provided towards the medical receptionist than they
will verify the data and will add the details within the system. As soon as the data of a patient is
added in the MHR system than the doctors and other users of system will be able to access it.
These actions are identified to be one of the important performances thus it is important
to ensure that proper control is maintained over these actions. In case login is provided to
unauthenticated person than it will become difficult to manage the activities. This will eventually
hamper the process and will impact the health records. Moreover they will get the power to
tamper the health records of patients. Thus proper login is needed to be provided towards the
users. This can harm the sensitive data that are stored within the system. The malicious attack
that can occur in response to adding patients within the MHR system is that if any patient data is
stored with inappropriate data than it can hamper the performance of the system. Moreover the if
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4CYBER ALGORITHMS ASSIGNMENT
any newly added patient turns to be fraud one than there is a high chance that the data stored
within the system will get highly impacted.
any newly added patient turns to be fraud one than there is a high chance that the data stored
within the system will get highly impacted.
5CYBER ALGORITHMS ASSIGNMENT

6CYBER ALGORITHMS ASSIGNMENT
Activity 2:
Cryptography is the method of encoding and decoding a message for the purpose of
ensuring better confidentiality. With a proper encoding and decoding method it becomes easy to
detect the errors and also ensures that proper measures are provided for correcting these errors.
The major methods that are used for error detection and correction are cyclic redundancy check
and RS algorithm. The RS algorithm helps in controlling the errors that arises while transmitting
a data. This also ensures that the data loss is being maintained effectively so that they can be
used for further transmissions effectively. In the MHR system the cyclic redundancy check
method is being implemented for the purpose controlling the errors that arises at the time of
transmitting data. This method uses an effective way of encoding and decoding the data so that
only authorized person can get the access over the system.
Activity 3
The ACID property states that the system is able to maintain proper atomicity throughout
the data stored. The MHR system focuses on storing the details associated with patients and
hence it becomes essential to ensure that proper security is maintained throughout the MHR
system. While analyzing the MHR system I have analyzed that it satisfies the ACID properties as
it maintains a proper consistency throughout the database. In addition to this the database system
is durable enough for holding all the records effectively and allows users to modify it as per the
needs. This ensures that proper security properties are implemented within the MHR system that
will help in providing better support.
Activity 2:
Cryptography is the method of encoding and decoding a message for the purpose of
ensuring better confidentiality. With a proper encoding and decoding method it becomes easy to
detect the errors and also ensures that proper measures are provided for correcting these errors.
The major methods that are used for error detection and correction are cyclic redundancy check
and RS algorithm. The RS algorithm helps in controlling the errors that arises while transmitting
a data. This also ensures that the data loss is being maintained effectively so that they can be
used for further transmissions effectively. In the MHR system the cyclic redundancy check
method is being implemented for the purpose controlling the errors that arises at the time of
transmitting data. This method uses an effective way of encoding and decoding the data so that
only authorized person can get the access over the system.
Activity 3
The ACID property states that the system is able to maintain proper atomicity throughout
the data stored. The MHR system focuses on storing the details associated with patients and
hence it becomes essential to ensure that proper security is maintained throughout the MHR
system. While analyzing the MHR system I have analyzed that it satisfies the ACID properties as
it maintains a proper consistency throughout the database. In addition to this the database system
is durable enough for holding all the records effectively and allows users to modify it as per the
needs. This ensures that proper security properties are implemented within the MHR system that
will help in providing better support.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER ALGORITHMS ASSIGNMENT
Role based access control is referred to the method that helps in restricting the access that
is provided towards the users of the system. Thus mainly performs its functionality by ensuring
proper authorization technique and ensuring better way of managing the responsibility. The
MHR system has included proper authentication method that will help in managing the data
stored within the system. With proper role based access control it will become easy to manage
the activities. This will ensure that only authorized person are given the access over the data.
Recommendation
The MHR system mainly focuses on storing the data associated with each patient. Hence
it becomes essential to verify the user details and should ensure that only authorized person is
given the access. The system needs to implement proper encryption method that will be capable
of maintaining proper security towards the data.
Conclusion
Thus from the above report it can be concluded that with proper analysis of malicious
attack within the MHR system it is expected that the system will be able to perform efficiently.
The report has explained the two major activities that are taking place within the MHR system.
Along with this the main properties that maintained by MHR system are also explained in the
above parts of the report. Lastly it can be concluded that by implementing proper authentication
measures it will become easy for the system to store the patient’s data. This will ensure that data
are maintained within the system effectively.
Role based access control is referred to the method that helps in restricting the access that
is provided towards the users of the system. Thus mainly performs its functionality by ensuring
proper authorization technique and ensuring better way of managing the responsibility. The
MHR system has included proper authentication method that will help in managing the data
stored within the system. With proper role based access control it will become easy to manage
the activities. This will ensure that only authorized person are given the access over the data.
Recommendation
The MHR system mainly focuses on storing the data associated with each patient. Hence
it becomes essential to verify the user details and should ensure that only authorized person is
given the access. The system needs to implement proper encryption method that will be capable
of maintaining proper security towards the data.
Conclusion
Thus from the above report it can be concluded that with proper analysis of malicious
attack within the MHR system it is expected that the system will be able to perform efficiently.
The report has explained the two major activities that are taking place within the MHR system.
Along with this the main properties that maintained by MHR system are also explained in the
above parts of the report. Lastly it can be concluded that by implementing proper authentication
measures it will become easy for the system to store the patient’s data. This will ensure that data
are maintained within the system effectively.

8CYBER ALGORITHMS ASSIGNMENT
Bibliography
Gierałtowski, J., Ciuchciński, K., Grzegorczyk, I., Kośna, K., Soliński, M. and Podziemski, P.,
2015. RS slope detection algorithm for extraction of heart rate from noisy, multimodal
recordings. Physiological measurement, 36(8), p.1743.
Learmonth, Y.C., Adamson, B.C., Balto, J.M., Chiu, C.Y., Molina‐Guzman, I., Finlayson, M.,
Riskin, B.J. and Motl, R.W., 2017. Multiple sclerosis patients need and want information on
exercise promotion from healthcare providers: a qualitative study. Health Expectations, 20(4),
pp.574-583.
Maheswari, T. and Sukumar, P., 2015. Error Detection and Correction in SRAM Cell Using
DecimalMatrix Code. IOSR Journal of VLSI and Signal Processing (IOSR-JVSP), 5(1), pp.09-
14.
Nakamura, S., Duolikun, D., Enokido, T. and Takizawa, M., 2015. A write abortion-based
protocol in role-based access control systems. International Journal of Adaptive and Innovative
Systems, 2(2), pp.142-160.
Pandey, S. and Shanker, U., 2016. Transaction execution in distributed real-time database
systems. In Proc. Int. Conf. Innov. Inf. Embed. Commun. Syst (pp. 96-100).
Rajpoot, Q.M., Jensen, C.D. and Krishnan, R., 2015, July. Integrating attributes into role-based
access control. In IFIP Annual Conference on Data and Applications Security and Privacy (pp.
242-249). Springer, Cham.
Bibliography
Gierałtowski, J., Ciuchciński, K., Grzegorczyk, I., Kośna, K., Soliński, M. and Podziemski, P.,
2015. RS slope detection algorithm for extraction of heart rate from noisy, multimodal
recordings. Physiological measurement, 36(8), p.1743.
Learmonth, Y.C., Adamson, B.C., Balto, J.M., Chiu, C.Y., Molina‐Guzman, I., Finlayson, M.,
Riskin, B.J. and Motl, R.W., 2017. Multiple sclerosis patients need and want information on
exercise promotion from healthcare providers: a qualitative study. Health Expectations, 20(4),
pp.574-583.
Maheswari, T. and Sukumar, P., 2015. Error Detection and Correction in SRAM Cell Using
DecimalMatrix Code. IOSR Journal of VLSI and Signal Processing (IOSR-JVSP), 5(1), pp.09-
14.
Nakamura, S., Duolikun, D., Enokido, T. and Takizawa, M., 2015. A write abortion-based
protocol in role-based access control systems. International Journal of Adaptive and Innovative
Systems, 2(2), pp.142-160.
Pandey, S. and Shanker, U., 2016. Transaction execution in distributed real-time database
systems. In Proc. Int. Conf. Innov. Inf. Embed. Commun. Syst (pp. 96-100).
Rajpoot, Q.M., Jensen, C.D. and Krishnan, R., 2015, July. Integrating attributes into role-based
access control. In IFIP Annual Conference on Data and Applications Security and Privacy (pp.
242-249). Springer, Cham.

9CYBER ALGORITHMS ASSIGNMENT
Sit, A., Bouchard, F., Fickler, R., Gagnon-Bischoff, J., Larocque, H., Heshami, K., Elser, D.,
Peuntinger, C., Günthner, K., Heim, B. and Marquardt, C., 2017. High-dimensional intracity
quantum cryptography with structured photons. Optica, 4(9), pp.1006-1010.
Sit, A., Bouchard, F., Fickler, R., Gagnon-Bischoff, J., Larocque, H., Heshami, K., Elser, D.,
Peuntinger, C., Günthner, K., Heim, B. and Marquardt, C., 2017. High-dimensional intracity
quantum cryptography with structured photons. Optica, 4(9), pp.1006-1010.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





