Demonstration of Network Security Tools
VerifiedAdded on 2022/12/22
|10
|2109
|85
AI Summary
This document provides a demonstration of network security tools, specifically Snort and Nessus. It explains what these tools are, their uses, and how they can help mitigate threats. The document also includes a comparison between Snort and Nessus, as well as information on determining network requirements and finding the best tool for your needs.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: DEMONSTRATION OF NETWORK SECURITY TOOLS
DEMONSTRATION OF NETWORK SECURITY TOOLS
Name of the Student:
Name of the University:
Author Note:
DEMONSTRATION OF NETWORK SECURITY TOOLS
Name of the Student:
Name of the University:
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1DEMONSTRATION OF NETWORK SECURITY TOOLS
Table of Contents
Snort...........................................................................................................................................2
What is snort?.........................................................................................................................2
Uses of snort:..........................................................................................................................2
Threat mitigation....................................................................................................................2
Nessus........................................................................................................................................3
What is Nessus?.....................................................................................................................3
Uses:.......................................................................................................................................3
Threat mitigation....................................................................................................................4
Comparison................................................................................................................................5
Determining network requirement for JKL:..............................................................................6
Best tool for JKL:.......................................................................................................................6
References:.................................................................................................................................8
Table of Contents
Snort...........................................................................................................................................2
What is snort?.........................................................................................................................2
Uses of snort:..........................................................................................................................2
Threat mitigation....................................................................................................................2
Nessus........................................................................................................................................3
What is Nessus?.....................................................................................................................3
Uses:.......................................................................................................................................3
Threat mitigation....................................................................................................................4
Comparison................................................................................................................................5
Determining network requirement for JKL:..............................................................................6
Best tool for JKL:.......................................................................................................................6
References:.................................................................................................................................8
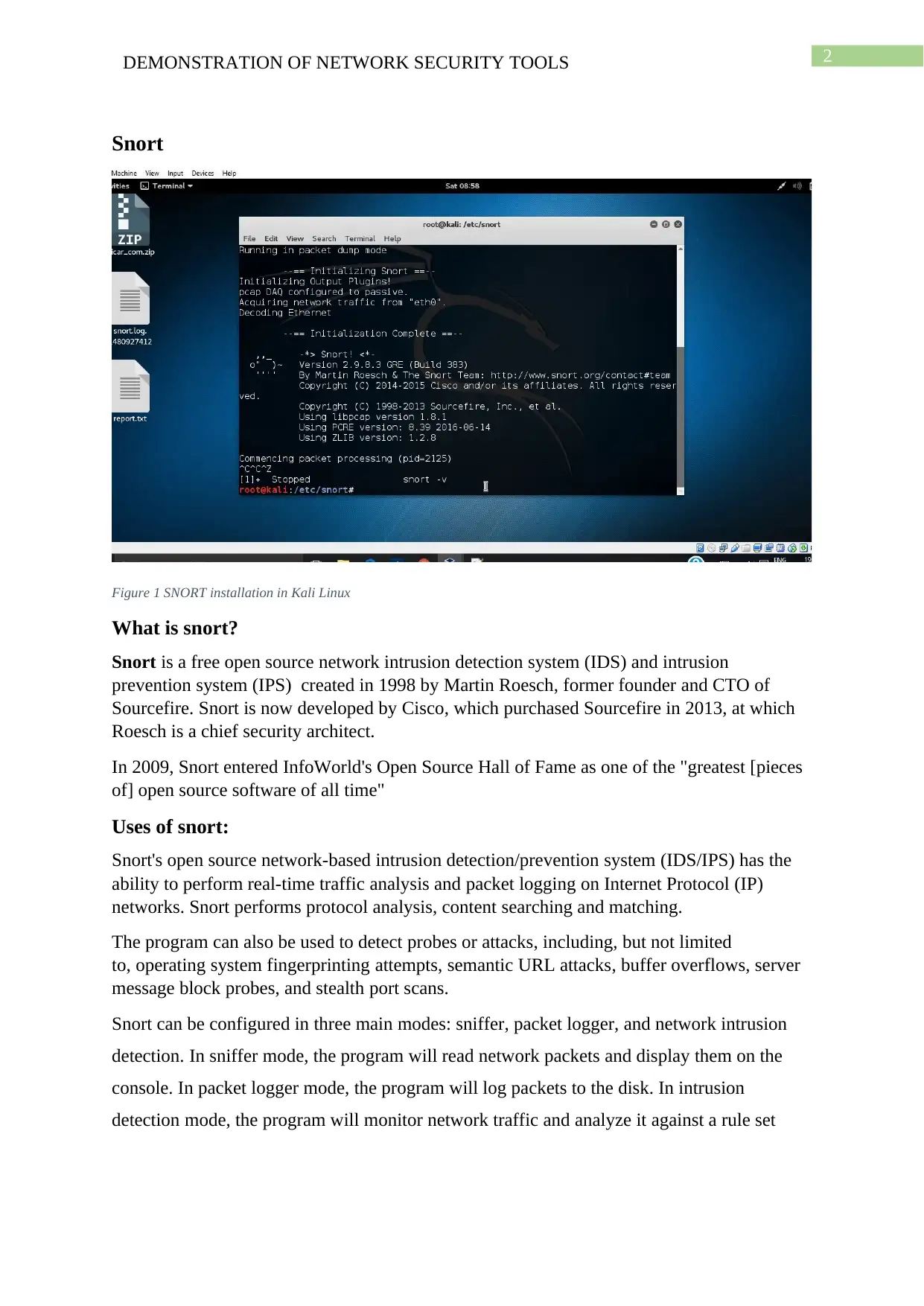
2DEMONSTRATION OF NETWORK SECURITY TOOLS
Snort
Figure 1 SNORT installation in Kali Linux
What is snort?
Snort is a free open source network intrusion detection system (IDS) and intrusion
prevention system (IPS) created in 1998 by Martin Roesch, former founder and CTO of
Sourcefire. Snort is now developed by Cisco, which purchased Sourcefire in 2013, at which
Roesch is a chief security architect.
In 2009, Snort entered InfoWorld's Open Source Hall of Fame as one of the "greatest [pieces
of] open source software of all time"
Uses of snort:
Snort's open source network-based intrusion detection/prevention system (IDS/IPS) has the
ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP)
networks. Snort performs protocol analysis, content searching and matching.
The program can also be used to detect probes or attacks, including, but not limited
to, operating system fingerprinting attempts, semantic URL attacks, buffer overflows, server
message block probes, and stealth port scans.
Snort can be configured in three main modes: sniffer, packet logger, and network intrusion
detection. In sniffer mode, the program will read network packets and display them on the
console. In packet logger mode, the program will log packets to the disk. In intrusion
detection mode, the program will monitor network traffic and analyze it against a rule set
Snort
Figure 1 SNORT installation in Kali Linux
What is snort?
Snort is a free open source network intrusion detection system (IDS) and intrusion
prevention system (IPS) created in 1998 by Martin Roesch, former founder and CTO of
Sourcefire. Snort is now developed by Cisco, which purchased Sourcefire in 2013, at which
Roesch is a chief security architect.
In 2009, Snort entered InfoWorld's Open Source Hall of Fame as one of the "greatest [pieces
of] open source software of all time"
Uses of snort:
Snort's open source network-based intrusion detection/prevention system (IDS/IPS) has the
ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP)
networks. Snort performs protocol analysis, content searching and matching.
The program can also be used to detect probes or attacks, including, but not limited
to, operating system fingerprinting attempts, semantic URL attacks, buffer overflows, server
message block probes, and stealth port scans.
Snort can be configured in three main modes: sniffer, packet logger, and network intrusion
detection. In sniffer mode, the program will read network packets and display them on the
console. In packet logger mode, the program will log packets to the disk. In intrusion
detection mode, the program will monitor network traffic and analyze it against a rule set

3DEMONSTRATION OF NETWORK SECURITY TOOLS
defined by the user. The program will then perform a specific action based on what has been
identified.
Threat mitigation
There were attempts made by the developers of the snort themselves to address this alert
flooding problem. The solution was to keep track of the states of all the TCP connections. As
we know TCP has states and it's possible to track the state of any TCP connection. They
redesigned Snort such that it doesn't accept packets from any connection that isn't properly
established through the famous three way handshake. Now the attacker cannot send the
packets as just 'single' packet but has to transmit three more packets in prior before sending
his attack packet to. The primary requirement for establishing a handshake with a host is that
they must already be communicating.
By design, Snort uses the 3WH to determine the initial sequence numbers of the TCP
connection. This is a blunder given the fact that it is possible for the attacker to produce a
fake handshake. The attacker will be using the connection parameters which will be of some
other connection will not be detected as the same parameters are being assigned to the
attacker initiated connection. This effect is called 'desynchronization'. This entire concept of
keeping track of TCP states is implemented by Snort designers as 'stream4'. But the cited
disadvantages render stream4 useless for preventing alert flooding.
defined by the user. The program will then perform a specific action based on what has been
identified.
Threat mitigation
There were attempts made by the developers of the snort themselves to address this alert
flooding problem. The solution was to keep track of the states of all the TCP connections. As
we know TCP has states and it's possible to track the state of any TCP connection. They
redesigned Snort such that it doesn't accept packets from any connection that isn't properly
established through the famous three way handshake. Now the attacker cannot send the
packets as just 'single' packet but has to transmit three more packets in prior before sending
his attack packet to. The primary requirement for establishing a handshake with a host is that
they must already be communicating.
By design, Snort uses the 3WH to determine the initial sequence numbers of the TCP
connection. This is a blunder given the fact that it is possible for the attacker to produce a
fake handshake. The attacker will be using the connection parameters which will be of some
other connection will not be detected as the same parameters are being assigned to the
attacker initiated connection. This effect is called 'desynchronization'. This entire concept of
keeping track of TCP states is implemented by Snort designers as 'stream4'. But the cited
disadvantages render stream4 useless for preventing alert flooding.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
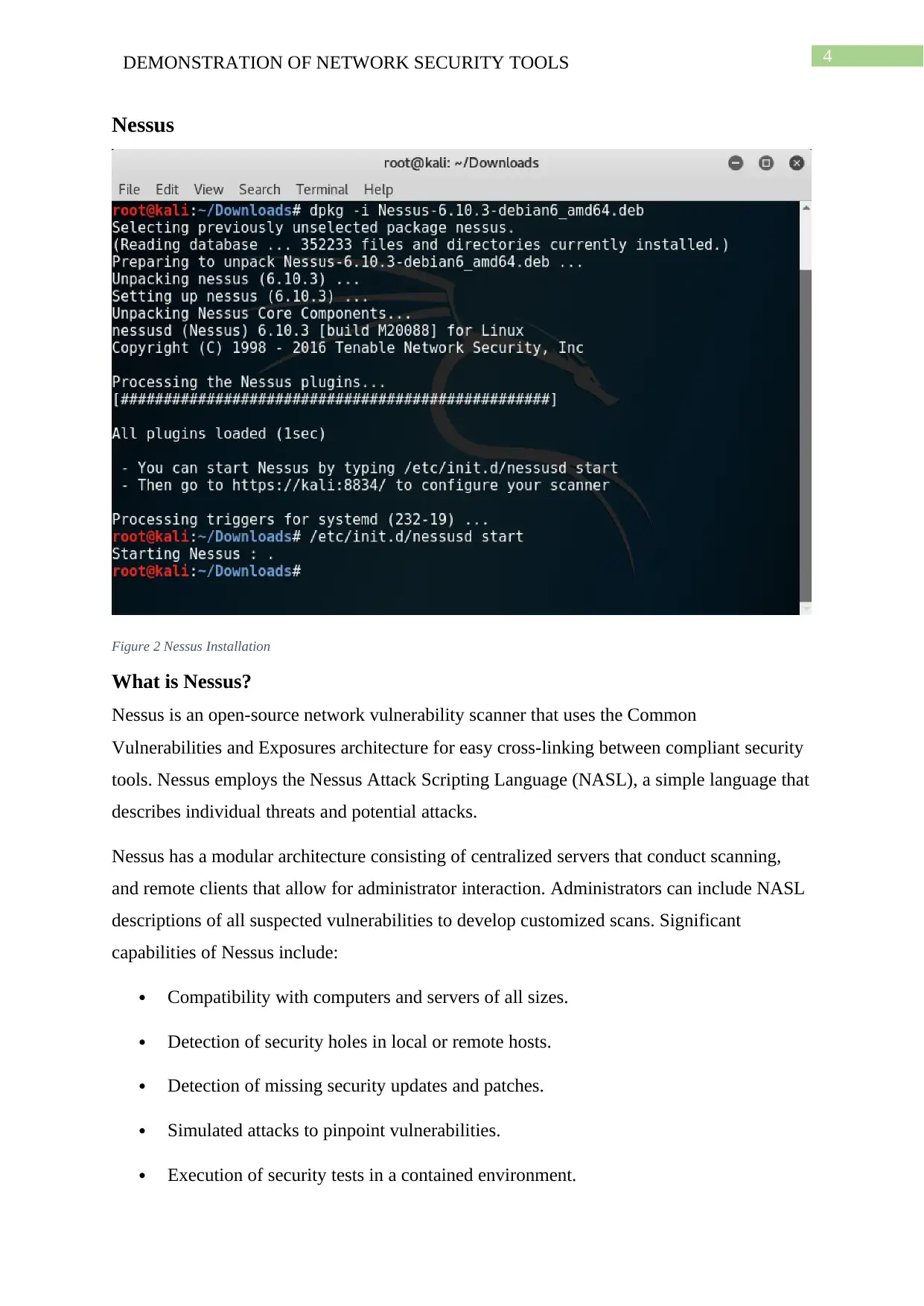
4DEMONSTRATION OF NETWORK SECURITY TOOLS
Nessus
Figure 2 Nessus Installation
What is Nessus?
Nessus is an open-source network vulnerability scanner that uses the Common
Vulnerabilities and Exposures architecture for easy cross-linking between compliant security
tools. Nessus employs the Nessus Attack Scripting Language (NASL), a simple language that
describes individual threats and potential attacks.
Nessus has a modular architecture consisting of centralized servers that conduct scanning,
and remote clients that allow for administrator interaction. Administrators can include NASL
descriptions of all suspected vulnerabilities to develop customized scans. Significant
capabilities of Nessus include:
Compatibility with computers and servers of all sizes.
Detection of security holes in local or remote hosts.
Detection of missing security updates and patches.
Simulated attacks to pinpoint vulnerabilities.
Execution of security tests in a contained environment.
Nessus
Figure 2 Nessus Installation
What is Nessus?
Nessus is an open-source network vulnerability scanner that uses the Common
Vulnerabilities and Exposures architecture for easy cross-linking between compliant security
tools. Nessus employs the Nessus Attack Scripting Language (NASL), a simple language that
describes individual threats and potential attacks.
Nessus has a modular architecture consisting of centralized servers that conduct scanning,
and remote clients that allow for administrator interaction. Administrators can include NASL
descriptions of all suspected vulnerabilities to develop customized scans. Significant
capabilities of Nessus include:
Compatibility with computers and servers of all sizes.
Detection of security holes in local or remote hosts.
Detection of missing security updates and patches.
Simulated attacks to pinpoint vulnerabilities.
Execution of security tests in a contained environment.

5DEMONSTRATION OF NETWORK SECURITY TOOLS
Scheduled security audits.
Uses:
Nessus allows scans for the following types of vulnerabilities:
Vulnerabilities that allow a remote hacker to control or access sensitive data on a system.
Misconfiguration (e.g. open mail relay, missing patches, etc.).
Default passwords, a few common passwords, and blank/absent passwords on some system
accounts. Nessus can also call Hydra (an external tool) to launch a dictionary attack.
Denials of service against the TCP/IP stack by using malformed packets
Preparation for PCI DSS audits
Initially, Nessus consisted of two main components; nessusd, the Nessus daemon, which does
the scanning, and nessus, the client, which controls scans and presents the vulnerability
results to the user. Later versions of Nessus (4 and greater) utilize a web server which
provides the same functionality as the client.
In typical operation, Nessus begins by doing a port scan with one of its four internal
portscanners (or it can optionally use AmapM[4] or Nmap[5]) to determine which ports are open
on the target and then tries various exploits on the open ports. The vulnerability tests,
available as subscriptions, are written in NASL (Nessus Attack Scripting Language), a
scripting language optimized for custom network interaction.
If the user chooses to do so (by disabling the option 'safe checks'), some of Nessus'
vulnerability tests may try to cause vulnerable services or operating systems to crash. This
lets a user test the resistance of a device before putting it in production.
Nessus provides additional functionality beyond testing for known network vulnerabilities.
For instance, it can use Windows credentials to examine patch levels on computers running
the Windows operating system, and can perform password auditing using dictionary and brute
force methods. Nessus 3 and later can also audit systems to make sure they have been
configured per a specific policy, such as the NSA's guide for hardening Windows servers.
This functionality utilizes Tenable's proprietary audit files or Security Content Automation
Protocol (SCAP) content.
Scheduled security audits.
Uses:
Nessus allows scans for the following types of vulnerabilities:
Vulnerabilities that allow a remote hacker to control or access sensitive data on a system.
Misconfiguration (e.g. open mail relay, missing patches, etc.).
Default passwords, a few common passwords, and blank/absent passwords on some system
accounts. Nessus can also call Hydra (an external tool) to launch a dictionary attack.
Denials of service against the TCP/IP stack by using malformed packets
Preparation for PCI DSS audits
Initially, Nessus consisted of two main components; nessusd, the Nessus daemon, which does
the scanning, and nessus, the client, which controls scans and presents the vulnerability
results to the user. Later versions of Nessus (4 and greater) utilize a web server which
provides the same functionality as the client.
In typical operation, Nessus begins by doing a port scan with one of its four internal
portscanners (or it can optionally use AmapM[4] or Nmap[5]) to determine which ports are open
on the target and then tries various exploits on the open ports. The vulnerability tests,
available as subscriptions, are written in NASL (Nessus Attack Scripting Language), a
scripting language optimized for custom network interaction.
If the user chooses to do so (by disabling the option 'safe checks'), some of Nessus'
vulnerability tests may try to cause vulnerable services or operating systems to crash. This
lets a user test the resistance of a device before putting it in production.
Nessus provides additional functionality beyond testing for known network vulnerabilities.
For instance, it can use Windows credentials to examine patch levels on computers running
the Windows operating system, and can perform password auditing using dictionary and brute
force methods. Nessus 3 and later can also audit systems to make sure they have been
configured per a specific policy, such as the NSA's guide for hardening Windows servers.
This functionality utilizes Tenable's proprietary audit files or Security Content Automation
Protocol (SCAP) content.

6DEMONSTRATION OF NETWORK SECURITY TOOLS
Threat mitigation
To mitigate risks within the enterprise, many organizations use a combination of manual and
automated solutions to deploy patches. Unfortunately, many organizations do not have an
effective plan in place for prioritizing, testing, and deploying patches. This issue can result in
organizations falling behind in their patch cycle and leave critical systems at risk. This
dashboard provides a high-level overview of current and mitigated vulnerabilities that will
enable security teams to quickly assess security risks and prioritize patch management
efforts.
This dashboard presents a summary of current and mitigated vulnerabilities over a set time
period. Trend charts provide a complete look at vulnerabilities by severity, which can
highlight the effectiveness of patch management efforts. Indicators using Common
Vulnerability Scoring System (CVSS) scores are presented that will enable analysts to
identify and address the most vulnerable hosts first. For each row, the CVSS scores
correspond to the Tenable severity levels as follows:
10.0 = Critical severity
7.0-9.9 = High
4.0-6.9 = Medium
0.0-3.9 = Low
Comparison
SNORT:
Snort is an awesome open source network intrusion prevention and detection system. It
combines the benefits of signature-, protocol- and anomaly-based inspection methods.
Snort is probably the most widely-deployed intrusion detection and prevention technology in
existence. It has developed through the years into a mature, feature-rich technology that has
essentially become a standard in intrusion detection and prevention.
Unfortunately, the Sourcefire-provided RPMs do not install on RHEL4 systems without using
third-party tools. You can build your own RPMs.
NESSUS:
Threat mitigation
To mitigate risks within the enterprise, many organizations use a combination of manual and
automated solutions to deploy patches. Unfortunately, many organizations do not have an
effective plan in place for prioritizing, testing, and deploying patches. This issue can result in
organizations falling behind in their patch cycle and leave critical systems at risk. This
dashboard provides a high-level overview of current and mitigated vulnerabilities that will
enable security teams to quickly assess security risks and prioritize patch management
efforts.
This dashboard presents a summary of current and mitigated vulnerabilities over a set time
period. Trend charts provide a complete look at vulnerabilities by severity, which can
highlight the effectiveness of patch management efforts. Indicators using Common
Vulnerability Scoring System (CVSS) scores are presented that will enable analysts to
identify and address the most vulnerable hosts first. For each row, the CVSS scores
correspond to the Tenable severity levels as follows:
10.0 = Critical severity
7.0-9.9 = High
4.0-6.9 = Medium
0.0-3.9 = Low
Comparison
SNORT:
Snort is an awesome open source network intrusion prevention and detection system. It
combines the benefits of signature-, protocol- and anomaly-based inspection methods.
Snort is probably the most widely-deployed intrusion detection and prevention technology in
existence. It has developed through the years into a mature, feature-rich technology that has
essentially become a standard in intrusion detection and prevention.
Unfortunately, the Sourcefire-provided RPMs do not install on RHEL4 systems without using
third-party tools. You can build your own RPMs.
NESSUS:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DEMONSTRATION OF NETWORK SECURITY TOOLS
No open source security article can be written without talking about Nessus. It is in use in
more than 75,000 unique organizations worldwide. Its scanners can be distributed throughout
an enterprise, inside DMZs and across physically separate networks. It includes more then
9,000 types of vulnerability checks that can also be made available for ad-hoc scanning, daily
scans and quick-response audits.
What's great about Nessus is that, unlike traditional network security scanners that focus on
the services listening on the network, Nessus also focuses on the local hosts. It can even
determine whether there are missing patches, whether they are running Windows, Unix or
RHEL4. And yes, it will run on RHEL4
Determining network requirement for JKL:
Designing a network can be a challenging task. Your first step is to understand your
networking requirements. The rest of this chapter explains how to determine these
requirements. Networking devices must reflect the goals, characteristics, and policies of the
organizations in which they operate. Two primary goals drive networking design and
implementation:
Application availability—Networks carry application information between
computers. If the applications are not available to network users, the network is not
doing its job.
Cost of ownership—Information system (IS) budgets today often run in the millions
of dollars. As large organizations increasingly rely on electronic data for managing
business activities, the associated costs of computing resources will continue to rise.
A well-designed network can help balance these objectives. When properly implemented, the
network infrastructure can optimize application availability and allow the cost-effective use
of existing network resources.
Best tool for JKL:
Snort is better than a proprietary solution because it is open source.
First, open source has the potential for more peer review, which translates into quality
assurance. No software is bug free, but no company can afford to hire the number of people
worldwide who take an interest in reviewing and securing open source code. Be aware that
No open source security article can be written without talking about Nessus. It is in use in
more than 75,000 unique organizations worldwide. Its scanners can be distributed throughout
an enterprise, inside DMZs and across physically separate networks. It includes more then
9,000 types of vulnerability checks that can also be made available for ad-hoc scanning, daily
scans and quick-response audits.
What's great about Nessus is that, unlike traditional network security scanners that focus on
the services listening on the network, Nessus also focuses on the local hosts. It can even
determine whether there are missing patches, whether they are running Windows, Unix or
RHEL4. And yes, it will run on RHEL4
Determining network requirement for JKL:
Designing a network can be a challenging task. Your first step is to understand your
networking requirements. The rest of this chapter explains how to determine these
requirements. Networking devices must reflect the goals, characteristics, and policies of the
organizations in which they operate. Two primary goals drive networking design and
implementation:
Application availability—Networks carry application information between
computers. If the applications are not available to network users, the network is not
doing its job.
Cost of ownership—Information system (IS) budgets today often run in the millions
of dollars. As large organizations increasingly rely on electronic data for managing
business activities, the associated costs of computing resources will continue to rise.
A well-designed network can help balance these objectives. When properly implemented, the
network infrastructure can optimize application availability and allow the cost-effective use
of existing network resources.
Best tool for JKL:
Snort is better than a proprietary solution because it is open source.
First, open source has the potential for more peer review, which translates into quality
assurance. No software is bug free, but no company can afford to hire the number of people
worldwide who take an interest in reviewing and securing open source code. Be aware that

8DEMONSTRATION OF NETWORK SECURITY TOOLS
just because the potential exists does not mean that all open source code is extensively
reviewed, but given Snort's popularity it's safe to say that a lot of people have looked at the
code.
Second, and more important in this case, Snort's rules are open source also. The rules or
signatures are the heart of a signature-based IDS. They describe the malicious traffic patterns
to look for and alert on if found. The problem with many of the commercial products is that
you don't get to see the actual rule. All you get to see is a couple of paragraphs that someone
at the vendor wrote about what that rule is SUPPOSED to do. Some vendor descriptions are
better than others, but the bottom line with Snort is that I can see the actual code that
triggered the alert. That means that I get to evaluate how relevant I find the alert, and I don't
have to depend on the person at the vendor who wrote the paragraph. When you spend a lot
of time looking at IDS events, which I do, this is key.
Snort is no more difficult to manage than any other IDS. The biggest challenge is probably
picking which tools and operating system you want, since Snort runs on Windows and all
major UNIX variations. Several companies support Snort appliances with Web GUI
management and reporting tools.
just because the potential exists does not mean that all open source code is extensively
reviewed, but given Snort's popularity it's safe to say that a lot of people have looked at the
code.
Second, and more important in this case, Snort's rules are open source also. The rules or
signatures are the heart of a signature-based IDS. They describe the malicious traffic patterns
to look for and alert on if found. The problem with many of the commercial products is that
you don't get to see the actual rule. All you get to see is a couple of paragraphs that someone
at the vendor wrote about what that rule is SUPPOSED to do. Some vendor descriptions are
better than others, but the bottom line with Snort is that I can see the actual code that
triggered the alert. That means that I get to evaluate how relevant I find the alert, and I don't
have to depend on the person at the vendor who wrote the paragraph. When you spend a lot
of time looking at IDS events, which I do, this is key.
Snort is no more difficult to manage than any other IDS. The biggest challenge is probably
picking which tools and operating system you want, since Snort runs on Windows and all
major UNIX variations. Several companies support Snort appliances with Web GUI
management and reporting tools.

9DEMONSTRATION OF NETWORK SECURITY TOOLS
References:
Naik, N., Diao, R., & Shen, Q. (2016, July). Application of dynamic fuzzy rule interpolation
for intrusion detection: D-FRI-Snort. In 2016 IEEE International Conference on Fuzzy
Systems (FUZZ-IEEE) (pp. 78-85). IEEE.
References:
Naik, N., Diao, R., & Shen, Q. (2016, July). Application of dynamic fuzzy rule interpolation
for intrusion detection: D-FRI-Snort. In 2016 IEEE International Conference on Fuzzy
Systems (FUZZ-IEEE) (pp. 78-85). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





