Cyber Security Detection of Common Attacks Using SNORT Project 2022
Online MSc Project Extended Project Proposal: Scores and Feedback
56 Pages14273 Words14 Views
Added on 2022-10-14
Cyber Security Detection of Common Attacks Using SNORT Project 2022
Online MSc Project Extended Project Proposal: Scores and Feedback
Added on 2022-10-14
ShareRelated Documents
Running Head: CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
Cyber Security: Detection of Common Attacks against an Information System using
SNORT
Name of the Student
Name of the University
Author Note
Cyber Security: Detection of Common Attacks against an Information System using
SNORT
Name of the Student
Name of the University
Author Note

CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
1
Table of Contents
1 CHAPTER 1: Introduction 3
1.1 Background: 3
1.2 Rationale 5
1.3 Problem Statement 6
1.4 Aim, Objectives and Research Questions 6
1.4.1 Research Questions: 7
1.4.2 Objectives: 8
1.5 Summary: 13
2 Chapter 2: Literature review 3000 14
2.1 Intrusion Detection System 14
2.2 Network Based Intrusion Detection and Prevention System 15
2.3 Network Behavior Analysis System 16
2.4 Snort 17
2.5 Summary 25
3 Chapter 3: Research Methodology 2000 26
3.1 Introduction 26
3.2 Research problem and questions 27
3.3 Research Approach 27
3.4 Research Philosophy 28
3.4.1 Pragmatism 29
3.4.2 Realism 29
3.4.3 Interpretivism 29
1
Table of Contents
1 CHAPTER 1: Introduction 3
1.1 Background: 3
1.2 Rationale 5
1.3 Problem Statement 6
1.4 Aim, Objectives and Research Questions 6
1.4.1 Research Questions: 7
1.4.2 Objectives: 8
1.5 Summary: 13
2 Chapter 2: Literature review 3000 14
2.1 Intrusion Detection System 14
2.2 Network Based Intrusion Detection and Prevention System 15
2.3 Network Behavior Analysis System 16
2.4 Snort 17
2.5 Summary 25
3 Chapter 3: Research Methodology 2000 26
3.1 Introduction 26
3.2 Research problem and questions 27
3.3 Research Approach 27
3.4 Research Philosophy 28
3.4.1 Pragmatism 29
3.4.2 Realism 29
3.4.3 Interpretivism 29

CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
2
3.5 Research Design 30
3.5.1 Data collection methods 30
3.5.2 Samplings 31
3.5.3 Ethical issues 31
3.6 Summary 31
4 Chapter 4: Findings and Analysis 2000 32
4.1 Introduction 32
4.2 SNORT as a tool and Snort deployment 33
4.3 Common and/or Top OWASP attacks 33
4.4 Application of penetration testing methodology 38
4.5 Optimization of SNORT rules to capture suspicious activity generating from the pen
testing 39
5 Chapter 5: Conclusion and Recommendation40
5.1 Conclusion 40
5.2 Recommendation 42
6 References: 44
2
3.5 Research Design 30
3.5.1 Data collection methods 30
3.5.2 Samplings 31
3.5.3 Ethical issues 31
3.6 Summary 31
4 Chapter 4: Findings and Analysis 2000 32
4.1 Introduction 32
4.2 SNORT as a tool and Snort deployment 33
4.3 Common and/or Top OWASP attacks 33
4.4 Application of penetration testing methodology 38
4.5 Optimization of SNORT rules to capture suspicious activity generating from the pen
testing 39
5 Chapter 5: Conclusion and Recommendation40
5.1 Conclusion 40
5.2 Recommendation 42
6 References: 44

CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
3
1 CHAPTER 1: Introduction
1.1 Background:
Intrusion Detection today gives a representation of various web attacks and is very
important for the defense of any Information system against the proper functioning of security
systems. The evolution of the internet provides many possibilities and chances are boundless
however the risks increases with the same. The interconnection of several links forms a network
and protection of this network plays a vital role in protecting the Information system externally
or internally from attacks such as dDOS, malicious activities. The security of network starts with
the authorization and authentication. In this report, analysis generated by snorting in accordance
with an alter ratio of performances from attacks is evaluated. Intrusion detection systems play a
vital role in the securing the Information systems. The IDS are care programs that are written in
order to detect the malicious activities without privileges by means of analyzing patterns that are
suspicious and has two categories, namely- detecting misuse and anomaly detections Snort was
created on the year 1998 by Martin Roesch. Just like most of the open source projects, snort
started as an application that was of a small-scale and another possibility to the fully-developed
commercial IDS. The most widely used IDS is snort and is small and light weighted. The
SNORT tool is able to perform tasks such as real-time analysis of traffic. It is free and is open
type of Network Intrusion Prevention System. Snort is set on rich rules that is dependent on the
signatures present in the packets header and payload packet of Intrusions detection. Snort uses
liable to capture packets that are raw and before forwarding it to engine that detects it snort
decodes and then processes. The process of pre-processing involves various functionalities such
as dropping of packets, network layer three reassemble of fragments (Internet Protocols), TCP
sessions of layer four reconstructions and many more functions. The snort engine that detects
packet headers also checks it with payloads for numerous regulations stored across the database
of signature attacks.
The various techniques of the intrusion detections are application based, signature-based
and anomaly based. Application IDS performs detections on the events that occurs on an
application that is specific. Signature based performs tasks on traffic, and kwon patterns of
known attacks as well as its activities and preceding. Anomaly based examines traffic that is
3
1 CHAPTER 1: Introduction
1.1 Background:
Intrusion Detection today gives a representation of various web attacks and is very
important for the defense of any Information system against the proper functioning of security
systems. The evolution of the internet provides many possibilities and chances are boundless
however the risks increases with the same. The interconnection of several links forms a network
and protection of this network plays a vital role in protecting the Information system externally
or internally from attacks such as dDOS, malicious activities. The security of network starts with
the authorization and authentication. In this report, analysis generated by snorting in accordance
with an alter ratio of performances from attacks is evaluated. Intrusion detection systems play a
vital role in the securing the Information systems. The IDS are care programs that are written in
order to detect the malicious activities without privileges by means of analyzing patterns that are
suspicious and has two categories, namely- detecting misuse and anomaly detections Snort was
created on the year 1998 by Martin Roesch. Just like most of the open source projects, snort
started as an application that was of a small-scale and another possibility to the fully-developed
commercial IDS. The most widely used IDS is snort and is small and light weighted. The
SNORT tool is able to perform tasks such as real-time analysis of traffic. It is free and is open
type of Network Intrusion Prevention System. Snort is set on rich rules that is dependent on the
signatures present in the packets header and payload packet of Intrusions detection. Snort uses
liable to capture packets that are raw and before forwarding it to engine that detects it snort
decodes and then processes. The process of pre-processing involves various functionalities such
as dropping of packets, network layer three reassemble of fragments (Internet Protocols), TCP
sessions of layer four reconstructions and many more functions. The snort engine that detects
packet headers also checks it with payloads for numerous regulations stored across the database
of signature attacks.
The various techniques of the intrusion detections are application based, signature-based
and anomaly based. Application IDS performs detections on the events that occurs on an
application that is specific. Signature based performs tasks on traffic, and kwon patterns of
known attacks as well as its activities and preceding. Anomaly based examines traffic that is

CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
4
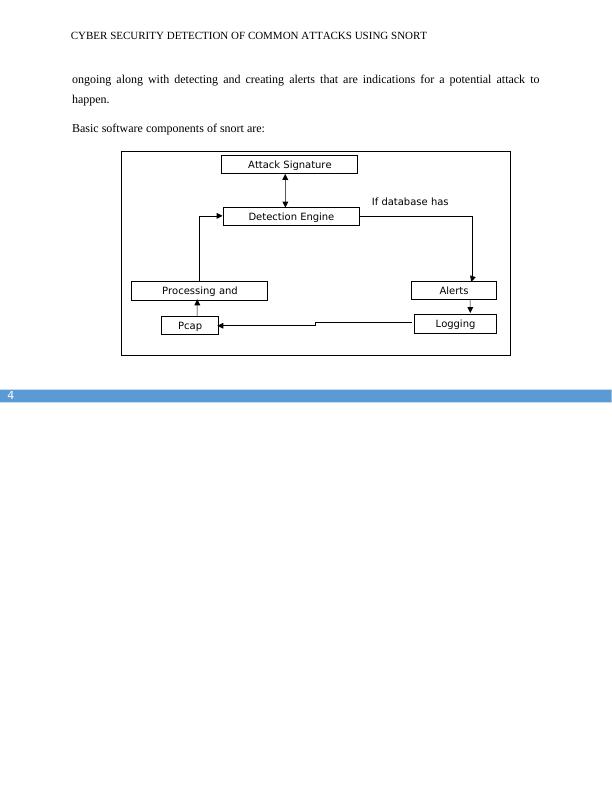
ongoing along with detecting and creating alerts that are indications for a potential attack to
happen.
Basic software components of snort are:
Attack Signature
If database has
Pcap Logging
AlertsProcessing and
Detection Engine
4
ongoing along with detecting and creating alerts that are indications for a potential attack to
happen.
Basic software components of snort are:
Attack Signature
If database has
Pcap Logging
AlertsProcessing and
Detection Engine
CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
5
1.2 Rationale
Detections of common attacks using SNORT is a technique to protect the Information
system and get all the information about the attacks as well as ways to overcome these. IDS has a
reputation of being a well-reserved yet requires a lot of precautions and the systems that are
commercial can be expensive but SNORT on the other hand is an open source IDS that is of
enterprise-grade and feasible. SNORT is a free toolkit and can function on any operating system
that is modern even if it is the only hardware of the system. The only investment required for the
snort toolkit is the time and effort and this enables the user to learn things about the network in-
depth. The toolkit enables the users to work on the network problems and intrusion detections
that is not visible. In addition to giving information in depth about the network the snort toolkit
also helps figure out the codes that are malicious. Snort has rules that are strong, easy to write
and flexible too. Within a timespan of hours new rules can be written by the snort community to
detect the malware that has just hit the network. This is a simple procedure and involves
implementing it to the local computer or rule files that are experimental and restart Snort and in
just in minutes the toolkit is ready to detect, eliminate and contain any malicious infestation that
passes the various layers of the security systems. SNORT rules can be easily found in snort.org
and bleedingsnort.com. A policy based Snort is an application that is obscure and needs to be
kept tabs on. Snort that is policy based is a concept that is very powerful and works in
environments that has traffics that are allowed and known. Policy based IDS is not for everyone
because defining and allowing what is known is a tricky procedure overall but also a very
simple. Snort rules also happen to be open-source and are overlooked but best. Security systems
such as ISS Real Secure abd Symantec ManHunt have modules allows the integrated
environment to use Snort Rules. These rules allows the environment make decisions that are
informed and criterions that causes systems alerts and is relevant to the environment.
The line of defense that comes first for any network is the Intrusion Detection System.
Working with Snort makes the network more secure and network core can be known because of
the possible attacks performed using Kali Linus as an attacker and using snort to detect the
attacks. This report shows the results once the snort in the IDS mode matches the data packets
and logs and alerts correspondingly. Internet Protocol traffic analysis is done to see the addresses
and the ports both source and destination. After the data packets are matched and filtered across
5
1.2 Rationale
Detections of common attacks using SNORT is a technique to protect the Information
system and get all the information about the attacks as well as ways to overcome these. IDS has a
reputation of being a well-reserved yet requires a lot of precautions and the systems that are
commercial can be expensive but SNORT on the other hand is an open source IDS that is of
enterprise-grade and feasible. SNORT is a free toolkit and can function on any operating system
that is modern even if it is the only hardware of the system. The only investment required for the
snort toolkit is the time and effort and this enables the user to learn things about the network in-
depth. The toolkit enables the users to work on the network problems and intrusion detections
that is not visible. In addition to giving information in depth about the network the snort toolkit
also helps figure out the codes that are malicious. Snort has rules that are strong, easy to write
and flexible too. Within a timespan of hours new rules can be written by the snort community to
detect the malware that has just hit the network. This is a simple procedure and involves
implementing it to the local computer or rule files that are experimental and restart Snort and in
just in minutes the toolkit is ready to detect, eliminate and contain any malicious infestation that
passes the various layers of the security systems. SNORT rules can be easily found in snort.org
and bleedingsnort.com. A policy based Snort is an application that is obscure and needs to be
kept tabs on. Snort that is policy based is a concept that is very powerful and works in
environments that has traffics that are allowed and known. Policy based IDS is not for everyone
because defining and allowing what is known is a tricky procedure overall but also a very
simple. Snort rules also happen to be open-source and are overlooked but best. Security systems
such as ISS Real Secure abd Symantec ManHunt have modules allows the integrated
environment to use Snort Rules. These rules allows the environment make decisions that are
informed and criterions that causes systems alerts and is relevant to the environment.
The line of defense that comes first for any network is the Intrusion Detection System.
Working with Snort makes the network more secure and network core can be known because of
the possible attacks performed using Kali Linus as an attacker and using snort to detect the
attacks. This report shows the results once the snort in the IDS mode matches the data packets
and logs and alerts correspondingly. Internet Protocol traffic analysis is done to see the addresses
and the ports both source and destination. After the data packets are matched and filtered across

CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
6
two designed factors and these are frequency and signature correlation. Frequency checks the fix
limits exceeding and on the other hand signature correlation combines frequency with the
correlations. Inside the snort database a table will be created and has two entries for the
frequency and these are signature name and frequency again. It is a challenge to protect systems
and information in it from attackers.
Snort depends on the bad suspected approach and relates with the suspicious or
pernicious applications. Snort can be downloaded from http://www.snort.org. Snort can double-
check the malicious malware defense just like it is designed to do. It is very easy to install snort
in windows environment as the host and using a Virtual Machine in this case (Virtual-Box).
1.3 Problem Statement
The perspective if we look from Information System refers to target a traffic also known
as routing the traffic so that it can be captured, monitoring and analysis. Snort IDS is a signature-
based methodology that can be compared to scanners that scans viruses, the process involves
detection of events by specific matching of patterns that are pre-defined and are called as
signatures. The drawback of the IDS system that is signature-based is the deficiency of
identification of attacks that are novel and are sometimes even the least of small variations or
patterns. Anomaly detection has an advantage as compared to the signature based detection and
this does not exist and is detectable and falls out of normal. A system when infested with worms
the alert system automatically starts to look for other malicious activities and capturing of
networks which hence triggers the TCP connection or the abnormal rules of the bandwidth. The
main drawback of this kind of attack is it has a false detection rate that happens to be high.
1.4 Aim, Objectives and Research Questions
The main aim of the project is to study various methodologies, techniques and ways of
adversary to perform tasks related to most common attacks that might cause or have caused
security breaches. The objective of this study in detection of common attacks using SNORT
helps evaluate the NIDS is configured to detect potential network attacks that is malicious. It also
shows what are the measures that can be taken to increase the performances of the detection
using the snort rules and varieties of configurations. Snort is an open source software program as
mentioned earlier and relies on the expertise and the determination of the intentions of the user
for good functioning and the detections made. The first initiative is to test the snort
6
two designed factors and these are frequency and signature correlation. Frequency checks the fix
limits exceeding and on the other hand signature correlation combines frequency with the
correlations. Inside the snort database a table will be created and has two entries for the
frequency and these are signature name and frequency again. It is a challenge to protect systems
and information in it from attackers.
Snort depends on the bad suspected approach and relates with the suspicious or
pernicious applications. Snort can be downloaded from http://www.snort.org. Snort can double-
check the malicious malware defense just like it is designed to do. It is very easy to install snort
in windows environment as the host and using a Virtual Machine in this case (Virtual-Box).
1.3 Problem Statement
The perspective if we look from Information System refers to target a traffic also known
as routing the traffic so that it can be captured, monitoring and analysis. Snort IDS is a signature-
based methodology that can be compared to scanners that scans viruses, the process involves
detection of events by specific matching of patterns that are pre-defined and are called as
signatures. The drawback of the IDS system that is signature-based is the deficiency of
identification of attacks that are novel and are sometimes even the least of small variations or
patterns. Anomaly detection has an advantage as compared to the signature based detection and
this does not exist and is detectable and falls out of normal. A system when infested with worms
the alert system automatically starts to look for other malicious activities and capturing of
networks which hence triggers the TCP connection or the abnormal rules of the bandwidth. The
main drawback of this kind of attack is it has a false detection rate that happens to be high.
1.4 Aim, Objectives and Research Questions
The main aim of the project is to study various methodologies, techniques and ways of
adversary to perform tasks related to most common attacks that might cause or have caused
security breaches. The objective of this study in detection of common attacks using SNORT
helps evaluate the NIDS is configured to detect potential network attacks that is malicious. It also
shows what are the measures that can be taken to increase the performances of the detection
using the snort rules and varieties of configurations. Snort is an open source software program as
mentioned earlier and relies on the expertise and the determination of the intentions of the user
for good functioning and the detections made. The first initiative is to test the snort

CYBER SECURITY DETECTION OF COMMON ATTACKS USING SNORT
7
configurations that are available when downloading. Secondly the configurations are further
extended by the available registered snort configurations given to users and then the
functionalities tested with the similar common attacks. Eventually, SNORT has to be tested by
the rules mentioned in the report. The attacks that tended to avoid the monitoring are tested with
these extended configurations that had avoided the simple snort rules. The report will also enable
the readers to have a clear insight on the popular and common attacks on the network about how
are these attacks designed to harm and infiltrate as well as the ways to mitigate it. At the end,
weak points in the SNORT are highlighted and what are the changes that can be made and what
are the improvements that can be added to encourage the enterprise network with the
implementation of the NIDS in a general way.
The outcome of the analysis and the functionalities mentioned will be a great help to the
enthusiasts of security system and the professionals to come up with the best defense system and
detect and prevent the possible harms using the various techniques and methodologies. This
report analyses how the Network Intrusion Detection Systems known as Snort with
configurations and rules will handle the common attacks caused on the networks. How the snort
functions and the attacks that it manages to evaluate the threats and vulnerabilities of the
configurations of the snort itself. Approaches such as bypassing the SNORT and the detection of
the common attacks has been highlighted in both theoretically as well as practically with
evaluations performed and experiments done using Windows 10 as the host OS and using a
Virtual box the snorting rules and tools configured in it. The attacks are mostly
performed using the Kali Linux terminal with implementation of various tools such as wire shark
for network packet detections and many other tools that will be further mentioned in the report.
1.4.1 Research Questions:
The research questions presented here aims to explore the uncertainties and the areas of
concerns and the need for an investigation that is deliberate. The research questions are
systematic and is thus meticulously formulated as the research guides through the potential
common attacks and network infiltrations of the current scenario. The research questions
mentioned here are feasible and relevant to the situation at hand and are as follows:
What are the most common attacks that an organization can face according to the
literature survey? What techniques and methods are used in order these attacks to be
7
configurations that are available when downloading. Secondly the configurations are further
extended by the available registered snort configurations given to users and then the
functionalities tested with the similar common attacks. Eventually, SNORT has to be tested by
the rules mentioned in the report. The attacks that tended to avoid the monitoring are tested with
these extended configurations that had avoided the simple snort rules. The report will also enable
the readers to have a clear insight on the popular and common attacks on the network about how
are these attacks designed to harm and infiltrate as well as the ways to mitigate it. At the end,
weak points in the SNORT are highlighted and what are the changes that can be made and what
are the improvements that can be added to encourage the enterprise network with the
implementation of the NIDS in a general way.
The outcome of the analysis and the functionalities mentioned will be a great help to the
enthusiasts of security system and the professionals to come up with the best defense system and
detect and prevent the possible harms using the various techniques and methodologies. This
report analyses how the Network Intrusion Detection Systems known as Snort with
configurations and rules will handle the common attacks caused on the networks. How the snort
functions and the attacks that it manages to evaluate the threats and vulnerabilities of the
configurations of the snort itself. Approaches such as bypassing the SNORT and the detection of
the common attacks has been highlighted in both theoretically as well as practically with
evaluations performed and experiments done using Windows 10 as the host OS and using a
Virtual box the snorting rules and tools configured in it. The attacks are mostly
performed using the Kali Linux terminal with implementation of various tools such as wire shark
for network packet detections and many other tools that will be further mentioned in the report.
1.4.1 Research Questions:
The research questions presented here aims to explore the uncertainties and the areas of
concerns and the need for an investigation that is deliberate. The research questions are
systematic and is thus meticulously formulated as the research guides through the potential
common attacks and network infiltrations of the current scenario. The research questions
mentioned here are feasible and relevant to the situation at hand and are as follows:
What are the most common attacks that an organization can face according to the
literature survey? What techniques and methods are used in order these attacks to be

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Penetration Testing and Intrusion Detection Name of the University Authorlg...
|57
|5094
|316
Network Intrusion Detection System Using SNORTlg...
|51
|9826
|455
Manage Network and Data Integritylg...
|62
|2549
|302
Cyber Security Strategies in Smart Grid Name of the University Preliminary Reportlg...
|46
|10914
|50
Firewall/IDS Security: Protection Researchlg...
|4
|3474
|42
Network Forensics Assignment - Real Time Analysislg...
|8
|1506
|265
