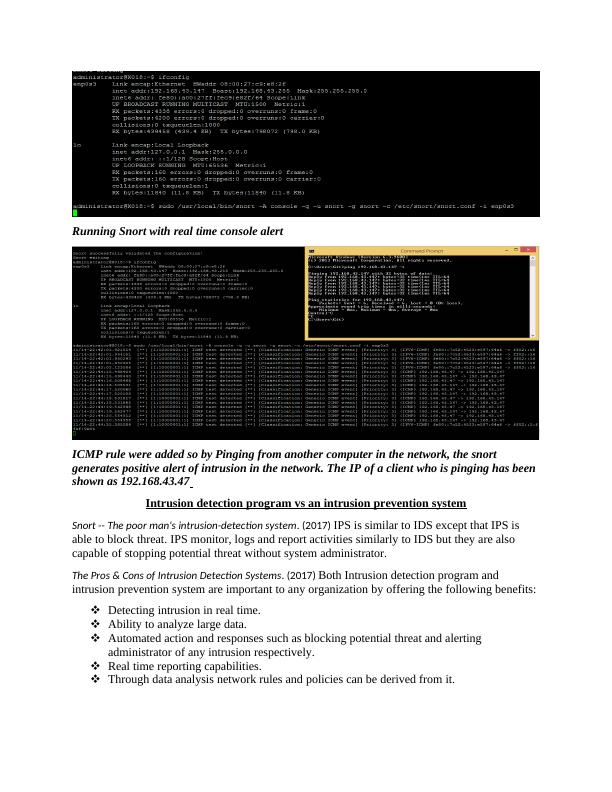
Justification for choosing Snort as IDS
Added on 2020-04-13
4 Pages708 Words101 Views
End of preview
Want to access all the pages? Upload your documents or become a member.
Networking and Security
|4
|801
|57
Demonstration of Network Security Tools
|10
|2109
|85
Intrusion Detection System and Snort: A Comprehensive Guide
|8
|857
|312
Information Management: Intrusion Detection, Firewalls, and Operating System Security
|4
|778
|289
Difference between Firewall and Intrusion Detection System
|4
|454
|21
Cyber Security Detection of Common Attacks Using SNORT Project 2022
|56
|14273
|14