Digital Forensic Investigation
VerifiedAdded on 2021/06/15
|10
|2304
|106
AI Summary
One day I will get a call from MD (Managing Director) of a famous company named as Vamos Solutions. In this company every day a crew they check each and every employee of the company Vamos Solutions to prevent any data theft. In this company every day a crew they check each and every employee of the company Vamos Solutions to prevent any data theft. In this company every day a crew they check each and every employee of the company Vamos Solutions to prevent any data theft.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Contents
1. Introduction...........................................................................................................................2
2. Digital Forensic Investigation Tools....................................................................................2
3. Image file Investigation........................................................................................................5
4. Result analysis......................................................................................................................6
5. Conclusion............................................................................................................................8
References..................................................................................................................................10
1
1. Introduction...........................................................................................................................2
2. Digital Forensic Investigation Tools....................................................................................2
3. Image file Investigation........................................................................................................5
4. Result analysis......................................................................................................................6
5. Conclusion............................................................................................................................8
References..................................................................................................................................10
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1. Introduction
UCLAN High Tech Crime Unit was a company that serves in digital forensic area. I am the
employer of that company. I am working as a digital forensic investigator. One day I will get a
call from MD (Managing Director) of a famous company named as Vamos Solutions.
In this company every day a crew they check each and every employee of the company
Vamos Solutions to prevent any data theft. As usual one day they checked one of his employee.
During the checking he have a USB flash stick in his hand. So security officials’ suspect that the
employee steal something from the office computer. So they informed that to his MD (Managing
Director). So he called me to investigate that case. And he gives a USB memory stick image file
for the investigation. And he said me to find if any data theft was traced, if any submit the
evidence to him.
Intention
The main intention of this investigation is to investigate image file (USB image file)
given to the investigation. That is belongs to the employee of the company.
Purpose
Main objectives,
Examine the USB flash disk
Collect data relevant to the case
Find motivation of the data theft
Identify further details required from the company regards to this case
2. Digital Forensic Investigation Tools
Digital forensics was a process of investing the cybercrimes. (InfoSec Resources, 2018) For
that kind of investigation there are lots and lots of methods and tools are available. (Casey, 2007)
As a digital forensic investigator we have to choose any one of the method. (Dudley-Gough,
2006) Available digital forensic tools are,
Regripper
Access data FTK
Autopsy Tool
Regripper
Regripper was a widely used digital forensic application to carry out a digital forensic
investigation. Carlon carvey was the creator of the software. (InfoSec Resources, 2018) The main
purpose of the software is to extract a data from register of the PC (Personnel Computer). That is
created to reduce the complication and timing of the extraction of computer register. That software
reduce the time to extract the register details from 10 hrs. To some minutes. The software was
created for the less skilled investigator. So it was in very simple form. This software allows to add a
plugin Auditpol (Audit Policy). That is used to find if user changes his audit policies. This software
also has a potential to convert raw image data extracted from the computer register to readable
format. Due this features this product was widely used by the digital forensic investigators.
2
UCLAN High Tech Crime Unit was a company that serves in digital forensic area. I am the
employer of that company. I am working as a digital forensic investigator. One day I will get a
call from MD (Managing Director) of a famous company named as Vamos Solutions.
In this company every day a crew they check each and every employee of the company
Vamos Solutions to prevent any data theft. As usual one day they checked one of his employee.
During the checking he have a USB flash stick in his hand. So security officials’ suspect that the
employee steal something from the office computer. So they informed that to his MD (Managing
Director). So he called me to investigate that case. And he gives a USB memory stick image file
for the investigation. And he said me to find if any data theft was traced, if any submit the
evidence to him.
Intention
The main intention of this investigation is to investigate image file (USB image file)
given to the investigation. That is belongs to the employee of the company.
Purpose
Main objectives,
Examine the USB flash disk
Collect data relevant to the case
Find motivation of the data theft
Identify further details required from the company regards to this case
2. Digital Forensic Investigation Tools
Digital forensics was a process of investing the cybercrimes. (InfoSec Resources, 2018) For
that kind of investigation there are lots and lots of methods and tools are available. (Casey, 2007)
As a digital forensic investigator we have to choose any one of the method. (Dudley-Gough,
2006) Available digital forensic tools are,
Regripper
Access data FTK
Autopsy Tool
Regripper
Regripper was a widely used digital forensic application to carry out a digital forensic
investigation. Carlon carvey was the creator of the software. (InfoSec Resources, 2018) The main
purpose of the software is to extract a data from register of the PC (Personnel Computer). That is
created to reduce the complication and timing of the extraction of computer register. That software
reduce the time to extract the register details from 10 hrs. To some minutes. The software was
created for the less skilled investigator. So it was in very simple form. This software allows to add a
plugin Auditpol (Audit Policy). That is used to find if user changes his audit policies. This software
also has a potential to convert raw image data extracted from the computer register to readable
format. Due this features this product was widely used by the digital forensic investigators.
2

Autopsy Tool
In market there is another software tools was used for the same purpose. But it has more
advantage than the above tool. (Sleuthkit.org, 2018) It has a fantastic graphical user interface. This
software has a high level performance also. So it is also widely used. (Altheide and Harlan Carvey,
2011) That software was created by the company named Basic Technology Corporation. They made
tutorials for this software and it was accessed from their (Basic Technology Corporation) company
website. The software has the following advantages,
Extensible – This software gives the permission to add a new plugins for adding the new
functions required by the user.
Frameworks – Standard procedures or set of instructions that governed by the software
creator was known as frame work. If we want to investigate the forensic case by this
software we have to obey the frame work.
Ease of Use – Its graphical user inter face (GUI) makes that this easy to use.
Standard Procedure to Examine the Forensic Data by Autopsy Tool
Here we have to obey to the set of ten instructions to investigate the digital Forensic case
by this method. (Jahankhani, 2010)
Step 1: Start
It is an online based digital Forensic investigation tool. At first we need to start this
digital Forensic investigation software works on windows OS and Linus OS.
Step 2: Open Newcase
In this digital Forensic software application we simply press the newcase icon which
starts the new investigation dialogue box.
Step 3: Data entering
This digital Forensic investigation tool we must enter the information required by create
dialogue box named as newcase.
Step 4: Selecting an image file
After completing the data entering, the evidence directory selection dialogue box will
open. In this dialogue box we are advised to select the address of the evidence (USB data in
image format).
Step 5: Adding name to the host
After that add host dialogue box will be opened. In this dialogue box you must need to
type the host name and its details.
Step 6: Identification location of host
After that you click the add image button to insert a forensic data (disk file in image
format).
Step 7: New disk image addition
Now we can able to see the dialogue box on the screen in this dialogue box you are
advised to press the add image icon to open a new image file in the Autopsy digital Forensic
software tool.
3
In market there is another software tools was used for the same purpose. But it has more
advantage than the above tool. (Sleuthkit.org, 2018) It has a fantastic graphical user interface. This
software has a high level performance also. So it is also widely used. (Altheide and Harlan Carvey,
2011) That software was created by the company named Basic Technology Corporation. They made
tutorials for this software and it was accessed from their (Basic Technology Corporation) company
website. The software has the following advantages,
Extensible – This software gives the permission to add a new plugins for adding the new
functions required by the user.
Frameworks – Standard procedures or set of instructions that governed by the software
creator was known as frame work. If we want to investigate the forensic case by this
software we have to obey the frame work.
Ease of Use – Its graphical user inter face (GUI) makes that this easy to use.
Standard Procedure to Examine the Forensic Data by Autopsy Tool
Here we have to obey to the set of ten instructions to investigate the digital Forensic case
by this method. (Jahankhani, 2010)
Step 1: Start
It is an online based digital Forensic investigation tool. At first we need to start this
digital Forensic investigation software works on windows OS and Linus OS.
Step 2: Open Newcase
In this digital Forensic software application we simply press the newcase icon which
starts the new investigation dialogue box.
Step 3: Data entering
This digital Forensic investigation tool we must enter the information required by create
dialogue box named as newcase.
Step 4: Selecting an image file
After completing the data entering, the evidence directory selection dialogue box will
open. In this dialogue box we are advised to select the address of the evidence (USB data in
image format).
Step 5: Adding name to the host
After that add host dialogue box will be opened. In this dialogue box you must need to
type the host name and its details.
Step 6: Identification location of host
After that you click the add image button to insert a forensic data (disk file in image
format).
Step 7: New disk image addition
Now we can able to see the dialogue box on the screen in this dialogue box you are
advised to press the add image icon to open a new image file in the Autopsy digital Forensic
software tool.
3

Step 8: Selecting the image file location
This is an option helps to make a duplicate copy of the image file. Because working with
original file has some deficiencies. When working with duplicate there is no problem.
Step 9: Investigation gallery
This is one of the advanced feature in this Autopsy forensic investigation tool which is
used for adding a host.
Step 10: Other features
In this stage you can see the different options on the screen, the different options are very
very useful on the investigation of the case.
Access data FTK
Forensic Tool Kit was an abbreviation FTK. It is a mostly used digital Forensic software
application for the purpose of examining and collecting the evidences of the digital forensics.
(AccessData, 2018) Which is created by Access Data Corporation. They sells the various
software tools for forensic investigation. It was helped to scan digital forensic data. This digital
Forensic software tool kit was also helps to create disk image this function was called as FTK
imager. This digital Forensic software application which gives flexibility in examination. Here
we would see about some of the digital Forensic image formats for various disk image file can be
analyzed by Accessdata Forensic Tool Kit digital Forensic software tool are as listed below,
Error Code Modeler Disc Image
Encase Image
Virtual Compact Disk Format
File Disk Image
Standard operating sequences of Accessdata Forensic Tool Kit
Accessdata Forensic Tool Kit was most commonly used DF software tool among other
digital forensic investigating tool kit, because of its easy working instructions. And various
stages involved in the investigation of DF analysis of the digital forensic image.
Step 1: Evidence file adding
Here first choose the evidence type among the available four types of evidence type that
is given to analyze. After that we need to choose the directory.
Step 2: Evidence tree
The tree structured arrangement of evidences was a tree developed by the digital forensic
tool to analyze the various files and folders are there in the image file to be given.
Step 3: Virtual disk mounting
In this digital forensic software we have option to mount a analyzed data as a virtual disk
(Read only Purpose).
4
This is an option helps to make a duplicate copy of the image file. Because working with
original file has some deficiencies. When working with duplicate there is no problem.
Step 9: Investigation gallery
This is one of the advanced feature in this Autopsy forensic investigation tool which is
used for adding a host.
Step 10: Other features
In this stage you can see the different options on the screen, the different options are very
very useful on the investigation of the case.
Access data FTK
Forensic Tool Kit was an abbreviation FTK. It is a mostly used digital Forensic software
application for the purpose of examining and collecting the evidences of the digital forensics.
(AccessData, 2018) Which is created by Access Data Corporation. They sells the various
software tools for forensic investigation. It was helped to scan digital forensic data. This digital
Forensic software tool kit was also helps to create disk image this function was called as FTK
imager. This digital Forensic software application which gives flexibility in examination. Here
we would see about some of the digital Forensic image formats for various disk image file can be
analyzed by Accessdata Forensic Tool Kit digital Forensic software tool are as listed below,
Error Code Modeler Disc Image
Encase Image
Virtual Compact Disk Format
File Disk Image
Standard operating sequences of Accessdata Forensic Tool Kit
Accessdata Forensic Tool Kit was most commonly used DF software tool among other
digital forensic investigating tool kit, because of its easy working instructions. And various
stages involved in the investigation of DF analysis of the digital forensic image.
Step 1: Evidence file adding
Here first choose the evidence type among the available four types of evidence type that
is given to analyze. After that we need to choose the directory.
Step 2: Evidence tree
The tree structured arrangement of evidences was a tree developed by the digital forensic
tool to analyze the various files and folders are there in the image file to be given.
Step 3: Virtual disk mounting
In this digital forensic software we have option to mount a analyzed data as a virtual disk
(Read only Purpose).
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

3. Digital forensics
Forensics was a science of investigating the things and collecting the evidence. (Carvey, n.d.)
Here digital forensics means the process of investigating the digital data stored on the digital
storage devices like USB flash stick, computer hard disk, and online based cloud storage. The
digital forensics also termed as the computer forensics. That is carried out to investigate the
cybercrimes and collect the evidences against the cybercriminal.
Digital forensic investigation has a huge variety of applications like ensure the security of the
confidential data. Here the evidences are retrieved from the computers, external storage devices,
online cloud storages etc… this also carried out by the private sectors. Because the no of users of
the computer and internet was increased day to day. Growth of the computer technologies are
also favorable for the cyber criminals.
In digital forensic investigation we need collect the evidences against the criminals by
inspecting the computer f the criminals. Then we have to convert the details into the readable
format. Then we have to create a report that must be understandable by the non-technical
audience. This is the standard procedure followed by all the digital forensic investigators. All the
details are collected must be stored as duplicate file because working with the original file was
not too good there is a possibility of loose the data contains the important evidences. Digital
forensic investigation also used to make the security system more strong. That ensures that the
same error won’t happen again.
4. Image file Investigation
In this case we got a USB flash stick image file for a digital forensic investigation. This USB
flash stick belongs to the employee of the Vamos Solutions. In this case we examine the USB
flash stick by use of DF software tool named as Accessdata Forensic Tool Kit. And investigation
reports are obtained from the pen drive data in image format was showed below.
5
Forensics was a science of investigating the things and collecting the evidence. (Carvey, n.d.)
Here digital forensics means the process of investigating the digital data stored on the digital
storage devices like USB flash stick, computer hard disk, and online based cloud storage. The
digital forensics also termed as the computer forensics. That is carried out to investigate the
cybercrimes and collect the evidences against the cybercriminal.
Digital forensic investigation has a huge variety of applications like ensure the security of the
confidential data. Here the evidences are retrieved from the computers, external storage devices,
online cloud storages etc… this also carried out by the private sectors. Because the no of users of
the computer and internet was increased day to day. Growth of the computer technologies are
also favorable for the cyber criminals.
In digital forensic investigation we need collect the evidences against the criminals by
inspecting the computer f the criminals. Then we have to convert the details into the readable
format. Then we have to create a report that must be understandable by the non-technical
audience. This is the standard procedure followed by all the digital forensic investigators. All the
details are collected must be stored as duplicate file because working with the original file was
not too good there is a possibility of loose the data contains the important evidences. Digital
forensic investigation also used to make the security system more strong. That ensures that the
same error won’t happen again.
4. Image file Investigation
In this case we got a USB flash stick image file for a digital forensic investigation. This USB
flash stick belongs to the employee of the Vamos Solutions. In this case we examine the USB
flash stick by use of DF software tool named as Accessdata Forensic Tool Kit. And investigation
reports are obtained from the pen drive data in image format was showed below.
5
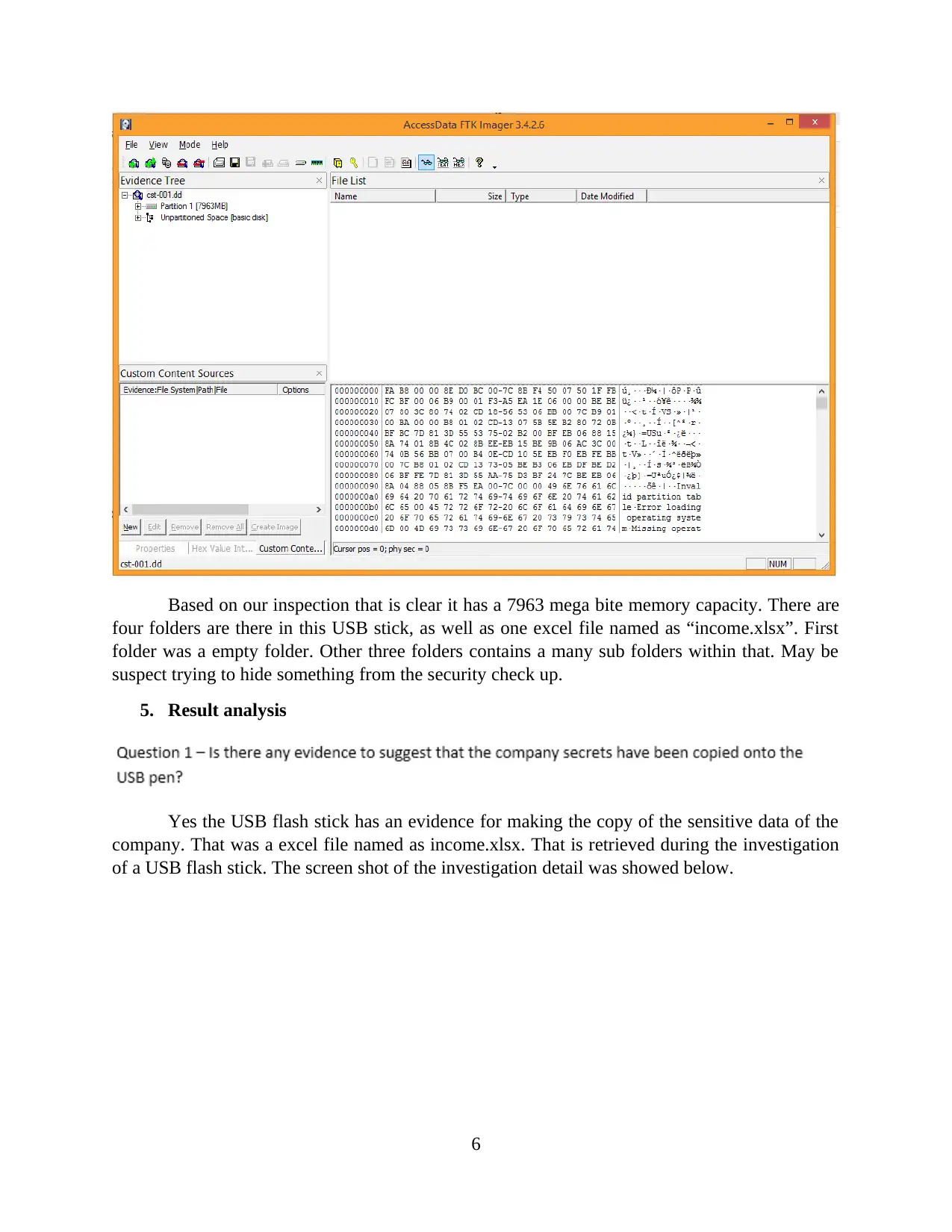
Based on our inspection that is clear it has a 7963 mega bite memory capacity. There are
four folders are there in this USB stick, as well as one excel file named as “income.xlsx”. First
folder was a empty folder. Other three folders contains a many sub folders within that. May be
suspect trying to hide something from the security check up.
5. Result analysis
Yes the USB flash stick has an evidence for making the copy of the sensitive data of the
company. That was a excel file named as income.xlsx. That is retrieved during the investigation
of a USB flash stick. The screen shot of the investigation detail was showed below.
6
four folders are there in this USB stick, as well as one excel file named as “income.xlsx”. First
folder was a empty folder. Other three folders contains a many sub folders within that. May be
suspect trying to hide something from the security check up.
5. Result analysis
Yes the USB flash stick has an evidence for making the copy of the sensitive data of the
company. That was a excel file named as income.xlsx. That is retrieved during the investigation
of a USB flash stick. The screen shot of the investigation detail was showed below.
6
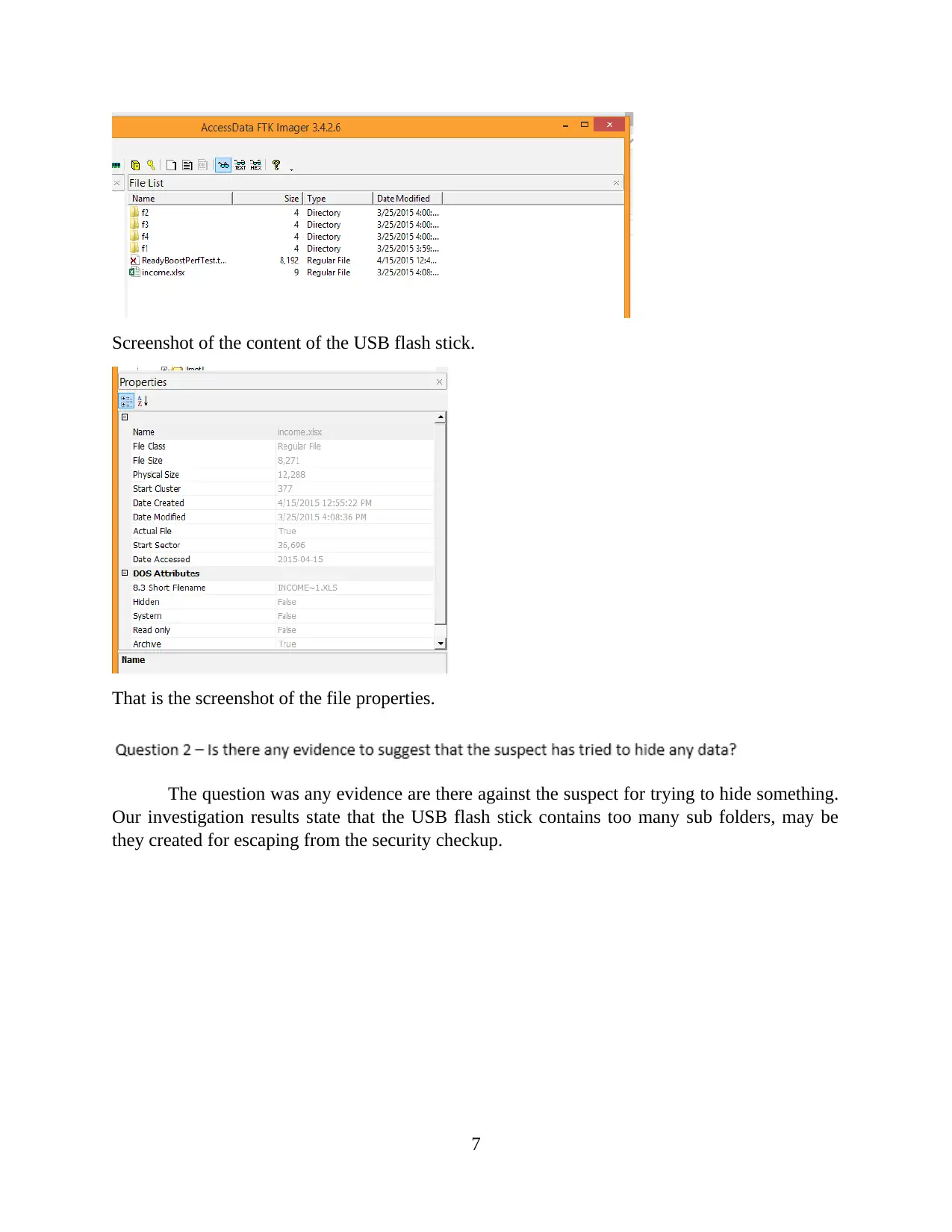
Screenshot of the content of the USB flash stick.
That is the screenshot of the file properties.
The question was any evidence are there against the suspect for trying to hide something.
Our investigation results state that the USB flash stick contains too many sub folders, may be
they created for escaping from the security checkup.
7
That is the screenshot of the file properties.
The question was any evidence are there against the suspect for trying to hide something.
Our investigation results state that the USB flash stick contains too many sub folders, may be
they created for escaping from the security checkup.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Screenshot of the investigation result that shows too dummy folders.
Investigation results gives the strong evidence against the employee. That is the creation of
dummy folders with same names. That is done by the employee because he wants to hide
something from the onsite security officials. The screen shot of the dummy folder tree was
showed in the above figure.
For the further investigation we requires the following details from the company.
Hard disk details of the PC
Online cloud storage details of the suspect
6. Conclusion
Investigation reports regards to the case of Vamos Solutions state that the employee copied
the file from the office computer which has the sensitive details about the company. The data
stealing of the employee was confirmed. In this investigation we investigate the USB flash stick
image file of the suspect. On this investigation we found the excel file named as “income.xlsx”.
Maybe this a file copied from the offices computer. The suspect created a too many sub folders
on the same name (f1, f2, f3, and f4). Those are created to hide something (it may be the
8
Investigation results gives the strong evidence against the employee. That is the creation of
dummy folders with same names. That is done by the employee because he wants to hide
something from the onsite security officials. The screen shot of the dummy folder tree was
showed in the above figure.
For the further investigation we requires the following details from the company.
Hard disk details of the PC
Online cloud storage details of the suspect
6. Conclusion
Investigation reports regards to the case of Vamos Solutions state that the employee copied
the file from the office computer which has the sensitive details about the company. The data
stealing of the employee was confirmed. In this investigation we investigate the USB flash stick
image file of the suspect. On this investigation we found the excel file named as “income.xlsx”.
Maybe this a file copied from the offices computer. The suspect created a too many sub folders
on the same name (f1, f2, f3, and f4). Those are created to hide something (it may be the
8

sensitive data of the company) from the security checkup carried out by the office security
officers.
9
officers.
9

References
AccessData. (2018). Forensic Toolkit. [online] Available at: https://accessdata.com/products-
services/forensic-toolkit-ftk [Accessed 8 May 2018].
Altheide, C. and Harlan Carvey (2011). Digital Forensics with Open Source Tools. Elsevier
Science.
Carvey, H. (2018). Using RegRipper. [online] Windowsir.blogspot.in. Available at:
http://windowsir.blogspot.in/2011/04/using-regripper.html [Accessed 8 May 2018].
Carvey, H. (n.d.). Windows registry forensics.
Casey, E. (2007). Handbook of computer crime investigation. Amstersdam: Academic.
Dudley-Gough, N. (2006). Digital Forensic Certification Board. Digital Investigation, 3(1), pp.7-
8.
InfoSec Resources. (2018). 7 Best Computer Forensics Tools. [online] Available at:
http://resources.infosecinstitute.com/7-best-computer-forensics-tools/#gref [Accessed 8 May
2018].
Jahankhani, H. (2010). Handbook of electronic security and digital forensics. New Jersey: World
Scientific.
Sleuthkit.org. (2018). Autopsy: Description. [online] Available at:
https://www.sleuthkit.org/autopsy/desc.php [Accessed 8 May 2018].
10
AccessData. (2018). Forensic Toolkit. [online] Available at: https://accessdata.com/products-
services/forensic-toolkit-ftk [Accessed 8 May 2018].
Altheide, C. and Harlan Carvey (2011). Digital Forensics with Open Source Tools. Elsevier
Science.
Carvey, H. (2018). Using RegRipper. [online] Windowsir.blogspot.in. Available at:
http://windowsir.blogspot.in/2011/04/using-regripper.html [Accessed 8 May 2018].
Carvey, H. (n.d.). Windows registry forensics.
Casey, E. (2007). Handbook of computer crime investigation. Amstersdam: Academic.
Dudley-Gough, N. (2006). Digital Forensic Certification Board. Digital Investigation, 3(1), pp.7-
8.
InfoSec Resources. (2018). 7 Best Computer Forensics Tools. [online] Available at:
http://resources.infosecinstitute.com/7-best-computer-forensics-tools/#gref [Accessed 8 May
2018].
Jahankhani, H. (2010). Handbook of electronic security and digital forensics. New Jersey: World
Scientific.
Sleuthkit.org. (2018). Autopsy: Description. [online] Available at:
https://www.sleuthkit.org/autopsy/desc.php [Accessed 8 May 2018].
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





